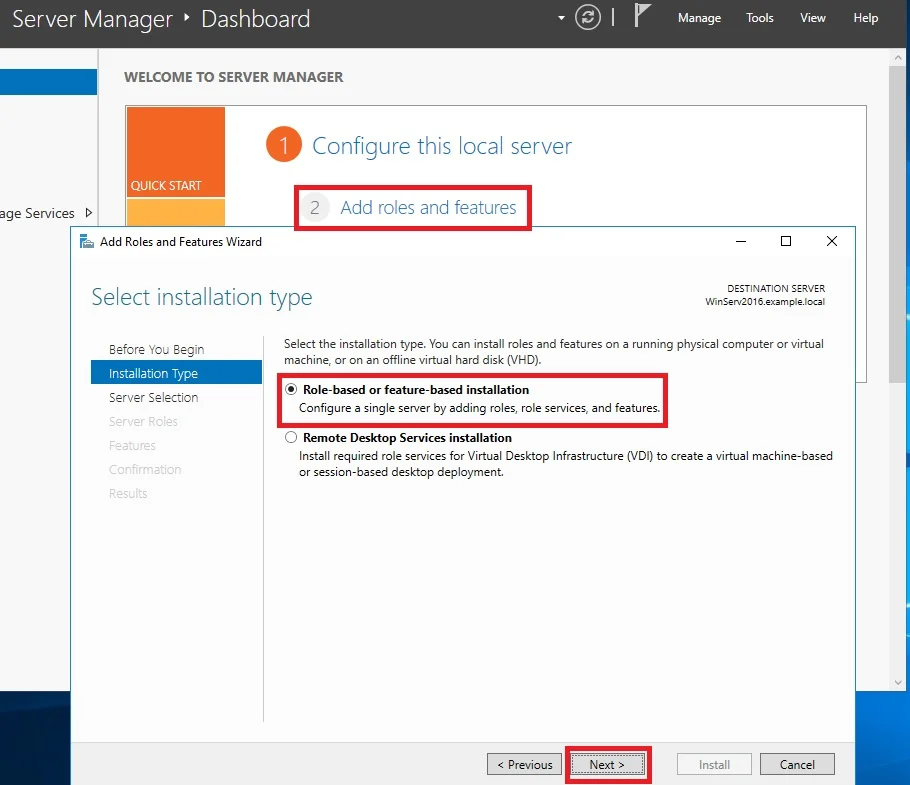
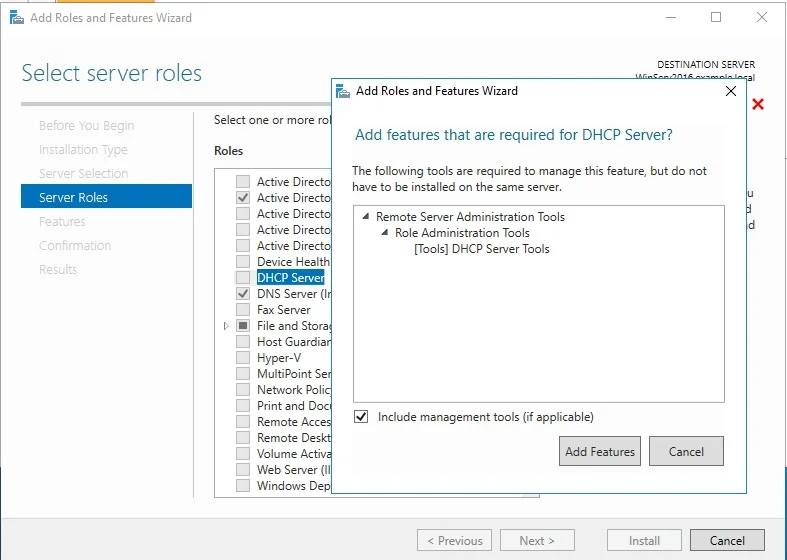
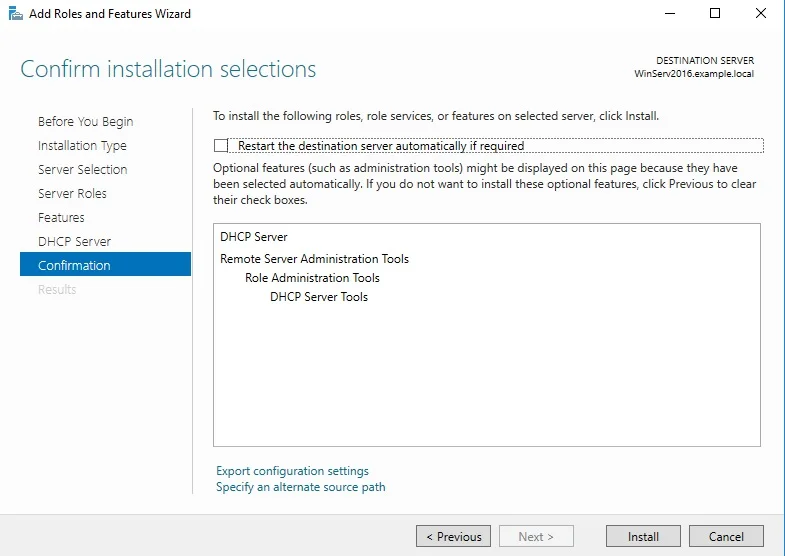
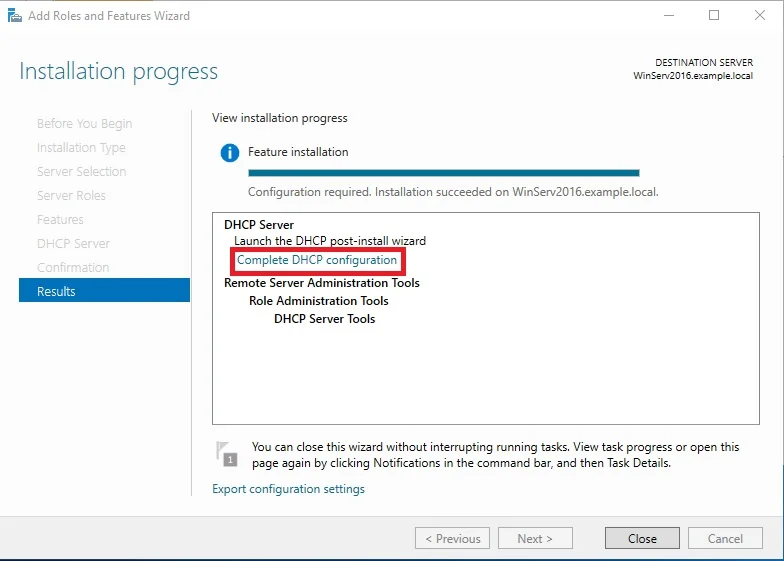
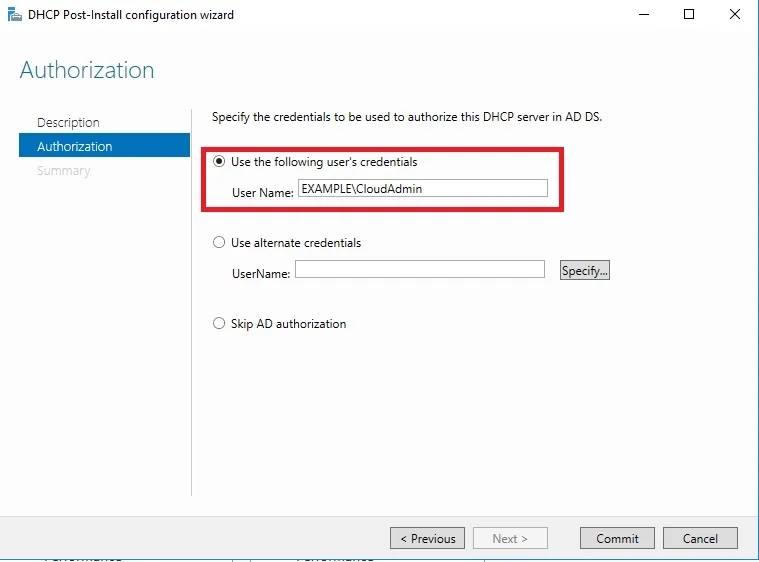
⊹ CCIE ⊹
CCIE DHCP
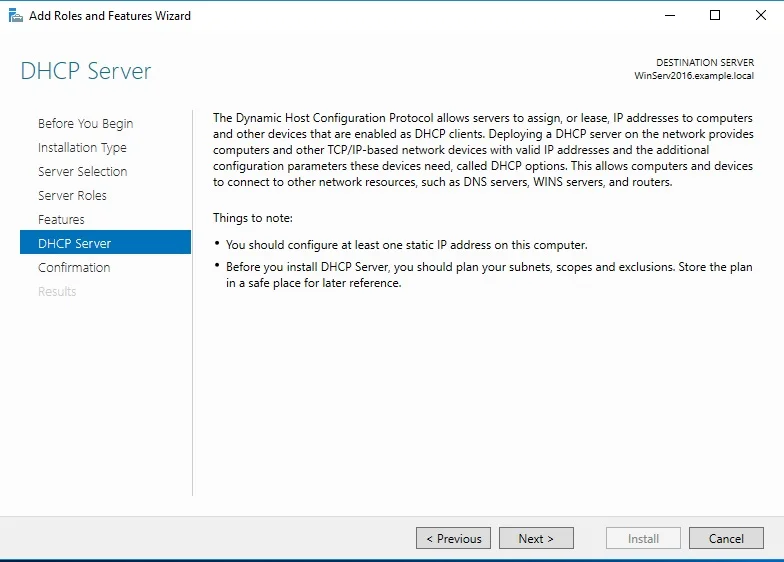
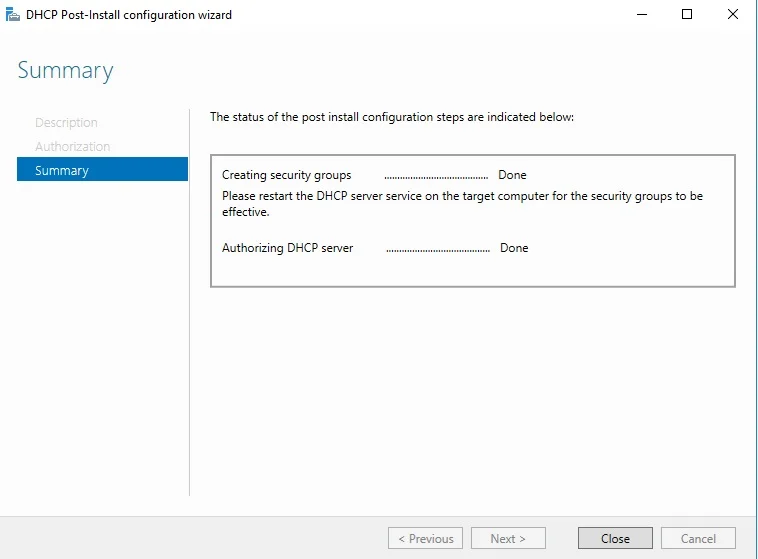
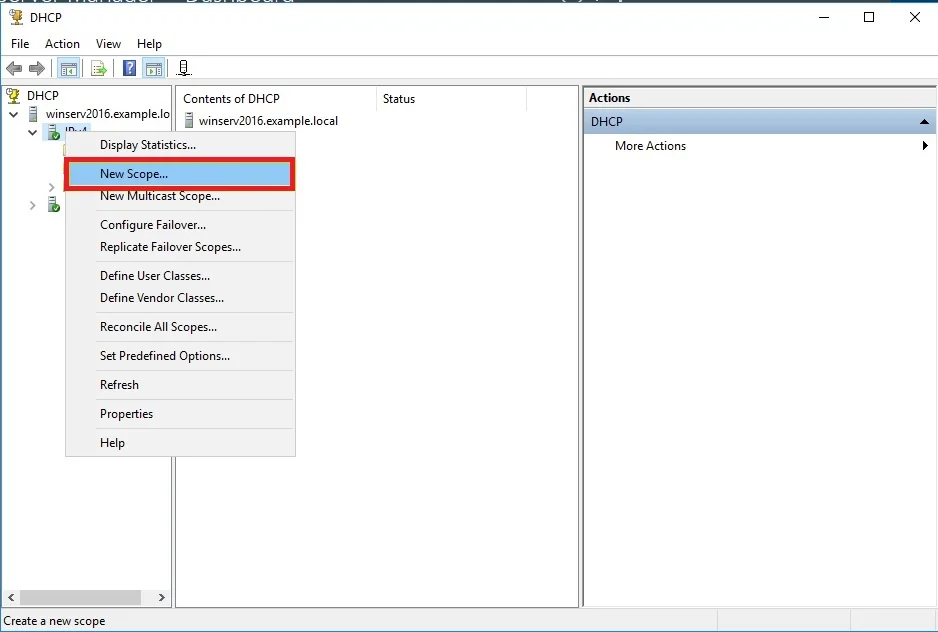
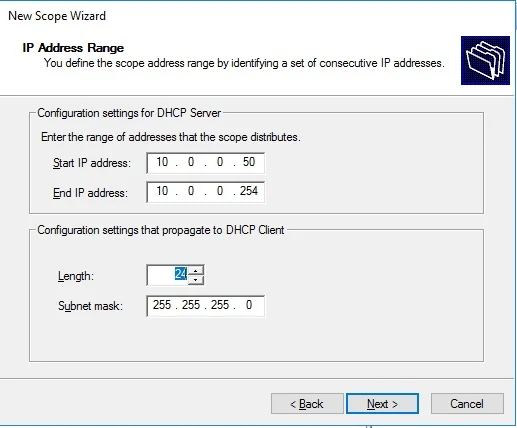
DHCP
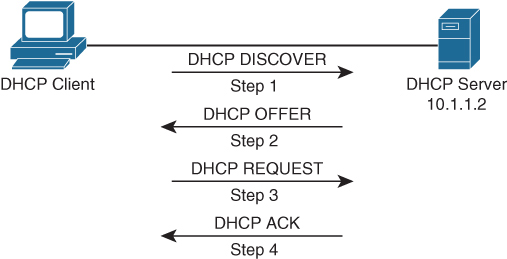
DHCP Client uses source port 68 and destination UDP port 67
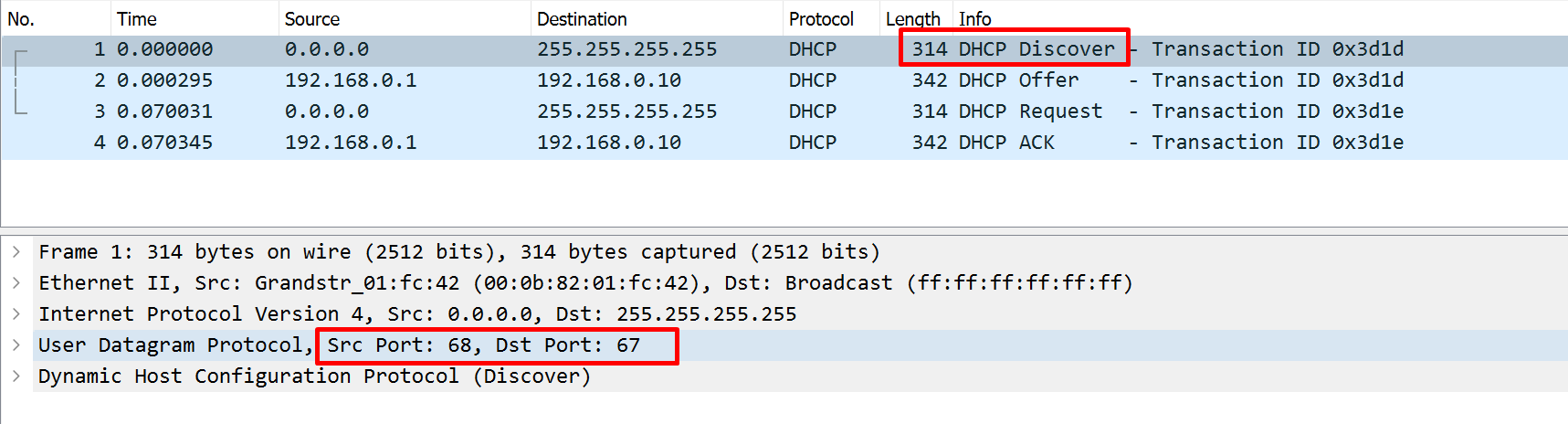

DHCPDISCOVER
DHCPDISCOVER is a broadcast message to 255.255.255.255 and MAC address FFFF:FFFF:FFFF, The source IP address is 0.0.0.0, and the source MAC address is the MAC address of the sending device
DHCPOFFER
DHCP server if on subnet or remote, responds with DHCPOFFER, if more than one DHCP servers respond then client typically selects the server that sent the first DHCPOFFER response it received
DHCPREQUEST
DHCP client selects a server and responds by sending a broadcasted DHCPREQUEST message indicating that it will be using the address provided in the DHCPOFFER
DHCPDECLINE
This message is sent from a client to a DHCP server to inform the server that an IP address is already in use on the network.
DHCPACK
DHCP server responds to the client with a DHCPACK message indicating that the IP address is leased to the client and includes any additional DHCP options
DHCPNAK
A DHCP server sends this message to a client and informs the client that the DHCP server declines to provide the client with the requested IP configuration information.
DHCPRELEASE
A client sends this message to a DHCP server and informs the DHCP server that the client has released its DHCP lease, thus allowing the DHCP server to reassign the client IP address to another client.
DHCPINFORM
A client sends this message to a DHCP server and requests IP configuration parameters. Such a message might be sent from an access server requesting IP configuration information for a remote client attaching to the access server.
DHCP relay
If DHCP server is located in remote subnet then it gateway on client’s subnet need to have DHCP relay agent configured in order to forward the broadcast packets as unicast packets to the server
Routers dont just relay DHCP but can also relay following protocols to remote servers
- TFTP
- Domain Name System (DNS)
- Internet Time Service (ITS)
- NetBIOS name server
- NetBIOS datagram server
- BootP
- TACACS
Router interface as DHCP client
Router or switch can act as DHCP client to obtain IP address on its own interface “ip address dhcp”
Router interface as DHCP server
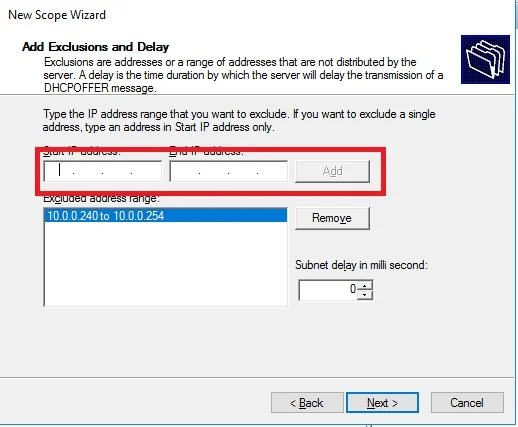
When router or switch is configured as a DHCP and pool is configured, excluding IP address with “ip dhcp excluded-address 10.8.8.1 10.8.8.10”, command prevents DHCP from assigning those IP addresses to a client. Note that you do not have to include the IP address of the router interface in this exclusion because the router never hands out its own interface IP address.
Potential DHCP issues
Helper address not configured: Router not configured with helper address under the interface facing clients – dhcp relay not configured
Incorrect Server configured: Incorrect DHCP server IP configured under helper address
Pool missing from DHCP server: Request originating from VLAN does not exist on DHCP server as pool, that VLAN or interface must also have IP address and helper configured
Pool exhaustion: DHCP pool could be out of IP addresses – pool exhaustion
High lease duration can cause pool exhaustion: A too high lease duration may cause pool exhaustion if you have more clients than the pool can support
Consider a wireless network at an airport. Let’s say there are 4096 addresses in the pool with a lease duration of 12 hours. Since users are typically not in an airport for more than 4 hours, this lease duration is too long, and the IP address will still be leased to that user until the lease expires, even if the user is no longer in the airport. Therefore, as the day progresses, more addresses are leased, until the pool is exhausted. So, setting a lower lease duration, such as 3 hours, would ensure that the lease expires sooner rather than later and helps prevent pool exhaustion.
Duplicate IP addresses: A DHCP server might hand out an IP address to a client that is already statically assigned to another host on the network. These duplicate IP addresses can cause connectivity issues for both the DHCP client and the host that was statically configured for the IP address.
next post
Multicast
Multicast
It allows a source host to send packets to a group of destination hosts (receivers) in an efficient manner
IGMP operates on Layer 2
PIM operates on Layer 3
Always start from source when thinking of multicast and then branch out to receivers top to bottom
Multicast Source connects to a router called First-Hop router or FHR, “First hop from the top but below source”
Router that has receivers connected is called Last-Hop router or LHR, on its LAN side it will have IGMP enabled, and also a role called IGMP querier will be active on that LAN side
Between these 2 routers, PIM will operate
Switch will run IGMP snooping in order to snoop the IGMP messages
Without Mutlicast
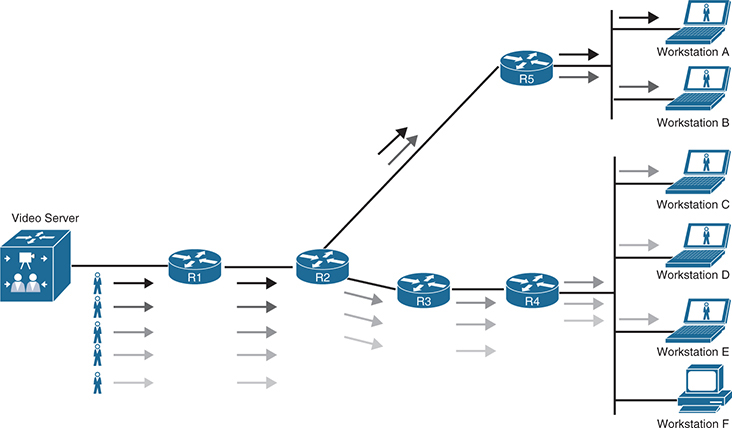
the network link between R1 and R2 needs 50 Mbps of bandwidth
Stream of data is sent to special addresses called group addresses
Local network control block 224.0.0.0 to 224.0.0.255
Addresses in the local network control block are used for “control traffic” that is not forwarded outside of a local broadcast domain. Examples of this type of multicast control traffic are all hosts in this subnet (224.0.0.1), all routers in this subnet (224.0.0.2), and all PIM routers (224.0.0.13). control traffic sent out on this range has TTL of 1 and packet expires as soon as it enters next hop router, you might think that packers from 224.0.0.0 network cannot propagate through the network? even though the packet expires reaching next router but that message is delivered through out the network using these packets with TTL of 1
224.0.0.1
All hosts in this subnet (all hosts listen on this address)
224.0.0.2
All routers in this subnet
224.0.0.5
All OSPF routers (AllSPFRouters)
224.0.0.6
All OSPF DRs (AllDRouters)
224.0.0.10
All EIGRP routers
224.0.0.13
All PIM routers
224.0.0.18
VRRP
224.0.0.22
IGMPv3
224.0.0.102
HSRPv2 and GLBP
Internetwork control block (224.0.1.0/24):
Addresses in the internetwork control block are used for “control traffic” that may be forwarded through the Internet. Examples include Network Time Protocol (NTP) (224.0.1.1), Cisco-RP-Announce (224.0.1.39), and Cisco-RP-Discovery (224.0.1.40).
224.0.1.1
NTP
224.0.1.39
Cisco-RP-Announce (Auto-RP)
224.0.1.40
Cisco-RP-Discovery (Auto-RP)
Source Specific Multicast (SSM) block
232.0.0.0 to 232.255.255.255 232.0.0.0/8
This is the default range used by SSM. SSM is a PIM extension
SSM forwards traffic only from sources for which the receivers have explicitly expressed interest.
Used for one-to-many applications.
Administratively scoped block 239.0.0.0 to 239.255.255.255
This range is like private 10.0.0.0/8 range that can be used for multicasting internally in organsiation’s network
Multicast & Layer 2
In order for multicast packets to be delivered to end hosts, their NIC needs to listen to “Multicast Group’s MAC address”
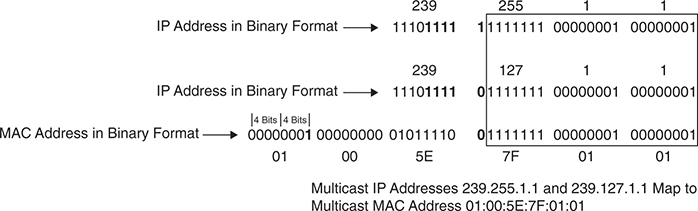
The first 24 bits of a multicast MAC address always start with “01:00:5E”
That “01” is Individual / Group bit (group means multicast group)
remaining 23 bits of the MAC address come from the lower 23 bits of the IPv4 multicast address.
an example of mapping the multicast IP address 239.255.1.1 into the multicast MAC address 01:00:5E:7F:01:01
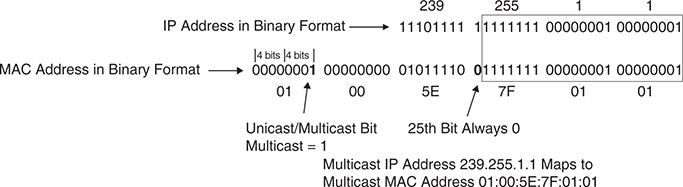
“some multicast group IP addresses can map to single MAC address“
because first 9 bits of the multicast IP address are not copied into the multicast mac address – and all multicast IP address have common first 1110, that leaves 9 – 4 = 5 bits that are varaible between multicast IP addresses that are not copied into the Multicast mac address
Because of this, there are 32 (25) multicast IP addresses that are not universally unique and could correspond to a single MAC address or overlap
When a receiver wants to receive a specific multicast feed, it sends an IGMP join using the multicast IP group address for that feed, The receiver reprograms its interface to accept the multicast MAC group address that correlates to the group address
IGMPv2
Receivers use IGMP to join multicast groups and leave multicast groups, When a receiver wants to receive multicast traffic from a source, it sends an IGMP join to its router. If the router does not have IGMP enabled on the interface, the request is ignored.
Most common IGMP version is IGMPv2
IGMPv3 is used by SSM
IGMPv2 uses “packet” that travels to the router with TTL of 1, if a router is the one that decremented the TTL from 1 to 0, that router does not proceed with forwarding / routing of that packet and that packet is then discarded.
Type Field
Version 2 membership report
also known as IGMP join
used by receivers to join a multicast group
or to respond to a local router’s membership query message
Version 1 membership report
is used by receivers for backward compatibility with IGMPv1
Version 2 leave group
is used by receivers to indicate they want to stop receiving multicast traffic for a group they joined.
General membership query is periodically sent to the all-hosts group address 224.0.0.1 to see whether there are any receivers in the attached subnet. It sets the group address field to 0.0.0.0 (and not to a specific group address).
Group specific query is sent in response to a leave group message to the group address the receiver requested to leave, this is a test by local router to see if there are any more receivers on LAN and if this leaving router is the last receiver.
Upstream after receiving IGMP join message from LAN
The local router once receives a IGMP join message on LAN side then sends a PIM join message upstream toward the source to request the multicast stream
When the local router starts receiving the multicast stream, it forwards it downstream to the subnet where the receiver that requested it resides.
Router then starts periodically sending general membership query messages into the subnet, to the all-hosts group address 224.0.0.1, to see whether any members are in the attached subnet. The general query message contains a max response time field that is set to 10 seconds by default
In response to this query, “receivers” set an internal random timer between 0 and 10 seconds (which can change if the max response time is using a non-default value). When the timer expires, receivers send membership reports for each group they belong to. If a receiver receives another receiver’s report for one of the groups it belongs to while it has a timer running, it stops its timer for the specified group and does not send a report; this is meant to suppress duplicate reports.
When the leave group message is received by the router, it follows with a group-specific membership query to the group multicast address to determine whether there are any receivers interested in the group remaining in the subnet. If there are none, the router removes the IGMP state for that group.
IGMP querier election (if there is more than one IGMP router on segment)
If there is more than one router in a LAN segment, an IGMP querier election takes place to determine which router will be the querier.
IGMPv2 routers send general membership “query” messages destined to the 224.0.0.1 multicast address
When an IGMPv2 router receives such a message, It cannot receive this “query” message, as host only “report” and not “query” that means there is another router on thet network
The router with the lowest interface IP address in the LAN subnet is elected as the IGMP querier.
All the non-
querier routers (routers that did not have lowest IP and lost) start a timer that resets each time they receive a membership query report from the querier router.
If the querier router stops sending membership queries for some reason (for instance, if it is powered down), a new querier election takes place. A non-querier router waits twice the query interval, which is by default 60 seconds, and if it has heard no queries from the IGMP querier, it triggers IGMP querier election.
IGMPv3
In IGMPv2, when a receiver sends a membership report to join a multicast group, it does not specify which source it would like to receive multicast traffic from. IGMPv3 is an extension of IGMPv2 that adds support for multicast source
gives the receivers the capability to pick the source they wish to accept multicast traffic from, it could be sender in same group such as 239.0.0.12 but receiver has ability to receive from better sender
IGMPv3 is designed to coexist with IGMPv1 and IGMPv2
IGMPv3 sources can be mentioned by receivers in following ways:
Include mode: In this mode, the receiver announces membership to a multicast group address and provides a list of source addresses (the include list) from which it wants to receive traffic.
Exclude mode: In this mode, the receiver announces membership to a multicast group address and provides a list of source addresses (the exclude list) from which it does not want to receive traffic. The receiver then receives traffic only from sources whose IP addresses are not listed on the exclude list. To receive traffic from all sources, which is the behavior of IGMPv2, a receiver uses exclude mode membership with an empty exclude list.
IGMPv3 is used to provide source filtering for Source Specific Multicast (SSM).
IGMP Snooping
To optimize forwarding and remove flooding, switches need a method of sending traffic only to interested receivers.
A multicast MAC address is never used as a source MAC address
And because multicast mac address is never seen as source MAC address, and never learned (because of source based learning), multicast frame going into the switch as destination is treated as unknown frame and flood them out all ports just like broadcast
IGMP snooping works by examining IGMP joins sent by receivers and maintaining a table of groups, IGMP joins and interfaces. When the switch receives a multicast frame destined for a multicast group, it forwards the packet only out the ports where IGMP joins were received for that specific multicast group
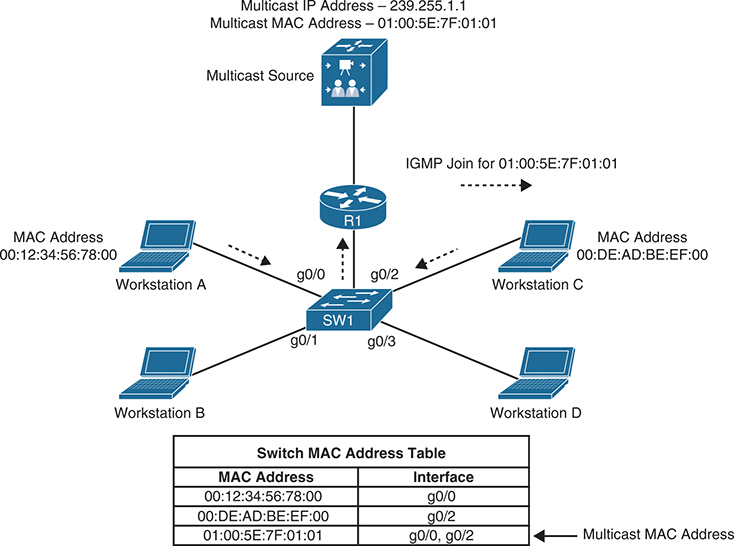
source sending traffic to 239.255.1.1 (01:00:5E:7F:01:01). Switch 1 receives this traffic, and it forwards it out only the g0/0 and g0/2 interfaces because those are the only ports that received IGMP joins for that group.
Even with IGMP snooping enabled, some multicast groups are still flooded on all ports (for example, 224.0.0.0/24 reserved addresses Local Network Control Block).
If IGMP snooping is not enabled, then a static entry can also be added in mac address table. A multicast static entry can also be manually programmed into the MAC address table, but this is not a scalable solution because it cannot react dynamically to changes; for this reason, it is not a recommended approach.
Protocol Independent Multicast
PIM uses routing table built and works at Layer 3
The two basic types of multicast distribution trees are
source trees as shortest path trees (SPTs), and shared trees (not shortest)
Source Trees or Shortest Path Tree SPT
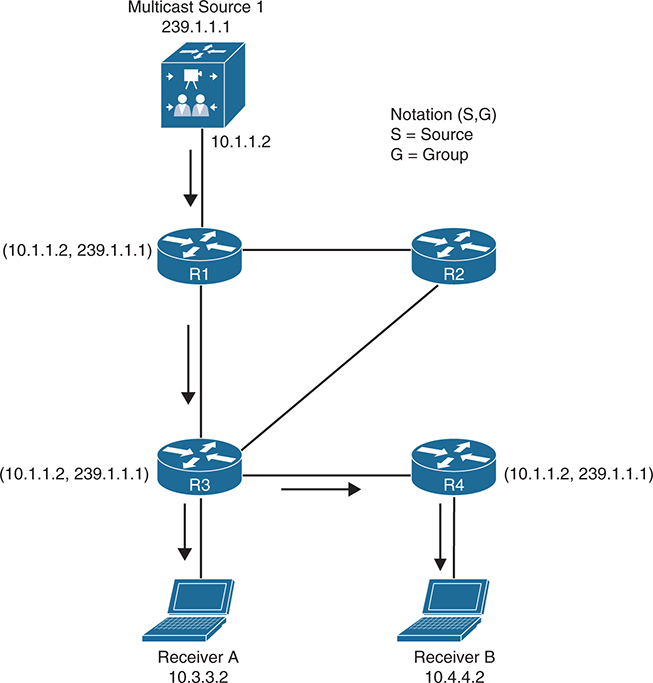
A source tree or SPT or (S,G) is a multicast distribution tree where the source is the root of the tree, and branches form a distribution tree through the network towards receivers. When this tree is built, it has the shortest path through from the source to the leaves of the tree; for this reason, it is also referred to as a shortest path tree (SPT).
Forwarding state of the SPT is known by the notation (S,G), pronounced “S comma G,” where S is the sender of the multicast stream (server), and G is the multicast group address
Notice that this is Specific source / sending server per group, if a new server or sender is creates a new (S,G) will need to be built
Shared Trees or Rendezvous Point Trees RPT
A shared tree or (*,G) is a multicast distribution tree where the root of the shared tree is not the source but a router designated as the rendezvous point (RP) is, For this reason, shared trees are also referred to as rendezvous point trees (RPTs)
Multicast traffic is forwarded down the shared tree via RP even if source is next to receivers
shared tree is referred to by the notation (*,G), pronounced “star comma G.”
notice that it is any senders / source servers per group
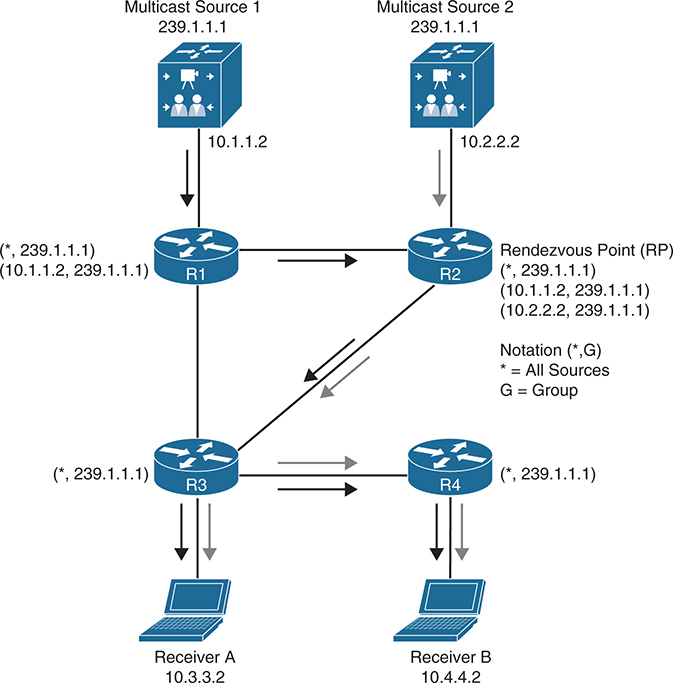
RP keeps record of all the senders (while R1 only has record of its sender) and is also responsible for receiving all Mcast streams, and then forwarded out of the RP
One of the benefits of shared trees over source trees is that they require fewer multicast entries (for example, S,G and *,G). For instance, as more sources are introduced into the network, sending traffic to the same multicast group, the number of multicast entries for R3 and R4 always remains the same: (*,239.1.1.1)
The major drawback of shared trees is that the receivers receive traffic from all the sources sending traffic to the same multicast group. Even though the receivers’ applications can filter out the unwanted traffic, this situation still generates a lot of unwanted network traffic, wasting bandwidth. In addition, because shared trees can allow multiple sources in an IP multicast group, there is a potential network security issue because unintended sources could send unwanted packets to receivers.
PIM Terminology
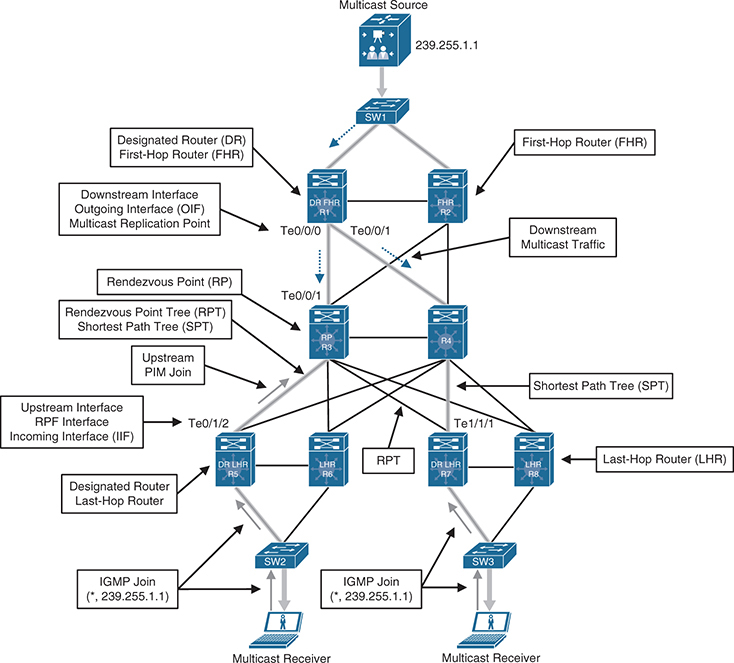
This diagram should be read from top or source to down, all the roles are from top to bottom such as First-hop Router
Reverse Path Forwarding (RPF) interface
The interface with the lowest-cost path to the IP address of the source (SPT) or the RP, If multiple interfaces have the same cost, the interface with the highest IP address is chosen as the tiebreaker
Also known as the incoming interface (IIF) (Incoming interface because this is where incoming multicast traffic will come), The only type of interface that can accept multicast traffic coming from the source, which is the same as the RPF interface. An example of this type of interface is Te0/0/1 on R3 because the shortest path to the source is known through this interface.
Another example of this type of interface is Te0/1/2 on R5 because it is the shortest path to the source. Another example is Te1/1/1 on R7 because the shortest path to the source was determined to be through R4.

RPF neighbor
The PIM neighbor or PIM enabled router on the RPF interface, if R7 is using the RPT shared tree, the RPF neighbor would be R3, which is the lowest-cost path to the RP. If it is using the SPT, R4 would be its RPF neighbor because it offers the lowest cost to the source.
A PIM join always travels upstream toward the source

Downstream interface
Any interface that is used to forward multicast traffic down the tree, also known as an outgoing interface (OIF). An example of a downstream interface is R1’s Te0/0/0 interface, which forwards multicast traffic to R3’s Te0/0/1 interface.

Outgoing interface (OIF)
Any interface that is used to forward multicast traffic down the tree, also known as the downstream interface.
Outgoing interface list (OIL)
A group of OIFs that are forwarding multicast traffic to the same group. An example of this is R1’s Te0/0/0 and Te0/0/1 interfaces sending multicast traffic downstream to R3 and R4 for the same multicast group.
Last-hop router (LHR)
A router that is directly attached to the receivers, also known as a leaf router. It is responsible for sending PIM joins upstream toward the RP or to the source.
First-hop router (FHR)
A router that is directly attached to the source, also known as a root router. It is responsible for sending register messages to the RP.
Multicast Routing Information Base (MRIB)
A topology table that is also known as the multicast route table (mroute). It is built based on information from the unicast routing table and PIM. MRIB contains the
source S, group G,
incoming interfaces (IIF),
outgoing interfaces (OIFs),
and RPF neighbor information
for each multicast route as well as other multicast-related information.
Multicast Forwarding Information Base (MFIB)
A forwarding table that uses the MRIB to program multicast forwarding information in hardware for faster forwarding.
There are currently five PIM operating modes:
- PIM Dense Mode (PIM-DM)
- PIM Sparse Mode (PIM-SM)
- PIM Sparse Dense Mode
- PIM Source Specific Multicast (PIM-SSM)
- PIM Bidirectional Mode (Bidir-PIM)
PIM-DM and PIM-SM are also commonly referred to as any-source multicast (ASM)
All PIM control messages use the IP protocol number 103
they are either unicast (higher TTL)
or multicast, with a TTL of 1 to the all PIM routers address 224.0.0.13
PIM Control Message Types
| Type | Message Type | Destination | PIM Protocol |
|---|---|---|---|
| 0 | Hello | 224.0.0.13 (all PIM routers) | PIM-SM, PIM-DM, Bidir-PIM, and SSM |
| 1 | Register | RP address (unicast) | PIM-SM |
| 2 | Register stop | First-hop router (unicast) | PIM SM |
| 3 | Join/prune | 224.0.0.13 (all PIM routers) | PIM-SM, Bidir-PIM, and SSM |
| 4 | Bootstrap | 224.0.0.13 (all PIM routers) | PIM-SM and Bidir-PIM |
| 5 | Assert | 224.0.0.13 (all PIM routers) | PIM-SM, PIM-DM, and Bidir-PIM |
| 8 | Candidate RP advertisement | Bootstrap router (BSR) address (unicast to BSR) | PIM-SM and Bidir-PIM |
| 9 | State refresh | 224.0.0.13 (all PIM routers) | PIM-DM |
| 10 | DF election | 224.0.0.13 (all PIM routers) | Bidir-PIM |
PIM hello messages are sent by default every 30 seconds out each PIM-enabled interface to learn about the neighboring PIM routers on each interface to the all PIM routers address
Hello messages are also the mechanism used to elect a designated router (DR)
PIM Dense Mode
PIM Dense Mode (PIM-DM), Dense means that there are Multicast receivers in every subnet of the network, in other words, when the multicast receivers of a multicast group are densely populated across the network.
For PIM-DM, the multicast tree is built by flooding traffic out every interface from the source to every Dense Mode router in the network
As each router receives traffic for the multicast group, it must decide whether it already has active receivers wanting to receive the multicast traffic. If so, the router remains quiet and lets the multicast flow continue. If no receivers have requested the multicast stream for the multicast group on the LHR, the router sends a prune message toward the source.
That branch of the tree is then pruned off so that the unnecessary traffic does not continue.
Initial Flooding
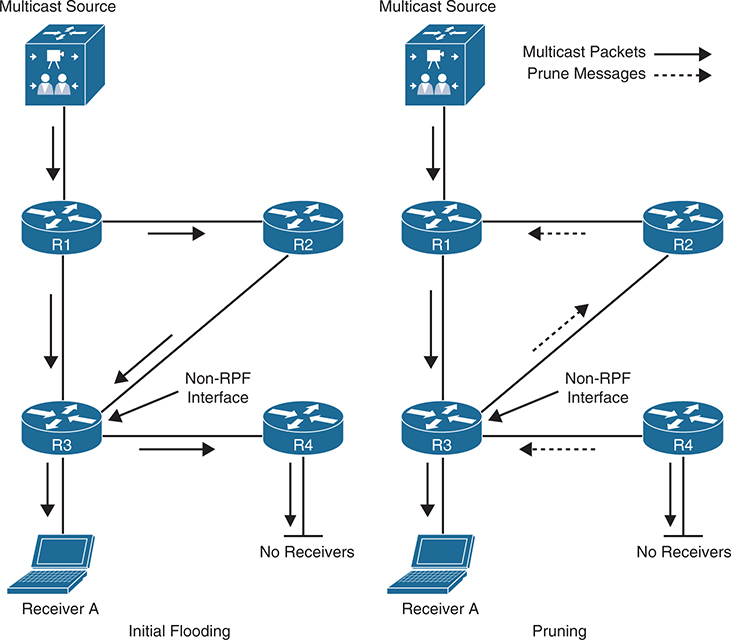
As each router receives the multicast traffic from its upstream neighbor via its RPF interface, it forwards the multicast traffic to all its PIM-DM neighbors, This results in some traffic arriving via a non-RPF interface, as in the case of R3 receiving traffic from R2 on its non-RPF interface. Packets arriving via the non-RPF interface are discarded because it is duplicate traffic and a prune message is prepared
Each router uses Reverse Path Forwarding (RPF) to decide which incoming interface is the correct one for multicast traffic from a particular source.
R3 checks its unicast routing table to see “Which interface would I use to reach the source?”
Route to the source (through R1) is the best path.
So, the interface from R1 is the RPF interface.
The interface from R2 is non-RPF.
That means:
R3 accepts multicast packets coming from R1 (RPF interface).
R3 drops multicast packets received from R2 (non-RPF interface).
These non-RPF multicast flows are normal for the initial flooding of multicast traffic and are corrected by the normal PIM-DM pruning mechanism.
Pruning after Initial Flooding
Prunes are sent out the RPF interface when the router has no downstream members that need the multicast traffic, as is the case for R4, which has no interested receivers, and they are also sent out non-RPF interfaces to stop the flow of multicast traffic that is arriving through the non-RPF interface, as is the case for R3
the resulting topology after all unnecessary links have been pruned off. This results in an SPT from the source to the receiver.
This (S,G) state remains until the source stops transmitting. S,G in this topology stands for, source is allowed / will come in to router from top and allowed / will go out from below interface
In PIM-DM, prunes expire after three minutes.
This causes the multicast traffic to be reflooded to all routers just as was done during the initial flooding. This periodic (every three minutes) flood and prune behavior is normal and must be taken into account when a network is designed to use PIM-DM.
PIM-DM is applicable to small networks where there are active receivers on every subnet of the network. Because this is rarely the case, PIM-DM is not widely deployed and not recommended for production environments.
PIM Sparse Mode
PIM Sparse Mode (PIM-SM) was designed for networks with multicast application receivers scattered throughout the network—in other words, when the multicast receivers of a multicast group are sparsely populated across the network. However, PIM-SM also works well in densely populated networks. It also assumes that no receivers are interested in multicast traffic unless they explicitly request, it opposite of PIM DM
Just like PIM-DM, PIM-SM uses the unicast routing table to perform RPF checks, and it does not care which routing protocol (including static routes) populates the unicast routing table; therefore, it is protocol independent.
PIM Shared and Source Path Trees
PIM-SM uses an explicit join model where the receivers send an IGMP join to their locally connected router, which is also known as the last-hop router (LHR), and this join causes the LHR to send a PIM join in the direction of the root of the tree, which is either the RP in the case of a shared tree (RPT) or in case of SPT, the first-hop router (FHR) where the source transmitting the multicast streams is connected
A multicast forwarding state is created as the result of these explicit joins
Multicast source sends multicast traffic to the FHR. The FHR then sends this multicast traffic to the RP, which makes the multicast source known to the RP
Receiver sends an IGMP join to the LHR to join the multicast group. The LHR then sends a PIM join (*,G) to the RP, and this forms a shared tree from the RP to the LHR, this (*,G) PIM join would travel hop-by-hop to the RP, building (*,G) on all routers it is passing through.
In essence, two trees are created: an SPT from the FHR to the RP (S,G) and a shared tree from the RP to the LHR (*,G).
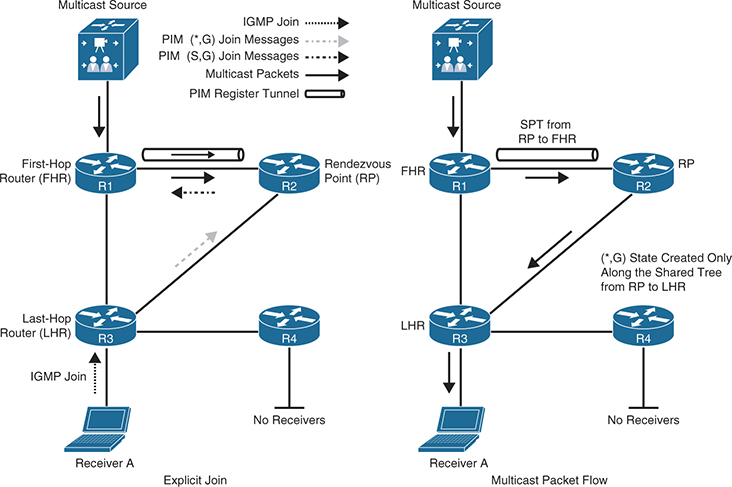
multicast starts flowing down from the source to the RP
and from the RP to the LHR and then finally to the receiver.
Receiver A attached to the LHR joins multicast group G using IGMP join. The LHR knows the IP address of the “RP for group G” – “there can be different RP per group” and LHR then sends (*,G) PIM join for this group to the RP.
Source for a group G sends a packet, the FHR that is attached to this source creates a “unidirectional ” PIM register tunnel interface that encapsulates the multicast data received from the source in a special PIM-SM message called the register message. The encapsulated multicast data is then unicast to the RP using the PIM register tunnel. This Multicast packet needs to be encapsulated in a unicast packet to RP, so it is not multicasted through the network below FHR
When the RP receives a register message, it decapsulates the multicast data packet inside the register message, and if there is no active shared tree because there are no interested receivers, the RP unicasts a register stop message directly to the registering FHR, without traversing the PIM register tunnel, instructing it to stop sending the register messages.
If there is an active shared tree for the group, it forwards the multicast packet down the shared tree, and it sends an (S,G) join back toward the source network S to create an (S,G) SPT. If there are multiple hops (routers) between the RP and the source, this results in an (S,G) state being created in all the routers along the SPT, There will also be a (*,G) in R1 and all of the routers between the FHR and the RP. So how can (*,G) and (S,G) co exist on same router?
(*,G): The “shared tree” state — means “any source for group G.”
It’s built towards the Rendezvous Point (RP).
Used before the specific source is known or joined.
(S,G): The “source tree” state — means “specific source S for group G.”
It’s built directly toward the multicast source (shortest path tree).
1. Initial IGMP Join
Receiver A (host) on R3 sends an IGMP Join for group G.
R3 (the Last-Hop Router, LHR) sends a PIM Join (*,G) upstream — towards the RP (R2).
So:
- R3 and R2 now have (*,G) state entries.
- This builds the shared tree (R3 → R2 → R1).
2. Source Starts Sending
When the multicast source (at R1) begins transmitting for group G:
- R1 (the First-Hop Router, FHR) registers with the RP using a PIM Register message.
- The RP learns that source S exists for group G.
3. Receiver Activity Triggers (S,G) Join
When the RP receives traffic from S, it knows there are active receivers (due to the earlier (*,G) join from R3).
So, the RP sends a PIM (S,G) Join back toward the source network — i.e., towards R1.
This creates:
- An (S,G) entry in R2 and R1 (routers along that source tree path).
- But — crucially — the (*,G) state still remains in R1 (and the path between R1 ↔ R2).
So Why Does (*,G) Exist in R1?
Even though R1 is the first-hop router (directly connected to the source), it forms a (*,G) state because:
- It’s part of the shared tree path from the RP to the source (built earlier when RP didn’t yet know the source existed).
The shared tree extends from RP → R1, so all routers on that path (including R1) must maintain(*,G)state. So this (*,G) is created on all routers around RP in 360 degrees. - Transitions are gradual, not instantaneous — both trees (shared and source) coexist temporarily while the network optimizes to the SPT.
As soon as the SPT is built from the source router to the RP, multicast traffic begins to flow natively from the source S to the RP instead of being encapsulated inside unicast PIM Regsiter tunnel
Once the RP begins receiving data natively from source S
it sends a register stop message to the source’s FHR to inform it that it can stop sending the unicast register messages. At this point, multicast traffic from the source is flowing down the SPT to the RP and, from there, down the shared tree (RPT) to the receiver – register stop message’s only function is to make FHR stop sending Register message for speicific group and not to stop multicast operation
The PIM register tunnel from the FHR to the RP remains in an active up/up state even when there are no active multicast streams, and it remains active as long as there is a valid RPF path for the RP.
PIM SPT Switchover
PIM-SM allows the LHR to switch from the RPT (shared tree) to an SPT for a specific source
In Cisco routers, this is the default behavior, and it happens immediately after the first multicast packet is received from the RP via the RPT on LHR, even if shortest parth to the source is through RP.
When the LHR receives the first multicast packet from the RP, it becomes aware of the IP address of the multicast source, at this point LHR sends (S,G) PIM Join towards the source IP following routing table (and not RP IP) and that can result in PIM Join going out of a different interface (shorter route) than interface through which RP is reachable
This PIM Join going from LHR to FHR creates (S,G) on all routers in the path
When the LHR receives a multicast packet from the source through the SPT, if the SPT RPF interface differs from the RPT RPF interface, the LHR will start receiving duplicate multicast traffic from the source; at this moment, it will switch the RPF interface to be the SPT RPF interface and send an (S,G) PIM prune message to the RP to shut off the duplicate multicast traffic coming through the RPT.
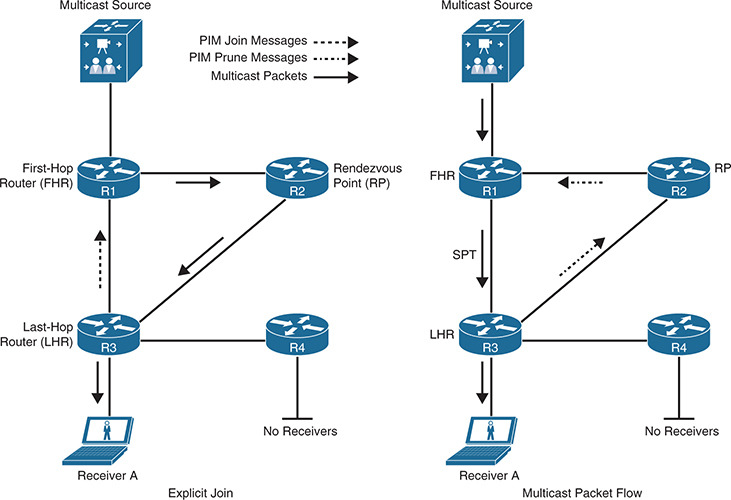
the shortest path to the source is between R1 and R3; if that link were shut down or not present, the shortest path would be through the RP, in which case an SPT switchover would still take place, even though the path used by the SPT is the same as the RPT.
The PIM SPT switchover mechanism can be disabled for all groups or for specific groups.
If the RP has no other interfaces that are interested in the multicast traffic, it sends a PIM prune message in the direction of the FHR. If there are any routers between the RP and the FHR, this prune message would travel hop-by-hop until it reaches the FHR.
Designated Routers
When multiple PIM-SM routers exist on a LAN segment, PIM hello messages are used to elect a designated router (DR) to avoid sending duplicate multicast traffic into the LAN (LHR) or to the RP (FHR). “Designated” router on LAN to receive traffic or send traffic, so second router does not duplicate multicast on network.
By default, the DR priority value of all PIM routers is 1, and it can be changed to force a particular router to become the DR during the DR election process, where a higher DR priority is preferred. If a router in the subnet does not support the DR priority option or if all routers have the same DR priority, the highest IP address in the subnet is used as a tiebreaker.
On an FHR, the designated router is responsible for encapsulating in unicast register messages any multicast packets originated by a source that are destined to the RP.
On an LHR, the designated router is responsible for sending PIM join and prune messages toward the RP to inform it about host group membership, and it is also responsible for performing a PIM SPT switchover.
Without DRs, all LHRs on the same LAN segment would be capable of sending PIM joins upstream, which could result in duplicate multicast traffic arriving on the LAN. On the source side, if multiple FHRs exist on the LAN, they all send register messages to the RP at the same time.
The default DR hold time is 3.5 times the PIM hello interval (PIM Hello is 30 seconds) which makes DR hold time to 105 seconds. If there are no hellos after this interval, a new DR is elected. To reduce DR failover time, the hello query interval can be reduced to speed up failover with a trade-off of more control plane traffic and CPU resource utilization of the router.
Reverse Path Forwarding
Reverse Path Forwarding is a method routers use when multicast traffic arrives on interface and it checks source address against routing table and if this is the interface., if not then interface is non RPF interface.
This is used to prevent loops and also avoid duplicated multicast traffic
If a router receives a multicast packet on an interface it uses to send unicast packets to the source, the packet has arrived on the RPF interface.
Next If the packet arrives on the RPF interface, a router forwards the packet out the interfaces present in the outgoing interface list (OIL) of a multicast routing table entry.
If the packet does not arrive on the RPF interface, the packet is discarded to prevent loops.
RPF check is performed differently for RPT and SPT
If a PIM router has an (S,G) entry present in the multicast routing table (an SPT state), the router performs the RPF check against the IP address of the source for the multicast packet.
If a PIM router has no explicit source-tree state, this is considered a shared-tree state. The router performs the RPF check on the address of the RP, which is known when members join the group.
PIM Assert , forwarder role
PIM assert mechanism is used to stop duplicate flows into LAN, well was it not the function of DR? yes DR does its best from control plane perspective to prevent duplicate flows, after DR elections only one router sends out PIM Join to receive traffic only on that specific DR router but in some cases (discussed below) you can still end up having duplicate multicast coming from 2 routers on same LAN and if that happens then this condition is detected and remediated using PIM Assert mechanism
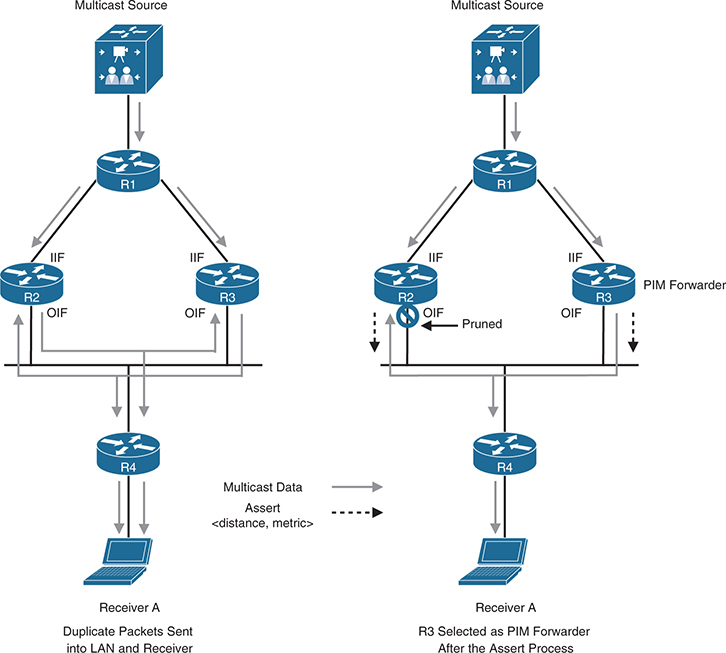
in above figure, Both R2 and R3 receive traffic on their (one and only) RPF interface, as these routers dispatch multicast traffic on LAN, R2’s sent multicast hits R3’s OIF interface and R3’s sent multicast traffic hits R2’s OIF, this triggers the PIM Assert mechanism on both routers as this should not happen
In other words, they detect a multicast packet for a specific (S,G) coming into their OIF that is also OIF for the same (S,G) (this OIF cannot be also IIF for same group)
R2 and R3 both send PIM assert messages into the LAN. These assert messages “send” each other following inside PIM Assert message to determine which router should forward the multicast traffic to that network segment.
- Administrative distance / preference
- Metric to the source (unicast routing metric)
- IP address (tie-breaker)
Each router compares its own values with the received values. Preference is given to the PIM message with the lowest AD to the source. If a tie exists, the lowest route metric for the protocol wins; and as a final tiebreaker, the highest IP address is used.
The losing router prunes its interface just as if it had received a prune on this interface, and the winning router is the PIM forwarder for the LAN.
The prune times out after three minutes on the losing router and causes it to begin forwarding on the interface again. This triggers the assert process to repeat. If the winning router were to go offline, the loser would take over the job of forwarding on to this LAN segment after its prune timed out.
The PIM forwarder concept applies to PIM-DM and PIM-SM. It is commonly used by PIM-DM but rarely required by PIM-SM because duplicate packets can end up in a LAN only if there is some sort of routing inconsistency.
PIM-SM would not send duplicate flows into the LAN as PIM-DM would because of the way PIM-SM operates.
Corner case for PIM-SM to send duplicated Multicast in LAN
PIM-SM will only forward duplicated multicast in LAN because of routing inconsistency only
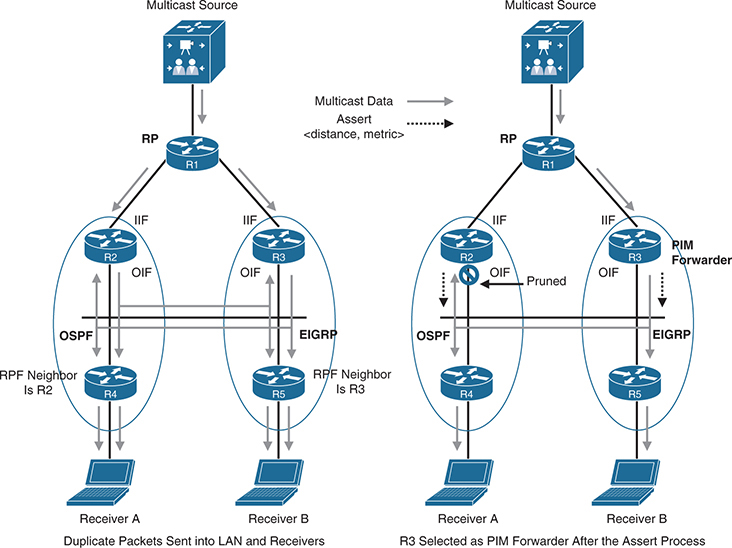
R1 is the RP
R2 and R4 are running the OSPF, and R3 and R5 are running EIGRP, and this is inconsistency in this network – to be more specific 2 different routing domains on same LAN.
R4 learns about the RP (R1) through R2, and R5 learns about the RP through R3
when R4 sends a PIM join message upstream toward it, it sends the message to the all PIM routers address 224.0.0.13, and R2 and R3 receive it but in PIM-SM PIM join message includes the IP address of the upstream neighbor, also known as the RPF neighbor (which is only one neighbor – PIM neighbor on RPF interface)
R4’s RPF neighbor is R2, and R5’s RPF neighbor is R3
Receiver A and Receiver B join the same group
Receiver A’s IGMP join will cause PIM Join from R4 to both R2 and R3 (because of same LAN) R2 is the only one that will send a PIM join to R1 because PIM join from R4 has header that contains R2 as its RPF neighbor, R3 will not because the PIM join was not meant for it, from R4 it was only meant for R2 (its RPF neighbor) and R2 will send PIM Join message to RP
Similarly IGMP join from receiver B will trigger R5 to send a PIM join to to both R2 and R3, but because PIM SM’s PIM Join has RPF neighbor R3 is specified in packet, R3 is the one that will send a PIM join to R1.
At this point, traffic starts flowing downstream from R1 into R2 and R3, and duplicate packets are then sent out into the LAN and to the receivers.
At this point, the PIM assert mechanism kicks in, R3 is elected as the PIM forwarder, and R2’s OIF interface is pruned, as illustrated in the topology on the right side.
Rendezvous Point Propagation
next post
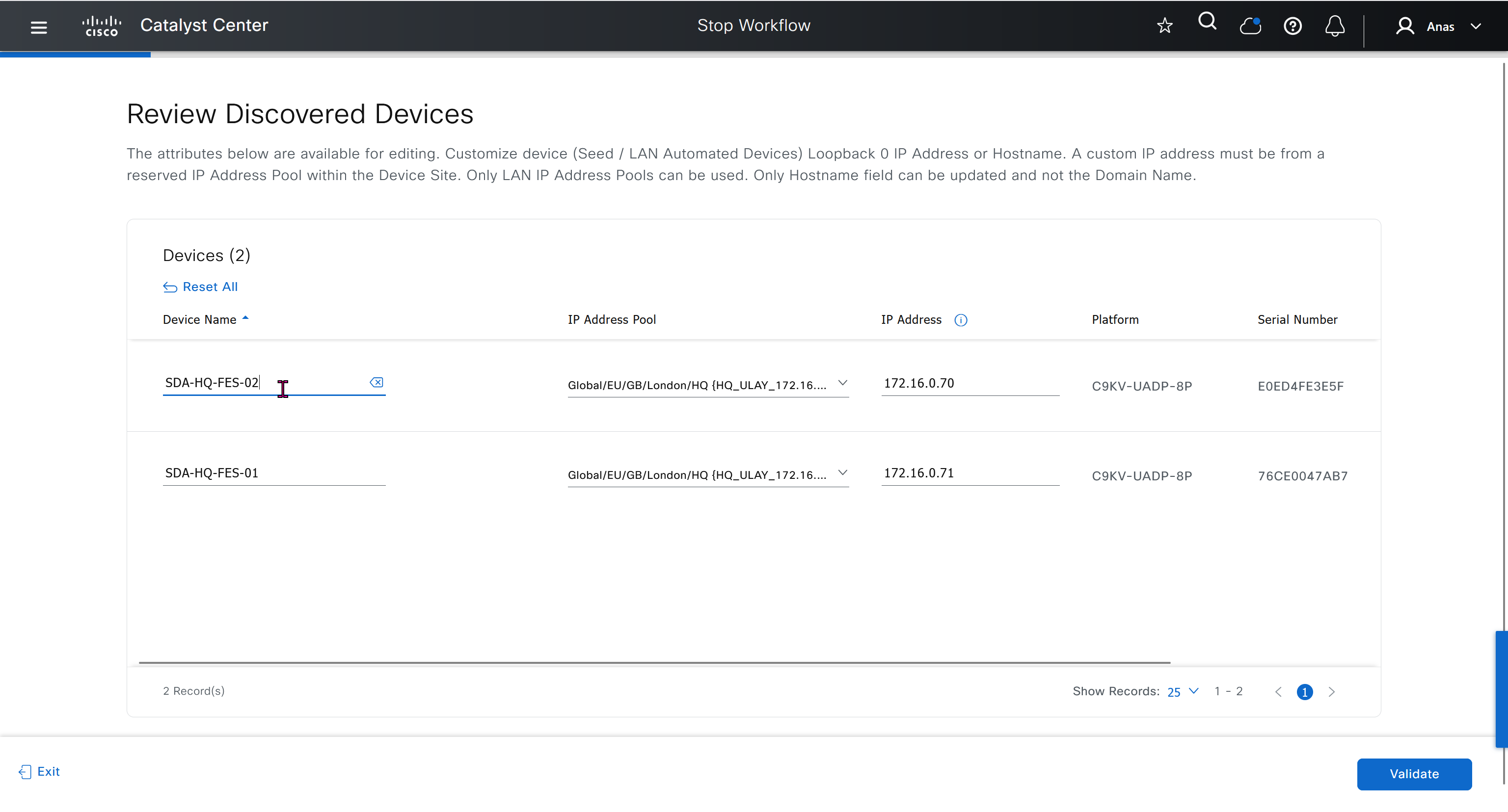
SDA LM5 – SDA Fabric Virtual Networks
Videos
SDA Fabric Virtual Networks
Fabric Site
Fabric Site contains its own components such as border node, control node, access switches and Wireless controllers – imagine a typical site or building or campus that has network components
A fabric site can span multiple building but only over a high speed, low latency network and not WAN connection
Transit Network
Transit Network either connects multiple Fabric Sites together or connects a Fabric site to an external network
and there are different types of transit networks which will be discussed
Fabric Domain
Fabric Domain is made up of one or more Fabric Sites
Geographic distance between buildings and location decides the fabric site’s boundary
Type of WAN decides the Transit Network type
Depending on the version of SDA and cisco documentation, fabric site can only be so big and scale, if fabric site is bigger than what is supported by SDA, then you will have to break up the single fabric site into 2 Fabric sites
So make sure to check scalability number in Cisco documentation
Make sure you have all devices that will be part of the fabric already discovered, reachable, managed and synced and LAN Automated, preferable compliant also

- Second most important thing is that, make sure that your edge devices do not have a route to DNAC via their default route and must have a specific route, I learned this the hard way
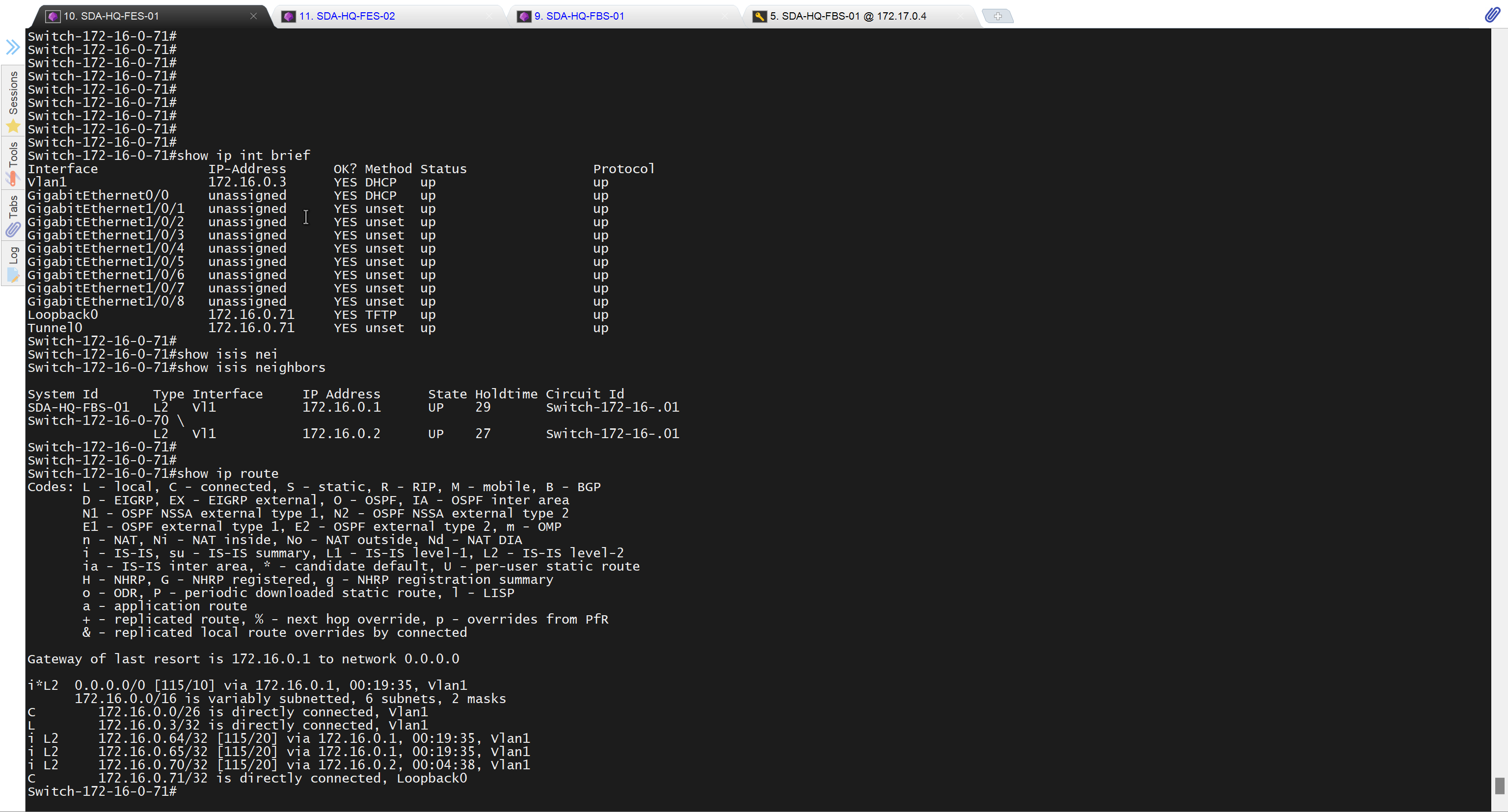
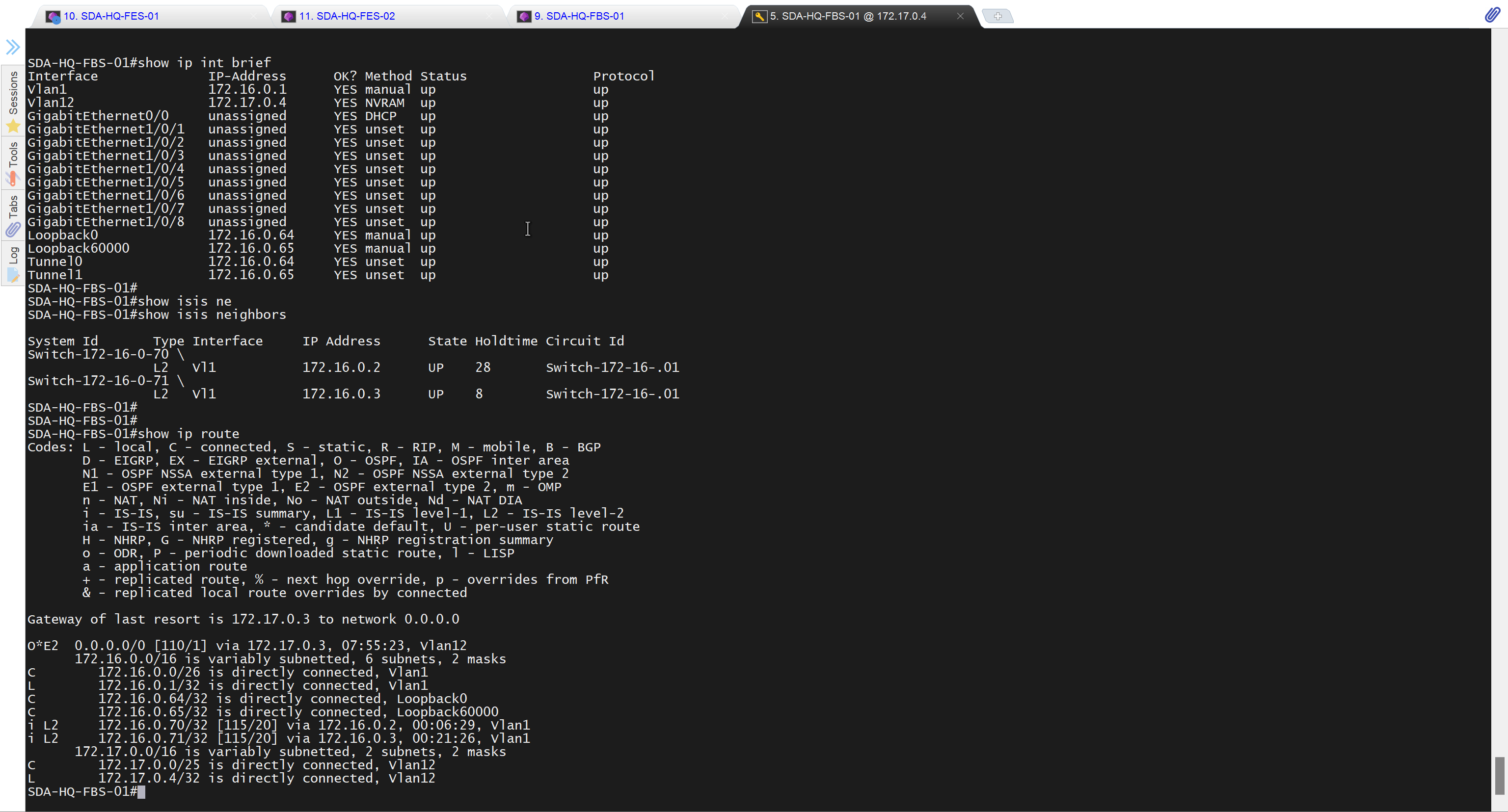
SDA-HQ-FES-01#show ip route 10.21.1.2
% Network not in tableSDA-HQ-FBS-01
conf t
ip route 10.21.1.0 255.255.255.0 172.17.0.3
!
router isis
redistribute static ipSDA-HQ-FES-01#show ip route 10.21.1.2
Routing entry for 10.21.1.0/24
Known via "isis", distance 115, metric 10, type level-2
Redistributing via isis
Last update from 172.16.0.72 on GigabitEthernet1/0/4, 00:00:05 ago
Routing Descriptor Blocks:
* 172.16.0.74, from 172.16.0.64, 00:00:05 ago, via GigabitEthernet1/0/3
Route metric is 10, traffic share count is 1
172.16.0.72, from 172.16.0.64, 00:00:05 ago, via GigabitEthernet1/0/4
Route metric is 10, traffic share count is 1SDA-HQ-FES-01#ping 10.21.1.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.21.1.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 114/131/164 msSDA-HQ-FES-01#ping 10.21.1.2 source loopback 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.21.1.2, timeout is 2 seconds:
Packet sent with a source address of 172.16.0.71
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 111/122/134 ms
DNAC comes with default LAN fabric
We can either choose to use this or create a new fabric
We should always create a new fabric and not use the default
next post
SDA LM4 – DNAC Web Interface
Videos
Introduction to UI
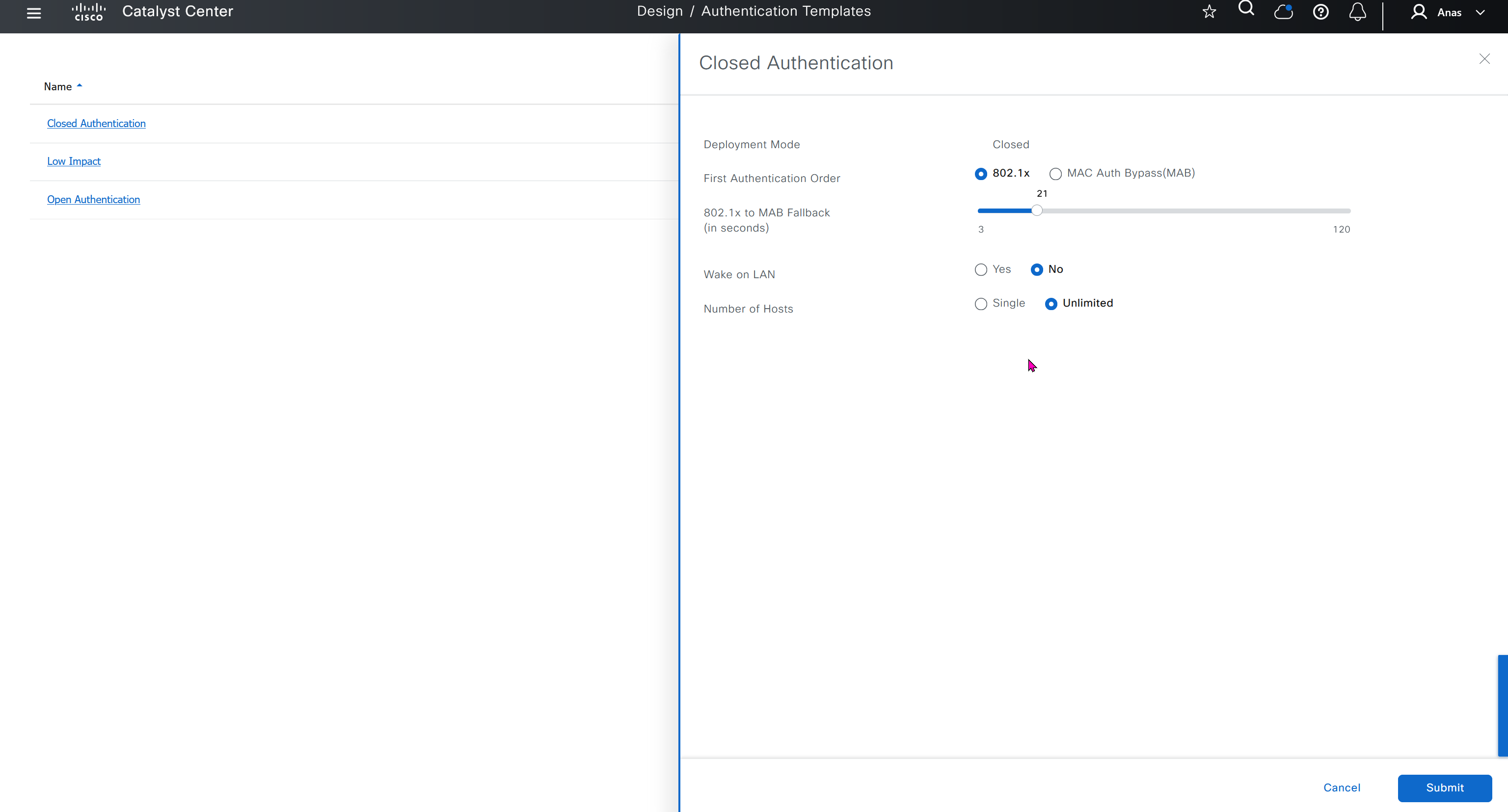
You can modify these authentication templates but cannot define more
If you want to define different SSID in europe or you want different ISE server for europe then use hierarchy and go to site specific level and override


IP based access control is used when you create non fabric based wireless and this is a very specific use, if we dont use non-fabric wireless then we will not have to touch this page
AI Endpoint Analytics
With new DNAC, AI Endpoint Analytics was introduced and this leverages AI capabilities in cloud and uses deep packet inspection in Catalyst 9K infrastructure to “identify types of endpoints” – this information can then be fed to ISE and can then be used as part of endpoint authentication, this provides additional network packet level context along side the profiling probes that ISE performs on its own and that information is communicated to ISE using PXGrid
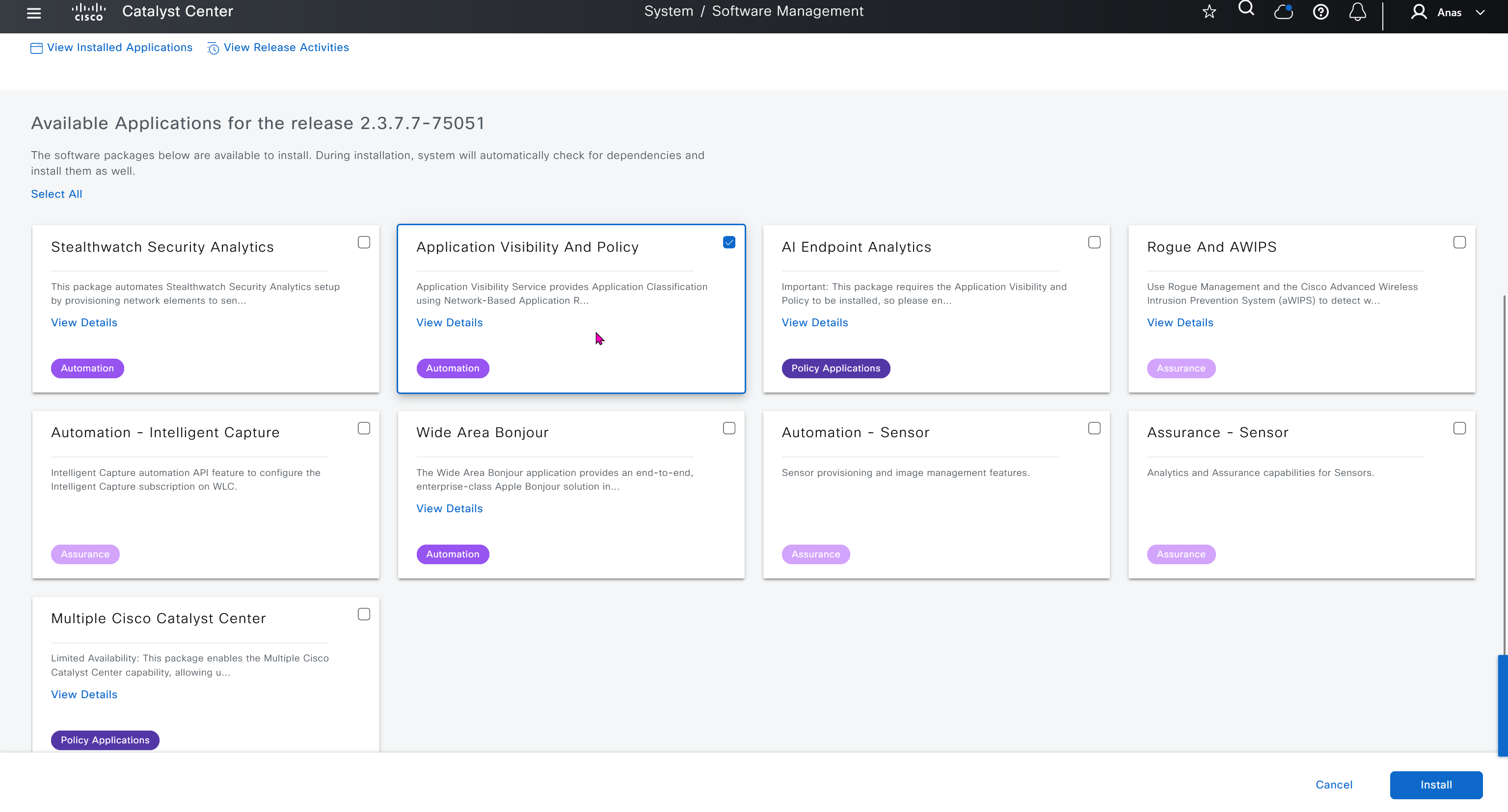
Application policies is the feature that was known as Easy QoS and it allows you to deploy QoS end to end in your network, for more details checkout RS0122 – SDA Application Policy (EasyQoS)
Traffic Copy is the way to span traffic from Fabric to a remote destination and this is part of SGT, as you can capture traffic between specific contracts or tags
Finally Virtual networks which are essentially VRFs and separate different (virtual) fabric on same network
Service catalog, these are different services that are offered
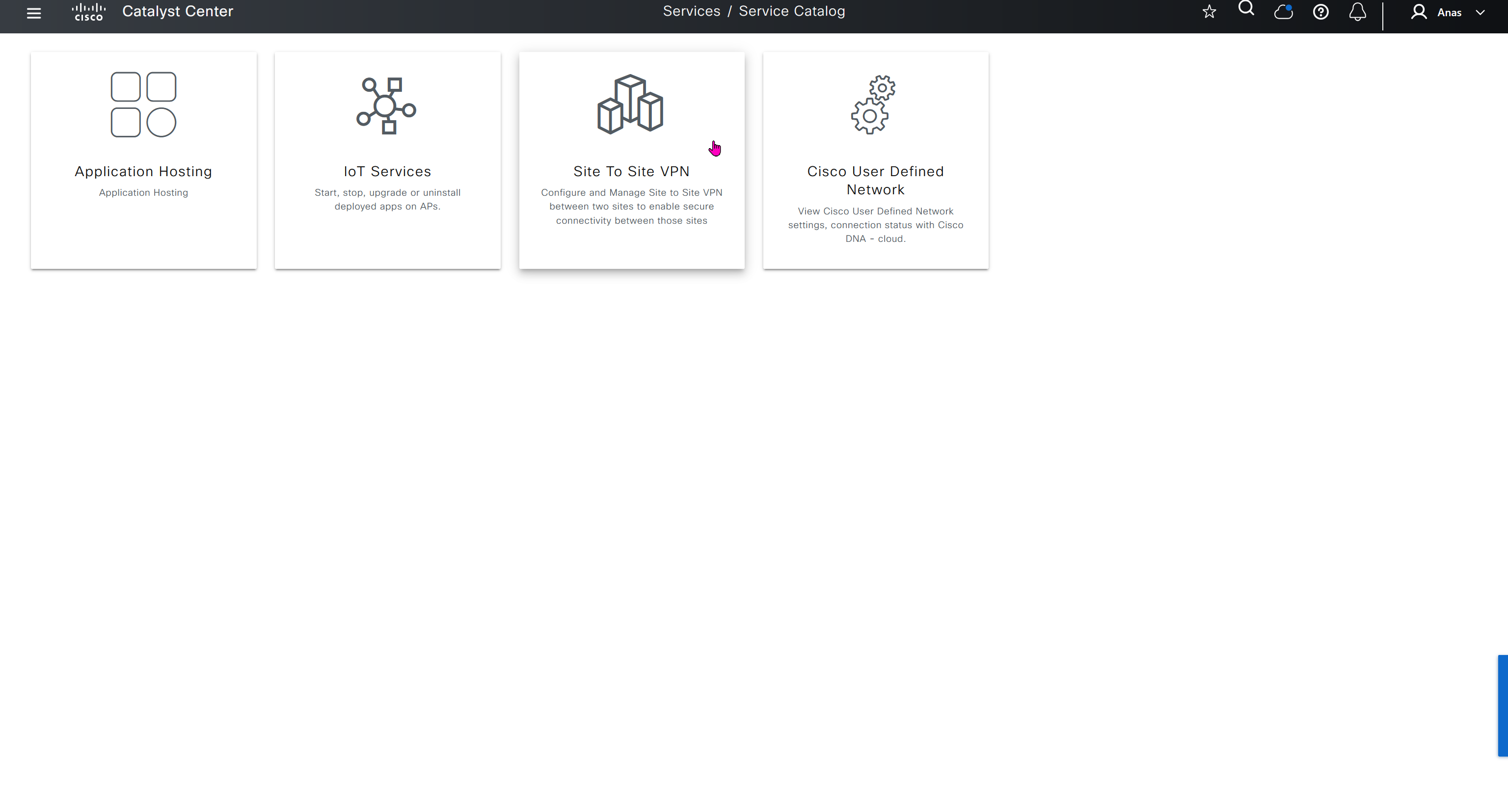
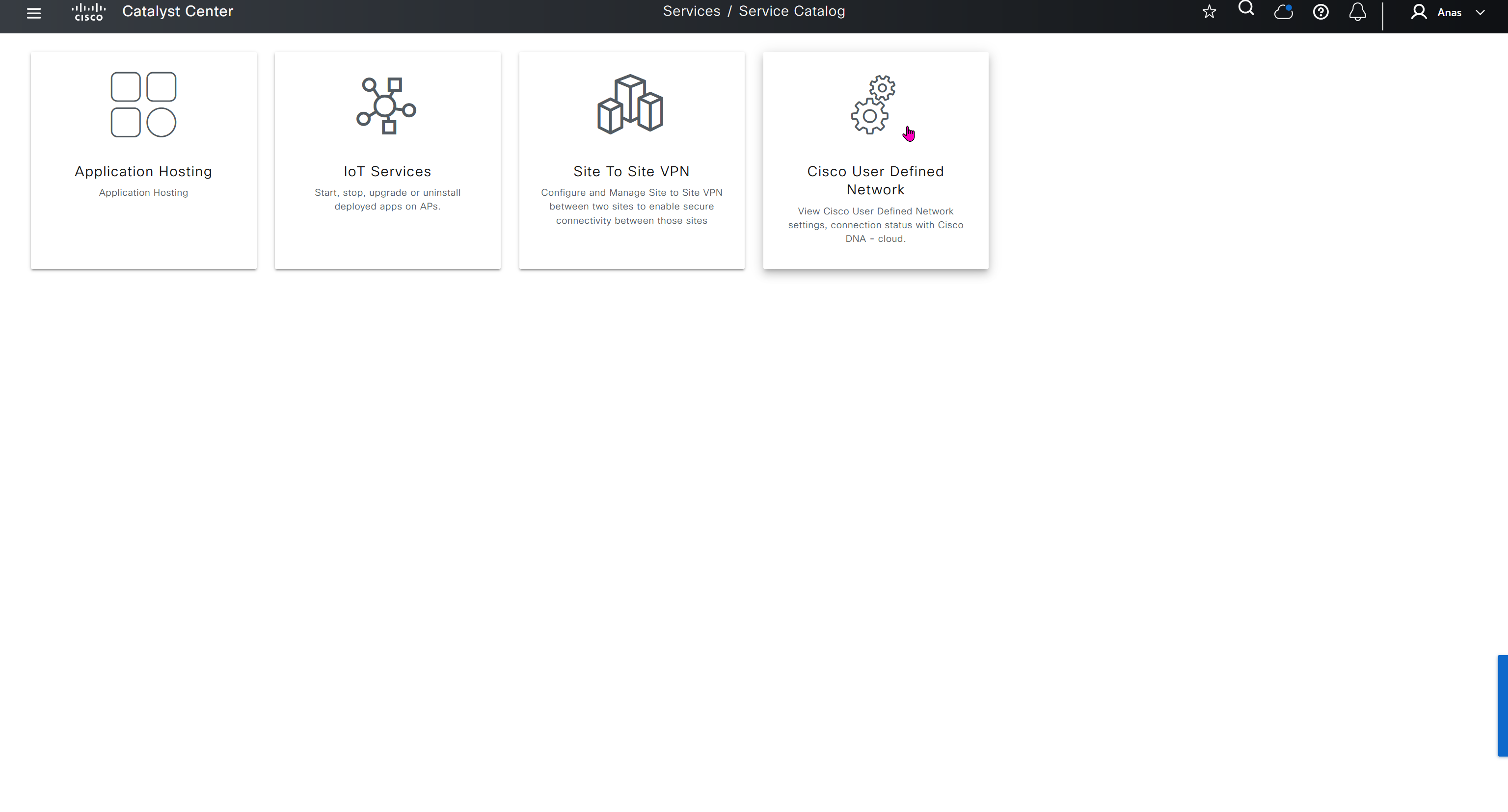
User defined network is a cool concept as it allows users to create personal network on top of shared infrastructure, users can then register their personal devices using an app and also invite other users into that network using same app and these networks are like bubbles
These 4 services are also listed under the services section of provision tab
Assurance does not just measures health and experience of network devices but also includes clients and helps us measure client’s experience on the network also and it does not stay at client but its scope one level more deep into application as well



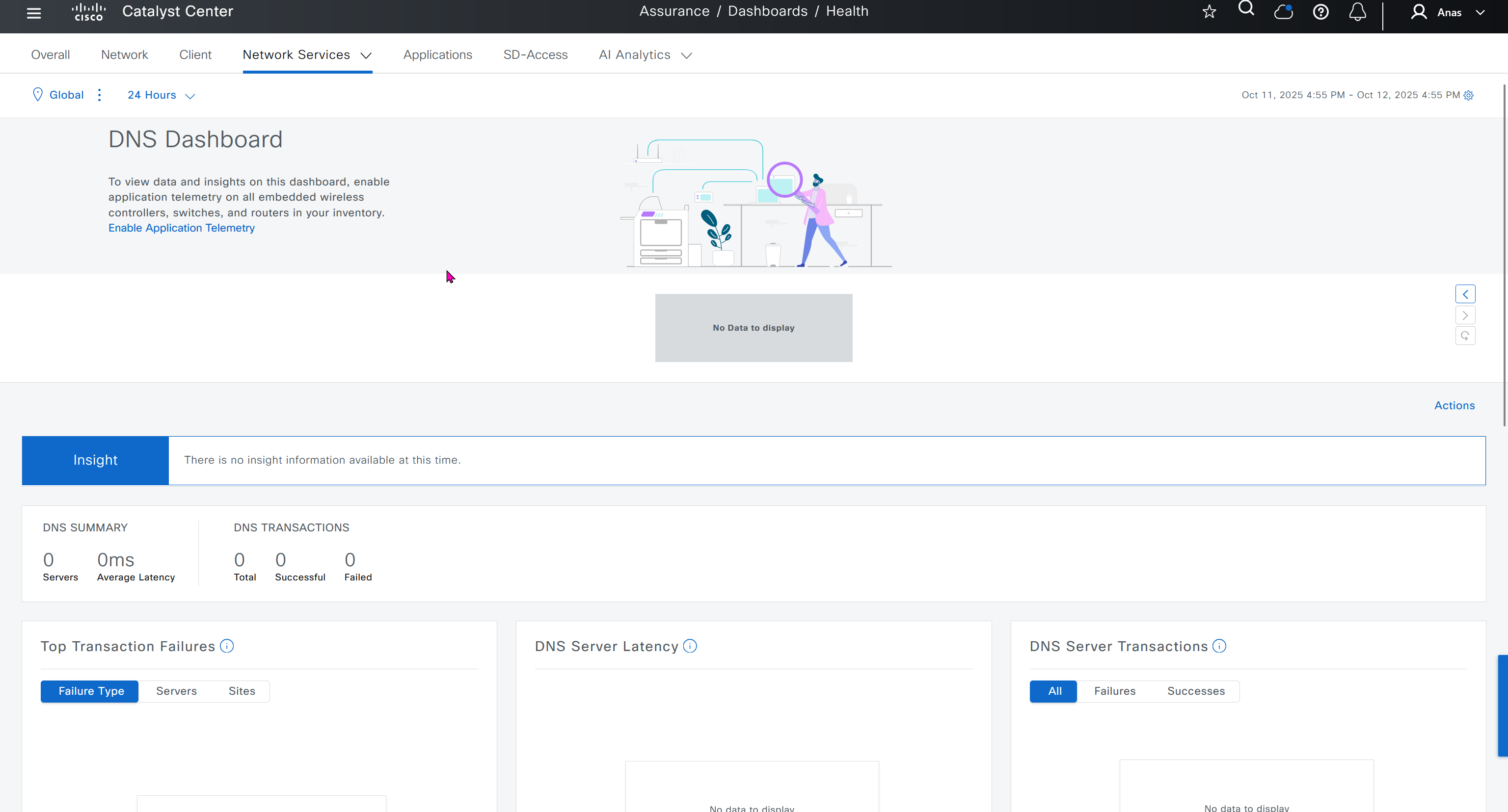
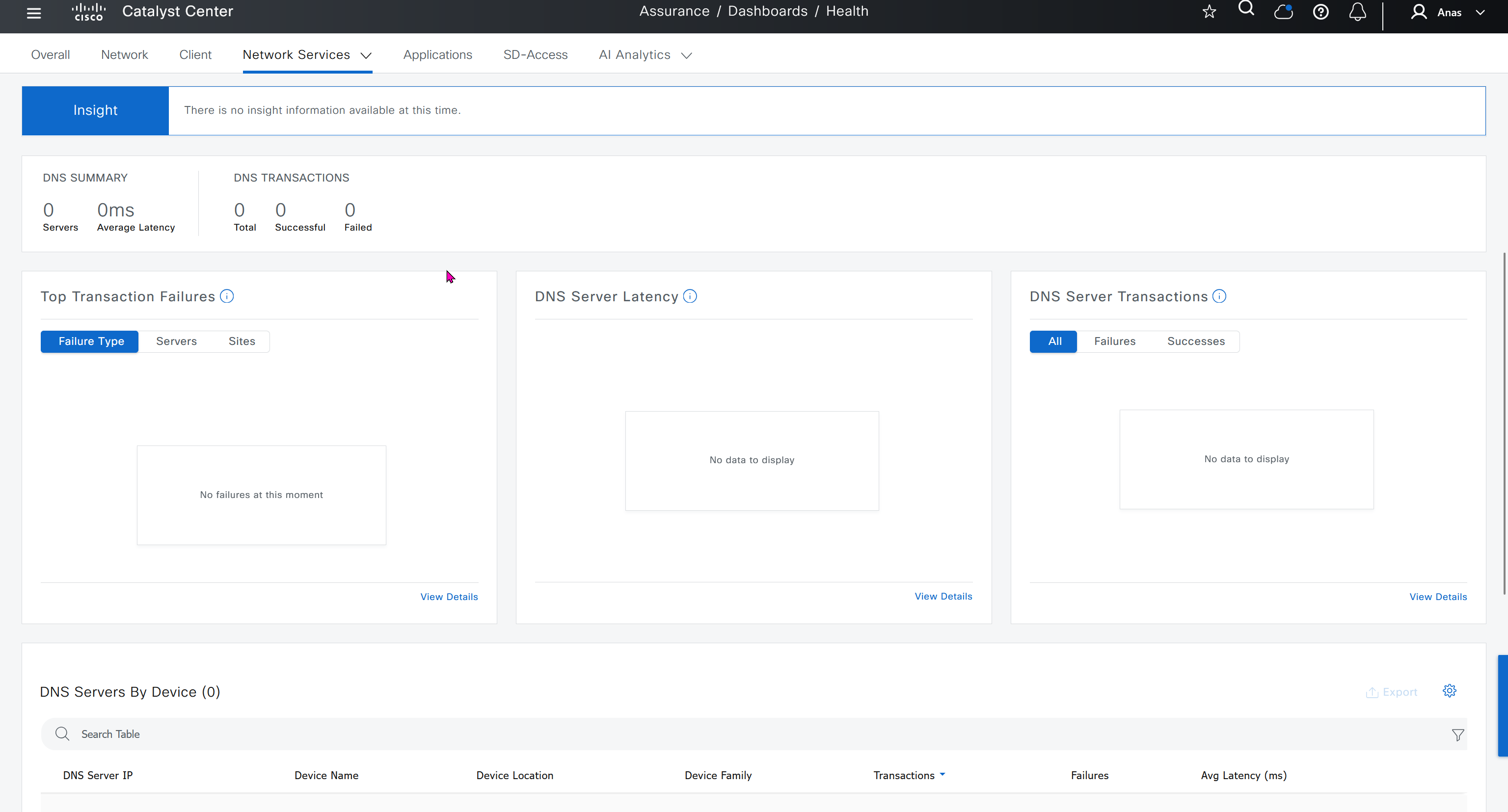


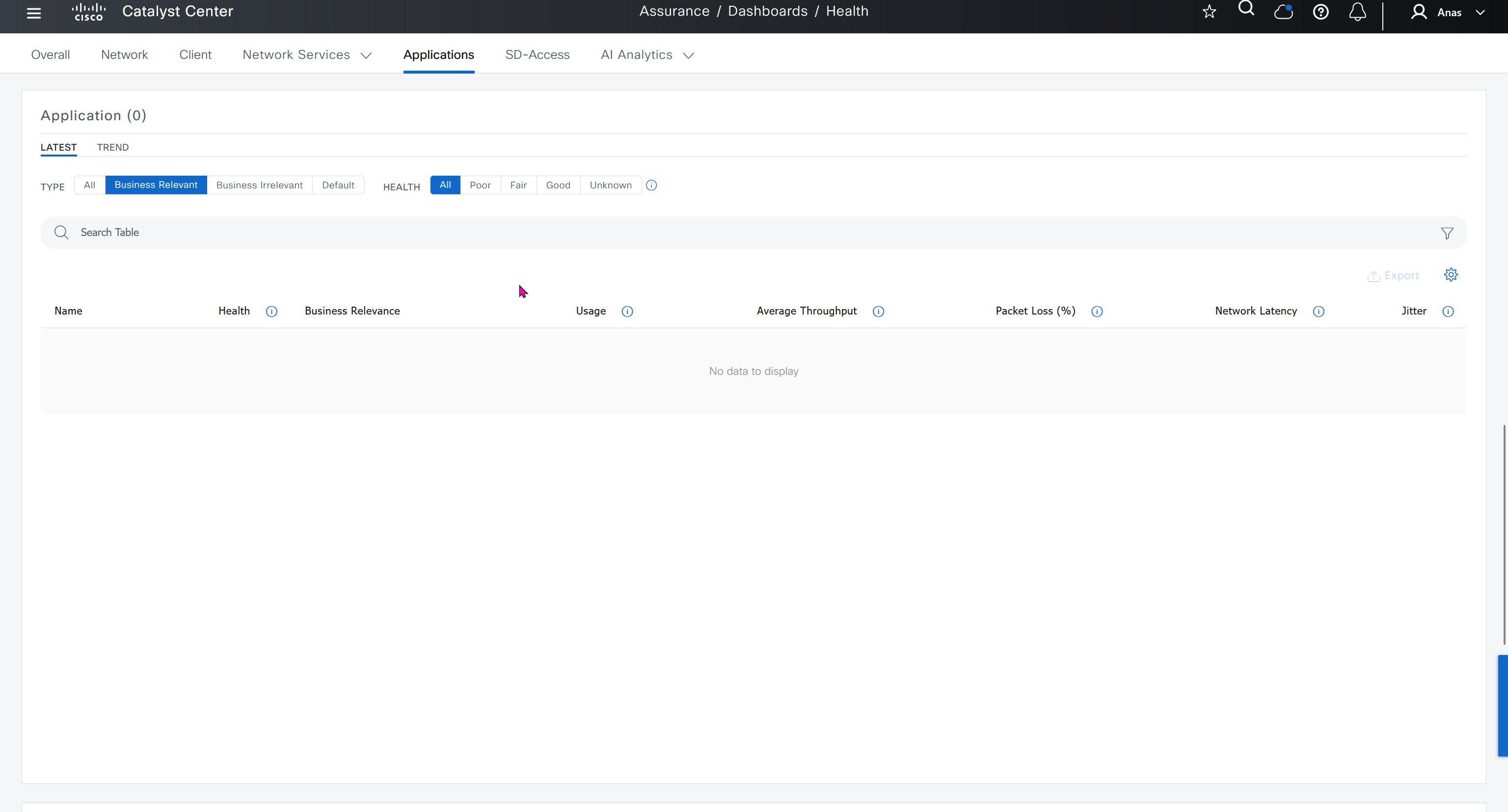

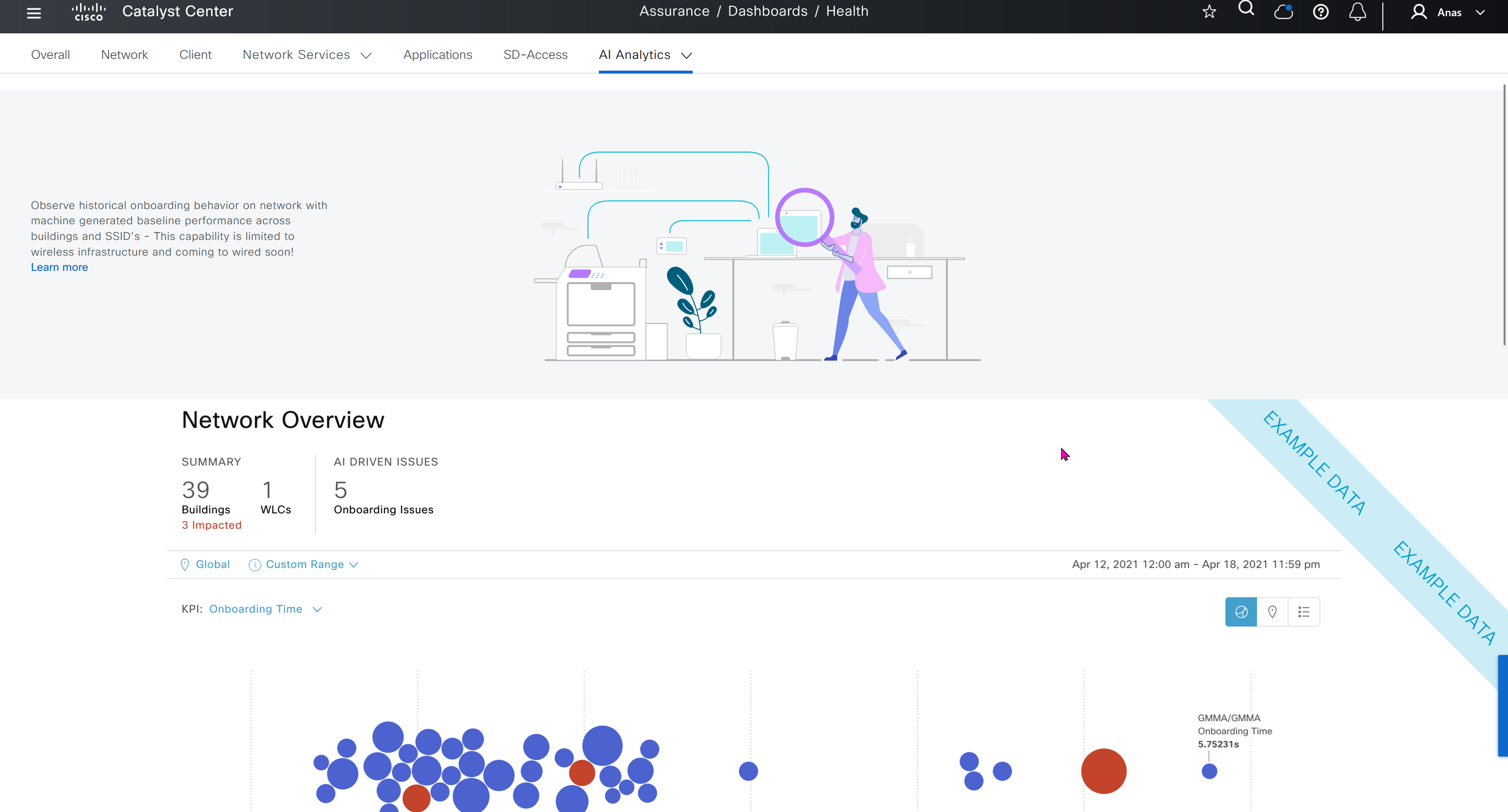
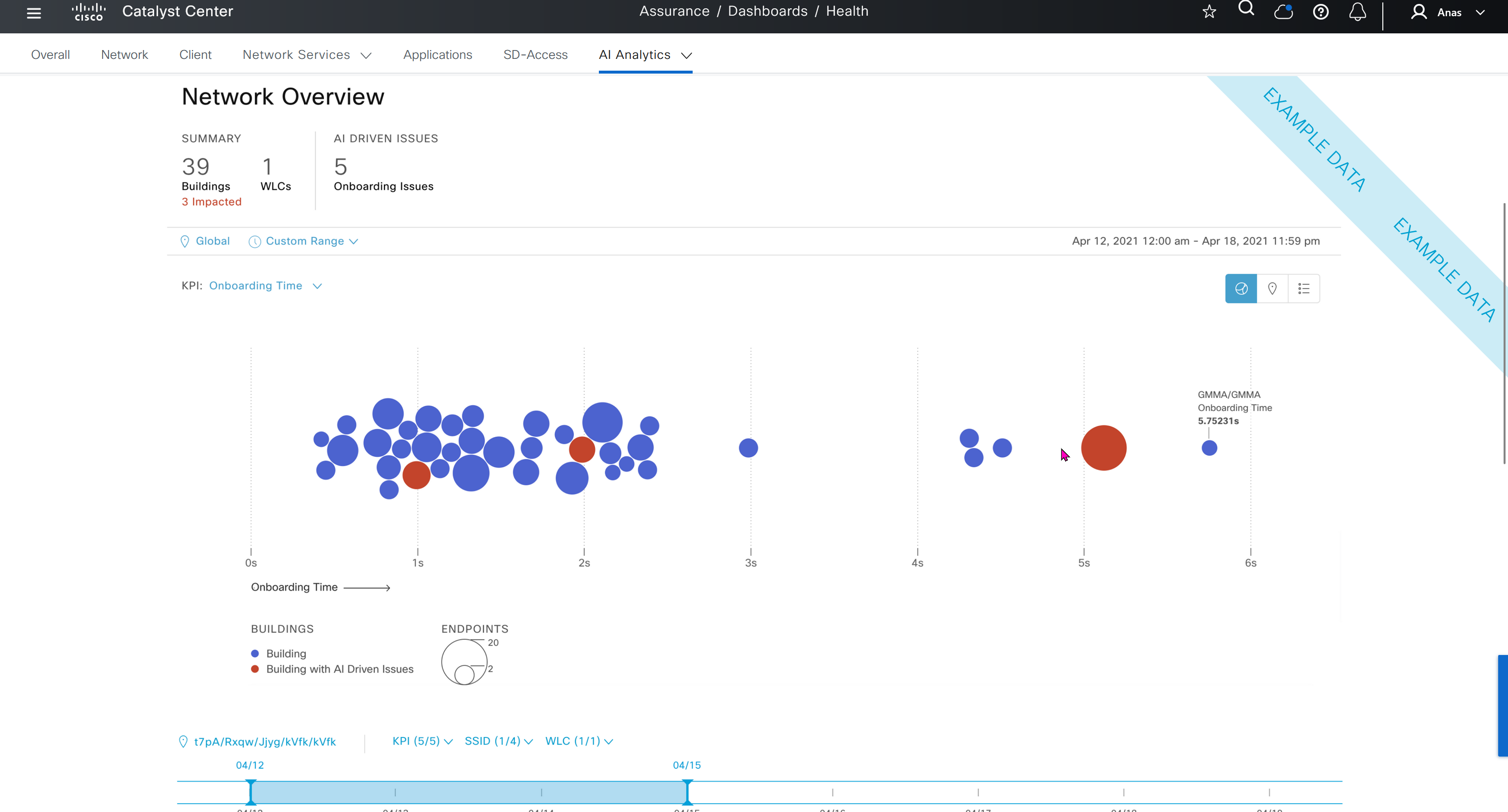
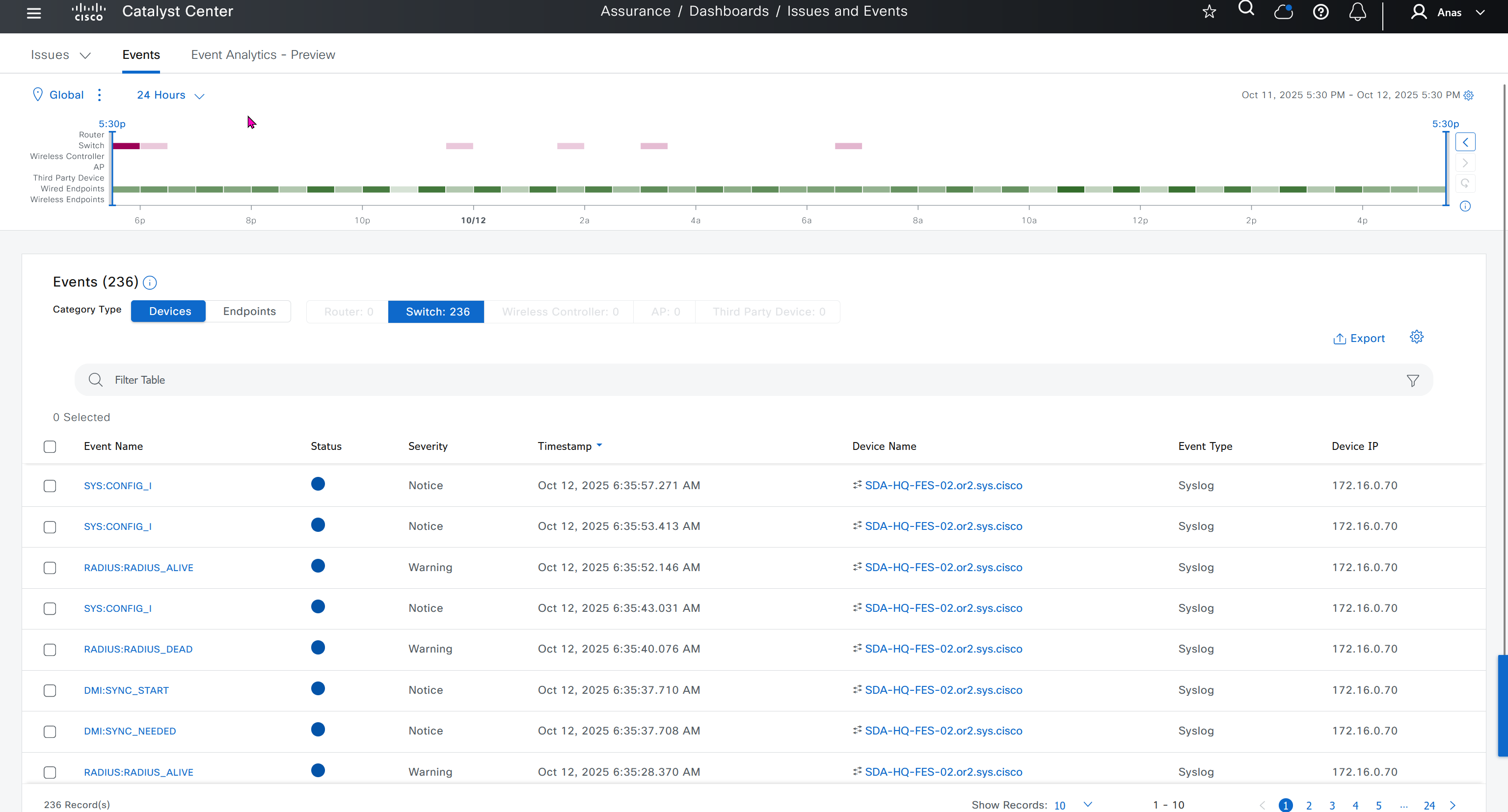
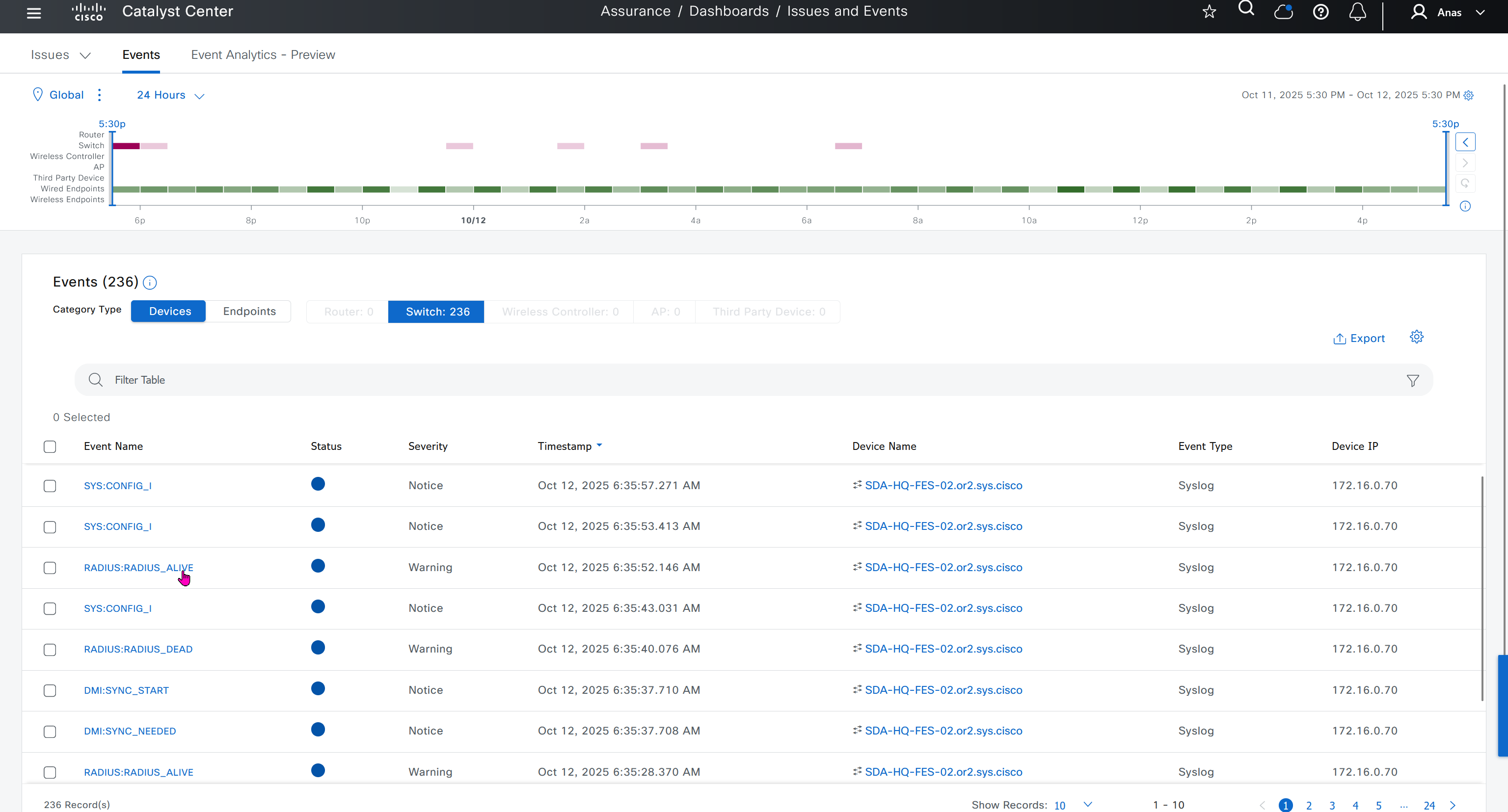
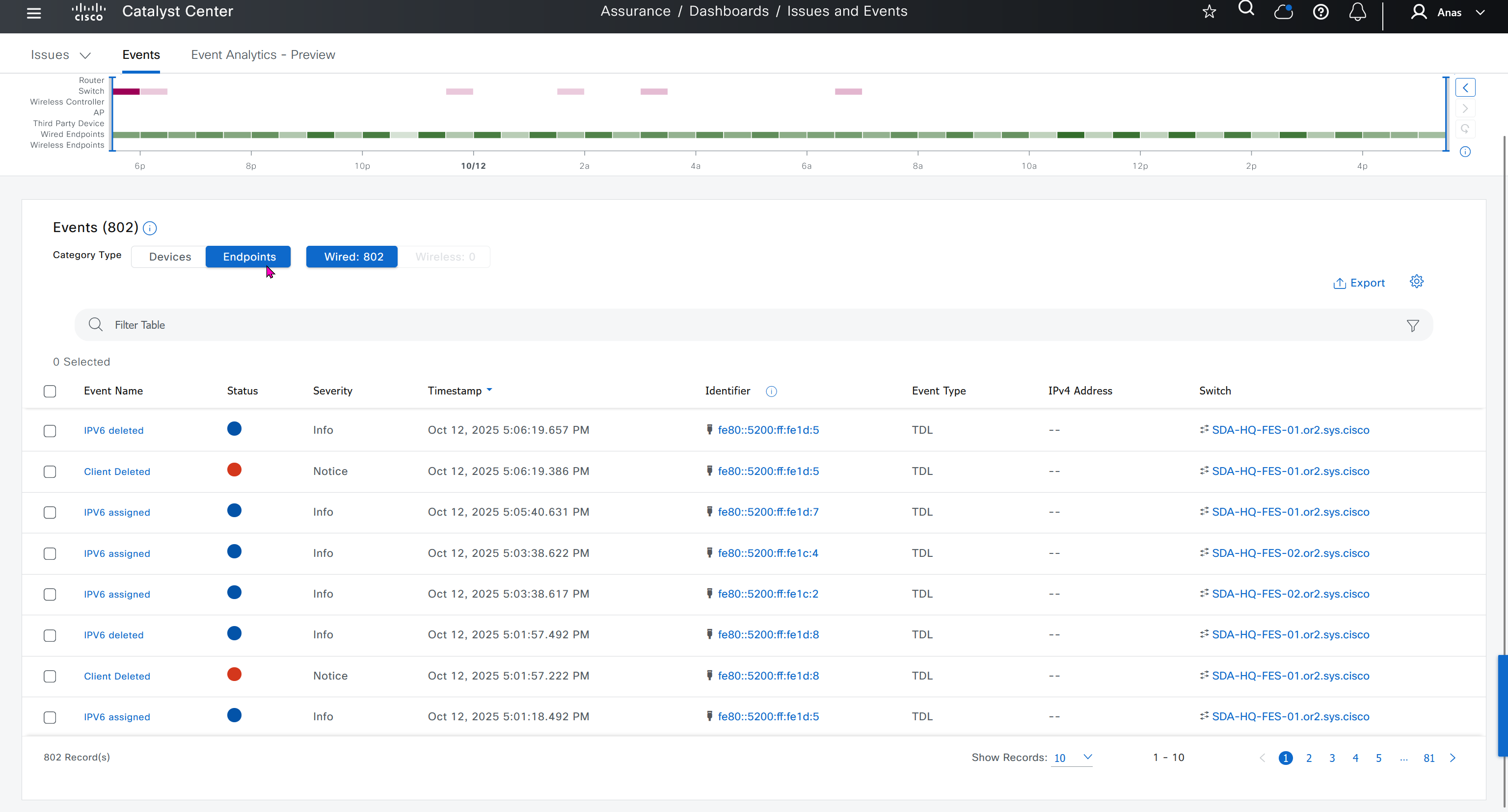
Events are for both Network devices and also for the clients, these are any events that happen in the network for network devices and its connected clients

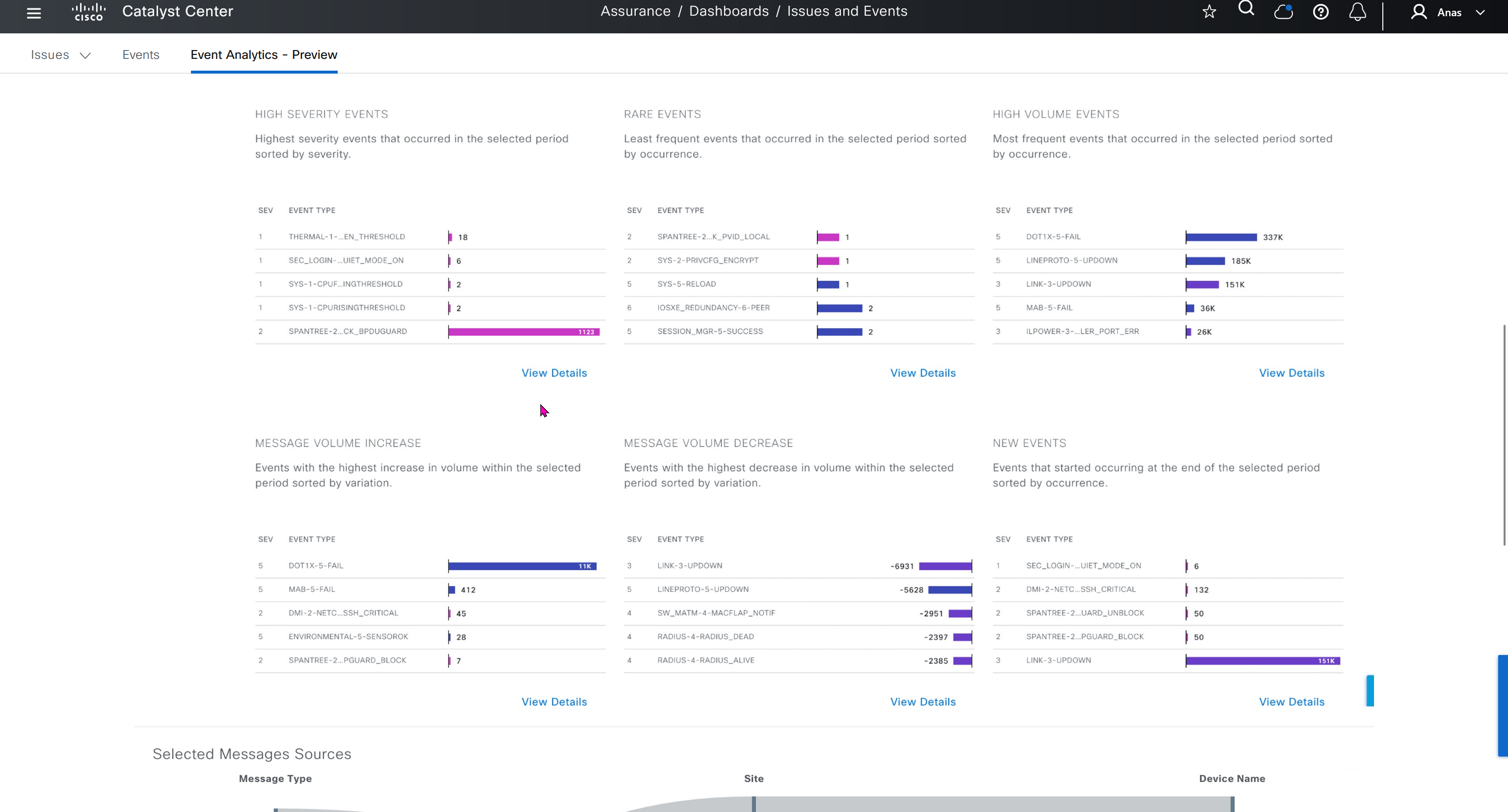
DNAC offers dedicated sensors that can perform series of tests to gauge performance from client perspective. These wireless sensors join network as wireless device and these can either be dedicated sensors or an AP can also be converted to a wireless sensor


Wi-Fi6 section is for Wi-Fi6 readiness assessment which shows us the percentage of AP and clients that are capable of Wi-Fi6, if large number of clients support Wi-Fi6 then we can think about more APs to be deployed that support Wi-Fi6


Dashboard Library is where we can create our own dashboards
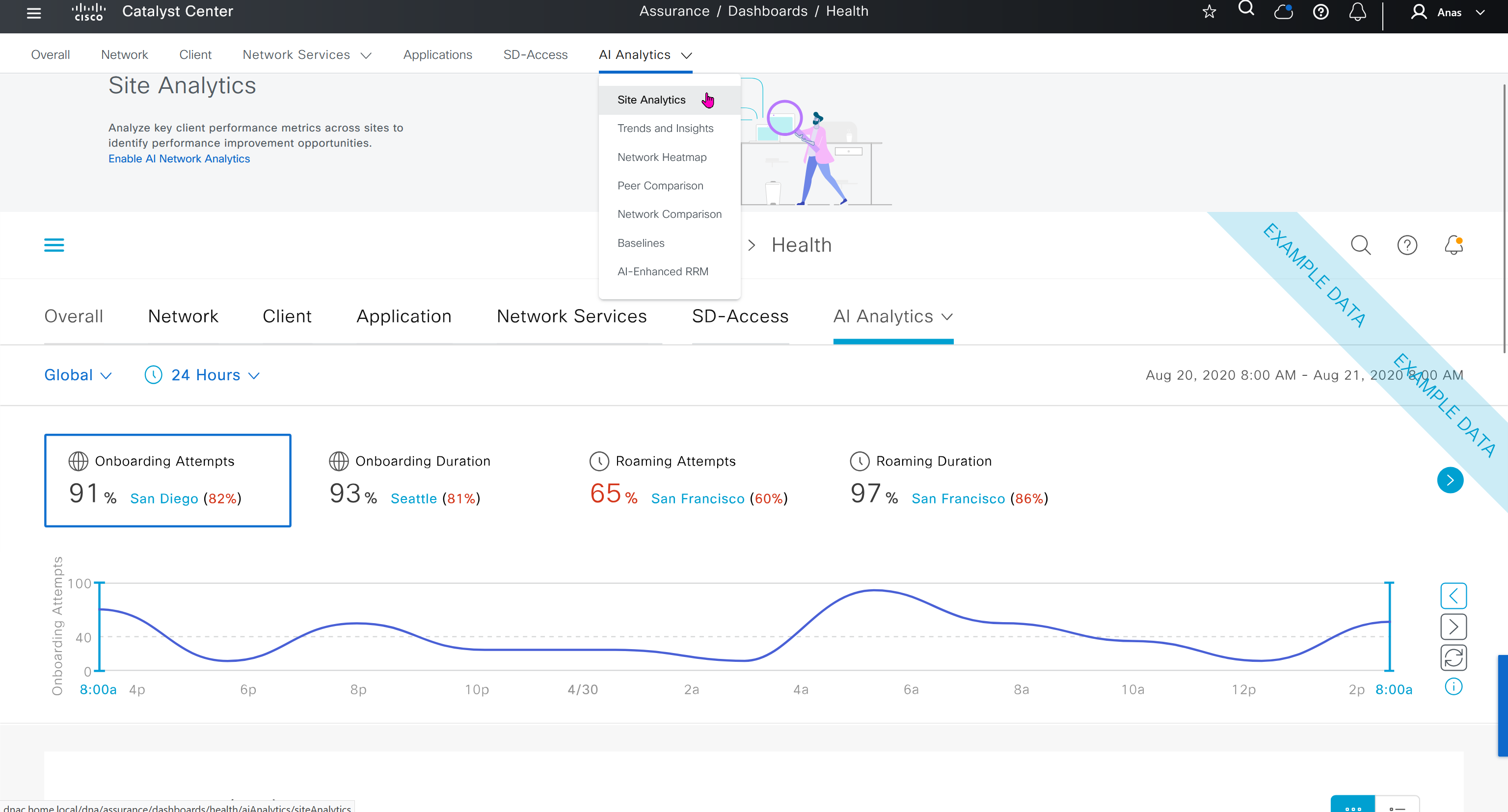
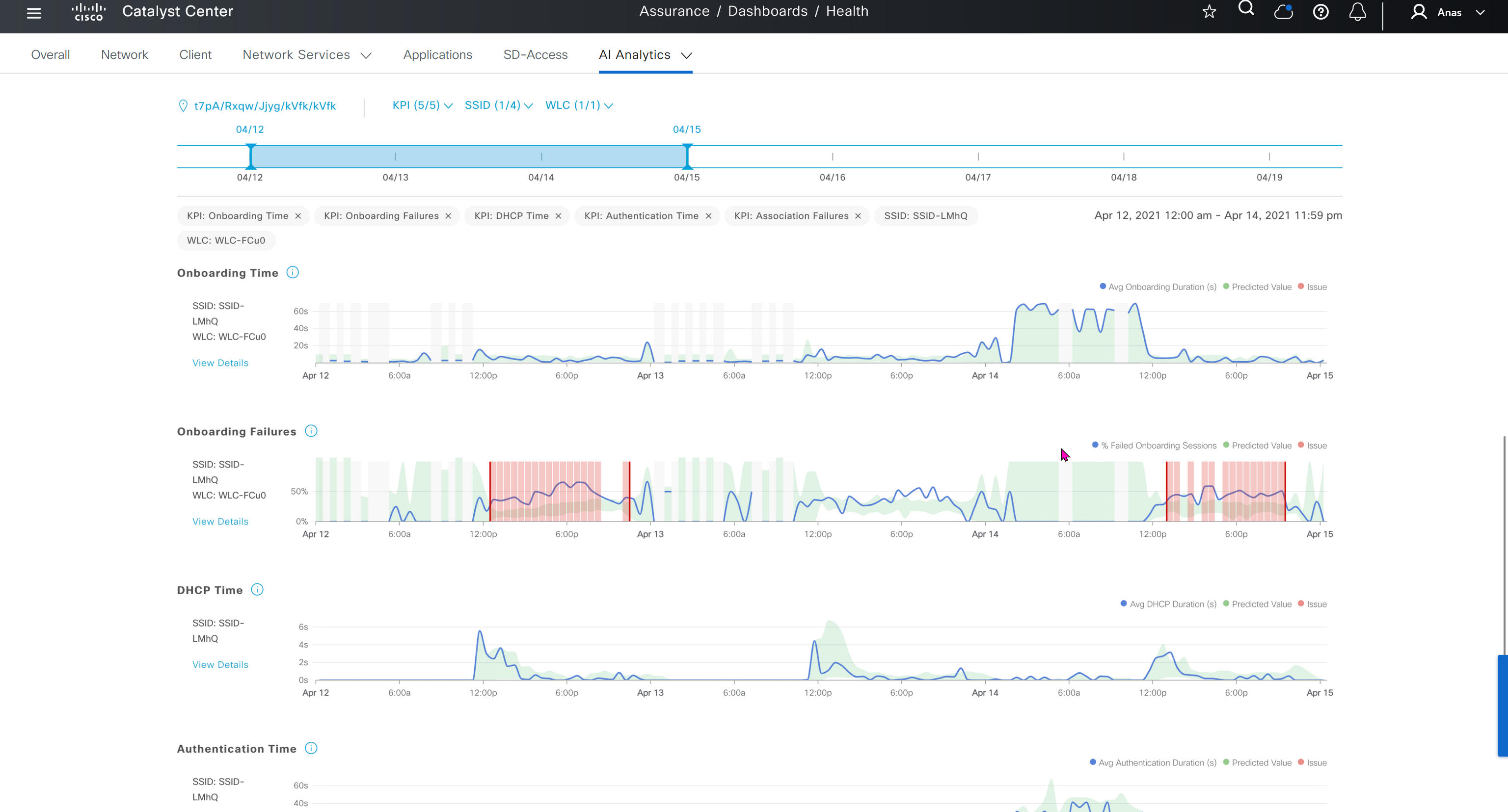
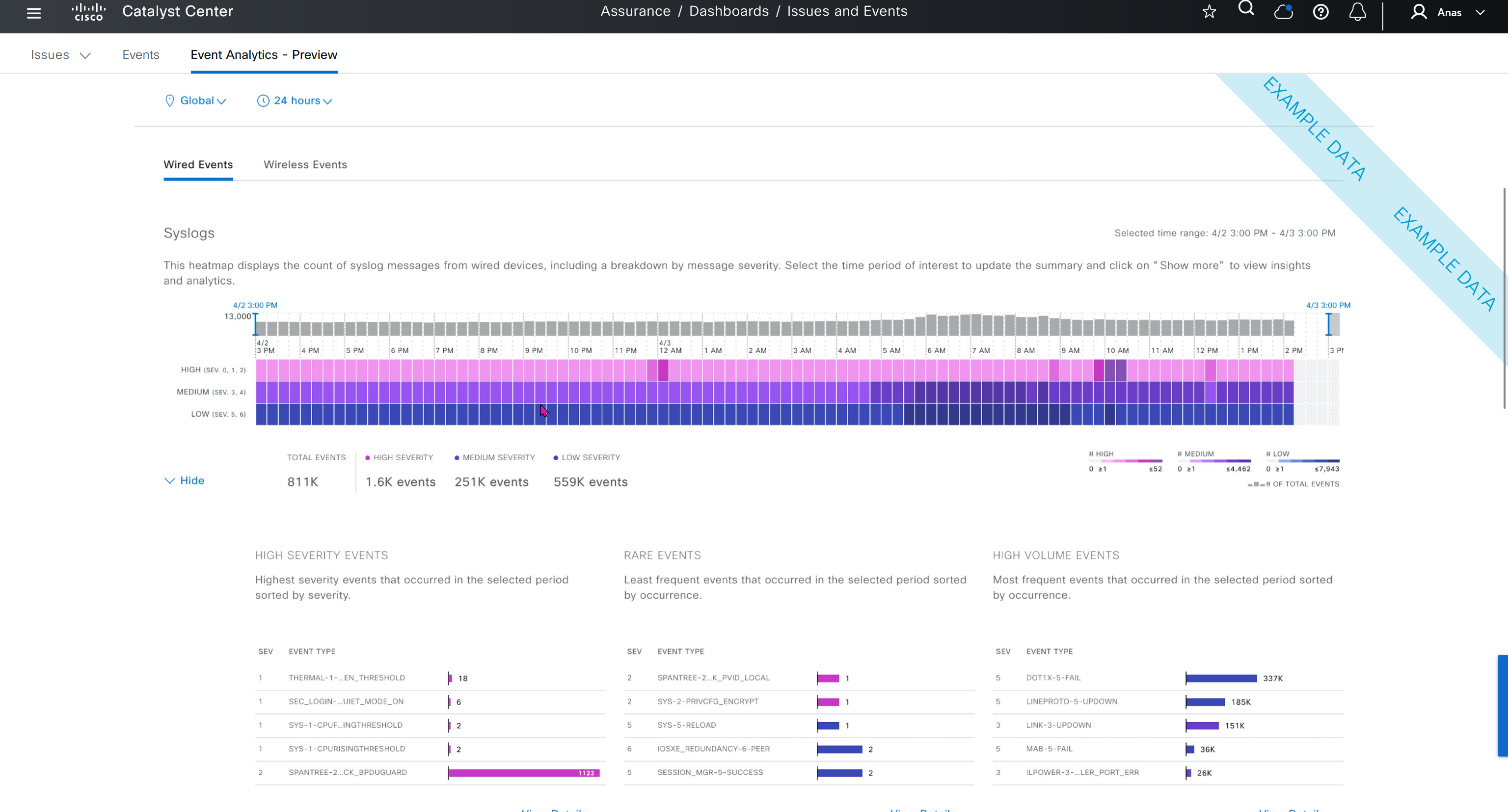
This Trends and Insights leverage AI in Cloud and Machine learning to spot issues in network,
Trends and Insights deals with deviation in capacity and performance
Site comparison shows us how one site compares to another, as in some cases one site can perform worse than the others


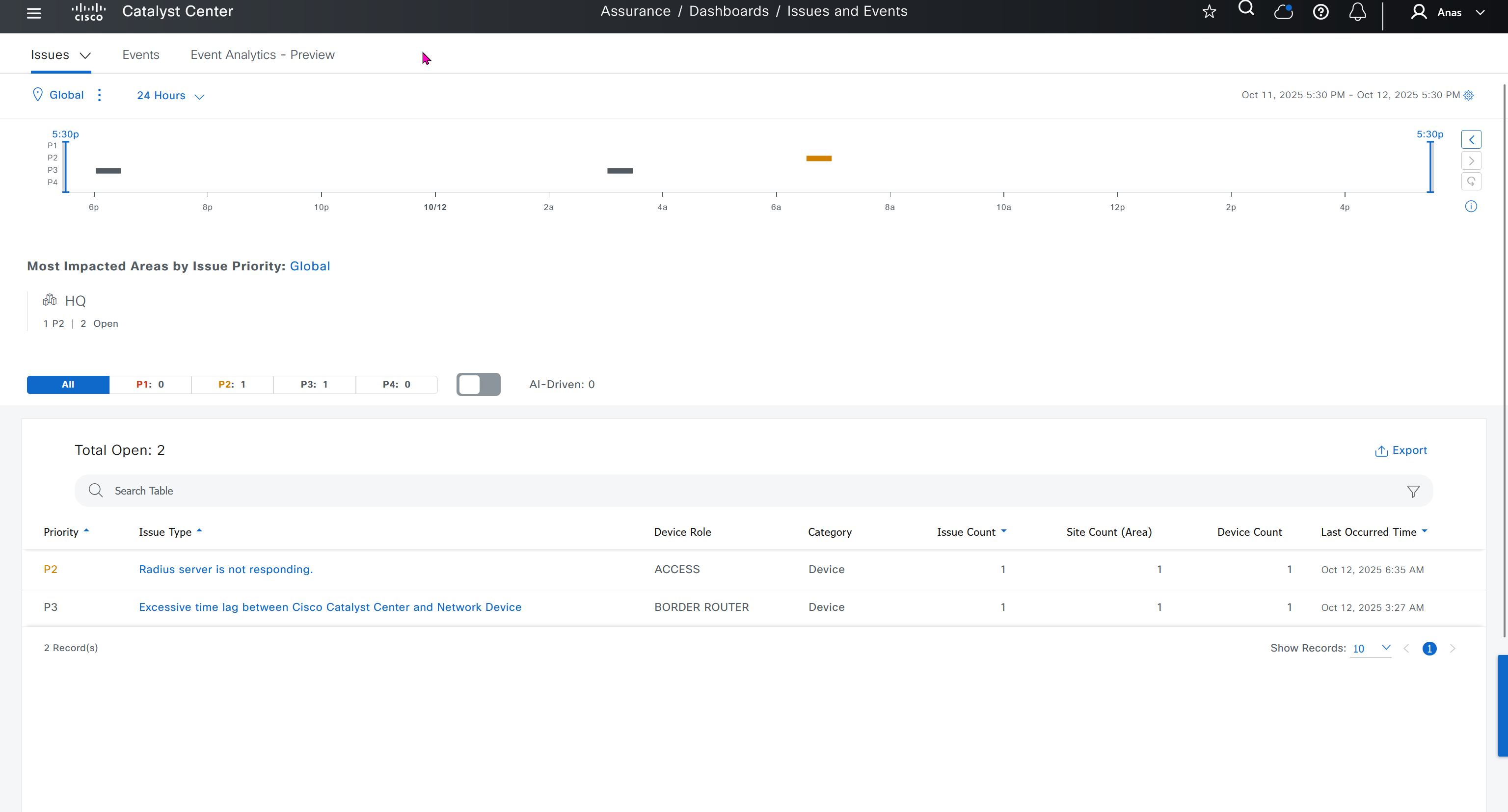
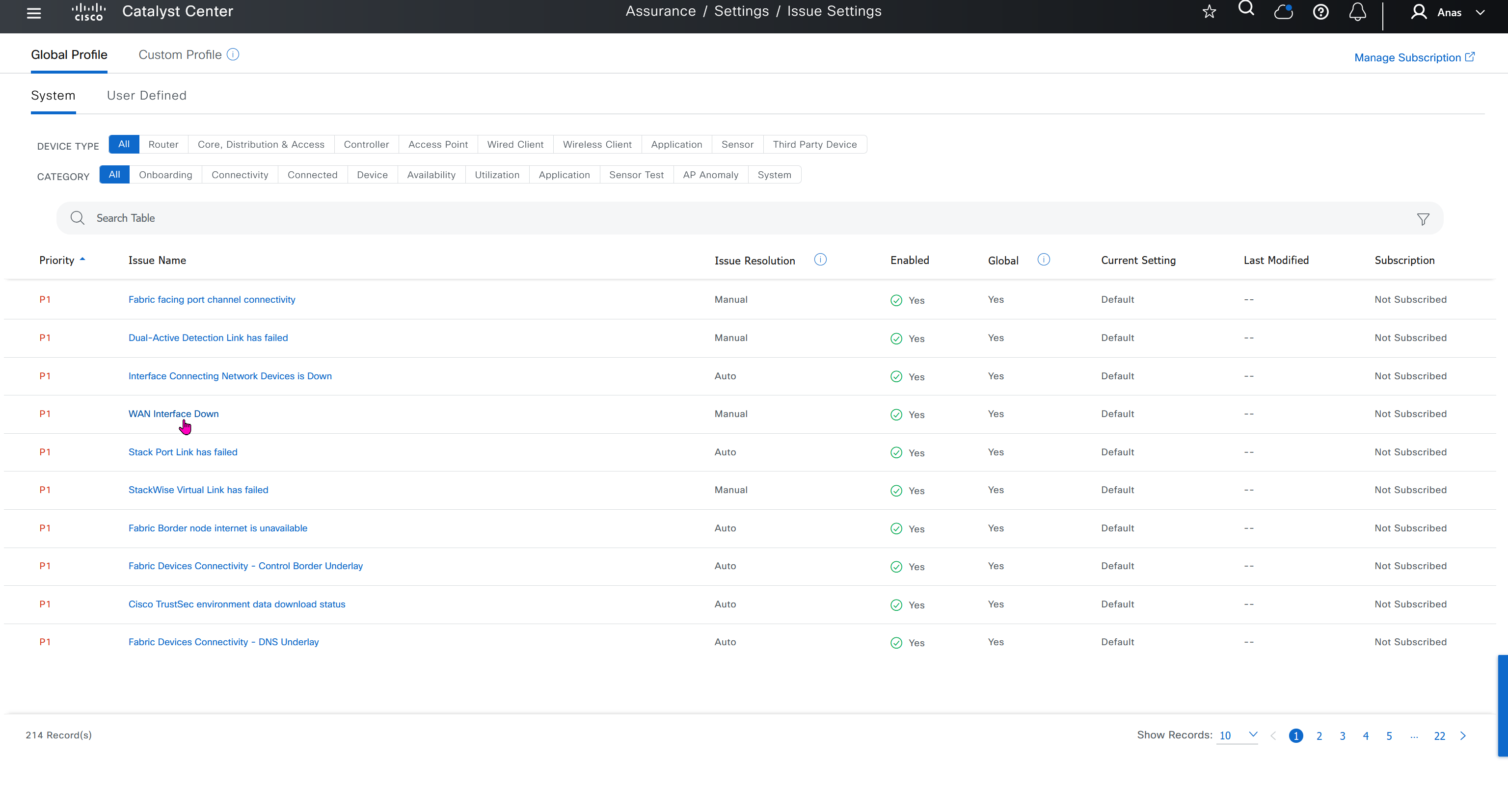
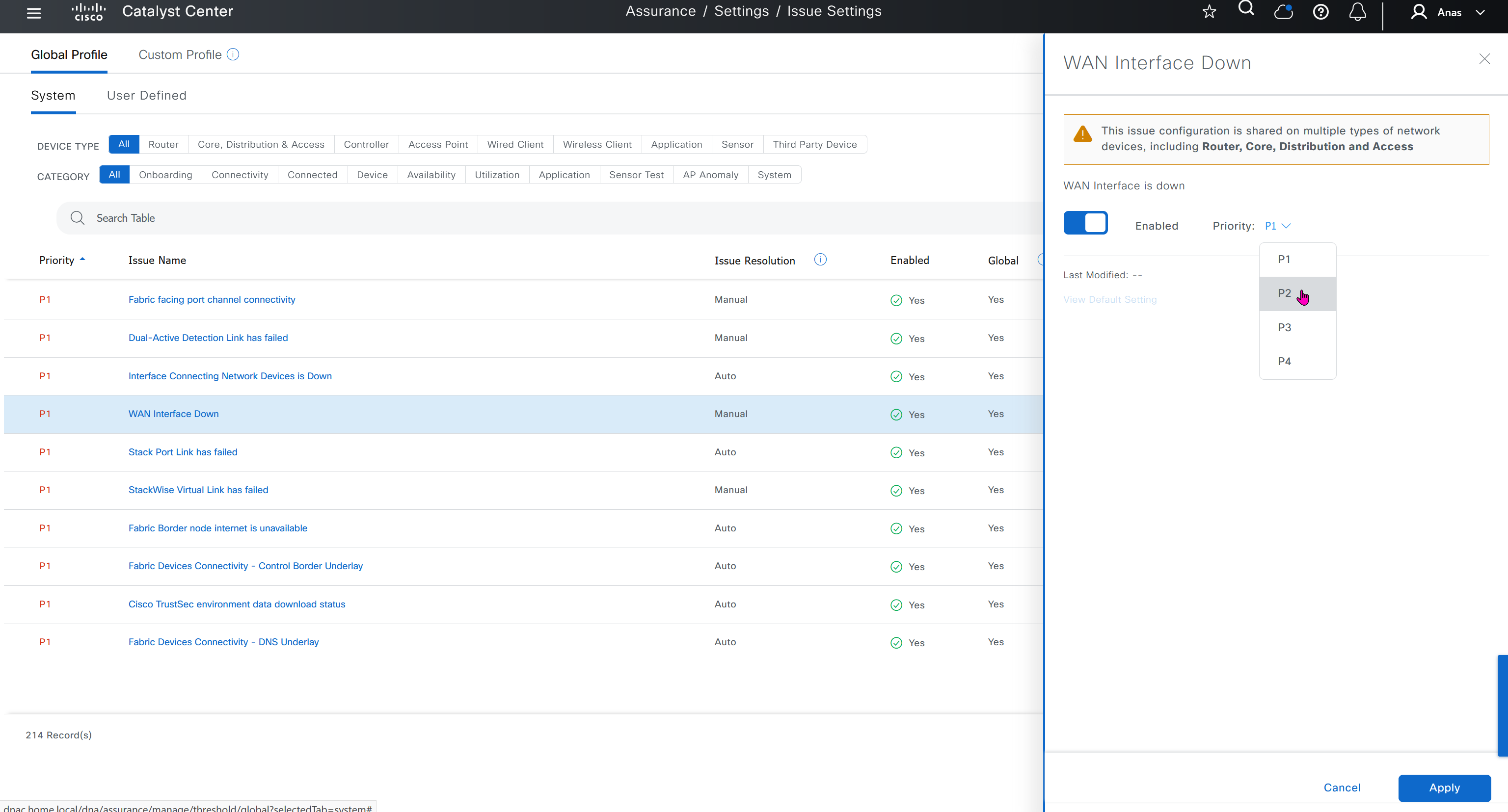
Issue settings is where we can control what issues such as P1 and P2 can be raised by DNAC such as Assurance > Issues & Events, we can enable or disable some of these issues if they are not important to us, we can also change priority on them

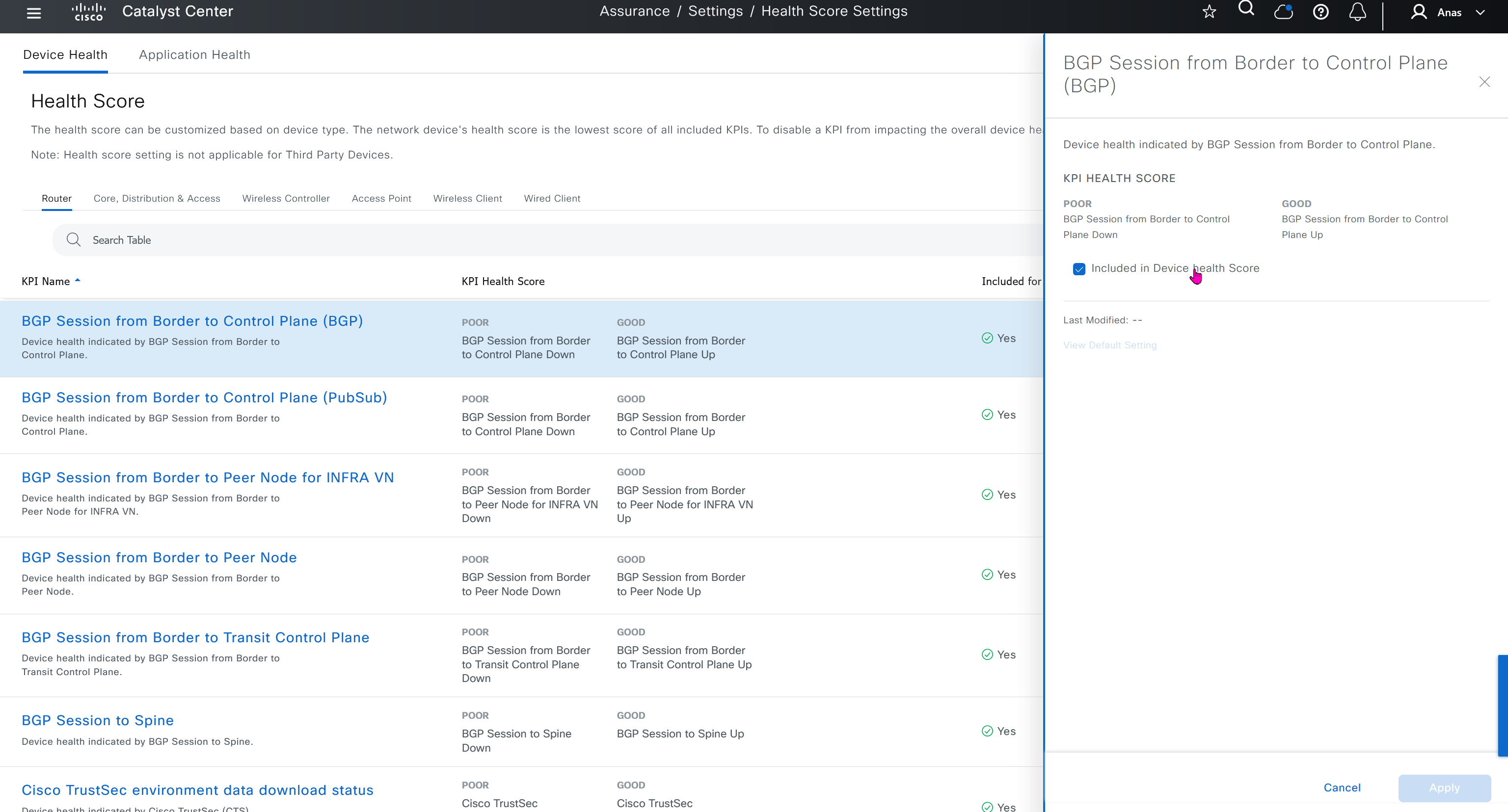
Health score is where you can turn on or off on what is included in determining device health score, these health score threshold values can be modified as well


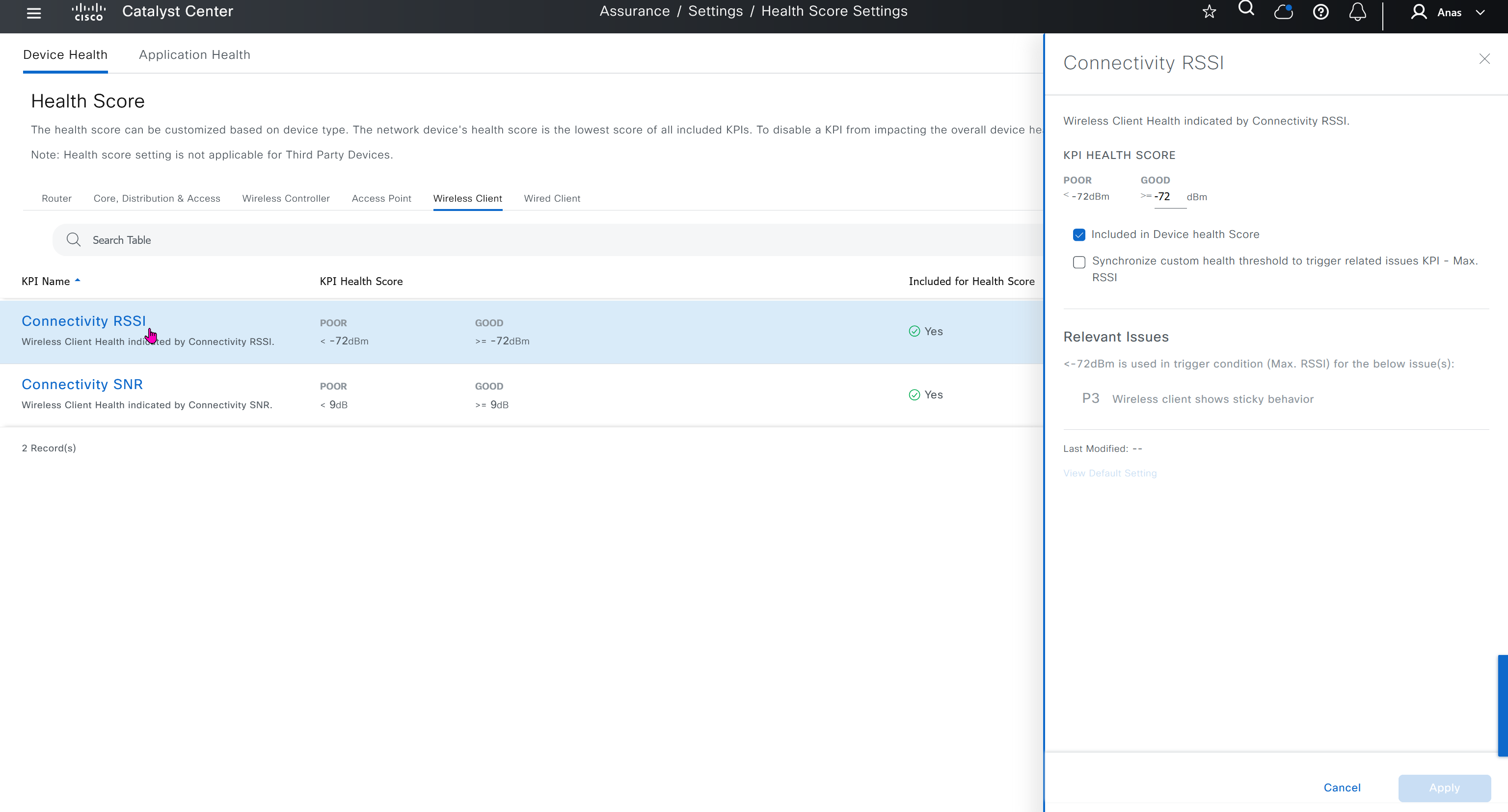
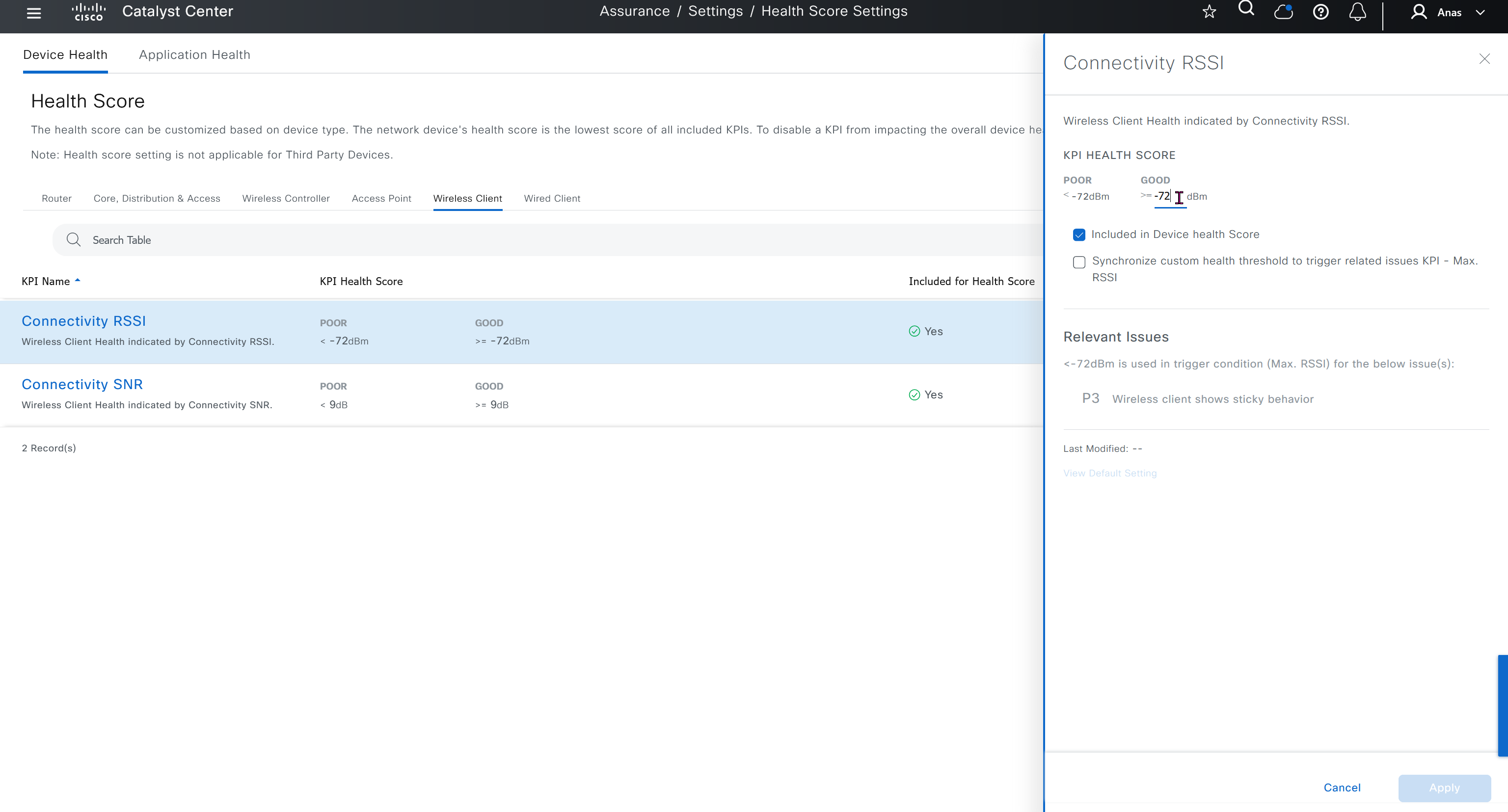

Sensor section here we define test settings such as ping, HTTPs, association test etc
Intelligent capture is where you define how and when you want your AP to perform capture of client traffic
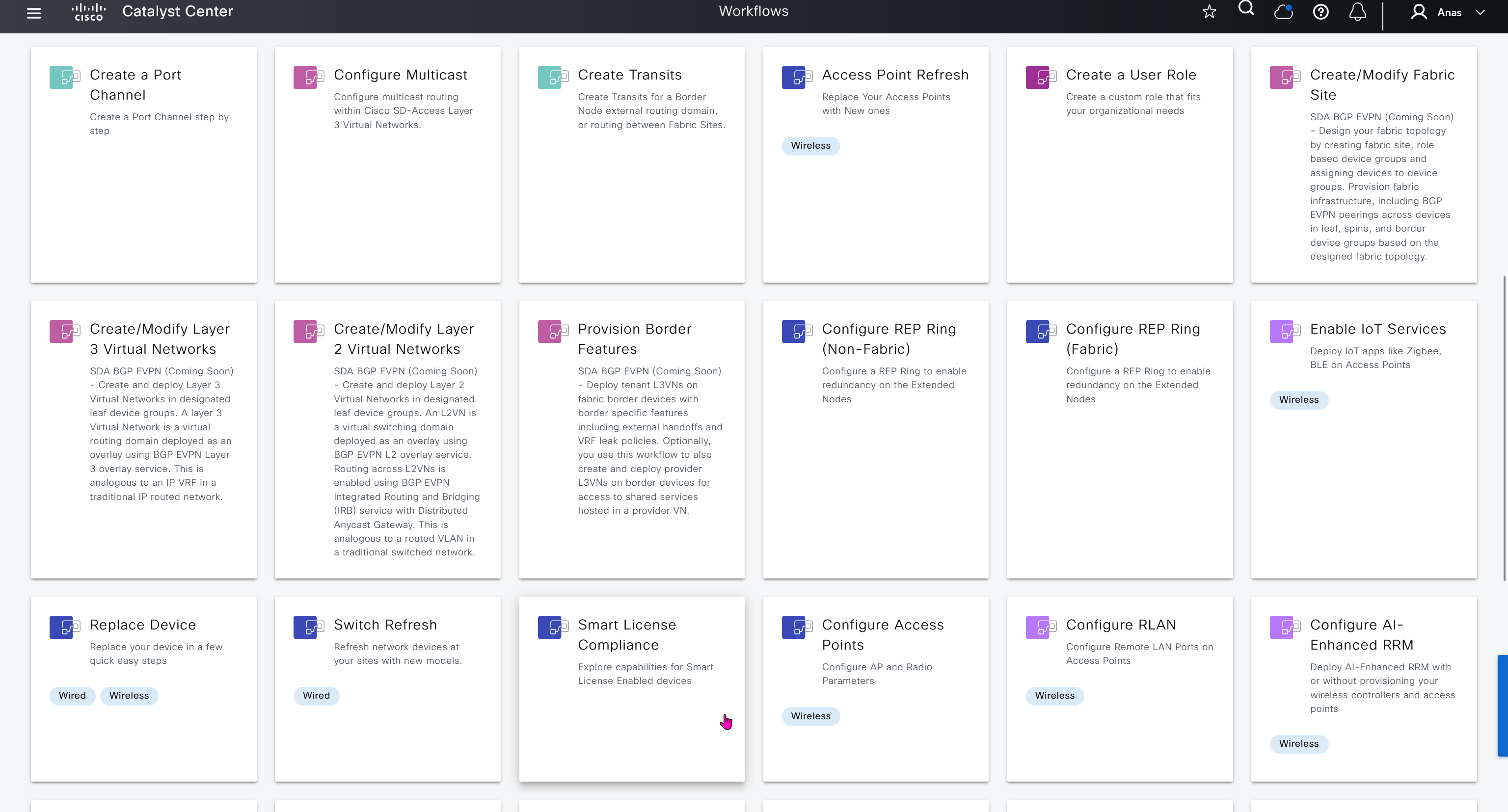
Workflows make things easy for us as they are guided configuration wizards that help us configure things easily and quickly without making mistakes




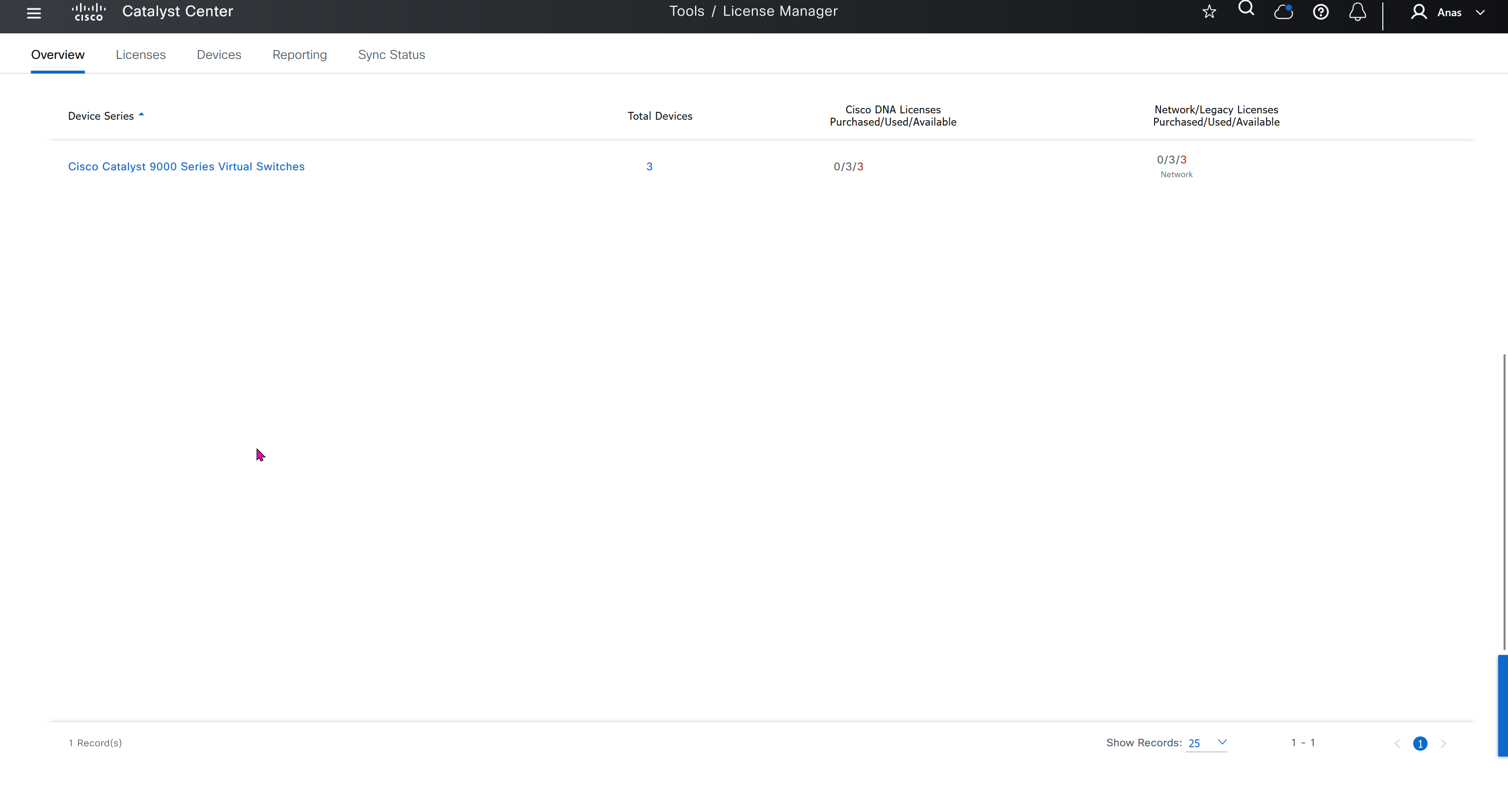
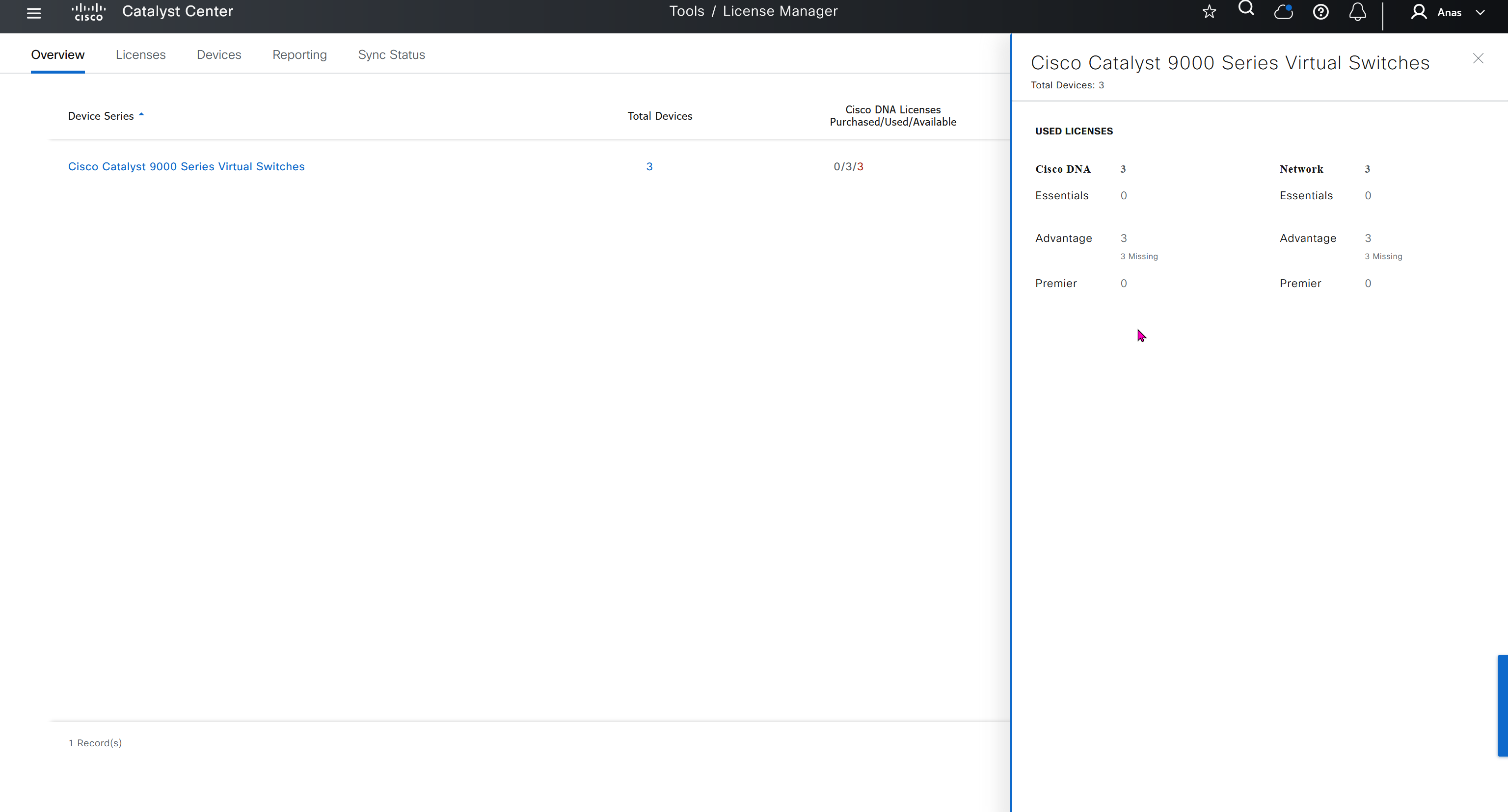
CLI templates is where we create templates, when it is time to apply template then we apply them using Network profiles

Feature templates are graphical UI based configuration unlike CLI template and they dictate best practice rather than manual CLI based templates, this makes configuration like Meraki but we only have this wireless at the moment
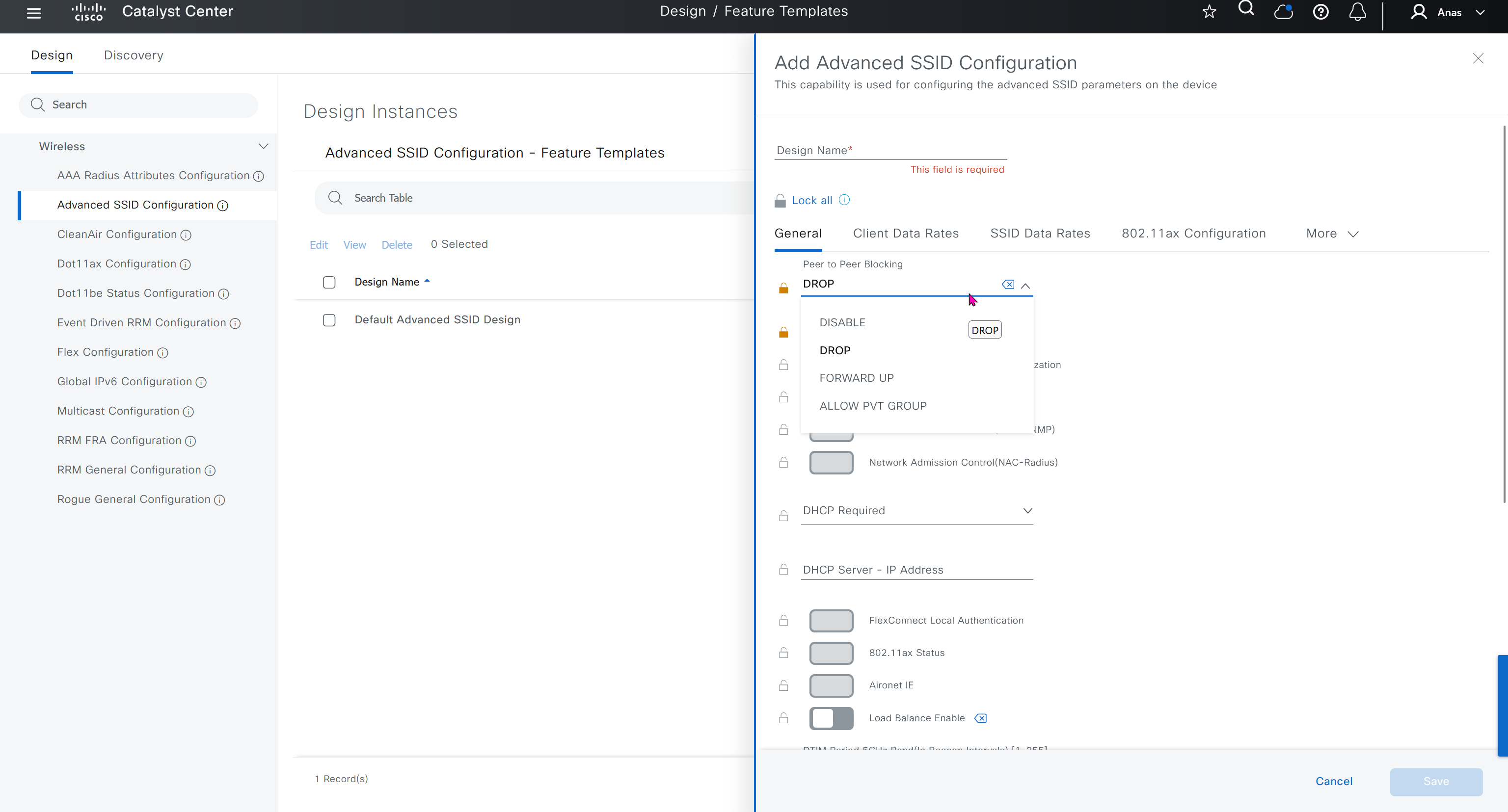
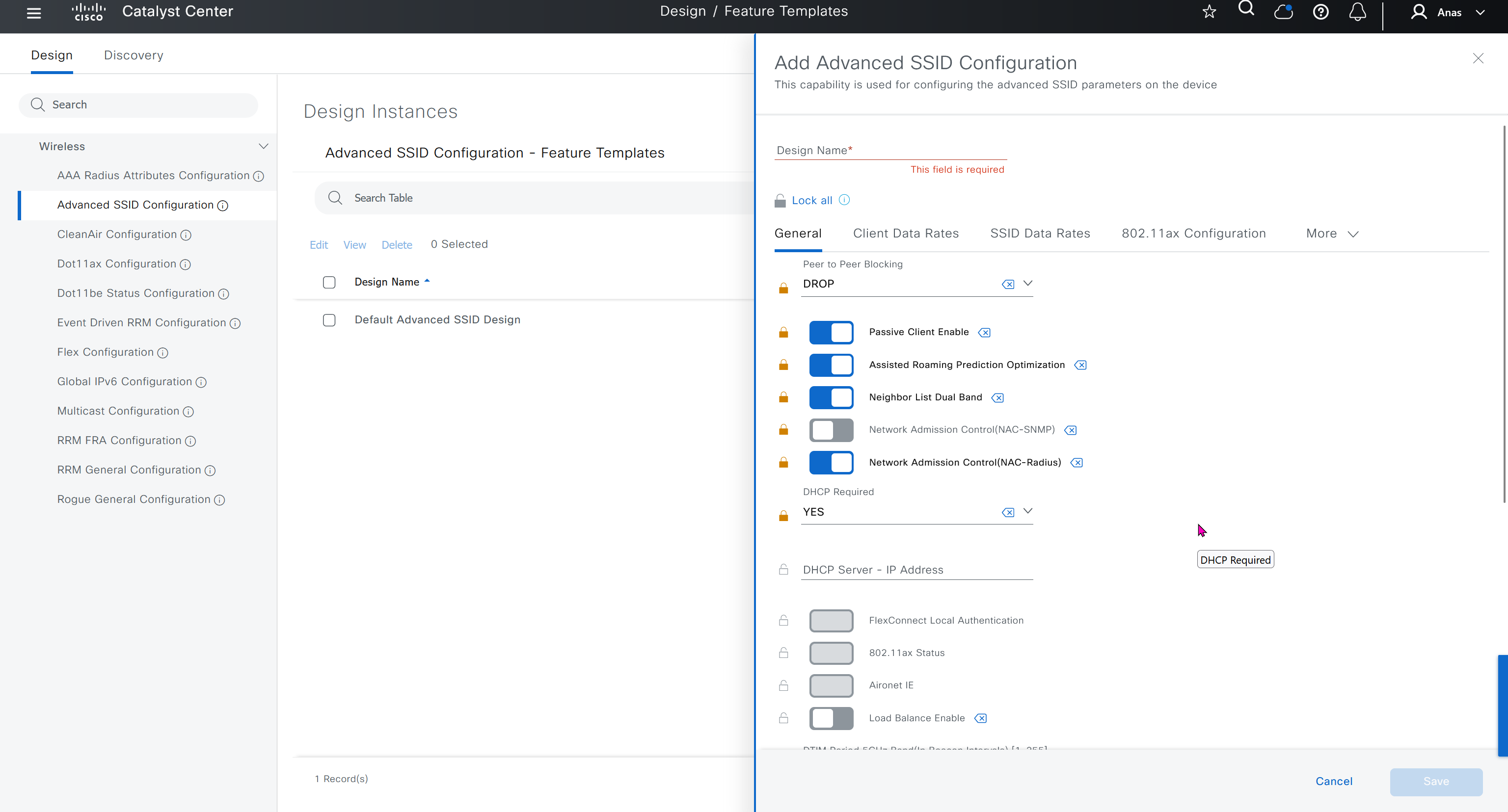
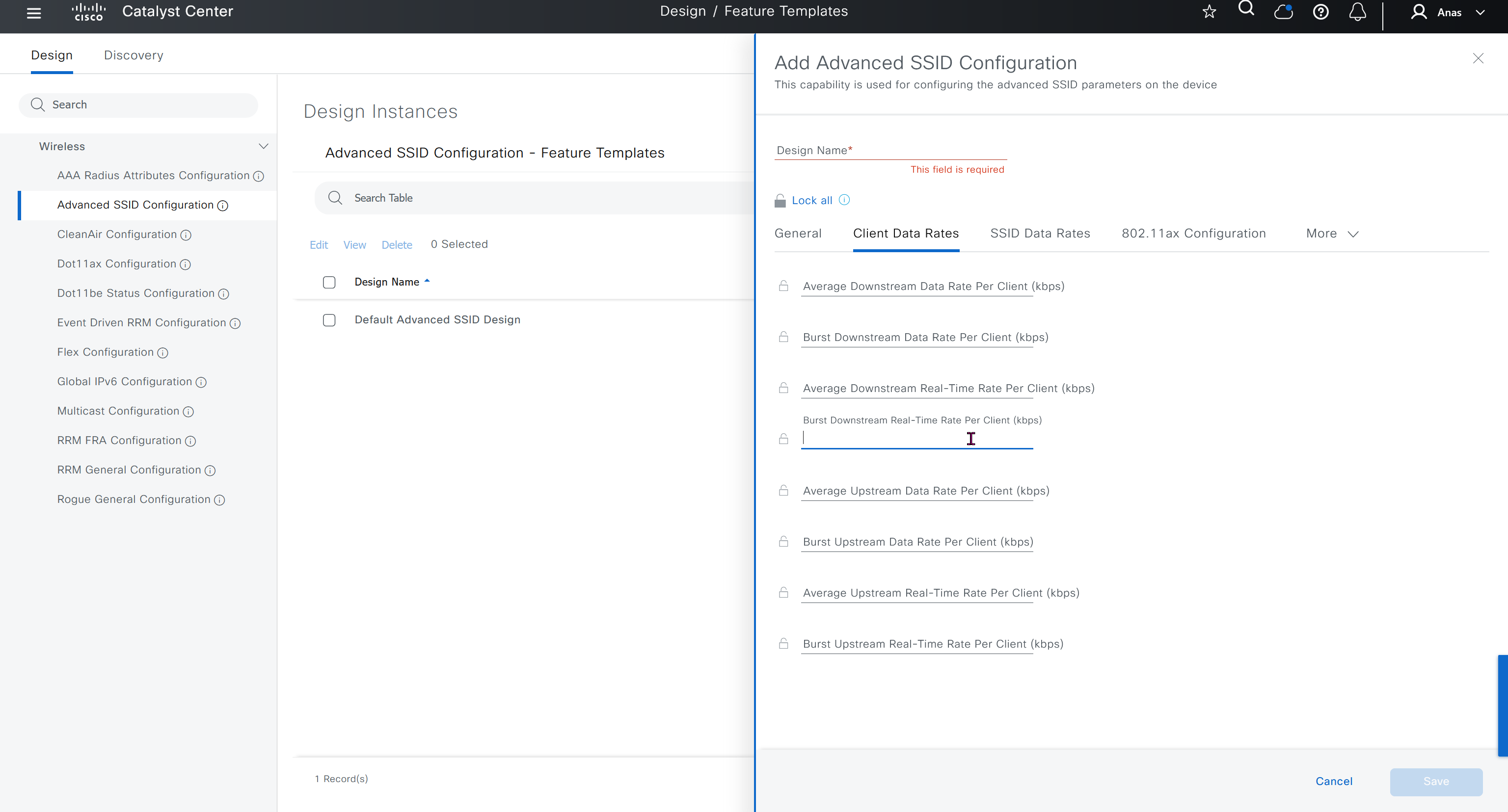

Network reasoner helps troubleshoot offered issues in Network reasoner dashboard

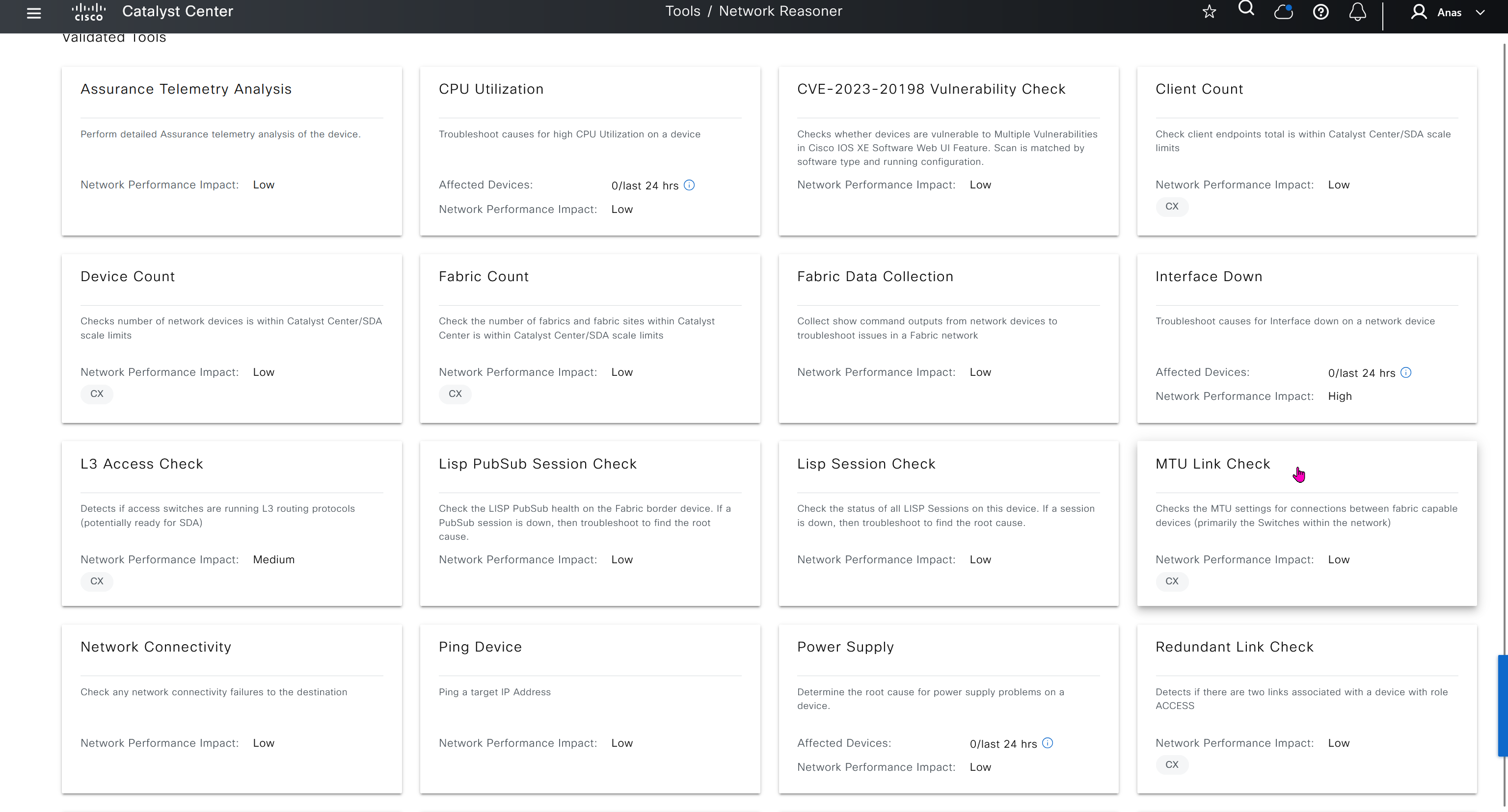
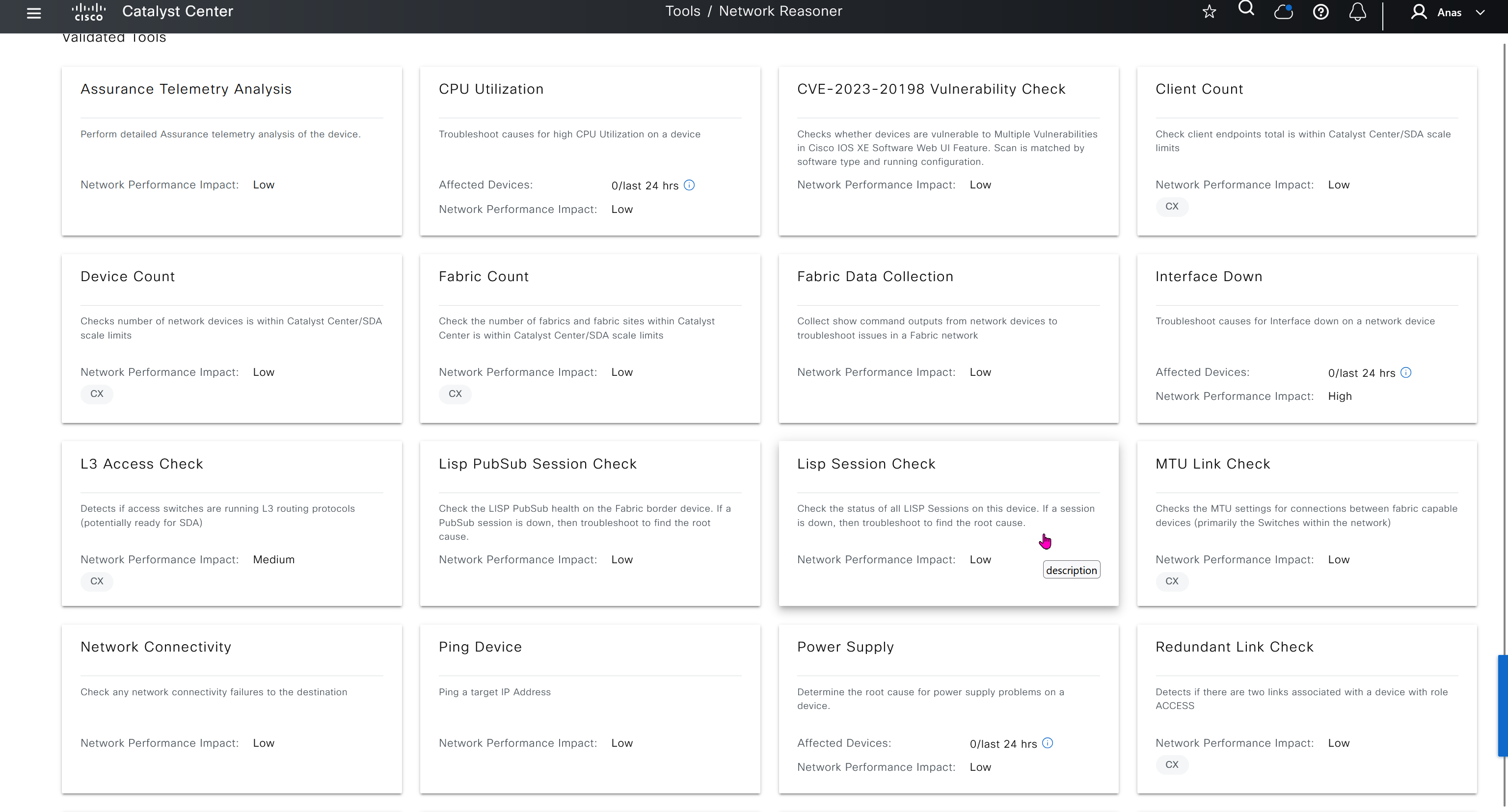
Platform section allows us to use DNAC API for automation and API interaction, it is also used to install device packs for non Cisco devices and also 3rd Party integration such as service now






DNAC comes with report templates
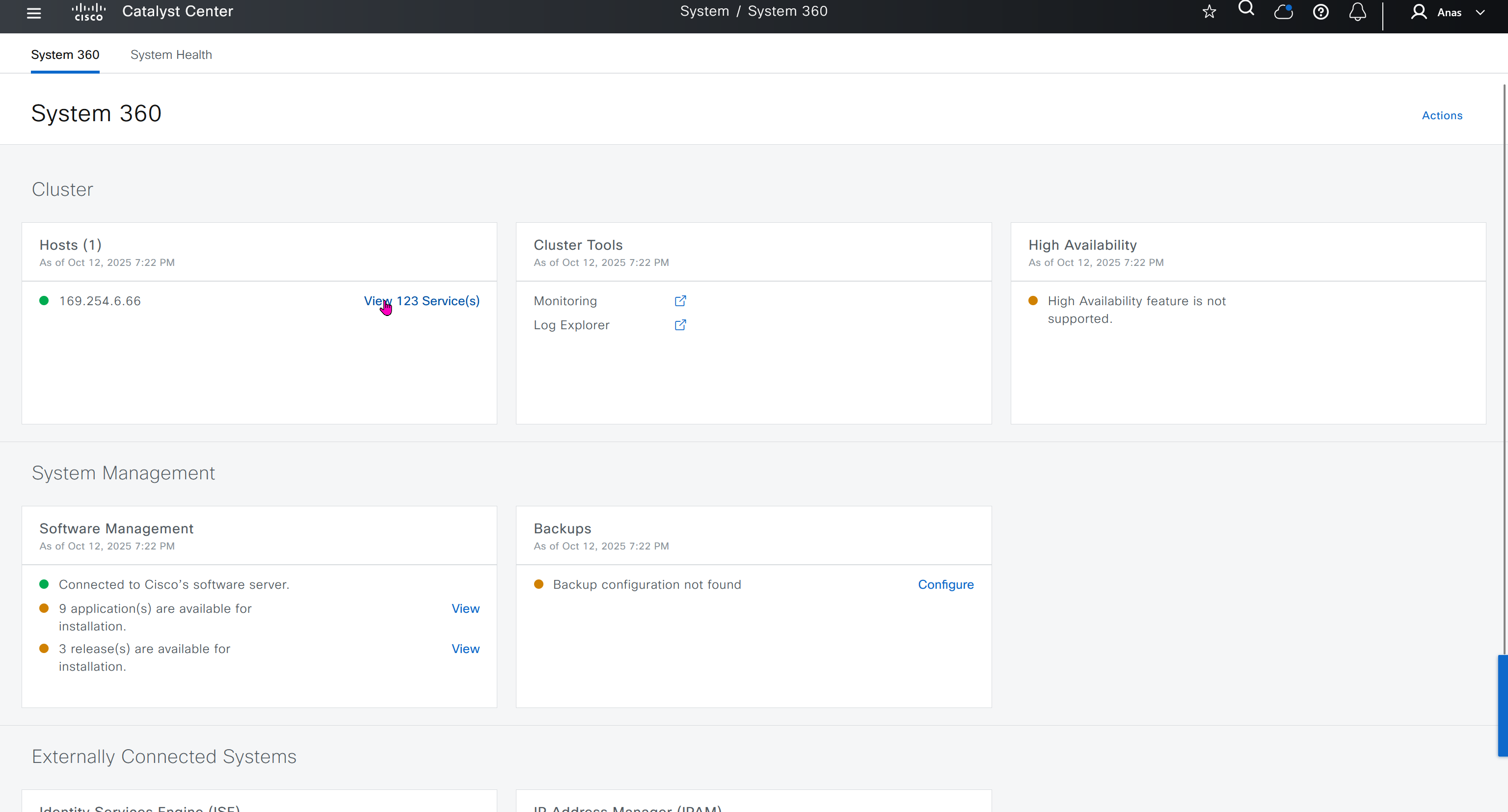
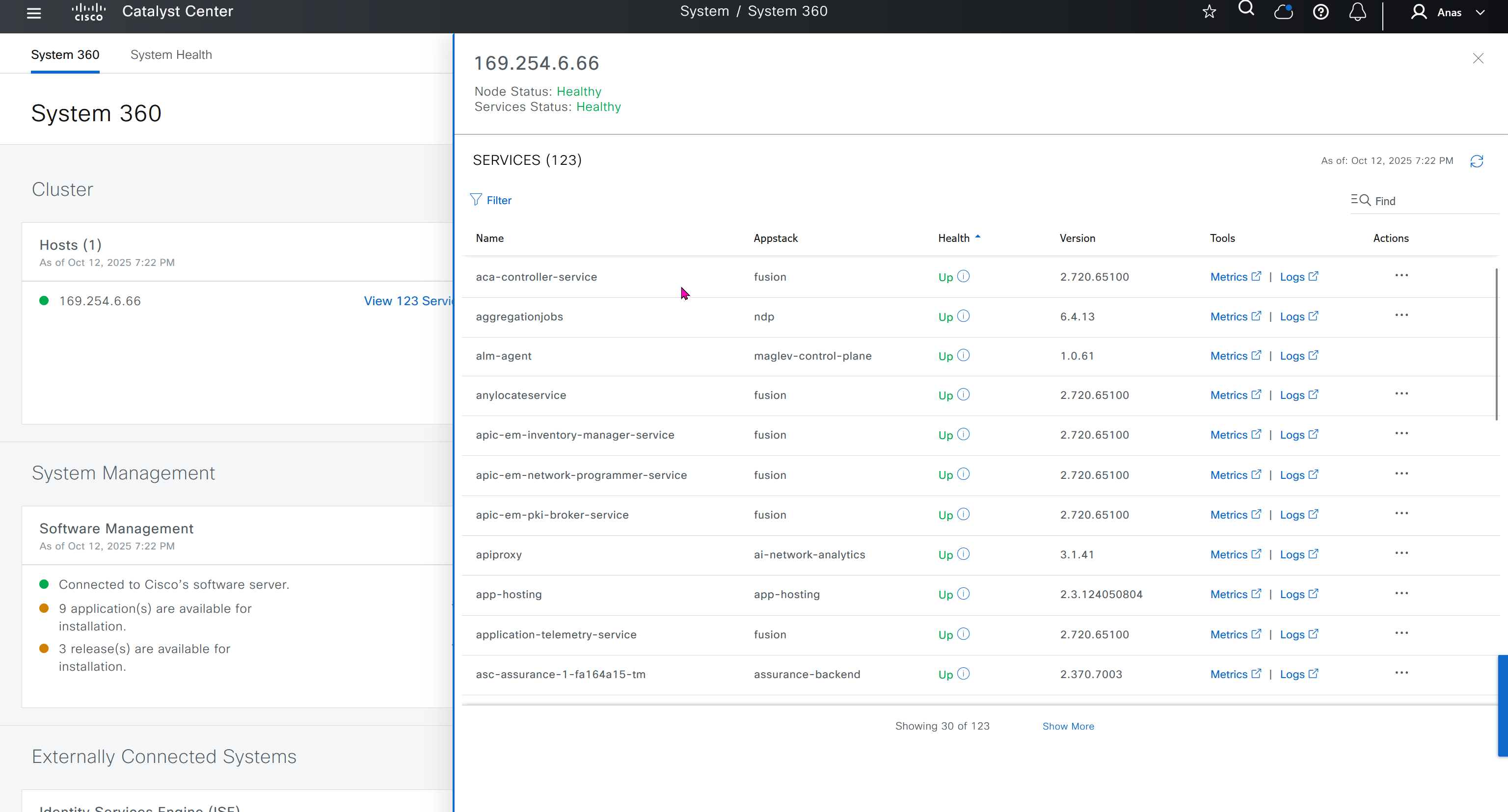

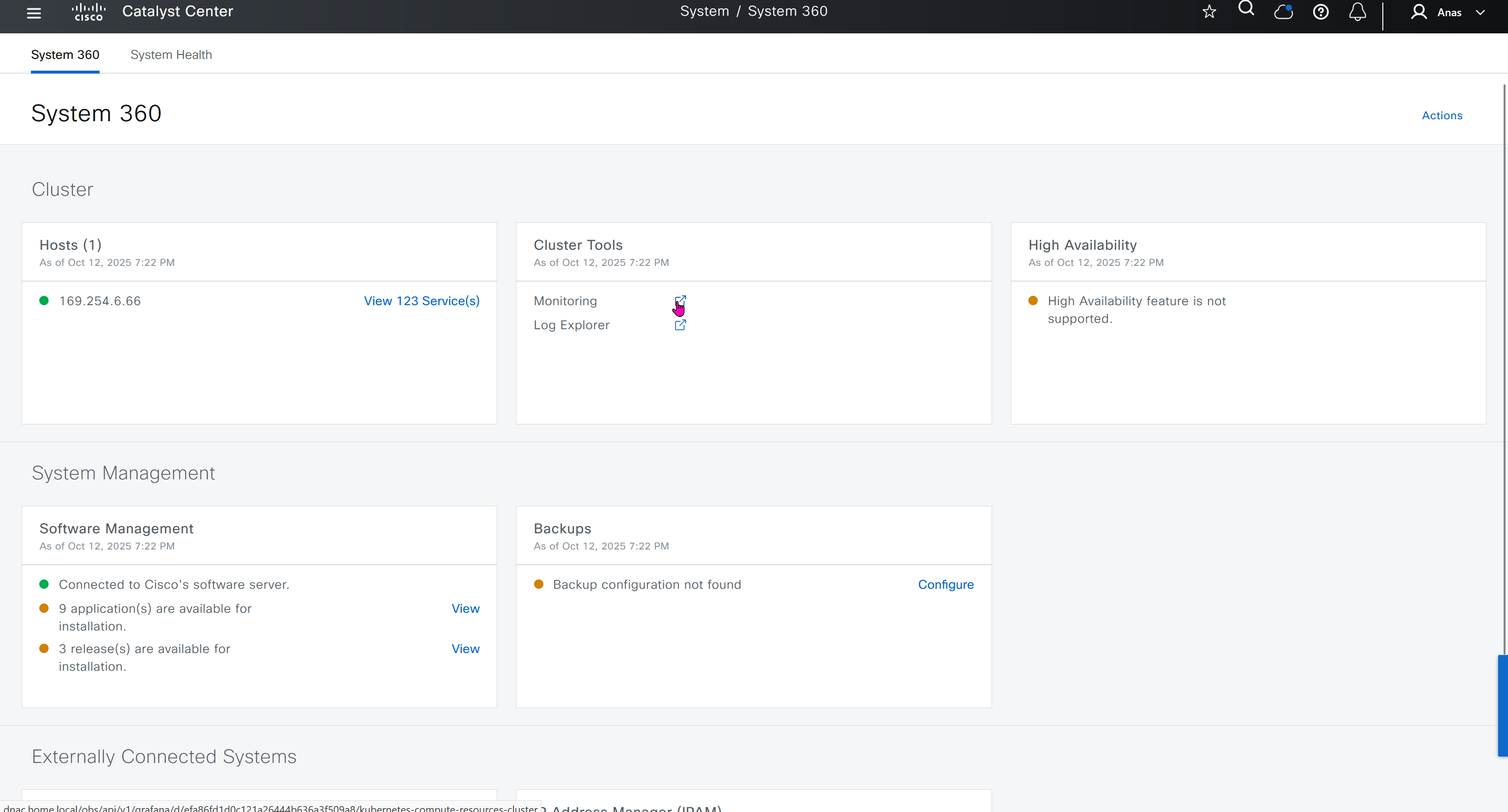





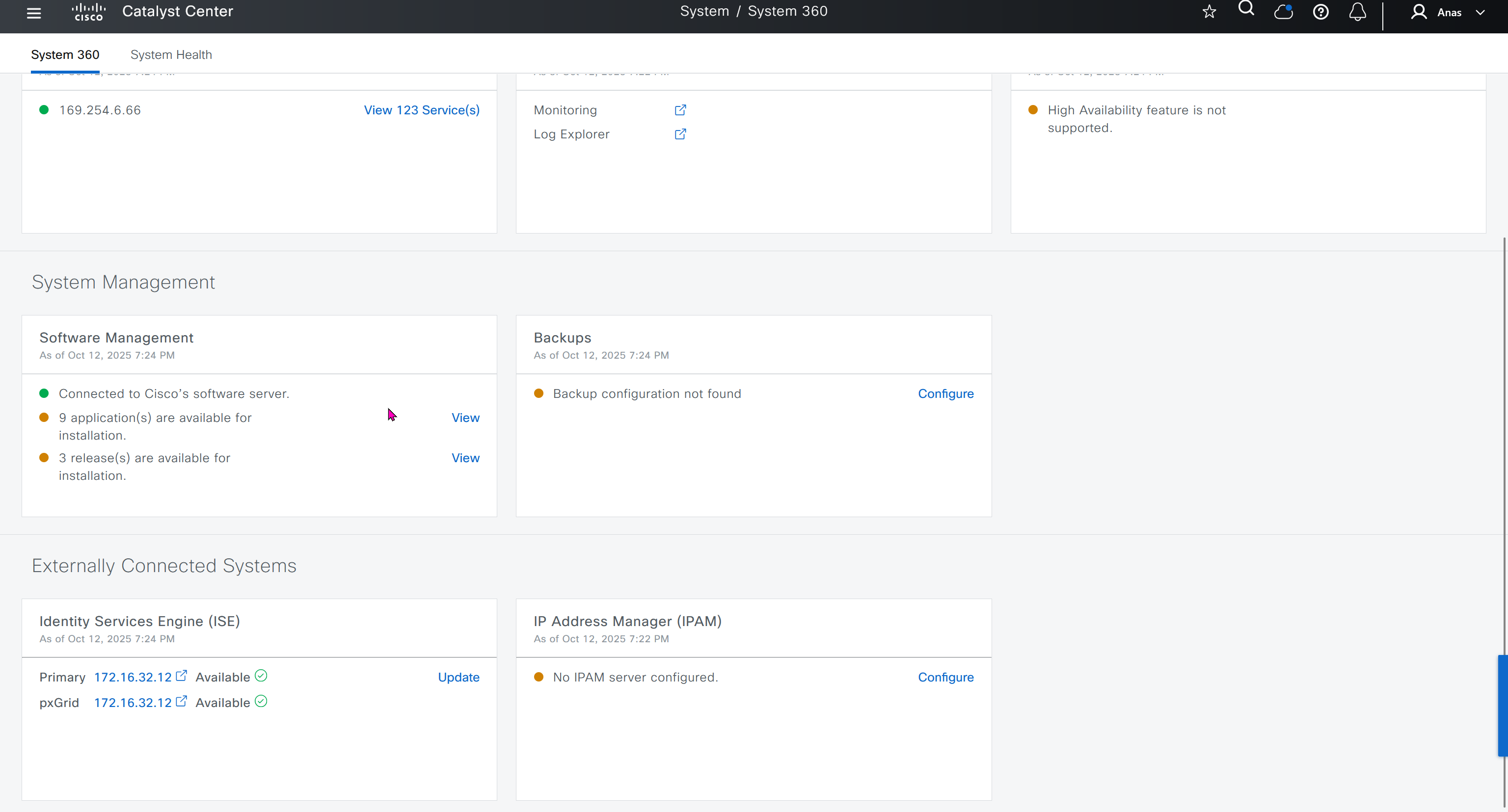

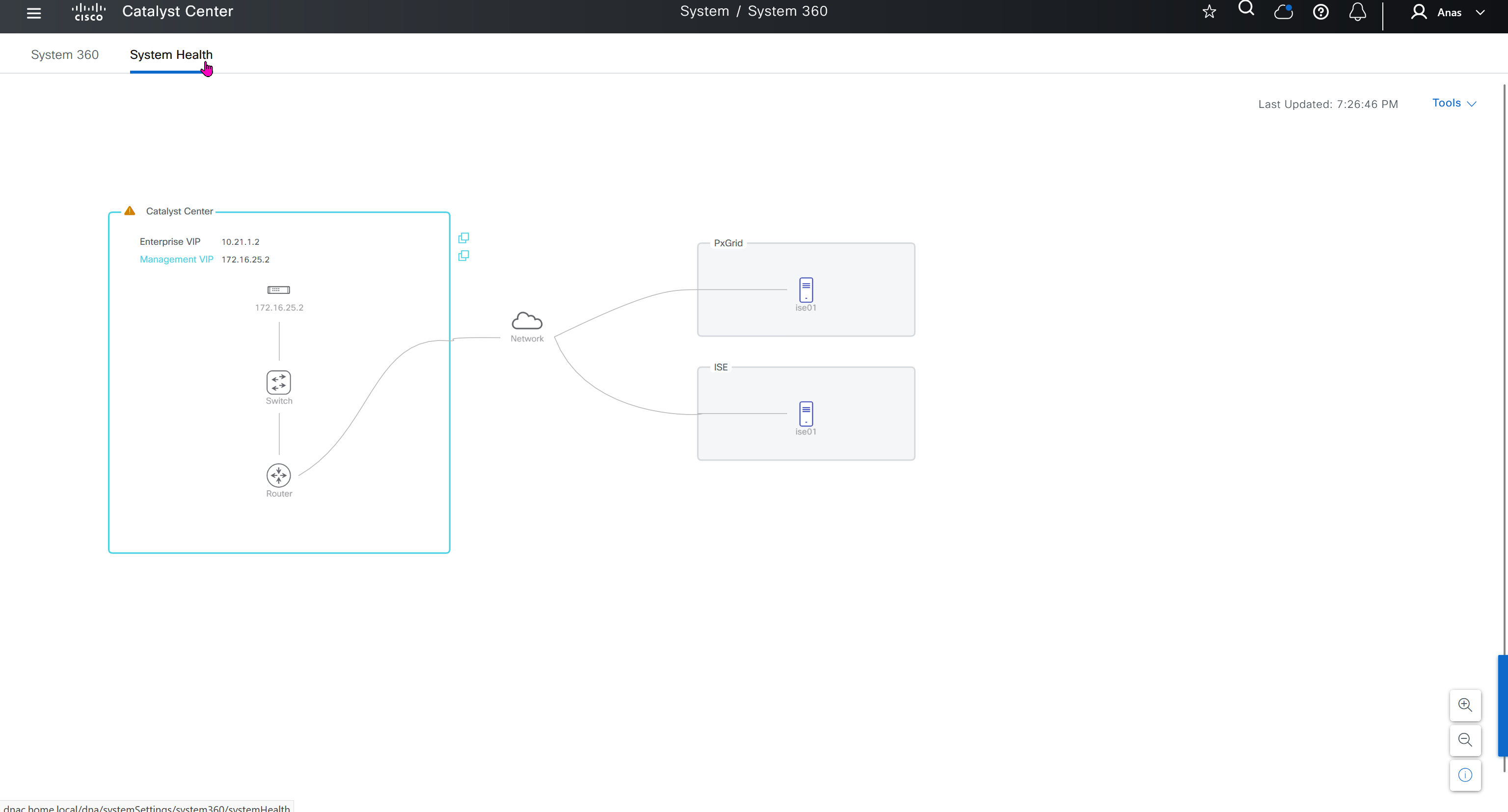

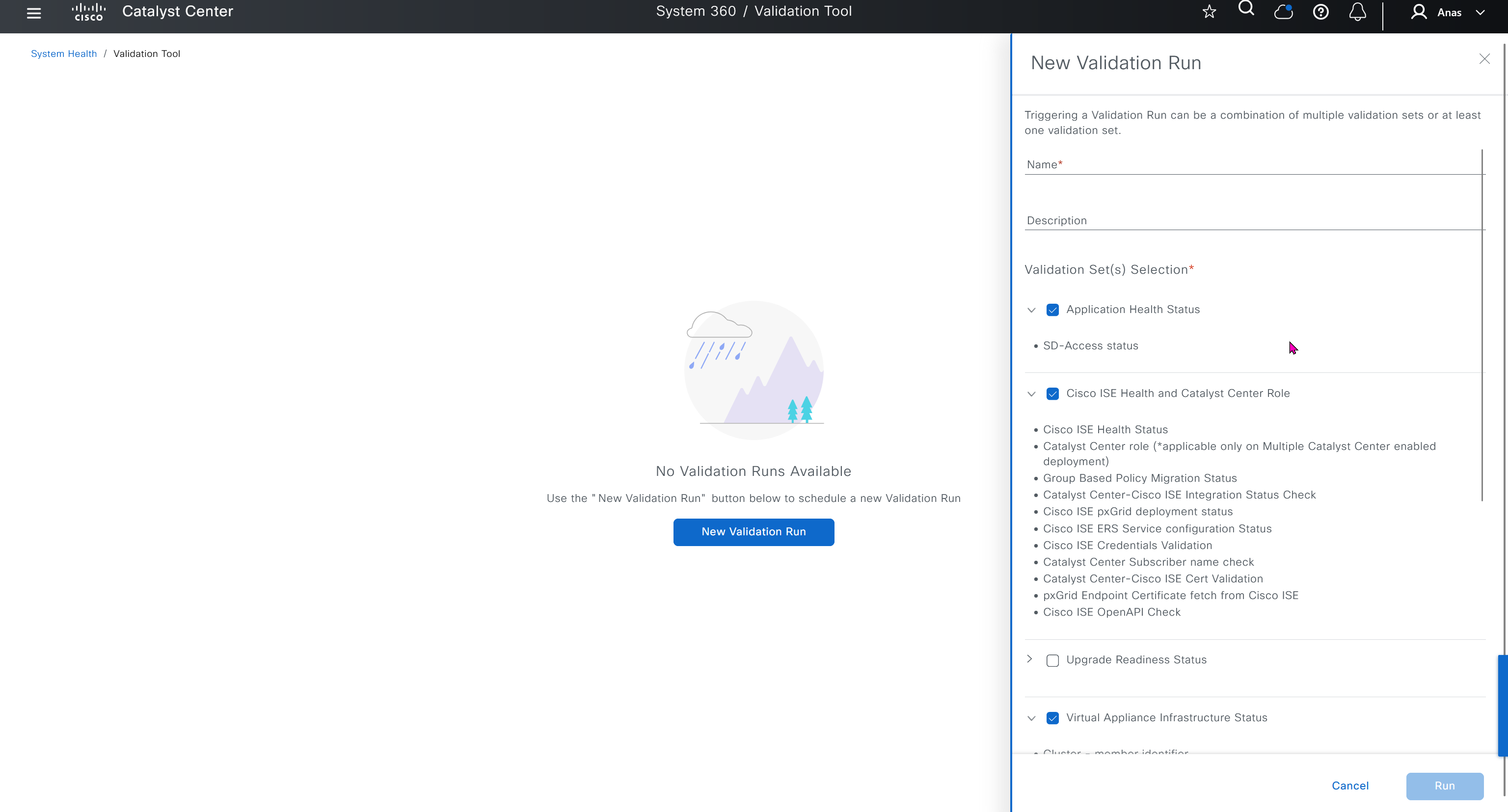
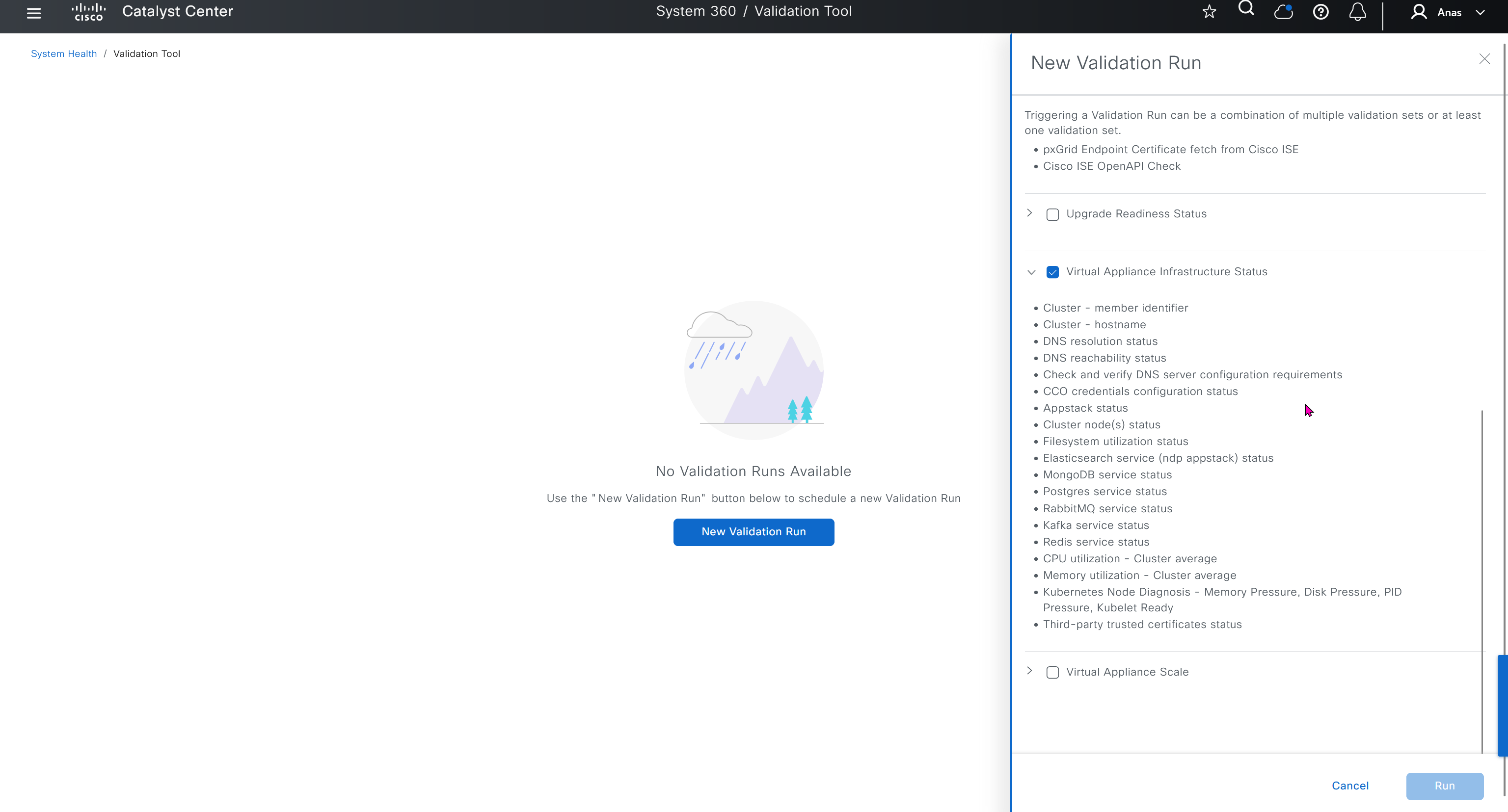

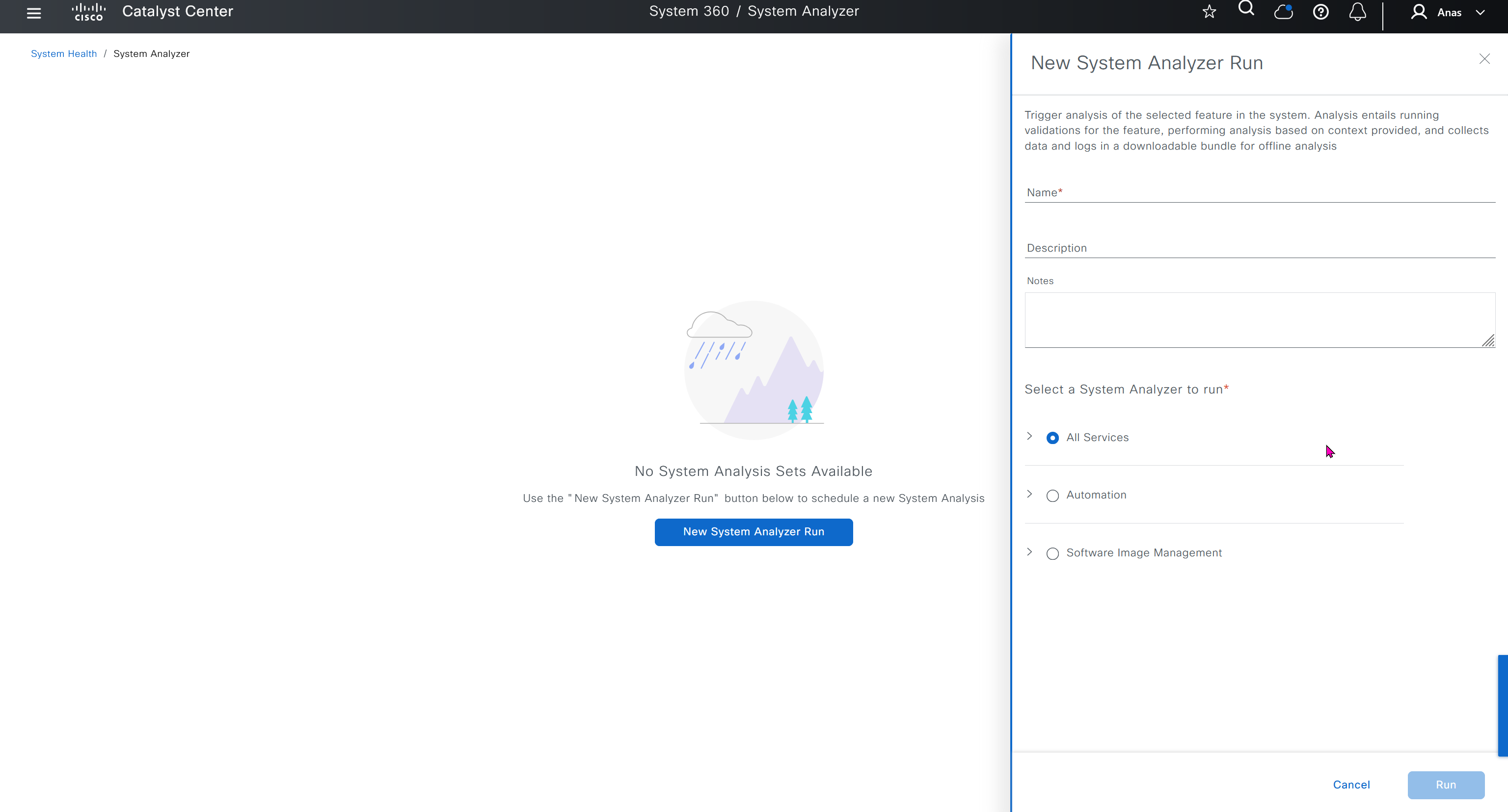
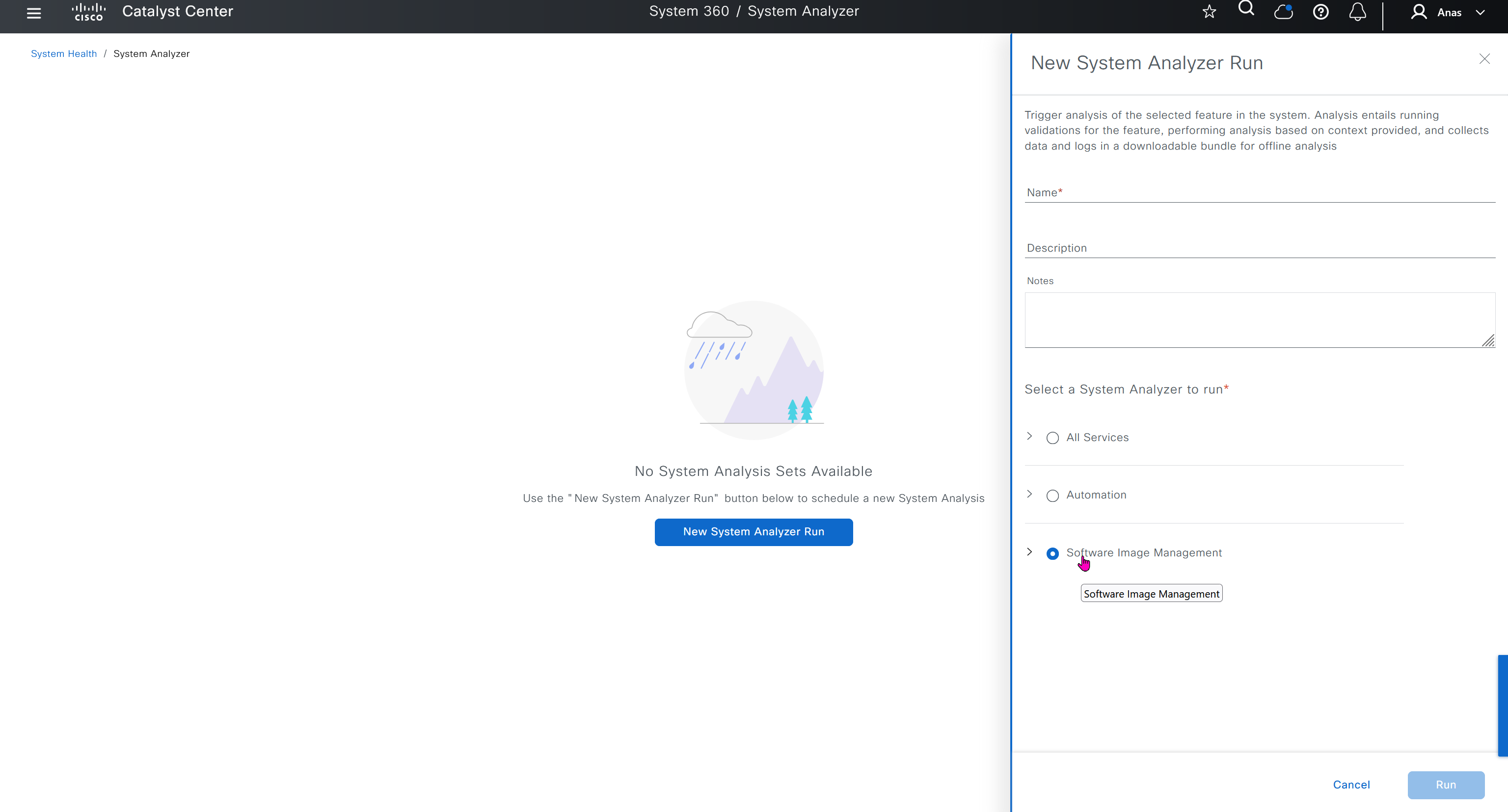
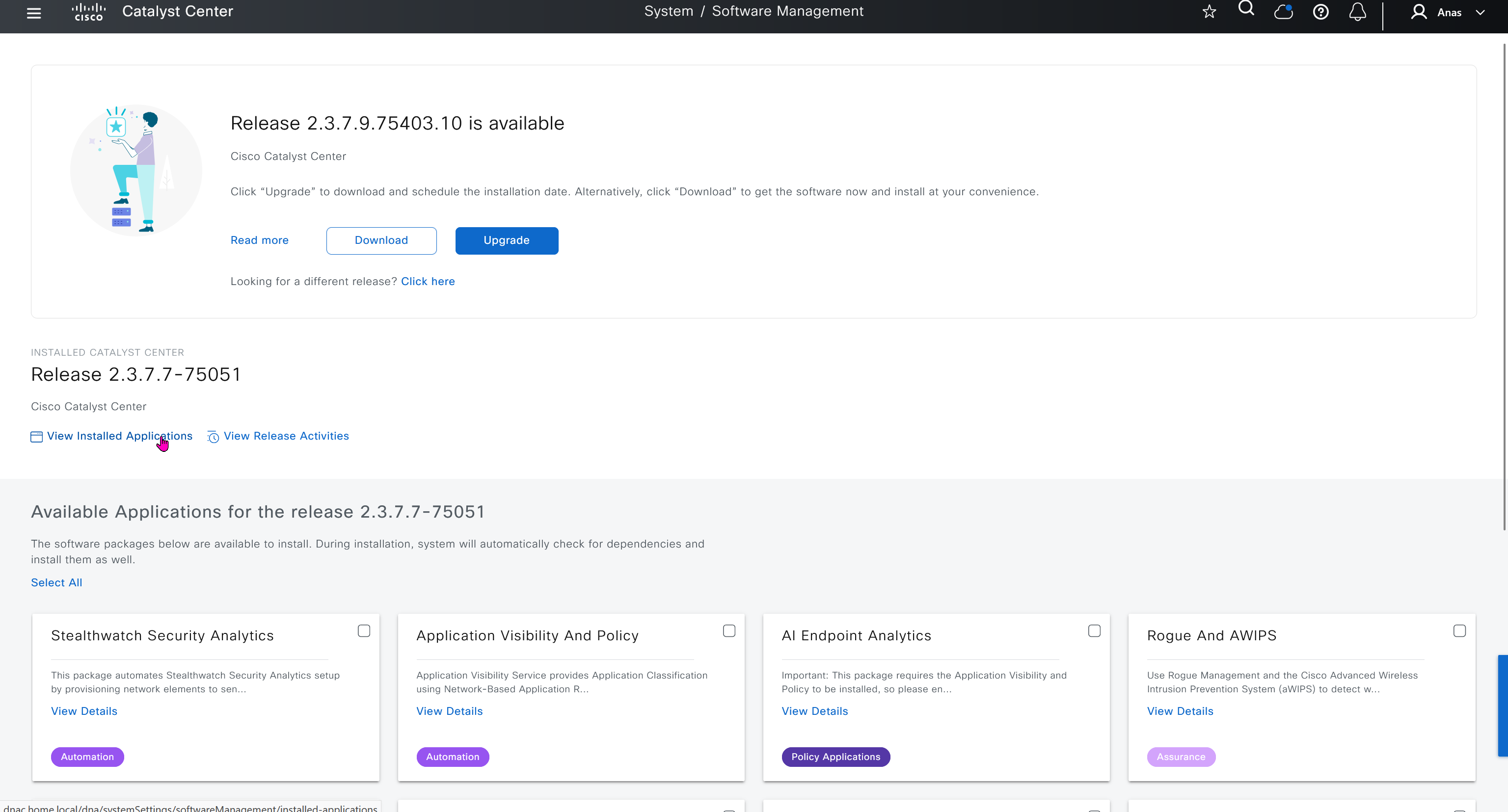
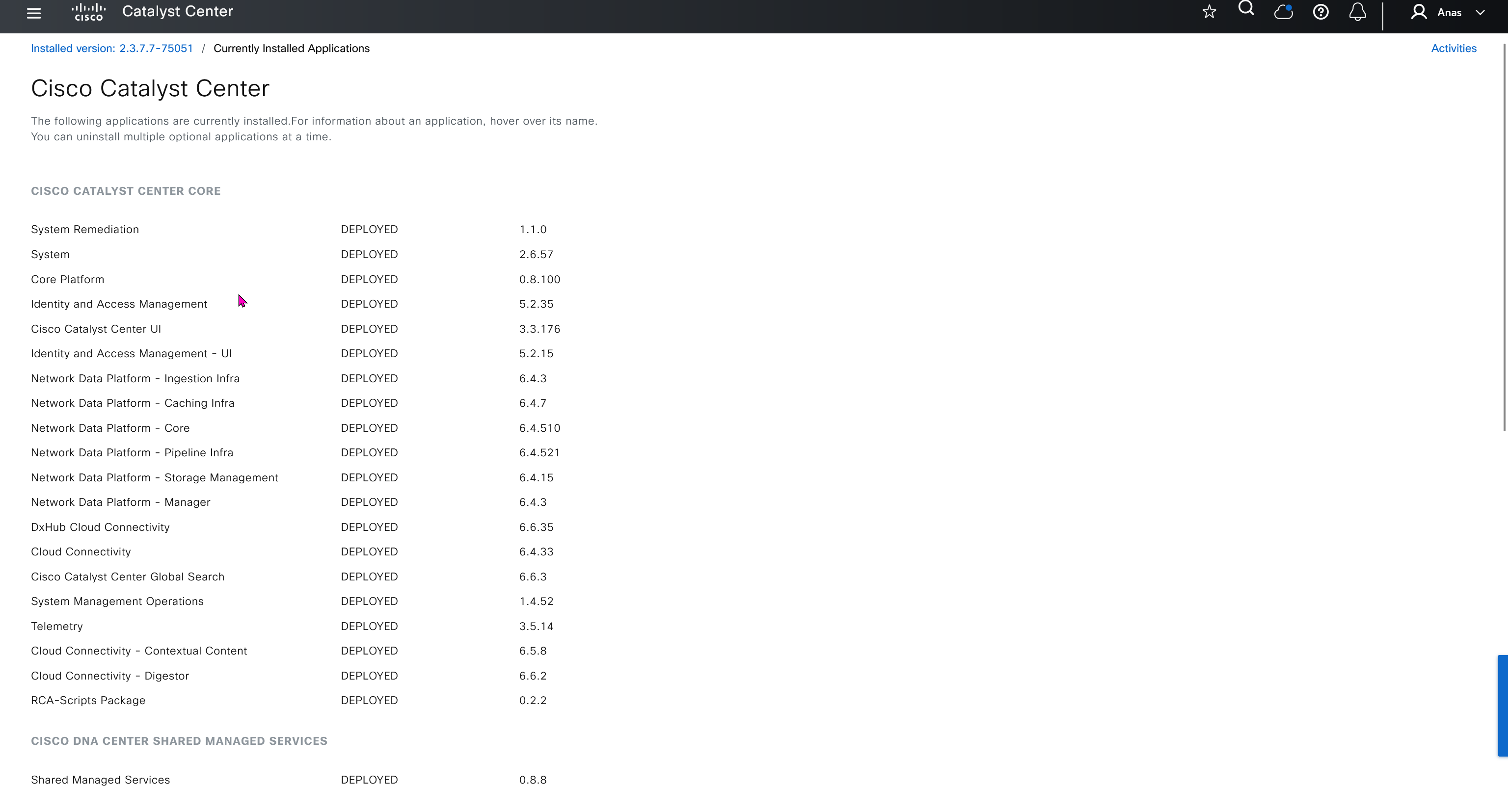
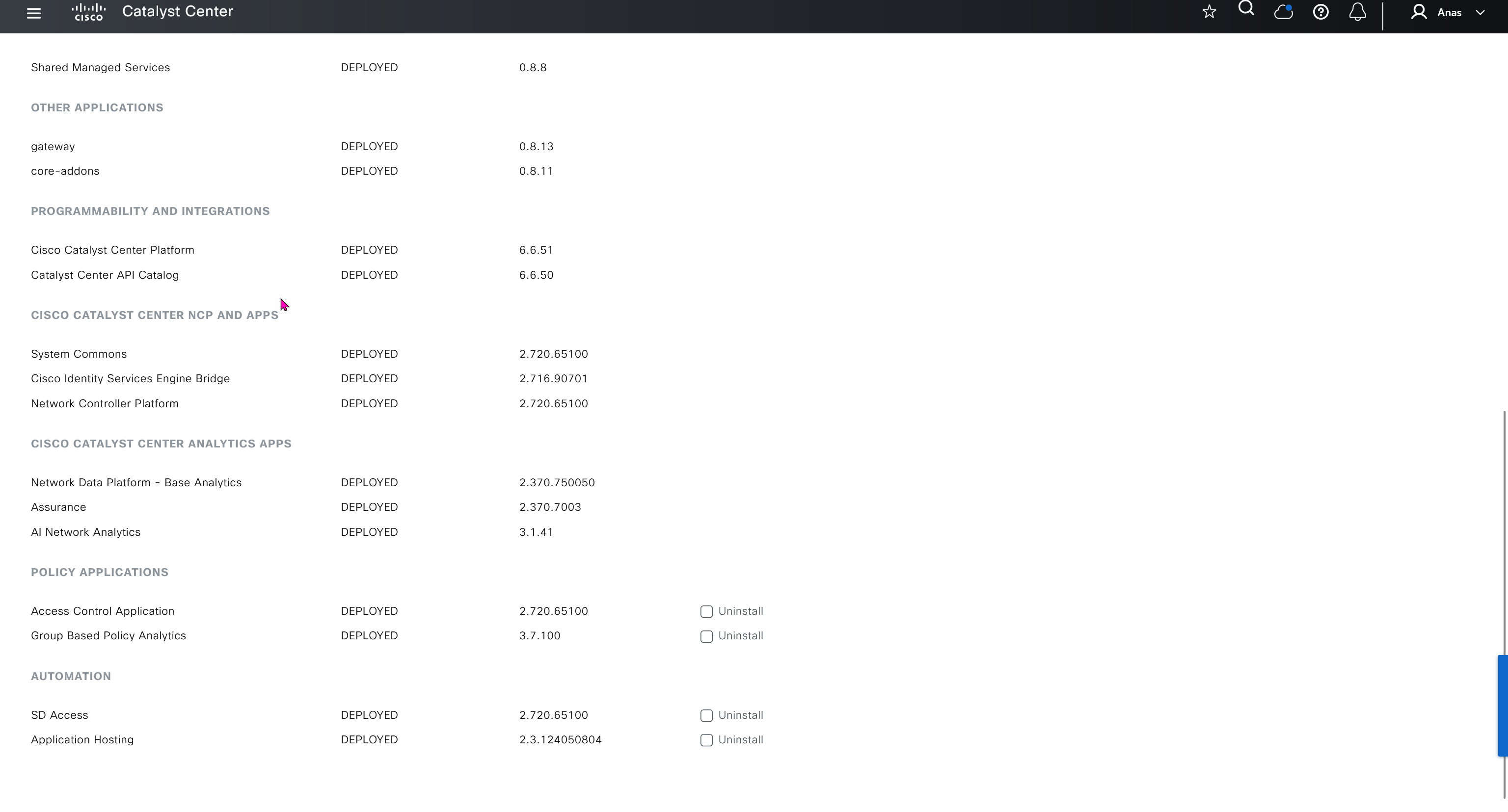
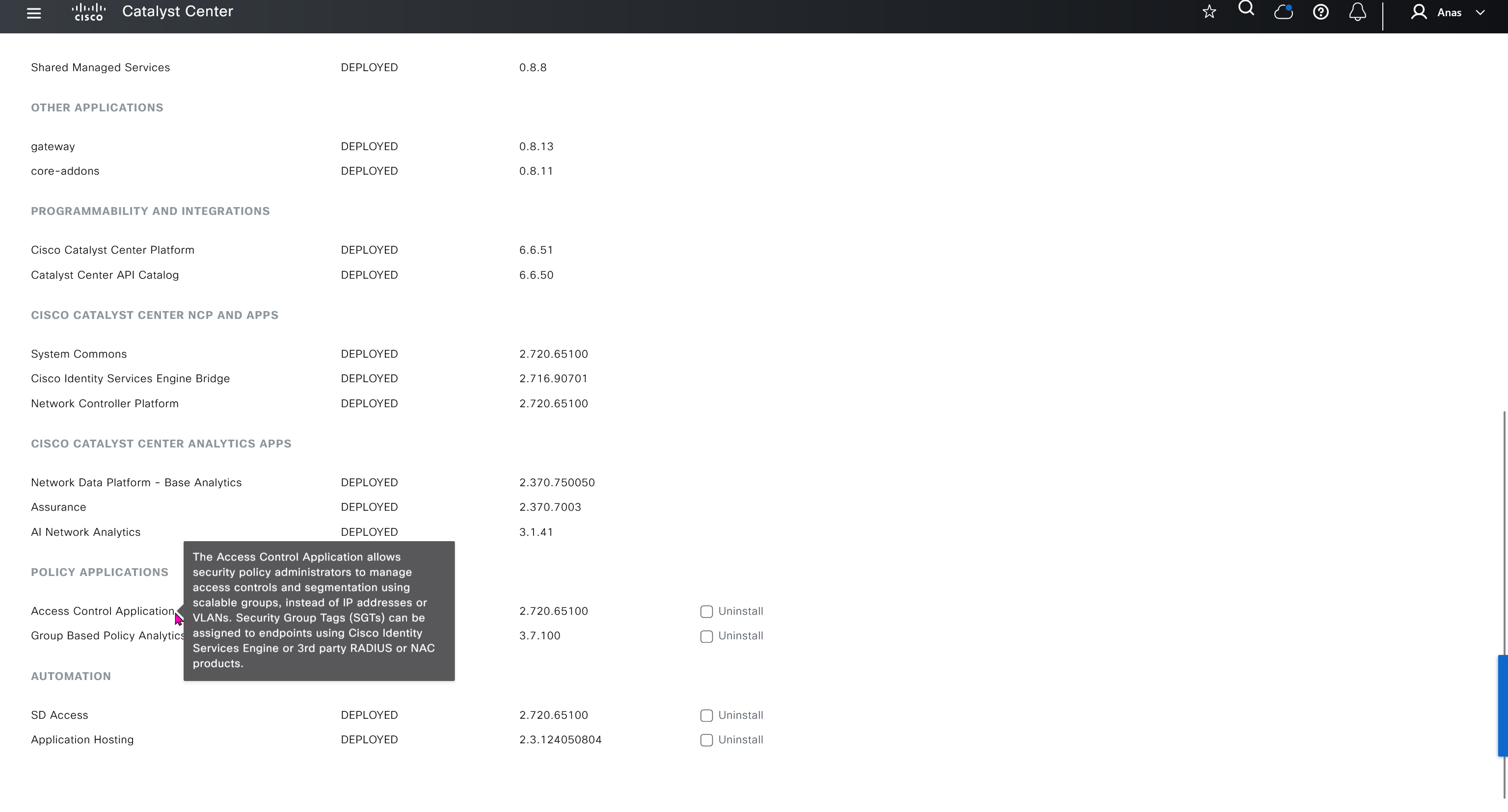
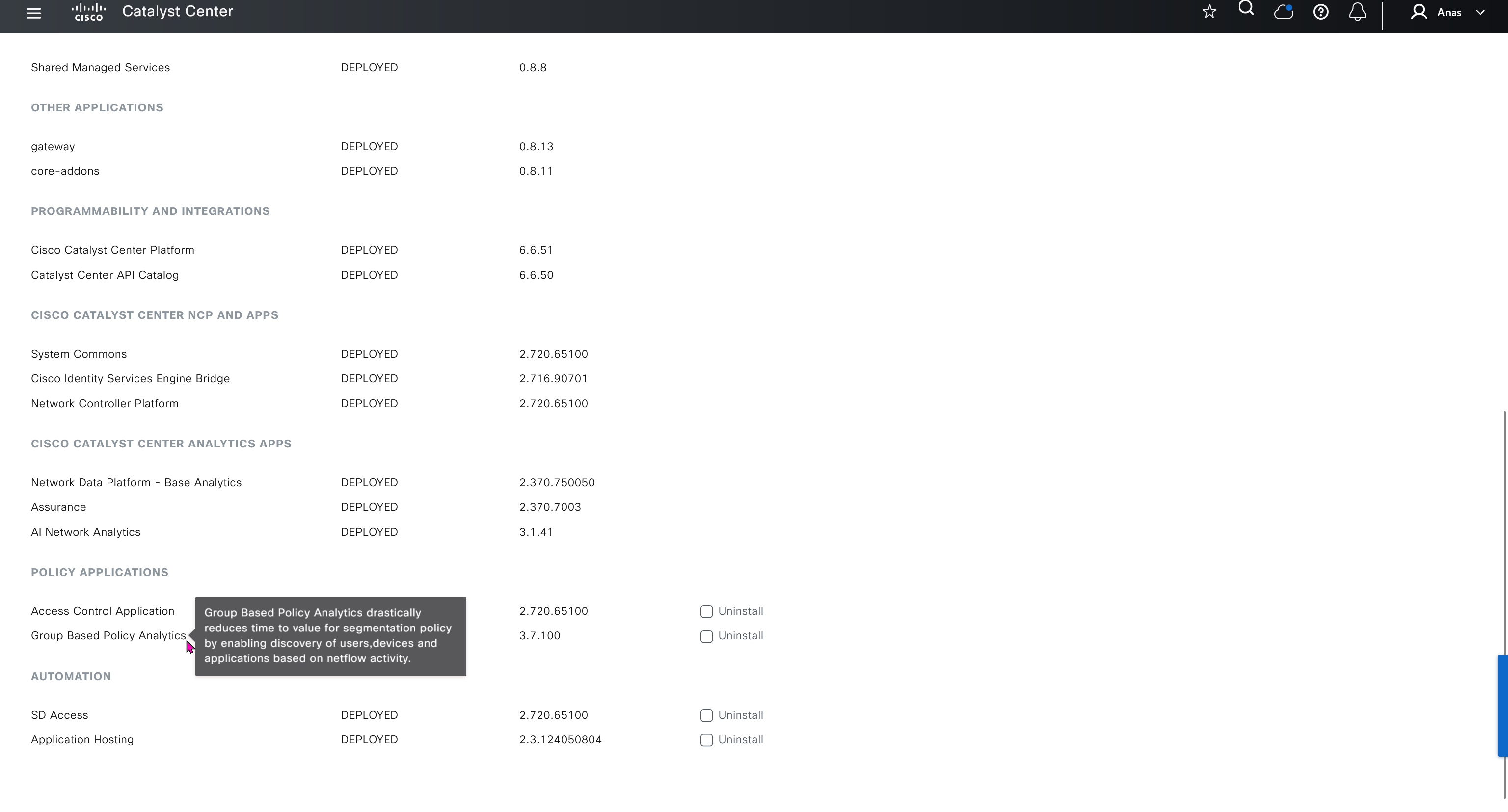


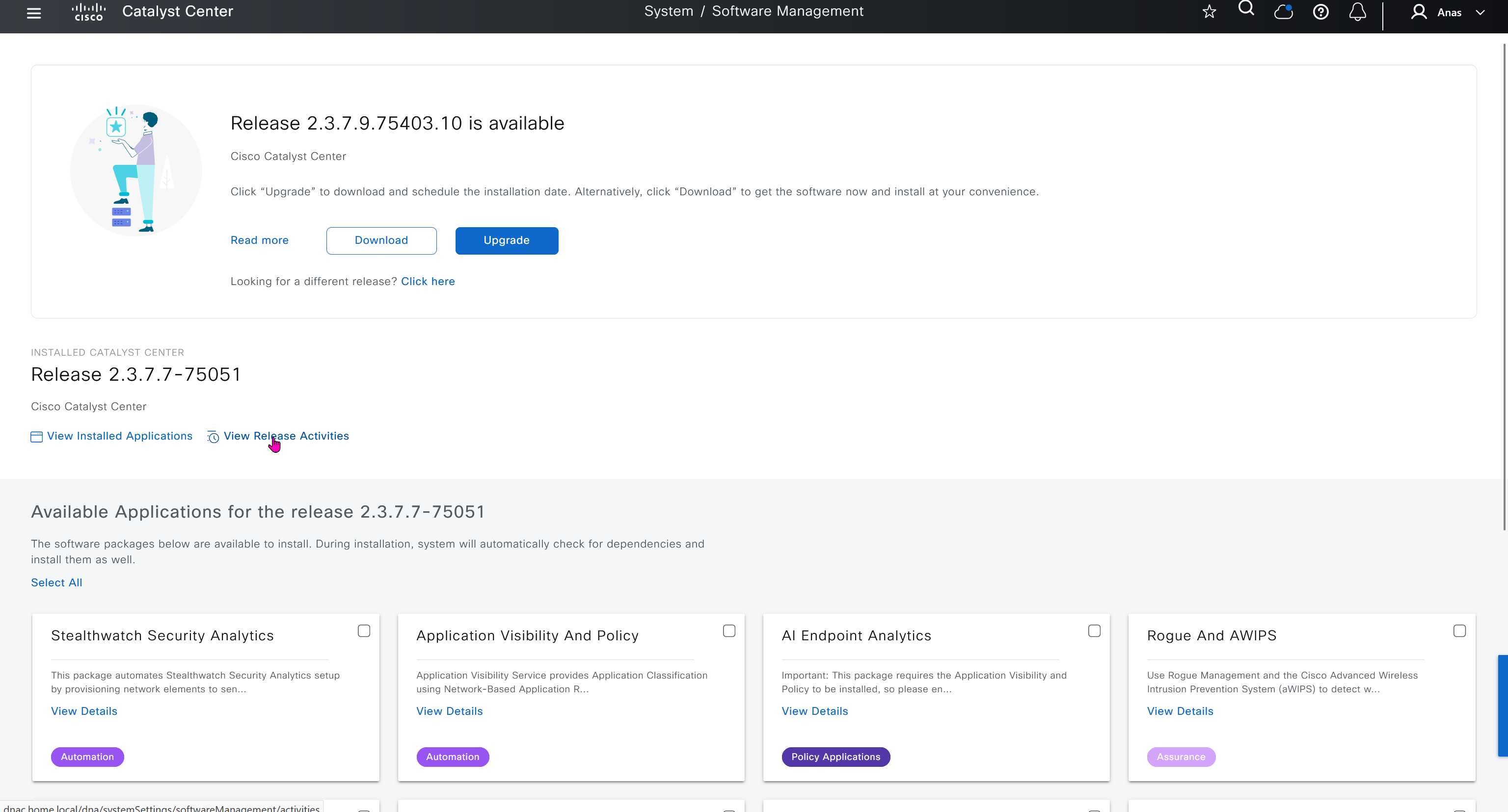
Cisco.com Credentials
Cisco credentials is the same credentials we entered after changing password for DNAC admin on first time login
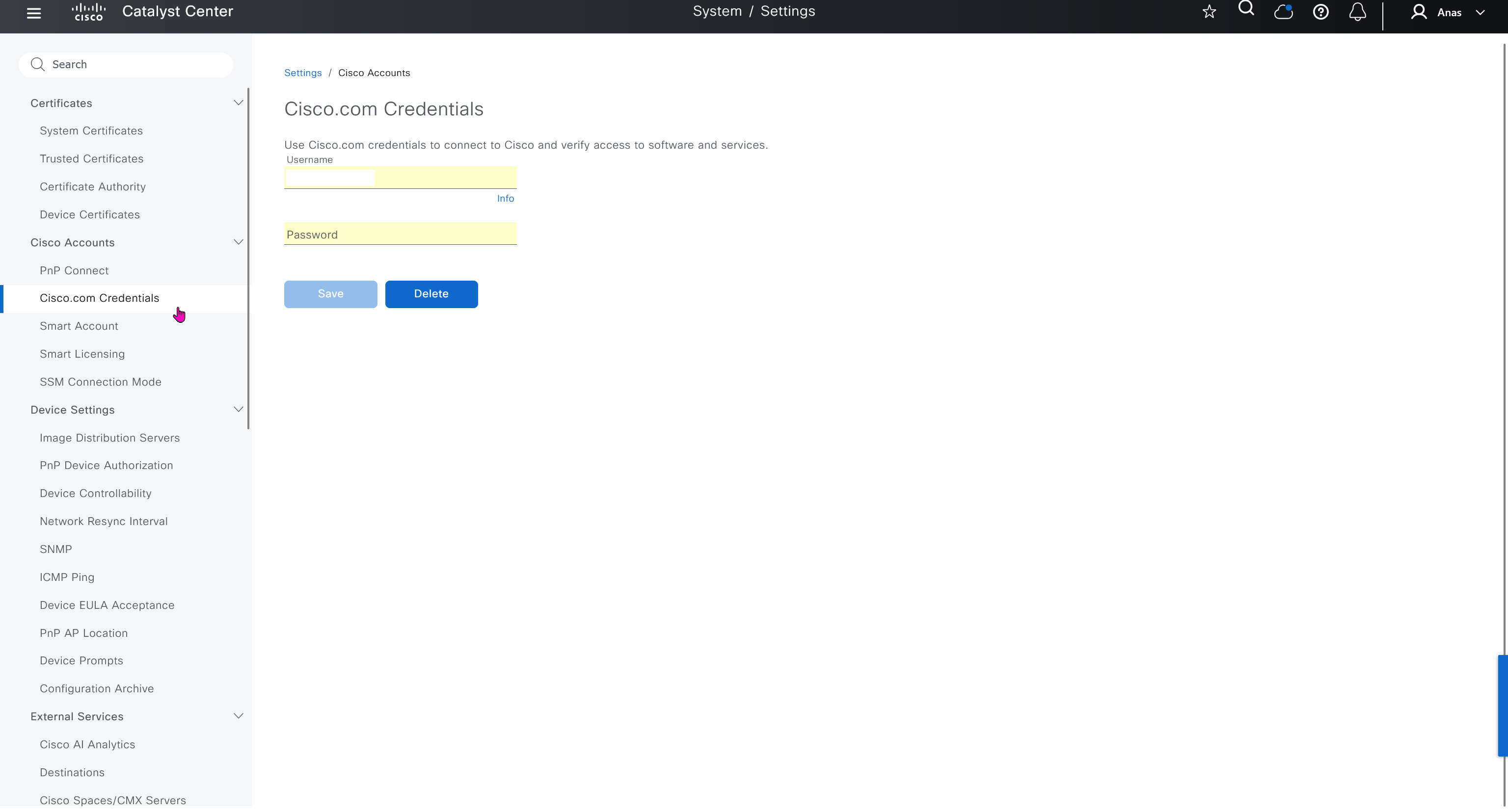
PnP Connect
PnP connect lets you sync your devices from internet based Cisco’s PnP to DNAC directly, this is used for onboarding routers and switches using PnP in Cloud
Cisco Plug and Play (PnP) Connect is a cloud-based onboarding service that helps you automatically provision new Cisco network devices (switches, routers, access points, etc.) with Cisco DNA Center — no manual configuration or console access needed similar to SDWAN or Meraki onboarding
When a new Cisco device boots up:
- It connects to the PnP Cloud portal.
- The PnP Cloud checks the device’s serial number.
- The device is matched to your DNA Center project.
- The device is redirected to your DNA Center for zero-touch provisioning.
Smart account
“Auto register smart license enabled devices” allows devices to register to selectable “Virtual account inside the Smart account”

Smart Licensing
Smart account defined earlier is used in Smart licensing section, register a smart account and virtual account to have DNAC licensed and in compliance state
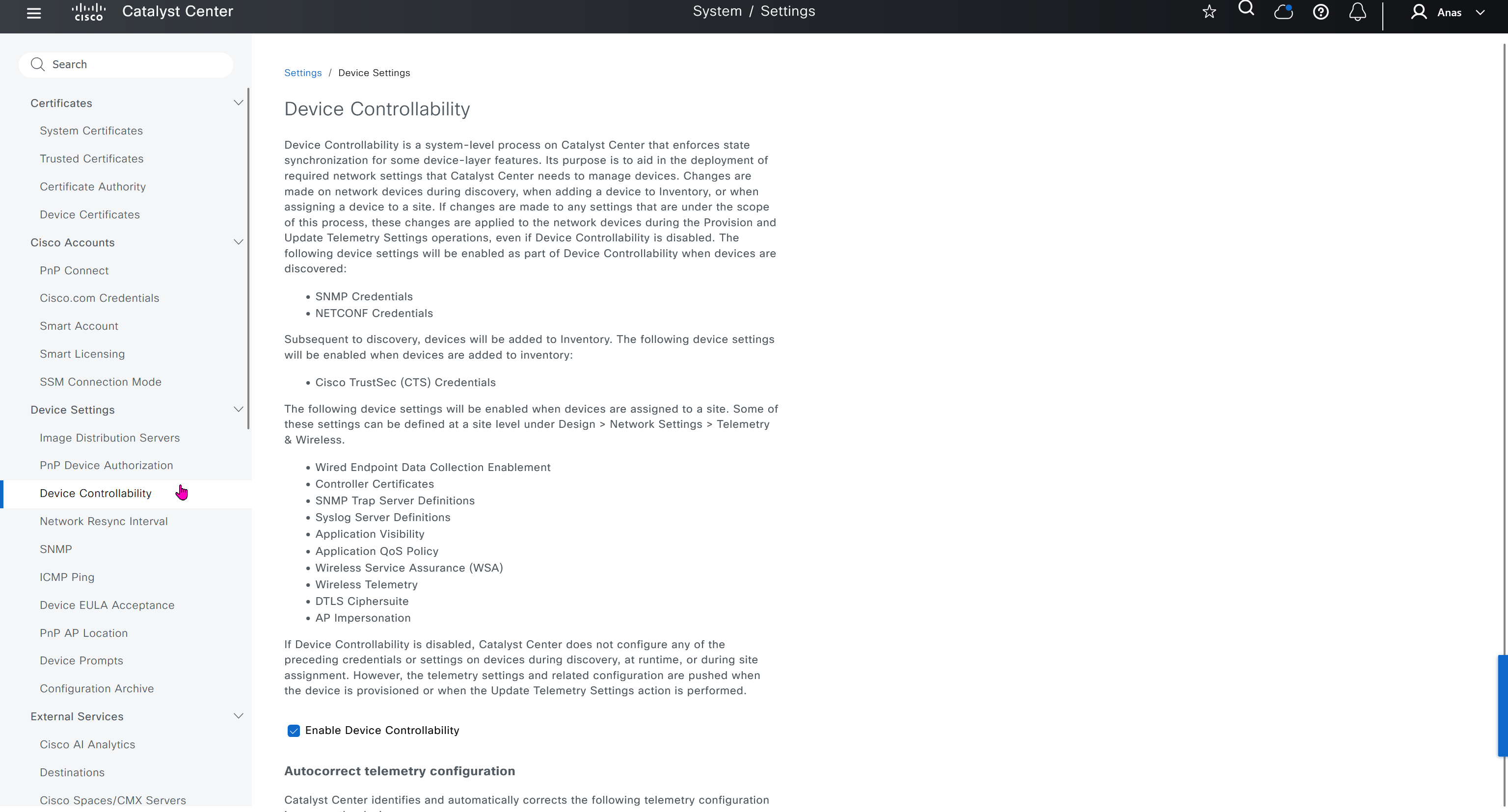
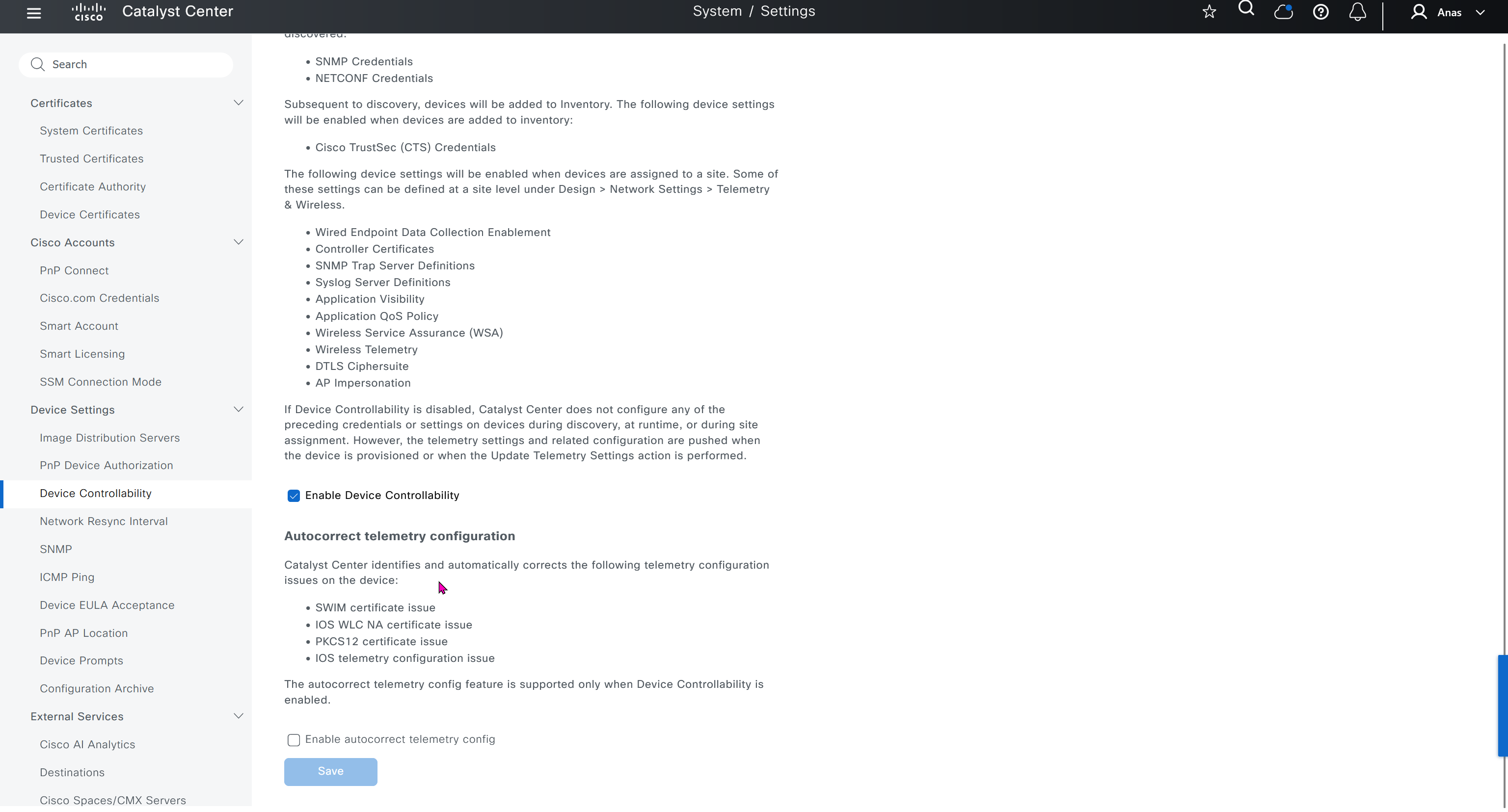
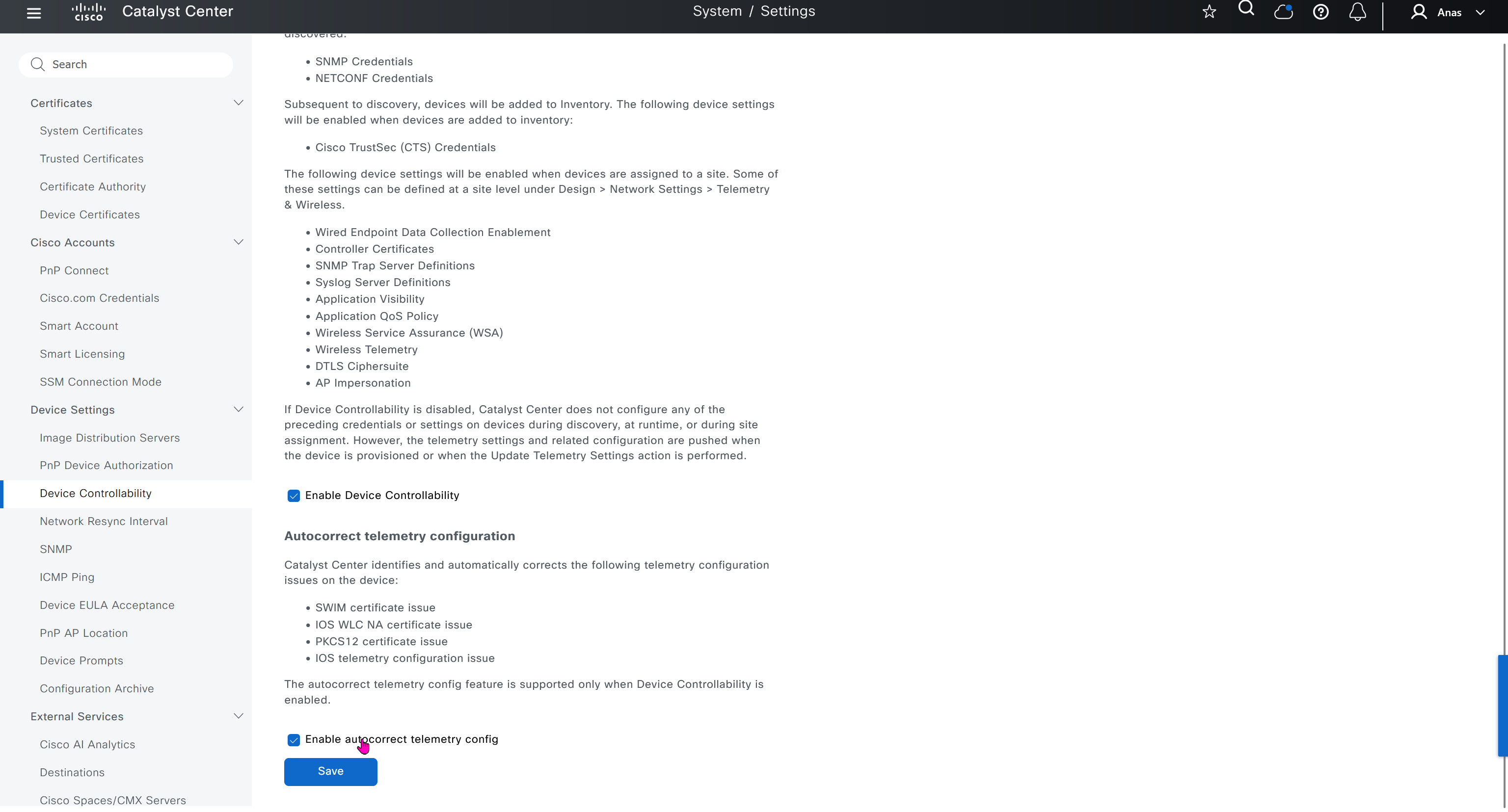
Device EULA Acceptance
For LAB I will not accept as not sure what might be the impact on CCO account against licenses
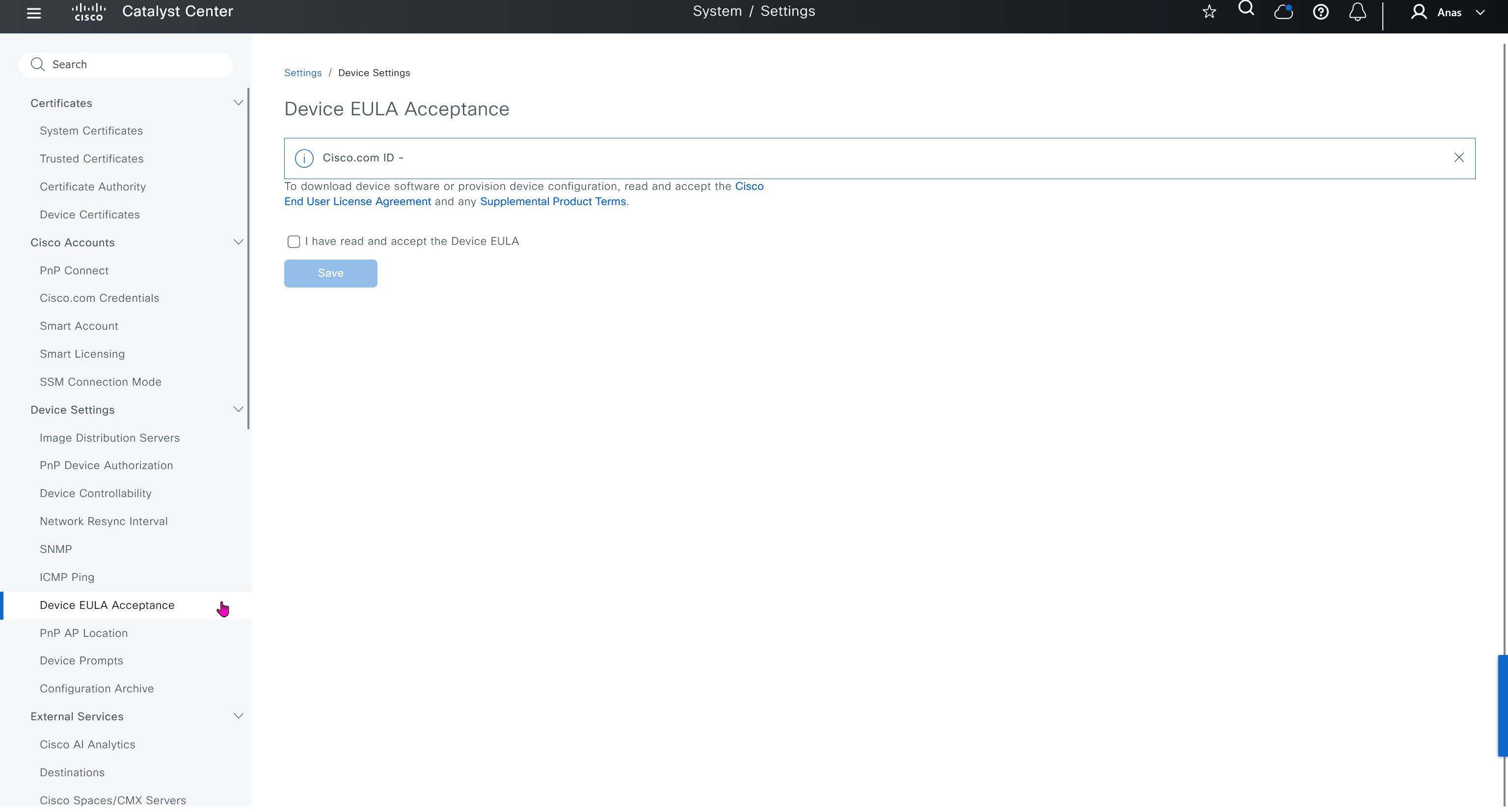
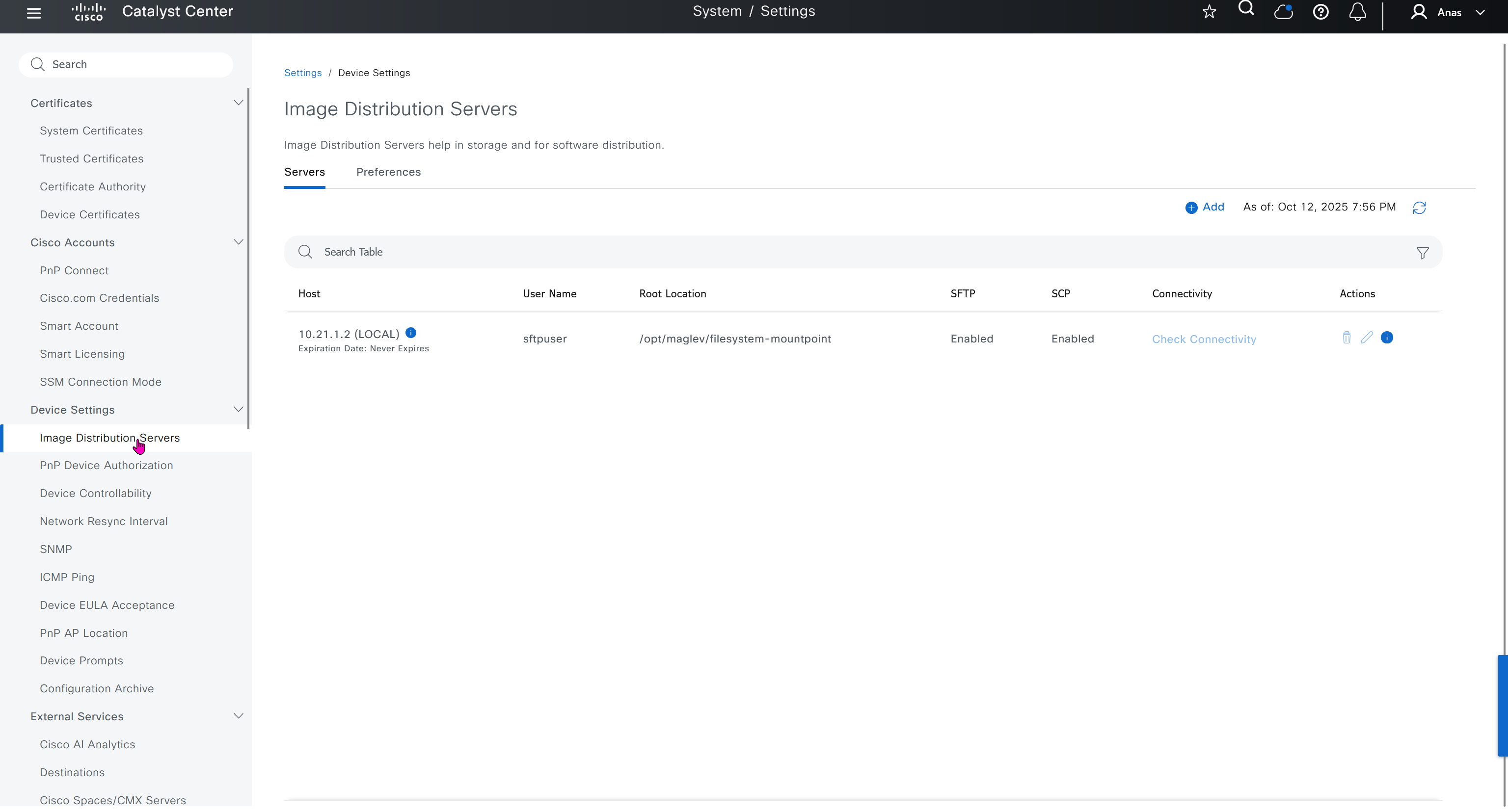
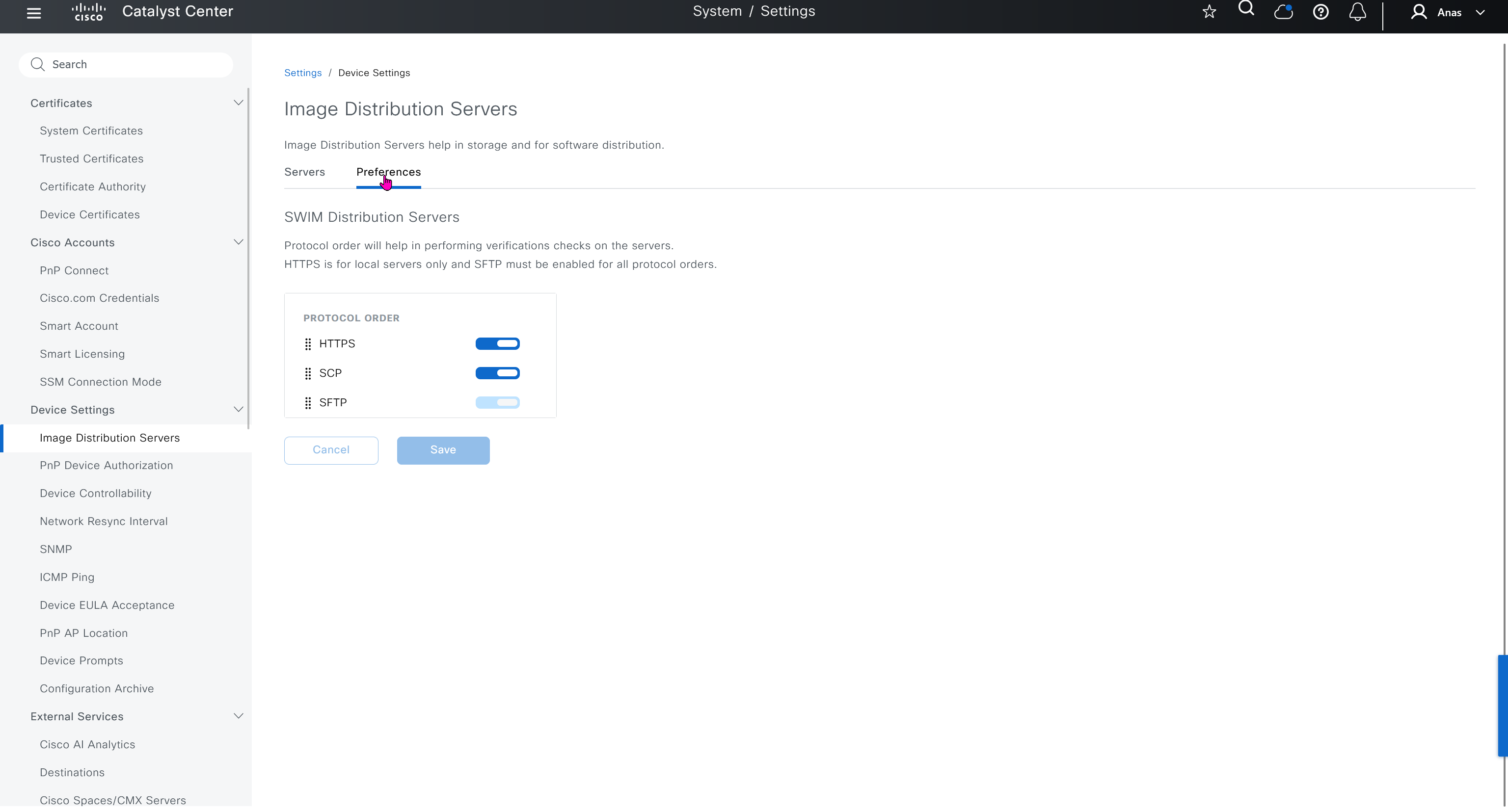
Image Distribution Servers
10.21.1.2 (LOCAL) is DNAC itself, but we can define other image distribution servers not to burden the WAN
Network Resync Interval
This is how often DNAC syncs with network devices, default is 24 hours

SNMP
is timeouts and retires

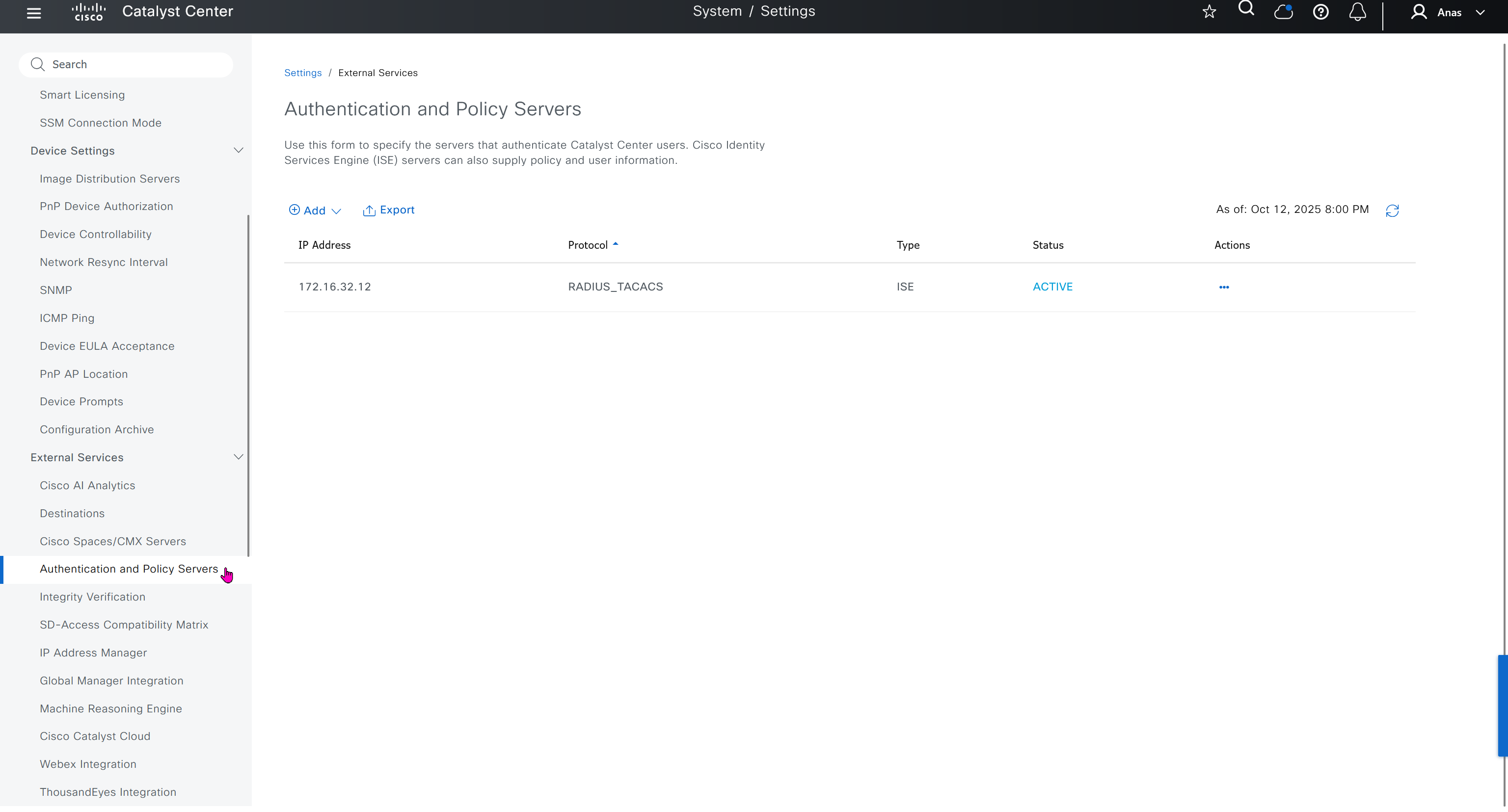
Authentication and Policy Servers
defined ISE servers
Cisco AI Analytics
This is where you configure AI analytics
Destinations
This is to deliver event notifications when events happen on DNAC
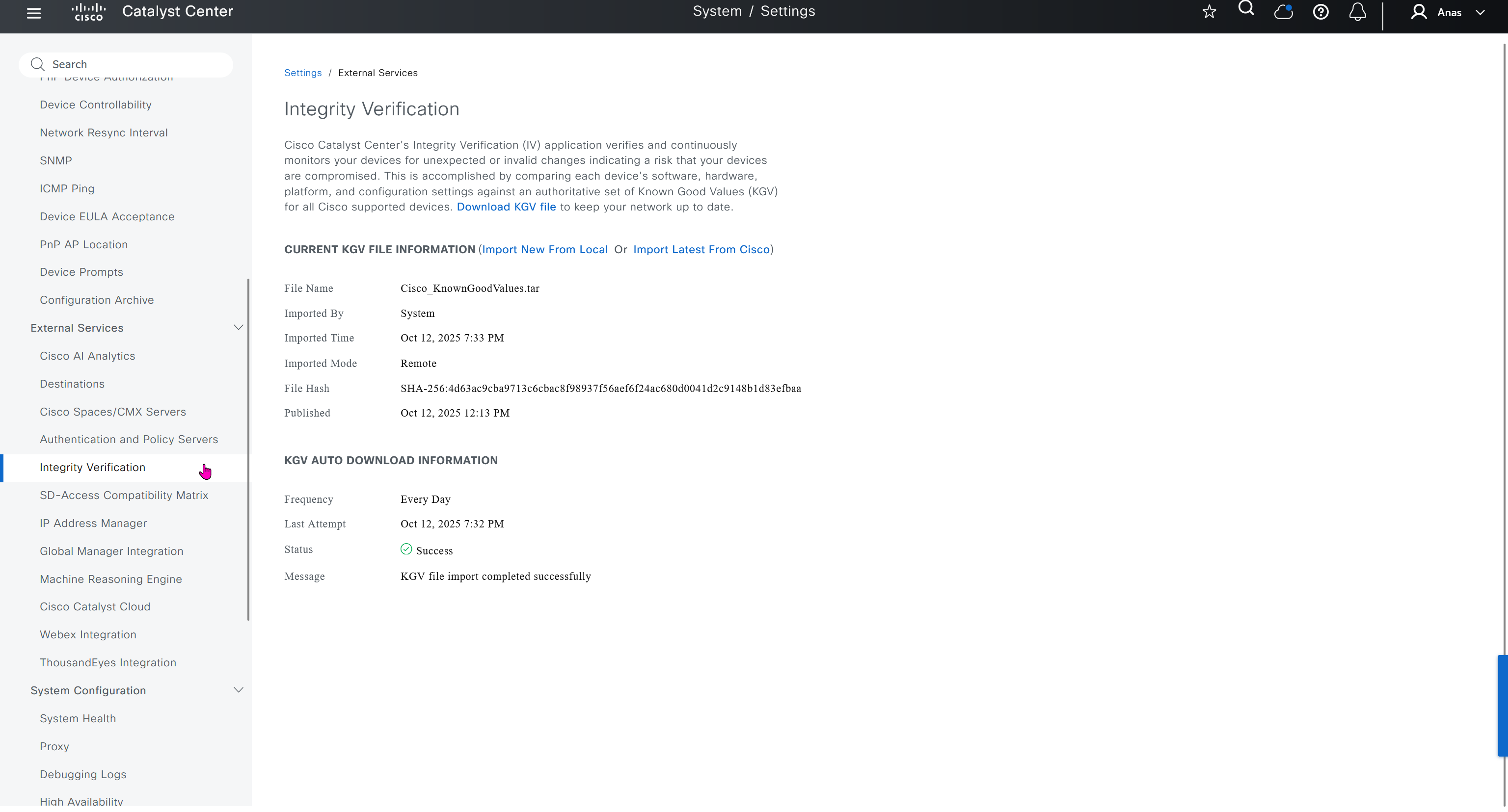
Integrity Verification
Checks if device is compromised on software, hardware level using Known Good Values KGV file from Cisco, which also requires updates from Cisco
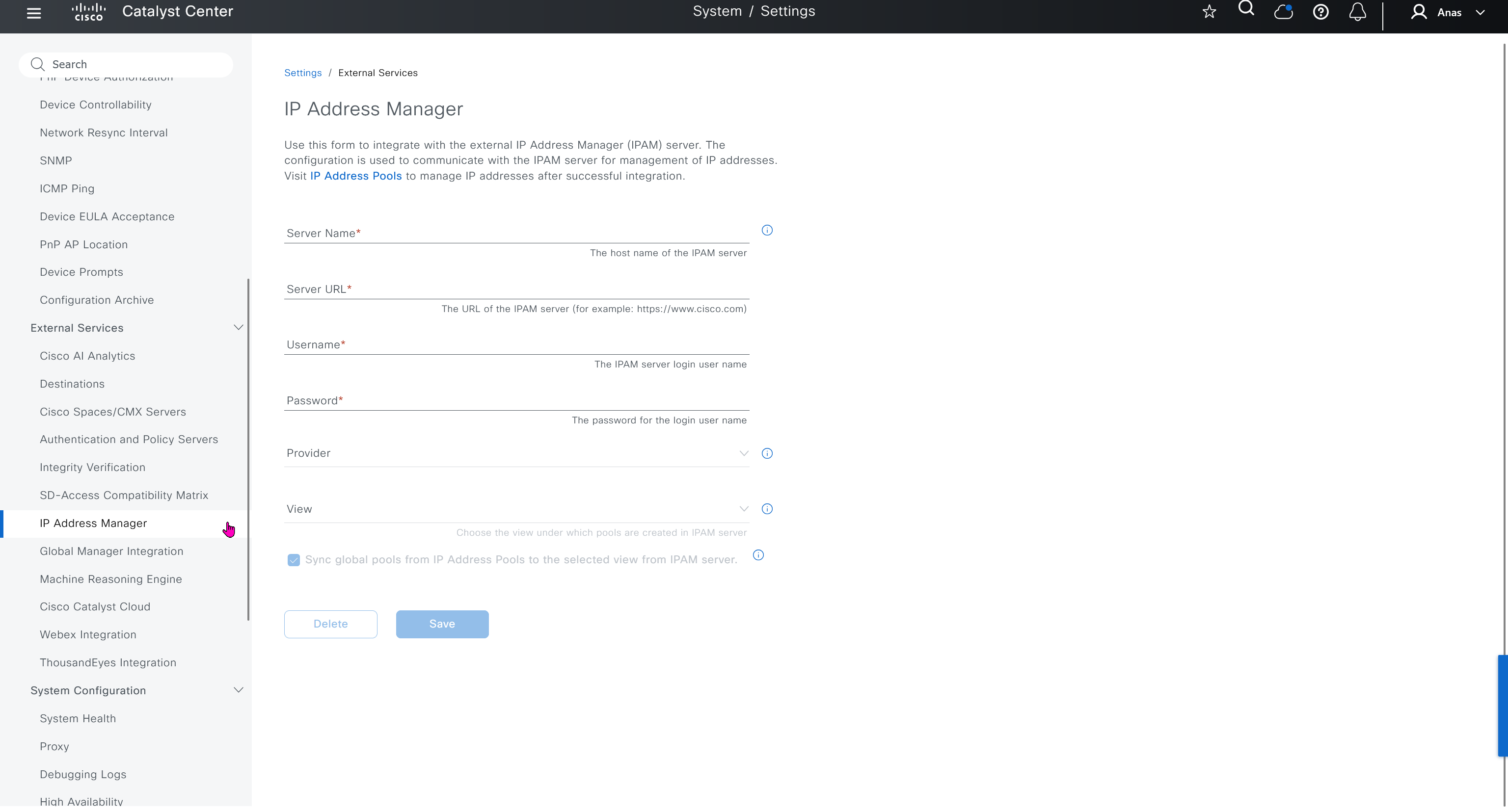
IP Address Manager
This is integration with IPAM
Machine Reasoning Engine
Download and keep upto date Cisco’s latest machine learned troubleshooting and reasoning database, make sure it is set to auto update


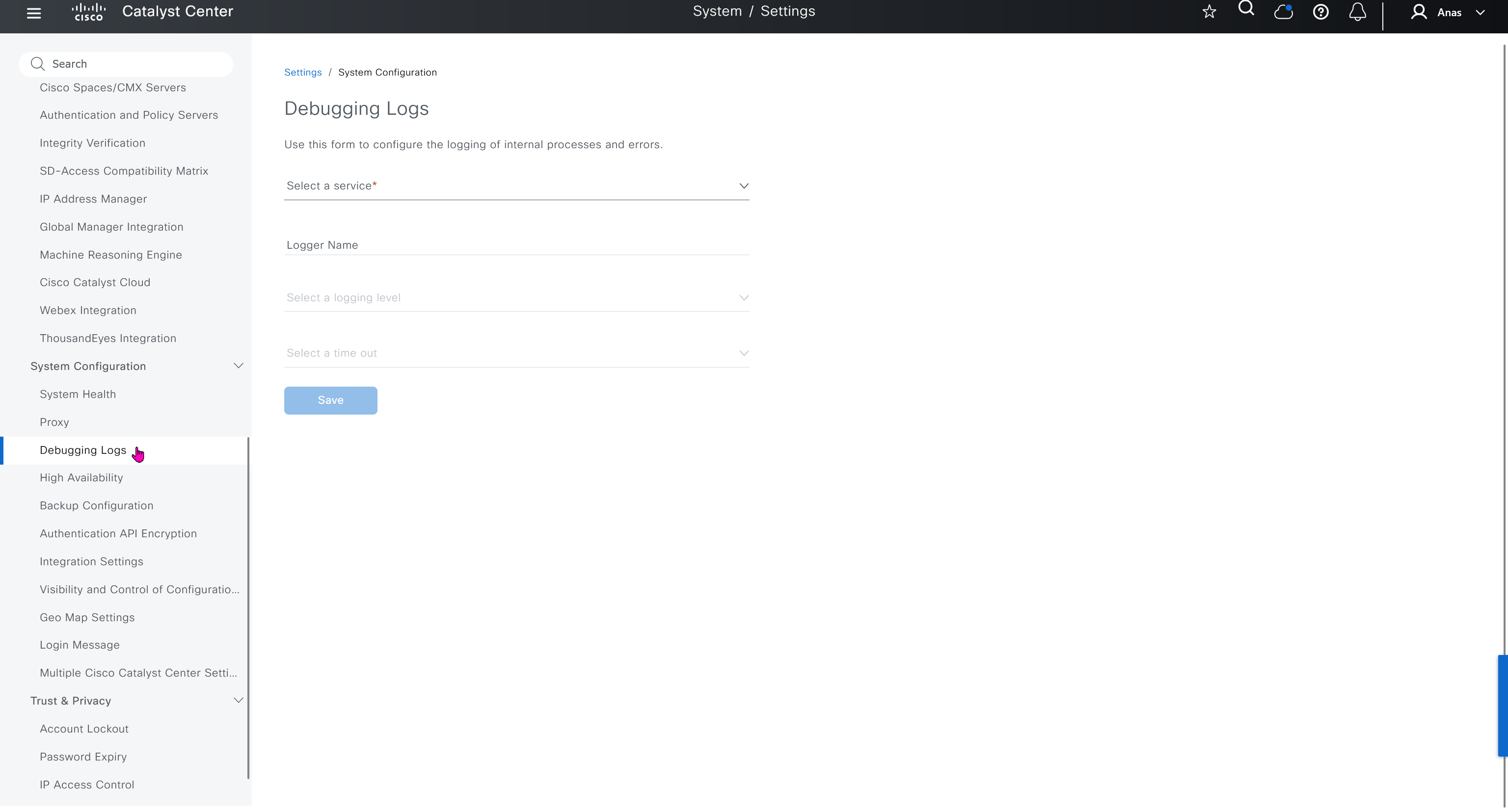
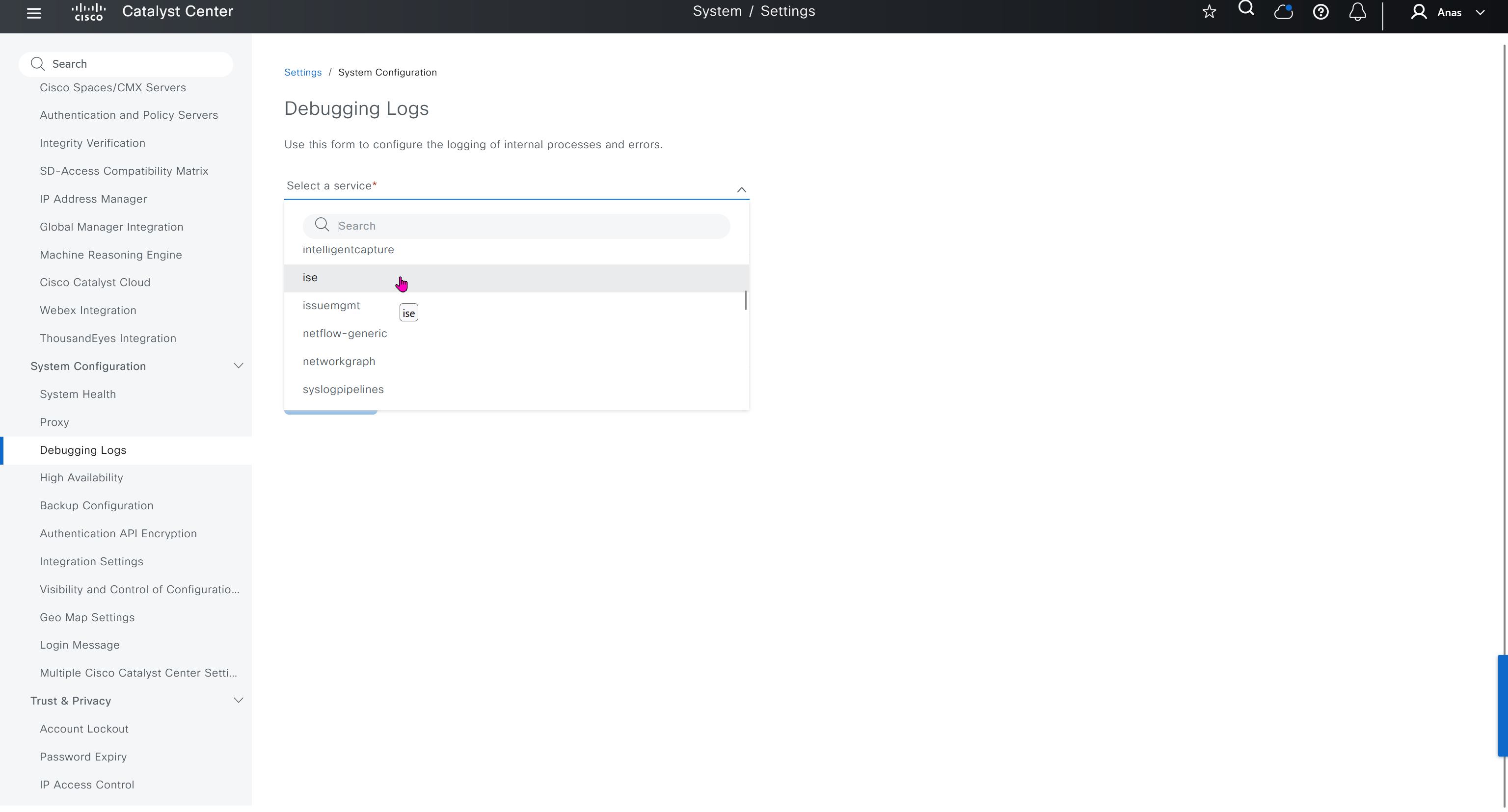
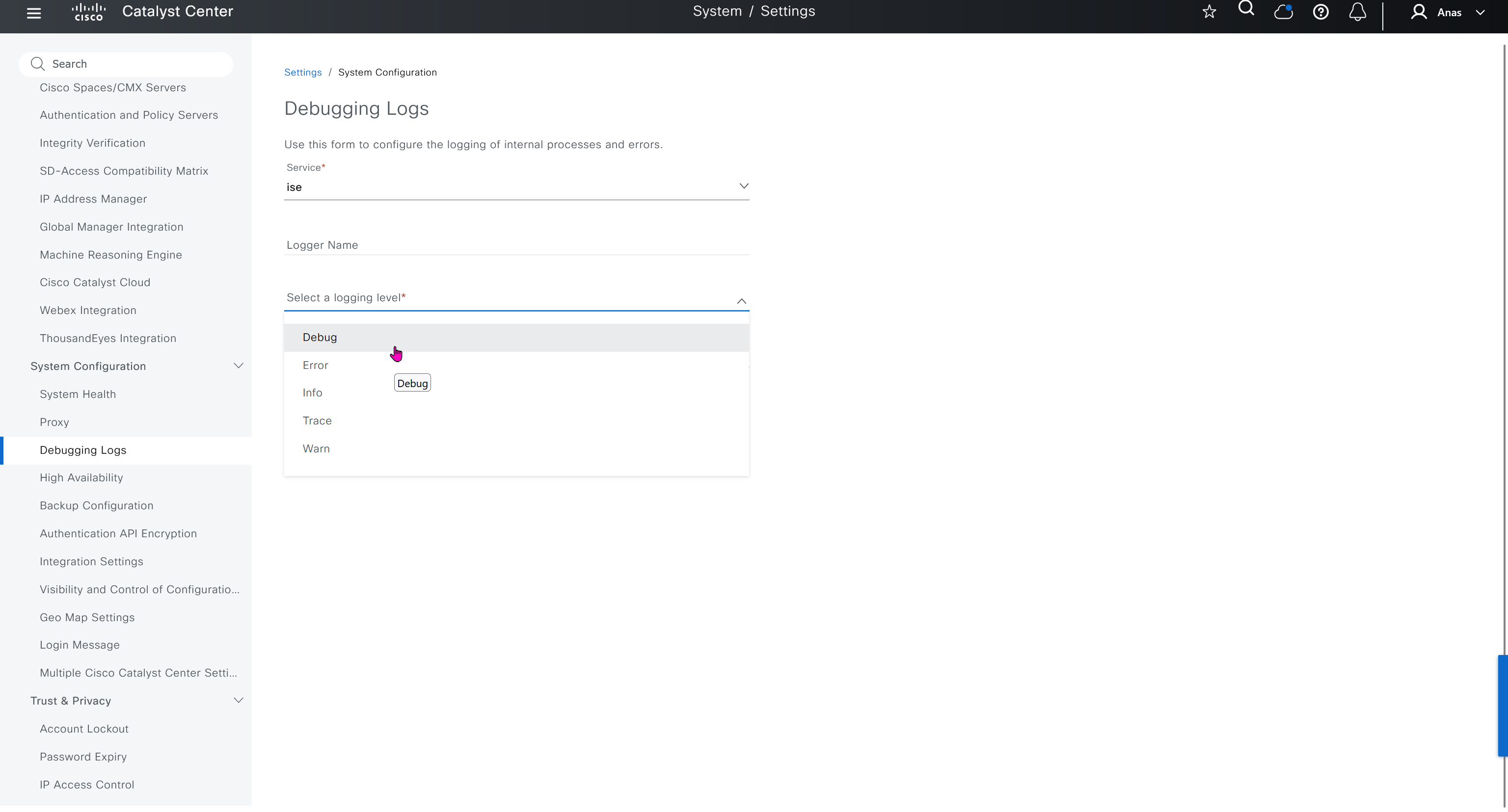
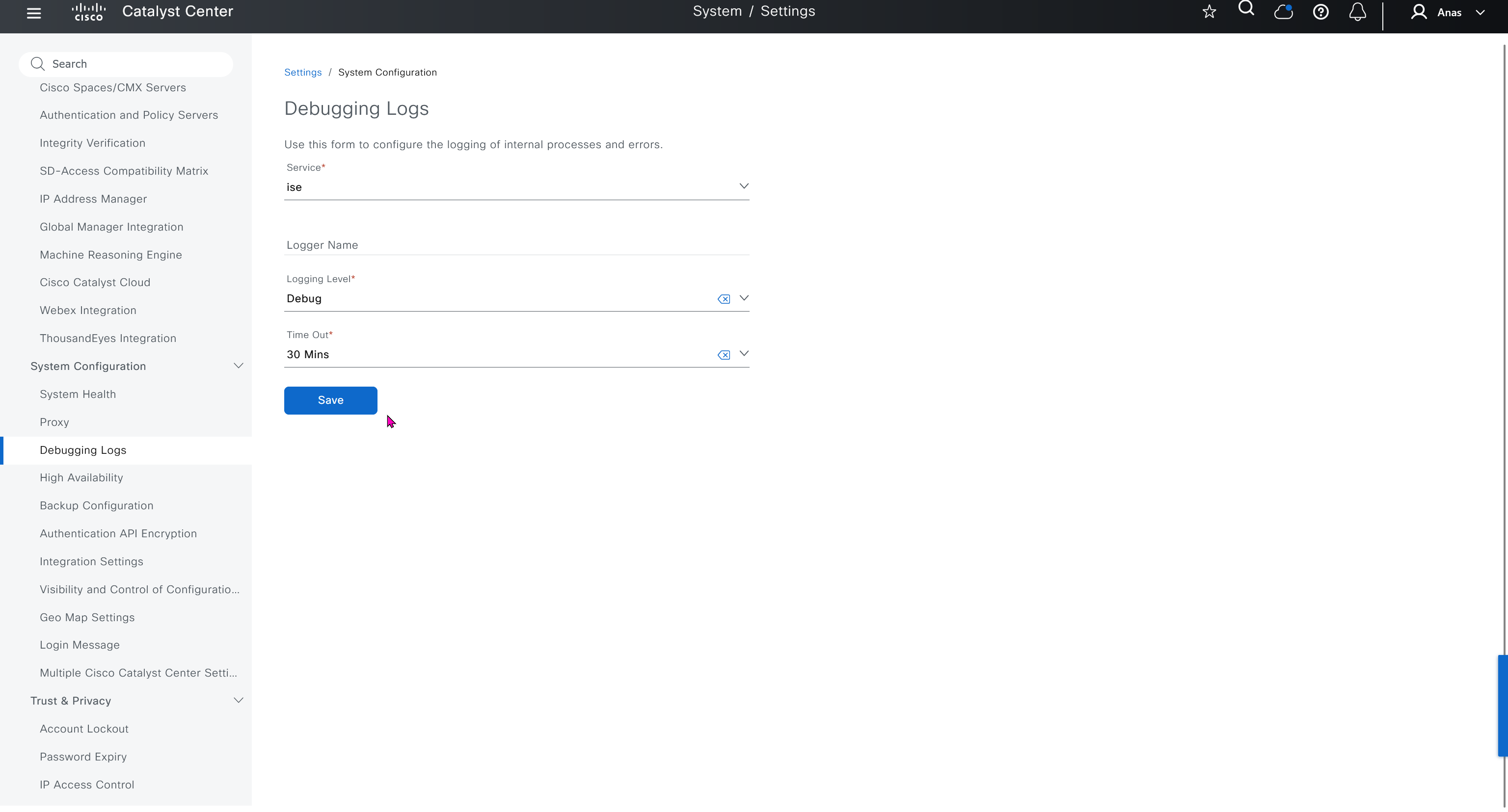
Debugging Logs
This is to debug logs for DNAC itself, specify a syslog server


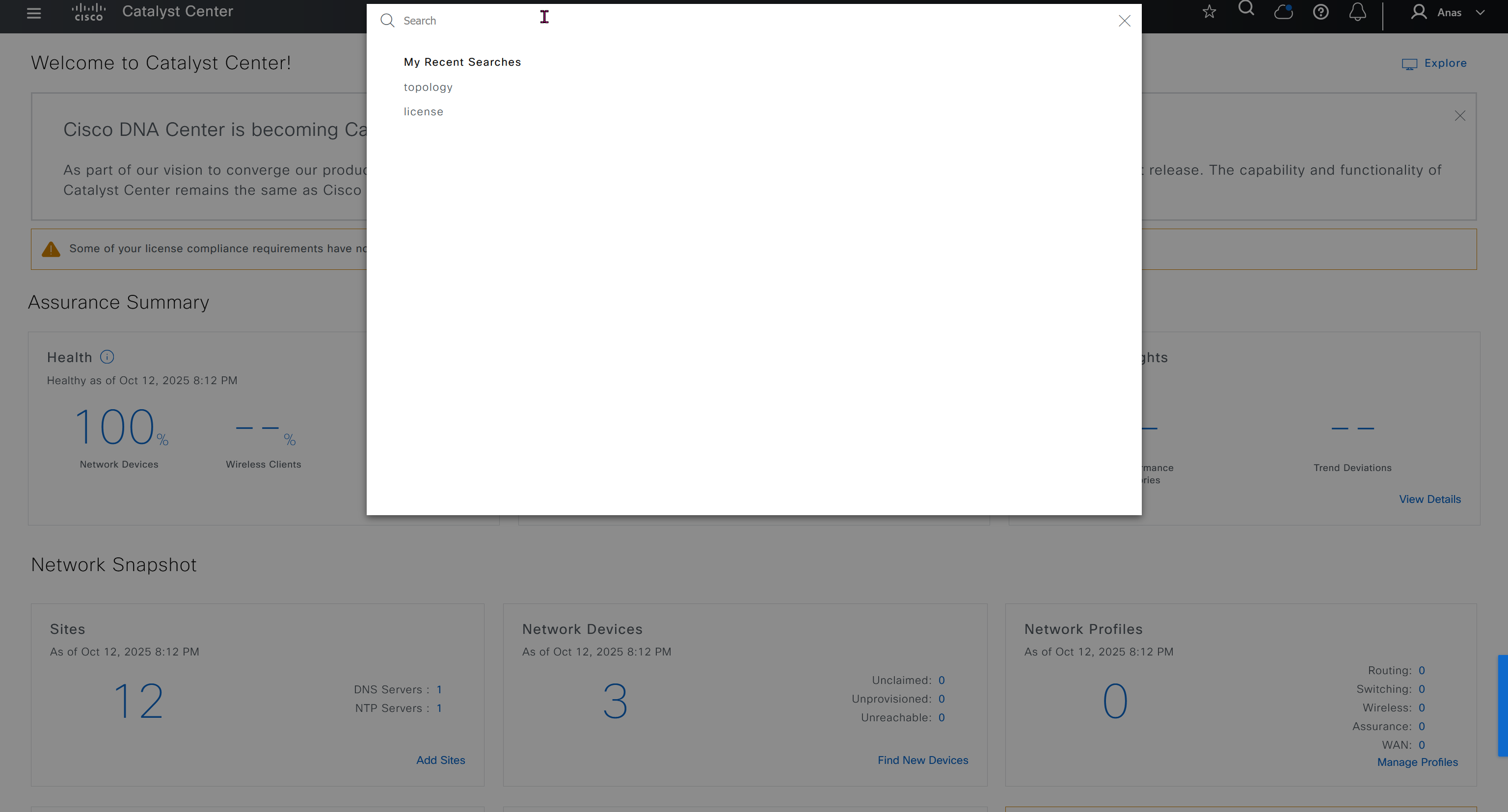
Search
Search in DNAC is amazing and you can search clients by MAC address or IP address / track clients with Client 360 link in search result and even search IP pools
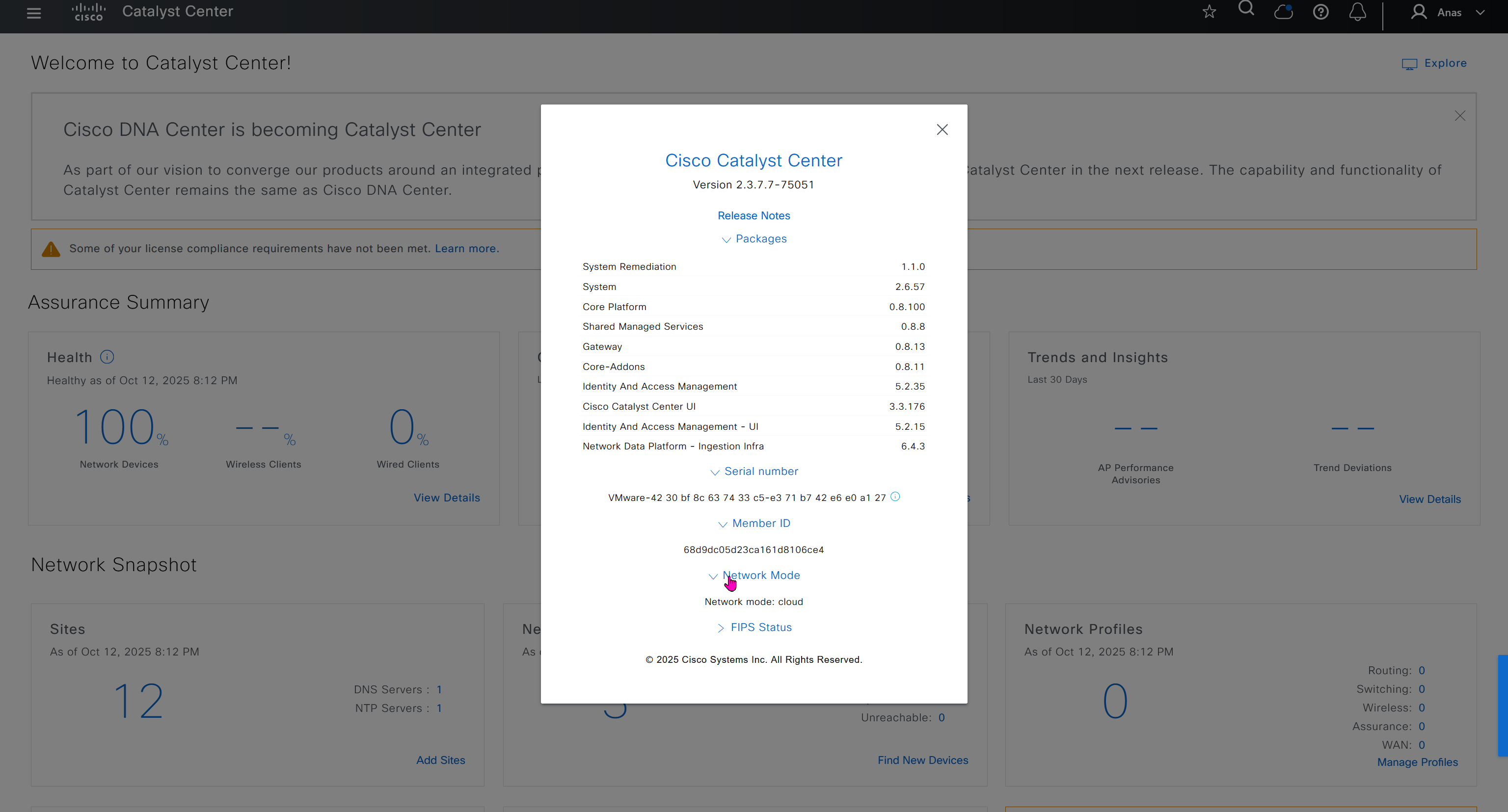
API Reference
This comes handy when you are working with API
next post
Enable logging of commands by DNAC
Configuration
conf t
!
! Enable the archive feature
archive
log config
logging enable
notify syslog contenttype plaintext
hidekeys
!
! Optional: Set up where the archived configs are stored
path flash:config-archive
write-memory
!
end
!
! Ensure syslog logging is enabled (optional but recommended)
conf t
logging buffered 64000
service timestamps log datetime msec
!
end
write mem next post
SD-Access LAN Automation Deployment
LAN Automation Deployment
LAN automation is a network management process that
simplifies underlay deployment
eliminates manual, repetitive network configuration tasks, and
establishes a standard, error-free underlay network.
Cisco LAN automation provides:
Zero-touch provisioning: Network devices are dynamically discovered (CLI controlled), onboarded, and automated from their factory default state to fully integrated and configured state (templates can be configured since CLI controlled) in the network.
Dynamically build end-to-end routing topologies.
Cisco LAN automation enables redundancy and automates best practices to ensure resiliency during planned or unplanned network outages.
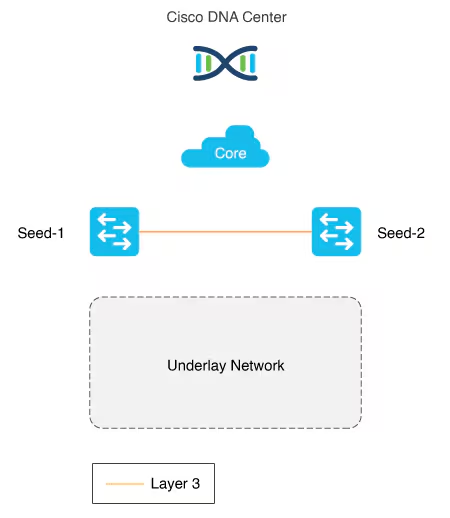
Seed device
Pre-deployed device and initial point through which LAN automation discovers and onboards new switches downstream
The seed device can run technologies such as Plug and Play (PnP) and zero-touch provisioning or configured manually.
Device discovery happens only on the primary seed device interfaces. One seed device can do the job but two can be deployed
PnP agent
The PnP agent is a Cisco Catalyst switch with factory default settings
The switch uses 0 day communication to communicate with Catalyst Center (PnP server)
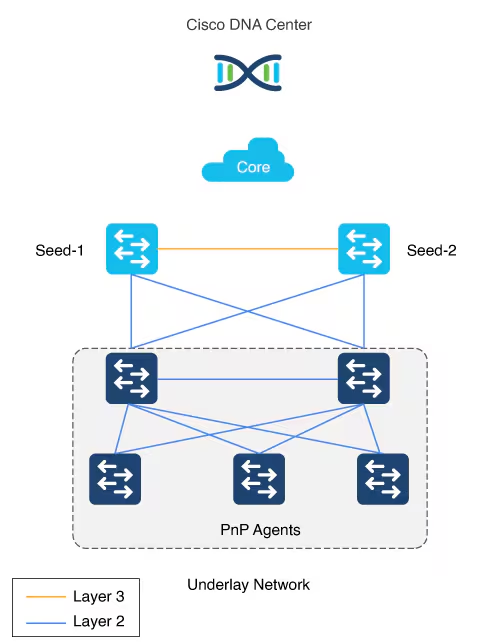
LAN automation in Catalyst Center supports a maximum of two hops from the initial automation boundary point device. Any additional network devices beyond two hops might be discovered but cannot be automated, Given that seed devices are core switches from the three tier model:
- Scenario 1: You have a three-tier network and you want to LAN “automate distribution and access layer switches”, both distribution- and access-layer switches will be discovered and LAN automated.
- Scenario 2: You have a three-tier network and you want to LAN automate distribution and access-layer switches. You already LAN automated the distribution layer. Later, you add access-layer switches to your network and you want to LAN automate these switches. “Because the distribution switches are already LAN automated and links converted to Layer 3, Tier 1 or core switches cannot be used as the seed. You must choose distribution as the seed in this scenario“.
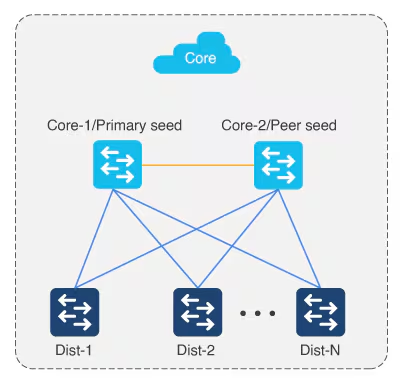
Multistep LAN automation for large topologies: First pass
Large topologies are brought up by performing LAN automation multiple times. During the first pass, core devices are chosen as seed devices to bring up the “distribution” switches as new devices.
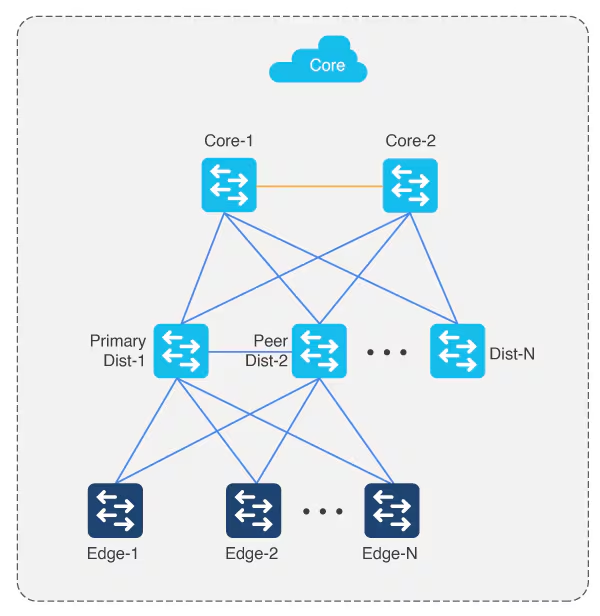
Multistep LAN automation for large topologies: Second pass with first group
During the second pass, two of the distribution switches act as seed devices to bring up the edge devices as new devices. All new devices in this session must connect directly to the two distribution switches that act as new seed devices. Repeat this process for the remaining set of distribution switches, two at a time (in pair).
Connect uplinks from edges to the primary and peer distribution switches only.
Always connect new devices to the primary seed device. Connection to the peer seed device is optional.
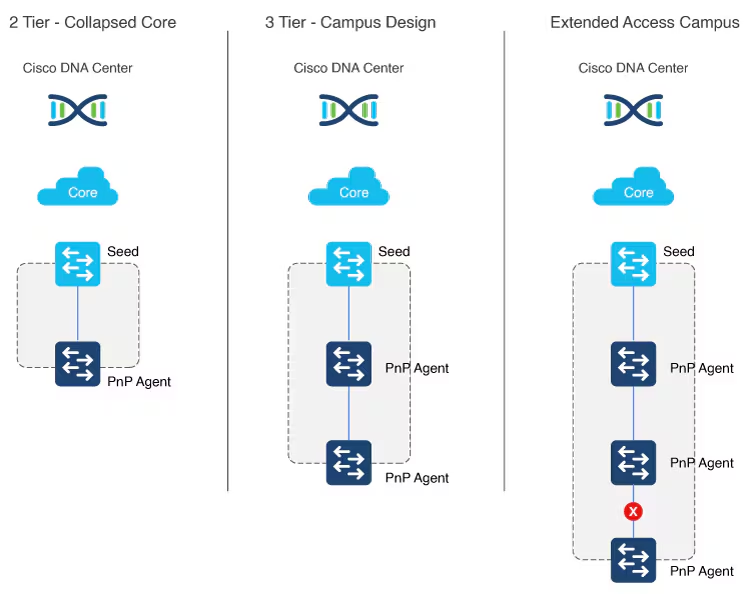
There can be two tiers of devices below the seeds.
Perform stacking before hand
Layer 3 link configuration after LAN Automation
After all devices are added to the Catalyst Center inventory, you can stop the LAN automation session on the GUI to begin the Layer 3 link configuration process.
If you accidentally stop the LAN automation process before all PnP devices are added to the Catalyst Center inventory, You must bring the in-progress devices to the factory-default state in order to do LAN automation again.
Catalyst Center Release 2.3.5 and later provide the support for day-n link configurations (add and delete link). For more information, see Create a link between interfaces.
Supported switches for each role at different layers
Site planning
Use the Catalyst Center Design feature to create the required sites, buildings, and floors.
Create a global pool in DNAC, reserve IP Pool specific per site
Different types of IP address assignments used:
- Temporary DHCP pool assigns IP to factory default pnp agents or new switches
- /31 L3 interswitch links
- Loopback IP
- Underlay multicast IP
Temporary DHCP pool so new device can get IP and speak to DNAC
One part of the IP pool per site, is reserved for a temporary DHCP server,
this DHCP server runs on DNAC itself and seed devices are used as relay to relay DHCP request from PnP agent or new switch without IP towards DNAC,
Temporary DHCP server (running on Catalyst Center) leases IP addresses from this temporary DHCP subpool.
Those IPs allow the new device to:
- Boot up with a valid IP address.
- Contact Catalyst Center over the network.
- Be discovered and provisioned automatically
Once the LAN automation session is finished:
- The DHCP service stops.
- The temporary subpool is released.
- All those IP addresses go back to the main LAN pool.
- The switches now have permanent IPs assigned by the automation process (usually from a different IP pool).
The size of this pool depends on the size of the parent LAN pool. For example, if the parent pool is 192.168.10.0/”24″, a /”26″ subpool is allocated for the DHCP server, Therefore, a /”24″ pool reserves /”26″ 64 hosts so we can think of this temporary DHCP pool size with the -2 rule
A /23 pool reserves /”25″ 128 hosts, a /22 pool reserves /24 256 hosts, and larger pools reserve (max) 512 IP addresses for the DHCP server, it steps up in this way and max pool size is 512 addresses for even bigger parent pools
for example initial blocks of 192.168.10.0/24 can be used since site is not operational and LAN automation is being run to deploy the site, once LAN automation is complete these chunks are released back in order for them to be reserved in site and used
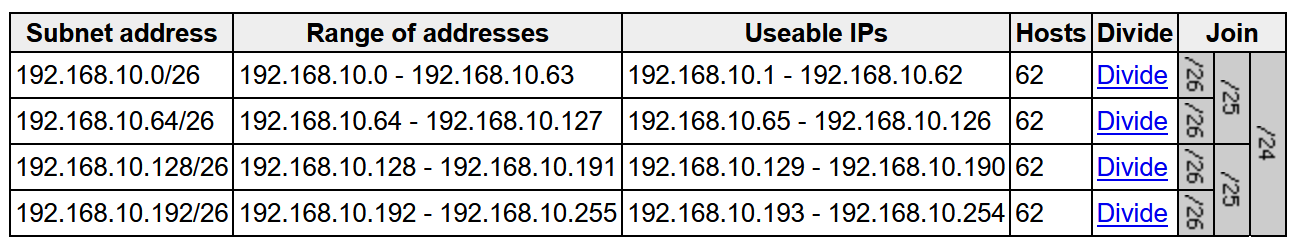
To start LAN automation, the pool size must be atleast /25, which reserves a /27 pool or 32 IP addresses for the DHCP pool.
This IP pool is reserved temporarily for the duration of the LAN automation discovery session. After the LAN automation discovery session completes, the DHCP pool is released, and the IPs are returned to the LAN pool
IP pool for loopback and /31 interswitch links
Another part of the IP pool is reserved internally with a subpool of fixed size /27. This subpool is for allocating single IPs for Loopback0 and Loopback60000 always. Also, two consecutive IPs for point-to-point L3 /31 links are allocated from this subpool also, if this pool is exhausted a new /27 subpool is created for allocating IPs
the subpools remain throughout the process and are not allowed to be removed. Due to this internal subpool allocation logic, the IP pool usage in IPAM counts the subpools as allocated.
When a dedicated (single) IP pool is used to build the underlay networks, each of the devices discovered via LAN automation gets a unique /31 per interface for point-to-point connection, and a unique /32 for Loopback0 and the underlay multicast.
Single Site vs Shared IP pool (overlaps between sites)
When a dedicated (single) IP pool is used to build the underlay networks, each device discovered via LAN automation gets a unique /31 per interface for point-to-point connection, and a unique /32 for Loopback0 and the underlay multicast.
A link overlapping IP pool (only for /31 interswitch links) or shared IP pool is used to optimize the IPv4 addressing in the underlay network by allowing overlapping /31 IP addresses for a multisite deployment. Hosts in different sites can get duplicate IP addresses on the /31 links. The /31s in the underlay are not advertised outside of the fabric site and hence there is no need for them to be unique. However, the /32 loopback needs to be unique to every device, and should be advertised to the global routing table to identify the device in the entire network.
IP pool roles
The LAN IP pool can have these two roles:
- Link Overlapping IP Pool: This pool role is optional for a LAN automation session. If provided, the allocation of IP addresses is only on the /31 point-to-point Layer 3 links, and can be same through out different sites, hence overlapping is in the name.
- Main IP Pool (Principal IP Address Pool in Catalyst Center Release 2.3.5 and later): This pool role is mandatory for every LAN automation session. This is the pool that is used for all management-related IP addressing such as loopbacks, multicast, and DHCP. If the Link Overlapping IP Pool is not provided, then the Main IP Pool is the default fallback pool for the /31 Layer 3 links IP addressing also.

Configuration on seed devices
- Ensure that the system MTU (maximum transmission unit) value is at least 9100 or jumbo frame –
show sys mtu - Turn on IP routing on the seed devices.
- Enable DNA advantage license
- Enable CLI credentials from DNAC
- Enable SNMP strings from DNAC
- Enable ssh
- Enable local authentication
- Enable netconf-yang
- Enable privilege level 15 on vty lines
- ip name-server 172.16.32.11
- ip domain name or2.sys.cisco
IP address allocation in Catalyst Center Release 2.3.7.x and later
In Catalyst Center Release 2.3.7.x and later, IP address allocation from LAN pool is based on IP address range instead of subnet allocation. This approach helps in minimizing the issue of IP address loss during subnet creation and in effective management of the IP addresses. Instead of creating a subnet, IP address range is blocked for both DHCP pool allocation and IP address assignment for point-to-point links, loopback, and multicast.
LAN Automation Example
Imagine you want to LAN automate 10 devices in a site using the same pool, where each device has one link to the primary seed and another link to the secondary.
Consider a 192.168.199.0/24 as an example pool. When LAN automation starts,
a first /26 pool is reserved for the DHCP addresses. In this example, 192.168.199.”1″ to 192.168.199.”63″ are reserved and assigned to VLAN 1 for the 10 devices.
Next, a “/27” pool is reserved for loopback addresses.
If there is no shared IP pool, then this pool is used for point-to-point links as well.
Because there are 10 devices with two links each, a total of 40 IP addresses are reserved for point-to-point links,
40 addresses because each switch needs 4 IP addressess (2 assigned on switch’s uplinks itself and 1 assigned on primary seed device and 1 assigned on peer seed device)
In total, 60 IP addresses are reserved for the 10 devices: 10 for each VLAN 1, 10 for each loopback, and 40 for the point-to-point links between devices and seeds.
After LAN automation stops, the VLAN 1 IP addresses are released back to the pool
We recommend that you use the default interfaces connected to PnP agents. If the peer seed device has IP interfaces configured on the interfaces connected to PnP agents, those links are not configured. Default the interfaces connected to ono agents and perform an inventory synchronization on the peer seed device. LAN automation works only when the ports are Layer 2. The ports on the Cisco Catalyst 6000 Series Switches are Layer 3 by default. Convert the ports to Layer 2 before starting LAN automation.
LAN automation configures loopback on the seed devices if they are not configured.
If you change configuration on the seed devices before running LAN automation, synchronize the seed devices with the Catalyst Center inventory.
If you plan to run multiple discovery sessions to onboard devices across different buildings and floors connected to the same seed devices, we recommend that you block the ports for PnP agents that do not participate in the upcoming discovery session yet.
For example, imagine seed devices in Building-23 connected to PnP agents on Floor-1 and Floor-2. Floor-1 devices are connected on interfaces Gig 1/0/10 through Gig 1/0/15. Floor-2 devices are connected on interfaces Gig 1/0/16 through Gig 1/0/20. For the discovery session on Floor-1, we recommend that you shut down ports connected to Gig 1/0/16 through Gig 1/0/20. Otherwise, the PnP agents connected to Floor-2 might also get DHCP IPs from the server running on the primary seed device. Because these interfaces aren’t selected for the discovery session, they remain as stale entries in the PnP database. When you run the discovery session for Floor-2, the discovery doesn’t function correctly until these devices are deleted from the PnP application and write erase/reloaded. Therefore, we recommend that you shut down other discovery interfaces
For Catalyst Center Release 1.2.8 and earlier, if clients are connected to a switch being discovered, they may contend for DHCP IP and exhaust the pool, causing LAN automation to fail. Therefore, we recommend that you connect the client after LAN automation is complete. but that is for older DNAC versions
This endpoint/client integration restriction does not apply to Catalyst Center Release 1.2.10 and later. Clients can remain connected while the switch is undergoing LAN automation.
on the edge nodes add license and then reset pnpa so pnp wizard becomes active after putting license
otherwise LAN Automation commands will fail as there is no dna-advantage
license boot level network-advantage addon dna-advantage
end
write mem
reload pnpa service reset no-promptSteps for LAN Automation
- Default the interfaces connected to agents and perform an inventory synchronization on the peer seed device
- LAN automation configures loopback on the seed devices if they are not configured.
- If you change configuration on the seed devices before running LAN automation, synchronize the seed devices with the Catalyst Center inventory.
- Add Site > Add Area
- Add Site > Add Building
- Add Site > Add Floor
- Design > Network Settings > Device Credentials
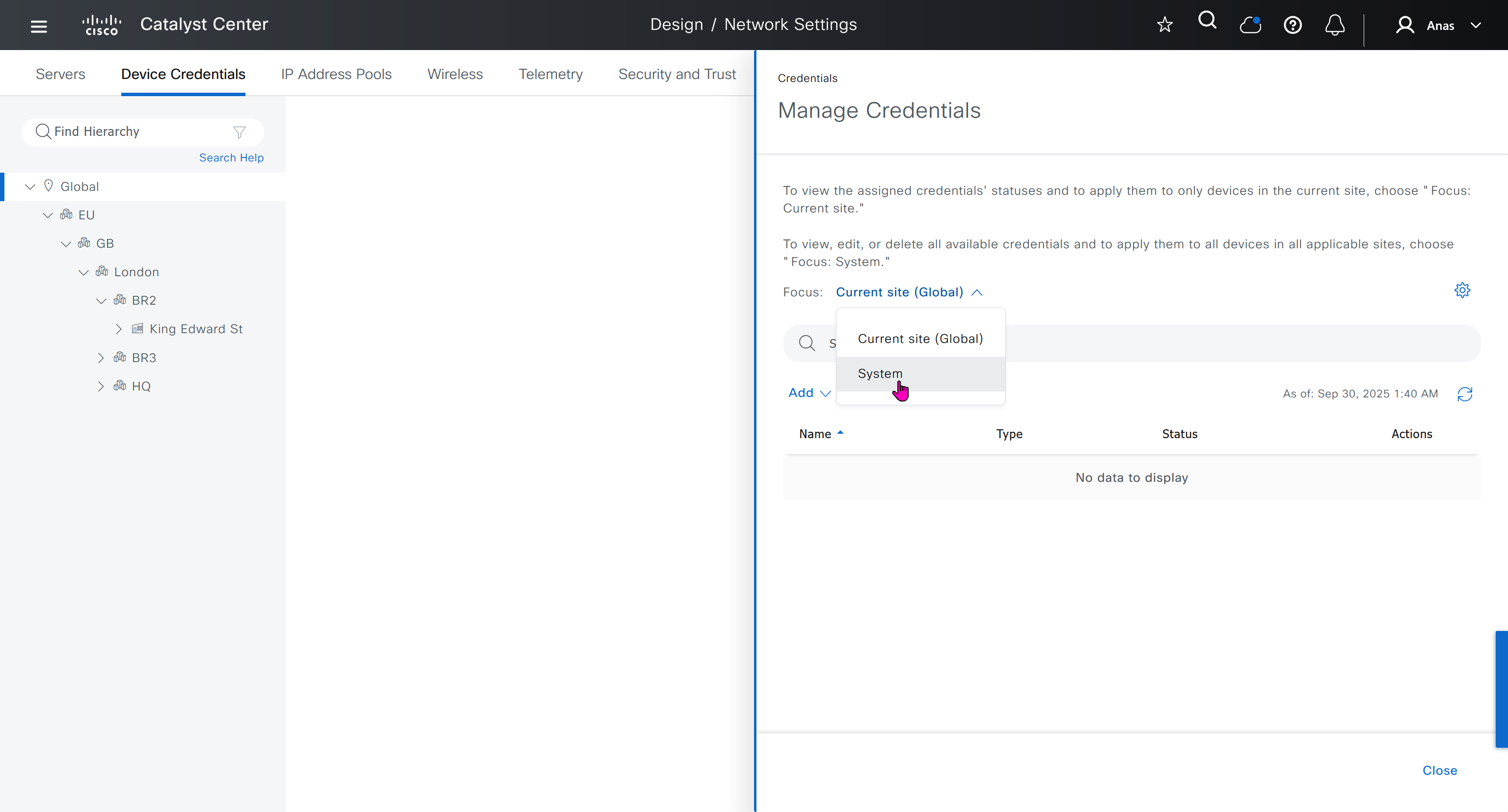
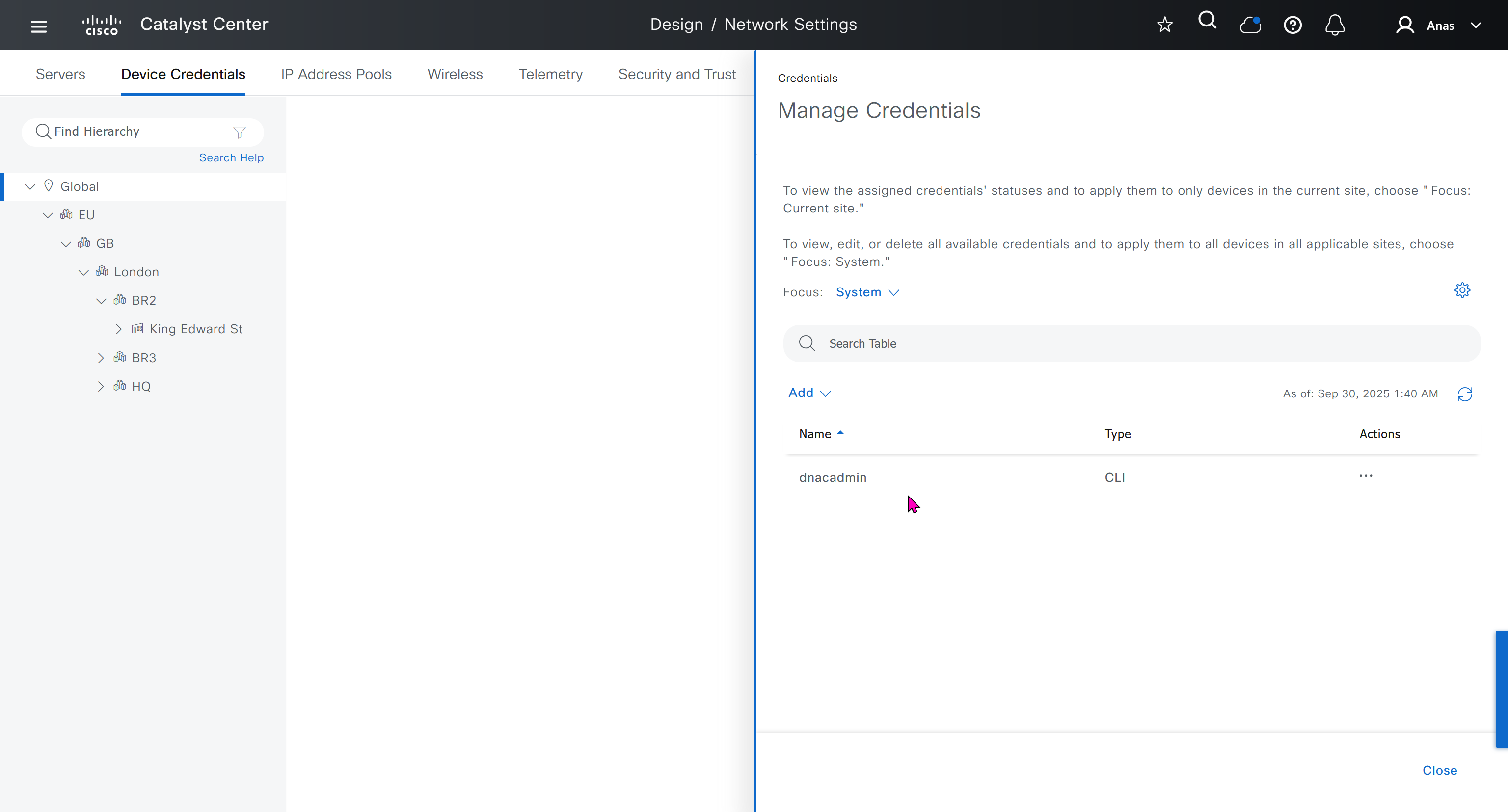
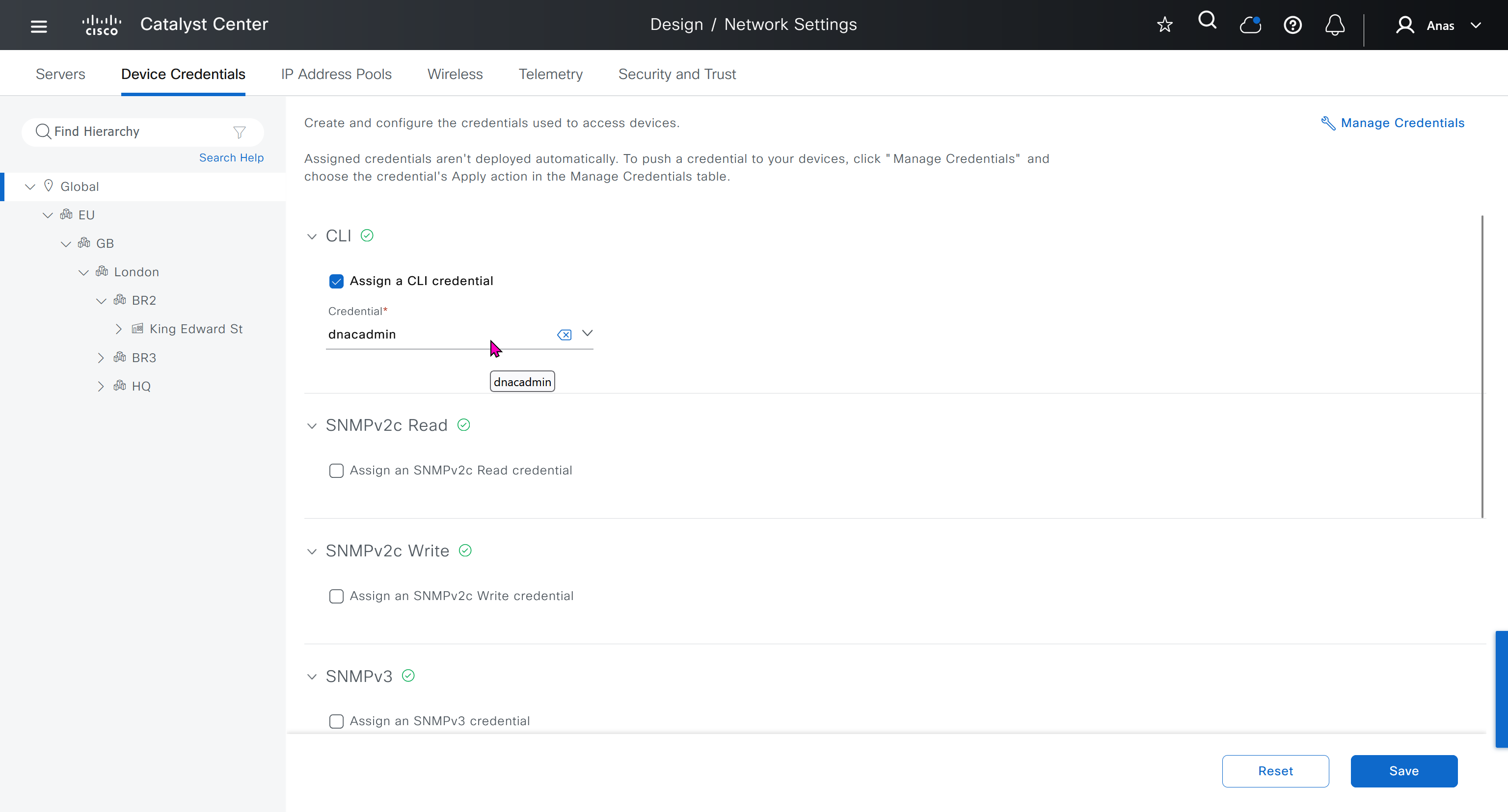
- Manage Credentials
- CLI
- SNMPV2C Read
- Netconf
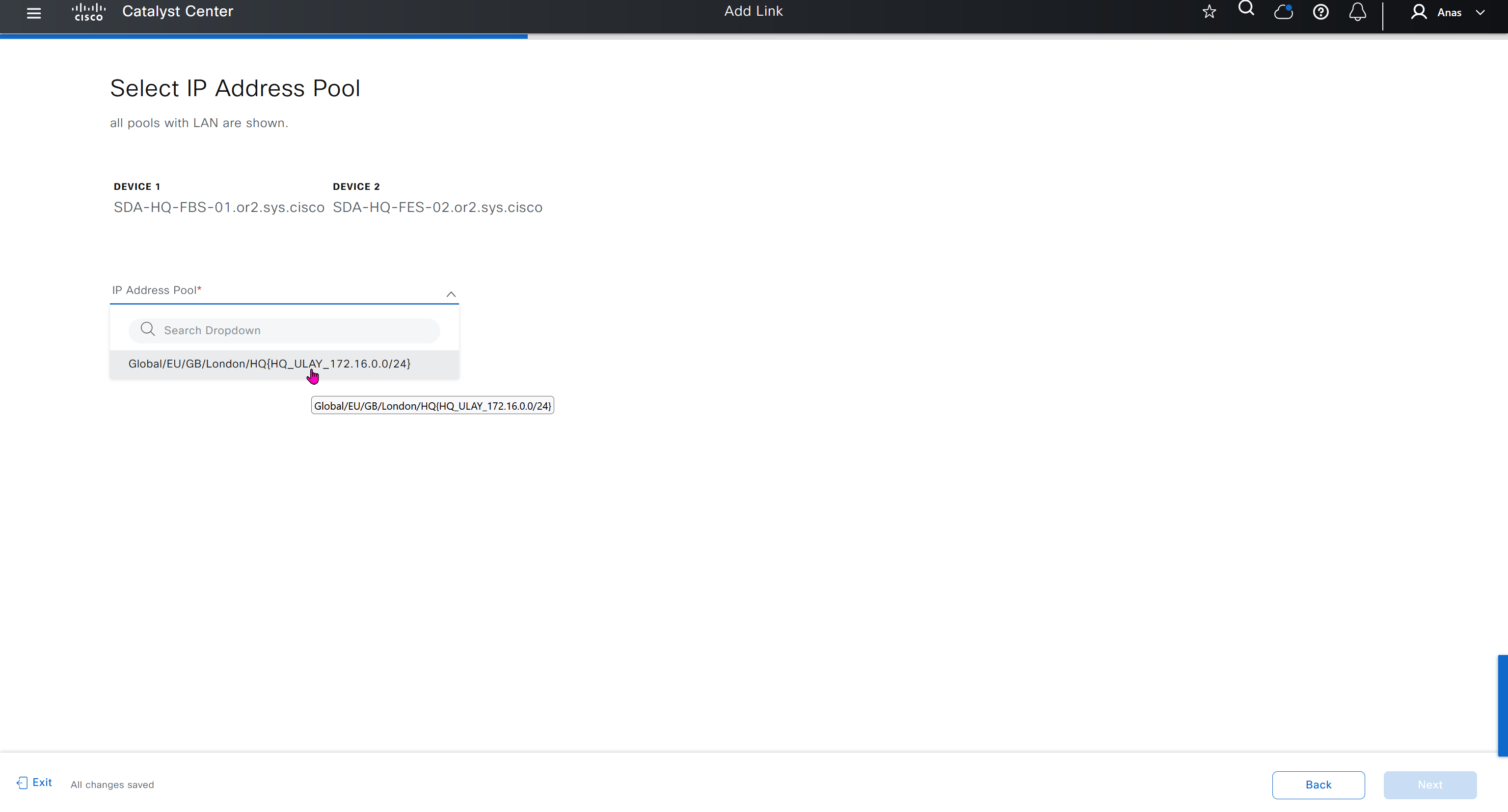
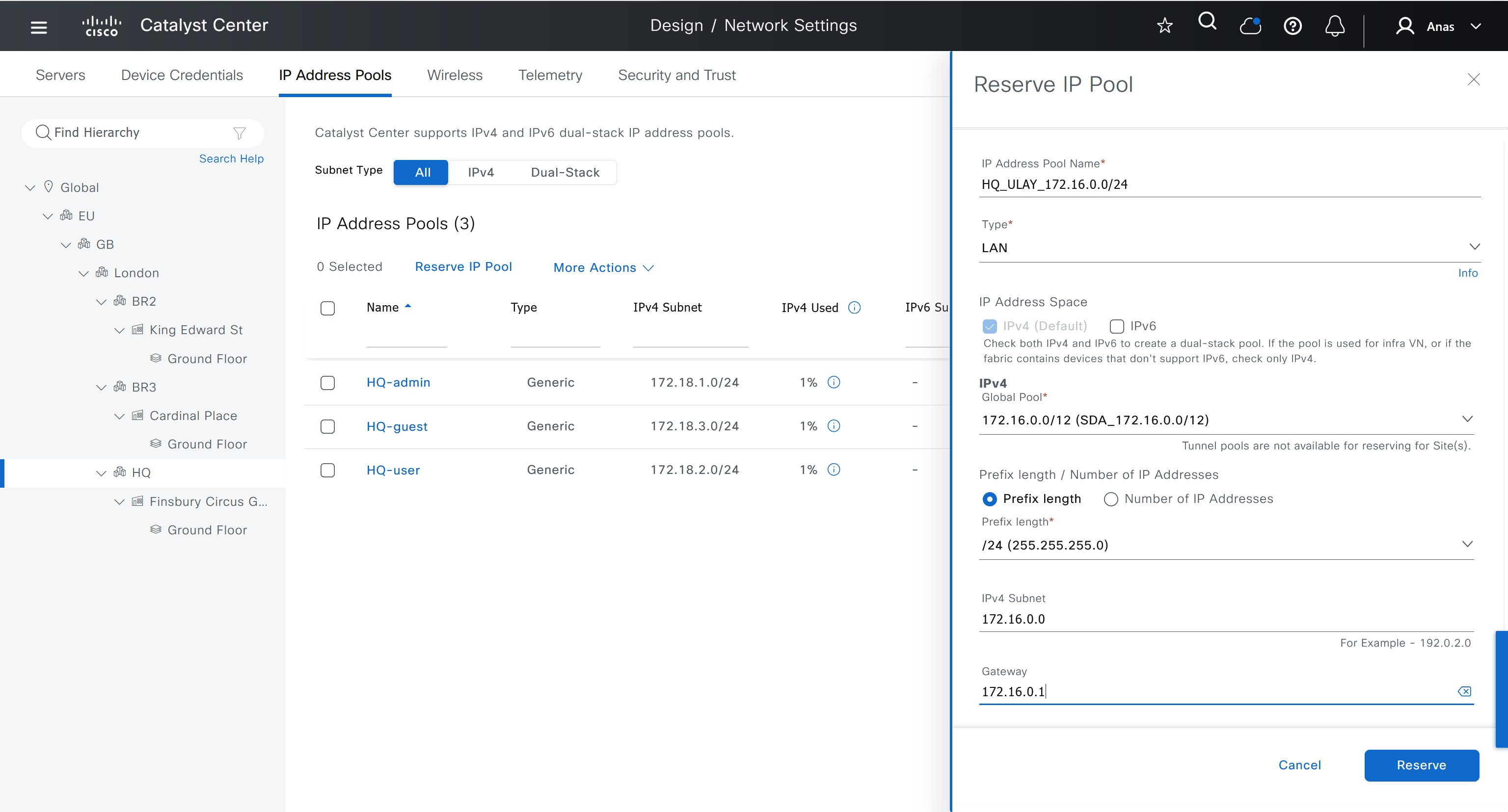
- Create an underlay pool that is not used any where in the network
See how the gateway address is set 172.16.0.1 and you ask why is that needed?
This is the address that will be assigned to FBS on vlan 1 interface (which is removed later on once LAN automation ends)
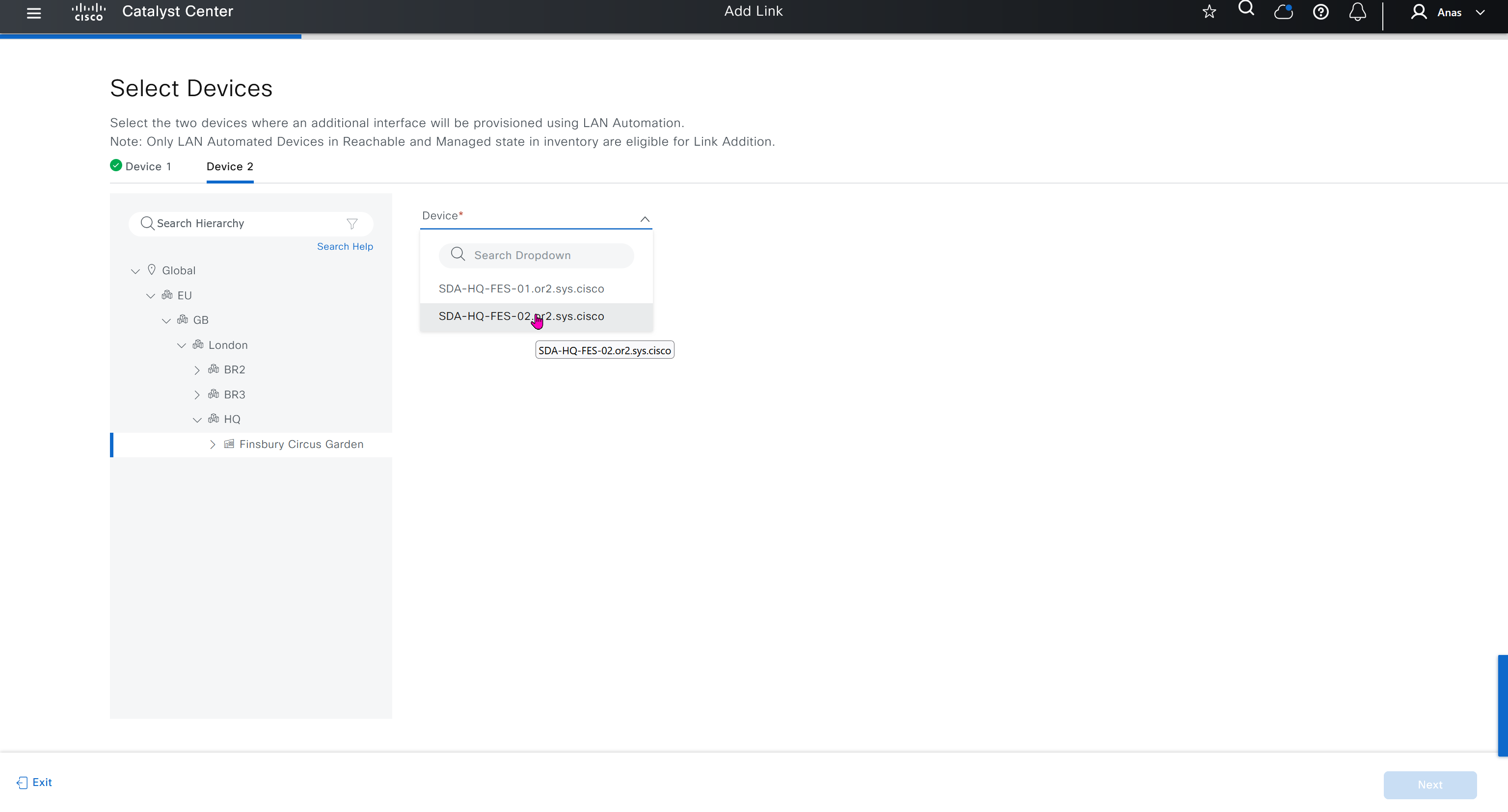
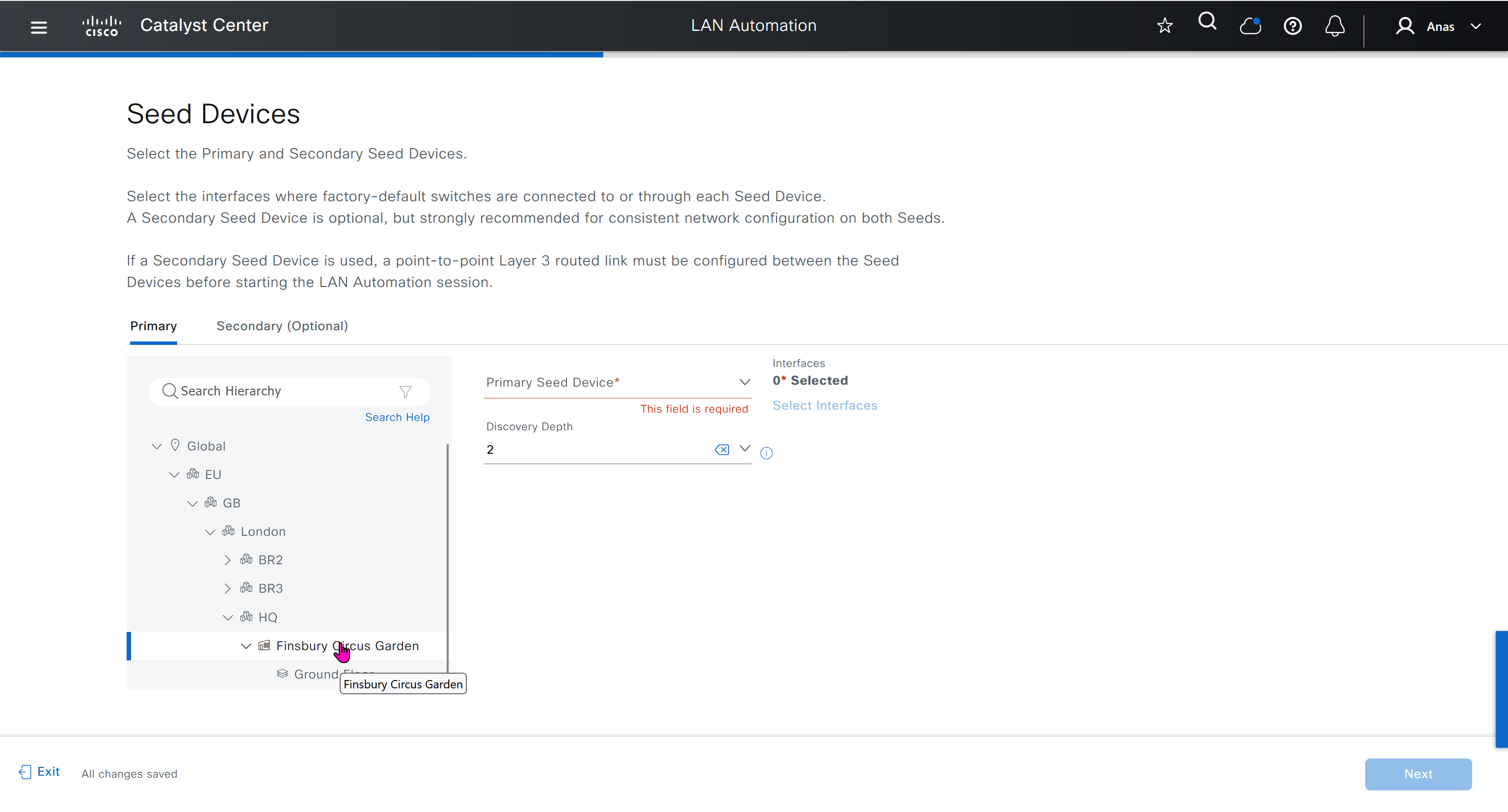
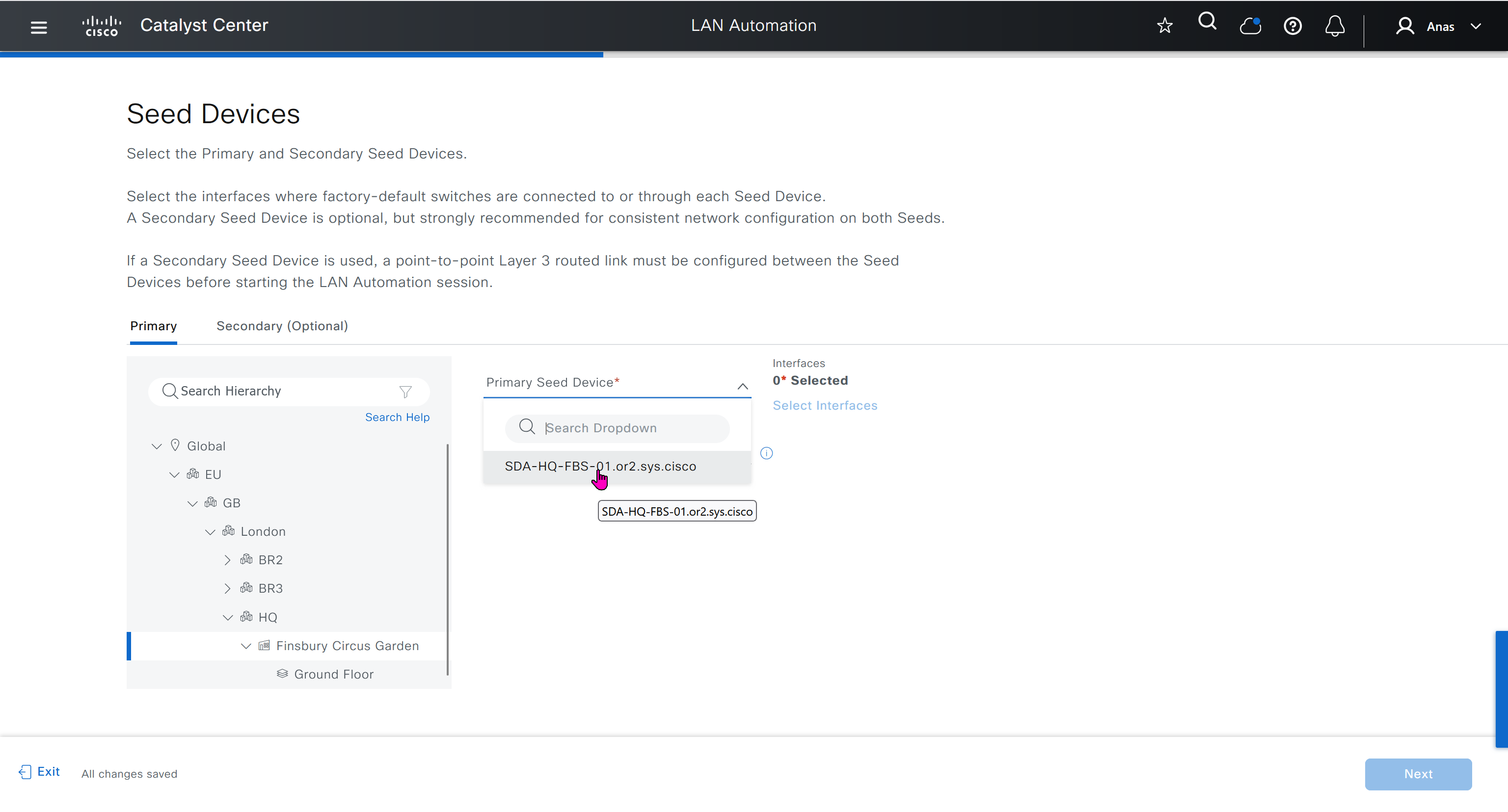
- Discover seed devices with discovery
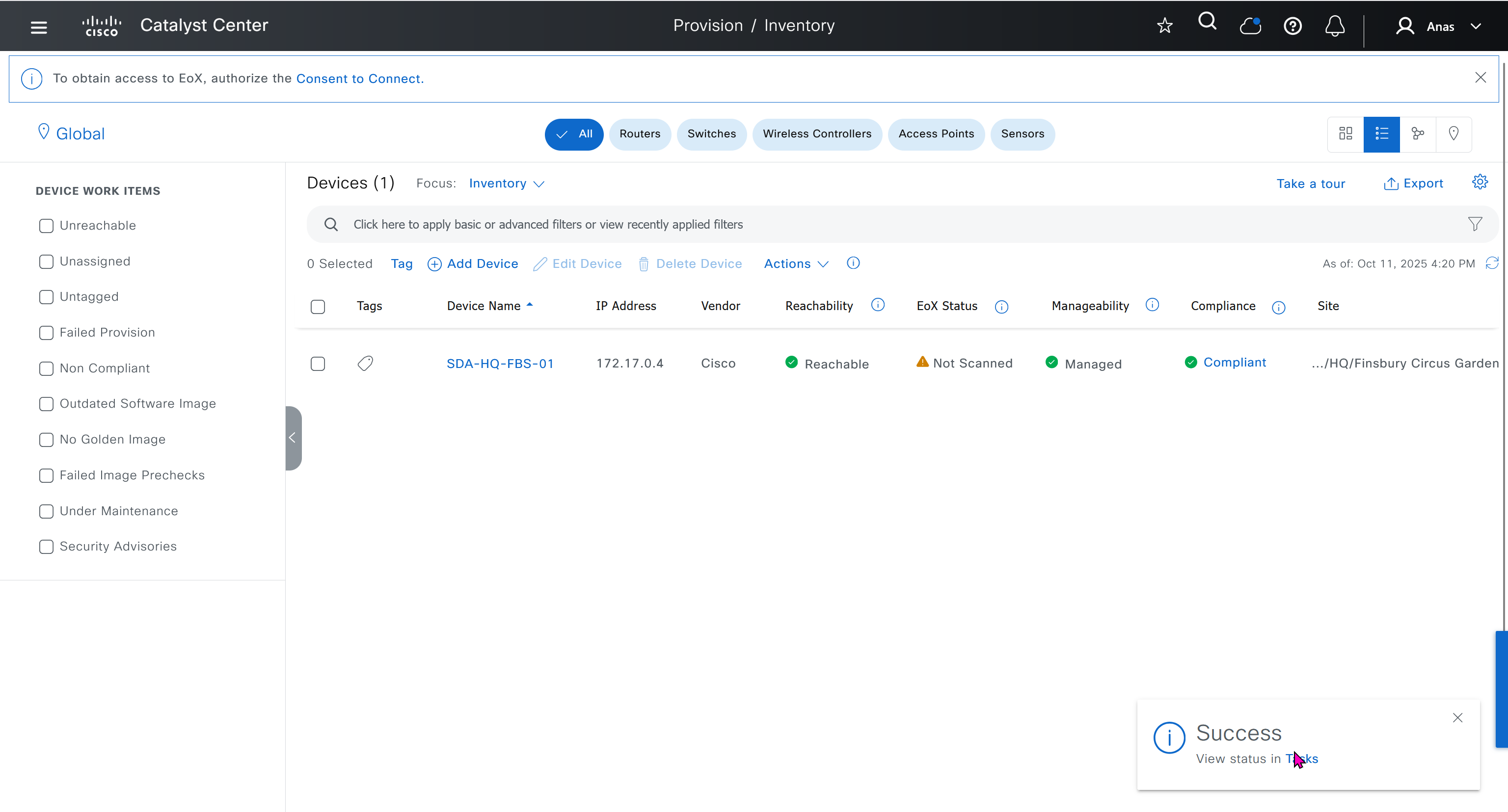
- Make sure that discovered devices are in Reachable + Managed state
- Actions > Provision > Assign Device to Site to assign the device to a site.
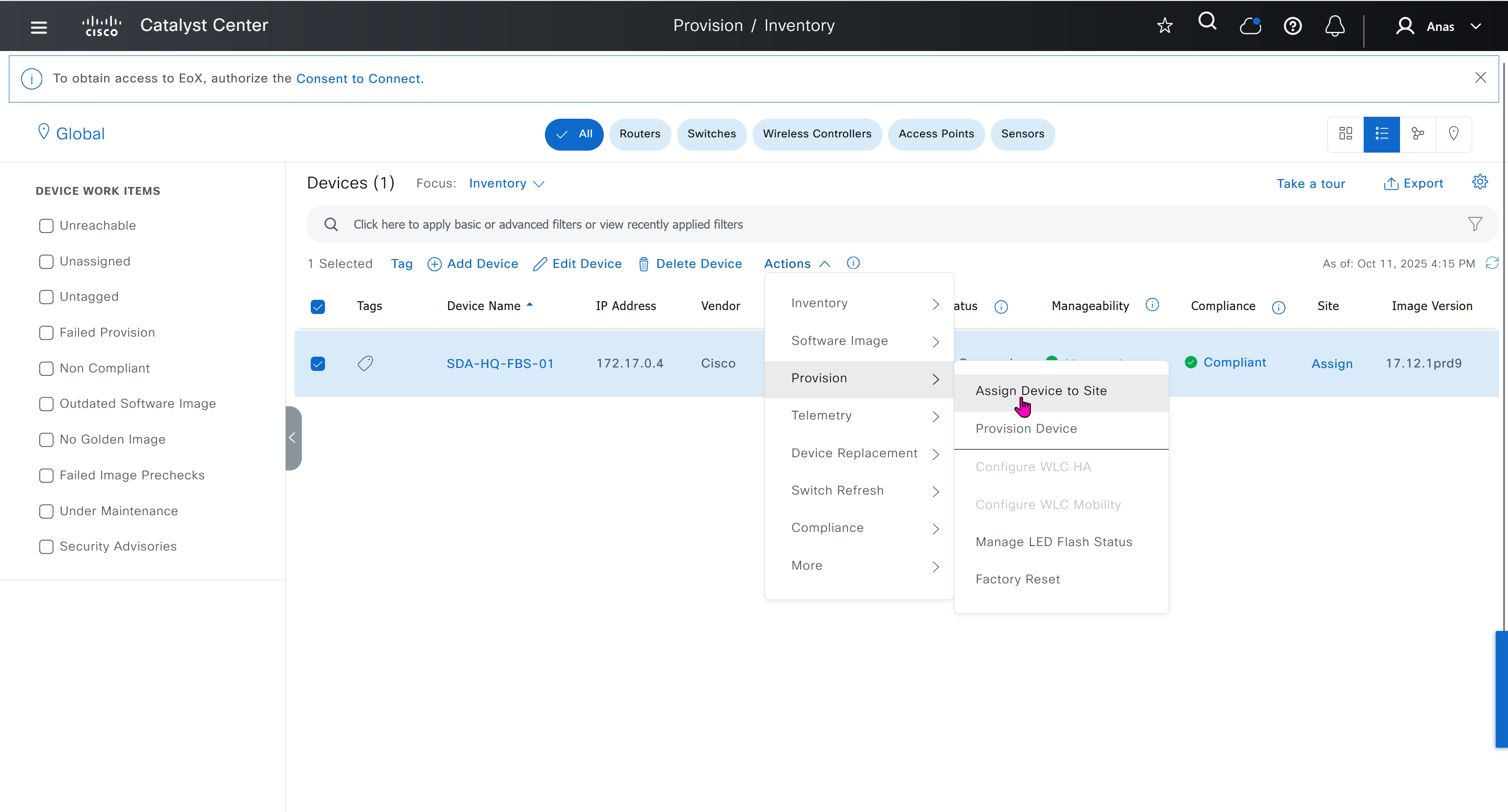
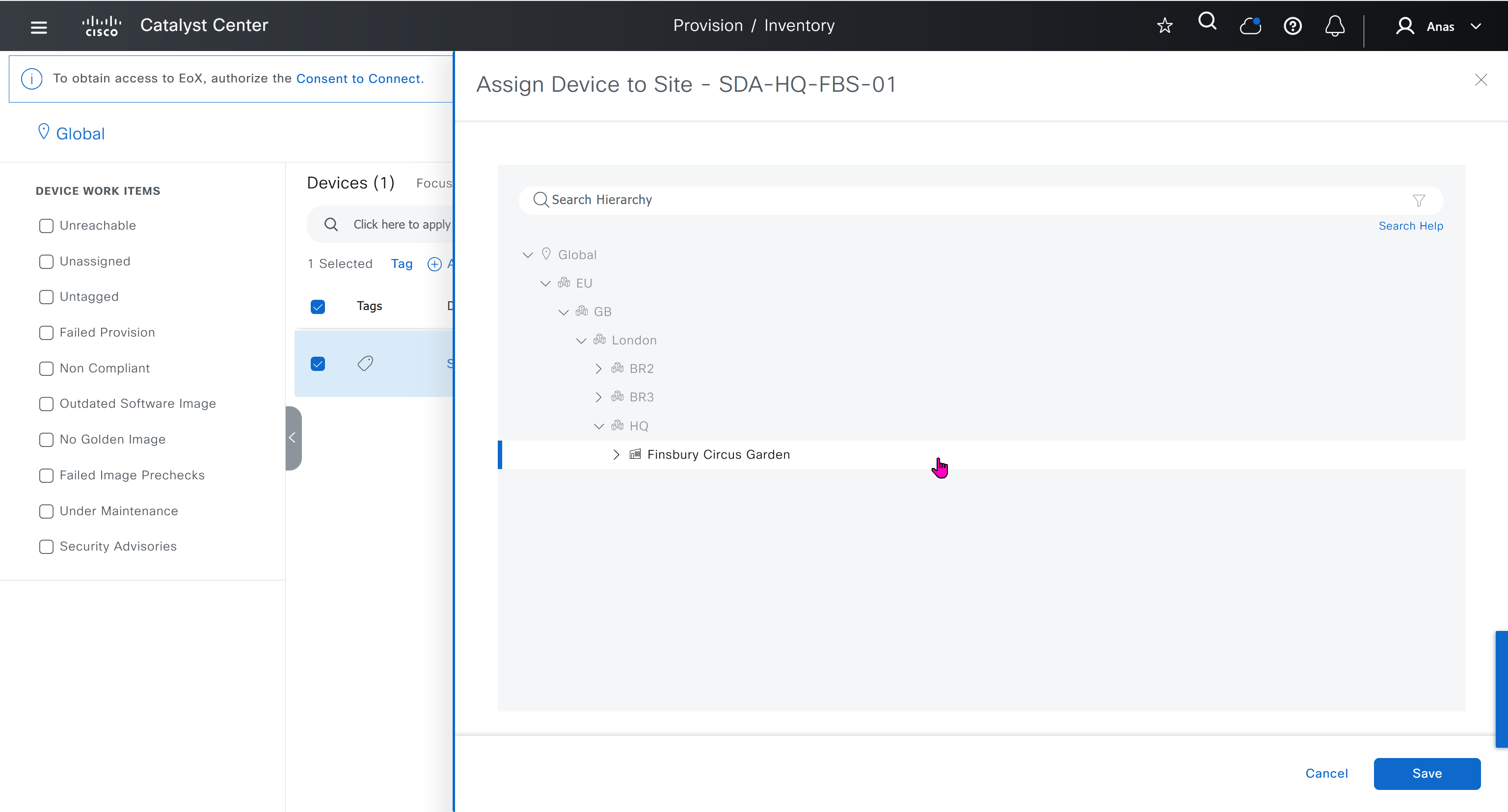

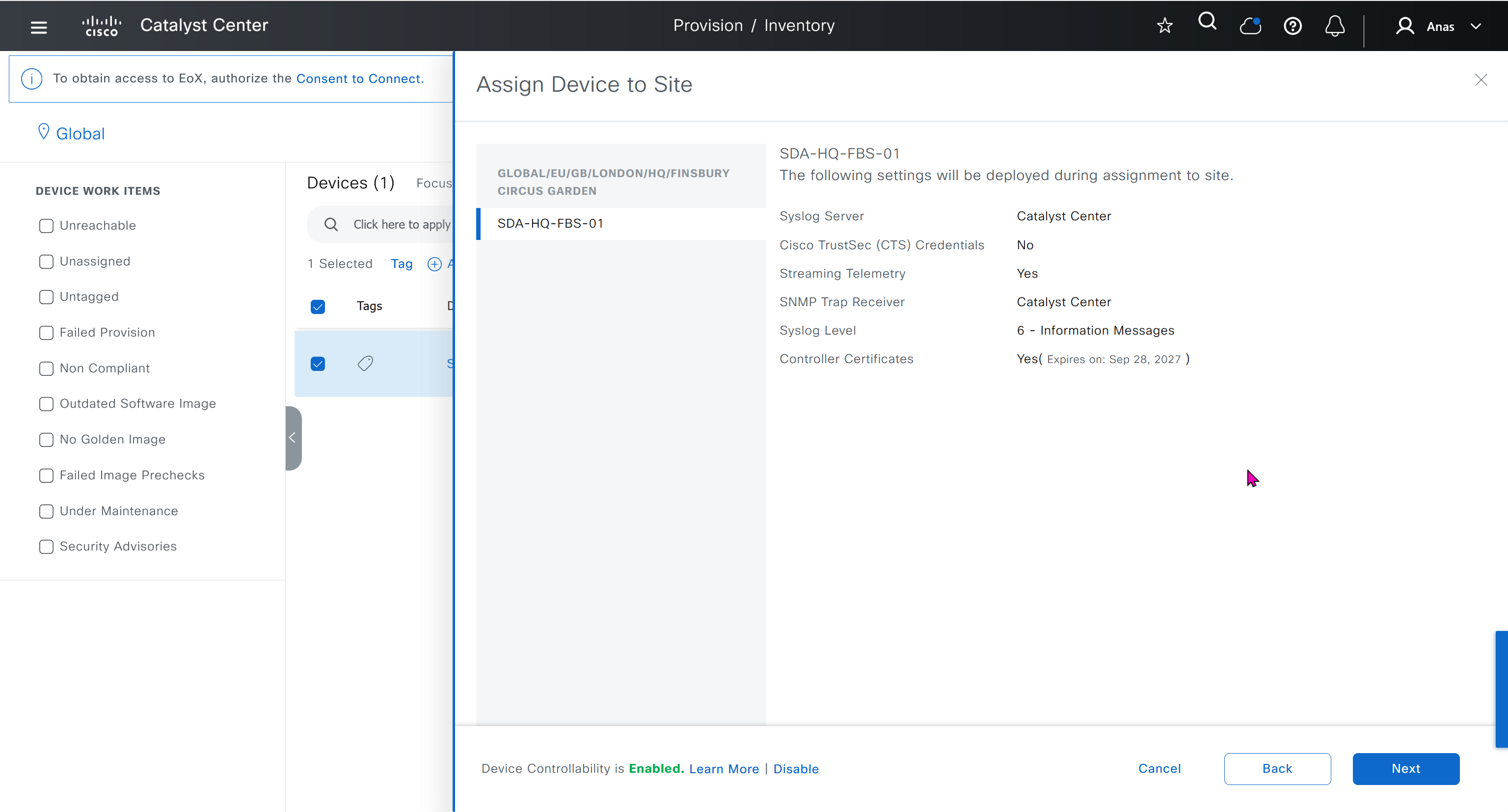



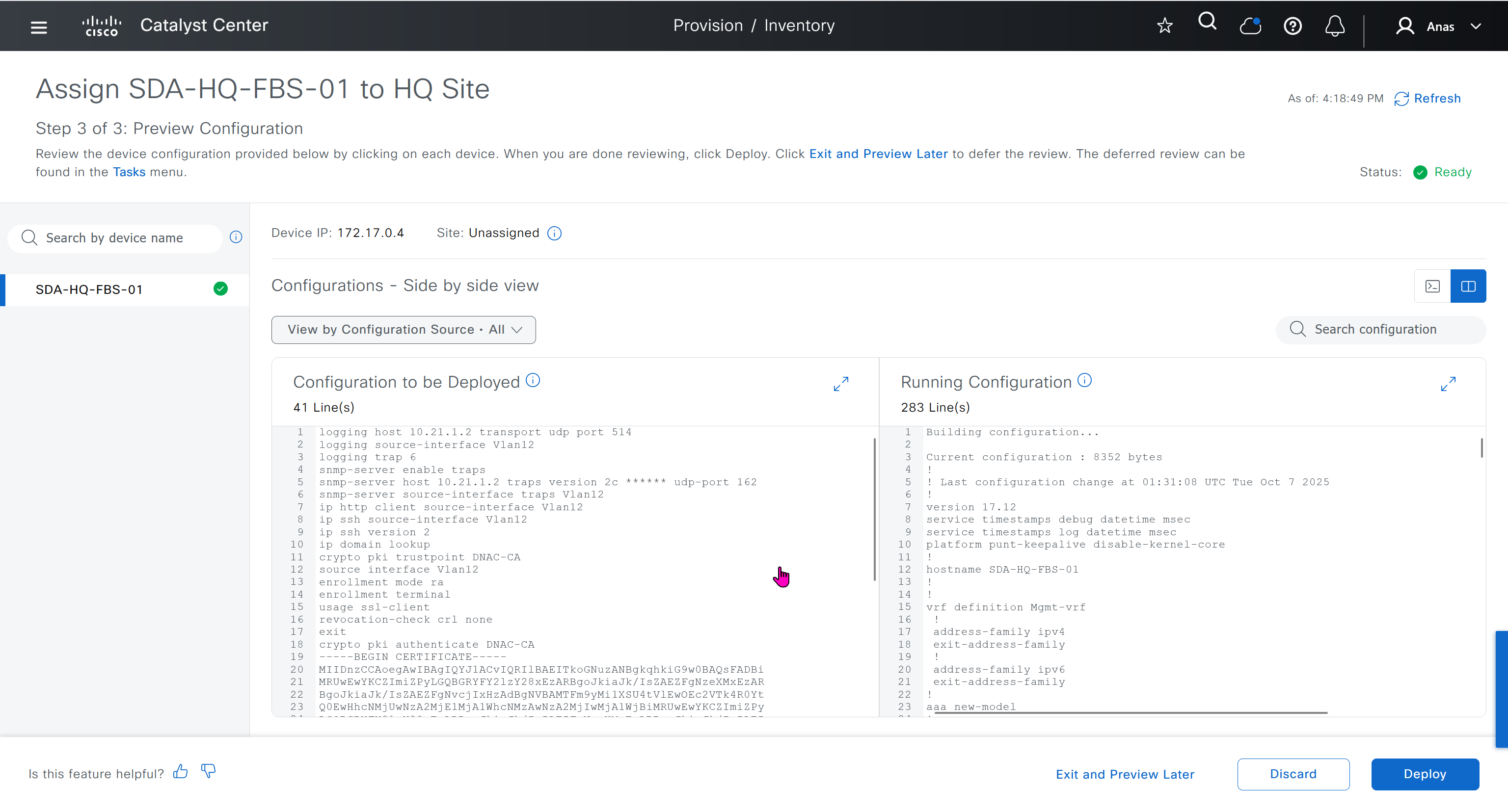
This is the configuration that will go on the seed device after only addign it to the site
logging host 10.21.1.2 transport udp port 514
logging source-interface Vlan12
logging trap 6
snmp-server enable traps
snmp-server host 10.21.1.2 traps version 2c ****** udp-port 162
snmp-server source-interface traps Vlan12
ip http client source-interface Vlan12
ip ssh source-interface Vlan12
ip ssh version 2
ip domain lookup
crypto pki trustpoint DNAC-CA
source interface Vlan12
enrollment mode ra
enrollment terminal
usage ssl-client
revocation-check crl none
exit
crypto pki authenticate DNAC-CA
-----BEGIN CERTIFICATE-----
MIIDnzCCAoegAwIBAgIQYJ1ACvIQRIlBAEITkoGNuzANBgkqhkiG9w0BAQsFADBi
MRUwEwYKCZImiZPyLGQBGRYFY2lzY28xEzARBgoJkiaJk/IsZAEZFgNzeXMxEzAR
BgoJkiaJk/IsZAEZFgNvcjIxHzAdBgNVBAMTFm9yMi1XSU4tVlEwOEc2VTk4R0Yt
Q0EwHhcNMjUwNzA2MjE1MjA1WhcNMzAwNzA2MjIwMjA1WjBiMRUwEwYKCZImiZPy
LGQBGRYFY2lzY28xEzARBgoJkiaJk/IsZAEZFgNzeXMxEzARBgoJkiaJk/IsZAEZ
FgNvcjIxHzAdBgNVBAMTFm9yMi1XSU4tVlEwOEc2VTk4R0YtQ0EwggEiMA0GCSqG
SIb3DQEBAQUAA4IBDwAwggEKAoIBAQCr6cjaoJz3vzgHlQ1hzhuy5WfIL/Ao0isM
ltIaGL+Z+9WftM1hNh10YECbxR71+lIpQKyBQTXQz8Of4nycxHjoI3dQdUvEYb8H
fysDXh4lYjQ60x82e5c7f1KPbD+AOhC31Zw1dgReMlPIuaa9LK903+z0FRnuCHaI
EG/Z9uCmv3JC22NgL69hscZc+NUGymMy1iBPN8G4EBkgqNVZ+zlRf/adW0JxEdc6
Sy53bp586/fXziRTW++jgdnhvfpn+VJ+BdG88/rEgMl7PUQE95lq4dih7qx0+OXu
ihFwQQvFxvi3dyqWWc0C1RKHPHtYQFz8rRuBJrR+uzgc0lVhrNHdAgMBAAGjUTBP
MAsGA1UdDwQEAwIBhjAPBgNVHRMBAf8EBTADAQH/MB0GA1UdDgQWBBQ/bI8yZeKD
fgjmmeWorjGo25t5hzAQBgkrBgEEAYI3FQEEAwIBADANBgkqhkiG9w0BAQsFAAOC
AQEAdtt6aiABkDDg/mAlcZfFPHcqmEEvQaMPeBaUqvfZKNrFVO8GMb9kingZJ62n
K05x5wE3tHy3jBmAl6eHZ/nUjXS11C06NwZMHpcDhty5BcDN08oEYdLF24upisNA
aRLOBhyEtKI9VKLAWfMkpWYEd/dqgVWs67GjAFT0Osgva9QHbz24iT6/c09jbZMt
41opmxacw8FFZcHMH9Afv1fIW9PwscrdlgjSSHR4XQLyDbyuDGsolzeh9PUVyPOd
f+/LYkLwH9jVcHlxl4Oy7MHRPtcbG9T3+vQGLjSAXu3Ybrl2R9Tn/sz5lYs44EEB
mqCxT00LxB3et6jAxJlEyE5vCw==
-----END CERTIFICATE-----
do cts credentials id 7c71627623014c0a83668477604a0c57 password ******
SDA-HQ-FBS-01# conf t
SDA-HQ-FBS-01# ! for reachability testing only
SDA-HQ-FBS-01# interface vlan 1
SDA-HQ-FBS-01# ip address 172.16.0.1 255.255.255.0
SDA-HQ-FBS-01# end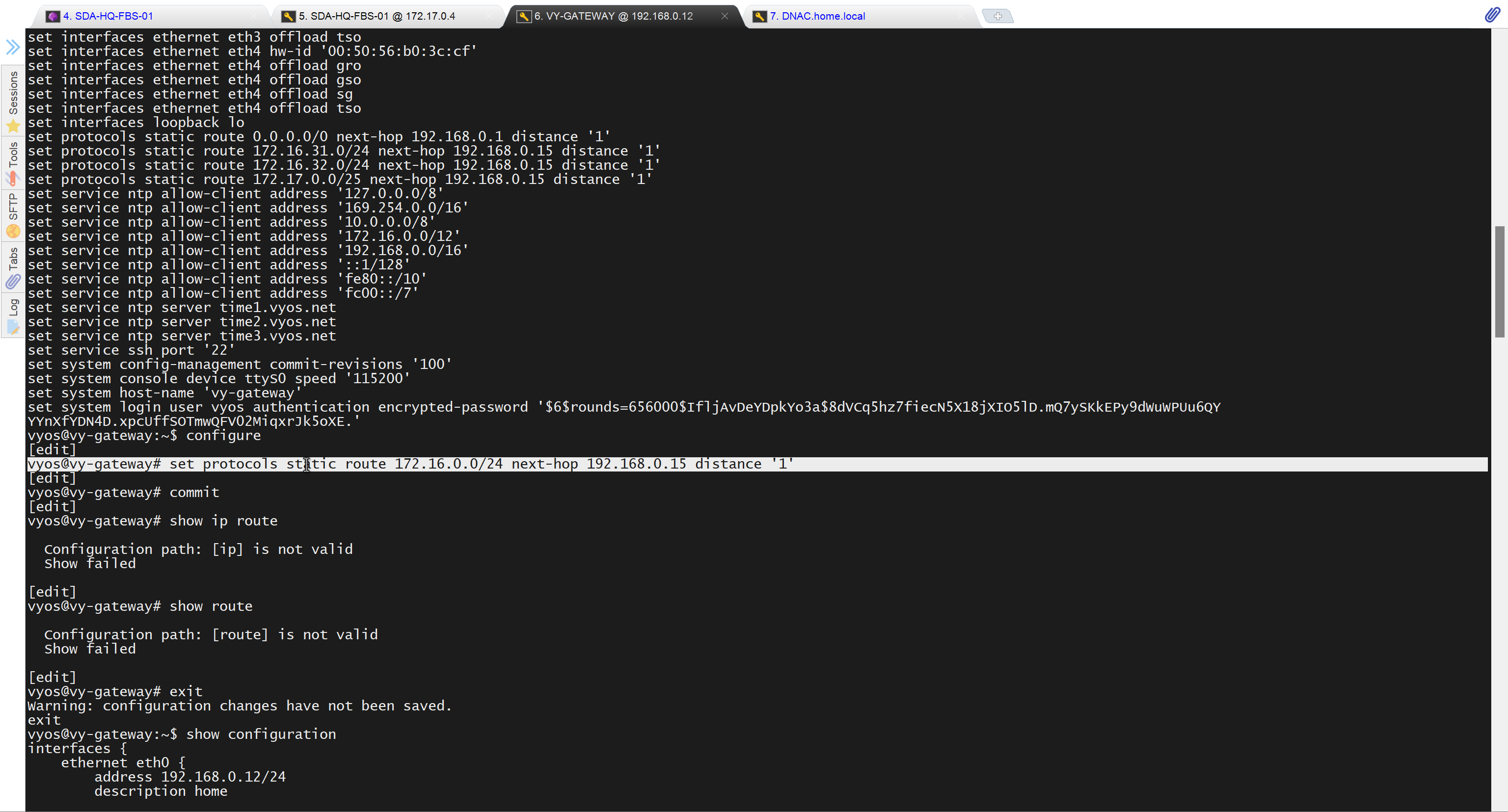
unable to reach
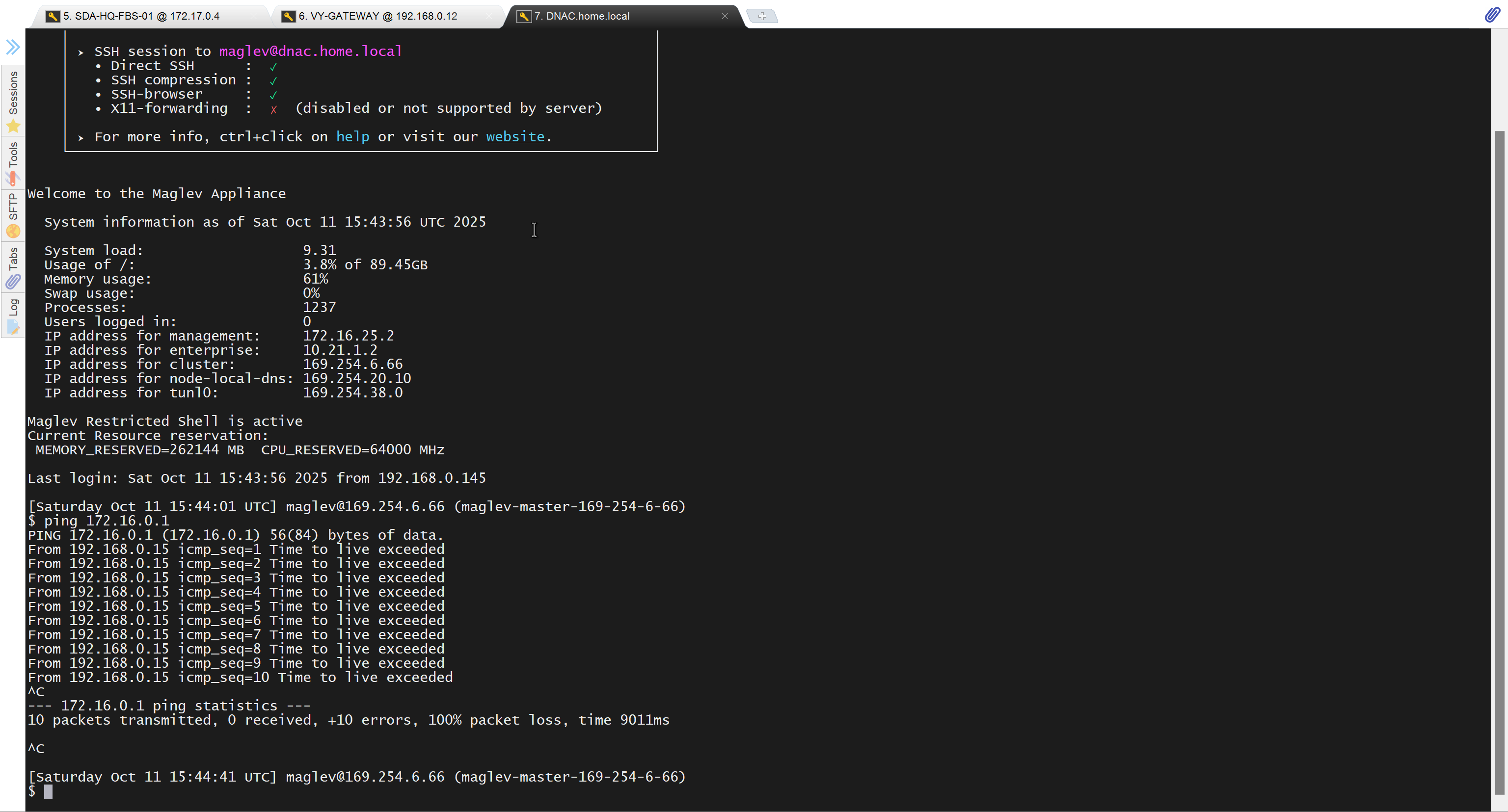
because missing route on HQ-SW in lab
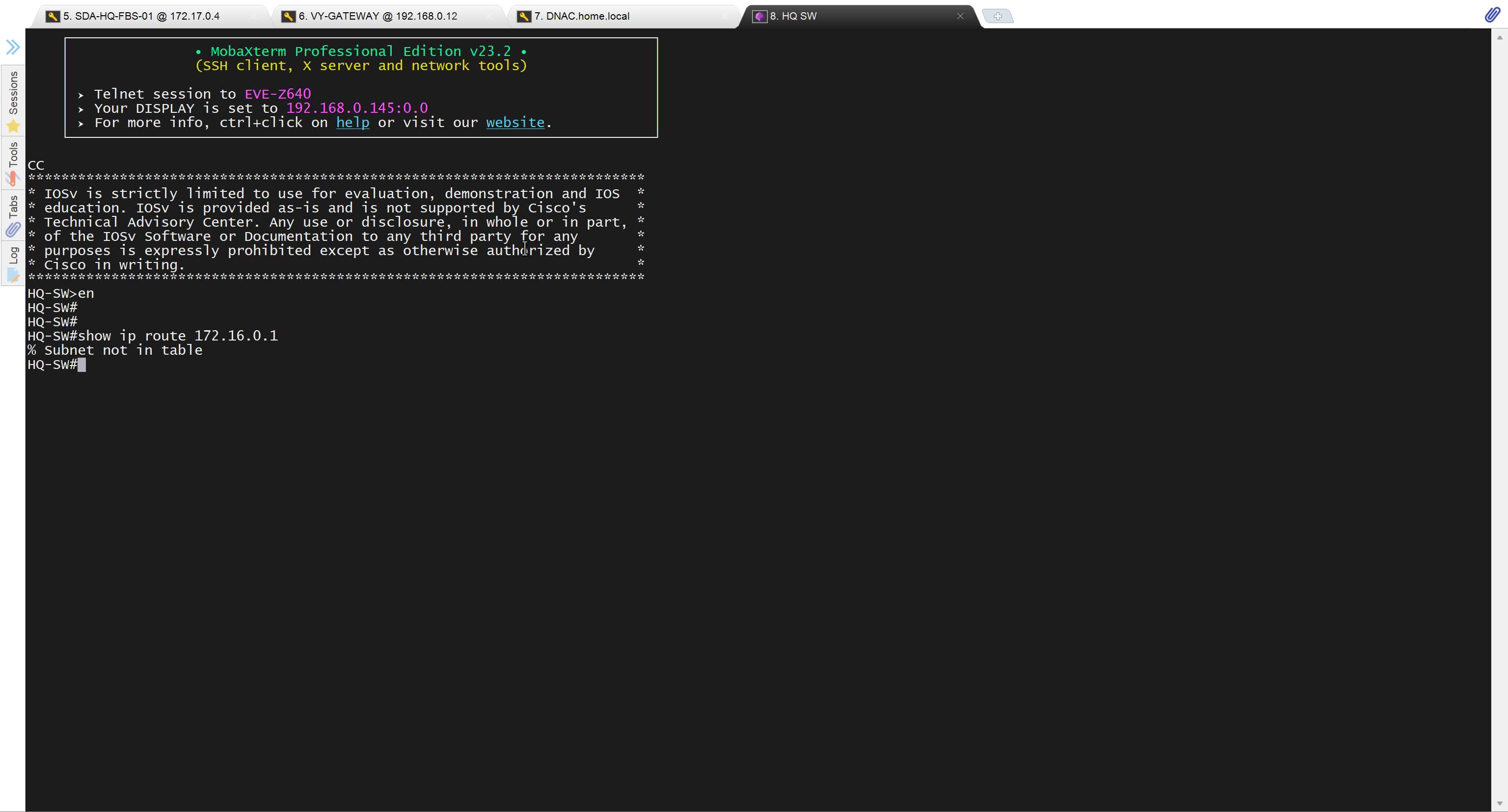
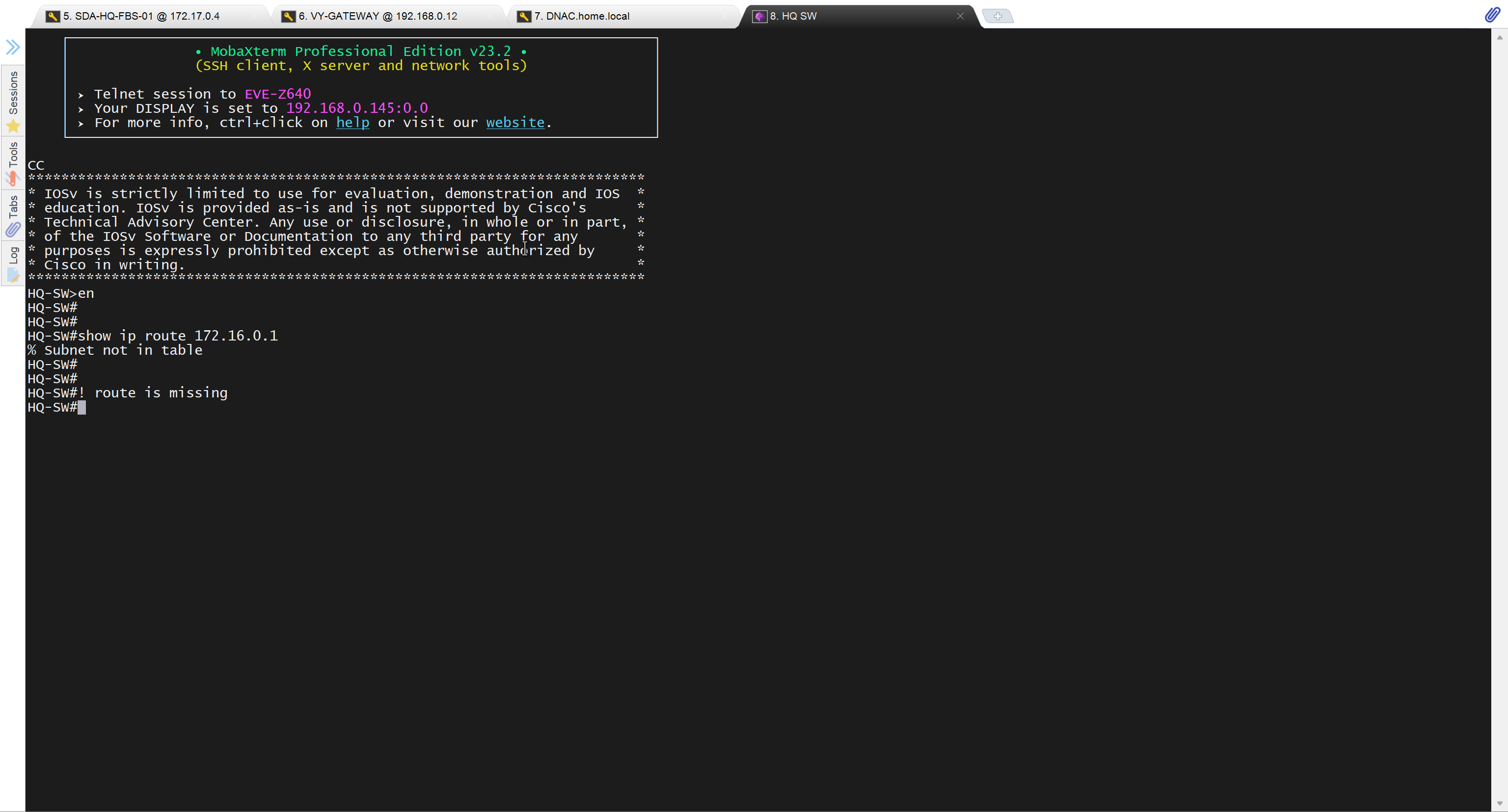
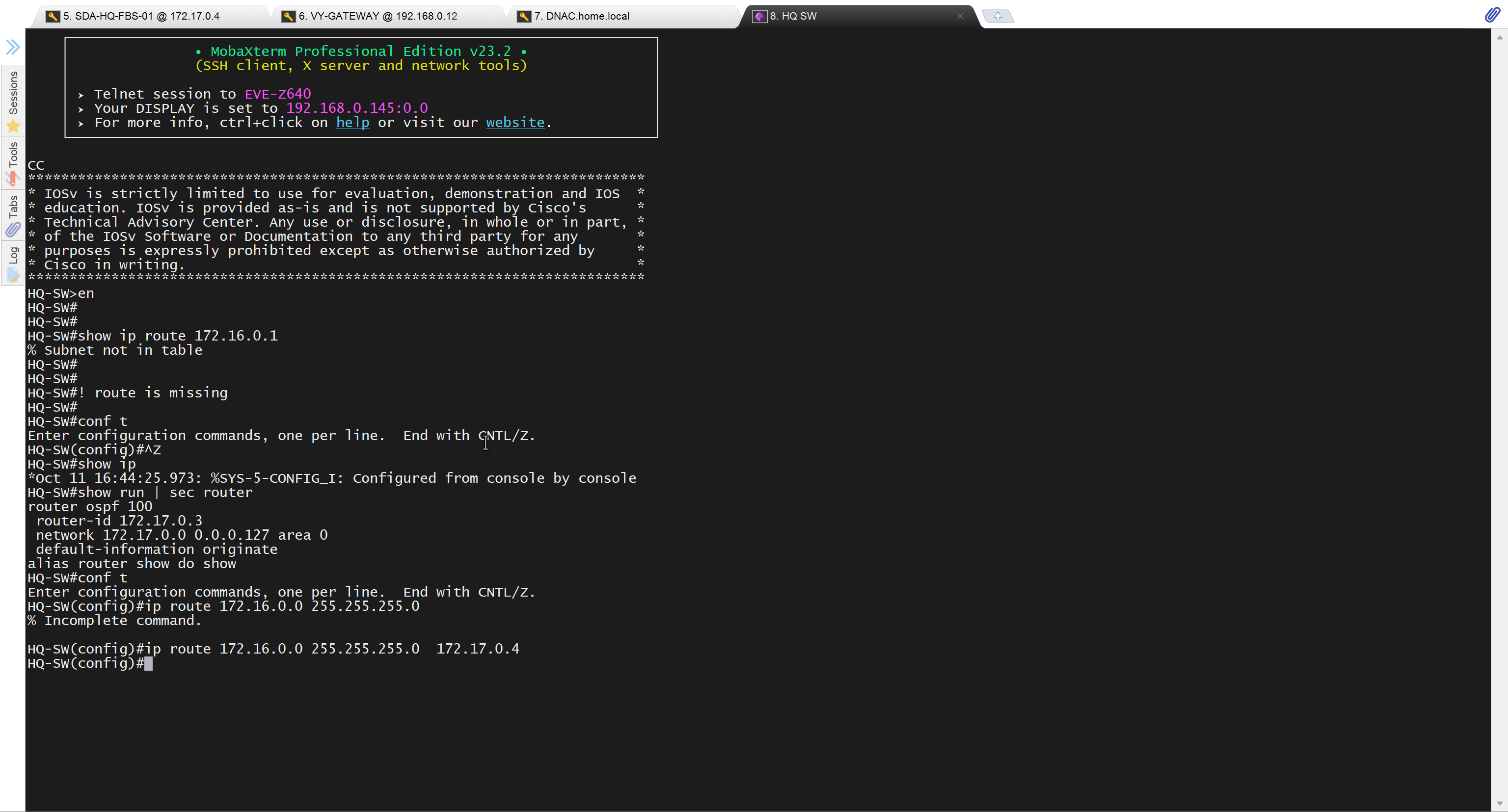
after adding route now we can reach
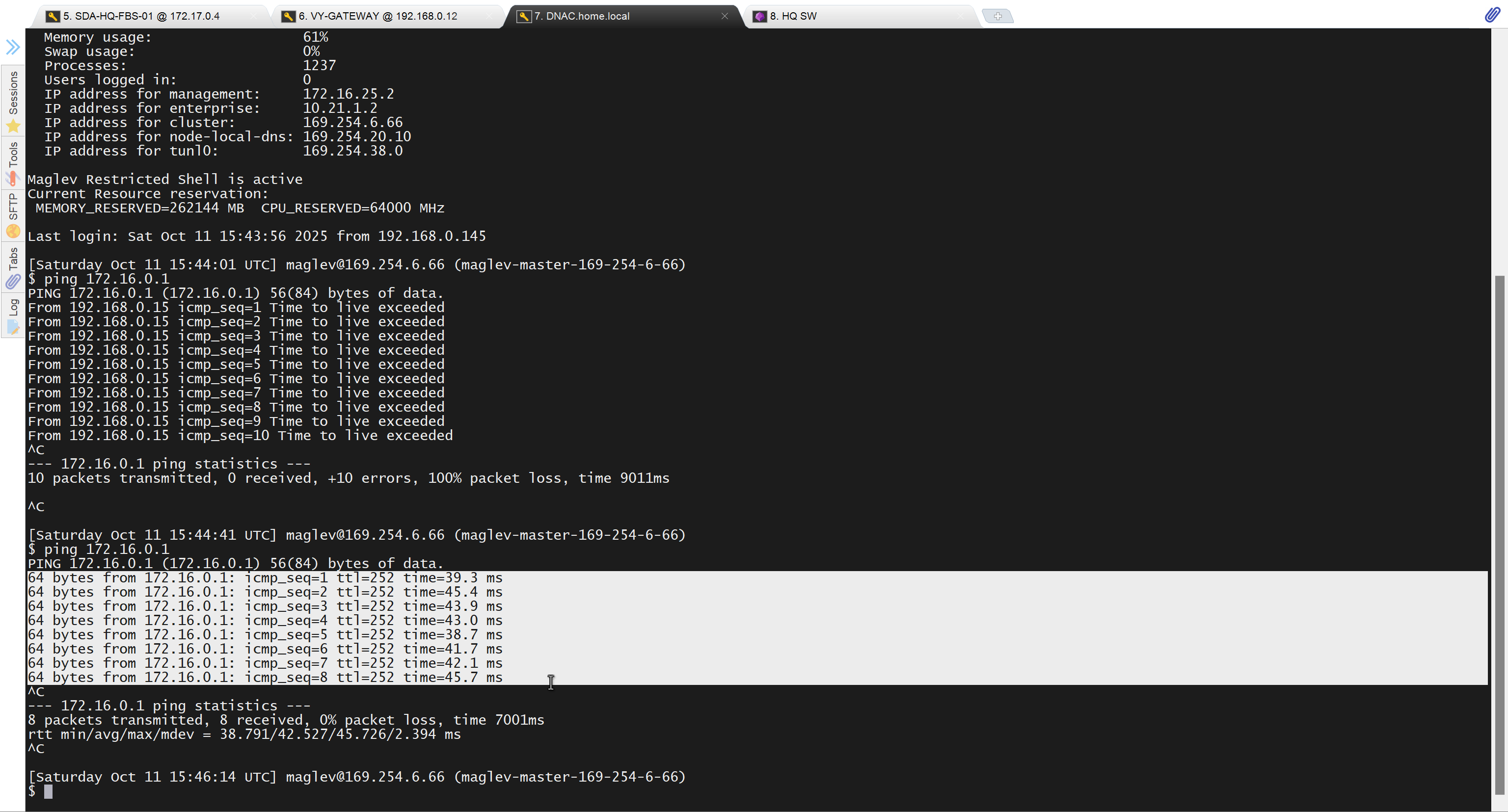
because it was only for testing, we will now remove it
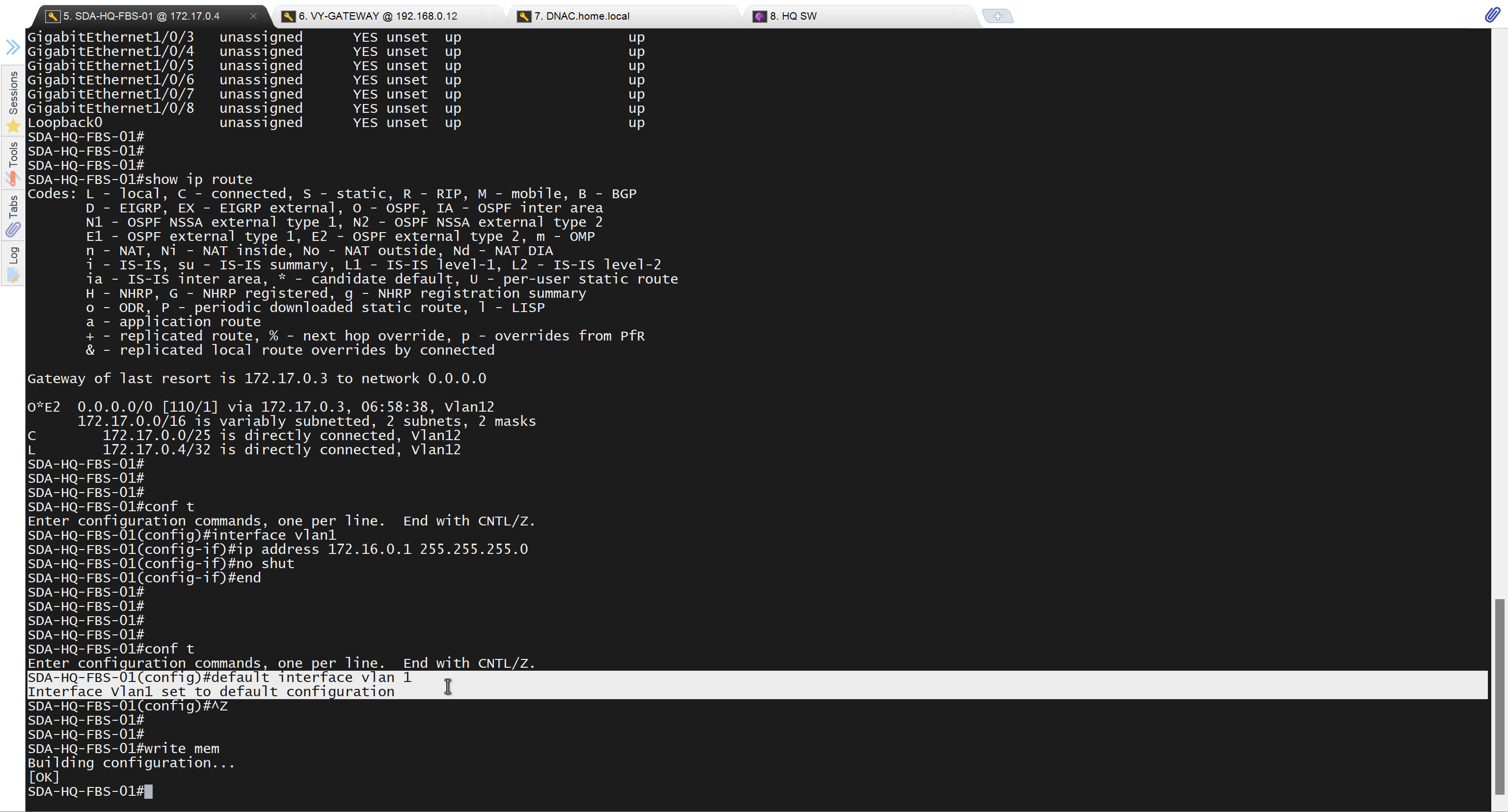
Now lets LAN Automate
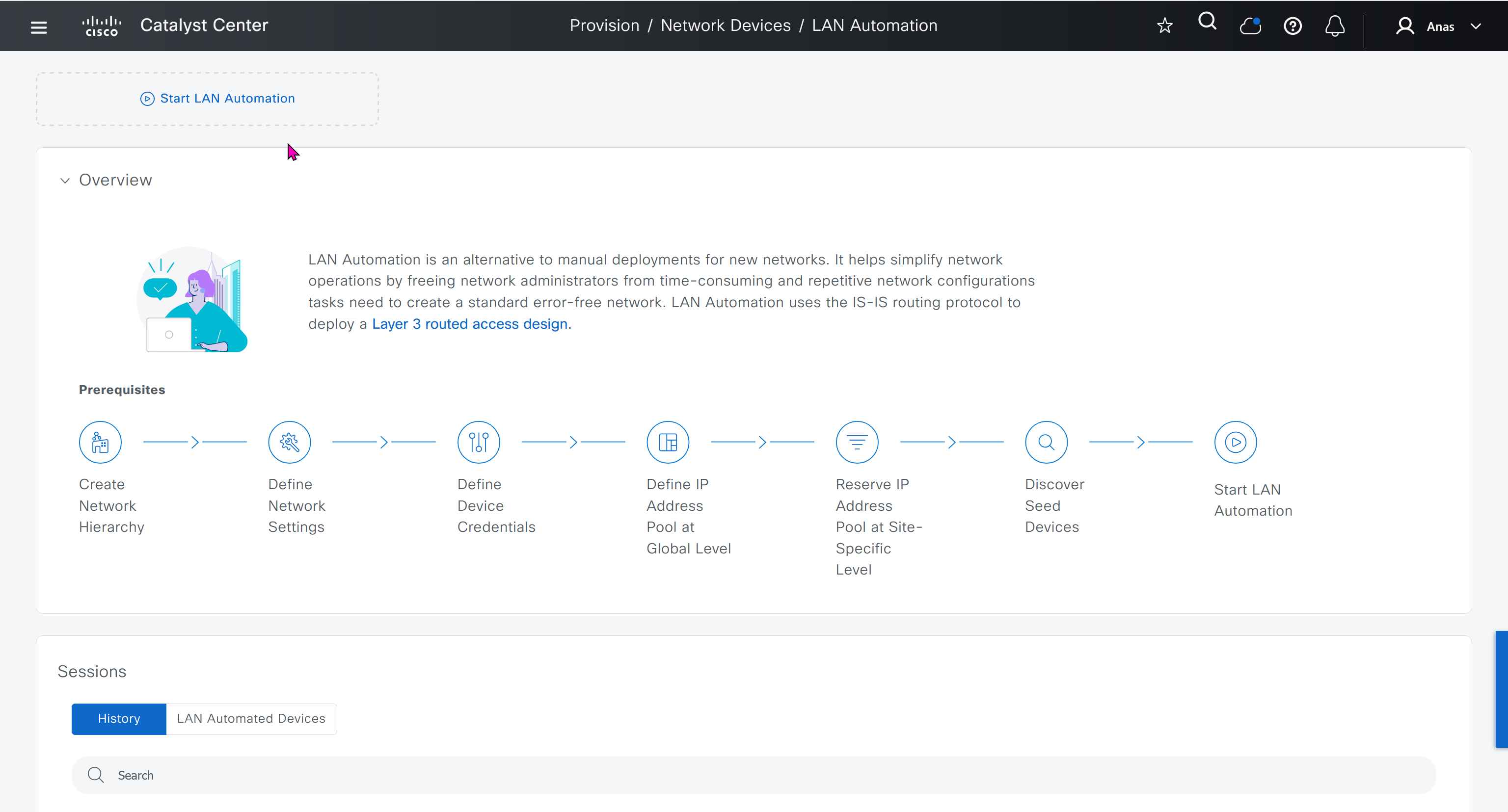
When LAN automation starts, Catalyst Center
pushes the loopback and IS-IS configuration to the primary and peer seed devices and the temporary configuration to the primary seed device
Catalyst Center Release 2.3.3 and later support is-type level-2-only as part of IS-IS configurations.
discovers new devices.
upgrades the device software image and pushes the configuration to discovered devices.
The image is updated only if a golden image is marked for that switch type in Catalyst Center under Design > Image repository.
When LAN automation starts, the temporary configuration is pushed to the primary seed device. This allows the device to discover and onboard the PnP agent. Next, the PnP agent image is upgraded and basic configurations such as loopback address, system MTU, and IP routing are pushed to the PnP agent.
- on PnP agent, Do not press Yes or No. Leave the device in the same state.
- Allow extra time to make sure that all members in the stack are up. Do not start LAN automation until all switches are up.
- LAN automation always begins on the active switch. When all switches in a stack are booted together, the switch with the lowest MAC address (assuming no switch priority is configured) becomes active. The switch with the second lowest MAC address becomes the standby, and so on. Some customers require the first switch to always be active. In this case, if all the switches are booted together and the first switch does not have the lowest MAC address, it does not become the active switch. To ensure that the first switch is active, boot the switches in a staggered manner: boot Switch 1; after 120 seconds, boot Switch 2, and so on. This approach ensures that the switch becomes active in the correct order—Switch 1 is active, Switch 2 is standby, and so on. However, after a reload, the order may change because switches obtain their role based on their MAC address.
- To make sure that the switches maintain their order after reload, it is a good practice to assign switch priorities to ensure that the switches always come up in the same order. The highest priority is 15. During LAN automation, the priority of active switch is set to 15 by default. The priority of other switches is not altered. When priorities are assigned, they take precedence over the switch MAC address. Assigning switch priorities does not change the NVRAM configuration. The values are written to ROMMON and persist after reload or write erase. Refer to this sample code:
3850_edge_2#switch 1 priority ? <1-15> Switch Priority 3850_edge_2#switch 1 priority 14 WARNING: Changing the switch priority may result in a configuration change for that switch. Do you want to continue?[y/n]? [yes]: y- You might have to clean up the switch after assigning priorities using “
pnpa service reset no-prompt“ - Connect PnP agents directly to seed devices. Do not connect PnP agents to any other network (for example, even the management network)
Interface Selection
consider four directly connected PnP agents: device 1 is connected through Gig1/0/10, device 2 through Gig 1/0/11, device 3 through Gig 1/0/12, and device 4 through Gig 1/0/13. If you choose Gig 1/0/11 and Gig 1/0/12 as discovery interfaces, LAN automation discovers only device 1 and device 2. If device 3 and device 4 try to initiate the PnP flow, LAN automation filters them because they connect through unselected interface.
You can also choose interfaces between the primary seed and the peer seed to configure with Layer 3 links. If there are multiple interfaces between the primary and peer seeds, you can choose to configure any set of these interfaces with Layer 3 links. If no interfaces are chosen, they aren’t configured with Layer 3 links.
You can reuse the same LAN pool for multiple LAN automation sessions. For example, you can run a discovery session to find the initial set of devices. After the session completes, you can provide the same IP pool for subsequent LAN automation sessions. Similarly, you can choose a different LAN pool for other discovery sessions. Make sure the LAN pool you select has enough capacity.
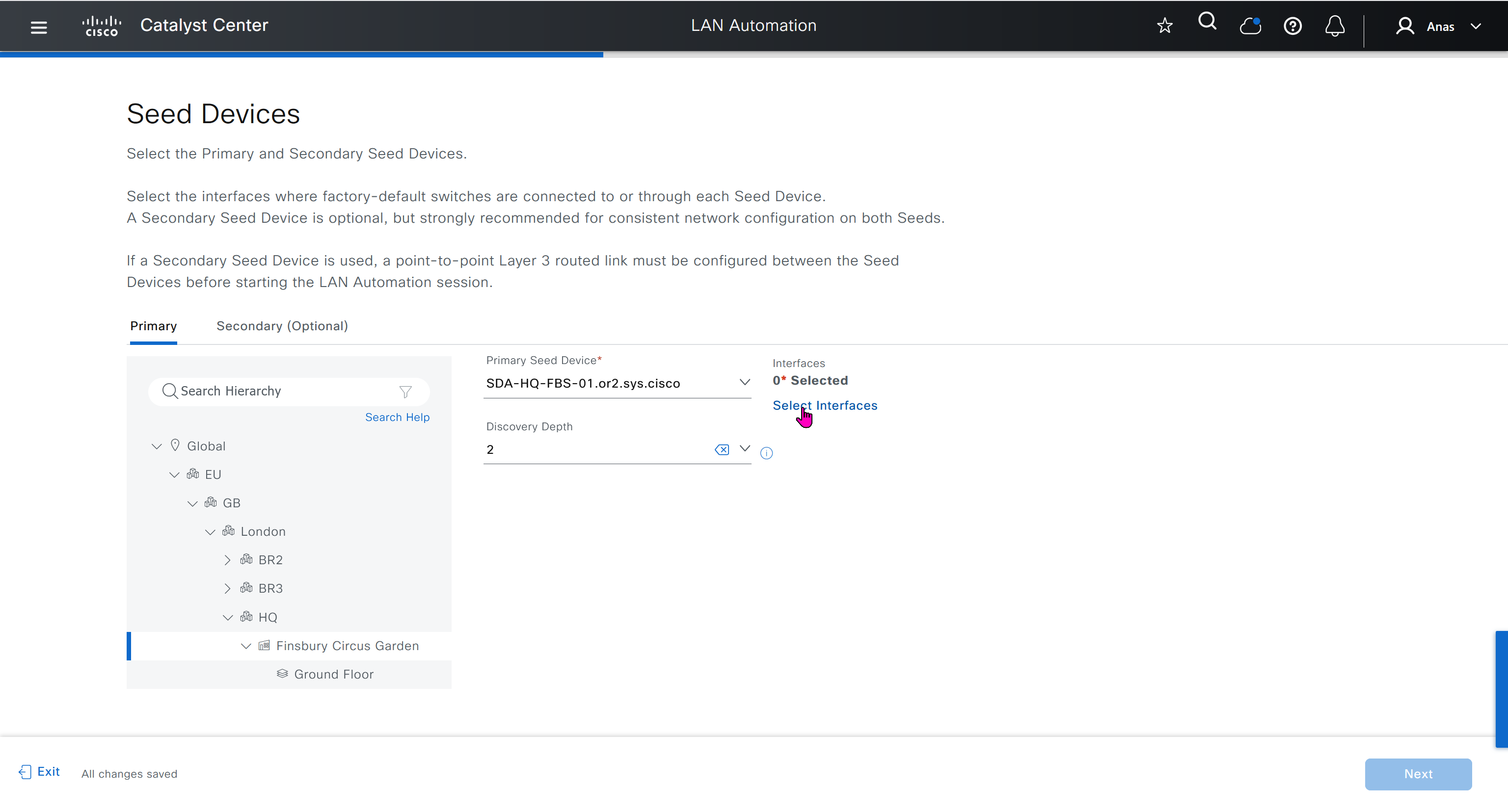

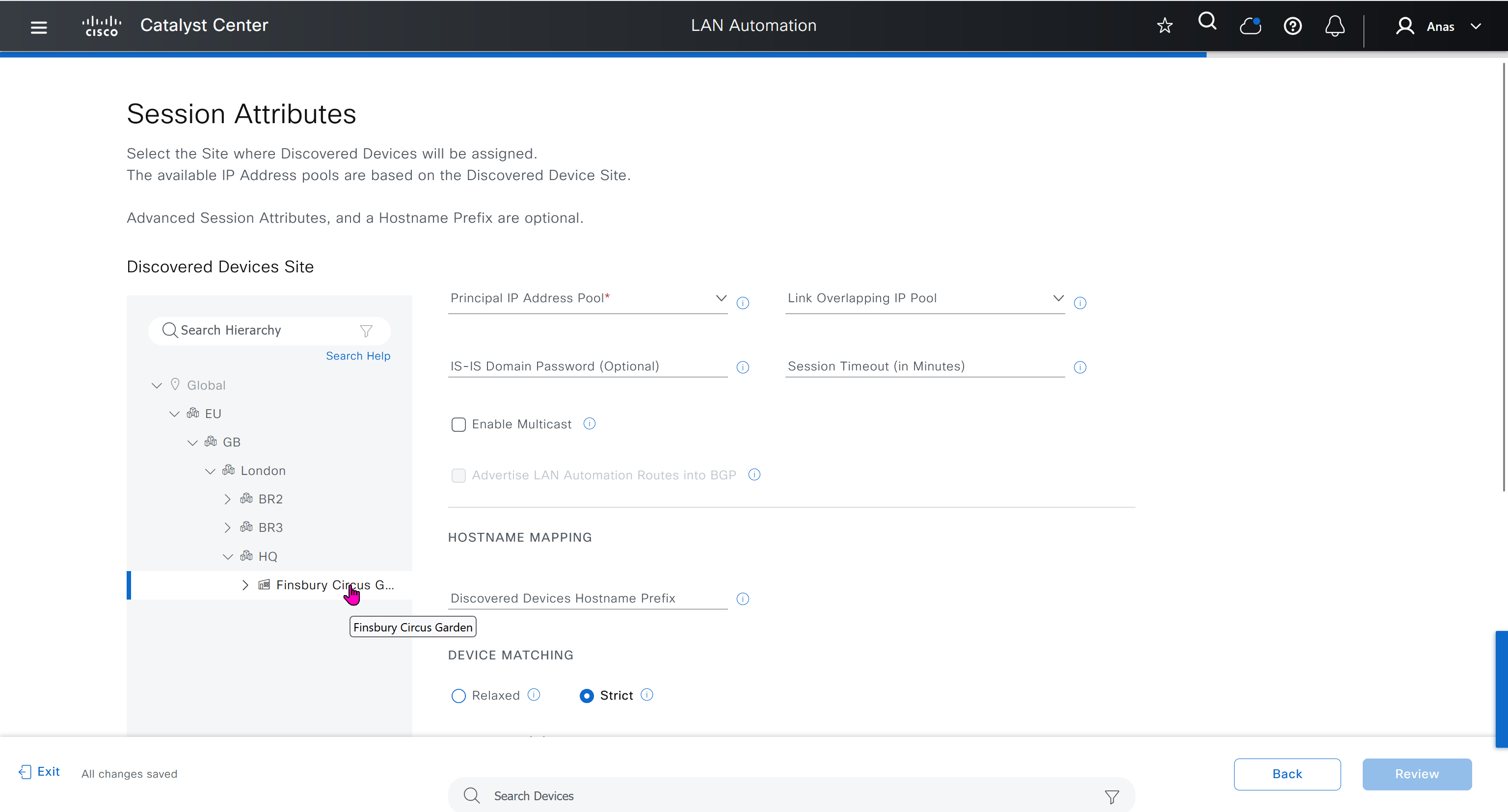
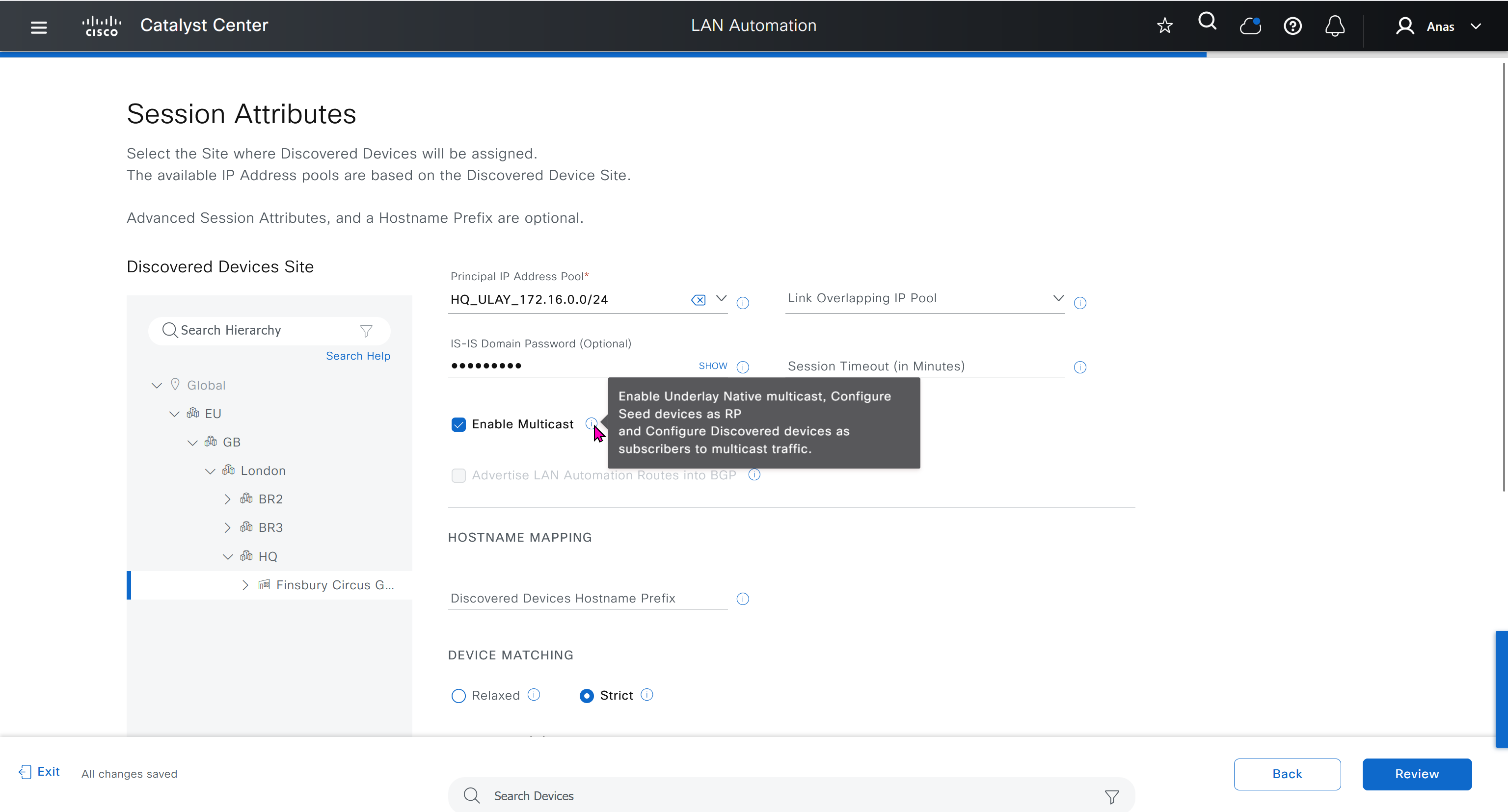


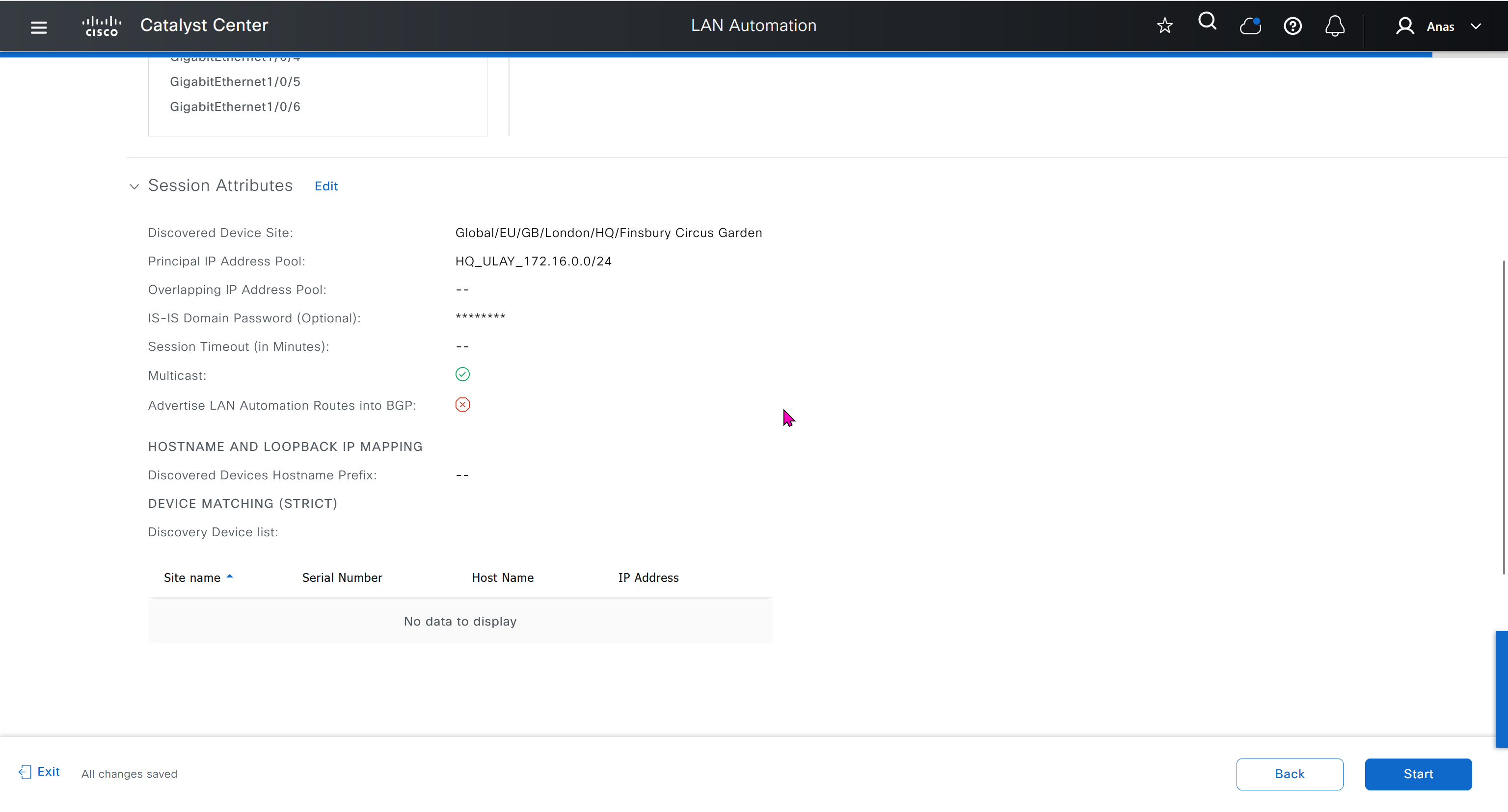
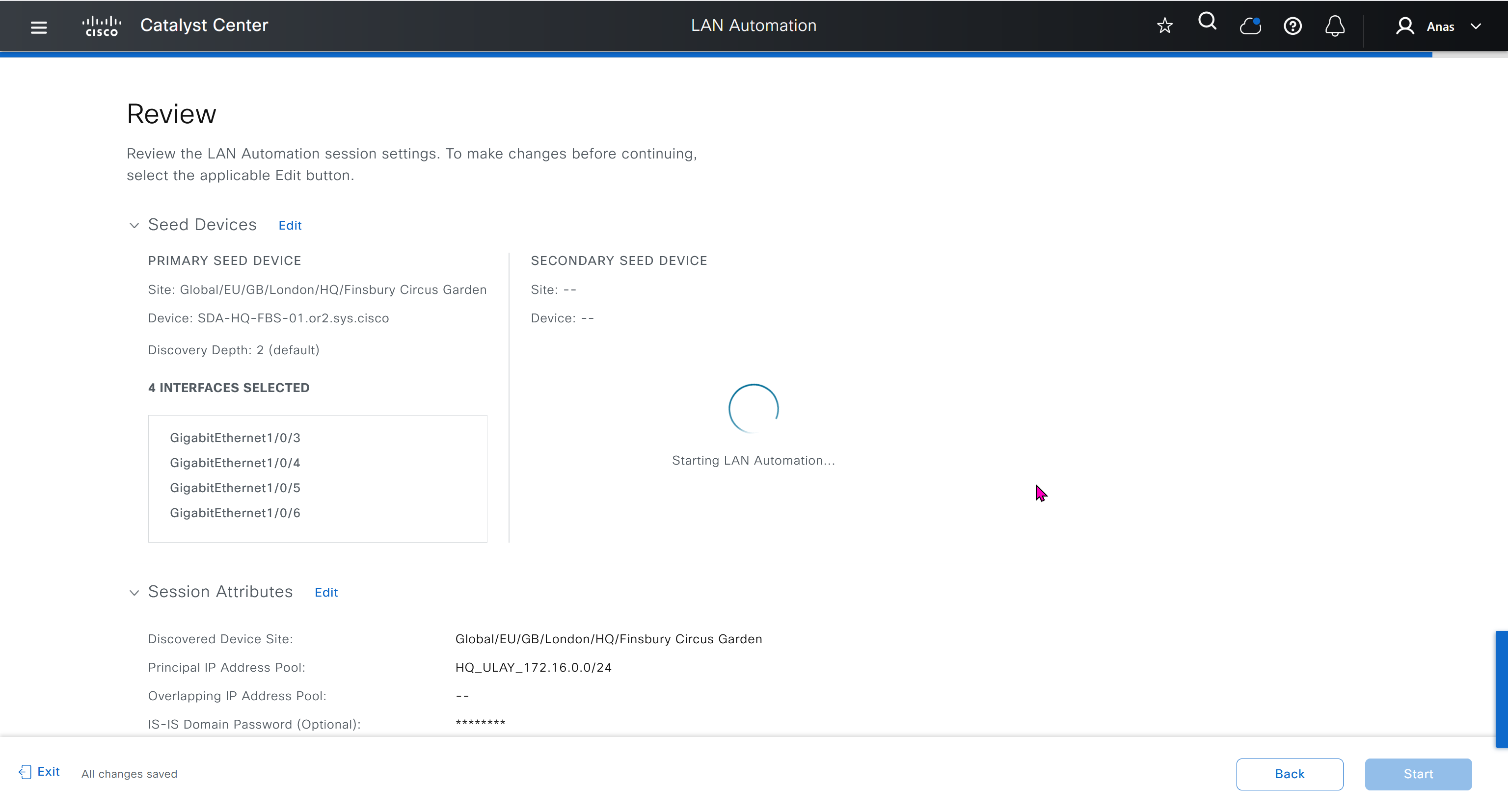
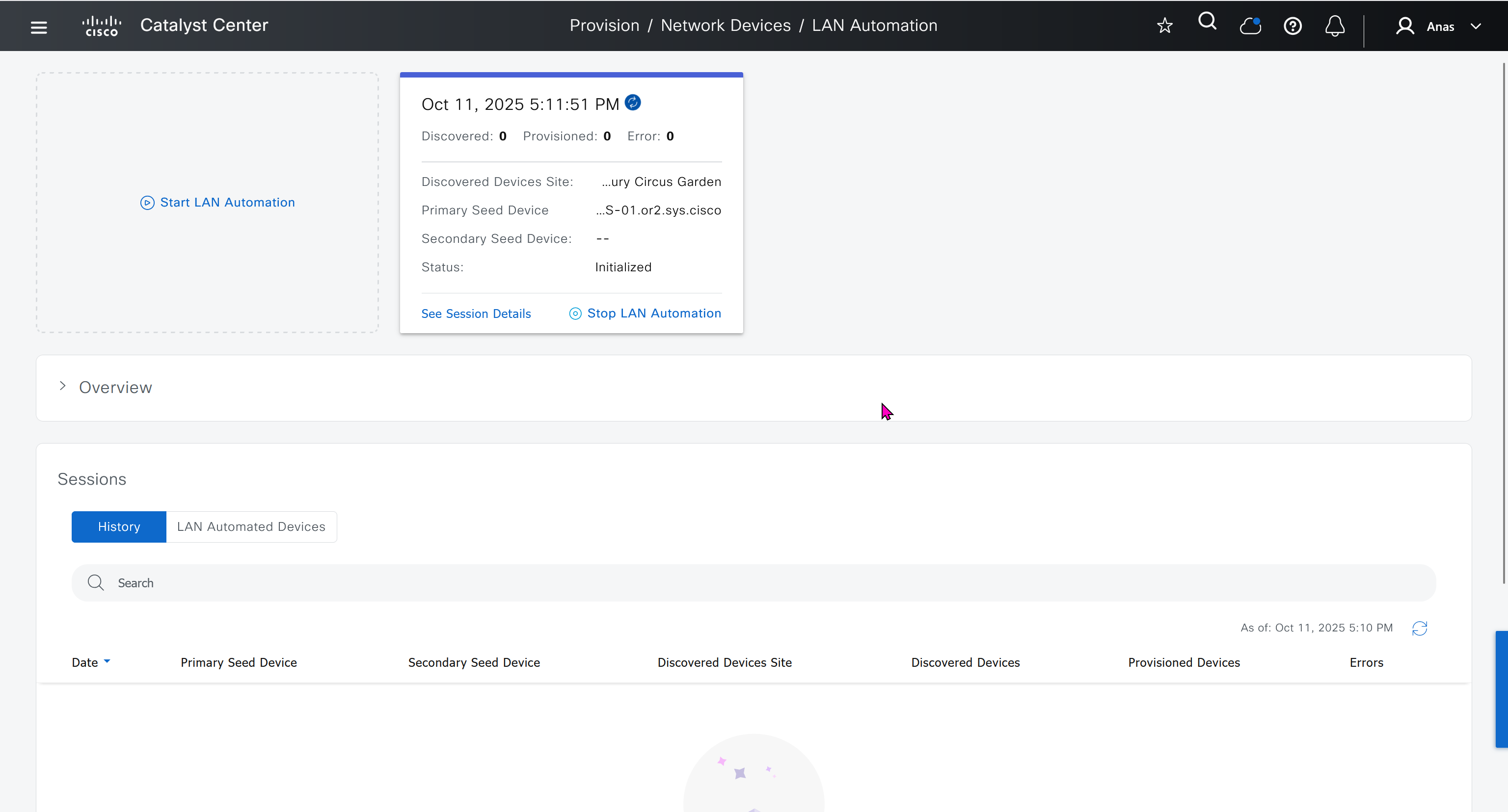
in order to catch all commands pushed by LAN automation to switches add below config and sync with DNAC
conf t
!
! Enable the archive feature
archive
log config
logging enable
notify syslog contenttype plaintext
hidekeys
!
! Optional: Set up where the archived configs are stored
path flash:config-archive
write-memory
!
end
!
! Ensure syslog logging is enabled (optional but recommended)
conf t
logging buffered 64000
service timestamps log datetime msec
!
end
write mem who
show user
! to see if DNAC is logged in and running commands
! to see commands
show logg | inc CFGLOG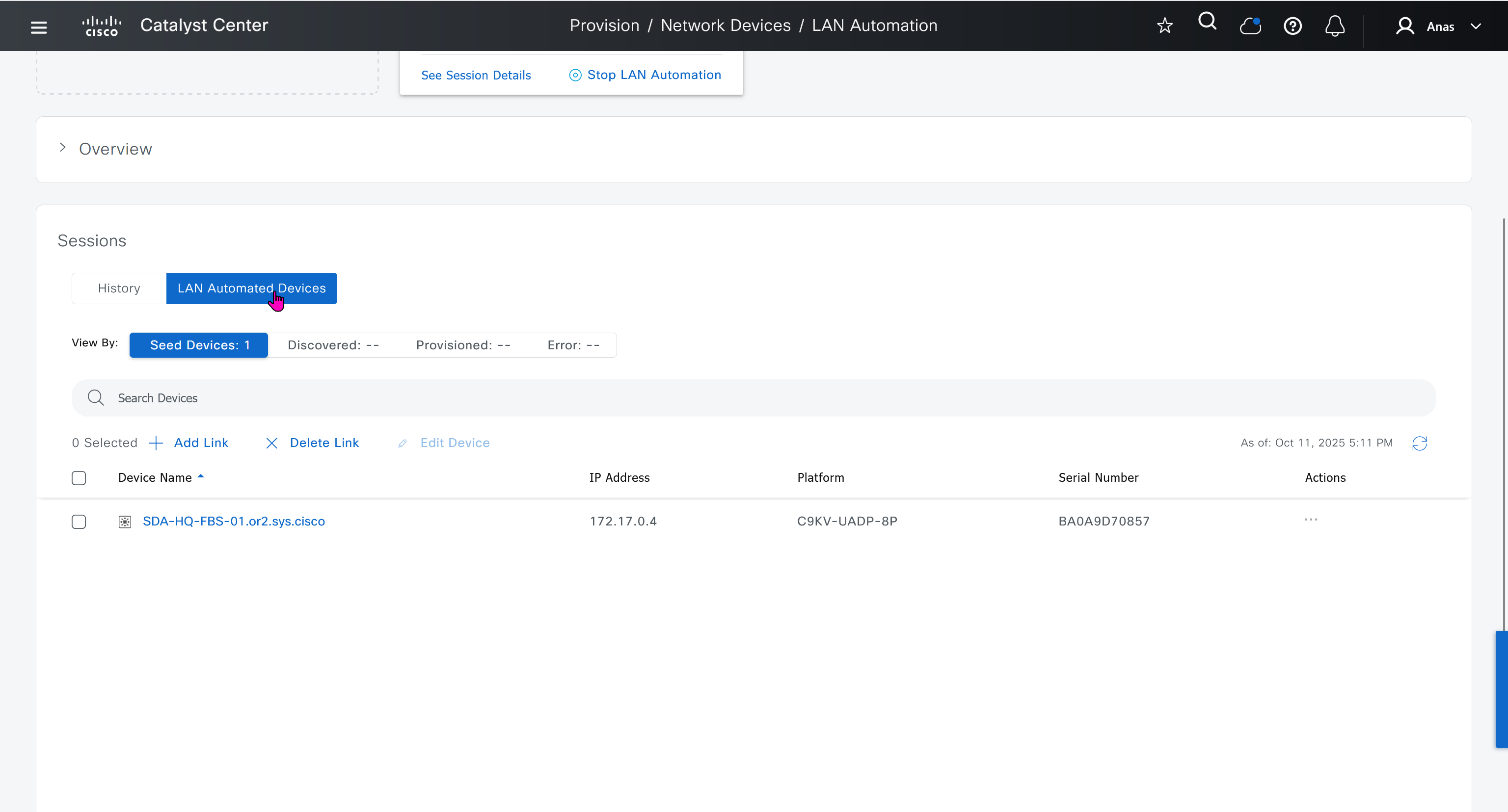
- Quickly as confiiguration is being deployed, intervene and remove using “no” following part of the configuration from “all” switches / routers
- router isis
net 49.0000.280e.ab15.fa02.00
is-type level-2-only
domain-password C0mplex30
metric-style wide
log-adjacency-changes
nsf ietf
bfd all-interfaces
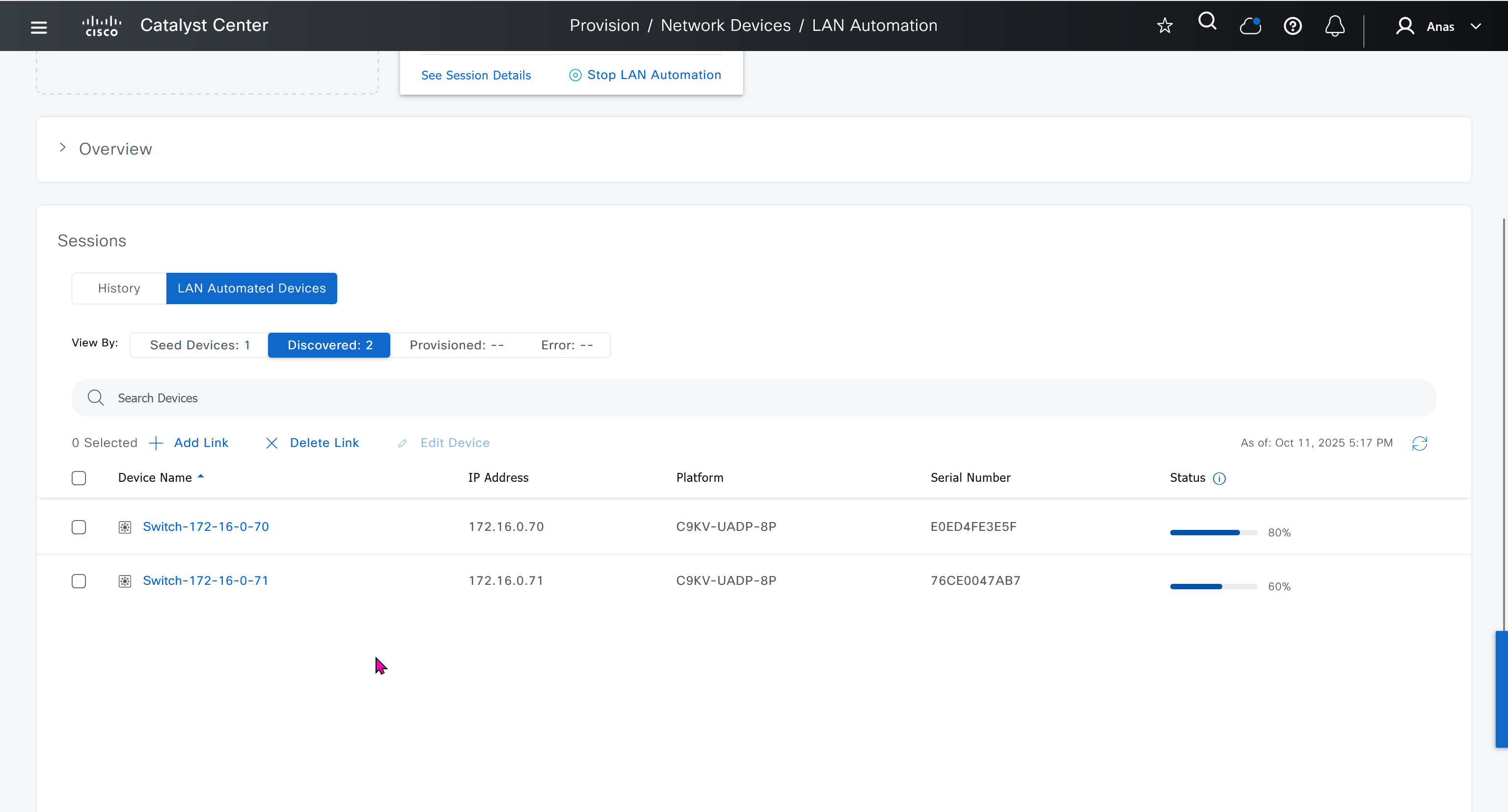


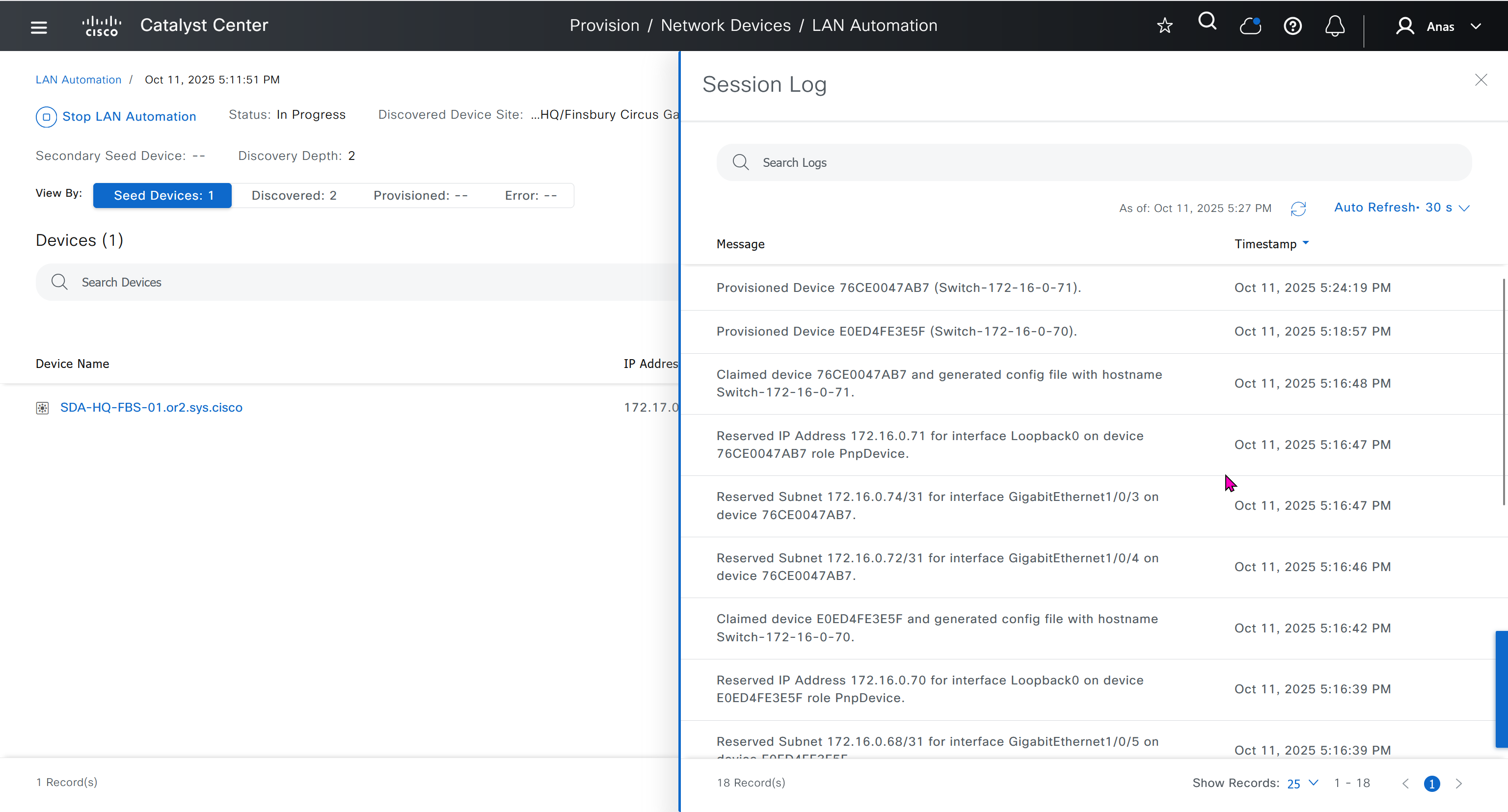
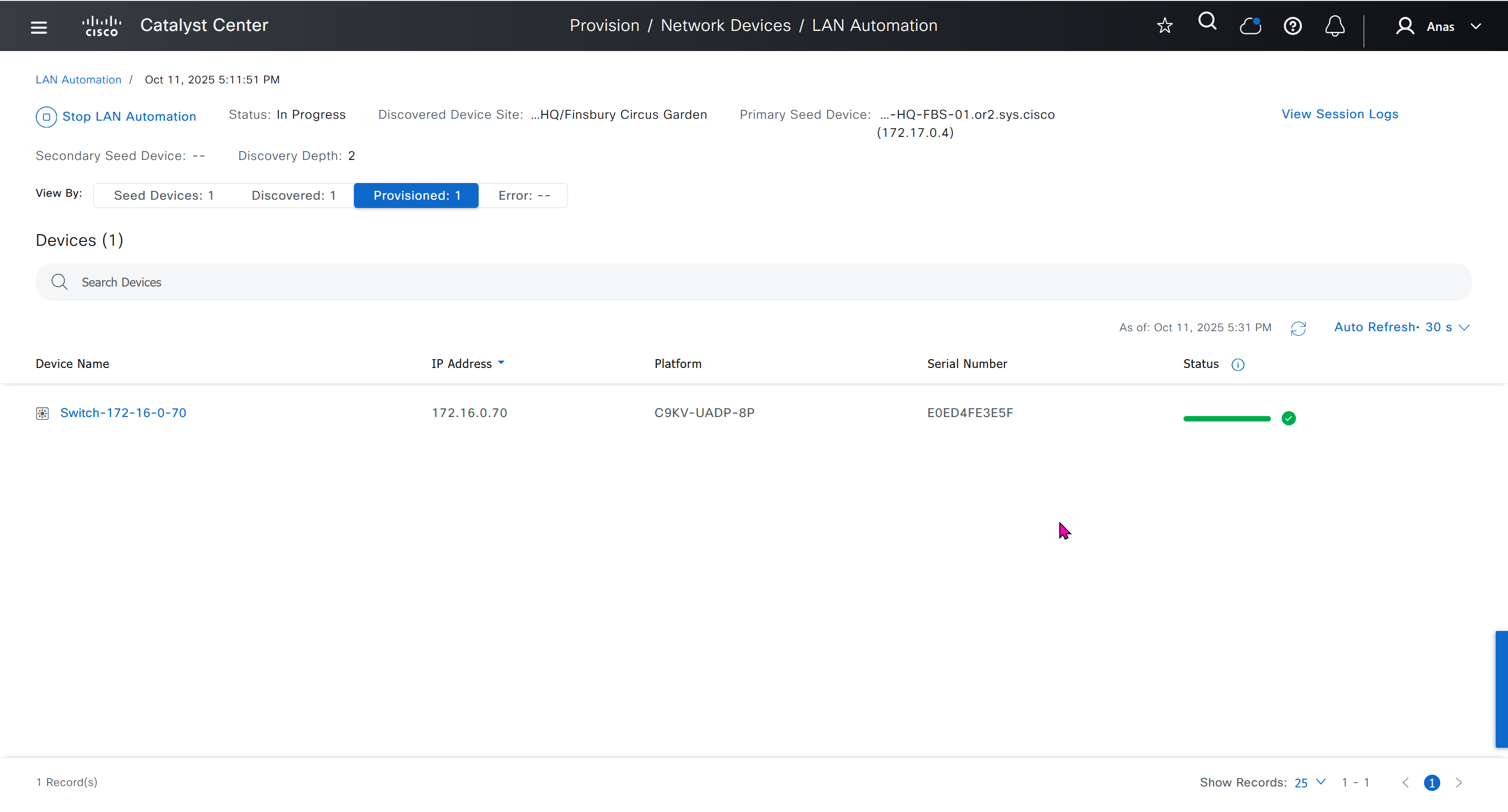
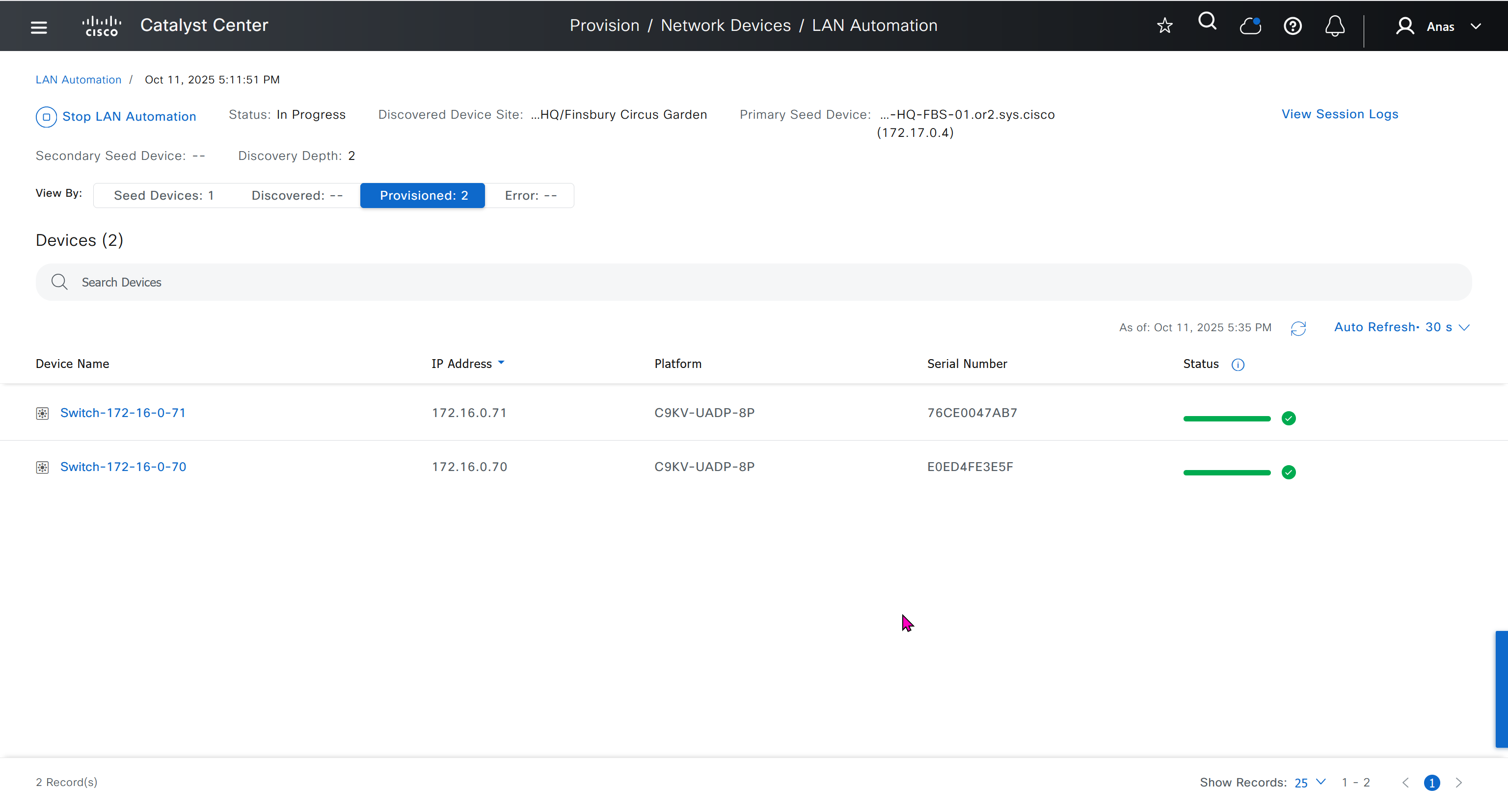


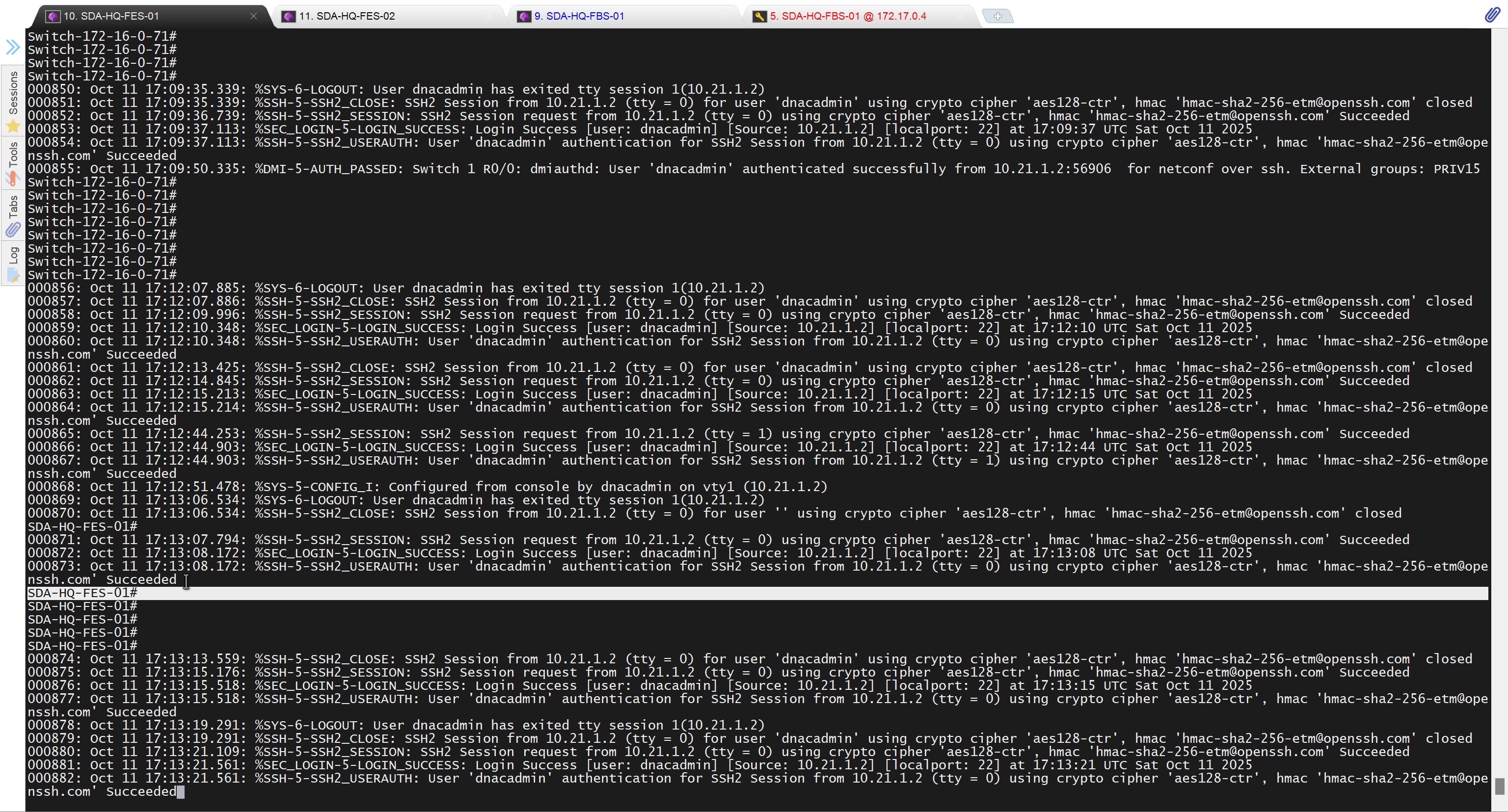
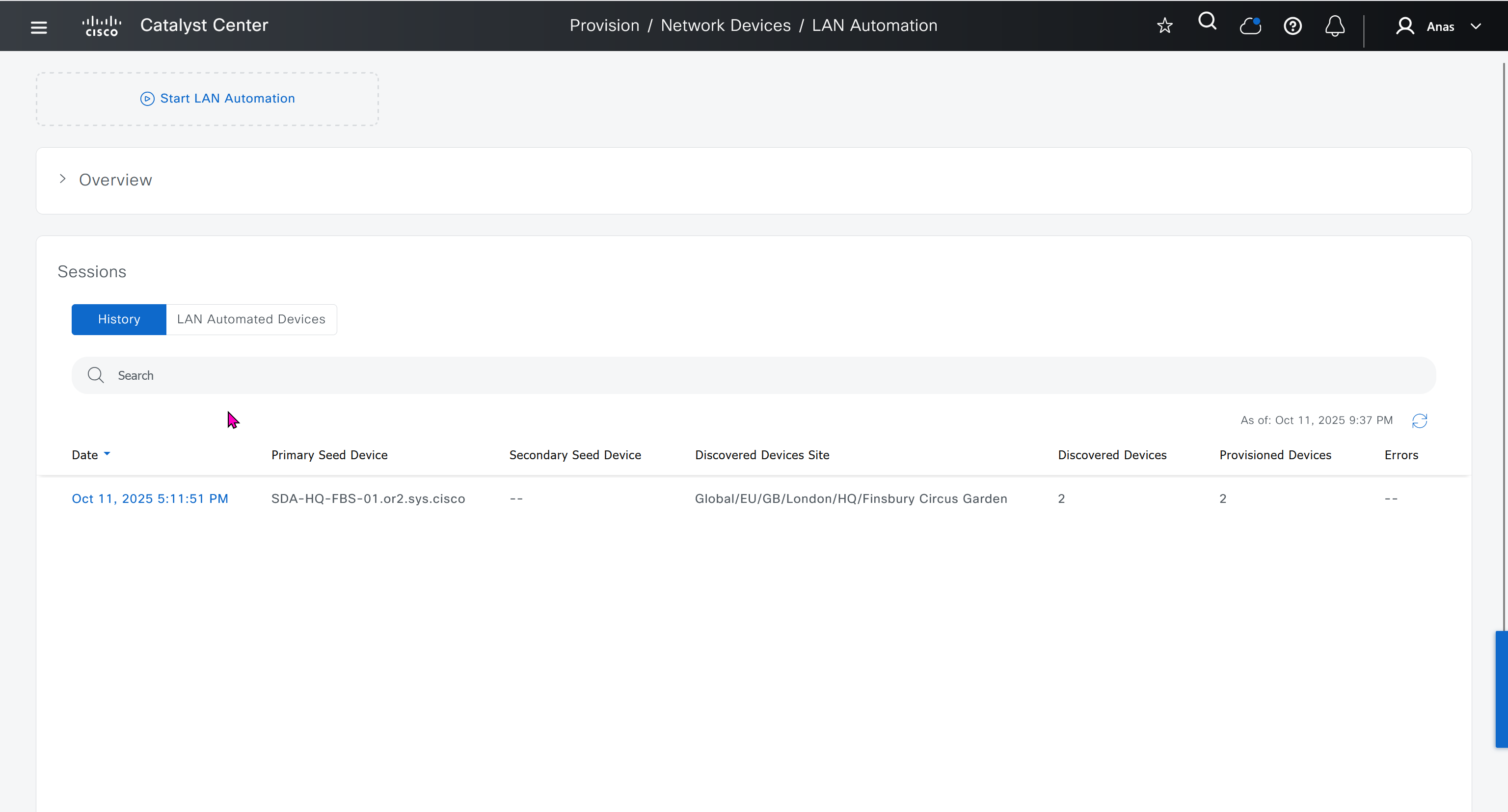
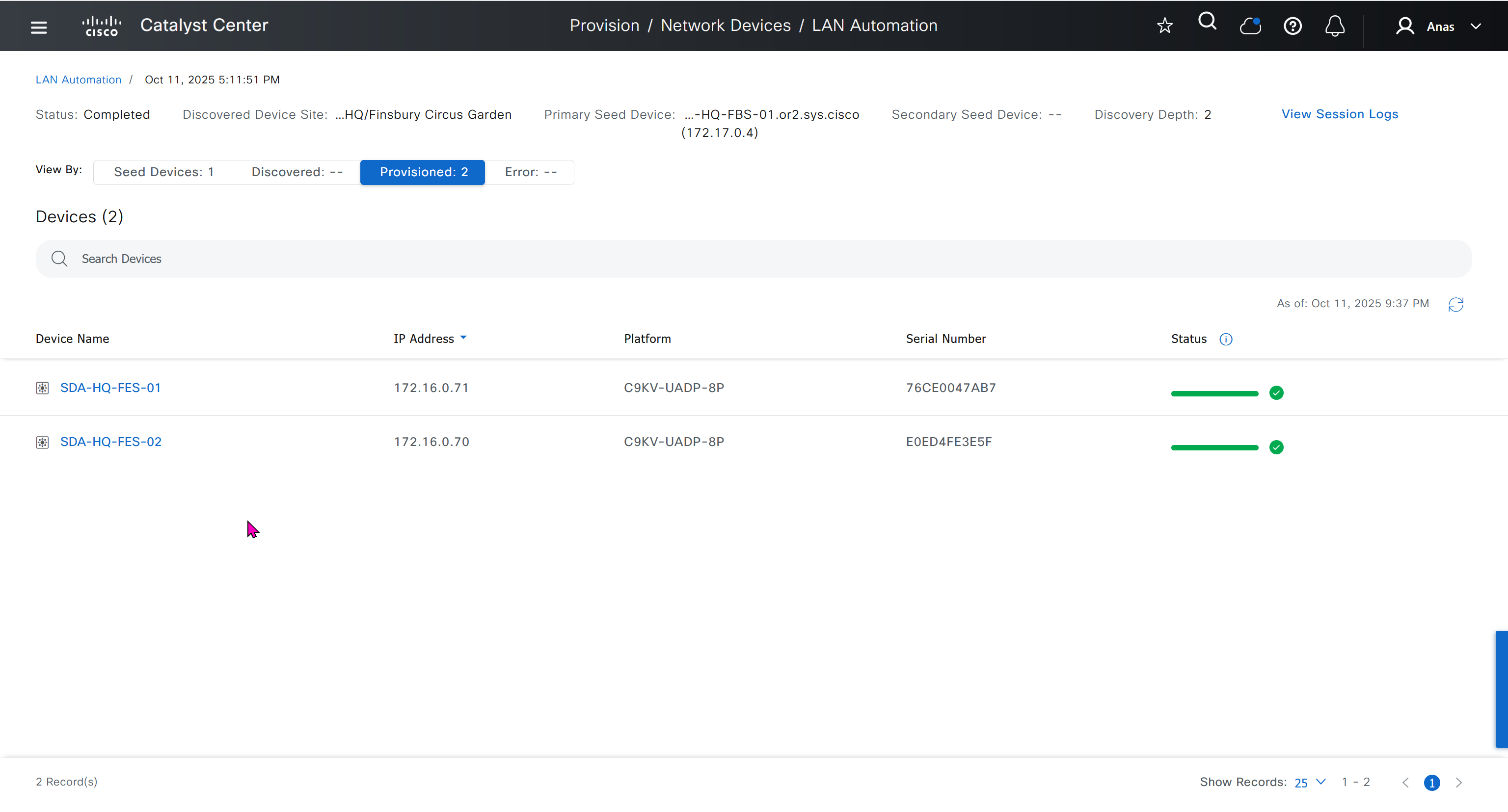
It takes long time to stop LAN automation
When the LAN automation process stops,
the discovery phase ends, and all point-to-point links between the seed and discovered devices and between the discovered devices (maximum of two hops) are converted to Layer 3.








Add a static route for LAN pool on DNAC through Enterprise facing interface
Skipped but complete it for CCIE LAB
next post
SDA LM 2 – Network Design
Videos
Network Design
An area represents the geographical location such as country, city or campus (regardless of the size of area), next level is building which represents physical structure, there cannot be buidling inside a building
Cisco recommends the hierarchy as Continent > Country > City > Campus > Buildings
This is how you are on safe side and covered for any future locations and changes with flexibility built in as it can difficult to adjust the hierarchy later on once everything is configured
For example, today you are domestic but tomorrow you might go international and open new offices in new country / continent

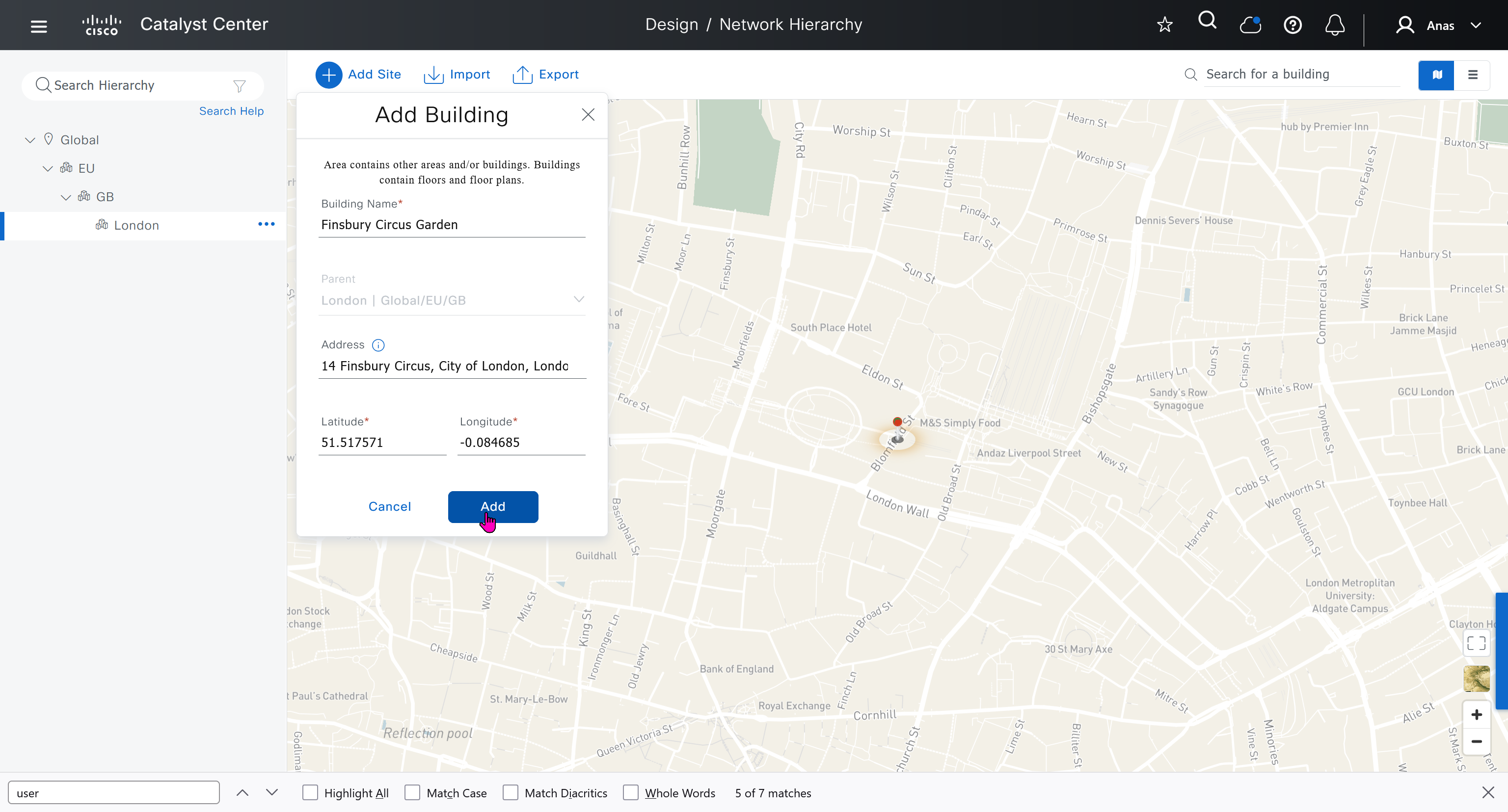
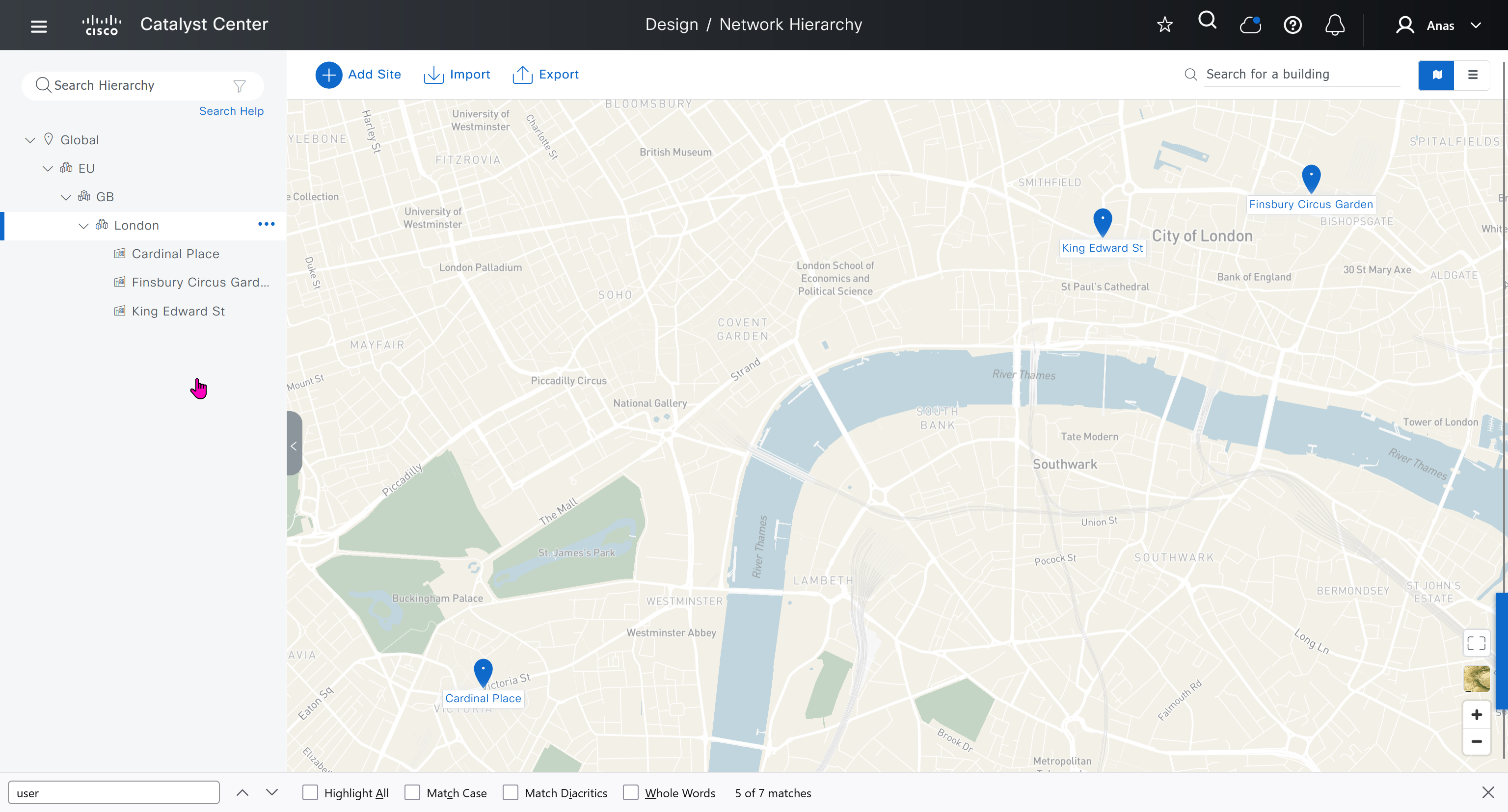
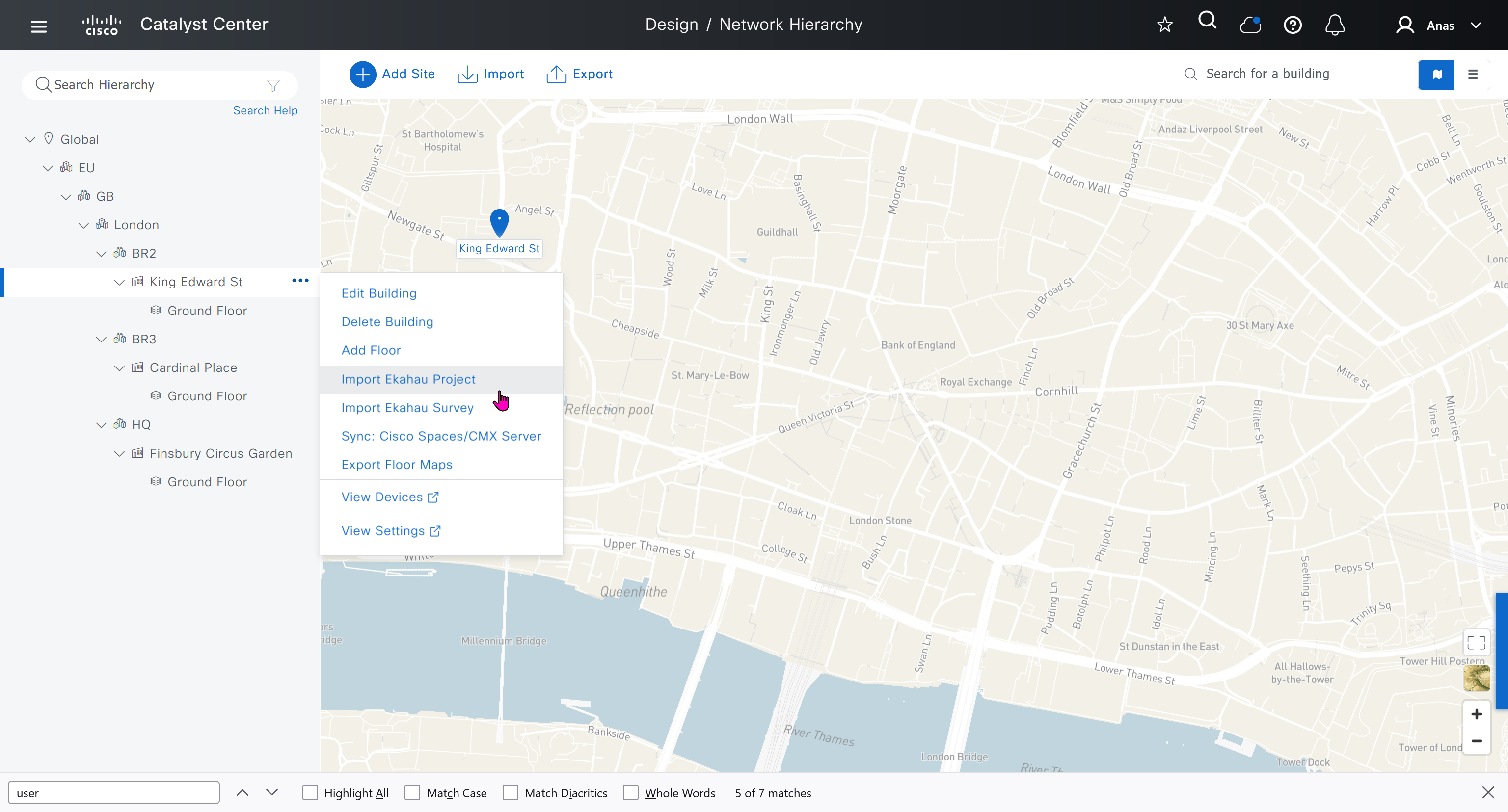
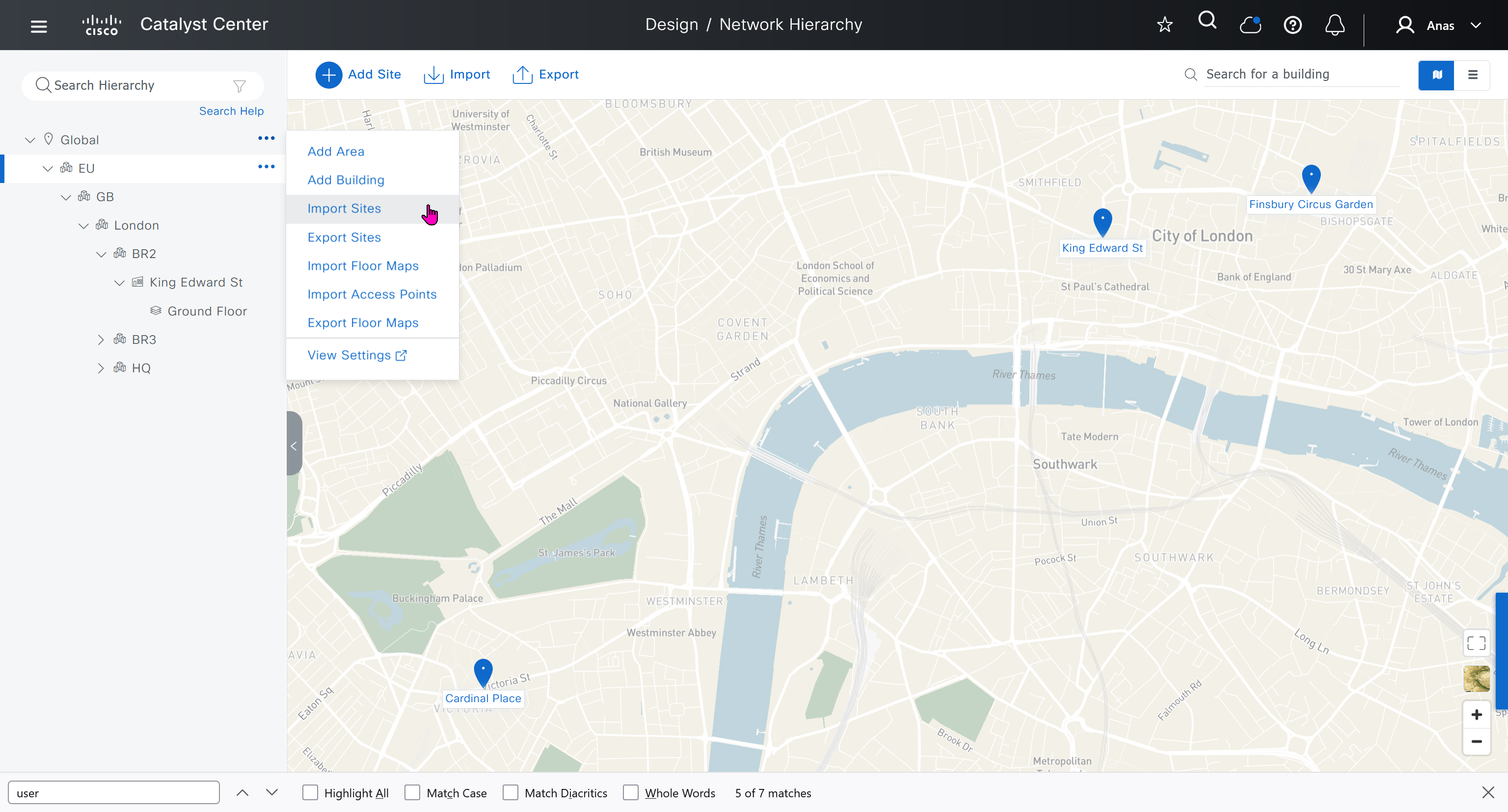
We will create 3 sites in EU > GB > London
- Finsbury Circus Garden, 14 Finsbury Circus, London EC2M 7EB
- 2, 7 King Edward St, London EC1A 1HQ
- Cardinal Place, 84 Victoria St, London SW1E 5JL
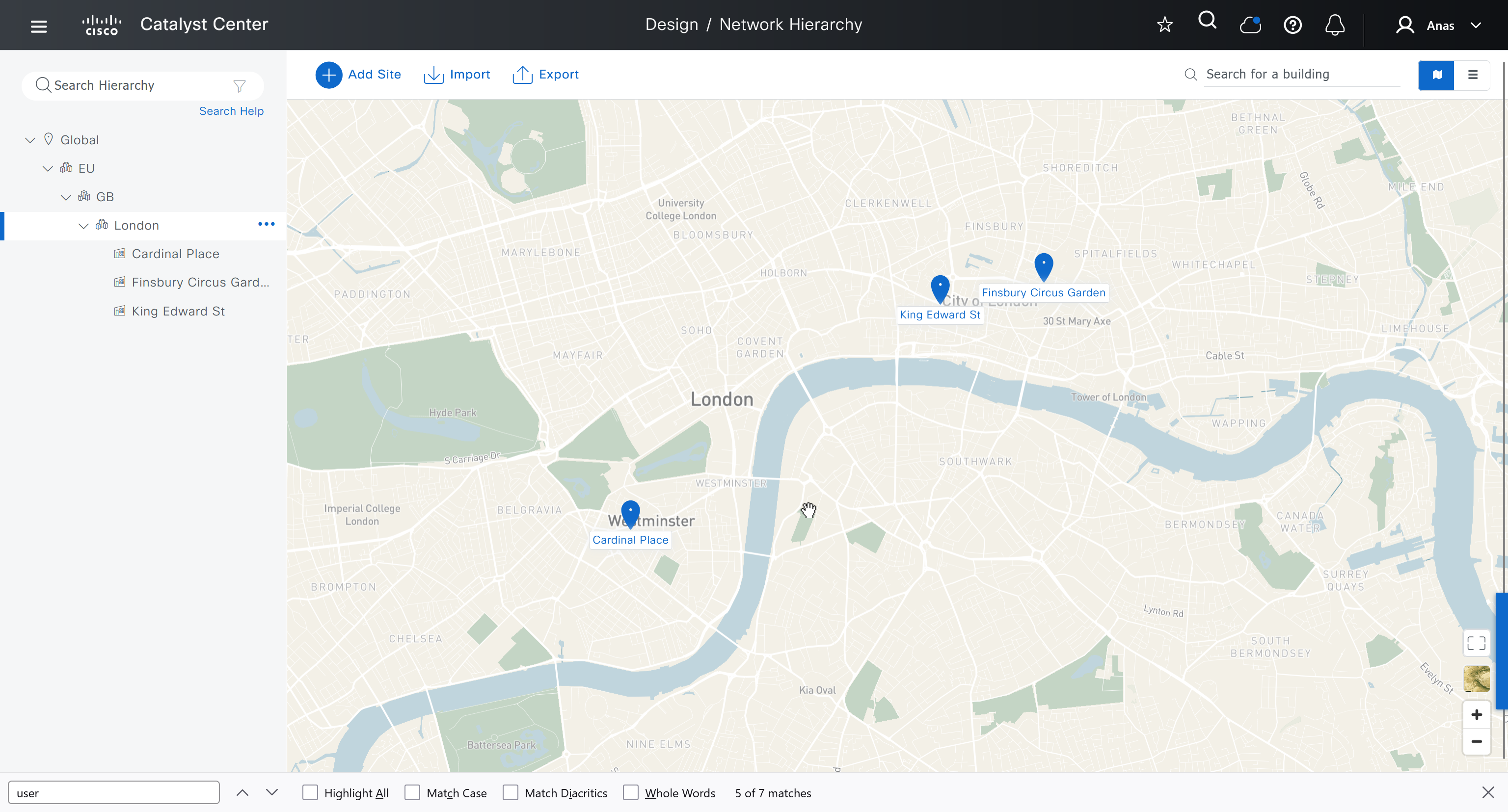

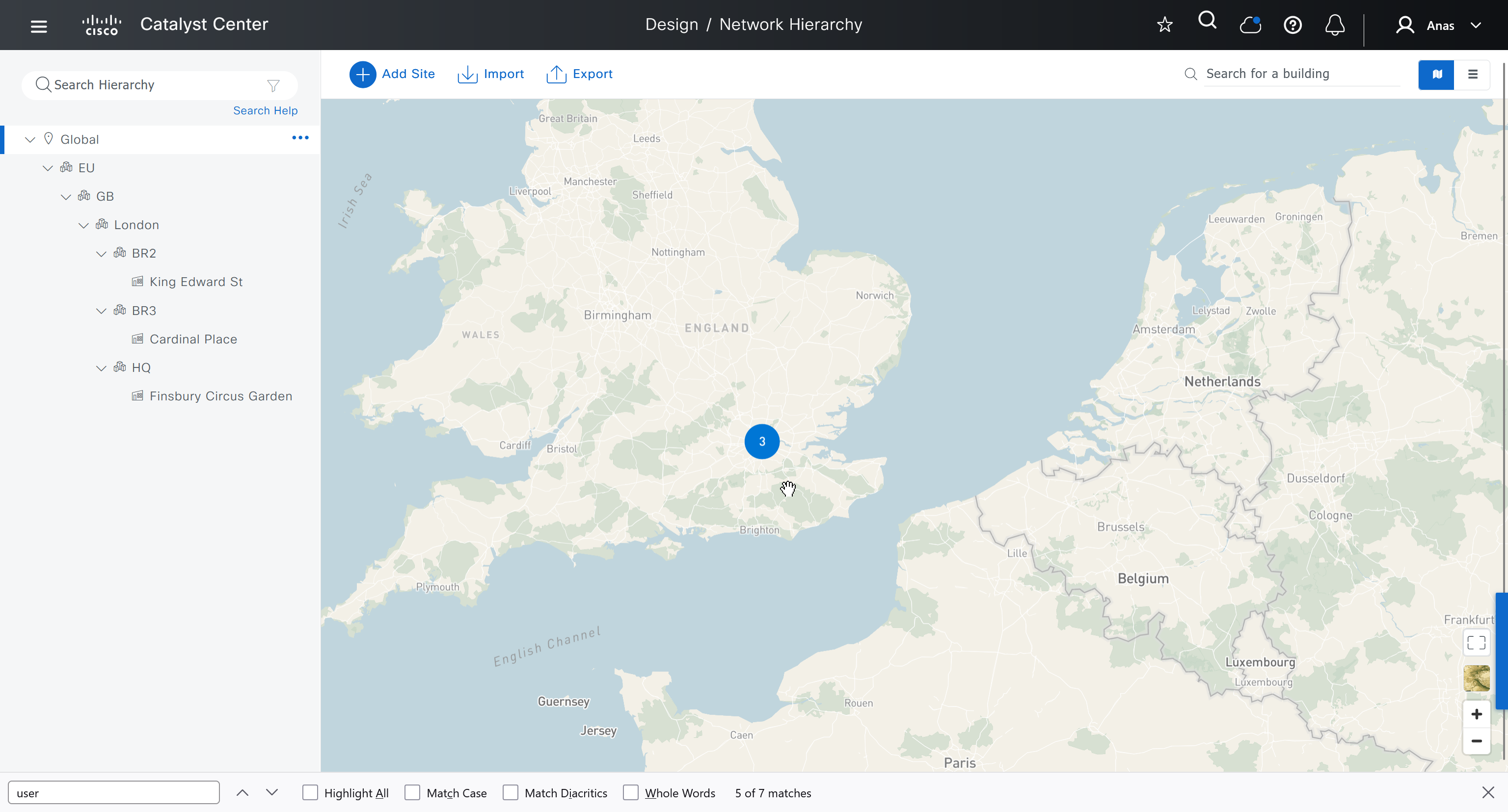
We should add HQ, BR2 and BR3

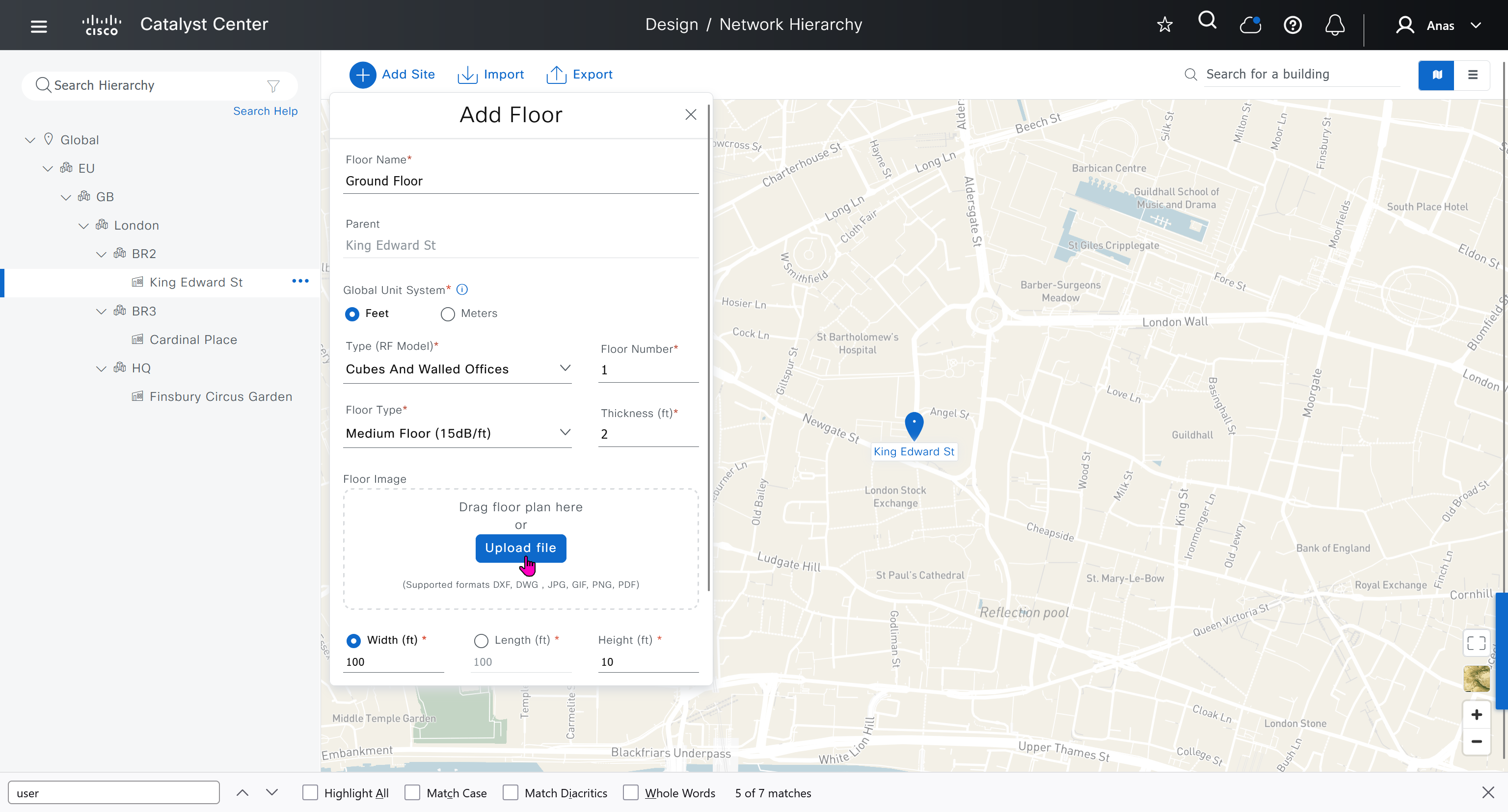
We can add floors and floors are mostly used for placing wireless access points but for SDA we can add ground floor, if customer had prime we can import APs on floor plans already from prime
for RF model on the floor just stick with default of “Cubes And Walled Offices”
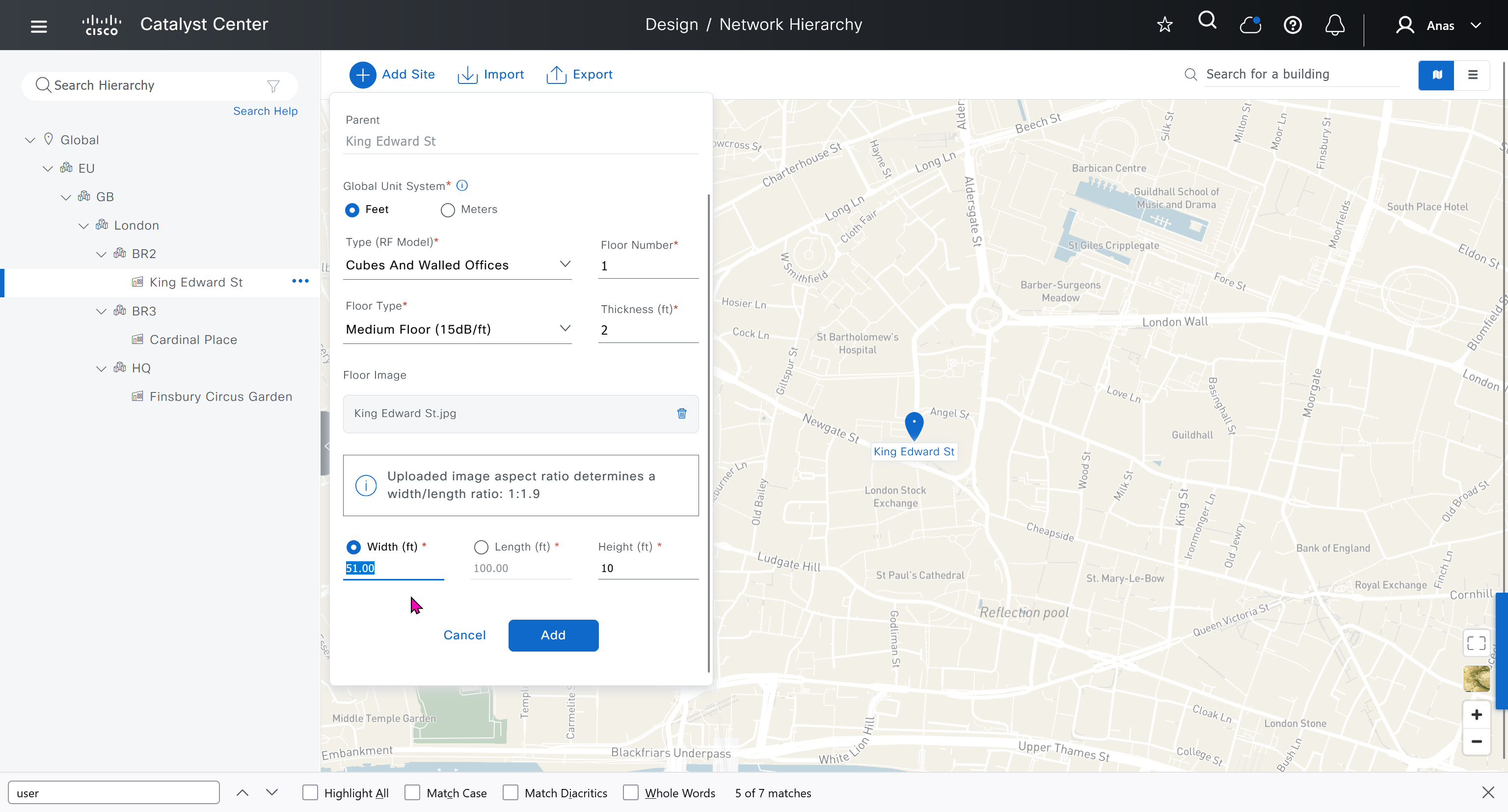
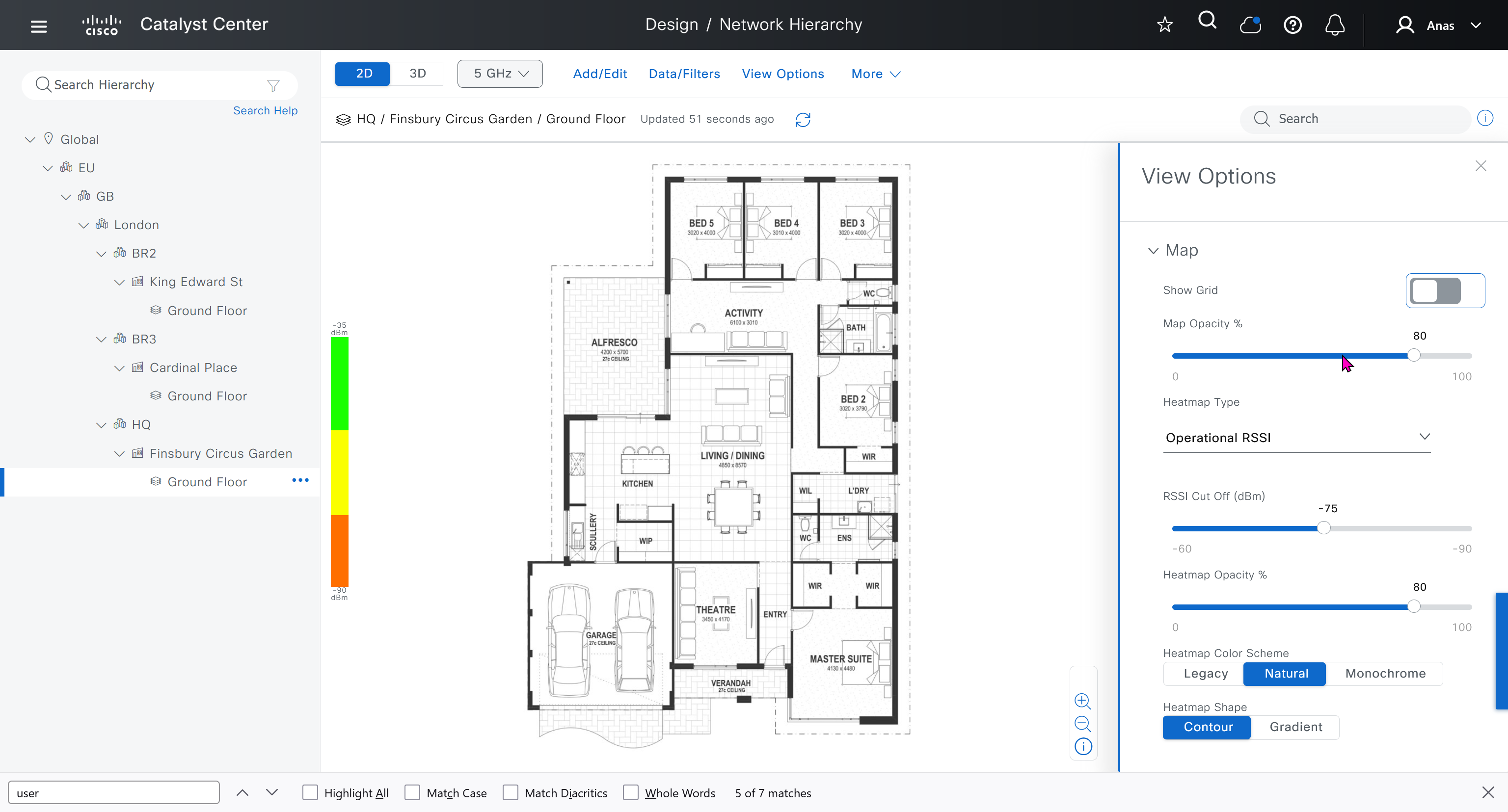
see that when I changed width, dnac maintained the aspect ratio from the image I uploaded

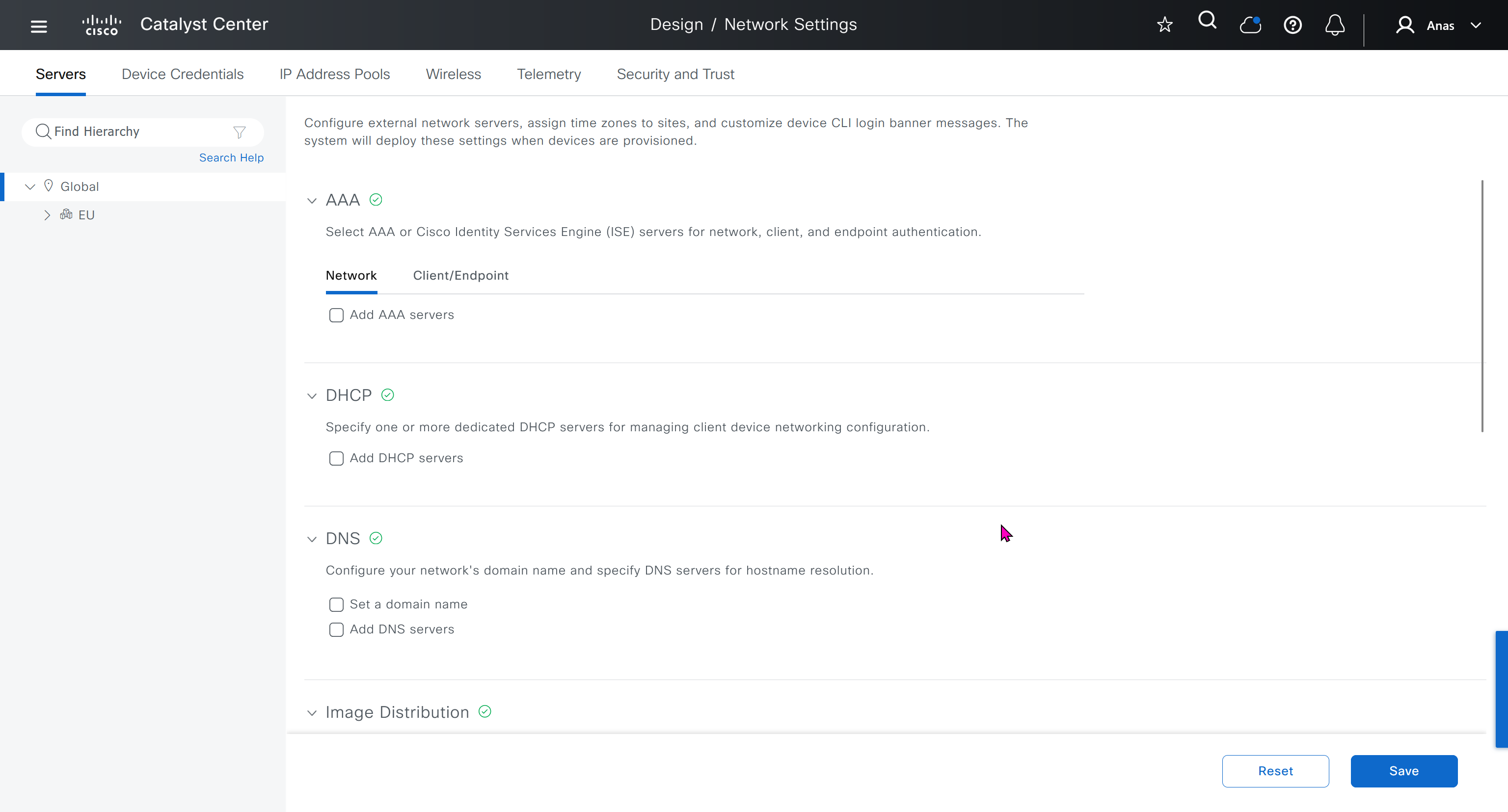
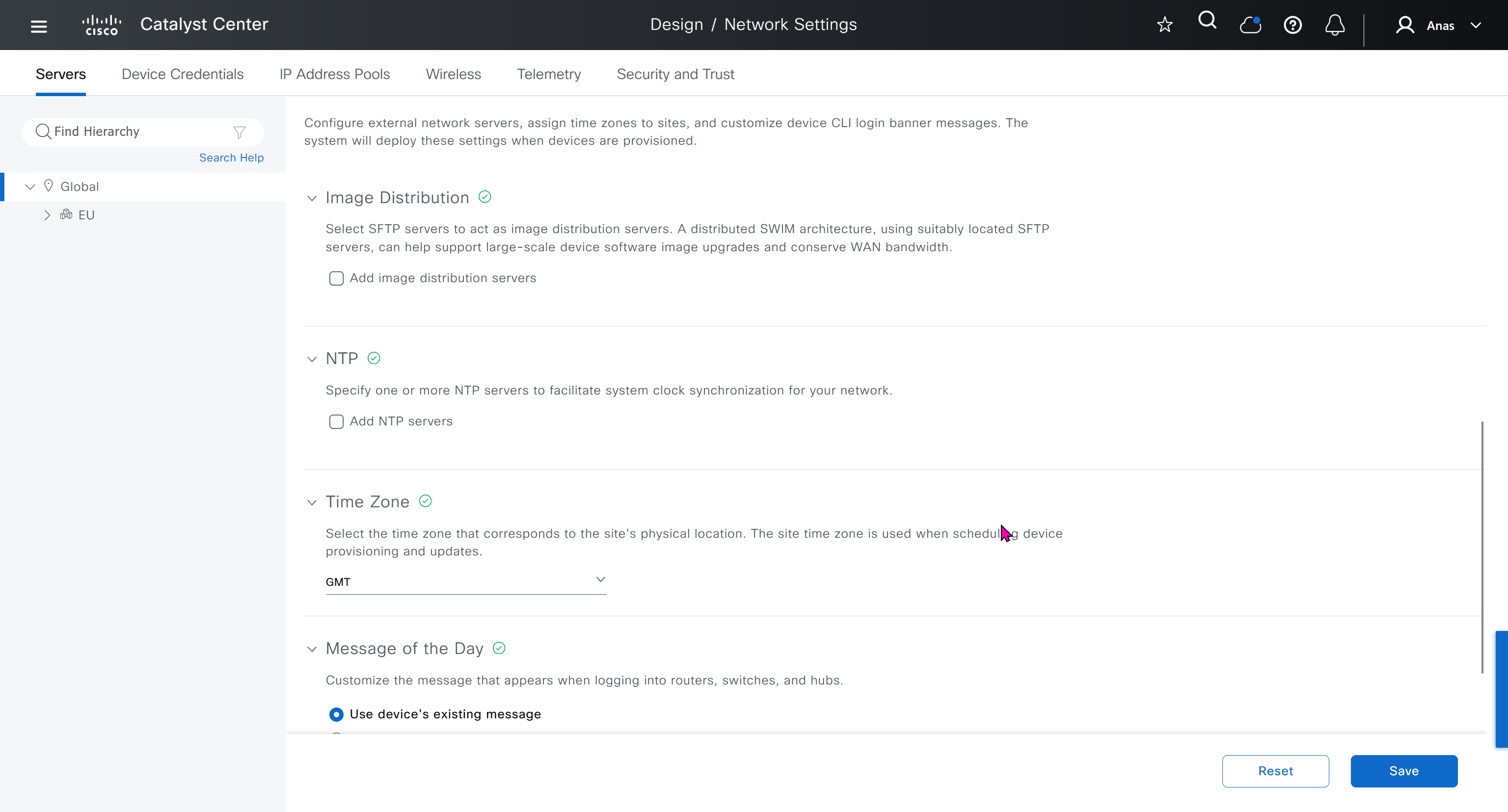
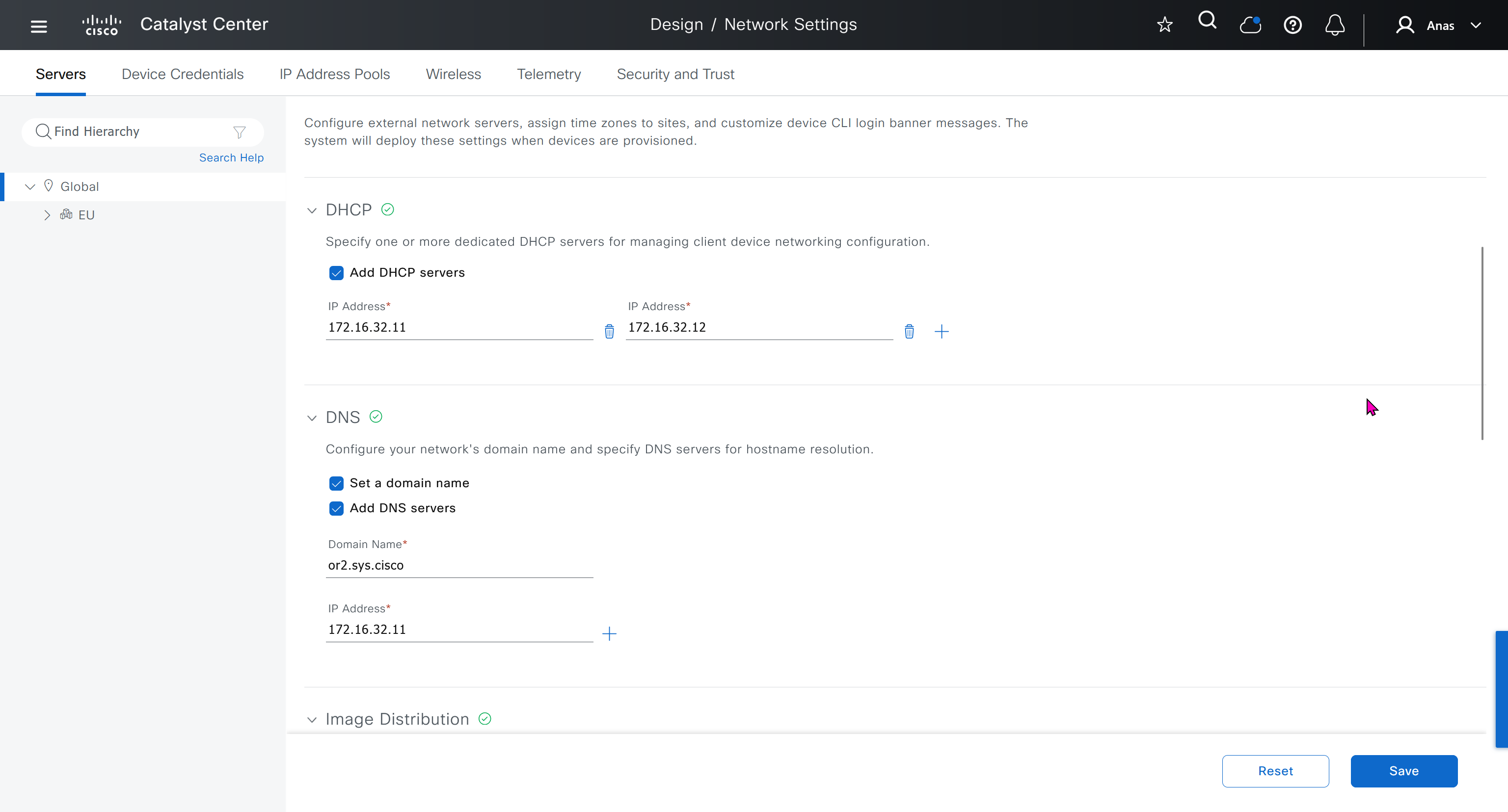
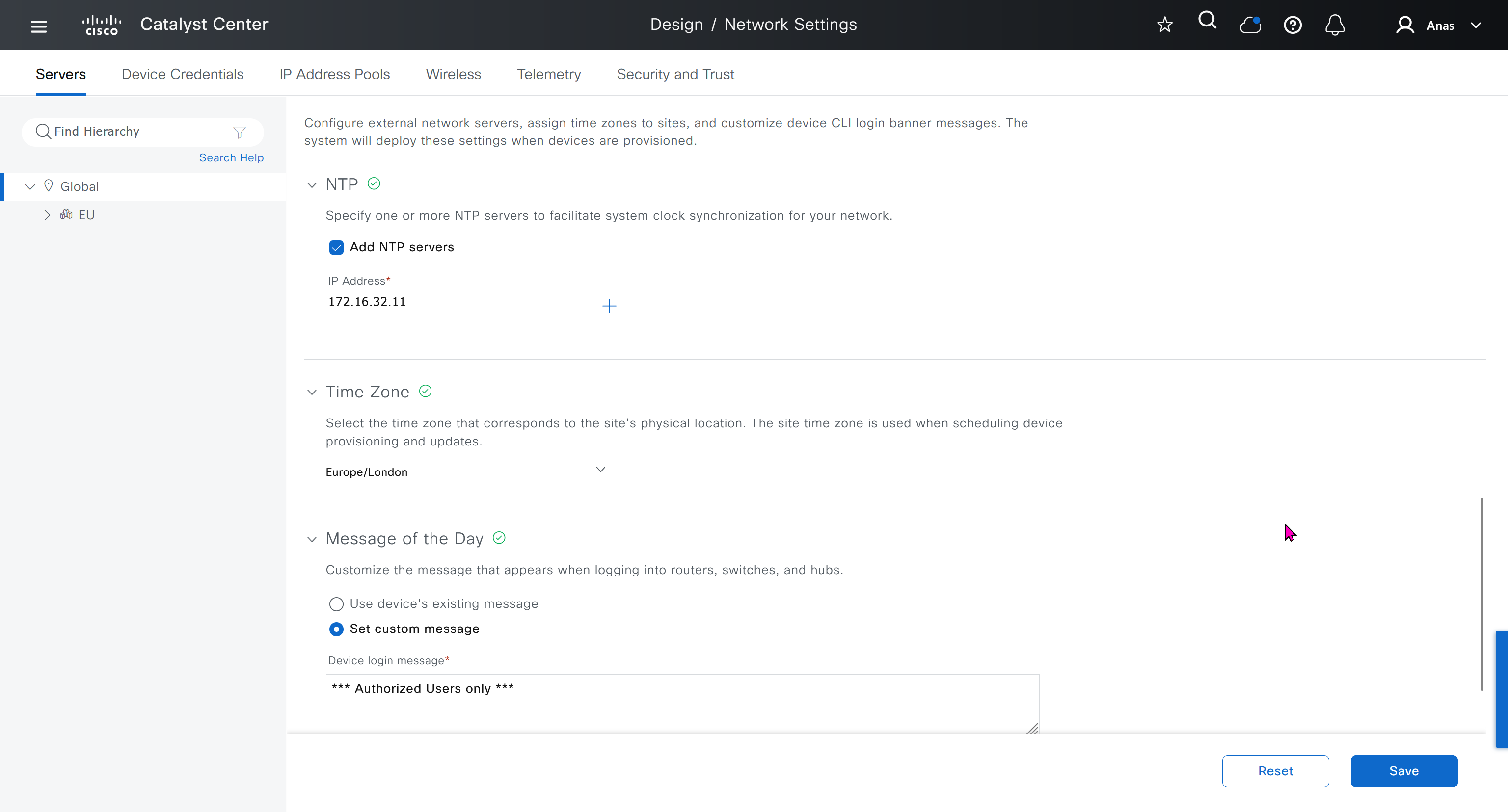
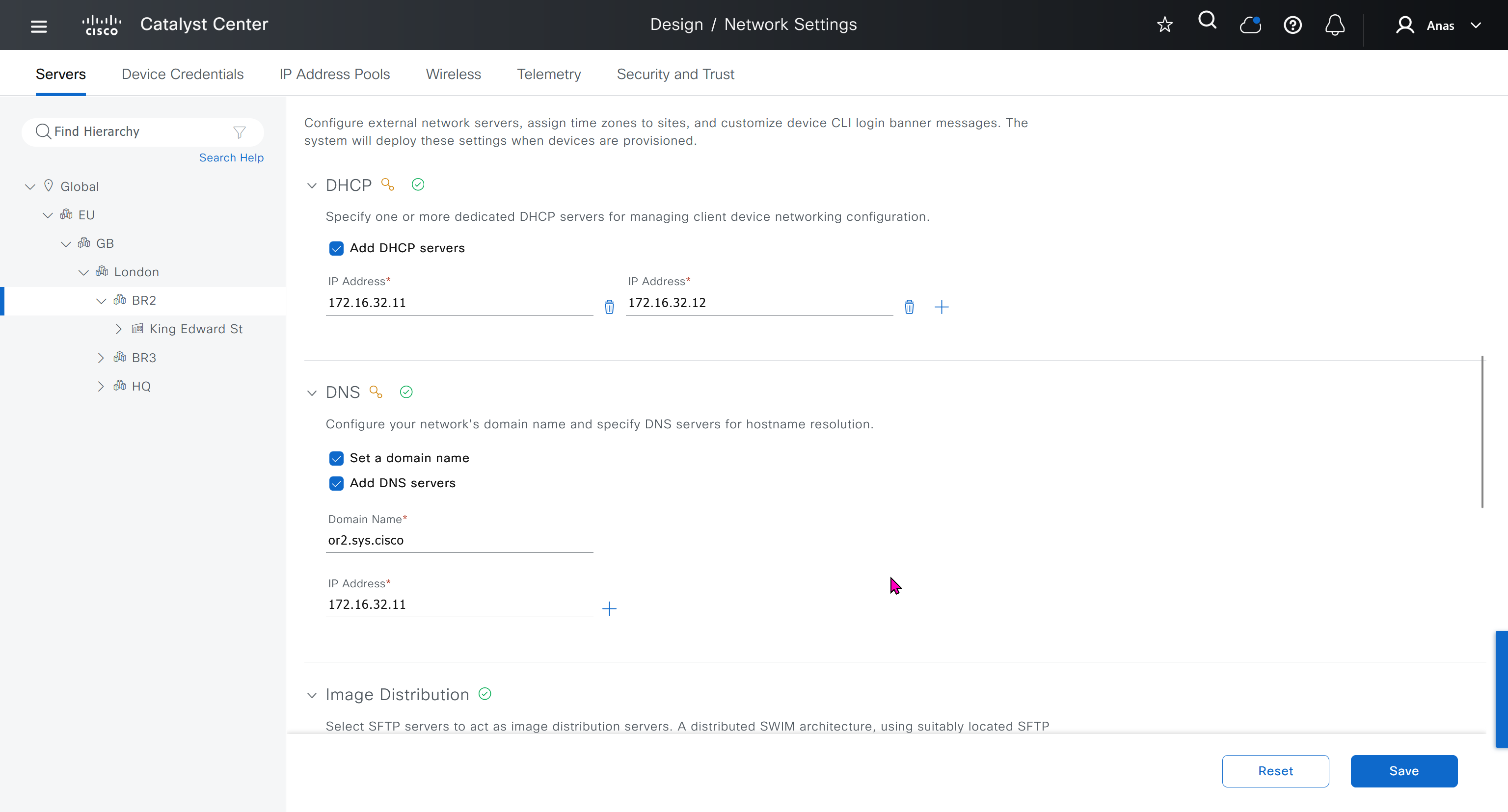
Network contains common settings similar to what DHCP contains but more such as AAA server, DHCP server, DNS server, Image Distribution (used to download the Catalyst IOS XE image), NTP server, Time Zone and Message of the day but looking at it feels like that this configuration is for the switches because this is the configuration that will be pushed to devices as they get provisioned into DNAC
In DHCP servers section we will also specify ISE IP address because it is one of the ways for ISE to perform profiling based on DHCP request from device
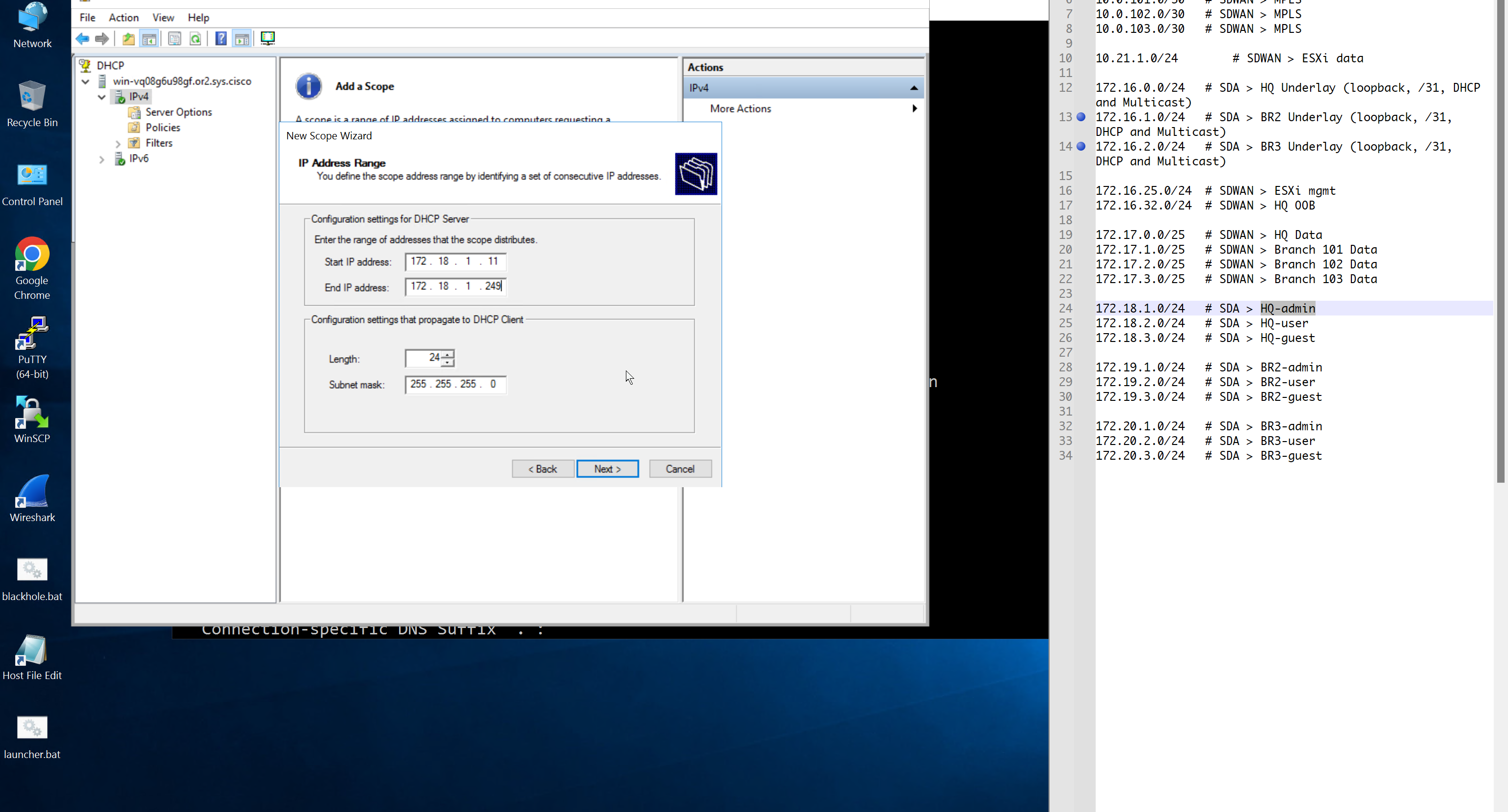
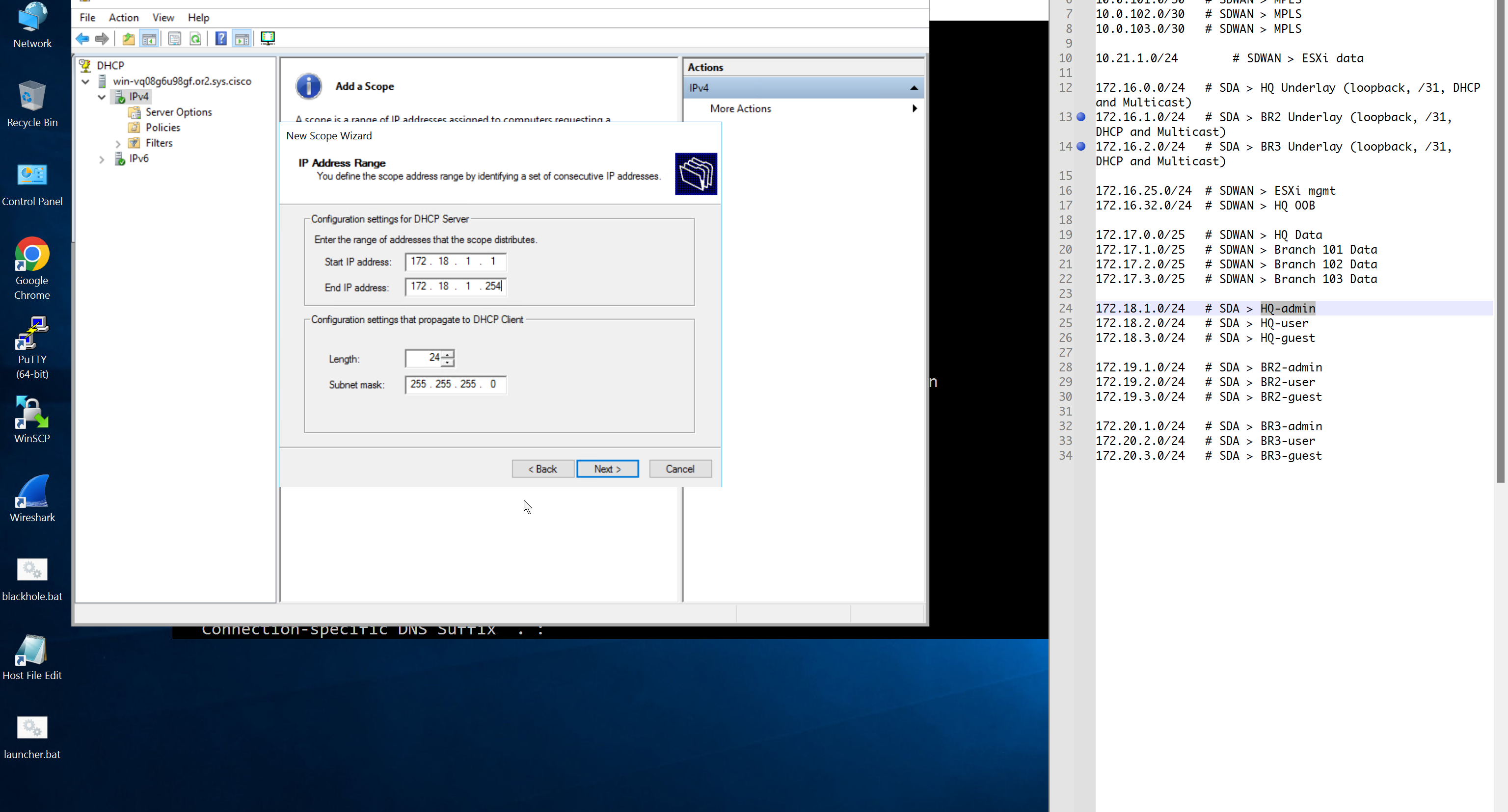
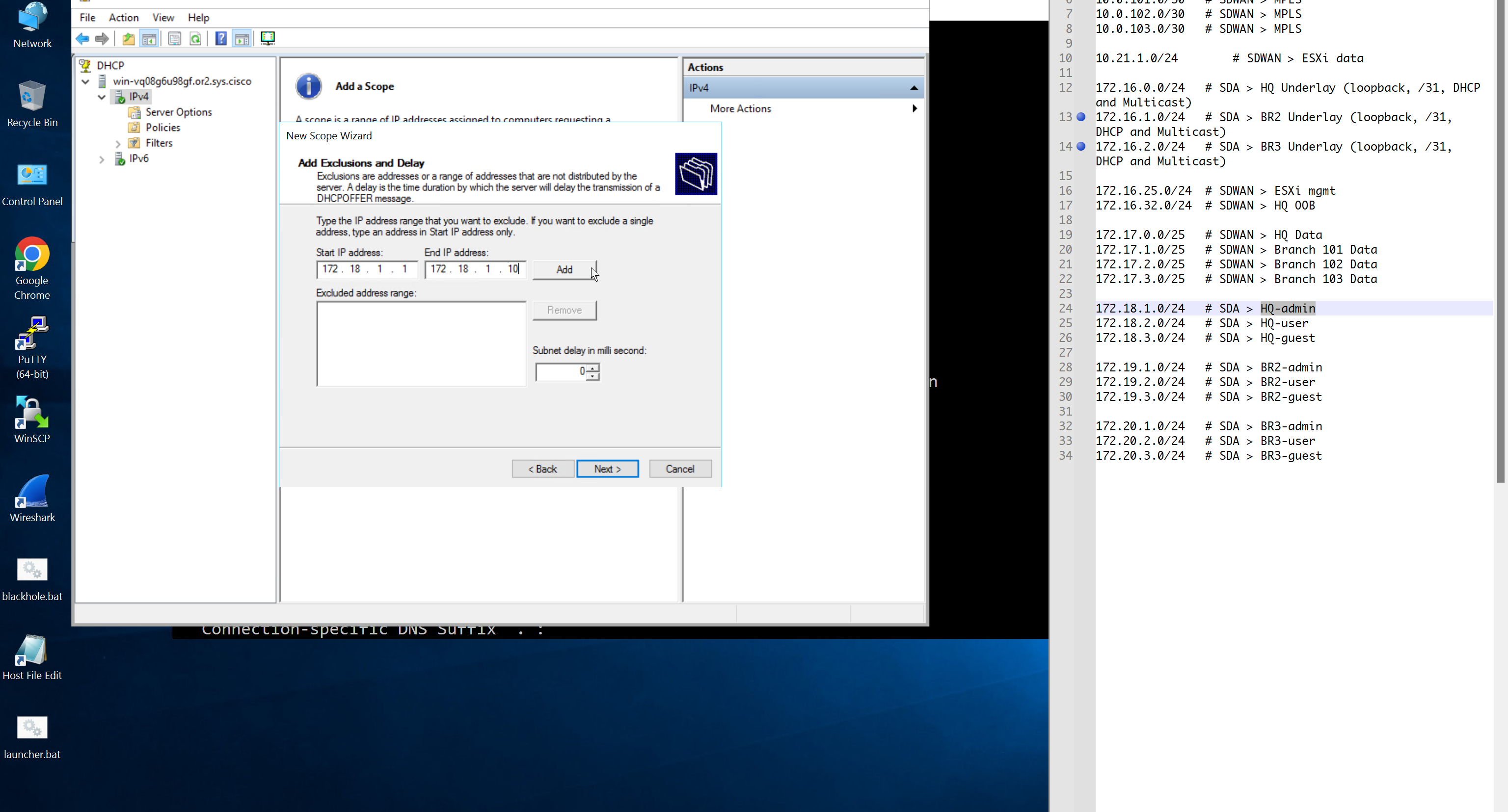
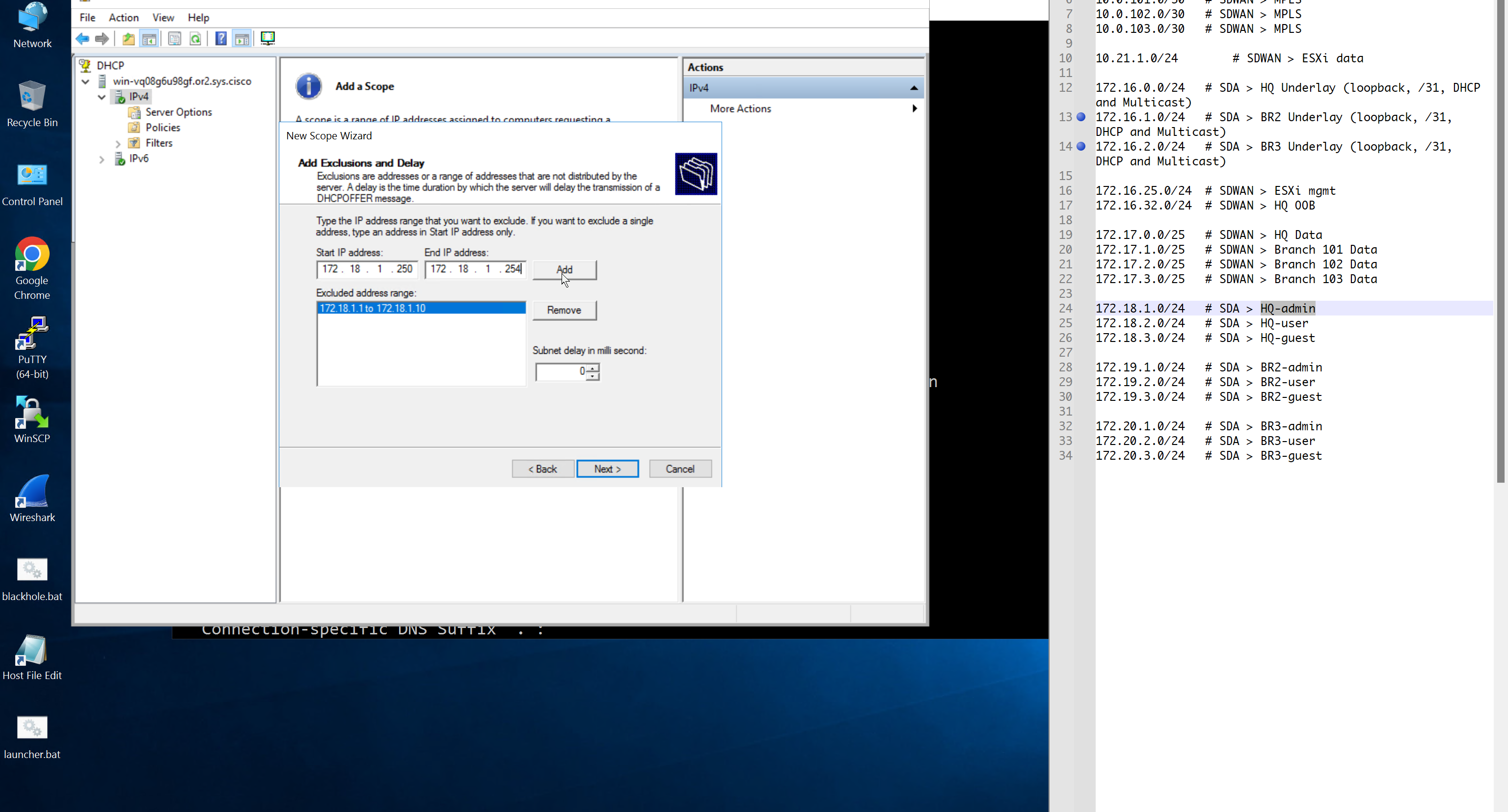
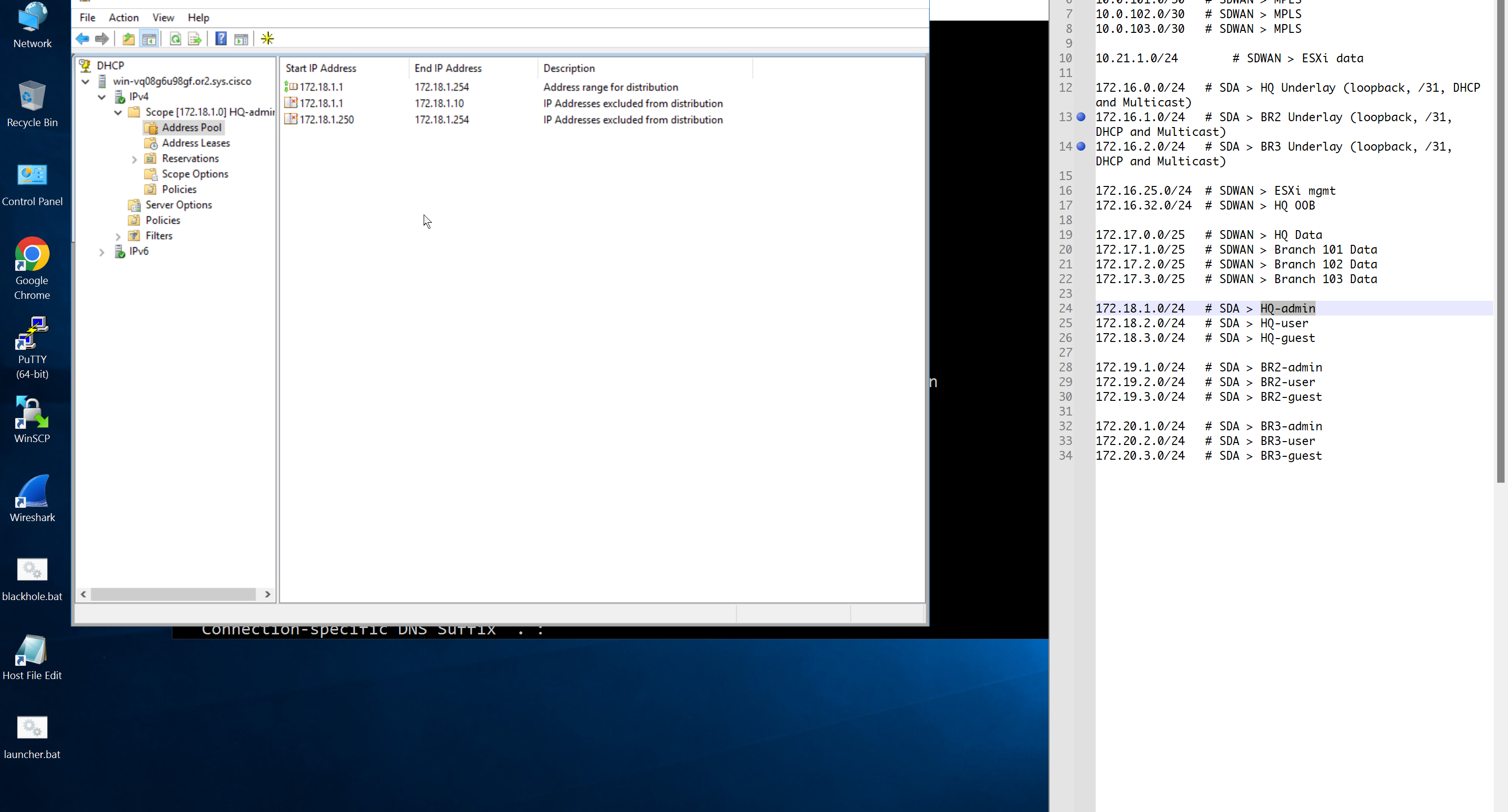
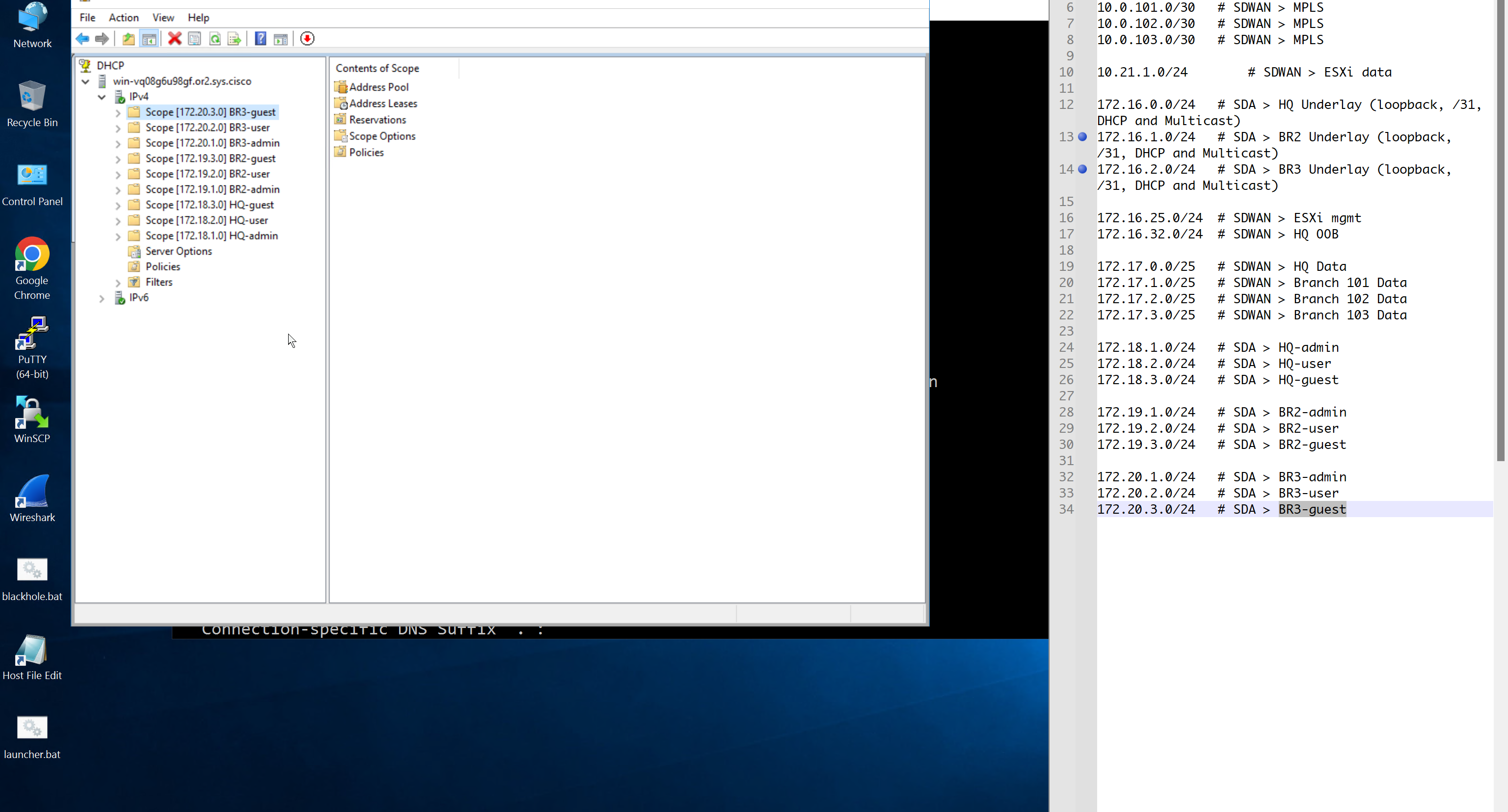
Create DHCP scopes as shown below



AAA “Network” is for network device administration
and AAA “Client/Endpoint” is 802.1x, we will only configure 802.1x for now


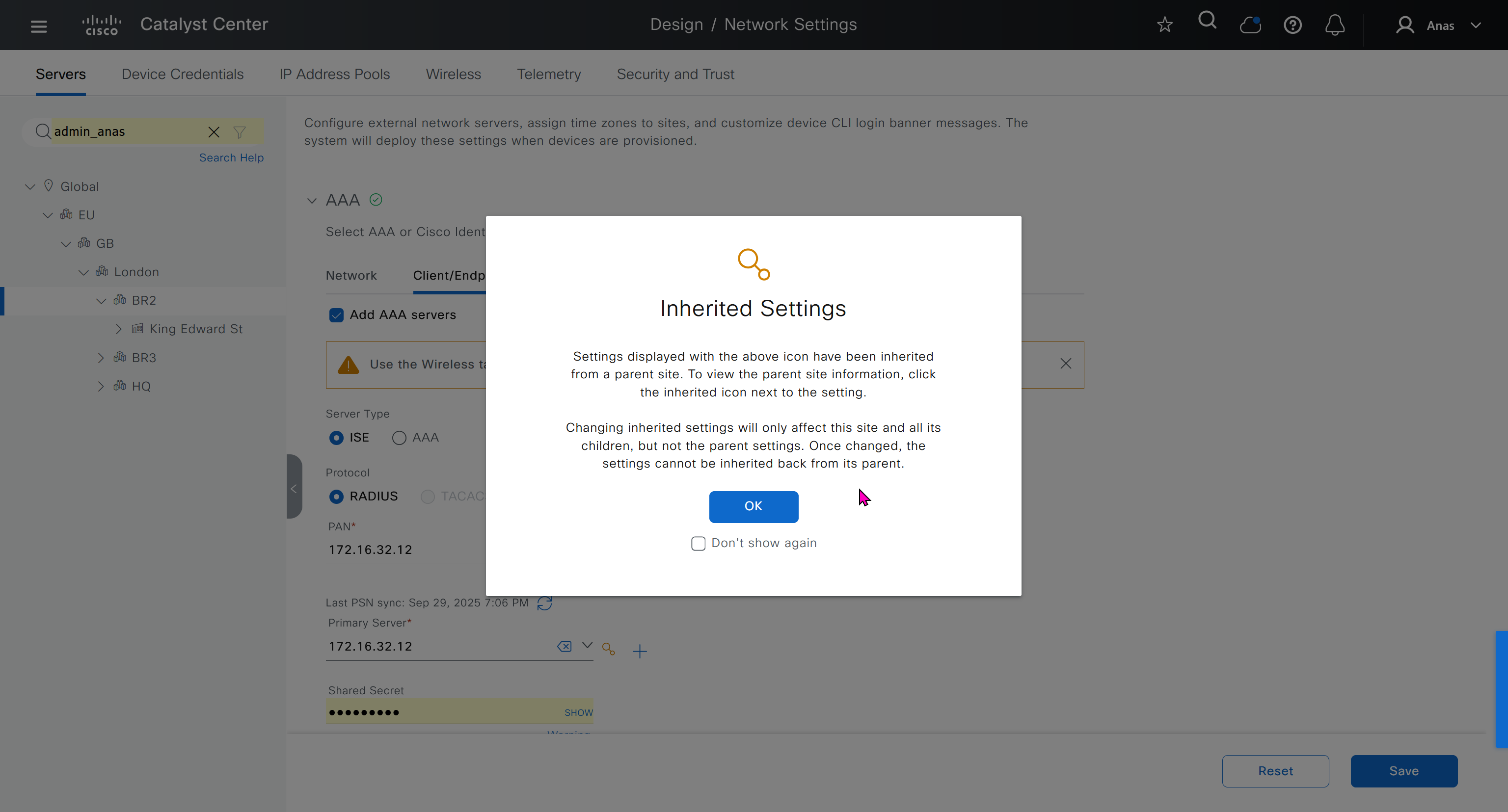
When we click on lower network in hierarchy, for first time we see this symbol which when used in GUI means that configuration is being inherited but they can be overwritten on lower levels


Device credentials is where we feed DNAC with device login details for SSH, SNMPv3 and HTTPS (usually not used

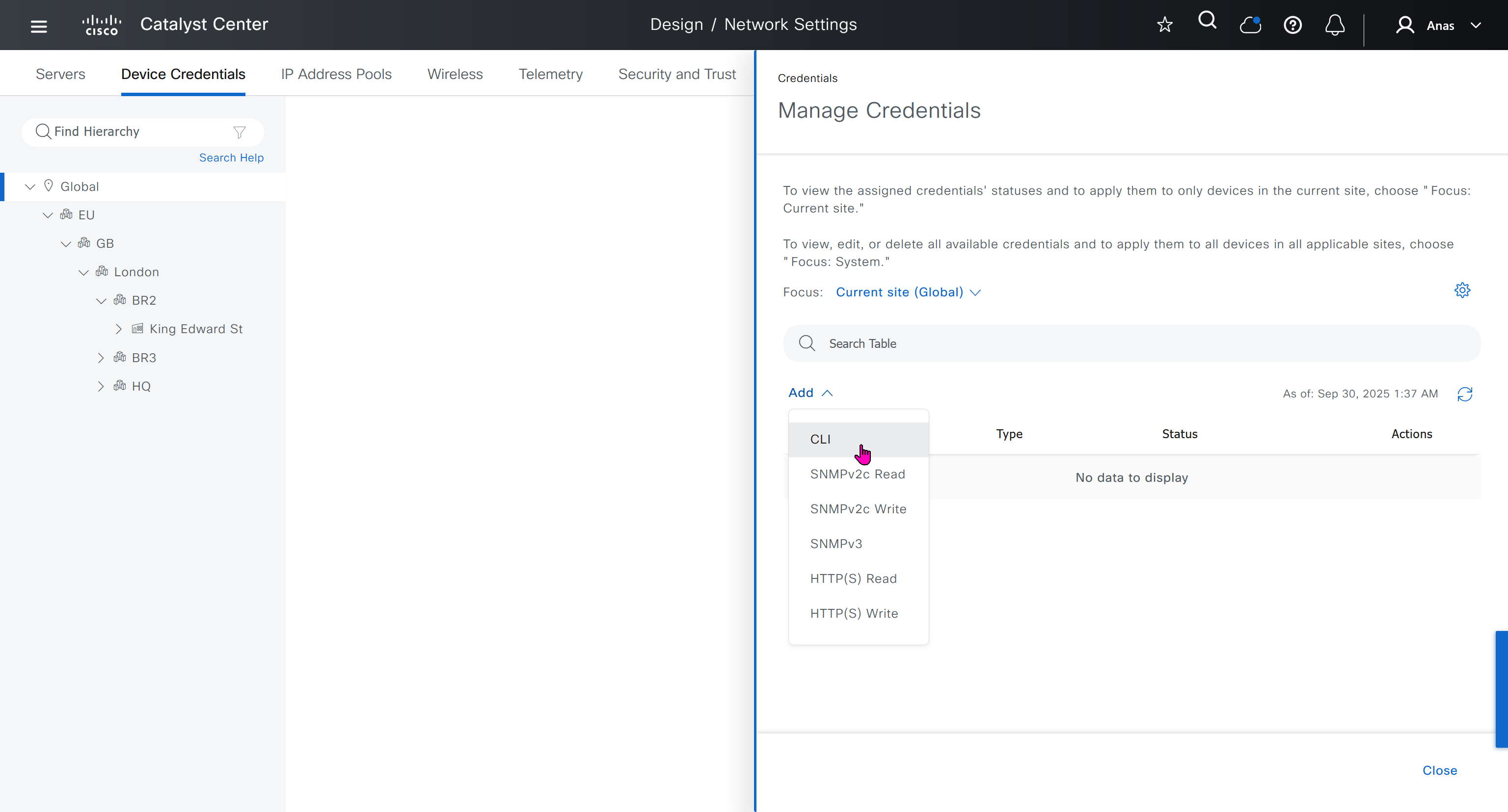
for dnac credentials, try not to use admin as it can cause conflict instead use dnacadmin
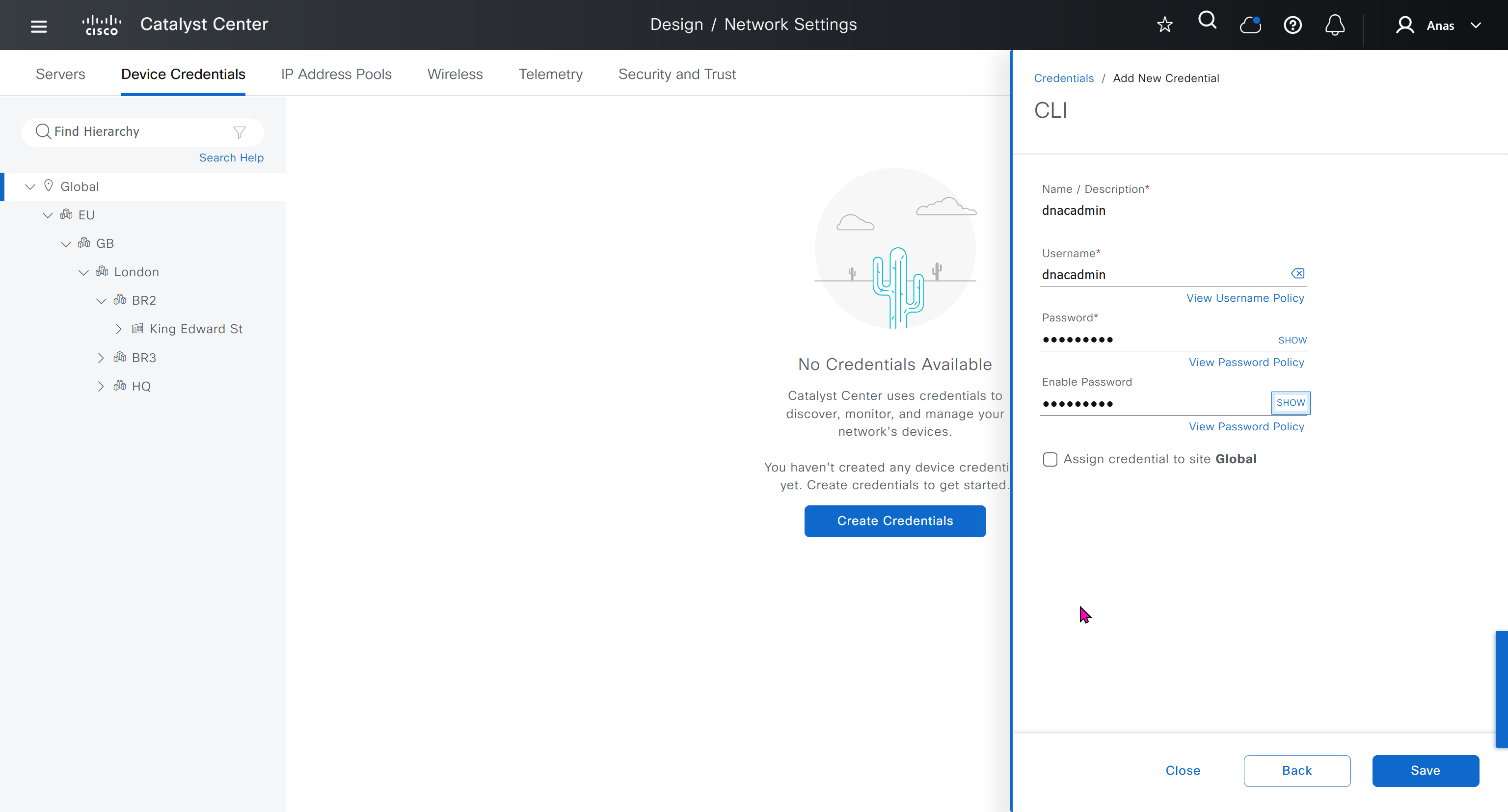
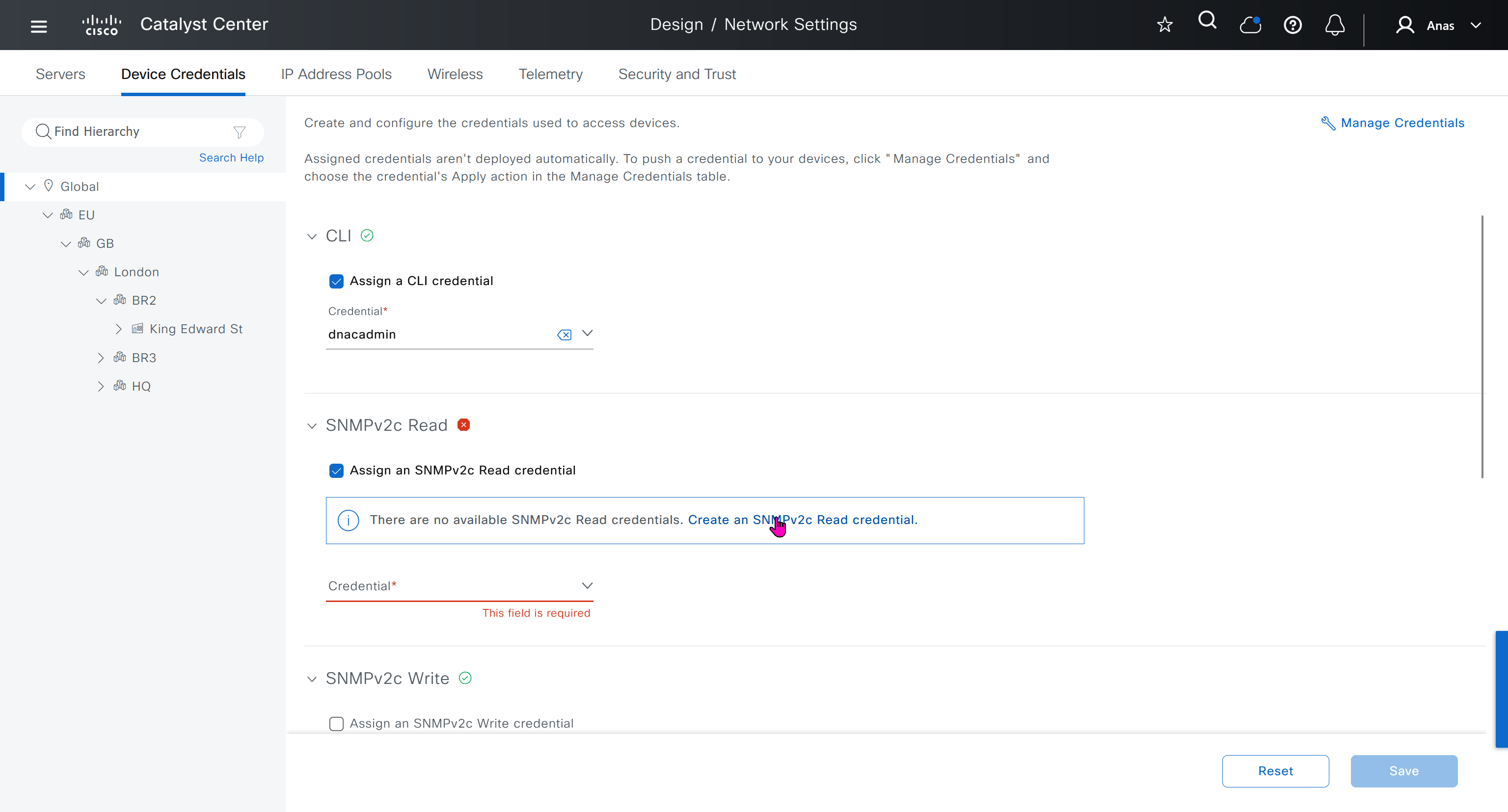
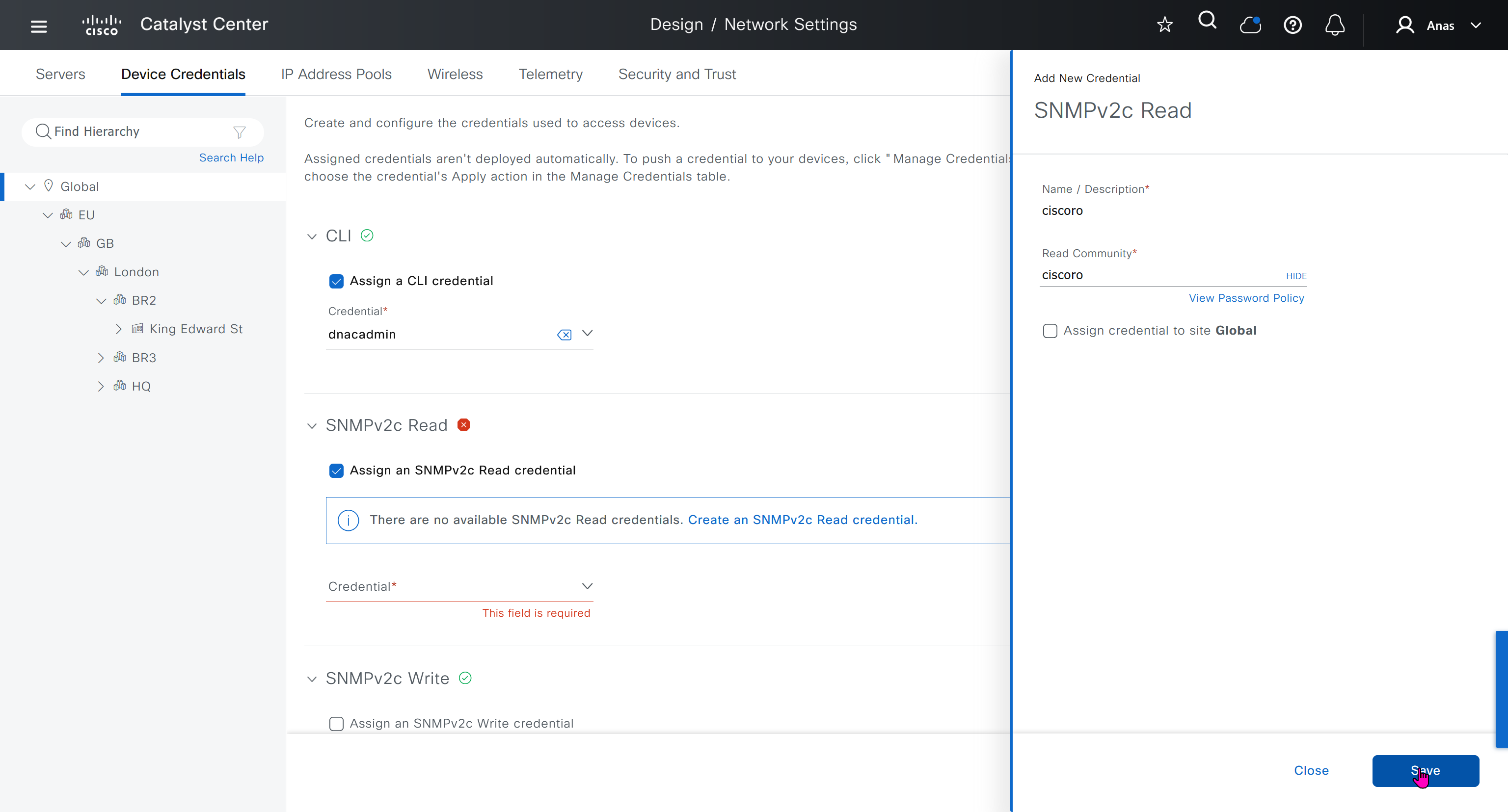
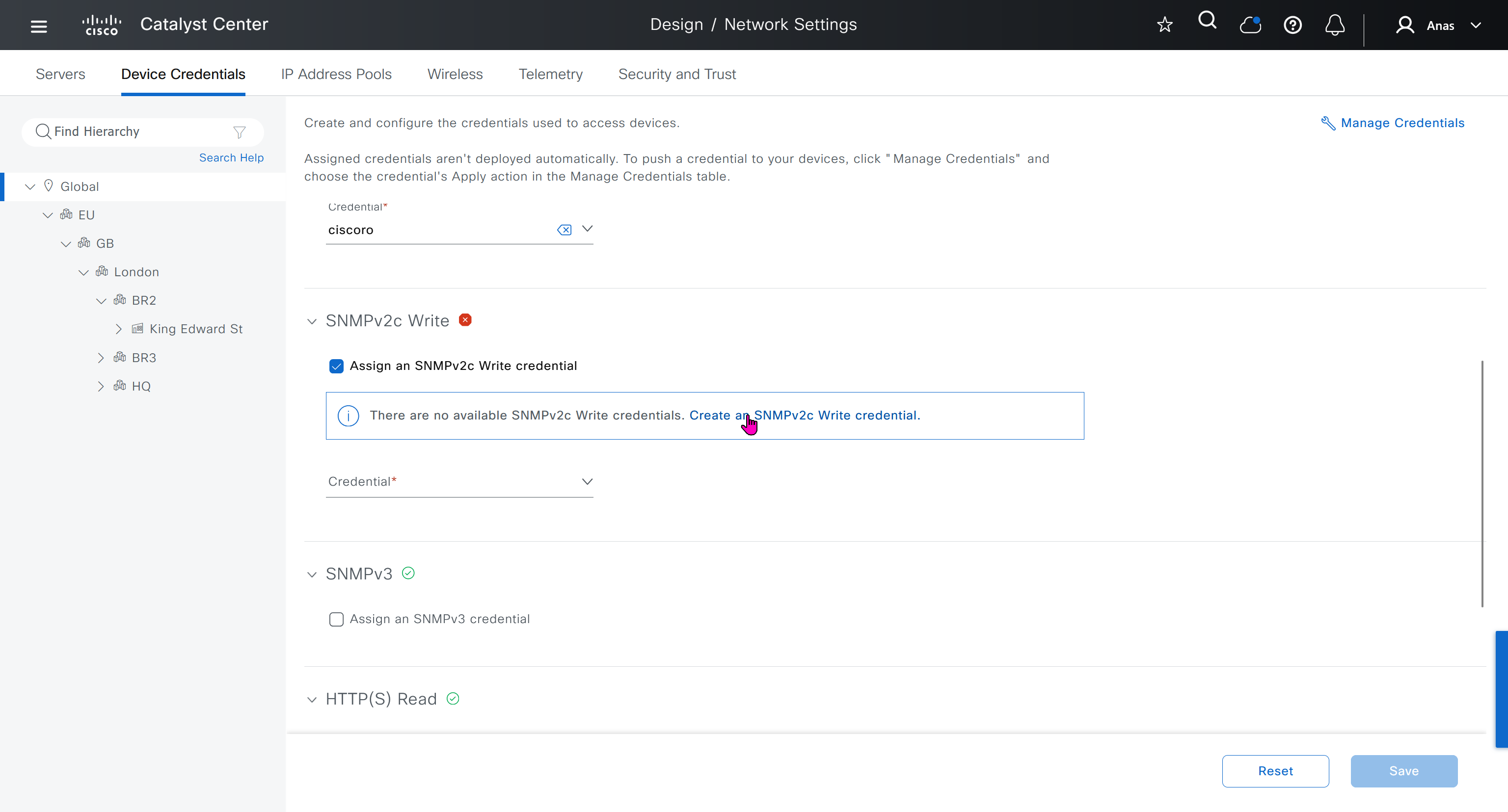
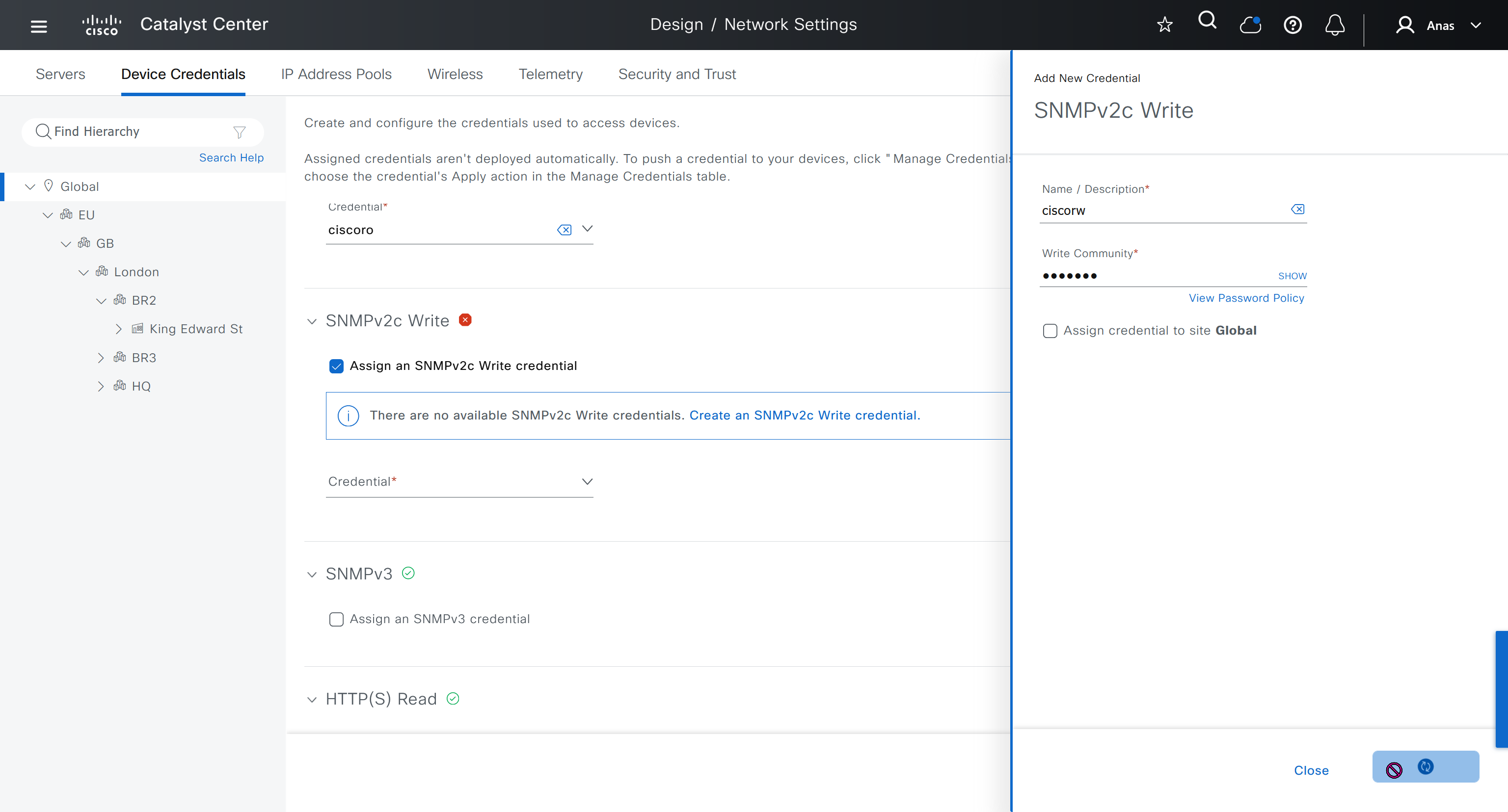
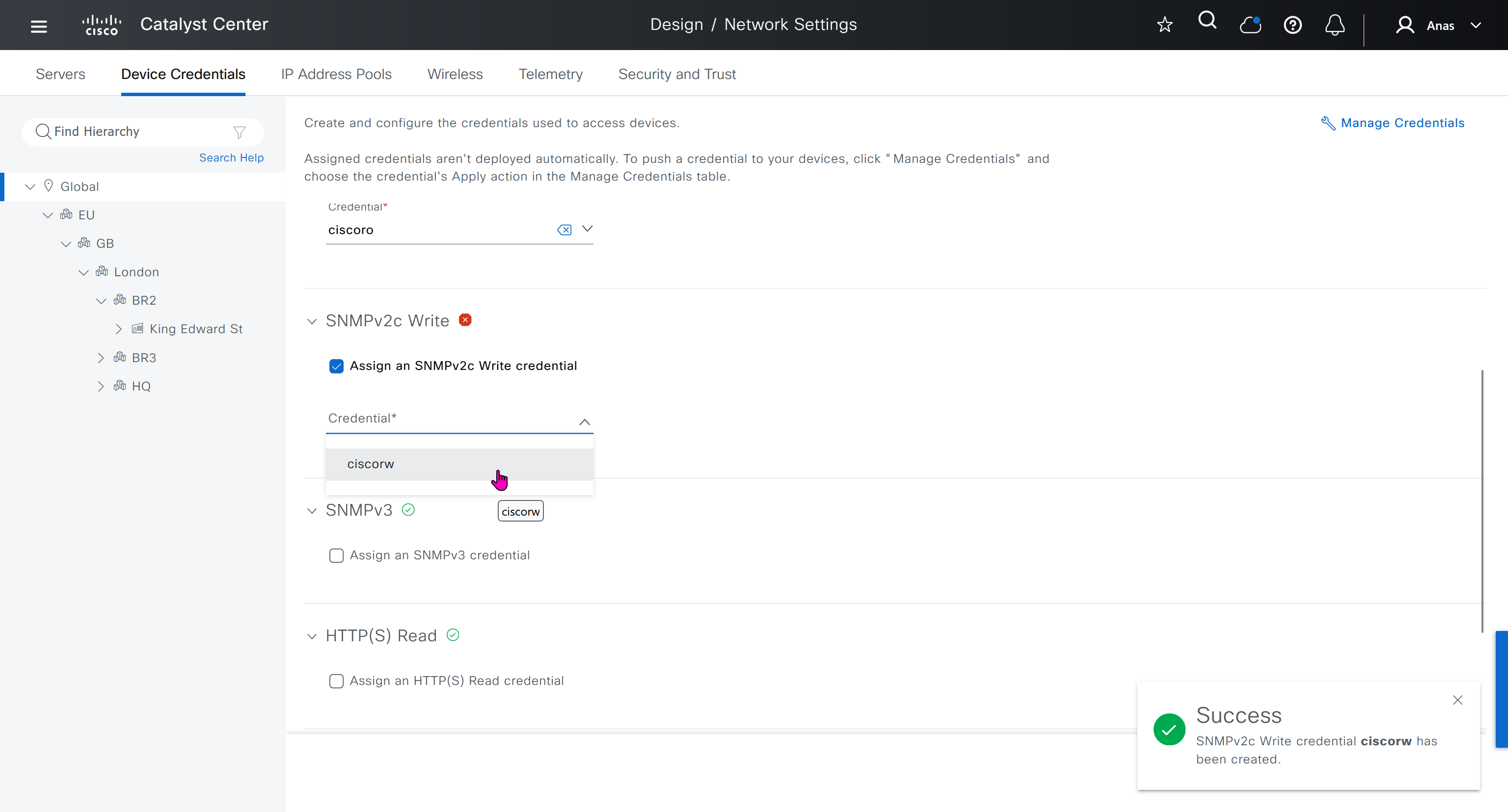
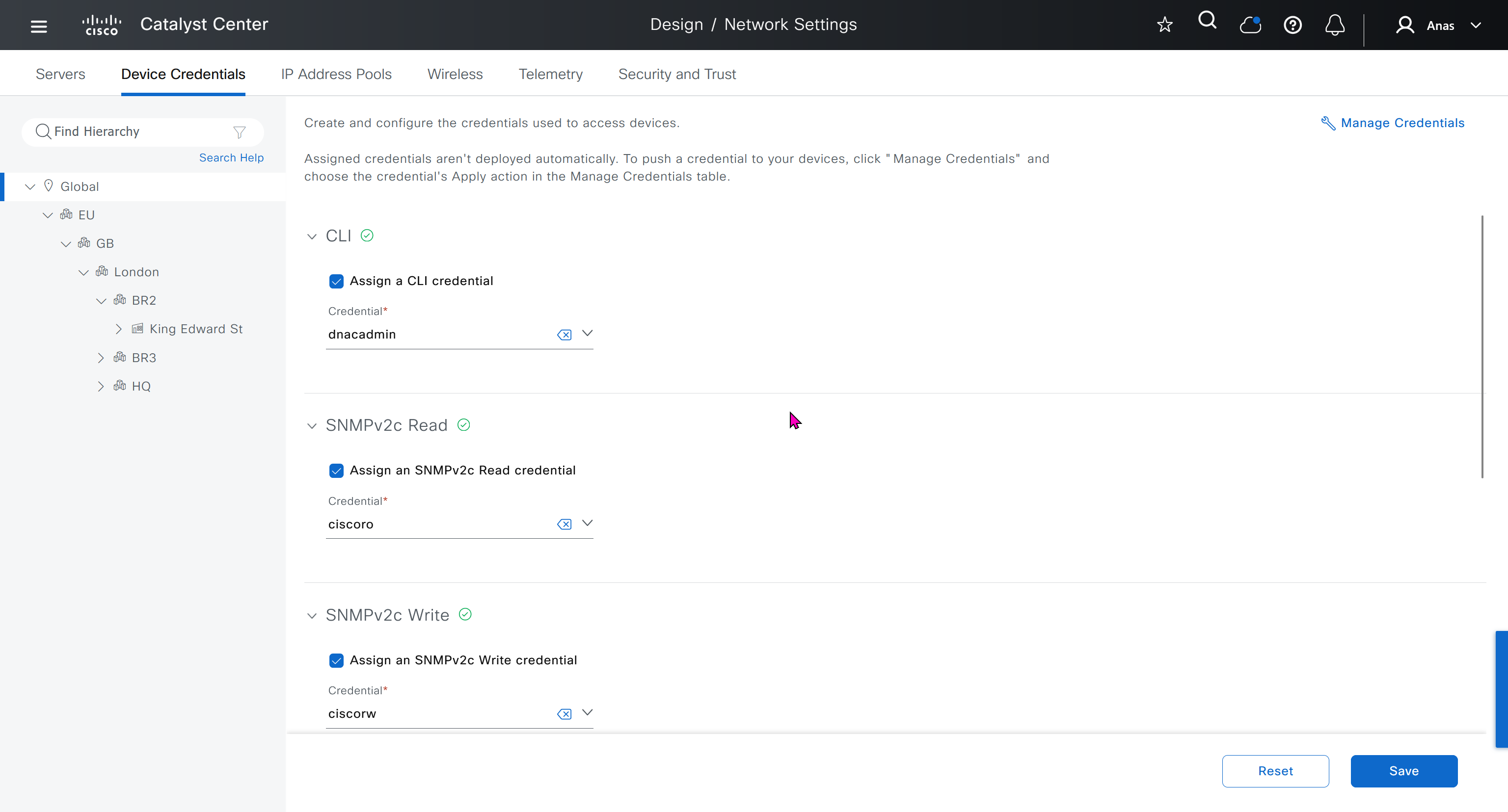
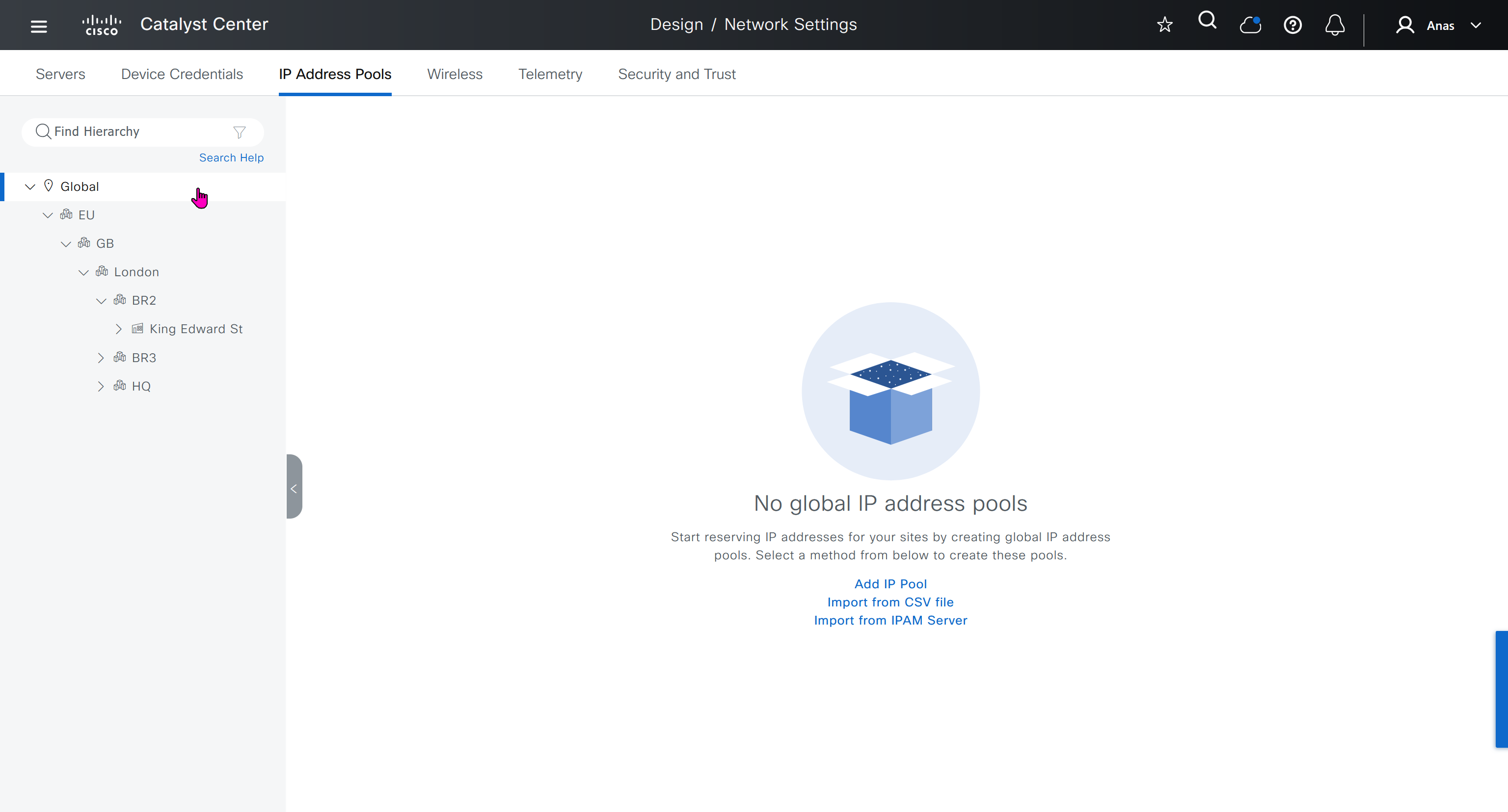
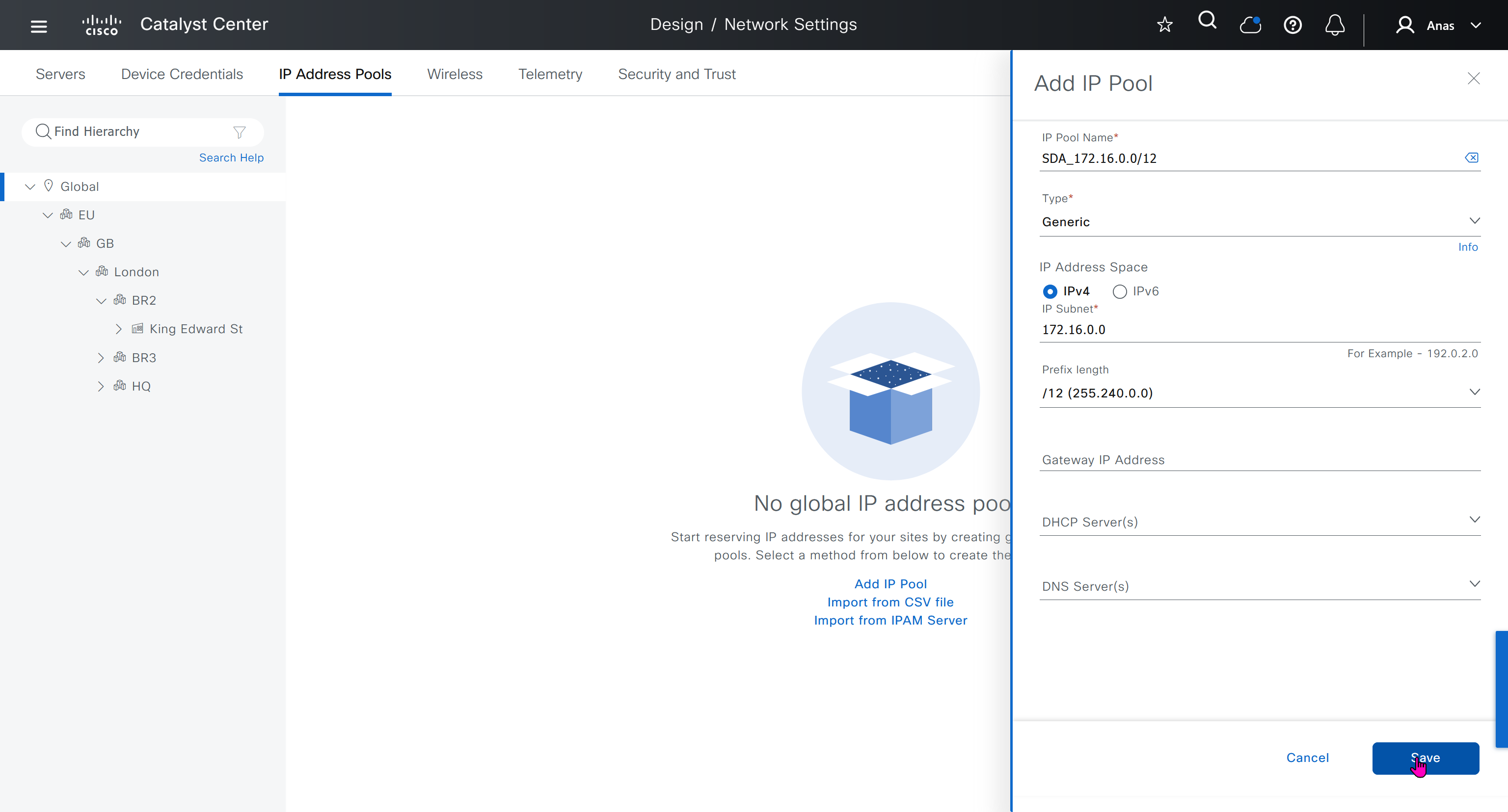
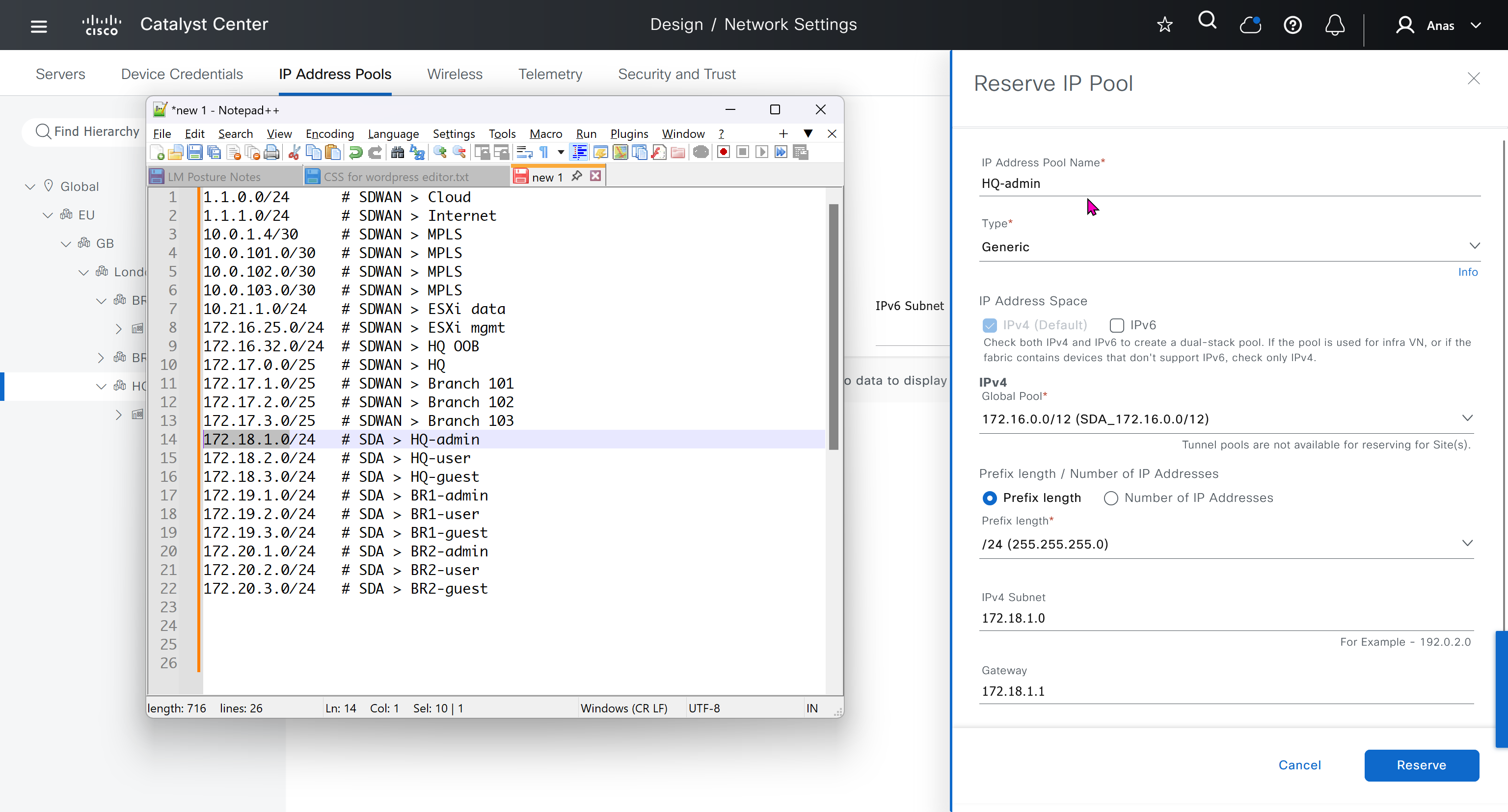
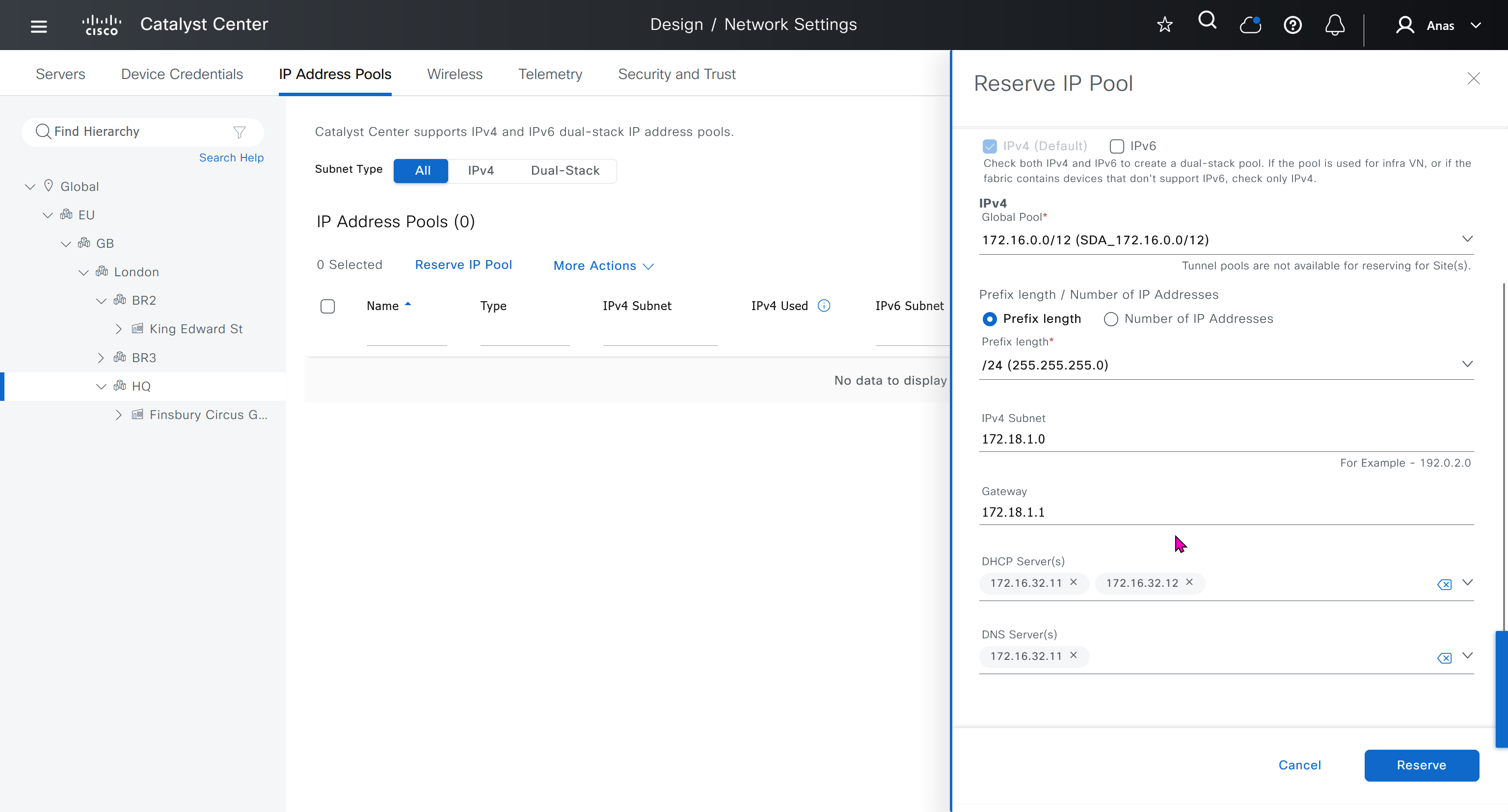
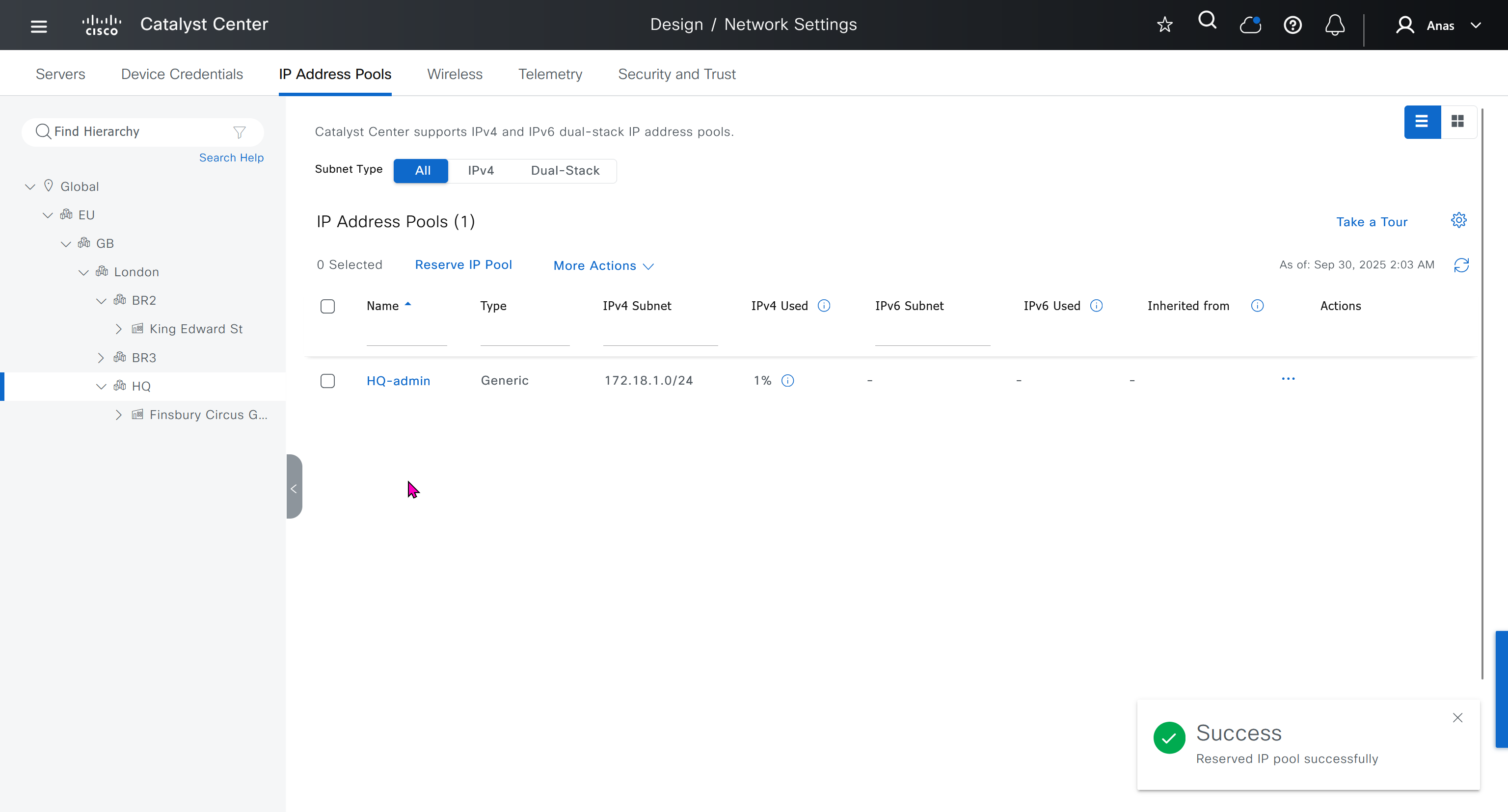
IP address pool is where you define all the subnets that we need to deploy all across SDA, make sure to reserve the supernet at global level
Make sure that we carefully plan and deploy subnets because once it becomes part of SDA, it can be hard to remove it
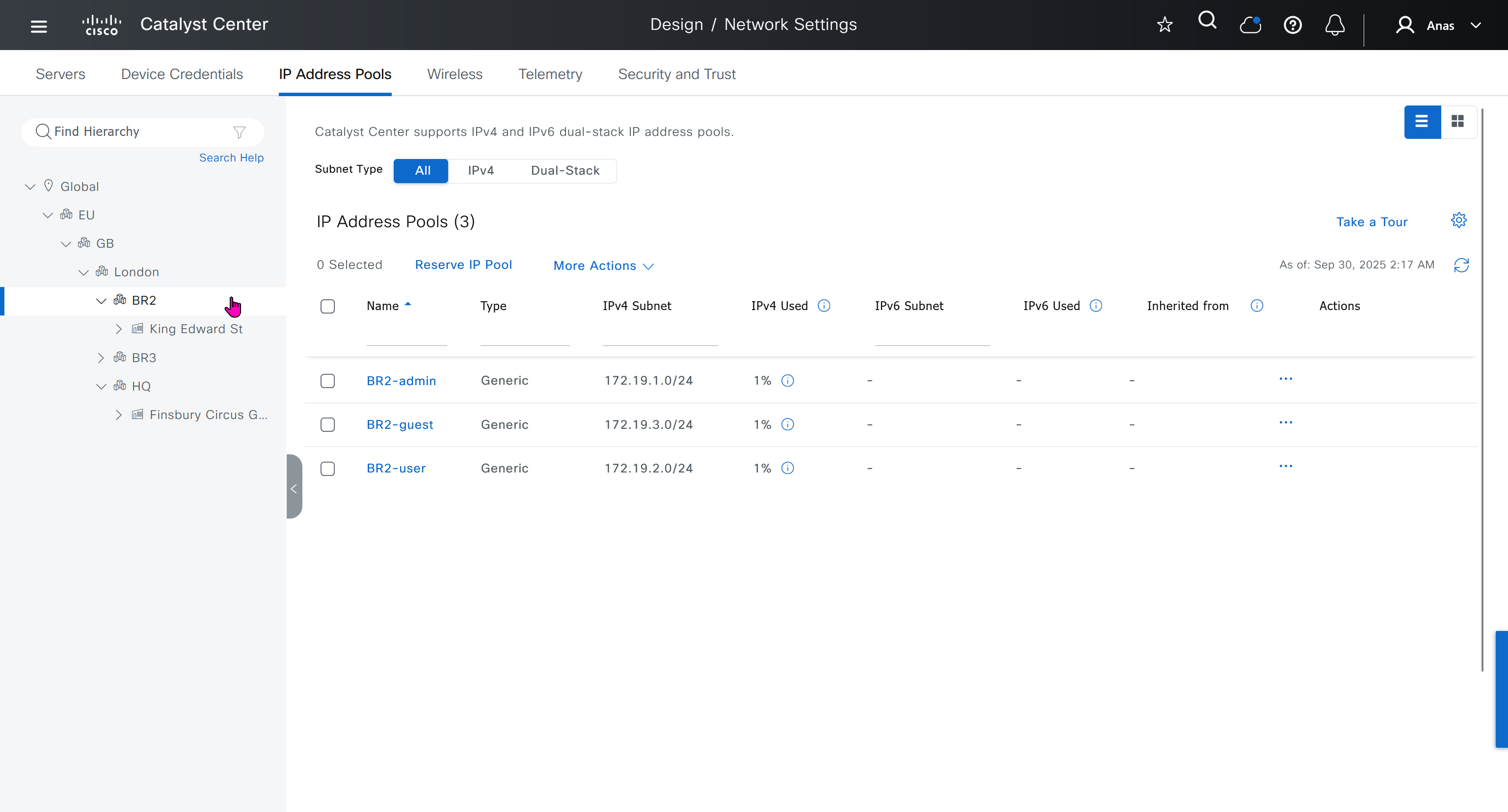
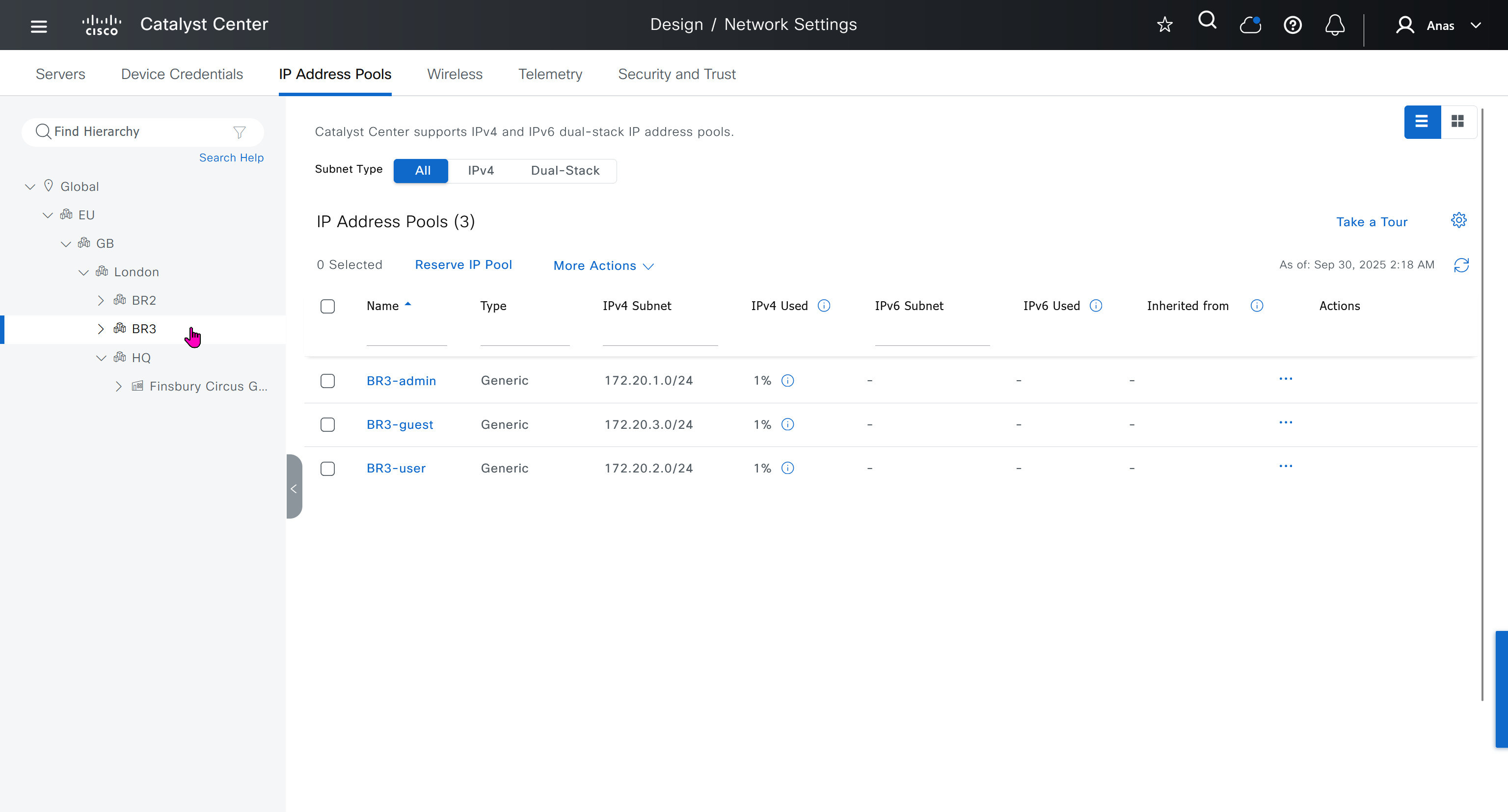
You can only create IP pools at the global level, Add button is only available at global level and at lower hierarchy you simply reserve IP pools for use
IP address pool type for SDA will be generic
When defining IP address pools at Global level then we don’t need to define the gateway IP address, DHCP server and DNS server
Telemetry section is where DNAC configured devices to uses SNMP, netflow and Syslog to send telemetry information to DNAC
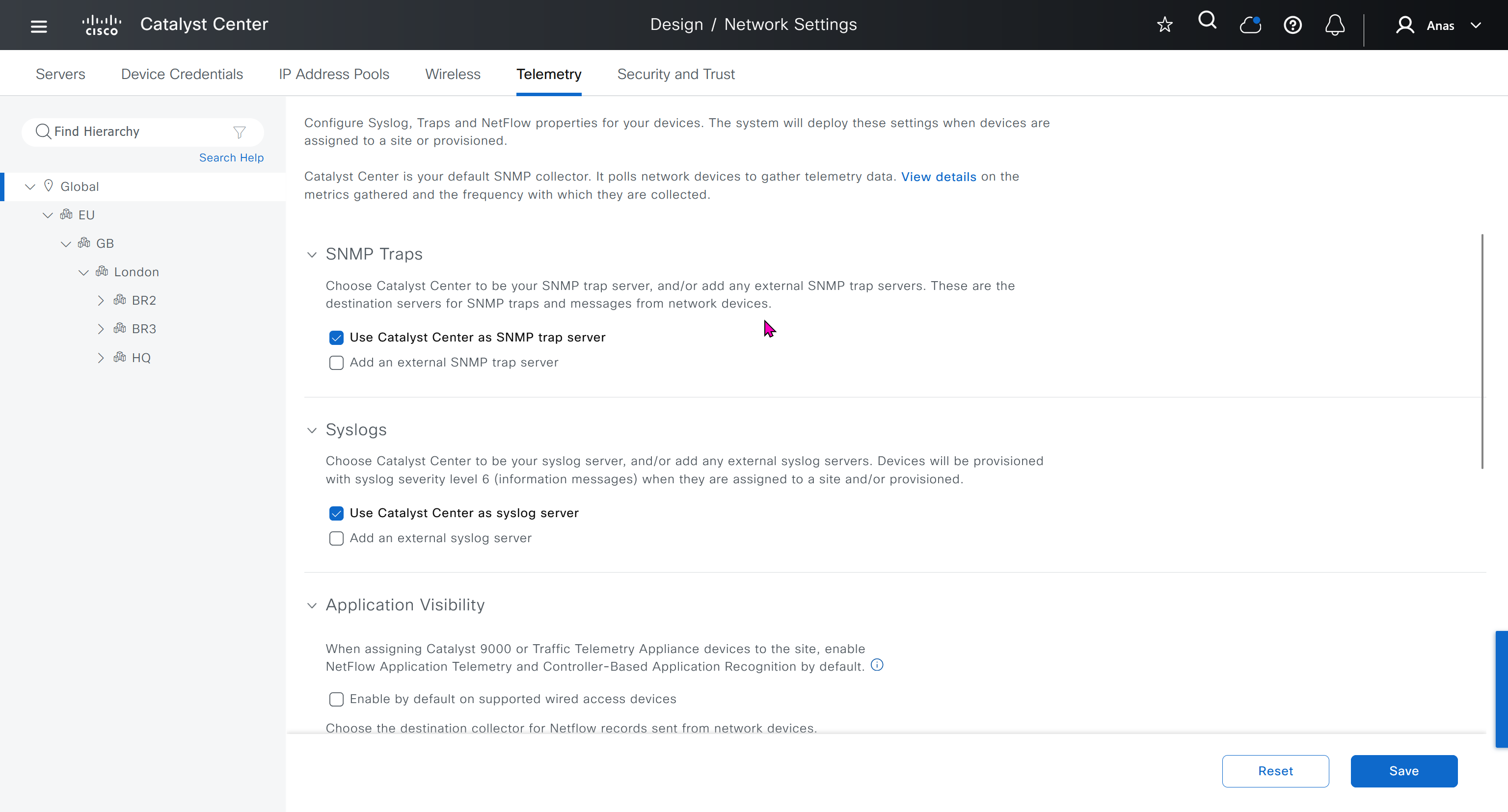

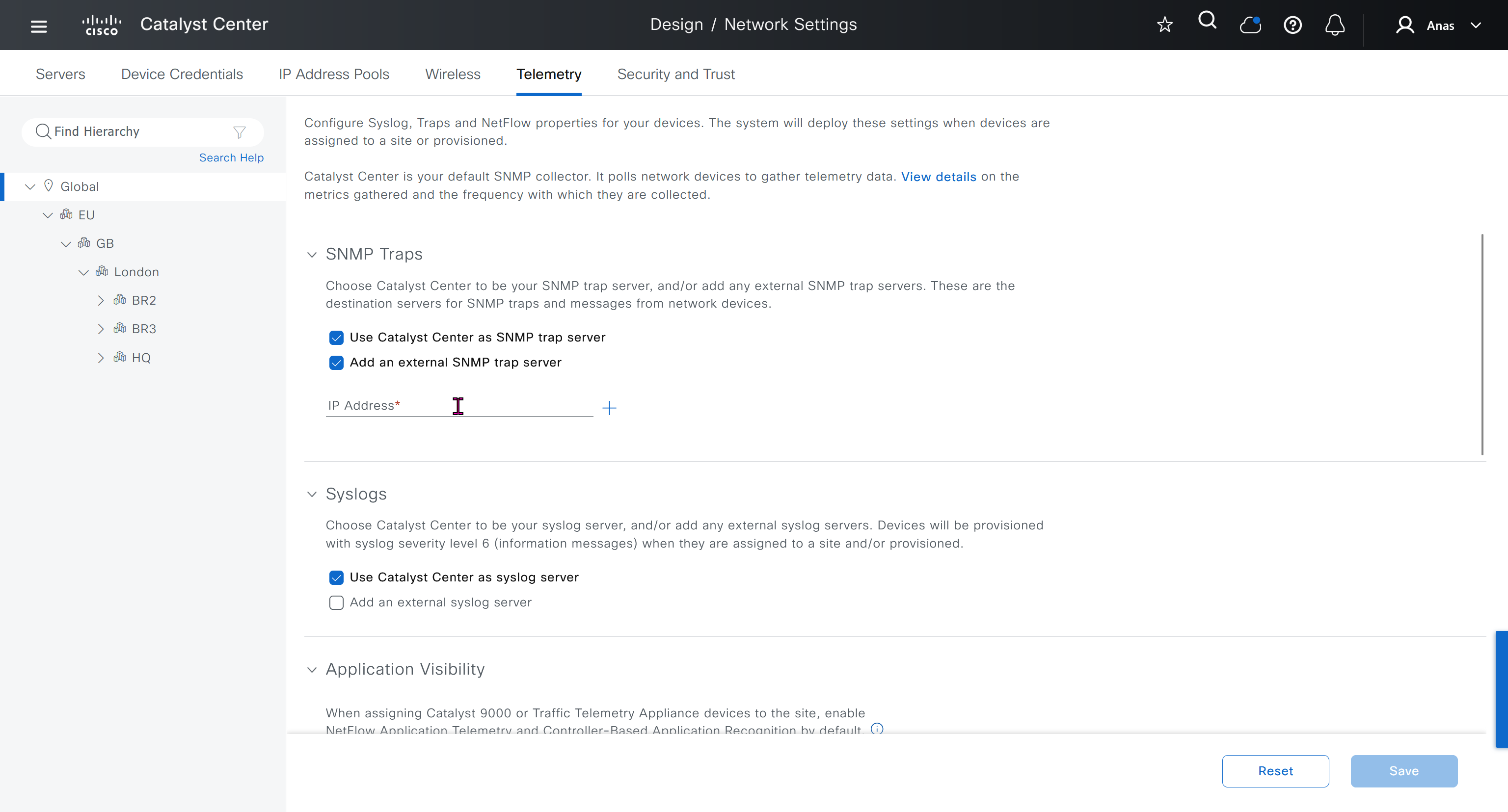
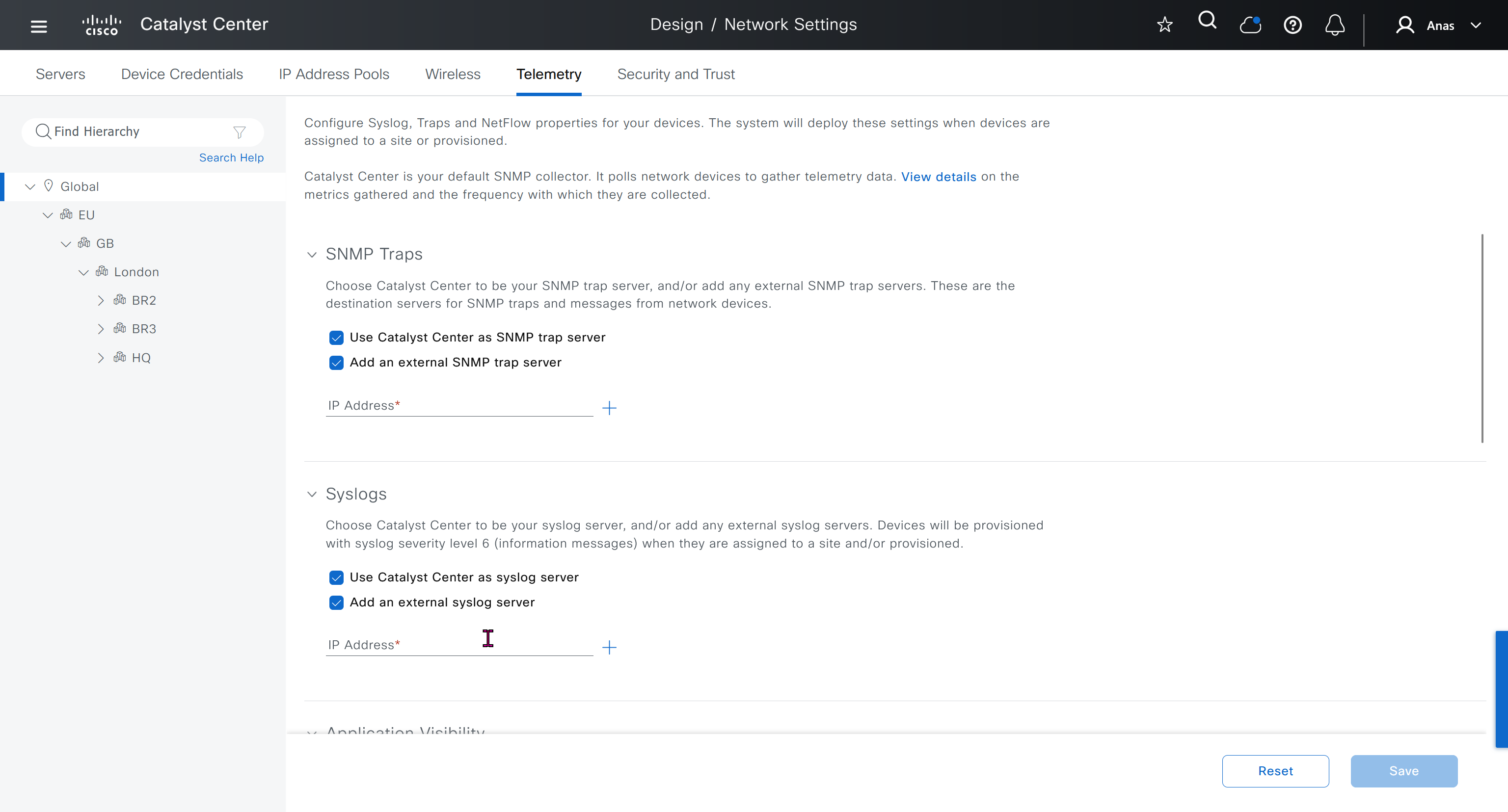
While configuring the Telemetry section, there are options to configure DNAC as SNMP Trap server, Syslog server and netflow collector also but under all these option there is an option also by dnac to configure other syslog and snmp trap server if desired such as SolarWinds
- Enable DNA advantage license
- Enable ip routing
- Enable jumbo frame
- Enable ospf on single vlan between switches (as configured below)
- Enable CLI credentials from DNAC
- Enable SNMP strings from DNAC
- Enable ssh
- Enable local authentication
- Enable netconf-yang
- Enable privilege level 15 on vty lines
conf t
license boot level network-advantage addon dna-advantage
end
write memory
reload
conf t
!
snmp-server community ciscoro RO
snmp-server community ciscorw RW
!
aaa new-model
!
aaa authentication login default local
aaa authorization exec default local
!
aaa session-id common
!
ip routing
!
license boot level network-advantage addon dna-advantage
!
system mtu 8978
!
enable secret 9 $9$WsbGbEnlY7ZnOE$8Y5qUmOgCatKFC2M/Kpmov7Dbd08QBhQlA8nlOXjnfA
!
username cisco privilege 15 secret 9 $9$K2c68lctCCR3v.$SgFneM9tcIGiIKFFsAsZDcBT/DX0ty2rJ01pQSVW5LU
username dnacadmin privilege 15 secret 9 $9$ss2NT8jXdGqUGU$QVfZV.IgKGnzd8GNy5oCLpfZvamjwuusTVNBK61XPMQ
!
interface GigabitEthernet1/0/x
description SDA-HQ-FXX-01
switchport access vlan 12
!
interface GigabitEthernet1/0/x
description SDA-HQ-FXX-01
switchport access vlan 12
!
interface Vlan1
no ip address
!
interface Vlan12
ip address 172.17.0.x 255.255.255.128
ip ospf mtu-ignore
!
router ospf 100
router-id 172.17.0.x
network 172.17.0.0 0.0.0.127 area 0
!
snmp-server community ciscoro RO
snmp-server community ciscorw RW
!
alias router show do show
alias interface show do show
alias configure show do show
!
line vty 0 98
privilege level 15
transport input ssh
!
netconf-yang
end
write memHQ-SW config
HQ-SW#show run
Building configuration...
Current configuration : 3914 bytes
!
! Last configuration change at 03:22:03 UTC Mon Oct 6 2025
!
version 15.2
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
service compress-config
!
hostname HQ-SW
!
boot-start-marker
boot-end-marker
!
!
!
username cisco privilege 15 secret 5 $1$SACq$2ExGwHsqUe3mKfho1B3AQ1
no aaa new-model
!
!
!
!
!
!
!
!
ip cef
no ipv6 cef
!
!
!
spanning-tree mode pvst
spanning-tree extend system-id
!
vlan internal allocation policy ascending
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0
description INTERNET
no switchport
ip address 1.1.1.11 255.255.255.0
negotiation auto
!
interface GigabitEthernet0/1
description WINSERVER
media-type rj45
negotiation auto
!
interface GigabitEthernet0/2
description home.local network
switchport access vlan 11
media-type rj45
negotiation auto
!
interface GigabitEthernet0/3
description ISE01
media-type rj45
negotiation auto
!
interface GigabitEthernet1/0
description SDA-HQ-FBS-01 HQ-DATA
switchport access vlan 12
switchport mode access
media-type rj45
negotiation auto
!
interface GigabitEthernet1/1
media-type rj45
negotiation auto
!
interface GigabitEthernet1/2
media-type rj45
negotiation auto
!
interface GigabitEthernet1/3
media-type rj45
negotiation auto
!
interface Vlan1
description HQ-OOB network
ip address 172.16.32.1 255.255.255.0
!
interface Vlan11
description home.local network
ip address 192.168.0.15 255.255.255.0
!
interface Vlan12
ip address 172.17.0.3 255.255.255.128
ip ospf mtu-ignore
!
router ospf 100
router-id 172.17.0.3
network 172.17.0.0 0.0.0.127 area 0
default-information originate
!
ip forward-protocol nd
!
no ip http server
no ip http secure-server
!
ip route 0.0.0.0 0.0.0.0 192.168.0.1
ip route 1.1.0.0 255.255.255.0 1.1.1.250
ip route 10.21.1.0 255.255.255.0 192.168.0.12
ip route 172.16.25.0 255.255.255.0 192.168.0.12
!
!
!
!
!
control-plane
!
banner exec ^CCC
**************************************************************************
* IOSv is strictly limited to use for evaluation, demonstration and IOS *
* education. IOSv is provided as-is and is not supported by Cisco's *
* Technical Advisory Center. Any use or disclosure, in whole or in part, *
* of the IOSv Software or Documentation to any third party for any *
* purposes is expressly prohibited except as otherwise authorized by *
* Cisco in writing. *
**************************************************************************^C
banner incoming ^CCC
**************************************************************************
* IOSv is strictly limited to use for evaluation, demonstration and IOS *
* education. IOSv is provided as-is and is not supported by Cisco's *
* Technical Advisory Center. Any use or disclosure, in whole or in part, *
* of the IOSv Software or Documentation to any third party for any *
* purposes is expressly prohibited except as otherwise authorized by *
* Cisco in writing. *
**************************************************************************^C
banner login ^CCC
**************************************************************************
* IOSv is strictly limited to use for evaluation, demonstration and IOS *
* education. IOSv is provided as-is and is not supported by Cisco's *
* Technical Advisory Center. Any use or disclosure, in whole or in part, *
* of the IOSv Software or Documentation to any third party for any *
* purposes is expressly prohibited except as otherwise authorized by *
* Cisco in writing. *
**************************************************************************^C
alias router show do show
alias interface show do show
alias configure show do show
!
line con 0
line aux 0
line vty 0 4
login
!
!
netconf-yang
endSDA-HQ-FBS-01 config
SDA-HQ-FBS-01#show run
Building configuration...
Current configuration : 8301 bytes
!
! Last configuration change at 03:40:18 UTC Mon Oct 6 2025
!
version 17.12
service timestamps debug datetime msec
service timestamps log datetime msec
platform punt-keepalive disable-kernel-core
!
hostname SDA-HQ-FBS-01
!
!
vrf definition Mgmt-vrf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization exec default local
!
!
aaa session-id common
switch 1 provision c9kv-uadp-8p
!
!
!
!
ip routing
!
!
!
!
!
!
!
!
login on-success log
vtp version 1
!
!
!
!
!
!
!
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
hash sha256
!
crypto pki trustpoint TP-self-signed-2070352050
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-2070352050
revocation-check none
rsakeypair TP-self-signed-2070352050
hash sha256
!
!
crypto pki certificate chain SLA-TrustPoint
certificate ca 01
30820321 30820209 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363
6F204C69 63656E73 696E6720 526F6F74 20434130 1E170D31 33303533 30313934
3834375A 170D3338 30353330 31393438 34375A30 32310E30 0C060355 040A1305
43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720
526F6F74 20434130 82012230 0D06092A 864886F7 0D010101 05000382 010F0030
82010A02 82010100 A6BCBD96 131E05F7 145EA72C 2CD686E6 17222EA1 F1EFF64D
CBB4C798 212AA147 C655D8D7 9471380D 8711441E 1AAF071A 9CAE6388 8A38E520
1C394D78 462EF239 C659F715 B98C0A59 5BBB5CBD 0CFEBEA3 700A8BF7 D8F256EE
4AA4E80D DB6FD1C9 60B1FD18 FFC69C96 6FA68957 A2617DE7 104FDC5F EA2956AC
7390A3EB 2B5436AD C847A2C5 DAB553EB 69A9A535 58E9F3E3 C0BD23CF 58BD7188
68E69491 20F320E7 948E71D7 AE3BCC84 F10684C7 4BC8E00F 539BA42B 42C68BB7
C7479096 B4CB2D62 EA2F505D C7B062A4 6811D95B E8250FC4 5D5D5FB8 8F27D191
C55F0D76 61F9A4CD 3D992327 A8BB03BD 4E6D7069 7CBADF8B DF5F4368 95135E44
DFC7C6CF 04DD7FD1 02030100 01A34230 40300E06 03551D0F 0101FF04 04030201
06300F06 03551D13 0101FF04 05300301 01FF301D 0603551D 0E041604 1449DC85
4B3D31E5 1B3E6A17 606AF333 3D3B4C73 E8300D06 092A8648 86F70D01 010B0500
03820101 00507F24 D3932A66 86025D9F E838AE5C 6D4DF6B0 49631C78 240DA905
604EDCDE FF4FED2B 77FC460E CD636FDB DD44681E 3A5673AB 9093D3B1 6C9E3D8B
D98987BF E40CBD9E 1AECA0C2 2189BB5C 8FA85686 CD98B646 5575B146 8DFC66A8
467A3DF4 4D565700 6ADF0F0D CF835015 3C04FF7C 21E878AC 11BA9CD2 55A9232C
7CA7B7E6 C1AF74F6 152E99B7 B1FCF9BB E973DE7F 5BDDEB86 C71E3B49 1765308B
5FB0DA06 B92AFE7F 494E8A9E 07B85737 F3A58BE1 1A48A229 C37C1E69 39F08678
80DDCD16 D6BACECA EEBC7CF9 8428787B 35202CDC 60E4616A B623CDBD 230E3AFB
418616A9 4093E049 4D10AB75 27E86F73 932E35B5 8862FDAE 0275156F 719BB2F0
D697DF7F 28
quit
crypto pki certificate chain TP-self-signed-2070352050
certificate self-signed 01
30820330 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
31312F30 2D060355 04030C26 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 32303730 33353230 3530301E 170D3235 30393231 32313439
32315A17 0D333530 39323132 31343932 315A3031 312F302D 06035504 030C2649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D32 30373033
35323035 30308201 22300D06 092A8648 86F70D01 01010500 0382010F 00308201
0A028201 0100BE6B 15431B3C C2F339F8 E68ED232 38C6D054 26256330 1860898B
3427C857 6F821274 0C5B8B21 D2B908B2 71205F22 E9E2D9EF CCCEF719 CB65D798
620546BE 724EFEE4 B7D9026F E94D9B0C A1B7755C 33C13A5B 5803DE7F DABC513B
17181601 AE98D442 44694CF2 57D1505F 3A119649 E0F7C524 A2C544D1 8C986BC2
89C8FAF7 0E72811A AC4FDC69 D0A4DE17 BE69A40F F83E5BFD B16E894B 18830516
06726E02 3E6F1A7F 3A202286 600059F0 CF9EC6A8 420946BD A0F70AFF CE386017
44CB8032 55B22C27 E240440C 39D3EEF3 B887DF4B ECECD738 76C531B7 DC43AC1F
38AAE8C1 A12B5574 0DCA1A63 88E12E80 62411882 573FBF7A 85DD348B 425A477E
9AF7DAB7 D9EF0203 010001A3 53305130 1D060355 1D0E0416 0414864F 5DC3AA3D
570D29AC 614578D3 7BCFD3AF 76D5301F 0603551D 23041830 16801486 4F5DC3AA
3D570D29 AC614578 D37BCFD3 AF76D530 0F060355 1D130101 FF040530 030101FF
300D0609 2A864886 F70D0101 0B050003 82010100 3037A0B0 4EE53529 F17F5DAF
A4B8BF4C 1B0B63D3 2F5785E9 4A2FFE10 46890D5C 3A50C253 6AF15B6F 13FA2AC8
EBF67CBD CFA8D7AE 756B2596 B554A972 40F4E277 98310DC0 9EA3EB9A B8CCD9BE
C5332F30 4C6A7F5B D76CF4DF 69E29977 745B232E EC606EB5 CD6CA542 A425C5CC
D307EE95 FBF9FE6A F0561077 83079168 0DEA031B 00D4D850 EFED9136 607A5F2F
FB848029 6C2457A0 1AD24EBB A915E9DE F0F4BFD5 DA125681 55183EE5 D62333F9
97EA23F6 F2925C1E 440888B7 34A5F17D 66245CF7 3D4C53EB 1E364B3F 9861630D
31F4E67F 05F58704 E4D4238D 539144CC 70F0A6AB F51BAFE9 F47D3E14 72AABFB8
F44C060A BE7D007B DA1DF7FB B73C8E9D 1B24F792
quit
!
!
license boot level network-advantage addon dna-advantage
memory free low-watermark processor 74862
!
system mtu 8978
diagnostic bootup level minimal
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
!
!
enable secret 9 $9$WsbGbEnlY7ZnOE$8Y5qUmOgCatKFC2M/Kpmov7Dbd08QBhQlA8nlOXjnfA
!
username cisco privilege 15 secret 9 $9$K2c68lctCCR3v.$SgFneM9tcIGiIKFFsAsZDcBT/DX0ty2rJ01pQSVW5LU
username dnacadmin privilege 15 secret 9 $9$ss2NT8jXdGqUGU$QVfZV.IgKGnzd8GNy5oCLpfZvamjwuusTVNBK61XPMQ
!
redundancy
mode sso
!
!
!
!
!
!
class-map match-any system-cpp-police-topology-control
description Topology control
class-map match-any system-cpp-police-sw-forward
description Sw forwarding, L2 LVX data, LOGGING
class-map match-any system-cpp-default
description EWLC control, EWLC data, Inter FED
class-map match-any system-cpp-police-sys-data
description Learning cache ovfl, High Rate App, Exception, EGR Exception, NFL SAMPLED DATA, RPF Failed
class-map match-any system-cpp-police-punt-webauth
description Punt Webauth
class-map match-any system-cpp-police-l2lvx-control
description L2 LVX control packets
class-map match-any system-cpp-police-forus
description Forus Address resolution and Forus traffic
class-map match-any system-cpp-police-multicast-end-station
description MCAST END STATION
class-map match-any system-cpp-police-multicast
description Transit Traffic and MCAST Data
class-map match-any system-cpp-police-l2-control
description L2 control
class-map match-any system-cpp-police-dot1x-auth
description DOT1X Auth
class-map match-any system-cpp-police-data
description ICMP redirect, ICMP_GEN and BROADCAST
class-map match-any system-cpp-police-stackwise-virt-control
description Stackwise Virtual
class-map match-any non-client-nrt-class
class-map match-any system-cpp-police-routing-control
description Routing control and Low Latency
class-map match-any system-cpp-police-protocol-snooping
description Protocol snooping
class-map match-any system-cpp-police-dhcp-snooping
description DHCP snooping
class-map match-any system-cpp-police-system-critical
description System Critical and Gold Pkt
!
policy-map system-cpp-policy
!
!
!
!
!
!
!
!
!
!
!
!
interface Loopback0
no ip address
!
interface GigabitEthernet0/0
vrf forwarding Mgmt-vrf
ip address dhcp
negotiation auto
!
interface GigabitEthernet1/0/1
description HQ-SW
switchport access vlan 12
!
interface GigabitEthernet1/0/2
!
interface GigabitEthernet1/0/3
!
interface GigabitEthernet1/0/4
!
interface GigabitEthernet1/0/5
!
interface GigabitEthernet1/0/6
!
interface GigabitEthernet1/0/7
description SDA-HQ-FIS-01
switchport access vlan 12
!
interface GigabitEthernet1/0/8
description SDA-HQ-FIS-01
switchport access vlan 12
!
interface Vlan1
no ip address
!
interface Vlan12
ip address 172.17.0.4 255.255.255.128
ip ospf mtu-ignore
!
router ospf 100
router-id 172.17.0.4
network 172.17.0.0 0.0.0.127 area 0
!
ip forward-protocol nd
ip tcp mss 1280
ip tcp window-size 212000
ip http server
ip http authentication local
ip http secure-server
ip ssh bulk-mode 131072
!
!
!
!
snmp-server community ciscoro RO
snmp-server community ciscorw RW
!
!
!
!
control-plane
service-policy input system-cpp-policy
!
!
alias router show do show
alias interface show do show
alias configure show do show
!
line con 0
stopbits 1
line vty 0 4
privilege level 15
transport input ssh
line vty 5 98
privilege level 15
transport input ssh
!
!
!
!
!
!
!
netconf-yang
endSDA-HQ-FES-01 config
SDA-HQ-FES-01#show run
Building configuration...
Current configuration : 8213 bytes
!
! Last configuration change at 03:42:50 UTC Mon Oct 6 2025
!
version 17.12
service timestamps debug datetime msec
service timestamps log datetime msec
platform punt-keepalive disable-kernel-core
!
hostname SDA-HQ-FES-01
!
!
vrf definition Mgmt-vrf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization exec default local
!
!
aaa session-id common
switch 1 provision c9kv-uadp-8p
!
!
!
!
ip routing
!
!
!
!
!
!
!
!
login on-success log
vtp version 1
!
!
!
!
!
!
!
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
hash sha256
!
crypto pki trustpoint TP-self-signed-4128105830
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-4128105830
revocation-check none
rsakeypair TP-self-signed-4128105830
hash sha256
!
!
crypto pki certificate chain SLA-TrustPoint
certificate ca 01
30820321 30820209 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363
6F204C69 63656E73 696E6720 526F6F74 20434130 1E170D31 33303533 30313934
3834375A 170D3338 30353330 31393438 34375A30 32310E30 0C060355 040A1305
43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720
526F6F74 20434130 82012230 0D06092A 864886F7 0D010101 05000382 010F0030
82010A02 82010100 A6BCBD96 131E05F7 145EA72C 2CD686E6 17222EA1 F1EFF64D
CBB4C798 212AA147 C655D8D7 9471380D 8711441E 1AAF071A 9CAE6388 8A38E520
1C394D78 462EF239 C659F715 B98C0A59 5BBB5CBD 0CFEBEA3 700A8BF7 D8F256EE
4AA4E80D DB6FD1C9 60B1FD18 FFC69C96 6FA68957 A2617DE7 104FDC5F EA2956AC
7390A3EB 2B5436AD C847A2C5 DAB553EB 69A9A535 58E9F3E3 C0BD23CF 58BD7188
68E69491 20F320E7 948E71D7 AE3BCC84 F10684C7 4BC8E00F 539BA42B 42C68BB7
C7479096 B4CB2D62 EA2F505D C7B062A4 6811D95B E8250FC4 5D5D5FB8 8F27D191
C55F0D76 61F9A4CD 3D992327 A8BB03BD 4E6D7069 7CBADF8B DF5F4368 95135E44
DFC7C6CF 04DD7FD1 02030100 01A34230 40300E06 03551D0F 0101FF04 04030201
06300F06 03551D13 0101FF04 05300301 01FF301D 0603551D 0E041604 1449DC85
4B3D31E5 1B3E6A17 606AF333 3D3B4C73 E8300D06 092A8648 86F70D01 010B0500
03820101 00507F24 D3932A66 86025D9F E838AE5C 6D4DF6B0 49631C78 240DA905
604EDCDE FF4FED2B 77FC460E CD636FDB DD44681E 3A5673AB 9093D3B1 6C9E3D8B
D98987BF E40CBD9E 1AECA0C2 2189BB5C 8FA85686 CD98B646 5575B146 8DFC66A8
467A3DF4 4D565700 6ADF0F0D CF835015 3C04FF7C 21E878AC 11BA9CD2 55A9232C
7CA7B7E6 C1AF74F6 152E99B7 B1FCF9BB E973DE7F 5BDDEB86 C71E3B49 1765308B
5FB0DA06 B92AFE7F 494E8A9E 07B85737 F3A58BE1 1A48A229 C37C1E69 39F08678
80DDCD16 D6BACECA EEBC7CF9 8428787B 35202CDC 60E4616A B623CDBD 230E3AFB
418616A9 4093E049 4D10AB75 27E86F73 932E35B5 8862FDAE 0275156F 719BB2F0
D697DF7F 28
quit
crypto pki certificate chain TP-self-signed-4128105830
certificate self-signed 01
30820330 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
31312F30 2D060355 04030C26 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 34313238 31303538 3330301E 170D3235 31303035 31393137
30325A17 0D333531 30303531 39313730 325A3031 312F302D 06035504 030C2649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D34 31323831
30353833 30308201 22300D06 092A8648 86F70D01 01010500 0382010F 00308201
0A028201 0100B7B2 70B7BDF4 91177742 63220480 4899E262 C48CF80E B97F5343
5BC116D2 EFE21CC5 7B2C5BDA 8A2A1397 D1BEE9BF 8EB1BF36 82F1AC35 C87B876D
B59424B1 E20EEE3C 1C0B2AC9 B769A6C9 2704BE3F F6C0C75C 2815086C 917819AA
82EF8509 92B044E2 48CA015B B7703328 A60A9DFF 27475FE8 C868CF1E 33037F41
F6B54D71 BB26B172 BB07764C 0805B093 DA0B75CD 0FC332B8 9E421DEB 10EF4640
E43766A7 32B8ACF5 8031B253 26AF5CFB 33520DCA 0E30F1E5 C9A63627 34440ACB
3F0368DD 0B0E3F3A BE744597 4820D2B1 2AF9D788 606318A6 7FCD560B E6DA777B
1EF3CE00 F1B9A366 B6D1D54A AD0388E2 DA333E0D 647E6CCB FF102702 917725FF
2F63BDC2 6DF30203 010001A3 53305130 1D060355 1D0E0416 0414B90C B90FAFDA
1F2782DC 146CA7D0 8D14E721 EF83301F 0603551D 23041830 168014B9 0CB90FAF
DA1F2782 DC146CA7 D08D14E7 21EF8330 0F060355 1D130101 FF040530 030101FF
300D0609 2A864886 F70D0101 0B050003 82010100 2C21E6F0 C64F7362 5B29B2FB
B45BCA4D 6A8E2C8E E5EFA844 7D8FC72C 274D3DA4 012F8940 464A1DE5 EA3D0E0D
37D92810 DC75FD6B 7160B76A 4FD75857 2DC18727 E2CFCB55 AA43C8E2 5A9AF302
FABFEF84 BC3D5CD1 4A2AB3AC D42FD4D6 5F588A68 B8F0788B 75634E4F 37F5D64B
33E533F5 79B81E64 D9232BBE 5F7CBB1A 7AF088CA 0BB04ADB 332680A1 E23F22A7
4F39F12F 82A0D7F3 D00F451E 5A247ABB E333C470 3C0A67D9 3D6DD9A3 554A51B8
DA59EEFD 621970F5 4958AB38 92CECECF 7AF08EE2 803B5F2B 3FB7195D BA49B4E0
4EB859F8 366D1A48 74B86593 6812A3E2 27683CA0 7C7045ED FD45961A C888D693
D75AF59C E28965D3 B2B7931B 3CD50C73 1E0D378A
quit
!
!
license boot level network-advantage addon dna-advantage
memory free low-watermark processor 74862
!
system mtu 8978
diagnostic bootup level minimal
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
!
!
enable secret 9 $9$WsbGbEnlY7ZnOE$8Y5qUmOgCatKFC2M/Kpmov7Dbd08QBhQlA8nlOXjnfA
!
username cisco privilege 15 secret 9 $9$K2c68lctCCR3v.$SgFneM9tcIGiIKFFsAsZDcBT/DX0ty2rJ01pQSVW5LU
username dnacadmin privilege 15 secret 9 $9$ss2NT8jXdGqUGU$QVfZV.IgKGnzd8GNy5oCLpfZvamjwuusTVNBK61XPMQ
!
redundancy
mode sso
!
!
!
!
!
!
class-map match-any system-cpp-police-topology-control
description Topology control
class-map match-any system-cpp-police-sw-forward
description Sw forwarding, L2 LVX data, LOGGING
class-map match-any system-cpp-default
description EWLC control, EWLC data, Inter FED
class-map match-any system-cpp-police-sys-data
description Learning cache ovfl, High Rate App, Exception, EGR Exception, NFL SAMPLED DATA, RPF Failed
class-map match-any system-cpp-police-punt-webauth
description Punt Webauth
class-map match-any system-cpp-police-l2lvx-control
description L2 LVX control packets
class-map match-any system-cpp-police-forus
description Forus Address resolution and Forus traffic
class-map match-any system-cpp-police-multicast-end-station
description MCAST END STATION
class-map match-any system-cpp-police-multicast
description Transit Traffic and MCAST Data
class-map match-any system-cpp-police-l2-control
description L2 control
class-map match-any system-cpp-police-dot1x-auth
description DOT1X Auth
class-map match-any system-cpp-police-data
description ICMP redirect, ICMP_GEN and BROADCAST
class-map match-any system-cpp-police-stackwise-virt-control
description Stackwise Virtual
class-map match-any non-client-nrt-class
class-map match-any system-cpp-police-routing-control
description Routing control and Low Latency
class-map match-any system-cpp-police-protocol-snooping
description Protocol snooping
class-map match-any system-cpp-police-dhcp-snooping
description DHCP snooping
class-map match-any system-cpp-police-system-critical
description System Critical and Gold Pkt
!
policy-map system-cpp-policy
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0
vrf forwarding Mgmt-vrf
ip address dhcp
negotiation auto
!
interface GigabitEthernet1/0/1
!
interface GigabitEthernet1/0/2
!
interface GigabitEthernet1/0/3
!
interface GigabitEthernet1/0/4
!
interface GigabitEthernet1/0/5
description SDA-HQ-FIS-01
switchport access vlan 12
!
interface GigabitEthernet1/0/6
description SDA-HQ-FIS-01
switchport access vlan 12
!
interface GigabitEthernet1/0/7
!
interface GigabitEthernet1/0/8
!
interface Vlan1
no ip address
!
interface Vlan12
ip address 172.17.0.6 255.255.255.128
ip ospf mtu-ignore
!
router ospf 100
router-id 172.17.0.6
network 172.17.0.0 0.0.0.127 area 0
!
ip forward-protocol nd
ip tcp mss 1280
ip tcp window-size 212000
ip http server
ip http authentication local
ip http secure-server
ip ssh bulk-mode 131072
!
!
!
!
snmp-server community ciscoro RO
snmp-server community ciscorw RW
!
!
!
!
control-plane
service-policy input system-cpp-policy
!
!
alias router show do show
alias interface show do show
alias configure show do show
!
line con 0
stopbits 1
line vty 0 4
privilege level 15
transport input ssh
line vty 5 98
privilege level 15
transport input ssh
!
!
!
!
!
!
!
netconf-yang
endSDA-HQ-FIS-01 config
SDA-HQ-FIS-01#show run
Building configuration...
Current configuration : 8321 bytes
!
! Last configuration change at 03:43:50 UTC Mon Oct 6 2025
!
version 17.12
service timestamps debug datetime msec
service timestamps log datetime msec
platform punt-keepalive disable-kernel-core
!
hostname SDA-HQ-FIS-01
!
!
vrf definition Mgmt-vrf
!
address-family ipv4
exit-address-family
!
address-family ipv6
exit-address-family
!
aaa new-model
!
!
aaa authentication login default local
aaa authorization exec default local
!
!
aaa session-id common
switch 1 provision c9kv-uadp-8p
!
!
!
!
ip routing
!
!
!
!
!
!
!
!
login on-success log
vtp version 1
!
!
!
!
!
!
!
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
hash sha256
!
crypto pki trustpoint TP-self-signed-3709873604
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-3709873604
revocation-check none
rsakeypair TP-self-signed-3709873604
hash sha256
!
!
crypto pki certificate chain SLA-TrustPoint
certificate ca 01
30820321 30820209 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363
6F204C69 63656E73 696E6720 526F6F74 20434130 1E170D31 33303533 30313934
3834375A 170D3338 30353330 31393438 34375A30 32310E30 0C060355 040A1305
43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720
526F6F74 20434130 82012230 0D06092A 864886F7 0D010101 05000382 010F0030
82010A02 82010100 A6BCBD96 131E05F7 145EA72C 2CD686E6 17222EA1 F1EFF64D
CBB4C798 212AA147 C655D8D7 9471380D 8711441E 1AAF071A 9CAE6388 8A38E520
1C394D78 462EF239 C659F715 B98C0A59 5BBB5CBD 0CFEBEA3 700A8BF7 D8F256EE
4AA4E80D DB6FD1C9 60B1FD18 FFC69C96 6FA68957 A2617DE7 104FDC5F EA2956AC
7390A3EB 2B5436AD C847A2C5 DAB553EB 69A9A535 58E9F3E3 C0BD23CF 58BD7188
68E69491 20F320E7 948E71D7 AE3BCC84 F10684C7 4BC8E00F 539BA42B 42C68BB7
C7479096 B4CB2D62 EA2F505D C7B062A4 6811D95B E8250FC4 5D5D5FB8 8F27D191
C55F0D76 61F9A4CD 3D992327 A8BB03BD 4E6D7069 7CBADF8B DF5F4368 95135E44
DFC7C6CF 04DD7FD1 02030100 01A34230 40300E06 03551D0F 0101FF04 04030201
06300F06 03551D13 0101FF04 05300301 01FF301D 0603551D 0E041604 1449DC85
4B3D31E5 1B3E6A17 606AF333 3D3B4C73 E8300D06 092A8648 86F70D01 010B0500
03820101 00507F24 D3932A66 86025D9F E838AE5C 6D4DF6B0 49631C78 240DA905
604EDCDE FF4FED2B 77FC460E CD636FDB DD44681E 3A5673AB 9093D3B1 6C9E3D8B
D98987BF E40CBD9E 1AECA0C2 2189BB5C 8FA85686 CD98B646 5575B146 8DFC66A8
467A3DF4 4D565700 6ADF0F0D CF835015 3C04FF7C 21E878AC 11BA9CD2 55A9232C
7CA7B7E6 C1AF74F6 152E99B7 B1FCF9BB E973DE7F 5BDDEB86 C71E3B49 1765308B
5FB0DA06 B92AFE7F 494E8A9E 07B85737 F3A58BE1 1A48A229 C37C1E69 39F08678
80DDCD16 D6BACECA EEBC7CF9 8428787B 35202CDC 60E4616A B623CDBD 230E3AFB
418616A9 4093E049 4D10AB75 27E86F73 932E35B5 8862FDAE 0275156F 719BB2F0
D697DF7F 28
quit
crypto pki certificate chain TP-self-signed-3709873604
certificate self-signed 01
30820330 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
31312F30 2D060355 04030C26 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 33373039 38373336 3034301E 170D3235 31303035 31393137
31335A17 0D333531 30303531 39313731 335A3031 312F302D 06035504 030C2649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D33 37303938
37333630 34308201 22300D06 092A8648 86F70D01 01010500 0382010F 00308201
0A028201 0100C759 F84AFB37 54B78EFF 9273D1C3 0D6C5070 A83E4D91 FCF8D23C
448032EA 06A19825 5079D281 48A6864B B52DD90F 3B8D38FD A94746E0 2F704FE5
9AEB1C6E 2641C6DE 7D8410A4 E9A7C403 F3C81746 2E68527D 3B7AD8DA 2CD42017
5605E8A7 2F2A9F7B 9BDCC916 A305847B 10338575 99FCB13B C698BC10 0040FC1B
008AC100 0CBE486E 2A3674F6 C3C29501 3225EB05 20948377 C5FB1B80 30B7C775
059FC53D 43CDA2BC 4551028A C92B19AE 26A16499 2D95D48E 7BDD5B2B 499E9825
A3355A37 BC1A0581 E5FAD1CD 9D71ED1F 394DCE1F 48BBB3B8 4B077745 385FE76D
F2B90AC7 9F048D9E 29B83A57 022FBA37 4BADD628 D7DA69BA 9172BEDE 7518F3BB
2E7878D3 A31F0203 010001A3 53305130 1D060355 1D0E0416 0414021D 7AFCBB5E
378C9A0F 5864A7C3 A633ABE1 4517301F 0603551D 23041830 16801402 1D7AFCBB
5E378C9A 0F5864A7 C3A633AB E1451730 0F060355 1D130101 FF040530 030101FF
300D0609 2A864886 F70D0101 0B050003 82010100 95998C49 0D9ABEC9 1E1B1DE8
54C08FCE 536685EB 9E3E8B44 FC13DDA4 658DD6D8 662DF08A 41749F88 891194E9
AF06D23D 0980F173 4DDA2F20 3BC6751F 4BF45821 6C4071BE 9F9B24EA 47B224EB
6E22FDA9 7B57181E 54691EFD DB0EC11D CBB42446 E4728F57 CA901250 A7C69207
36DEDB9A 4B377903 92FC2684 AF2EAC79 5E45EB4C 29F8F083 77099D29 3877C84D
CC7A28D8 2C1E8B2F 4E1361EE 2ABA2D60 A6DD101F 12560715 29439D98 AA1F3167
404629FA D6CB1F8F 5A5A4C6E 181178BF 9500A404 1F3D13C8 22FE5BEA 8E8F247E
BBCAE461 365EA67E DFF2F9F1 97AD52D2 8269E54F B4E63F25 797C2720 258F8505
4ACCE8A9 6CC78BDA 532508B4 9D74C3A0 BE6F2A7B
quit
!
!
license boot level network-advantage addon dna-advantage
memory free low-watermark processor 74862
!
system mtu 8978
diagnostic bootup level minimal
!
spanning-tree mode rapid-pvst
spanning-tree extend system-id
!
!
!
enable secret 9 $9$WsbGbEnlY7ZnOE$8Y5qUmOgCatKFC2M/Kpmov7Dbd08QBhQlA8nlOXjnfA
!
username cisco privilege 15 secret 9 $9$K2c68lctCCR3v.$SgFneM9tcIGiIKFFsAsZDcBT/DX0ty2rJ01pQSVW5LU
username dnacadmin privilege 15 secret 9 $9$ss2NT8jXdGqUGU$QVfZV.IgKGnzd8GNy5oCLpfZvamjwuusTVNBK61XPMQ
!
redundancy
mode sso
!
!
!
!
!
!
class-map match-any system-cpp-police-topology-control
description Topology control
class-map match-any system-cpp-police-sw-forward
description Sw forwarding, L2 LVX data, LOGGING
class-map match-any system-cpp-default
description EWLC control, EWLC data, Inter FED
class-map match-any system-cpp-police-sys-data
description Learning cache ovfl, High Rate App, Exception, EGR Exception, NFL SAMPLED DATA, RPF Failed
class-map match-any system-cpp-police-punt-webauth
description Punt Webauth
class-map match-any system-cpp-police-l2lvx-control
description L2 LVX control packets
class-map match-any system-cpp-police-forus
description Forus Address resolution and Forus traffic
class-map match-any system-cpp-police-multicast-end-station
description MCAST END STATION
class-map match-any system-cpp-police-multicast
description Transit Traffic and MCAST Data
class-map match-any system-cpp-police-l2-control
description L2 control
class-map match-any system-cpp-police-dot1x-auth
description DOT1X Auth
class-map match-any system-cpp-police-data
description ICMP redirect, ICMP_GEN and BROADCAST
class-map match-any system-cpp-police-stackwise-virt-control
description Stackwise Virtual
class-map match-any non-client-nrt-class
class-map match-any system-cpp-police-routing-control
description Routing control and Low Latency
class-map match-any system-cpp-police-protocol-snooping
description Protocol snooping
class-map match-any system-cpp-police-dhcp-snooping
description DHCP snooping
class-map match-any system-cpp-police-system-critical
description System Critical and Gold Pkt
!
policy-map system-cpp-policy
!
!
!
!
!
!
!
!
!
!
!
!
interface GigabitEthernet0/0
vrf forwarding Mgmt-vrf
ip address dhcp
negotiation auto
!
interface GigabitEthernet1/0/1
!
interface GigabitEthernet1/0/2
!
interface GigabitEthernet1/0/3
!
interface GigabitEthernet1/0/4
!
interface GigabitEthernet1/0/5
description SDA-HQ-FIS-01
switchport access vlan 12
!
interface GigabitEthernet1/0/6
description SDA-HQ-FIS-01
switchport access vlan 12
!
interface GigabitEthernet1/0/7
description SDA-HQ-FBS-01
switchport access vlan 12
!
interface GigabitEthernet1/0/8
description SDA-HQ-FBS-01
switchport access vlan 12
!
interface Vlan1
no ip address
!
interface Vlan12
ip address 172.17.0.5 255.255.255.128
ip ospf mtu-ignore
!
router ospf 100
router-id 172.17.0.5
network 172.17.0.0 0.0.0.127 area 0
!
ip forward-protocol nd
ip tcp mss 1280
ip tcp window-size 212000
ip http server
ip http authentication local
ip http secure-server
ip ssh bulk-mode 131072
!
!
!
!
snmp-server community ciscoro RO
snmp-server community ciscorw RW
!
!
!
!
control-plane
service-policy input system-cpp-policy
!
!
alias router show do show
alias interface show do show
alias configure show do show
!
line con 0
stopbits 1
line vty 0 4
privilege level 15
transport input ssh
line vty 5 98
privilege level 15
transport input ssh
!
!
!
!
!
!
!
netconf-yang
endshow netconf-yang status
If you just want to use DNAC without SDA and take advantage of things such as image management and telemetry, you can use DNAC, but SDA changes the way LAN operates
one very important point to keep in mind is that we need is the latency requirements for SDA between DNAC and devices is 100ms and 200ms is kind of pushing
From ISE we only have 100ms to play with anyway
latency requirement between WLC and AP is 20ms
within the cluster of DNAC (which includes ISE as policy node) needs to be 10 msec
another requirement is that all devices be configured with SSH access with credentials that were configured in DNAC with full access and not just enable prompt
Device controllability during discovery means that configuration changes will be done during inventory / discovery or when device is associated to site, it is enabled by default
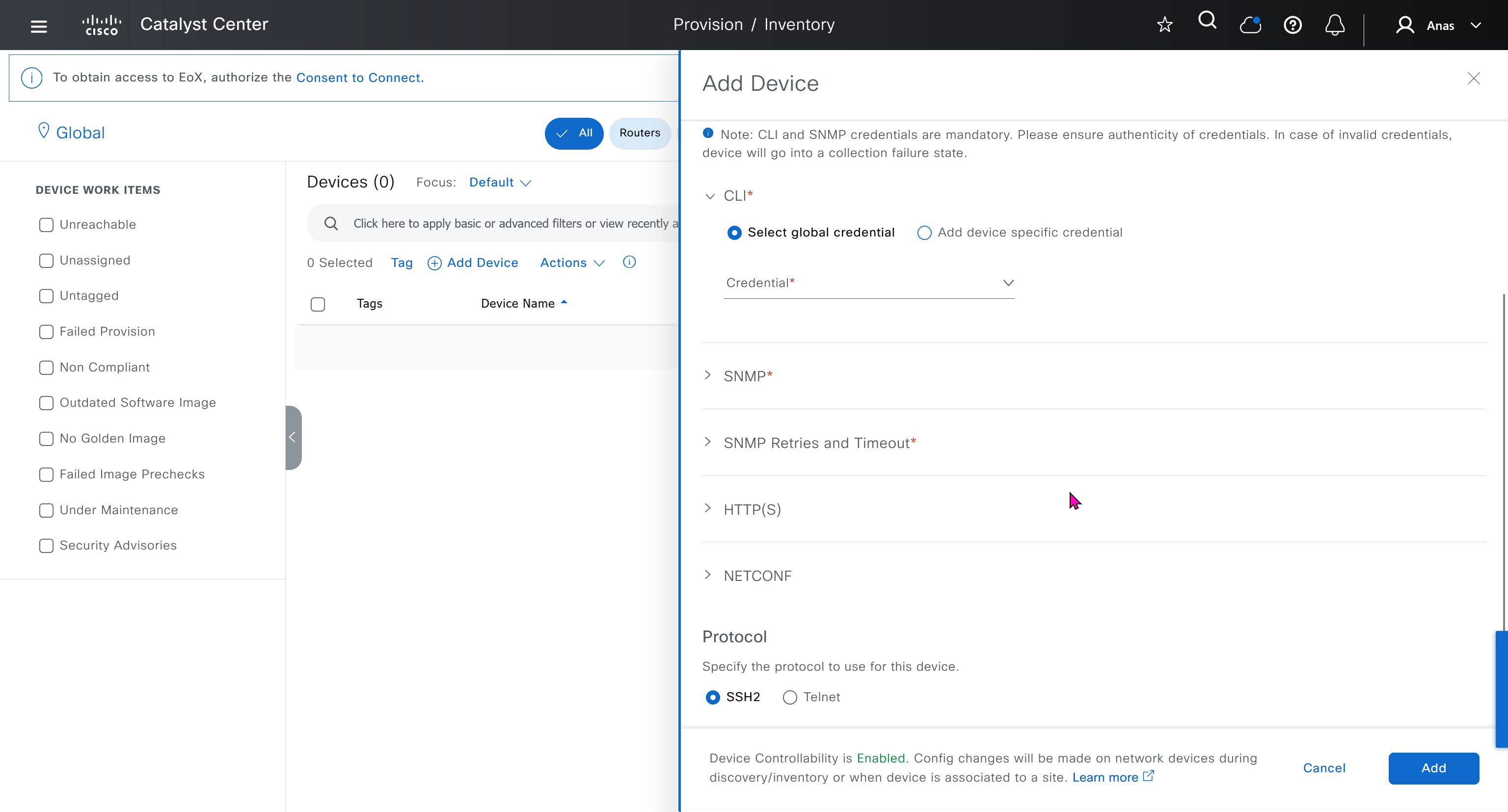

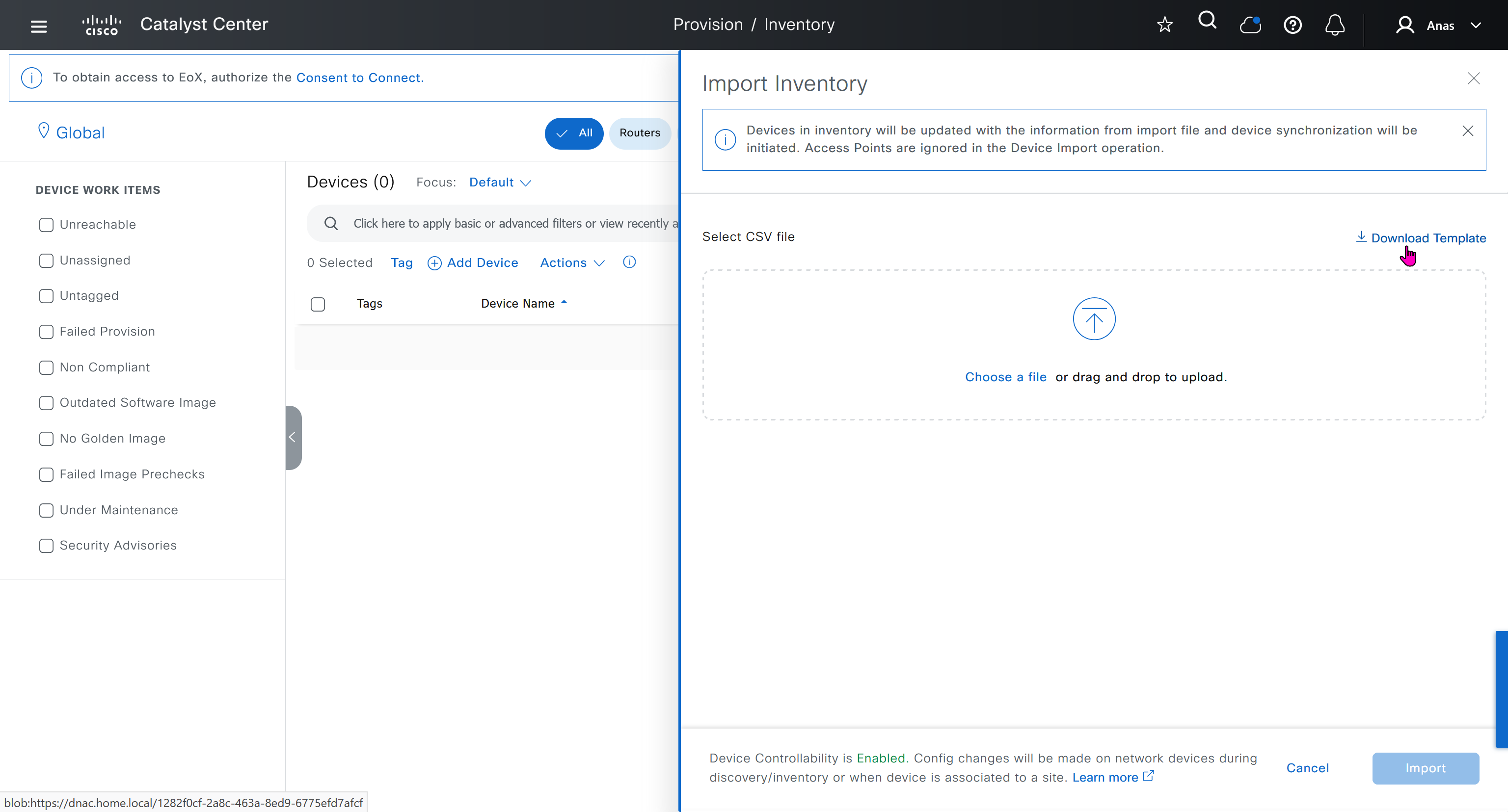

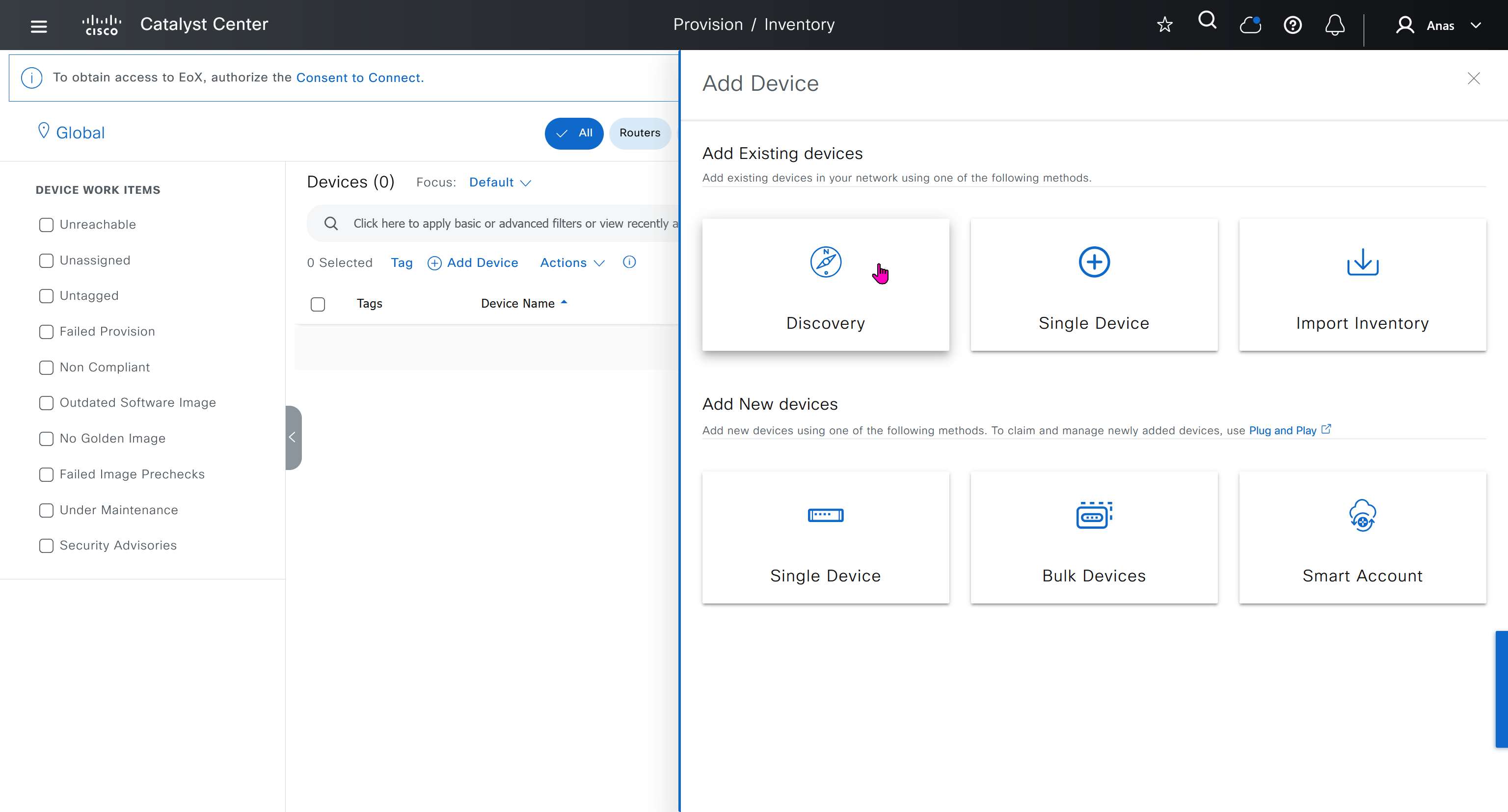
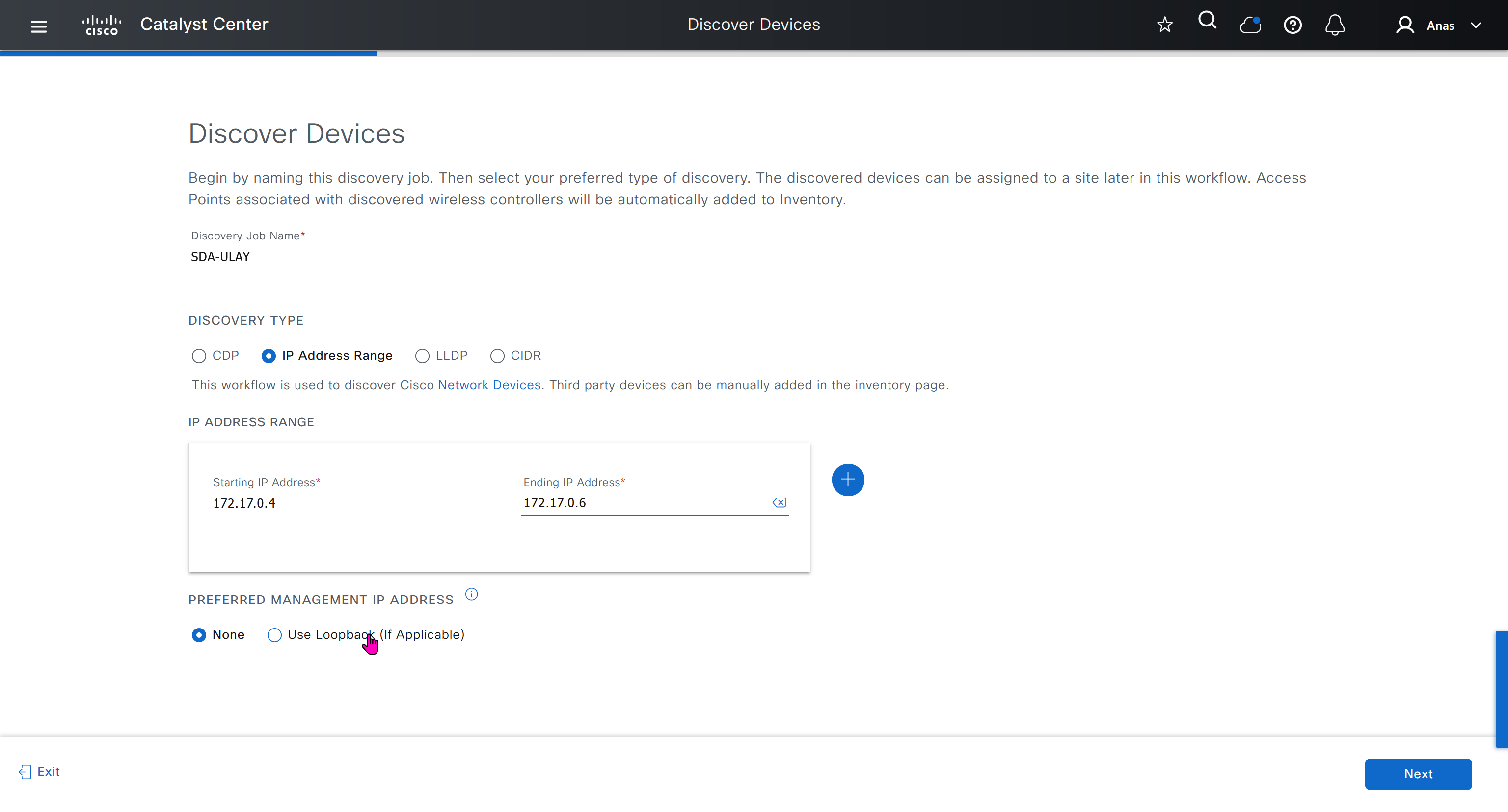
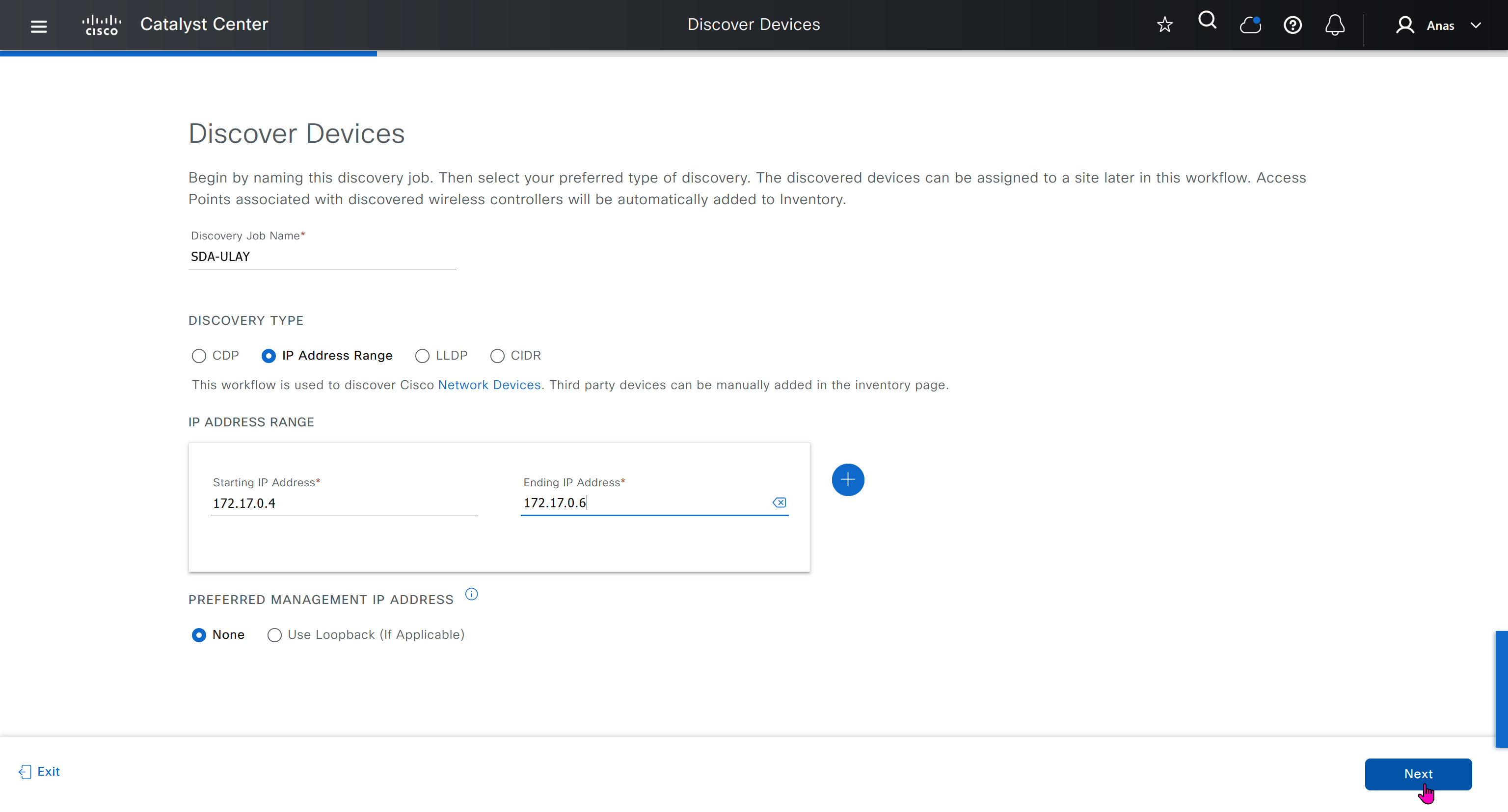
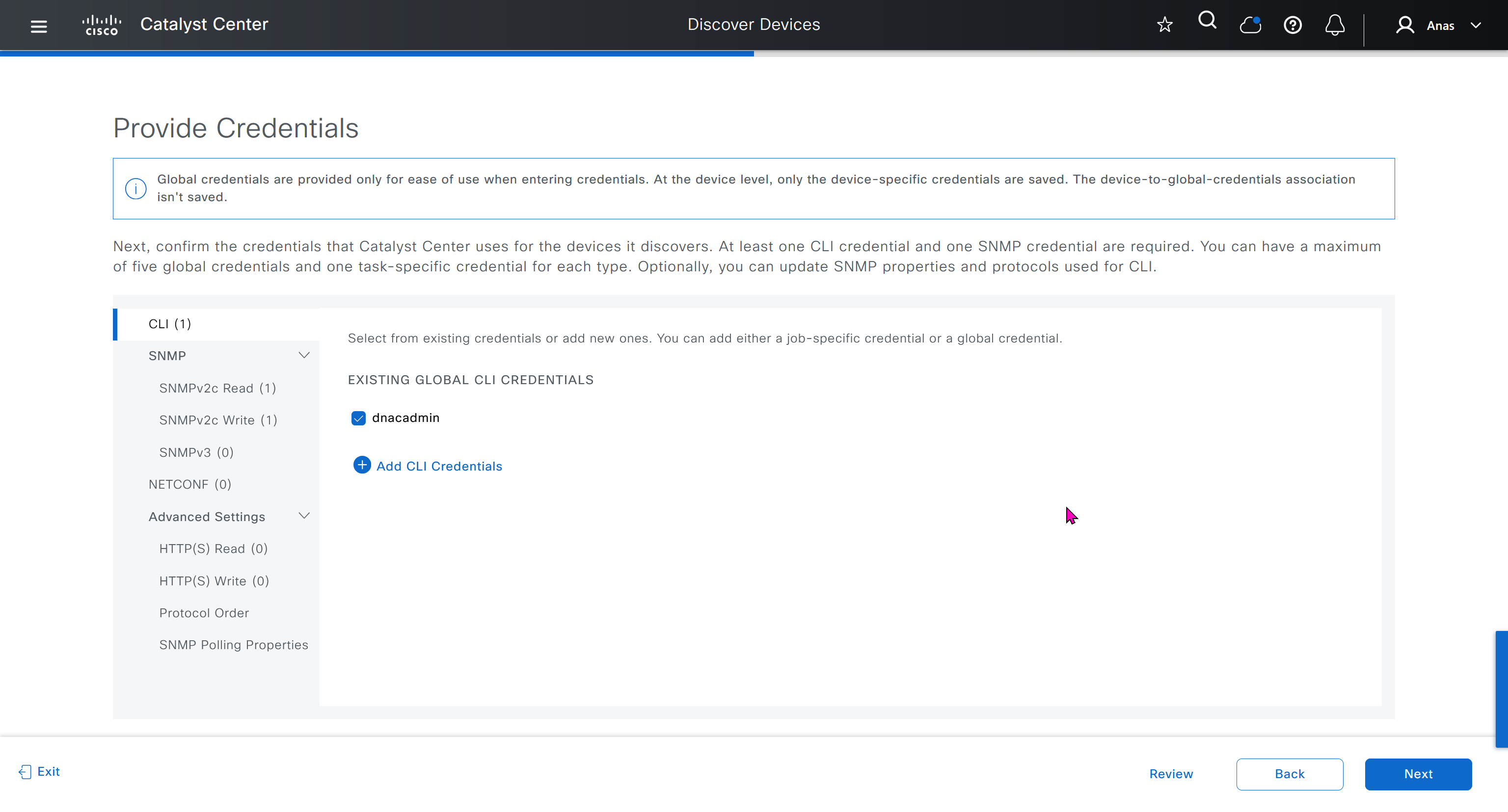
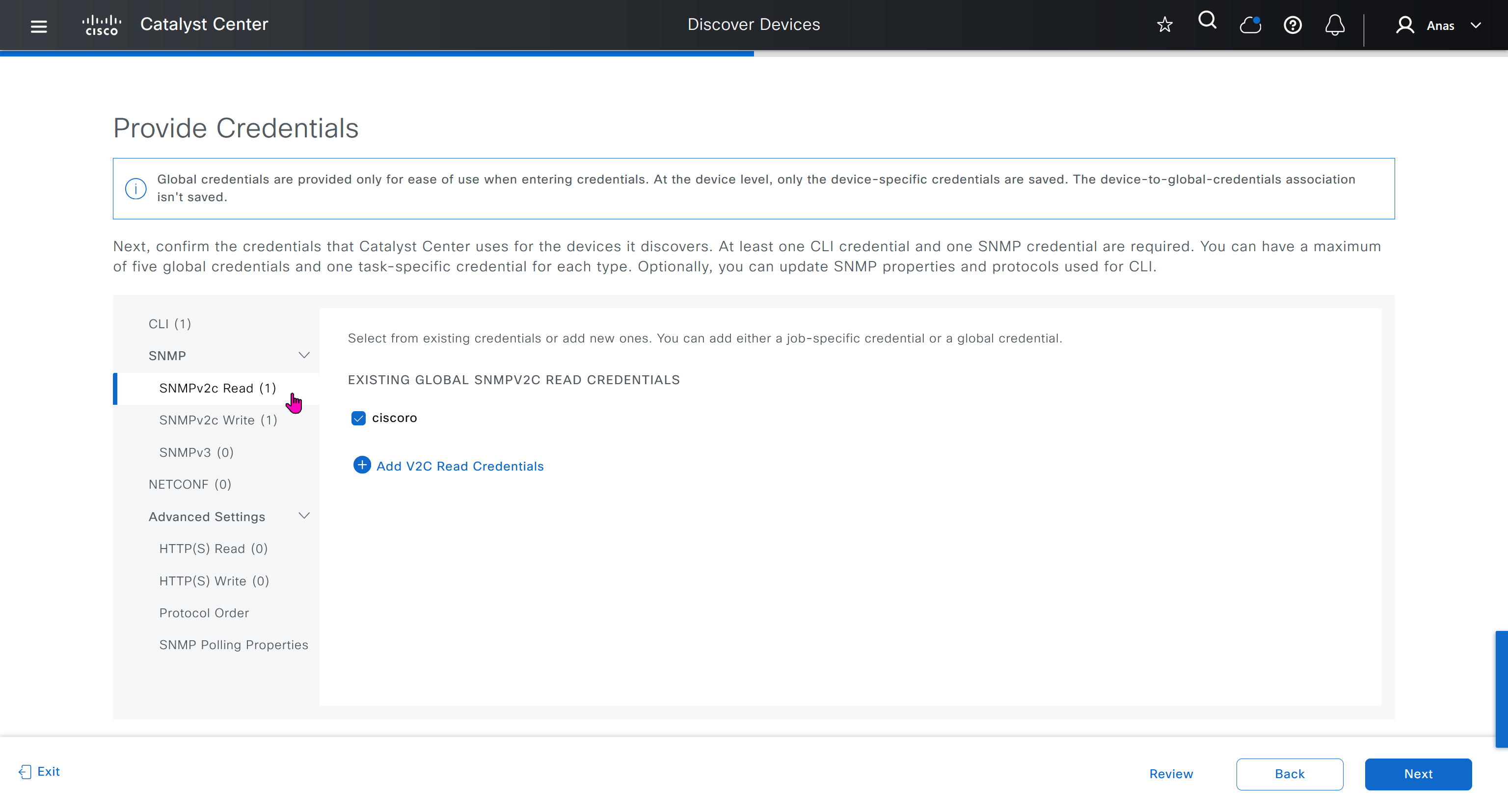
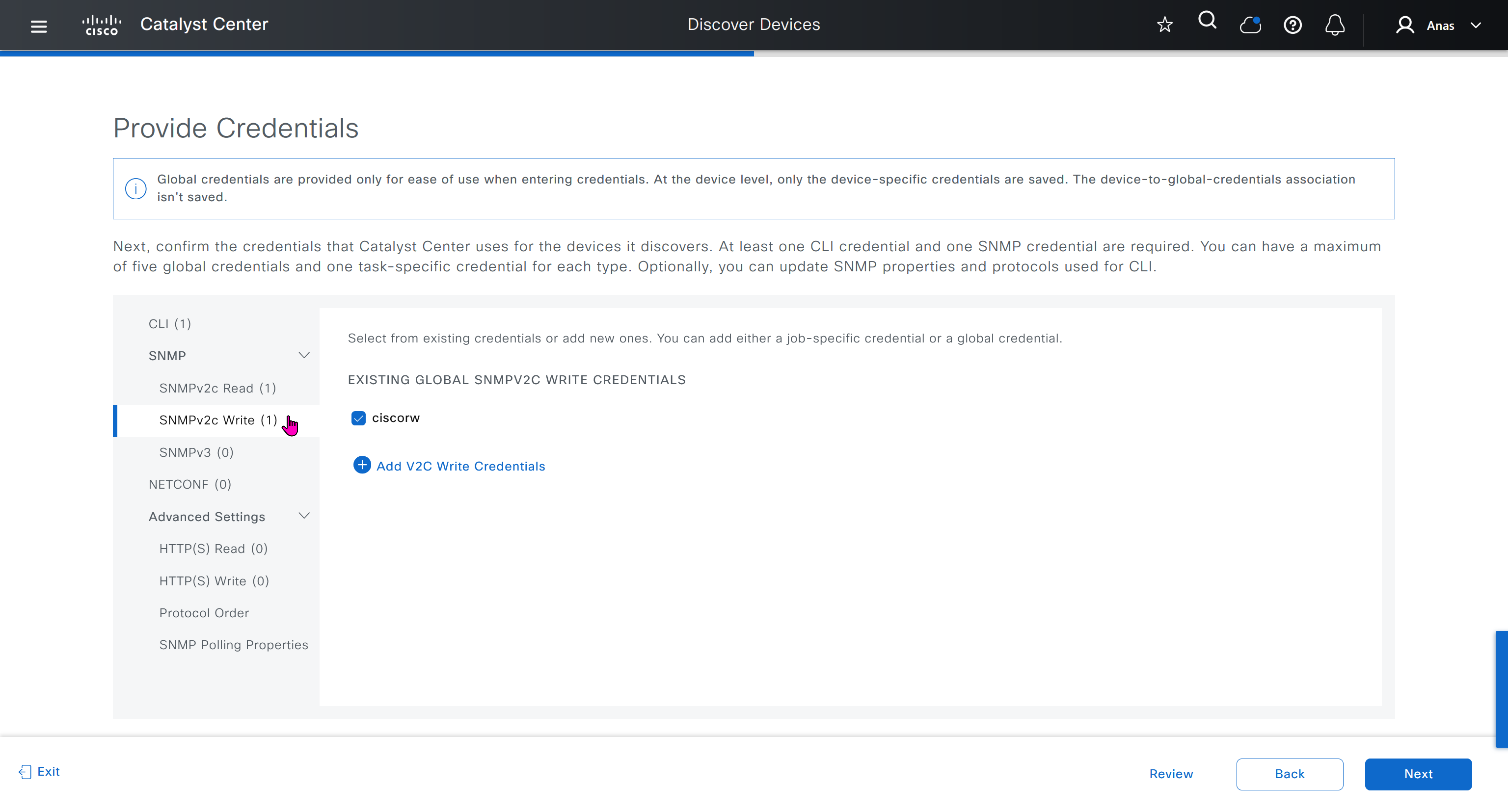

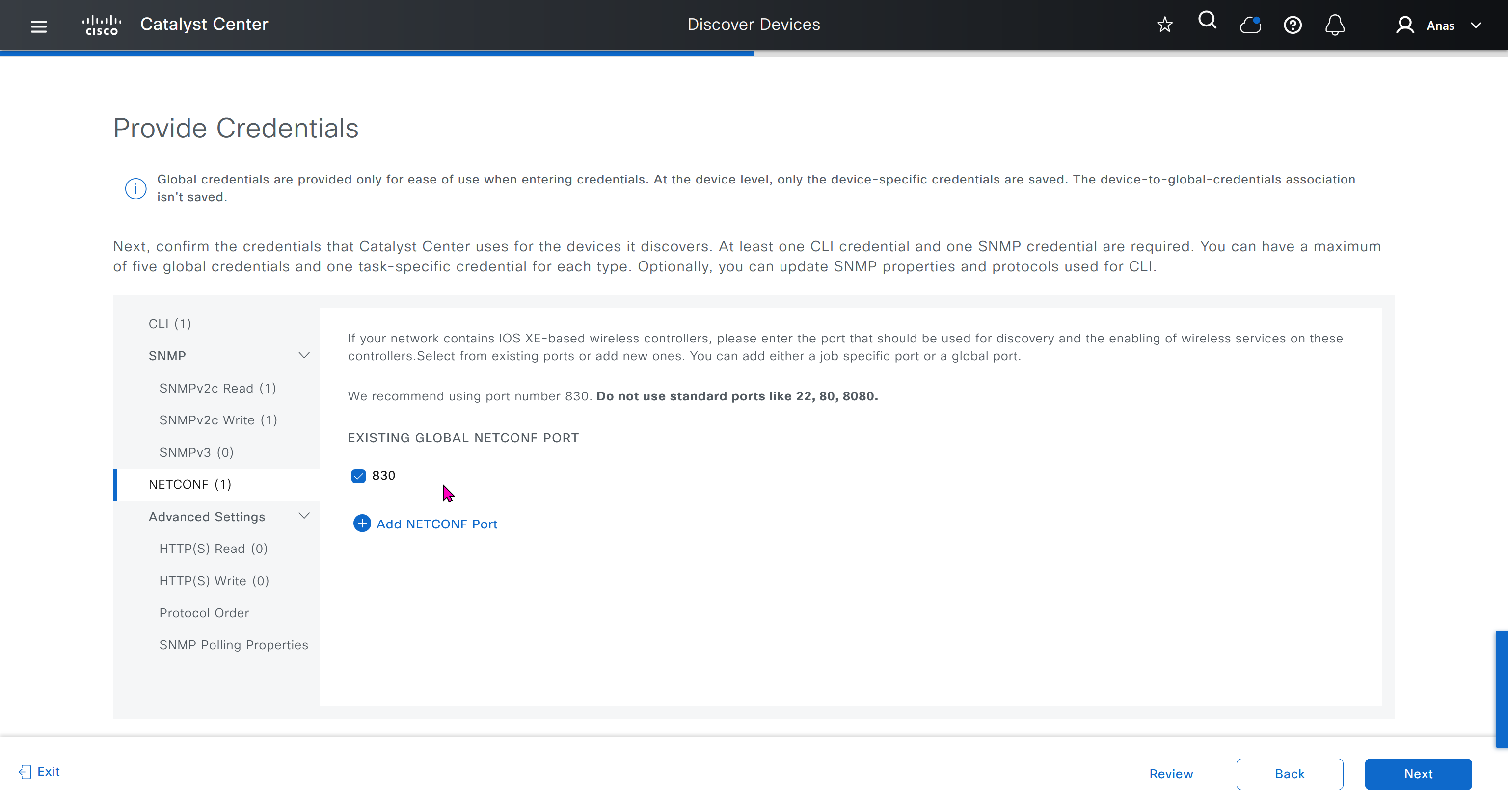
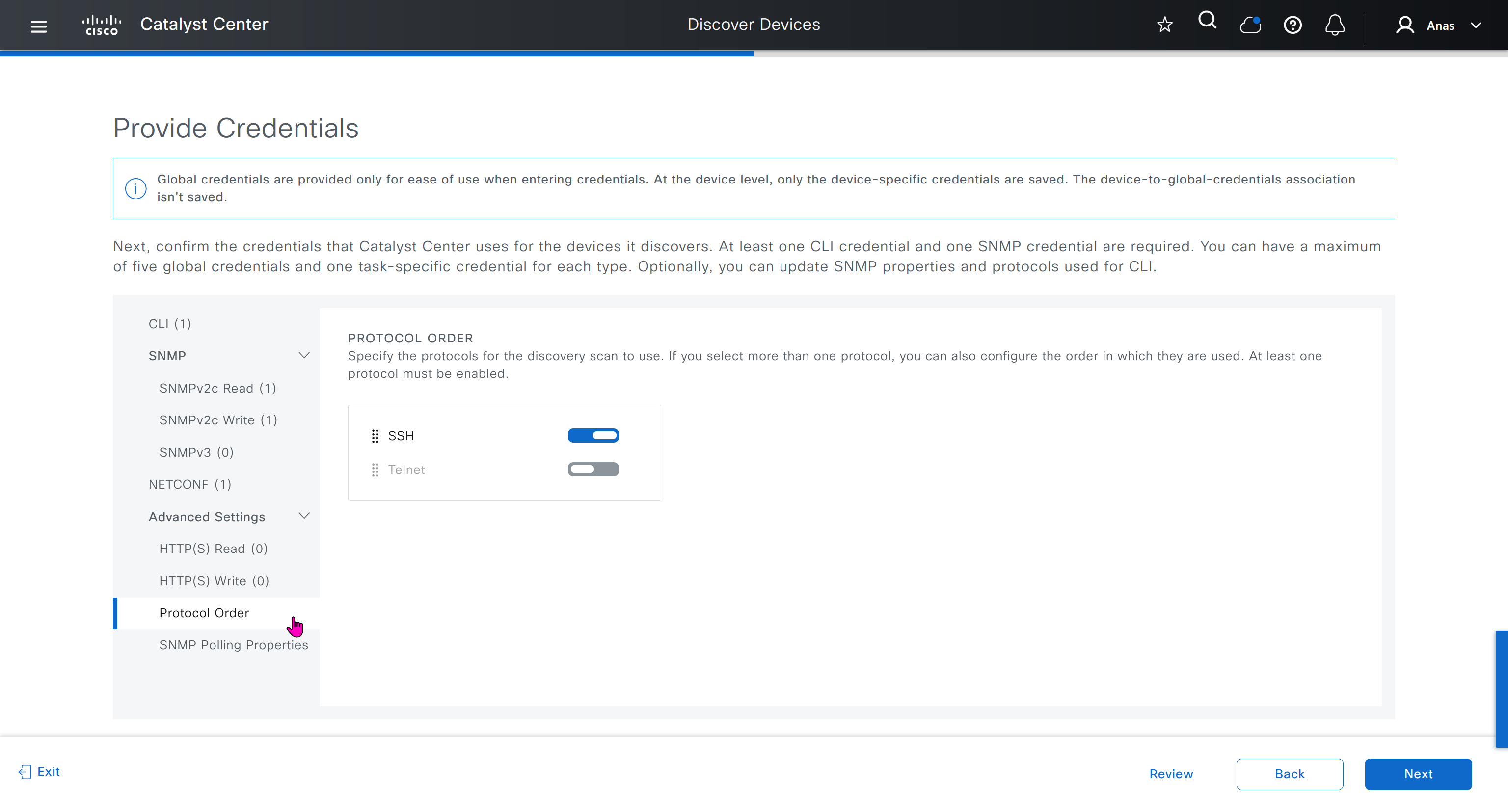
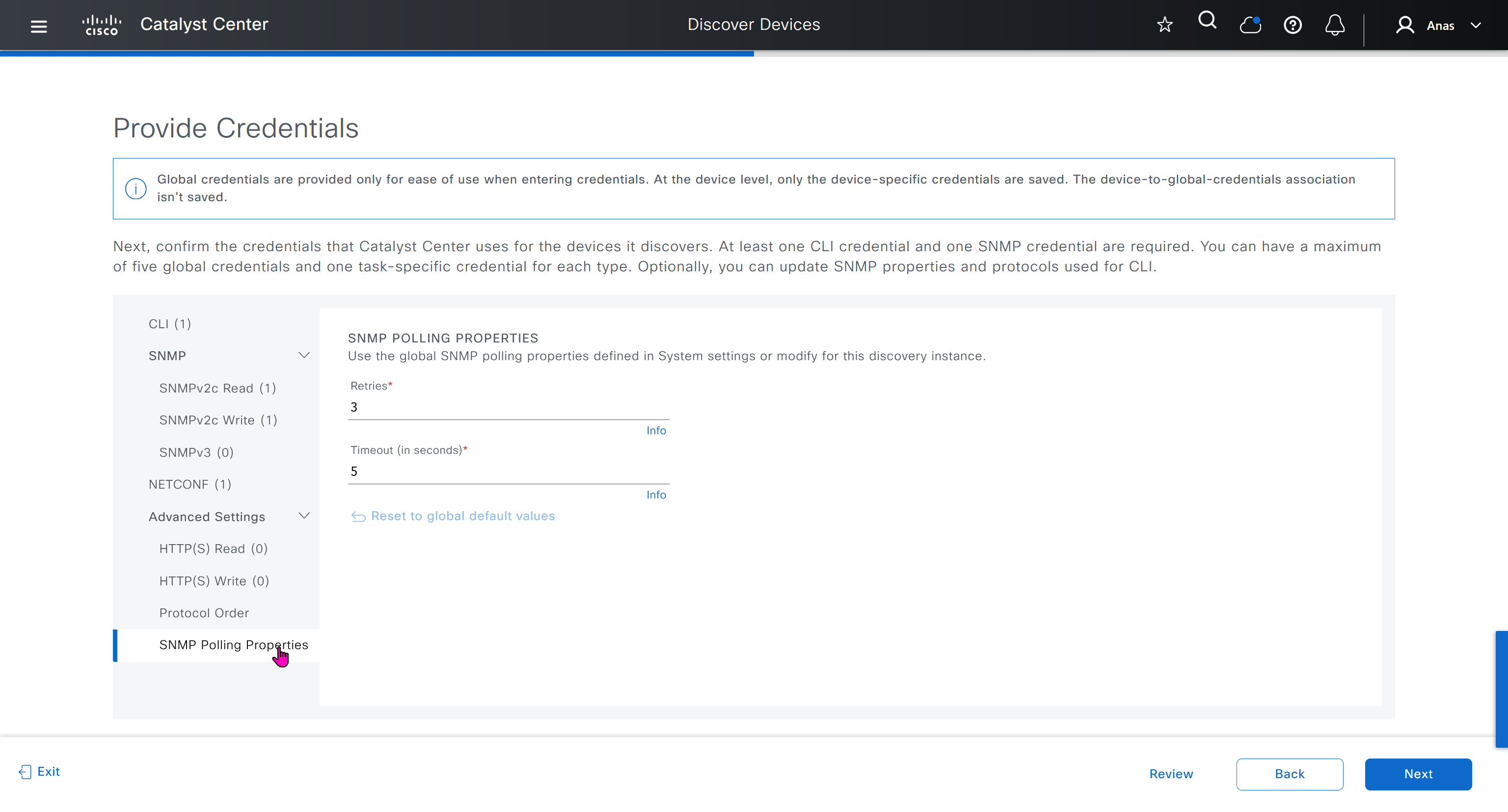
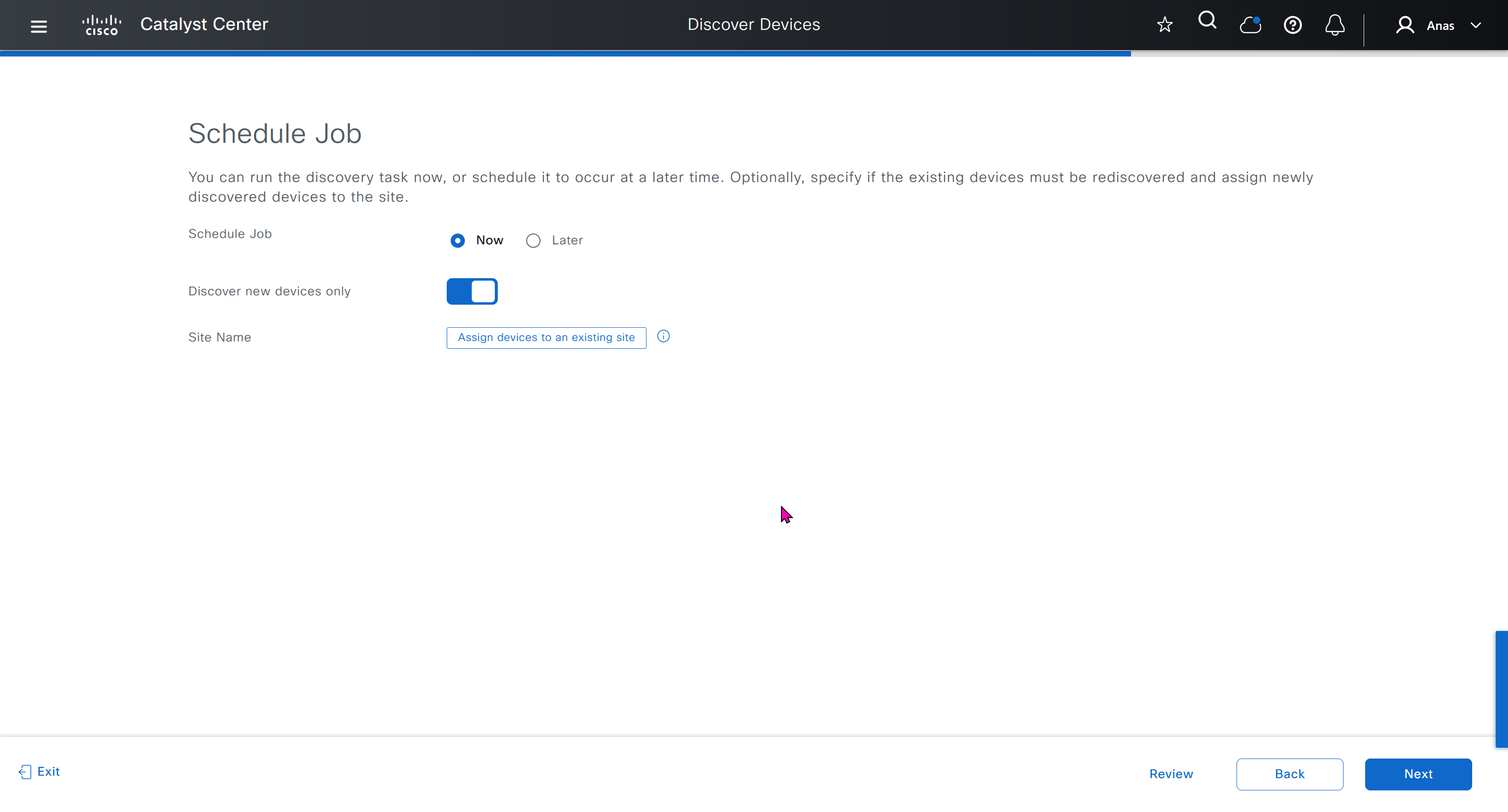

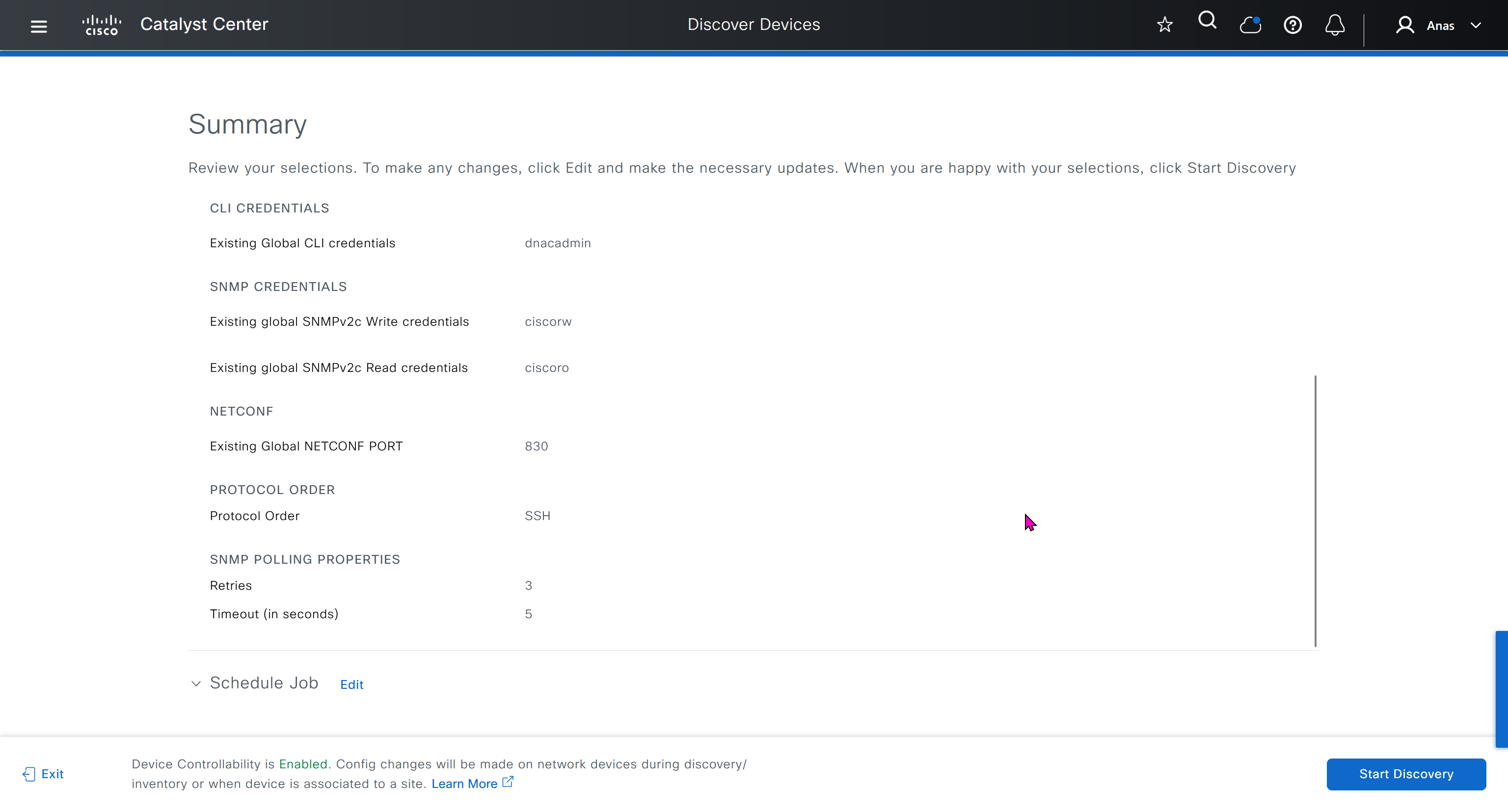
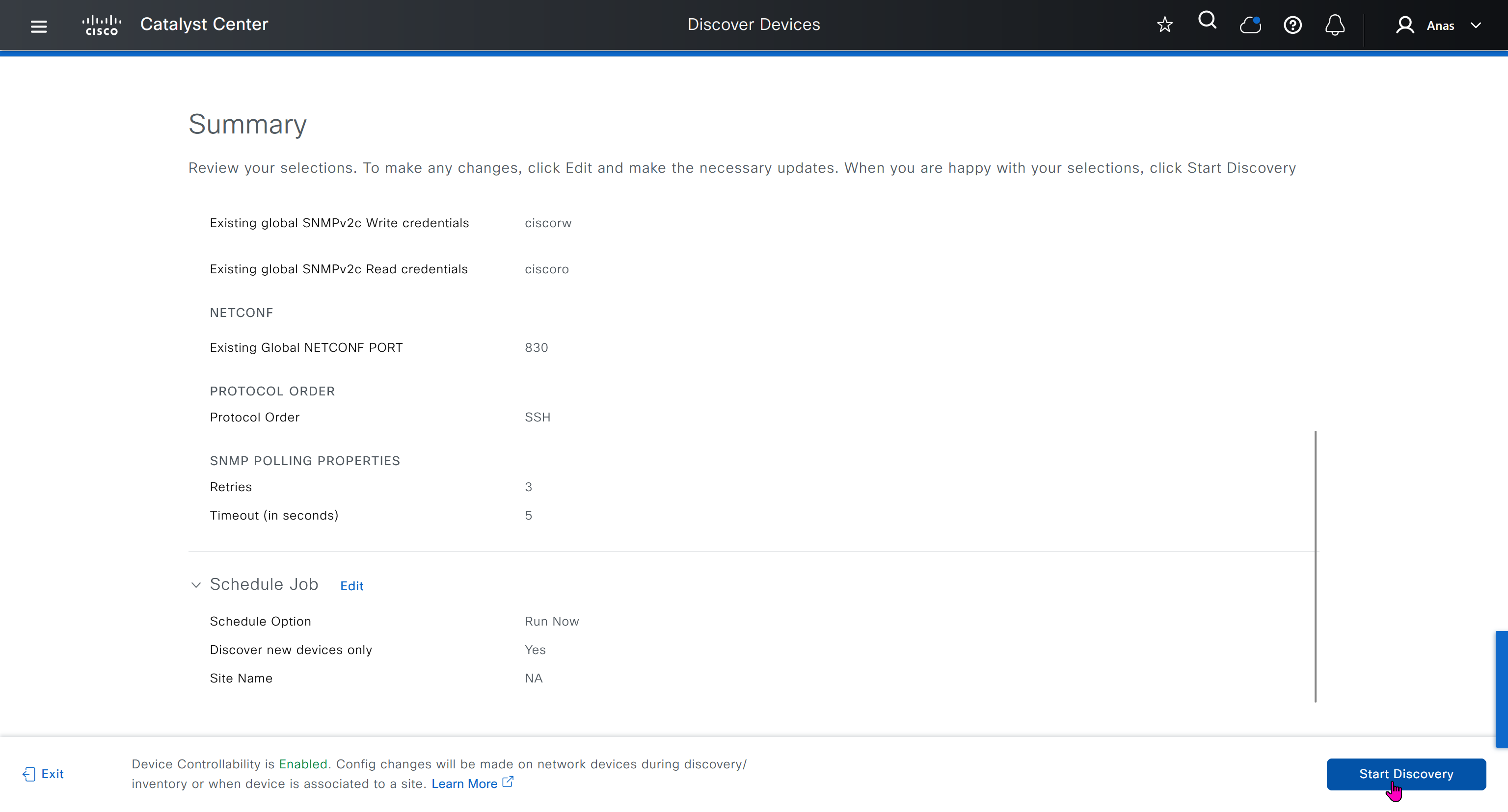
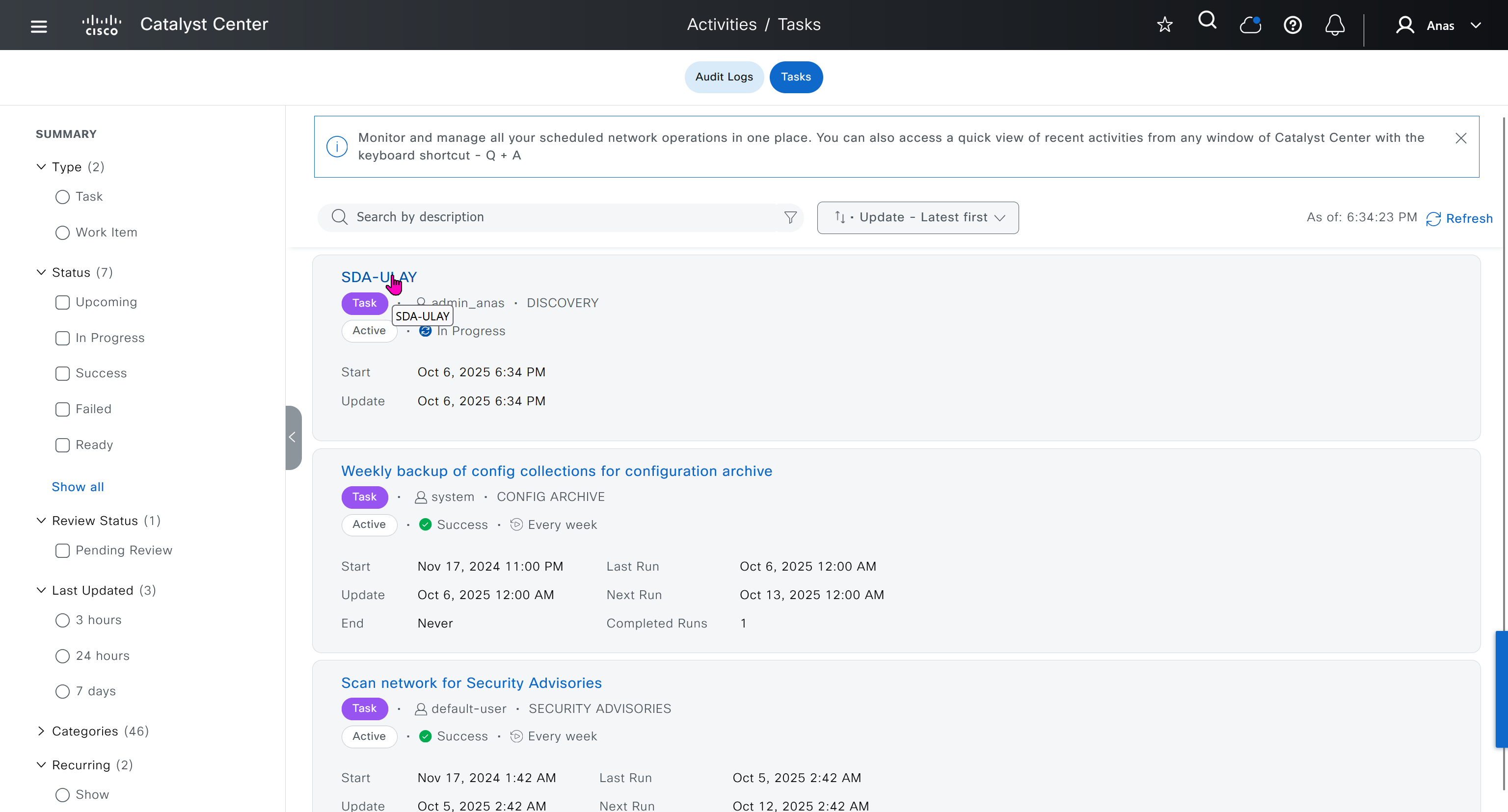

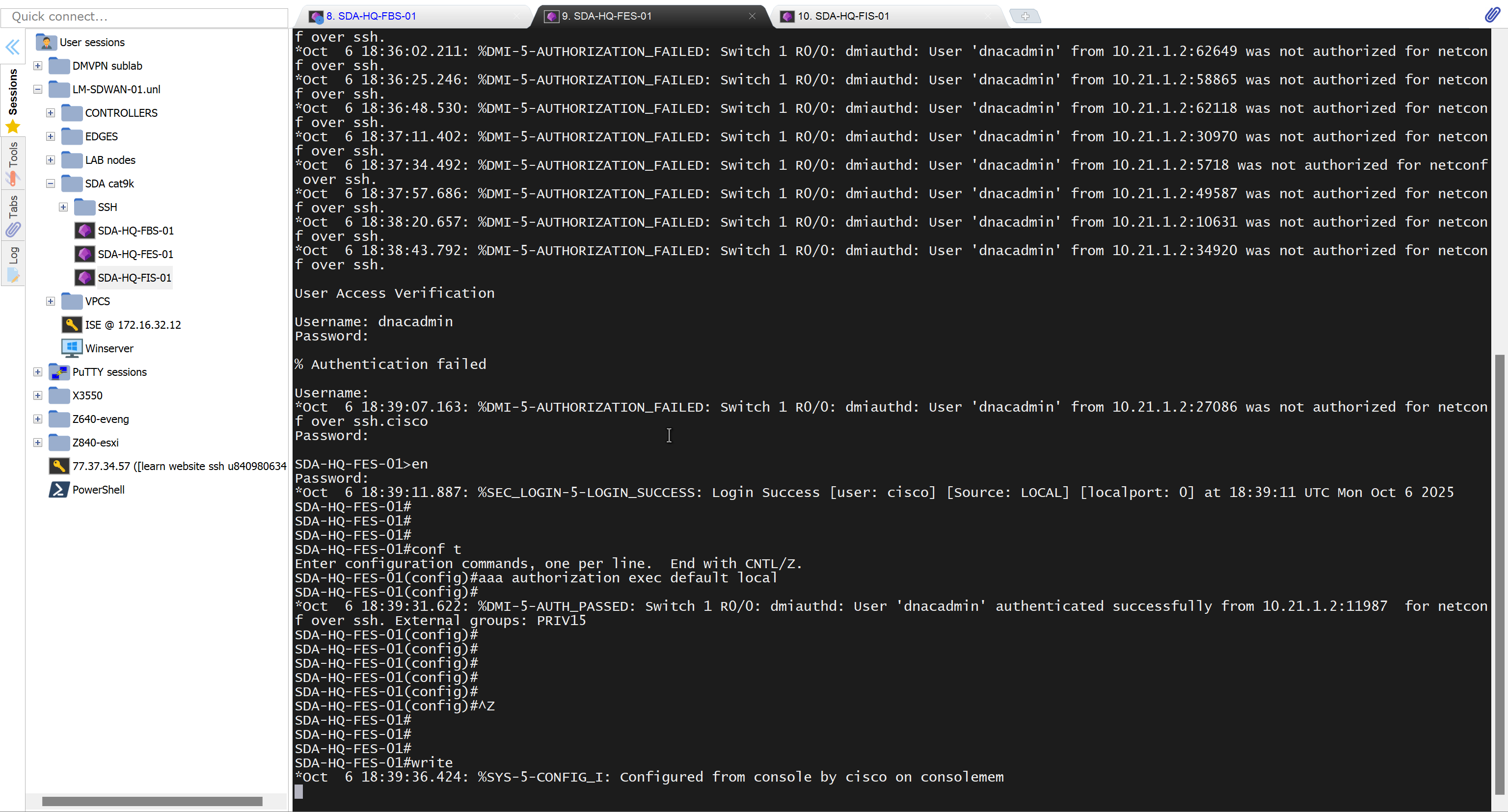

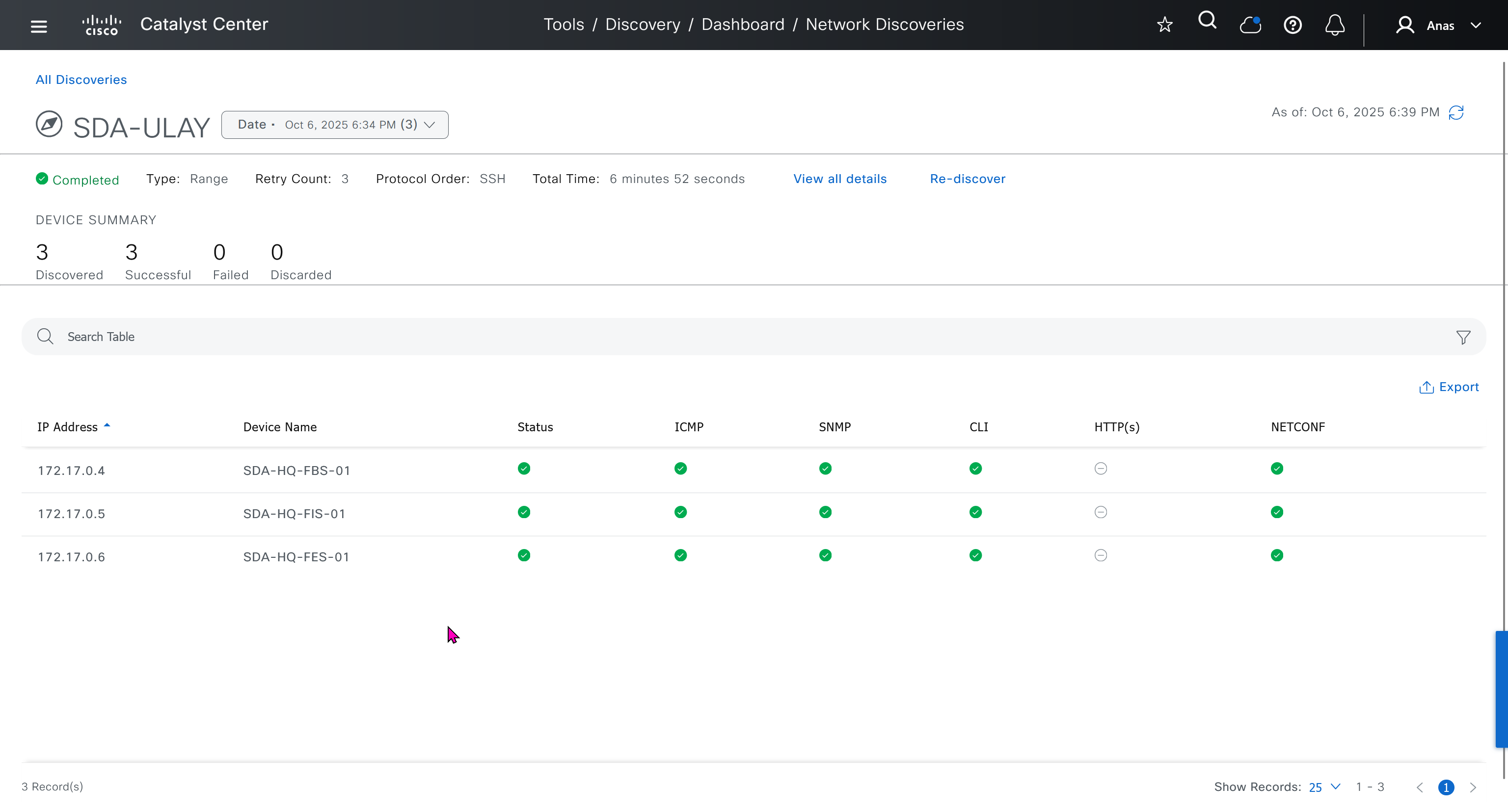

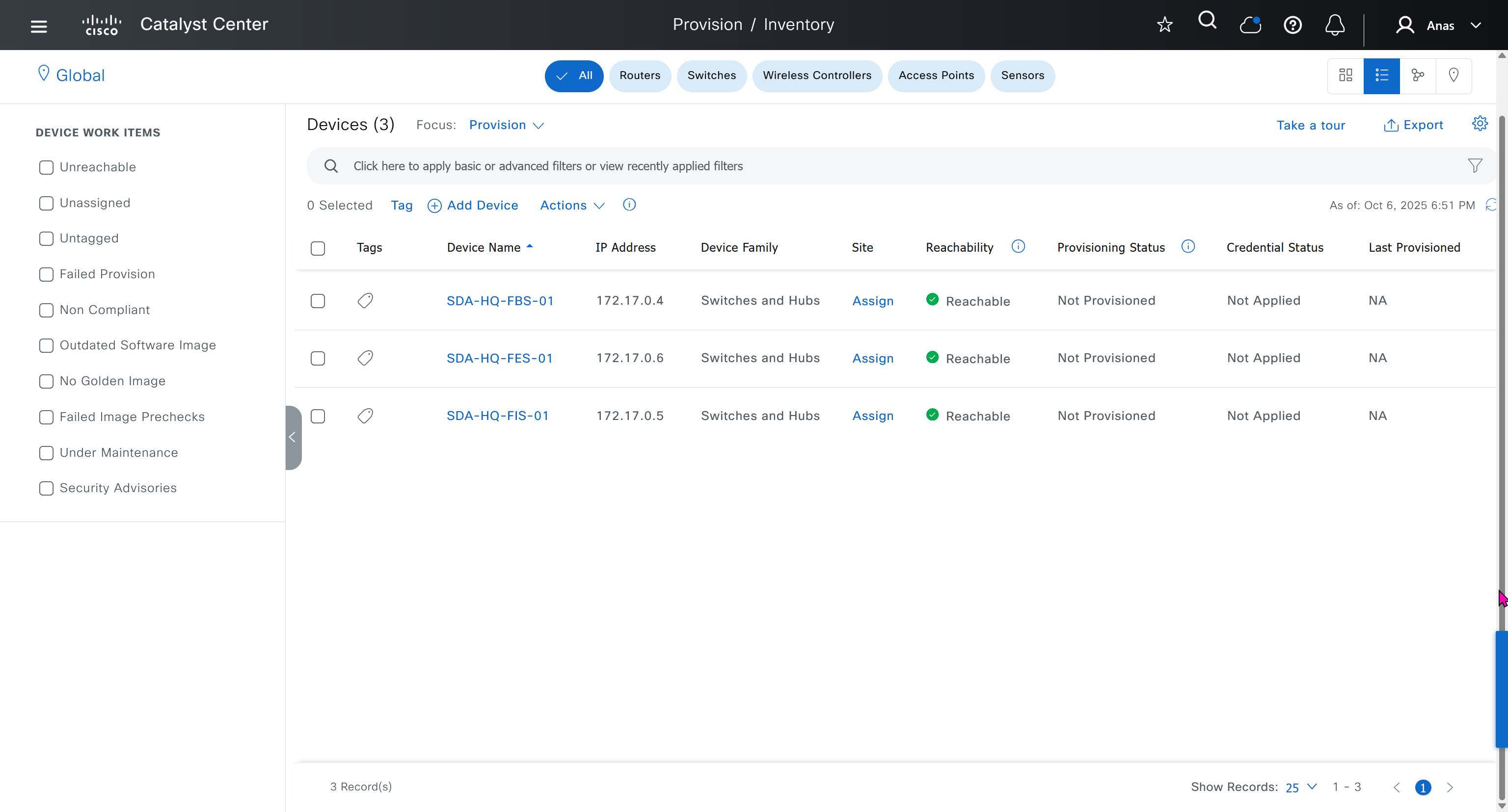
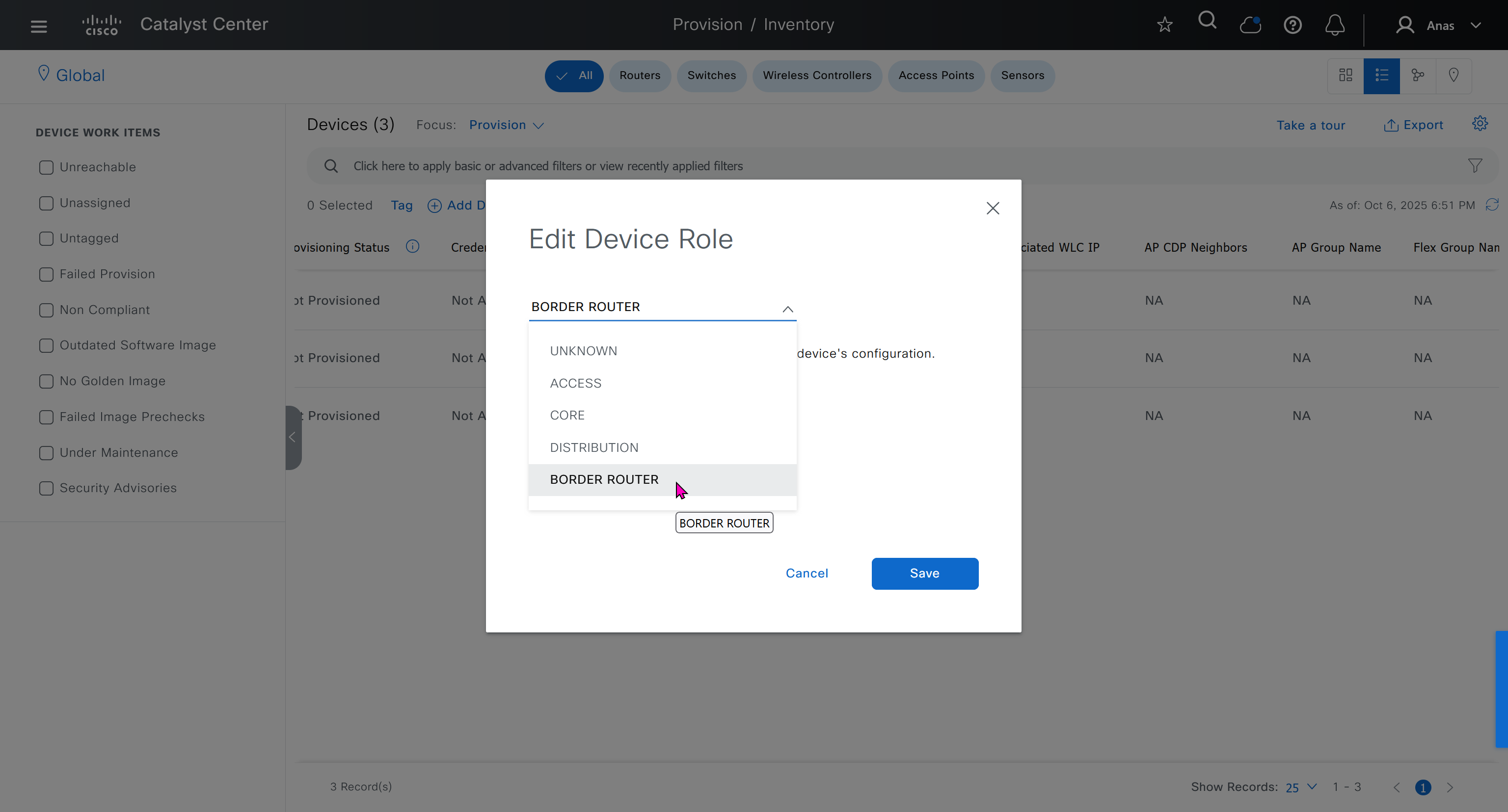
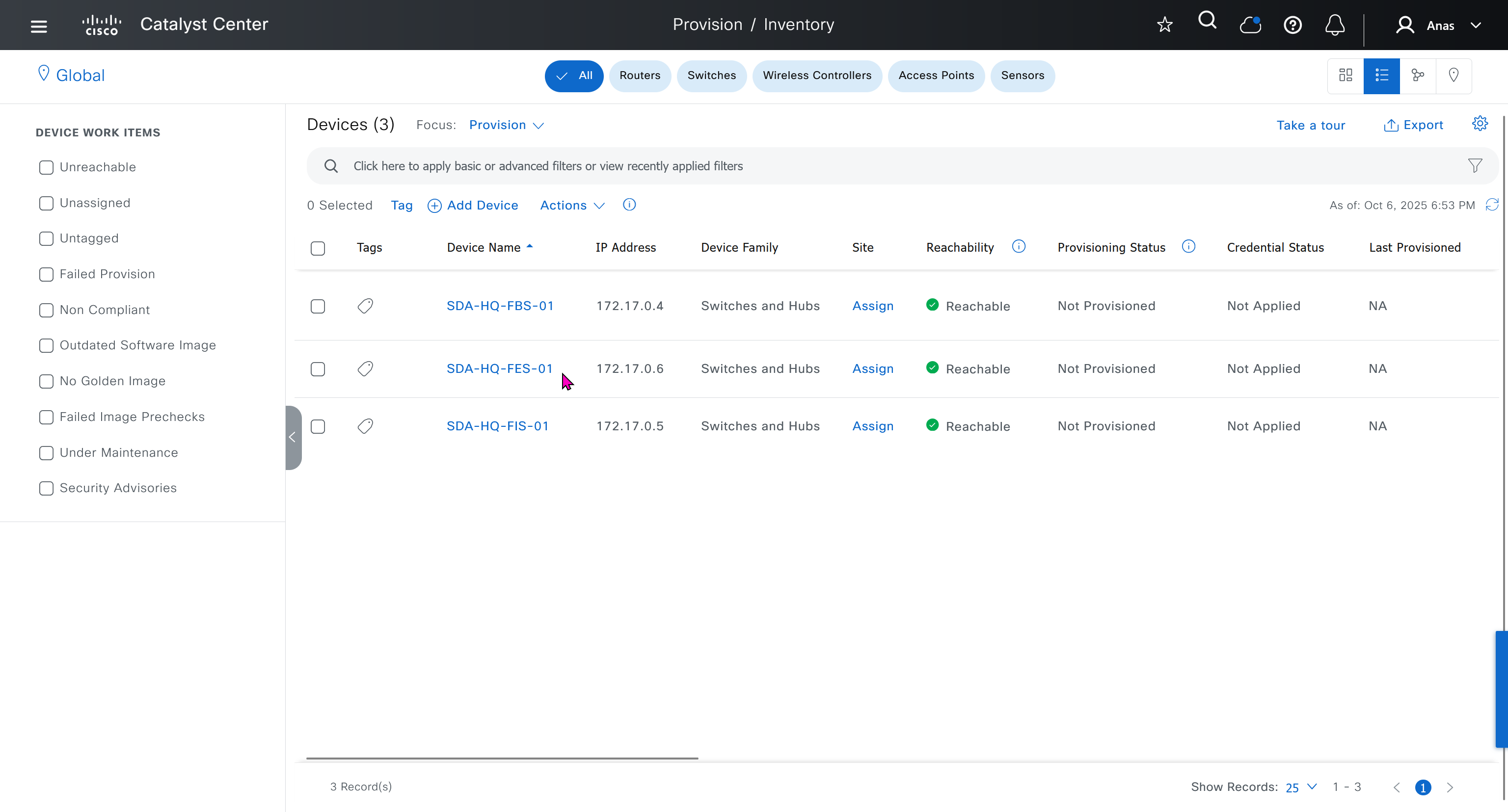

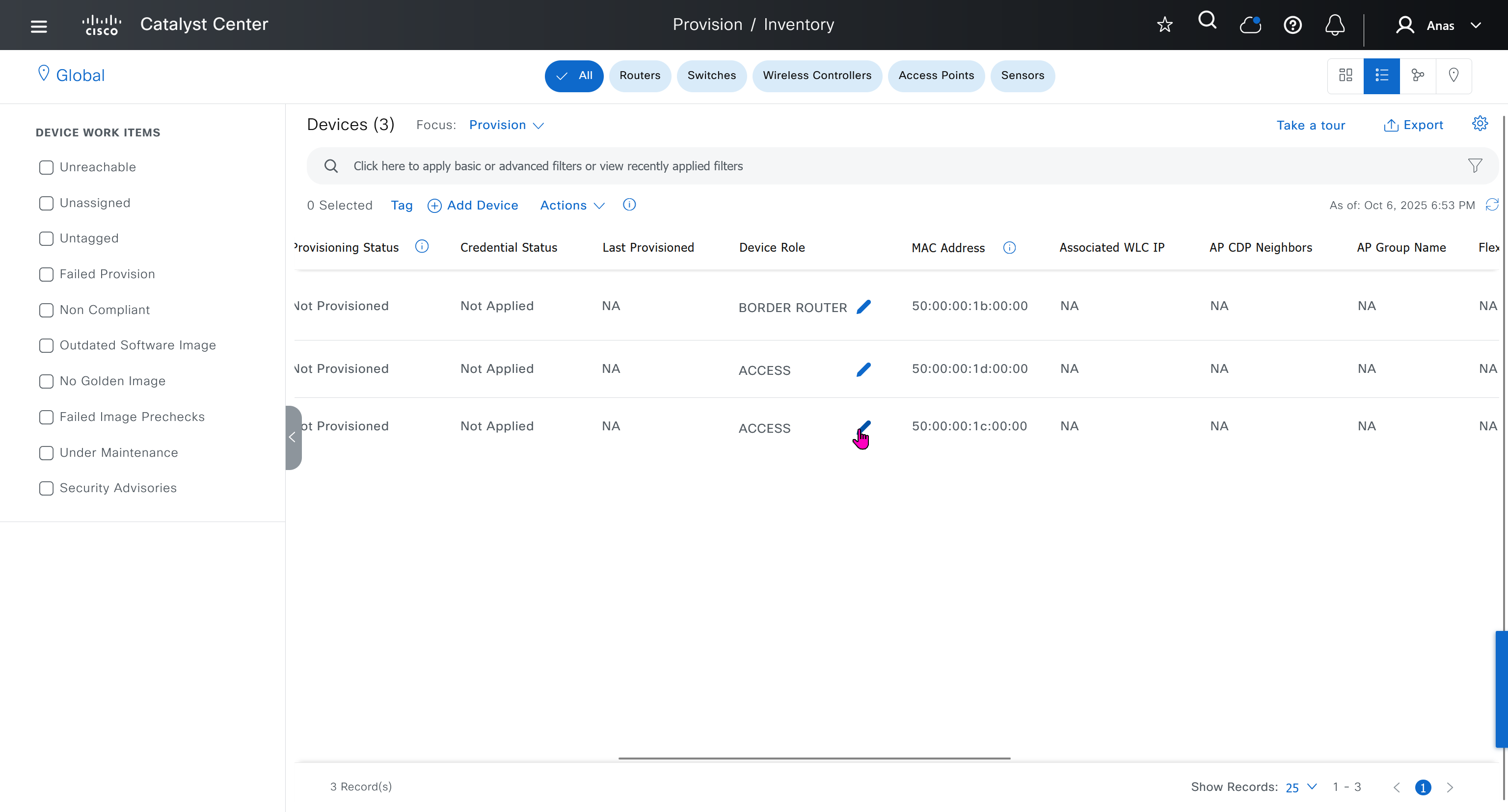

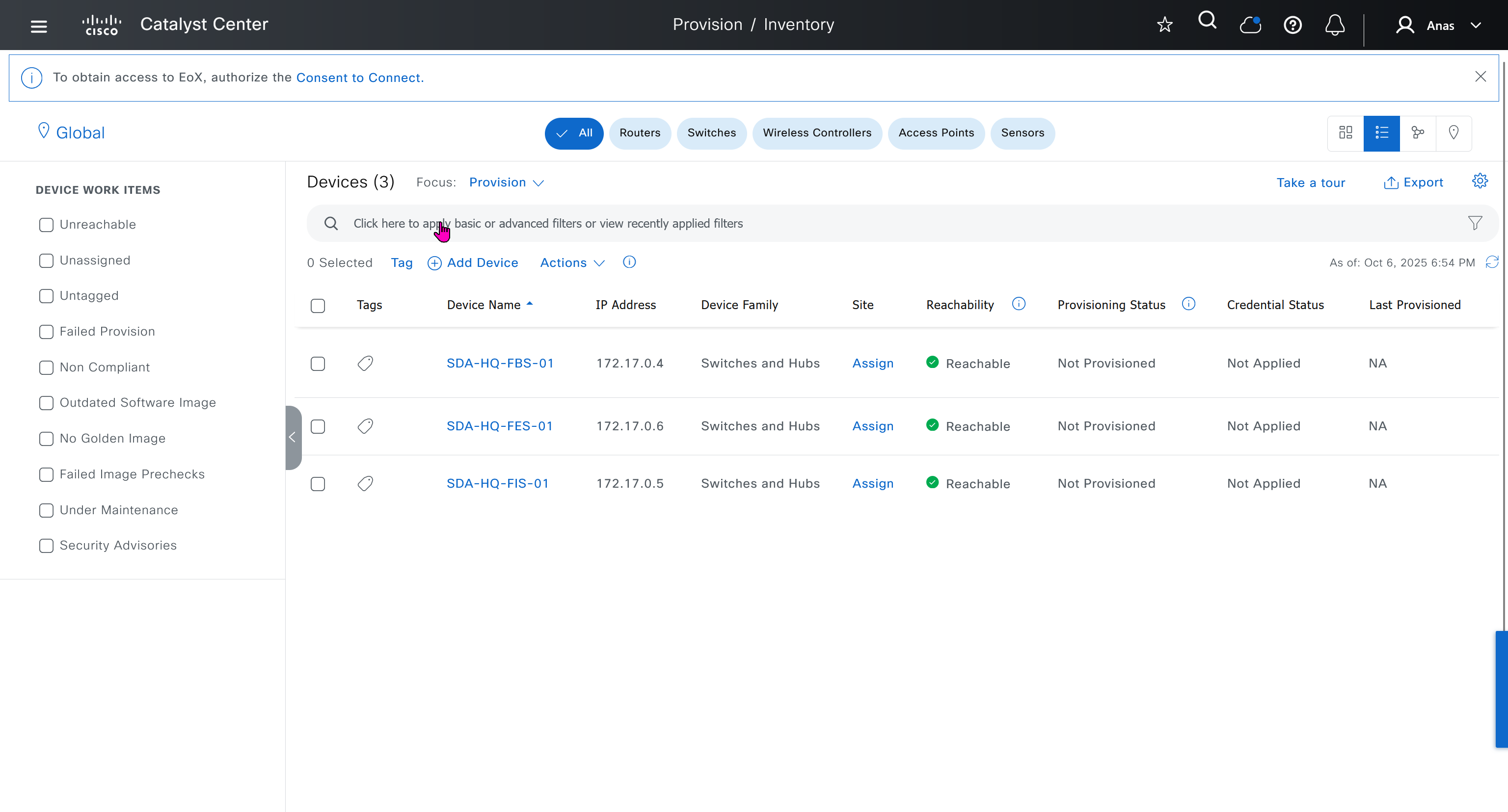
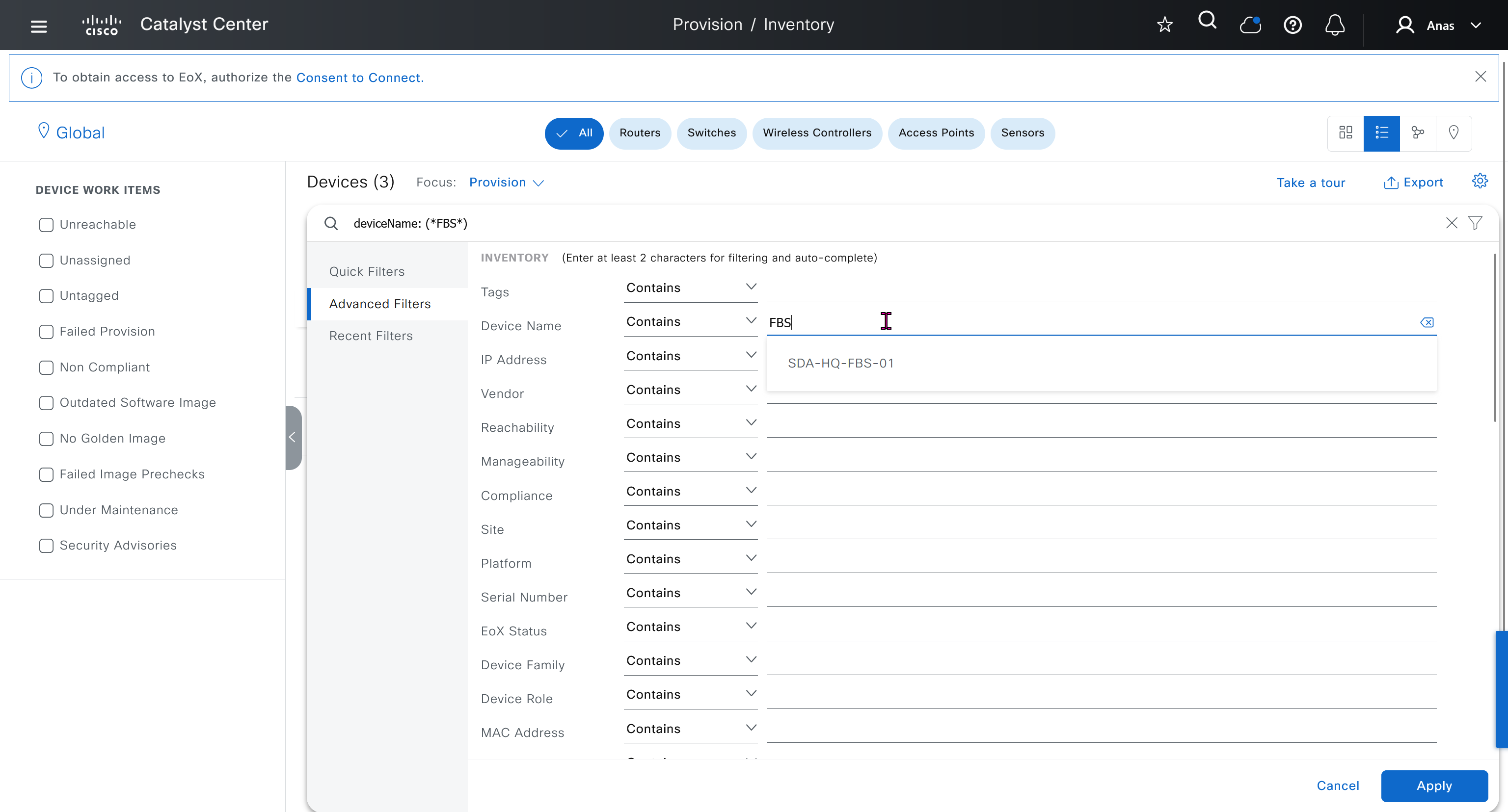
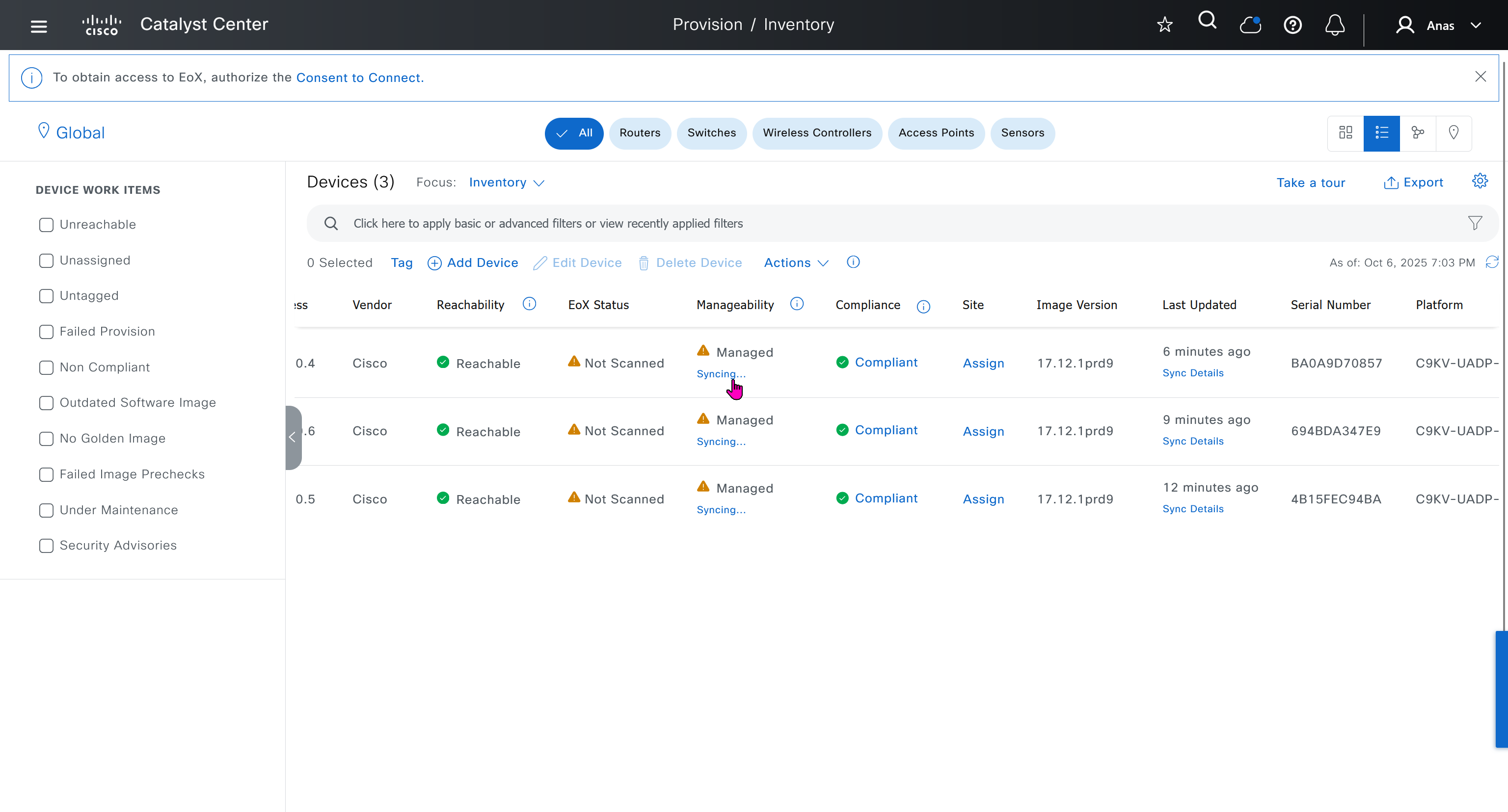
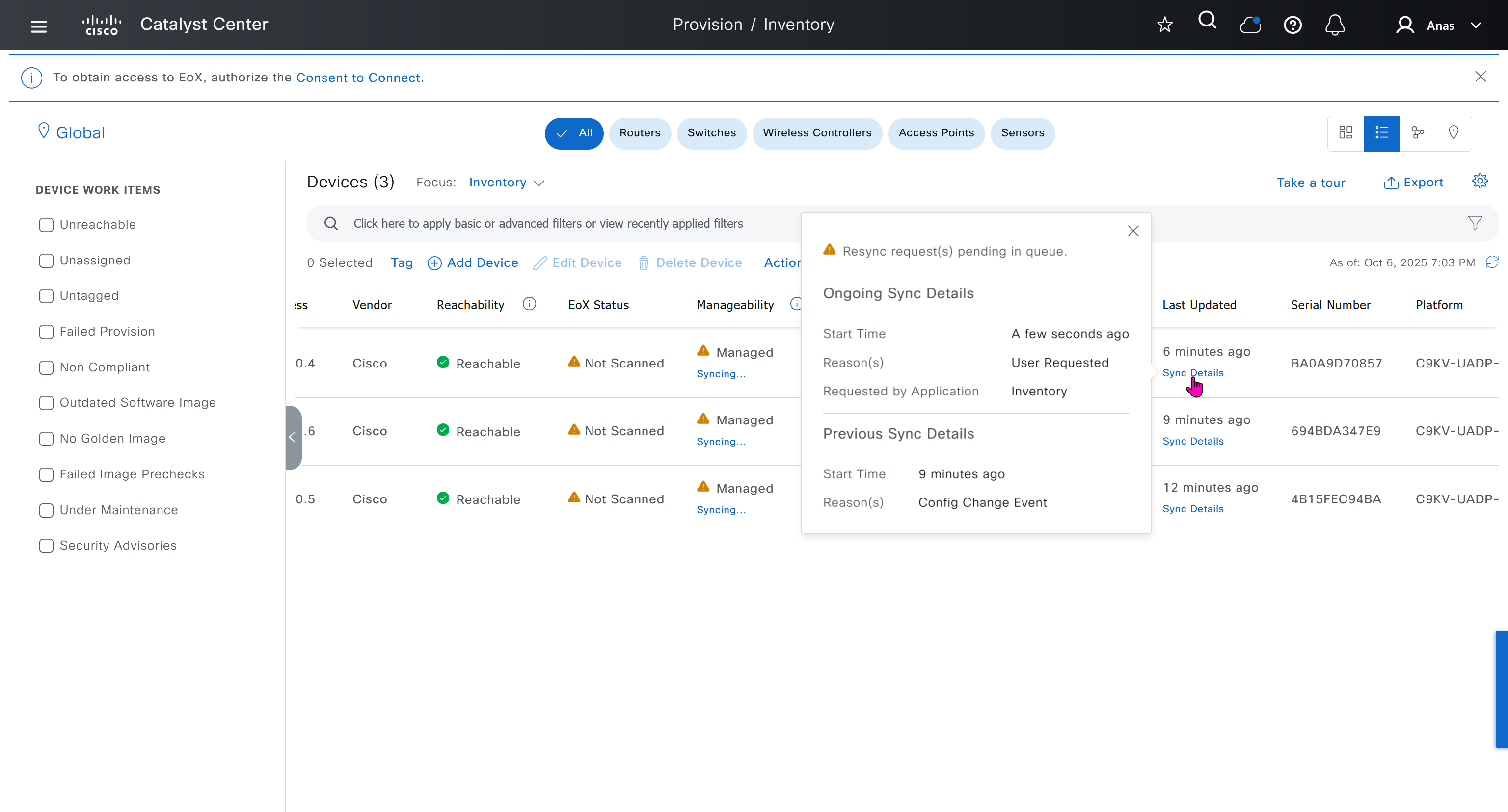
next post
QoS
QoS
Why QoS?
Even in the presence of 10G links or 100G links we still need QoS since we could have 100Mbps internet link

Some oversubscribed topologies have a need for QoS (just in case all servers start transmitting at the same time)
QoS only works when there is congestion at times of the day, if your network is congested all the time then you need to increase more bandwidth
2 types of QoS models
Best Effort – FIFO queuing , first packet that comes into the router is the first packet that will exit the [queue + interface] without any preferential treatment in a straight line
DiffServ – means “differentiated” “services” which means different treatment for different services
QoS Tools
Classification and Marking (tagging at IPv4 level)
Congestion Avoidance via Policing / Dropping (it is best to “avoid” first by cutting)
Congestion Management via Queueing | Scheduling | Shaping (delaying only as cutting / policing has been done earlier) – at this stage you can only manage as avoidance was earlier (tried to avoid but can only manage now)
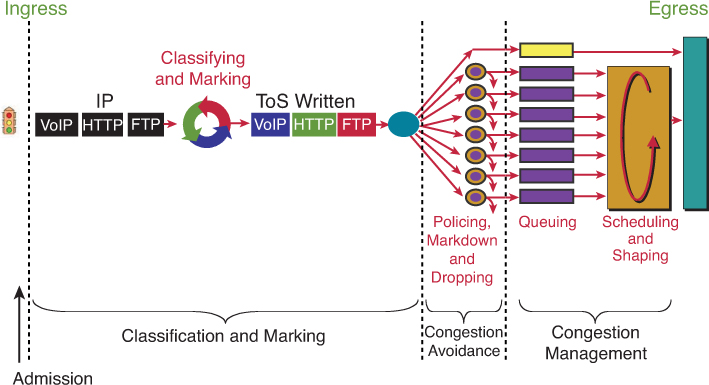
CMPQS – Classification , Marking , Policing , Queueing , Shaping

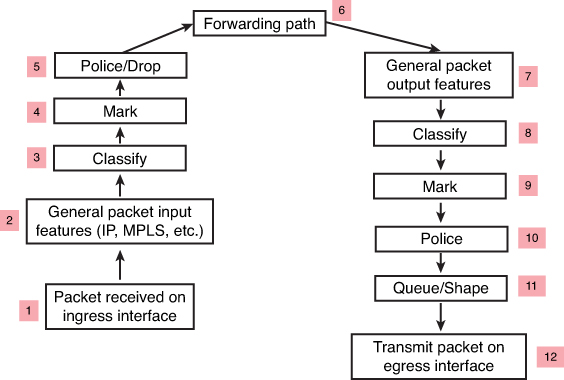
CMP — <ROUTER> — CMPQS
Classification may happen on ingress (3) and egress (8) in the packet path
but classification should be done as close to the source on ingress
but sometimes the attributes for classification are not known until the exit interface has been chosen. This is true for locally generated packets and even some transit packets,
If exit interface has service policy applied and that interface is chosen based on destination IP and routing table, Classify on Egress (8) is for those scenarios
Similarly, a packet may be marked on ingress (4), but perhaps requires to be re-marked on egress (9). For example, a policer may re-mark a nonconforming packet on egress rather than drop it—the fact that the packet is nonconforming is not known until the packet reaches the egress interface (where non conformance is determined by filling up queues and congestion) that has service policy applied and that interface is chosen based on destination IP and routing table, Mark on Egress (9) is for those scenarios
Classification and Marking
We want to save on processing for all nodes in the network and classify only once and best way to do is for edge nodes to classify once but tag or mark for it to be used forever through the network
All other tools in the list also use marked packets such as queueing , congestion avoidance and policing / shaping etc
IPv4 packet carries an 8-bit Type of Service (ToS) byte
IPv6 header carries an 8-bit Traffic Class field
first 3 bits in both IPv4 and IPv6 are for IP Presedence
DSCP first 6 bits offer a maximum of 64 possible classes of service
There is also layer 2 marking called Ethernet 802.1p CoS bits
General marking guidance
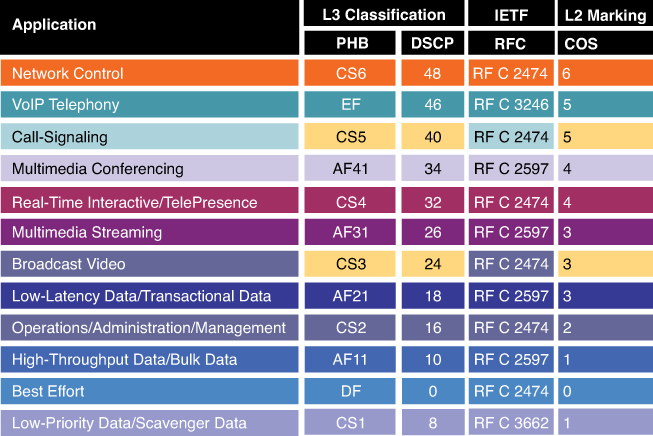
but in reality only 8 classes traffic model is implemented instead of 12 shown above

Marking can be new marking or even remarking such as marking down the class of non conforming or violating traffic
Class-based marking occurs after classification of the packet (in other words, set happens after the match criteria). Therefore, if used on an output policy, the packet marking applied can be used by the next-hop node to classify the packet but cannot be used on this node for classification purposes. However, if class-based marking is used on an ingress interface (blindly without going through match purely based on interface the traffic is coming from) as an input policy, the marking applied to the packet can be used on the same device on its egress interface for classification purposes.
On output policies both classification and marking can happen before or after tunnel encapsulation, depending on where the service policy is attached. Therefore, if a policy is attached to a GRE or IPsec tunnel interface, the marking is applied to the original inner packet header. However, if the policy is attached to the physical interface, only the tunnel header (the outer header) is marked, and the inner packet header is left unchanged.
CoS is usually used at Ethernet Layer 2 frames, contains 3 bits and can only be done at trunk, it makes sense to have it only on trunk since trunk is the only place where multiple VLANs traffic aggregate and compete from one another
CS is a term used to indicate a 3-bit subset of DSCP values; it designates the same 3 bits of the field as IP Precedence, but the interpretation of the field values maps to the per-hop behaviors as per the RFCs defining 6-bit DSCPs.
DSCP is a set of values, based on a 6-bit width
TID is a term used to indicate a 3-bit field in the QoS Control field of the 802.11 WiFi MAC frame. The 8 values of this field correspond to eight user priorities (UPs). TID is typically used for wireless Ethernet connections, and CoS is used for wired Ethernet connections
Trust Boundary
A trust boundary is a network location where packet markings are not accepted and are rewritten
In an enterprise campus network, the trust boundary is almost always at the edge switch
For example, a user computer set up to mark all traffic at DSCP EF will be ignored by the access switch at the trust boundary, and the traffic is inspected and re-marked according to enterprise QoS policies implemented on the switch.
Video traffic comes in a wide array of different traffic types belonging to applications that may be extremely high priority and delay sensitive (such as immersive Cisco TelePresence traffic) to unwanted Scavenger class traffic (nonorganization entertainment videos, such as YouTube) that in many cases may be dropped outright.
IEEE 802.11 specification, which provides a means for wireless devices to request traffic in different access categories with different markings (which are usually on the untrusted side of the network trust boundary and so raises the question of whether the trust boundary for wireless devices could, or should, be extended to the wireless device under certain circumstances).
L2 Frame
Ethernet frames can be marked with their relative importance at Layer 2 by setting the 802.1p user priority bits (CoS) of the 802.1Q
Wireless Ethernet frames can be marked at Layer 2 by setting the 802.11 WiFi Traffic Identifier (TID) field with in the QoS Control field
GRE , IPSec

The marking field from the inner header might or might not be copied automatically to the outer header. If not, explicit CLI must be used to mark the outer header. Methods to achieve this include the qos pre-classify CLI on the tunnel interface
l2tp tos reflect CLI can also be used on L2TP tunnels. L2TPv3 is widely used to transport L2 frames over IP networks.
MPLS
4-bit CoS field – 3 bits MPLS EXP (Experimental) bits and 1 bit Bottom of Stack Indicator
In MPLS tunneling scenarios, there can be multiple MPLS headers on a packet. The set mpls experimental imposition command sets a value on all labels on the packet, and the set mpls experimental topmost command sets a specific value only on the outermost label.
DSCP PHBs: Best-Effort (BE or DSCP 0), Assured Forwarding (AFxy), Expedited Forwarding (EF) and Class-Selector (CSx) code points
Class-Selector (CSx) code points have been defined to be backward compatible with IP precedence. (In other words, CS1 through CS7 are identical to IP precedence values 1 through 7

The first digit denotes the “AF class” and can range from 1 through 4. The second digit refers to the level of drop preference within each AF class and can range from 1 (lowest drop preference) to 3 (highest drop preference).
For example, during periods of congestion (on an RFC 2597-compliant node), AF33 would statistically be dropped more often than AF32, which, in turn, would be dropped more often than AF31
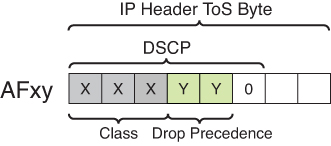
NBAR
NBAR is a L4–L7 deep-packet inspection classifier triggered by the match protocol in class-map
It is a more CPU-intensive than classifiers that match traffic by markings (DSCPs), addresses, or ACLs.
identifying application layer protocols by matching them against a Protocol Description Language Module (PDLM)
PDLM definitions are modular, and new ones can be added to a system without requiring a Cisco IOS upgrade.
Two modes of operation that NBAR offers:
Passive mode: Discovers and provides real-time statistics on applications per interface or protocol and gives bidirectional statistics such as bit rate (bps), packet, and byte counts
Active mode: Classifies applications for the purpose of marking the traffic so that QoS policies can be applied.
Router# show run
interface fastethernet 0/0
ip nbar protocol-discovery
! NBAR used as a classifier
Router# show run
class-map match-any MY-VIDEO
match protocol cuseeme
match protocol h323
match protocol rtp video
-----------------------------------------------------
class-map match-any ERP
match protocol sqlnet
match protocol ftp
match protocol telnet
class-map match-any AUDIO-VIDEO
match protocol http mime "*/audio/*"
match protocol http mime "*/video/*"
class-map match-any WEB-IMAGES
match protocol http url "*.gif"
match protocol http url "*.jpg|*.jpeg"
-----------------------------------------------------
match protocol h323 ! identifies all H.323 voice traffic
match protocol rtp [audio | video | payload-type payload-string]Sequence of classes within a policy map
Sequence of classes within a policy map is significant
packet is examined against each subsequent class within a policy map until a match is found. When found, the examination process terminates, and no further classes are checked. If no matches are found, the packet ends up in the default class (because policy map is applied on the interface and every policy map has class class-default section)
class-map match-all FAX-RELAY
match dscp ef
class-map match-all VOICE
match protocol rtp audio
!
policy-map VOICE-AND-FAX
class FAX-RELAY
priority 64
police cir 64000
class VOICE
priority 216
police cir 216000No traffic would ever show against the VOICE class because both voice and fax-relay traffic would match on DSCP EF and would therefore be assigned to the FAX-RELAY class, to fix it we will need to reverse the order of classes inside policy map
service-policy command also specifies whether the policies should be applied to ingress or egress traffic on this interface using keywords input and output.
policy-map POLICY-1
...
bandwidth 20000
policy-map POLICY-2
...
bandwidth 64000
!
interface Ethernet 1/0
service-policy input POLICY-1
!
interface Ethernet 1/1
service-policy output POLICY-2Subinterfaces

the two subinterfaces are collectively allowing 22K of traffic, which in turn is shaped to 20K throughput, on the main interface to maintain an aggregate throughput not to exceed 20K and shave off the extra 2Kbps.
! Definitions for sub-interface GE1.1
policy-map CHILD1
class VOICE1
priority 3000
class VIDEO1
bandwidth 5000
policy-map PARENT1
class class-default
shape average 15000
service-policy CHILD1
!
! Definitions for sub-interface GE1.2
policy-map CHILD2
class VOICE2
priority 1500
class VIDEO2
bandwidth 2500
policy-map PARENT2
class class-default
shape average 7000
service-policy CHILD2
!
! Definitions for the main interface
policy-map AGGREGATE
class class-default
shape average 20000
!
interface ge 1/1.1
service-policy output PARENT1
interface ge 1/1.2
service-policy output PARENT2
interface ge 1/1
service-policy output AGGREGATEPARENT1 policy:
Shapes all traffic on GE1.1 to an average of 15 Mbps.
Within that shaped pipe, it applies the CHILD1 policy, enforcing priority for voice and bandwidth for video.
AGGREGATE policy:
Shapes the whole physical interface GE1/1 to 20 Mbps total.
This ensures the combined traffic from both sub-interfaces (GE1.1 + GE1.2) cannot exceed 20 Mbps.
GE1/1.1 → applies PARENT1 (→ CHILD1) = 15 Mbps max.
GE1/1.2 → applies PARENT2 (→ CHILD2) = 7 Mbps max.
GE1/1 → applies AGGREGATE = 20 Mbps total for both.
all traffic at the interface level being shaped overall to 20K (policy-map AGGREGATE), while voice traffic within that rate is guaranteed to get a minimum of 3K or 1.5K of bandwidth
Marking conversion with table map
You can build a conversion table with the table-map CLI and then reference the table in a set command to do the translation
Any values not explicitly defined in a “to-from” relationship are set to the default value
If the default value is omitted from the table, the content of the packet header is left unchanged.
In this example, the DSCP value will be set according to the CoS value defined in the table
table-map MAP1
map from 0 to 0
map from 2 to 1
default 3
!
policy-map POLICY1
class traffic1
set dscp cos table MAP1Congestion Avoidance
Congestion avoidance aims to control traffic before it enters the queueing phase. Congestion should be avoided at all cost because it can cause TCP global sync for all TCP connection flows simultaneously
dropping and marking the packet, are applied before the packet enters a queue for egress scheduling
“bandwidth,” “police,” and “shape”
Bandwidth
The bandwidth command is used to assign “minimum bandwidth” to a traffic class during congestion times. Just like a rubber “band” can be stretched and then it comes back to its original size, This is how a class can use positively more bandwidth or minimum of defined bandwidth (under congestion)
It is often used in conjunction with the Low Latency Queueing (LLQ) or Class-Based Weighted Fair Queueing (CBWFQ) to assign different classes different bandwidths. Assigning predictable bandwidth or chunks of interface speed to classes is much better way to handle the times of congestion
bandwidth {value in kbps}bandwidth 2000 (This allocates 2000 kbps to the class.)Police
The police command is used to force traffic to a rate limit regardless of congestion or not. Police command and shape command are applied all the time regardless if congestion is happening or not
Traffic of class where policing is applied can use less or equal to rate specified in police command
It is used to control the “max” speed a traffic can use often used to hard rate limit certain class.
Remember this from Police on highway, they make public drivers conform to max speeds defined, if a driver exceeds that speed, police stops or gives ticket to that person
Policing drops or marks packets that exceed the specified rate, traffic exceeding the specified rate is either dropped or remarked for lower marking
police {rate in bps} [burst-normal in bytes] [burst-max in bytes] [conform-action transmit] [exceed-action drop] [violate-action {drop | remark}]
police 1000000 20000 20000 conform-action transmit exceed-action drop
(This limits the traffic to 1 Mbps, with a normal burst of 20,000 bytes and a maximum burst of 20,000 bytes. Conforming packets are transmitted, while exceeding packets are dropped.)
Shape
The shape command (traffic shaping) is used to buffer and smooth out bursts of traffic to a specified rate regardless of the congestion or not. Like police command, it also has a reducing function, It is used to ensure that traffic rate is controlled, and used in scenarios where you want to rate limit traffic to a rate but also not drop any traffic instead delay it.
Shaping delays excess packets by storing them in a queue , buffer and releasing them at a controlled rate. This helps in smoothing traffic flows and prevents sudden bursts that could overwhelm network devices.
shape average {rate in bps} [burst-size in bytes] [excess-burst-size in bytes]
Example: shape average 1000000 20000 20000
(This shapes the traffic to an average rate of 1 Mbps, with a burst size of 20,000 bytes and an excess burst size of 20,000 bytes.)
Key Differences:
Bandwidth vs. Police:
bandwidth reserves a minimum guaranteed bandwidth, ensuring that a class gets its share of the link capacity even under congestion.
police enforces a maximum rate, dropping or marking packets that exceed this rate.
Police vs Shape:
police drops or marks packets that exceed the specified rate, providing a hard limit.shape smooths out bursts of traffic instead of dropping packets, sending traffic at a controlled rate.

Policers are also often deployed at egress to control bandwidth used (or allocated) to a particular class of traffic, because such a decision often cannot be made until the packets reach the egress interface.
Shapers are commonly used on enterprise-to-service-provider links (on the enterprise egress side) to ensure that traffic destined for the service provider (SP) does not exceeds a contracted rate
Policer and Tail drop
When traffic exceeds the policed pipe, it does not expand the pipe but instead excess traffic / rate stays at the tail of the pipe and that is why it is called tail drop
A policer does tail drop, which describes an action that drops every packet that exceeds the given rate, until the traffic drops below the rate
Tail drop can have adverse effects on TCP retransmission methods and cause TCP global sync. Another mechanism of dropping packets is random dropping, which proactively drop packets before the queue is full to signal TCP flows to slow down inside the queue, known as random early detection (RED) and weighted RED (WRED). These methods work more effectively with TCP retransmission logic, but they are not policing/shaping tools. RED and WRED which are part of queue management / congestion avoidance (sometimes described as “intelligent dropping” inside the queue)
Instead of waiting for the queue to fill up and then tail-drop, RED/WRED randomly drop packets early, which prevents global synchronization and keeps throughput smoother.
Policing and RED/WRED can be applied on same service policy on interface but they work at different stages of packet handling, so you need to be clear how they interact.

Policing action will be taken as shown in above diagram since Congestion Avoidance takes place first and that controls the rate but for some reason if queue starts to fill up due to any other reason (since back pressure is on due to constant rate coming through policer) then WRED will activate
police command for tail drop and random-detect for WRED
They don’t “conflict,” but the policer acts first. If the policer already drops excess traffic, less traffic even reaches the queue, so WRED might do little and in production networks only should be implemented, unless there are complaints about TCP Global Sync, then honestly pipe should be increased rather than implementation of WRED
More common combo = shaping + WRED (because shaping delays bursts, then WRED handles congestion gracefully inside the queue).
policer when drops packets, it does “tail drop” on queues, it sounds like a queueing function (congestion management) but it is not, it is part of policer and it is general drop of traffic that simply exceeds the rate or pipe
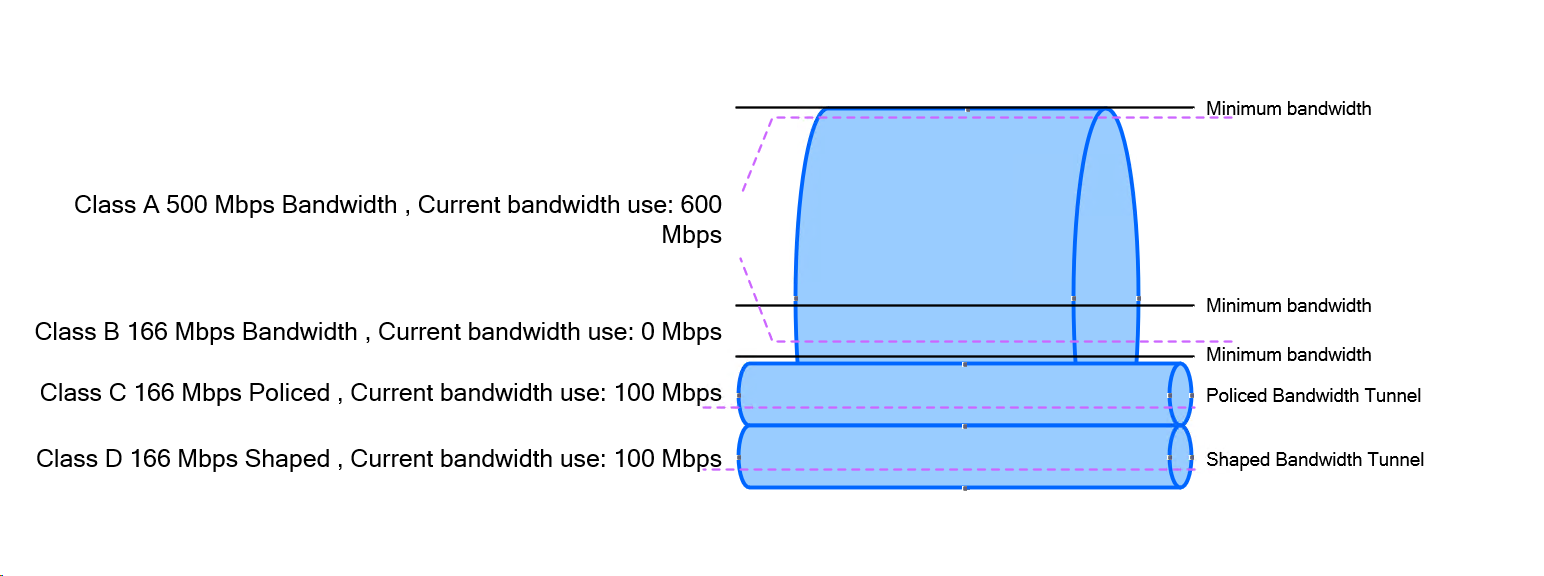
When a traffic rate is exceeded, a policer can take one of two actions:
- Drop the traffic
- Re-mark
Section: Random Detect example with remark , mark down
re-marking (or markdown) should be done according to standards-based defined in Per Hop Behavior PHB – Assured Forwarding (AF) for example: excess traffic arriving as AFx1 should be marked down to AFx2 (or AFx3, whenever dual-rate policing is supported)
Then when traffic reaches the queue (congestion management), queue should be configured with (DSCP)-based WRED, WRED policy should be to drop AFx3 (statistically) more aggressively than AFx2, which in turn should be dropped (statistically) more aggressively than AFx1.
! ---- Classify AF queues (typical) ----
class-map match-any AF1
match dscp af11 af12 af13
class-map match-any AF2
match dscp af21 af22 af23
class-map match-any AF3
match dscp af31 af32 af33
class-map match-any AF4
match dscp af41 af42 af43
! ---- Policy with WRED tuned by drop precedence ----
policy-map WAN-OUT
class AF1
bandwidth percent 10
random-detect dscp-based
! AF13 (x3) most aggressive
random-detect dscp af13 20 40 5
! AF12 (x2) medium aggressive
random-detect dscp af12 30 55 7
! AF11 (x1) least aggressive
random-detect dscp af11 40 70 10
class AF2
bandwidth percent 10
random-detect dscp-based
random-detect dscp af23 20 40 5
random-detect dscp <DSCP-value> <min-threshold> <max-threshold> <mark-prob-denominator>
random-detect dscp af23
This tells the router to apply DSCP-based WRED to packets marked AF23.
Each DSCP value can have its own drop profile.
<min-threshold> → 20
This is the queue depth (in packets) at which WRED starts dropping probabilistically.
At queue length below 20 packets, no drops occur for AF23.
<max-threshold> → 40
This is the queue depth at which WRED reaches 100% drop probability for AF23.
At 40 packets or more, all AF23 packets are dropped.
<mark-prob-denominator> → 5
This controls the slope of the drop curve between min and max threshold (as seen in chart below).
Drop probability = 1 / denominator at max-threshold
Here: 1/5 = 20% max probability (at threshold just below 40).
So queue depth
at 20 → 0% drop chance,
at 30 → ~10% drop chance,
at 39 → ~20% drop chance,
at ≥40 → 100% drop.
AF23 (x3): min 20, max 40, denom 5 → starts dropping early, ramps quickly → Most aggressive (drops at shallow queue depth).
AF22 (x2): min 30, max 55, denom 7 → later start, gentler slope → Medium aggressive.
AF21 (x1): min 40, max 70, denom 10 → starts dropping late, gentlest slope → Least aggressive (protected).
random-detect dscp af22 30 55 7
random-detect dscp af21 40 70 10
class AF3
bandwidth percent 10
random-detect dscp-based
random-detect dscp af33 20 40 5
random-detect dscp af32 30 55 7
random-detect dscp af31 40 70 10
class AF4
bandwidth percent 10
random-detect dscp-based
random-detect dscp af43 20 40 5
random-detect dscp af42 30 55 7
random-detect dscp af41 40 70 10
class class-default
fair-queue
random-detect
! Apply to the egress interface
interface GigabitEthernet0/0
service-policy output WAN-OUT✅ So: AFx3 packets hit drop earliest and hardest, AFx2 later/softer, AFx1 latest and mildest.
This all happening in a single queue and this queue contains multiple packets with AF21 , AF22 and AF23 packets and as queue if filling up they are all getting dropped in progression but AF23 will start dropping early and hard before AF21 starts dropping
See how drop probability gets lower and lower (AF21 at 10%) before 100% drop, as this is design intention to have AF21 suffer from only 10% of total packets drop before queue that has multiple packets made up of AF23 , AF22 and AF21 hits queue size of 70
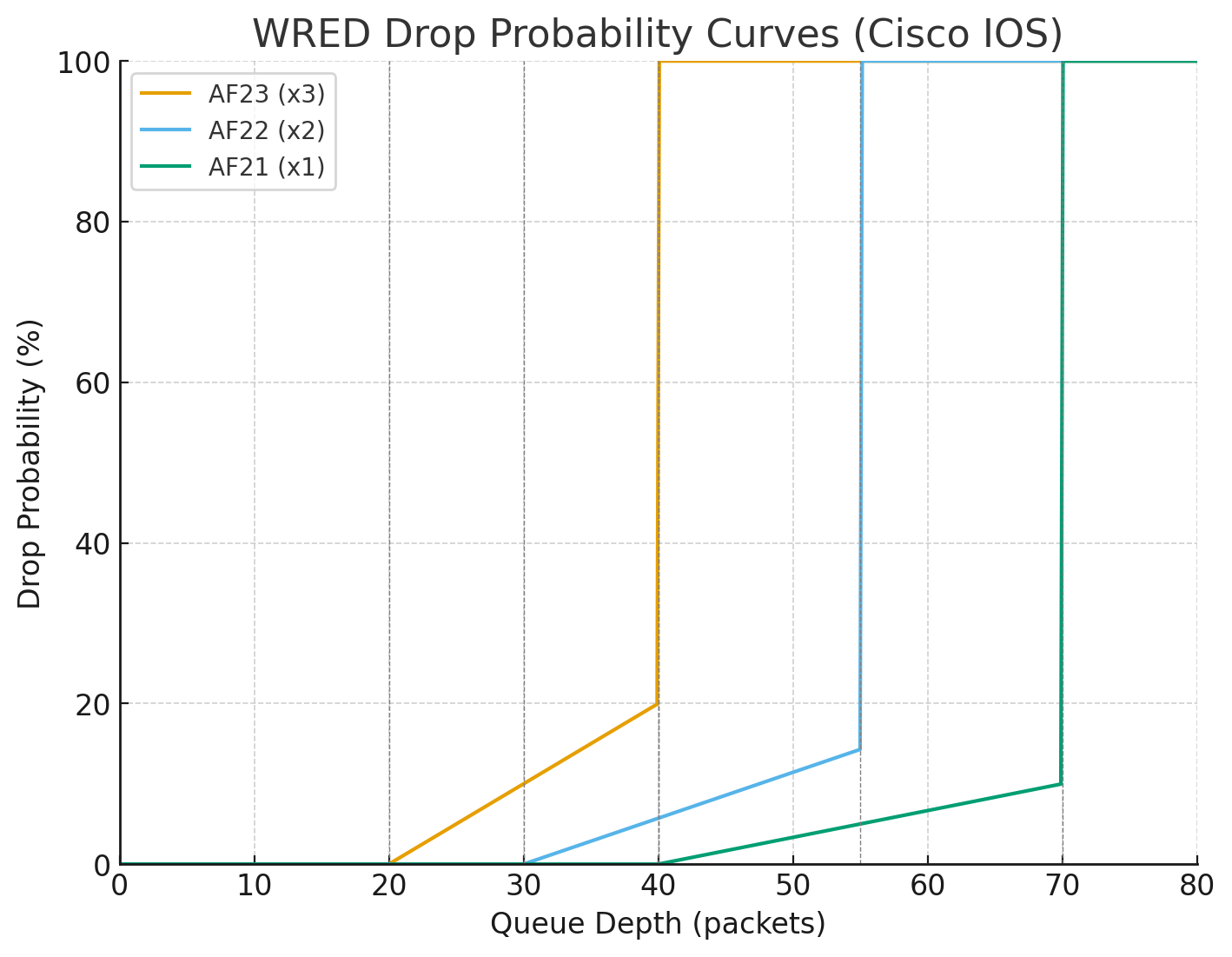
What if we want drop probability to be 80%?

1 / 80 = 0.0125
0.0125 * 100 = 1.25
If we enter 1.25 that will not be accepted by cisco command line and it only allows us whole numbers
If we want increase in drop probability we can use 2 which will give us sharp drop of 50%
Token Bucket Algorithms
Token bucket algorithms are metering engines that keep track of how much traffic can be sent
One token permits a single unit (usually a bit, but can be a byte) of traffic to be sent
New Tokens equal to “CIR” are granted usually every second
For example, if the CIR is set to 8000 bps, 8000 tokens are placed in a bucket at the beginning of the time period. Each time a 1 bit of traffic passes “policer”, the bucket is checked for tokens
-> If there are tokens in the bucket, the traffic is viewed as conforming to the rate and the typical action is to send the traffic.
-> One token is removed from the bucket for each bit of traffic passed.
-> If there are no tokens, any additional offered traffic is viewed to exceed the rate, and the exceed action is taken, which is typically either to re-mark or drop the traffic.
At the end of the second, there might be unused tokens. The handling of unused tokens is a key differentiator among policers
Rate limit using TDM
With TDM, when a rate limit (or CIR) is imposed on an interface, the traffic bits are pinned to subsecond milliseconds – 1 thousandth of a second units
This multiple subsecond time slices are combined into larger interval called “Tc”
For example, if an 8-Kbps CIR is imposed on a 64-Kbps link, traffic can be sent for an interval of 125 ms (64,000 bps / 8000 bits). We just divided the total rate of the link with desired rate 64000 / 8000 = 8, and 8th of a second is 125 ms and that 125 ms will be our Tc value.
The entire amount allowed by the CIR (8000 bits) could theoretically be sent at once, but then the algorithm would have to wait 875 ms before it could send any more data
Therefore, to smooth out the allowed flow over each second, traffic is released on the link in smaller bursts called committed burst “Bc” which can be sent per Tc interval
Below illustration only shows scenarios for different Tc times and not Tc of 125 ms
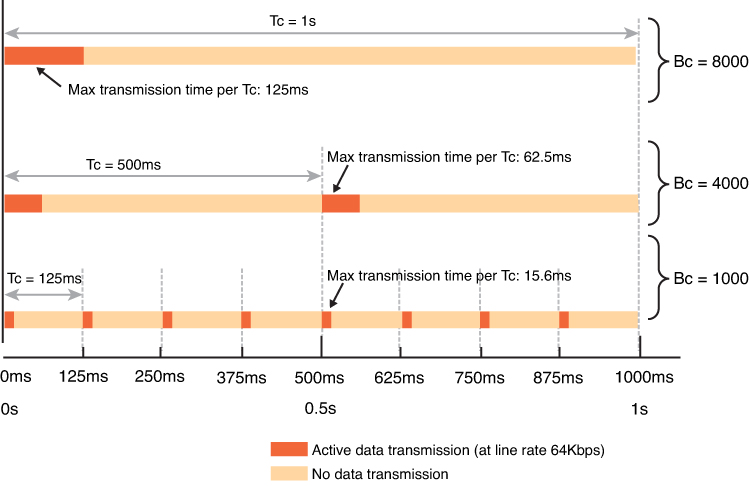
It is not necessary for device to keep sending during whole of Tc, instead device can send for some duration of Tc but send whole of Bc and wait for next Tc interval as shown in last example of Bc = 1000 in illustration above
token bucket algorithm is as follows: Bc = CIR * Tc (Bits = Rate * Time)
Cisco IOS Software does not allow the explicit definition of the interval (Tc). Instead, it takes the CIR and Bc values as arguments
From a practical perspective, when implementing networks, Tc should not exceed 125 ms. Shorter intervals can be configured and are necessary to limit jitter in real-time traffic, but longer intervals are not practical for most networks because the interpacket delay becomes too large
so we can drive down the value of Tc from 125 ms to 62.5 ms (half) using below
Bc = CIR * Tc (Bits = Rate * Time) using this formula we can figure out or set the Tc
for Tc of 125 ms
CIR or total rate 64000 bits/sec * Tc 125 ms = 8000000
8000000 / 1000 ms or 1 sec for result in seconds = 8000 -> Bc
( 64000 * 125 ) / 1000 = 8000 -> Bc
for Tc of 62.5 ms
( 64000 * 62.5 ) / 1000 = 4000 -> Bc
Types of Policers
There are different variations of policing algorithms, including the following:
Single-rate two-color
Single-rate three-color
Dual-rate three-color
Single-Rate Two-Color Policers
The original policers implemented use a single-rate, two-color model with
A single rate and single token bucket algorithm
Traffic identified as one of two states (or colors): conforming to or exceeding the CIR. Marking or dropping actions are performed on each of the two states of traffic
Single-Rate Three-Color Policers
An improvement on single-rate two-color policer algorithm
Traffic identified as one of three states (or colors): conforming to, exceeding or “violating” the CIR.
First part operates just like the single-rate two-color system But if there are any tokens left over in the bucket after each time period, these are placed in the second bucket to be used as credits later for temporary bursts that might exceed the CIR
Tokens placed in this second bucket are called the excess burst (Be). Be is the maximum number of bits that can exceed the Bc burst size.
With this two token-bucket mechanism, traffic can be identified in three states (or three colors) as follows:
Conform: Traffic within the CIR—usually sent (optionally re-marked)
Exceed: Traffic within the excess burst allowance above CIR—can be dropped, or re-marked and sent
Violate: Traffic beyond the excess burst—usually dropped (optionally re-marked and transmitted)
CIR: Committed information rate, the policed rate
CBS: Committed burst size, the maximum size of the first token bucket
EBS: Excess burst size, the maximum size of the second token bucket
Tc: Token count of CBS, the number of tokens in the CBS bucket (Do not confuse the term Tc here with the earlier use of Tc in the context of time but this Tc is only used for diagram below)
Te: Token count of EBS, the instantaneous number of tokens left in the EBS bucket
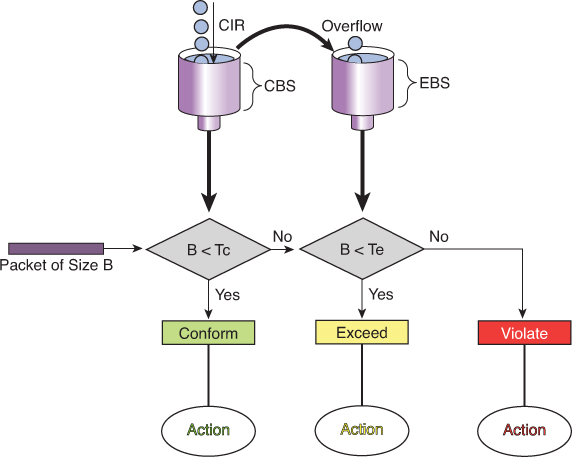
Single-rate three-color policer’s tolerance of temporary bursts results in fewer TCP retransmissions and is therefore more efficient for bandwidth utilization. It is a highly suitable tool for marking according to RFC 2597 AF classes, which have three “colors” (or drop preferences) defined per class (AFx1, AFx2, and AFx3). Using a three-color policer generally makes sense only if the actions taken for each color differ. If the actions for two or more colors are the same, a simpler policer (and therefore a simpler QoS policy) is more suitable to implement, making the network easier to maintain.
! -----------------------------
! Classify traffic (examples)
! -----------------------------
ip access-list extended AF1-TRAFFIC
remark <<< define your AF1 class traffic here >>>
permit ip 10.1.0.0 0.0.255.255 any
ip access-list extended AF2-TRAFFIC
remark <<< define your AF2 class traffic here >>>
permit ip 10.2.0.0 0.0.255.255 any
ip access-list extended AF3-TRAFFIC
remark <<< define your AF3 class traffic here >>>
permit ip 10.3.0.0 0.0.255.255 any
class-map match-any CLASS-AF1
match access-group name AF1-TRAFFIC
class-map match-any CLASS-AF2
match access-group name AF2-TRAFFIC
class-map match-any CLASS-AF3
match access-group name AF3-TRAFFIC
! ---------------------------------------------------------
! Single-rate three-color policer per AF class
! - Adjust CIR/Bc/Be to your needs (bps / bytes).
! - Typical starting point: Be ≈ 2*Bc
! ---------------------------------------------------------
policy-map POLICE-AF
class CLASS-AF1
! Example: 10 Mbps CIR, Bc/Be placeholders
police cir 10000000 bc 312500 be 625000 \
conform-action set-dscp-transmit af11 \
exceed-action set-dscp-transmit af12 \
violate-action drop
class CLASS-AF2
! Example: 5 Mbps CIR
police cir 5000000 bc 156250 be 312500 \
conform-action set-dscp-transmit af21 \
exceed-action set-dscp-transmit af22 \
violate-action drop
class CLASS-AF3
! Example: 2 Mbps CIR
police cir 2000000 bc 62500 be 125000 \
conform-action set-dscp-transmit af31 \
exceed-action set-dscp-transmit af32 \
violate-action drop
class class-default
set dscp default
! ---------------------------------------
! Apply the policy (ingress or egress)
! ---------------------------------------
interface GigabitEthernet0/0
description WAN-Uplink
service-policy output POLICE-AF
police cir 10000000 bc 312500 be 625000 -> in order to find its Tc
This Bc of 312500 is not optimal as it results in 250 ms
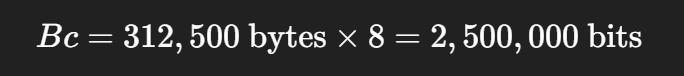
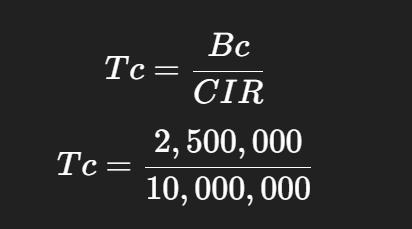

Bc = CIR * Tc
10000000 bits * 125 ms = 1250000000 / 1000 ms = 1250000 bits of Bc
for command line we will convert it to bytes 1250000 / 8 = 156,250 bytes
police cir 10000000 bc 156250 be 312500
Dual-Rate Three-Color Policers
The single-rate three-color marker/policer was a significant improvement for policers—it made allowance for temporary traffic bursts
the two-rate three-color marker/policer allows for a sustainable excess burst (negating the need to accumulate credits to accommodate temporary bursts) and allows for different actions for the traffic exceeding the different burst values.
This policer addresses the peak information rate (PIR), which is unpredictable in the RFC 2697 model two-rate three-color marker/policer. Furthermore, the two-rate three-color marker/policer allows for a sustainable excess burst (negating the need to accumulate credits to accommodate temporary bursts) and allows for different actions for the traffic exceeding the different burst values.
The dual-rate three-color marker/policer uses the following definitions parameters to meter the traffic stream:
PIR: Peak information rate, the maximum rate that traffic ever is allowed
PBS: Peak burst size, the maximum size of the first token bucket
CIR: Committed information rate, the policed rate
CBS: Committed burst size, the maximum size of the second token bucket
Tp: Token count of PBS, the instantaneous number of tokens left in the PBS bucket
Tc: Token count of CBS, the instantaneous number of tokens left in the CBS bucket
B: Byte size of offered packet
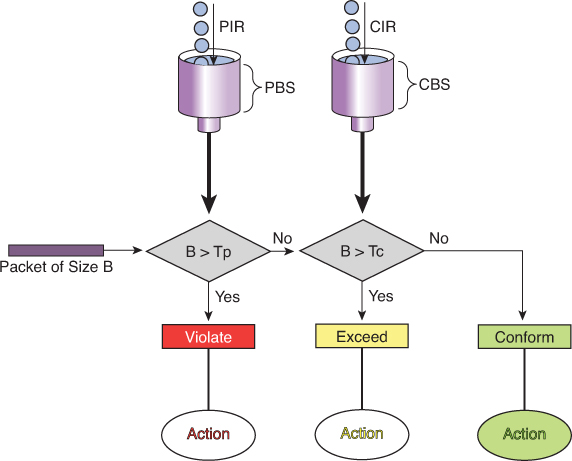
Policing Logic
- First check against PIR (Peak Bucket):
- If B > Tp (packet size larger than available tokens in PBS) → Violate (red).
- Packet is non-conformant and marked/dropped depending on policy.
- Otherwise, move to next step.
- If B > Tp (packet size larger than available tokens in PBS) → Violate (red).
- Then check against CIR (Committed Bucket):
- If B > Tc (packet size larger than tokens in CBS) → Exceed (yellow).
- Packet is considered “in excess traffic” but not outright violation.
- Otherwise → Conform (green).
- If B > Tc (packet size larger than tokens in CBS) → Exceed (yellow).
Actions
- Violate (Red): Drop or heavily penalize traffic.
- Exceed (Yellow): Forward, but mark as lower-priority (may be dropped if congestion occurs).
- Conform (Green): Forward as guaranteed/priority traffic.
! Class-map: match the traffic you want to police
class-map match-any APP-TRAFFIC
match access-group 101
! or DSCP/ACL/etc.
policy-map POLICE-TRTCM
class APP-TRAFFIC
police cir 1000000 bc 10000 pir 2000000 be 20000 \
conform-action transmit \
exceed-action set-dscp-transmit cs1 \
violate-action drop
!
! Apply inbound (or outbound if supported)
interface GigabitEthernet0/0/0
description Ingress toward core
service-policy input POLICE-TRTCMCoPP is a feature that allows the configuration of QoS policers to rate-limit the traffic destined to the main CPU of the switch/router. Such CoPP policers serve to protect the control plane of the switch/router from DoS attacks and reconnaissance activity in order to protect the CPU and control plane running as CPU processes
! Single-rate policer
policy-map POLICY1
class C1
police cir 1000000 conform-action transmit exceed-action drop
!
! Dual-rate policer
policy-map POLICY2
class C2
police cir 500000 bc 10000 pir 1000000 be 10000 conform-action
transmit exceed-action set-prec-transmit 2 violate-action drop
!
! Percentage-based policing
policy-map POLICY3
class C3
police cir percent 20 bc 300 ms be 400 ms pir percent 40
conform-action set-cos-inner-transmit 3Summary
Policing happens before packets enter the output queue.
A policer enforces a traffic contract (rate/committed burst).
Packets that exceed the configured rate are either dropped (default) or remarked (e.g. to a lower priority).
This happens regardless of whether there is congestion or not.
Congestion occurs after packets have entered the interface output queue.
Congestion management mechanisms (like Weighted Fair Queuing, Priority Queuing, CBWFQ, LLQ, etc.) decide which packets get queued and transmitted.
If a queue overflows (due to congestion), packets are dropped from that queue.
This can happen even for traffic that has already been policed — if the queue fills, traffic is dropped.
Hierarchical Policing
it might be desirable to limit all TCP traffic to 10 Mbps, while at the same time limiting FTP traffic (a subset of TCP traffic) to no more than 1.5 Mbps. To achieve this nested policing requirement, hierarchical policing can be used with up to three levels.
policy-map FTP-POLICER
class FTP
police cir 1500000
conform-action transmit
exceed-action drop
!
policy-map TCP-POLICER
class TCP
police cir 10000000
conform-action transmit
exceed-action drop
service-policy FTP-POLICER
!
interface ge 1/1
service-policy output TCP-POLICERPercentage-Based Policing
Most networks contain a wide array of interfaces with different bandwidths. If it is desirable to have an overall network policy in which, for example, FTP traffic is not to exceed 10 percent of the bandwidth on any interface, percentage-based policing can be used.
CIR and PIR values can be specified with percent, but not the burst sizes; the burst sizes are configured in units of milliseconds. If the CIR is configured in percent, the PIR also must be
When the service policy is attached to an interface, the CIR (and PIR, if configured) is determined as a percentage of the interface bandwidth. If the interface bandwidth is changed, the CIR and PIR values and burst sizes are automatically recalculated using the new interface bandwidth value
For subinterfaces, the bandwidth of the main interface is used for the calculation
If the percent feature is used in a second- or third-level policy, the bandwidth of the lower-level policy statement is determined by the configuration of the higher or parent level
LLQ is a policer and not bandwidth
LLQ mechanism “priority” contains an implicit policer and LLQ gives strict transmission priority to real-time traffic, and by doing so it introduces the possibility of starving lower-priority traffic. To prevent this situation, the LLQ mechanism polices traffic to the bandwidth specified in the priority statement by indiscriminately tail-dropping traffic exceeding the configured rate
priority statement can be specified with an absolute bandwidth or by using a percentage.
Control Plane Policing
CoPP allows the configuration of QoS policers to rate-limit the traffic handled by the main CPU of the switch. These policers serve to protect the control plane of the switch/router from DoS attacks and reconnaissance activity. With CoPP, QoS policies are configured to permit, block, or rate-limit packets destined to the main CPU. For example, if a large amount of multicast traffic is introduced into the network with a Time To Live (TTL) of 1, this traffic would force the switch to decrement the TTL, and thereby force the control plane to send an ICMP (Internet Control Message Protocol) error message. If enough of these events happened, the CPU would not be able to process them all, and the node would be effectively taken out of service
CoPP can protect a node against this type of attack
Shaper
Continue from file:///G:/My%20Drive/Learn%20Journey/2_QoS/Book%20HTMLs/End-to-End%20QoS%20Network%20Design%20Quality%20of%20Service%20for%20Rich-Media%20&%20Cloud%20Networks,%20Second%20Edition/online%20version/Chapter%204.%20Policing,%20Shaping,%20and%20Markdown%20Tools.html
“Traffic Shaping Tools”
! PRACTICE
! This class map relies on packets with marking already applied
class-map match-any REALTIME
match dscp ef ! Matches VoIP bearer traffic
match dscp cs5 ! Matches Broadcast Video traffic
match dscp cs4 ! Matches Realtime-Interactive traffic
!
class-map match-any CONTROL
match dscp cs6 ! Matches Network-Control traffic
match dscp cs3 ! Matches Voice/Video Signaling traffic
match dscp cs2 ! Matches Network Management traffic
!
class-map match-any CRITICAL-DATA
match dscp af41 af42 af43 ! Matches Multimedia Conf. on AF4
match dscp af31 af32 af33 ! Matches Multimedia Streaming on AF3
match dscp af21 af22 af23 ! Matches Transactional Data on AF2
match dscp af11 af12 af13 ! Matches Bulk Data on AF1
!
policy-map WAN-EDGE-4-CLASS
class REALTIME
priority percent 33 ! 33% LLQ for REALTIME class
class CONTROL
bandwidth percent 7 ! 7% CBWFQ for CONTROL class
class CRITICAL-DATA
bandwidth percent 35 ! 35% CBWFQ for CRITICAL-DATA class
fair-queue ! Fair-queuing on CRITICAL-DATA
random-detect dscp-based ! DSCP-based WRED on CRITICAL-DATA
class class-default
bandwidth percent 25 ! 25% CBWFQ for default class
fair-queue ! fair-queuing on default class
random-detect dscp-based ! DSCP-based WRED on default class
!
interface serial 1/0/0
service-policy output WAN-EDGE-4-CLASS
-----------------------------------------------------
class-map markings
match dscp af41 af42 af43
!
class-map mac-address
match destination-address mac 00:00:00:00:00:00
!
class-map ftp
match protocol ftp
-----------------------------------------------------
policy-map SET-DSCP
class DSCP-AF31
set dscp af31
-----------------------------------------------------
class-map match-any TRAFFICTYPE1
match <criteria1>
match <criteria2>
class-map match-all TRAFFICTYPE2
match <criteria3>
match <criteria4>
class-map TRAFFICTYPE3
match not <criteria5>
! reusing previously defined class
class-map DETAILS
match <criteria6>
class-map HIGHER-LEVEL
match class-map DETAILS
match <criteria7>
-----------------------------------------------------
! police set actions for remarking
Router(config)# policy-map CB-POLICING
Router(config-pmap)# class FOO
Router(config-pmap-c)# police 8000 conform-action ?
drop drop packet
exceed-action action when rate is within conform and
conform + exceed burst
set-clp-transmit set atm clp and send it
set-discard-class-transmit set discard-class and send it
set-dscp-transmit set dscp and send it
set-frde-transmit set FR DE and send it
set-mpls-exp-imposition-transmit set exp at tag imposition
and send it
set-mpls-exp-topmost-transmit set exp on topmost label
and send it
set-prec-transmit rewrite packet precedence
and send it
set-qos-transmit set qos-group and send it
transmit transmit packetWhen you configure multiple DSCP values on the same line, like this:
match dscp af41 af42 af43This is treated as a logical OR within that line.
match-any → logical OR
The packet only needs to match one of the listed conditions to be considered a match.
match-all → logical AND
The packet must satisfy all of the listed conditions at the same time to be considered a match.
The default logical operator (if unspecified) is match-all.
match not
will select inverse traffic
Note that class map and policy map names are case sensitive. Thus, class-map type1 is different from class-map Type1, which is different from class-map TYPE1. Class map names and cases must match exactly the class names specified in policy maps.
Unclassified traffic (traffic that does not meet the match criteria specified in the explicit traffic classes) is treated as belonging to the implicit default class.
specifying a policy map for “class-default” is optional, and if not specified, default class traffic has no QoS features assigned
default class traffic has no QoS features assigned, receives best-effort treatment, and can use all bandwidth not allotted or needed by the classes explicitly specified in the configuration – so if a lot of bandwidth is left on link then this class wins, if there is a less bandwidth left on the link then this class default traffic is looser
The default treatment for unclassified traffic with no QoS features enabled is a first-in, first-out (FIFO) queue with tail drop (which treats all traffic equally and simply drops packets when the output queue is full).
priority queuing, fair queuing are queueing treatments called priority queuing and fair queuing
priority command allocates bandwidth and also sets queuing treatment of priority as well, any traffic that has priority applied is sent out as soon as received, “skips to the front of the queue and scheduled first over anything else”
Queueing
Queueing types FIFO, CBWFQ and LLQ
Queue is a memory or buffer allocated on the interface and queue is always there on an interface, it only comes into play (holds packet to wait) when packets are coming into router faster than it can send them out or dispatch them out of egress interface
queue or buffer is a limited memory that can fill up and overflow and if we try to put a packet into this overflowing queue, packet will be dropped
A brilliant solution is to make sub queues or smaller queues carved out of that one big queue
so queue for best effort overflows it does not effect the voip traffic, only best effort packets will be denied or dropped while traffic for all other services keep working
Cisco recommends no more than 11 sub queues
If all traffic is dropped due to single queue for all services – TCP global Sync
TCP has sliding window, which means that TCP can gradually start skipping the acknowledgements as time passes and this window or set or number of segments start to increase till one ack is missed and TCP thinks that there is no accountability for what was sent and what was received (from remote end) so it shrinks that window down
random-detect
random-detect command enables Weighted Random Early Detection (WRED) on a queue.
It monitors the average queue depth.
If the queue starts filling:
Below the minimum threshold → no packets dropped.
Between min and max thresholds → packets are randomly dropped with increasing probability.
Above the maximum threshold → all packets are dropped (tail drop).
This prevents global synchronization of TCP flows and smooths congestion
See Section: Random Detect example with remark , mark down
for config example and explanation
fair-queue (queueing)
fair-queue command is one of the older queueing mechanisms in IOS, before CBWFQ and LLQ became standard
Fair Queueing (FQ) = A congestion management method that automatically creates separate queues per flow (based on source/destination IP and port), Used mainly on slow links (≤ 2 Mbps)
The router then services each queue in a round-robin fashion, so no single flow (e.g. a big FTP transfer) can dominate the link
Cisco recommends CBWFQ/LLQ instead of fair-queue on modern WANs
QoS commands
show qos interface show queueing interface show class-map show policy-map show policy-map interface show table-map C4500# show policy-map interface TenGigabitEthernet 1/1 TenGigabitEthernet1/1 Service-policy output: 1P7Q1T Class-map: PRIORITY-QUEUE (match-any) 102598 packets Match: dscp ef (46) 102598 packets Match: dscp cs5 (40) 0 packets Match: dscp cs4 (32) 0 packets priority queue: Transmit: 22782306 Bytes, Queue Full Drops: 0 Packets Class-map: CONTROL-MGMT-QUEUE (match-any) 24847 packets Match: dscp cs7 (56) 0 packets Match: dscp cs6 (48) 0 packets Match: dscp cs3 (24) 24847 packets Match: dscp cs2 (16) 0 packets bandwidth remaining 10 (%) Transmit: 24909844 Bytes, Queue Full Drops: 0 Packets Class-map: MULTIMEDIA-CONFERENCING-QUEUE (match-all) 22280511 packets Match: dscp af41 (34) af42 (36) af43 (38) bandwidth remaining 10 (%) Transmit: 4002626800 Bytes, Queue Full Drops: 0 Packets dbl Probabilistic Drops: 0 Packets Belligerent Flow Drops: 0 Packets Class-map: MULTIMEDIA-STREAMING-QUEUE (match-all) 0 packets Match: dscp af31 (26) af32 (28) af33 (30) bandwidth remaining 10 (%) Transmit: 0 Bytes, Queue Full Drops: 0 Packets dbl Probabilistic Drops: 0 Packets Belligerent Flow Drops: 0 Packets Class-map: TRANSACTIONAL-DATA-QUEUE (match-all) 235852 packets Match: dscp af21 (18) af22 (20) af23 (22) bandwidth remaining 10 (%) Transmit: 247591260 Bytes, Queue Full Drops: 0 Packets dbl Probabilistic Drops: 0 Packets Belligerent Flow Drops: 0 Packets Class-map: BULK-DATA-QUEUE (match-all) 2359020 packets Match: dscp af11 (10) af12 (12) af13 (14) bandwidth remaining 4 (%) Transmit: 2476460700 Bytes, Queue Full Drops: 0 Packets dbl Probabilistic Drops: 0 Packets Belligerent Flow Drops: 0 Packets Class-map: SCAVENGER-QUEUE (match-all) 78607323 packets Match: dscp cs1 (8) bandwidth remaining 1 (%) Transmit: 98144078642 Bytes, Queue Full Drops: 26268 Packets Class-map: class-default (match-any) 12388183 packets Match: any 12388183 packets bandwidth remaining 25 (%) Transmit: 13001465825 Bytes, Queue Full Drops: 0 Packets dbl Probabilistic Drops: 0 Packets Belligerent Flow Drops: 0 Packets C4500#
next post
SDWAN | LM Notes
SDWAN Basics & LAB Controllers / Edge Standup

in above, only vbond authenticates to the vmanage, every thing else authenticates to the vbond including vsmart and all wan edges
All are assigned certificate from vmanage but they all authenticate to vbond except vbond itself which has to authenticate with vmanage as there is nothing else
Step 1. First we install vmanage and add vbond to vmanage
vmanage then issues certificate to vbond
vmanage and vbond then perform mutual certificate based authentication and establish a management channel indicated by the grey arrow
Step 2. Then we add vsmart to vmanage and vmanage then issues certificate to the vsmart
you will see after step 2 vsmart information is uploaded to vbond (so vsmart can first authenticate to vbond)
vsmart then contacts and authenticates with vbond
after authentication vsmart will have management channel with vbond and vmanage
At this stage, if we have more vsmarts, they will learn about other vsmarts from vbond
Step 3. Either vmanage can sync with your smart account and download the list of devices
or we can use the serial file method which is offline method of importing devices
once device list has been uploaded to vmanage, it uploads this device list to all controllers (vbond and vsmart)
at this point all the controllers are aware of all the wan edge devices which will join
Step 4 When the wan edge device comes up it gets DHCP ip and contacts ZTP on a pre-defined URL
ZTP in this case is cisco’s online server that will have all the licenses generated will redirect the wan edge to organisation’s vbond
wan edge will authenticate with vbond
vbond will inform the wan edge about how to get to vmanage and vsmart
Step 5. wan edge will go and authenticate with vmanage and establish the management channel
Step 6. wan edge will go and authenticate with vsmart and establish the OMP channel
Step 7. wan edge will establish the IPSec tunnel with other wan edge routers
TLOC = System IP + Color + Encapsulation protocol
There are 3 kinds of routes
OMP routes
TLOC routes
Service routes
TLOC is maintained using BFD, if a TLOC goes down then all routes associated to that TLOC are removed just like next hop interface
BFD does more than reachability check, it checks for Loss (completely no response) , delay (delayed response) , jitter (variation in delay) as well also called path quality, these path quality metrics are then used in application aware routing
If there is a second vsmart, wan edge will have another omp peering with that vsmart
VPN number is tagged in the IPSec header so other router can land that traffic in same VPN
Configuration is not only pushed to wan edge devices but also to the vsmart
vsmart is also considered a managed device like wan edge router since it needs to be added to vmanage and applied configuration through the template etc just like wan edge device
once template is applied, devices go in something called vmanage mode and then we cannot configure devices from CLI (initially you can configure devices from CLI but once managed by vmanage you cannot)
Device template > feature template
As can be seen above
Centralized control policy (vsmart)
Centralized data policy (wan edge)
Localized control policy (wan edge)
Localized data policy (wan edge)
Centralized control policy is used to create different types of topologies
Centralized data policy is like route-map that is applied on interface effects the data packet directly, we can match packets based on packet header or application based matching which relies on deep packet inspection and take actions such as dropping packets, QoS classification, policing, change next hop and so on – but this is pushed by vsmart and lives in wan edge memory and does not really get added to the device local configuration, remember that from central keyword, anything that is centralized, its policies are in wan edge’s memory and not in the wan edge config
Localized control policy – this is effective or configured on the service side only, so if OSPF and BGP is running on LAN of the wan edge, localized control policy is needed
Localized Data policy is very similar to the Centralized Data policy, only difference is that is configuration is pushed and becomes part of wan edge configuration and is per interface
make sure when connecting vbond device to switch, it is connected using ge0/0 instead of eth0
this will save you a lot of troubleshooting time when standing up vBond

WINSERVER configuration
Setup same as https://learn.anasather.uk/masters/eveng/eveng-ccie-lab-and-megalinks/
Assign IP address as to Win server as below

Deploy NTP on Windows Server
https://www.domat-int.com/en/how-to-configure-a-local-ntp-server
https://docs.litmus.io/litmusedge/product-features/system/network/configure-dns-ntp-servers/configure-local-ntp-server
Configure the Windows Time Service
In the File Explorer, navigate to: Control Panel\System and Security\Administrative Tools
Double-click Services. This same task can be completed by entering services.msc in the Windows Run dialog (Windows Key + R).
In the Services list, right-click on Windows Time and click Stop.
Note: The Windows Time service may already be stopped. In this case, skip this step and go to the next step to Update the Windows Registry
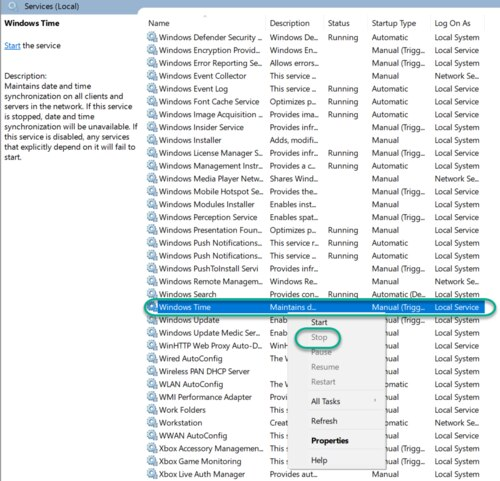
Update the Windows Registry to Create a Local NTP Service
Launch Windows Run (Windows Key + R).
Enter regedit and click OK.
Navigate to the registry key: Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\Parameters
If you do not see LocalNTP REG_DWORD in the list, create it using the following steps.
Right-click in the Registry Editor, select New, select DWORD and enter LocalNTP (note that this name is case sensitive).
Double-click LocalNTP, change the Value data to 1, select a Base of Hexadecimal , and click OK.
Do not close the Registry Editor because it is used in the following steps.
Update the Windows Registry to Configure the Time Provider
Navigate to the registry key: Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders
Select NtpServer, double-click Enabled, change the Value Data to 1, select a Base of Hexadecimal and click OK.
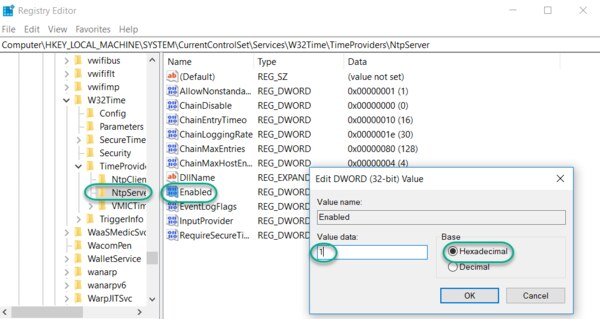
Do not close the Registry Editor because it is used in the following steps.
Update the Windows Registry to Configure the Announce Flags
Navigate to the registry key: Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\Config
Double-click AnnounceFlags, change the Value data to 5, select a Base of Hexadecimal, and click OK.
Close the Registry Editor.
Start the Local Windows NTP Time Service
In the File Explorer, navigate to: Control Panel\System and Security\Administrative Tools
Double-click Services.
In the Services list, right-click on Windows Time and configure the following settings:
Startup type: Automatic
Service Status: Start
OK
Finally, enable UDP port 123 on the Windows firewall for incoming connections.
In Search find Firewall in Windows Defender…
Go to Incoming rules
In the right column, select New rule…
Select the rule Port
Enter UDP port 123 and click Next
Select Allow connection and click Next
Select all domains
Enter the rule name, e.g. Local NTP server, and click Finish.
The local NTP Time Server configuration is now complete. You now can synchronize the time of other computers and devices on your local network.
To test the server functionality from another PC (e.g. a service notebook) use for example the NTP Server Test Tool:
https://www.ntp-time-server.com/ntp-software/ntp-server-tool.html
Configure CA Server
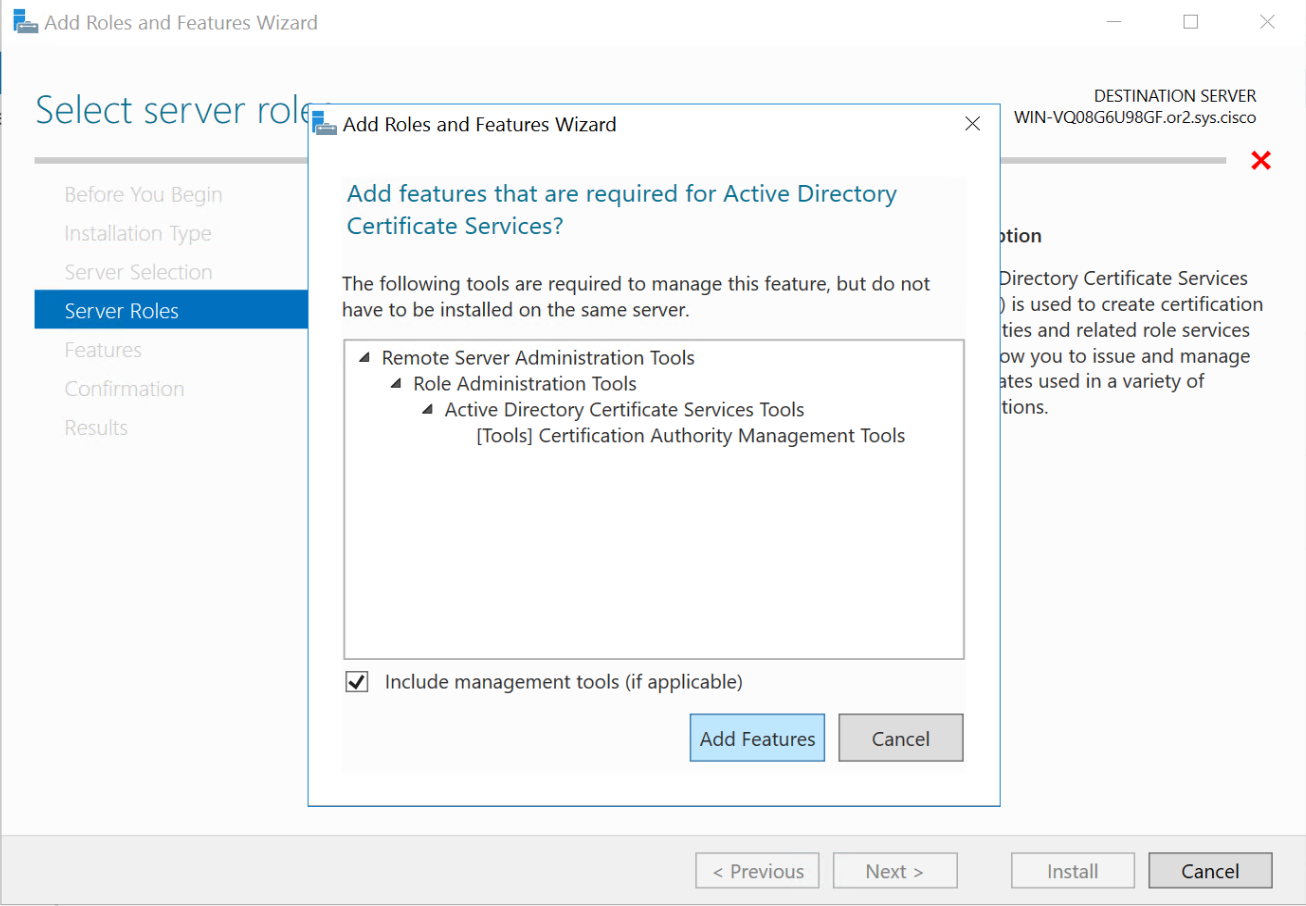
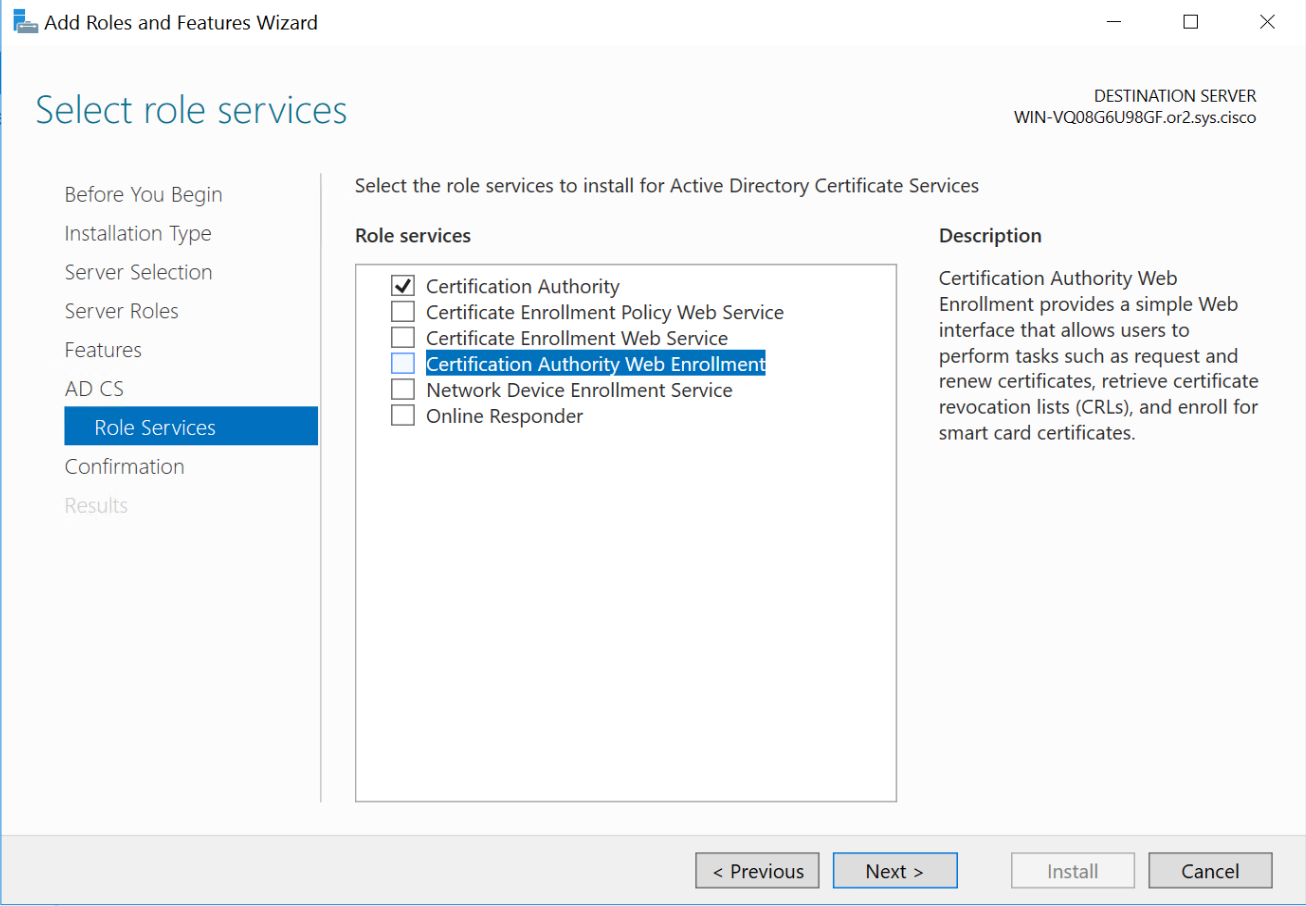
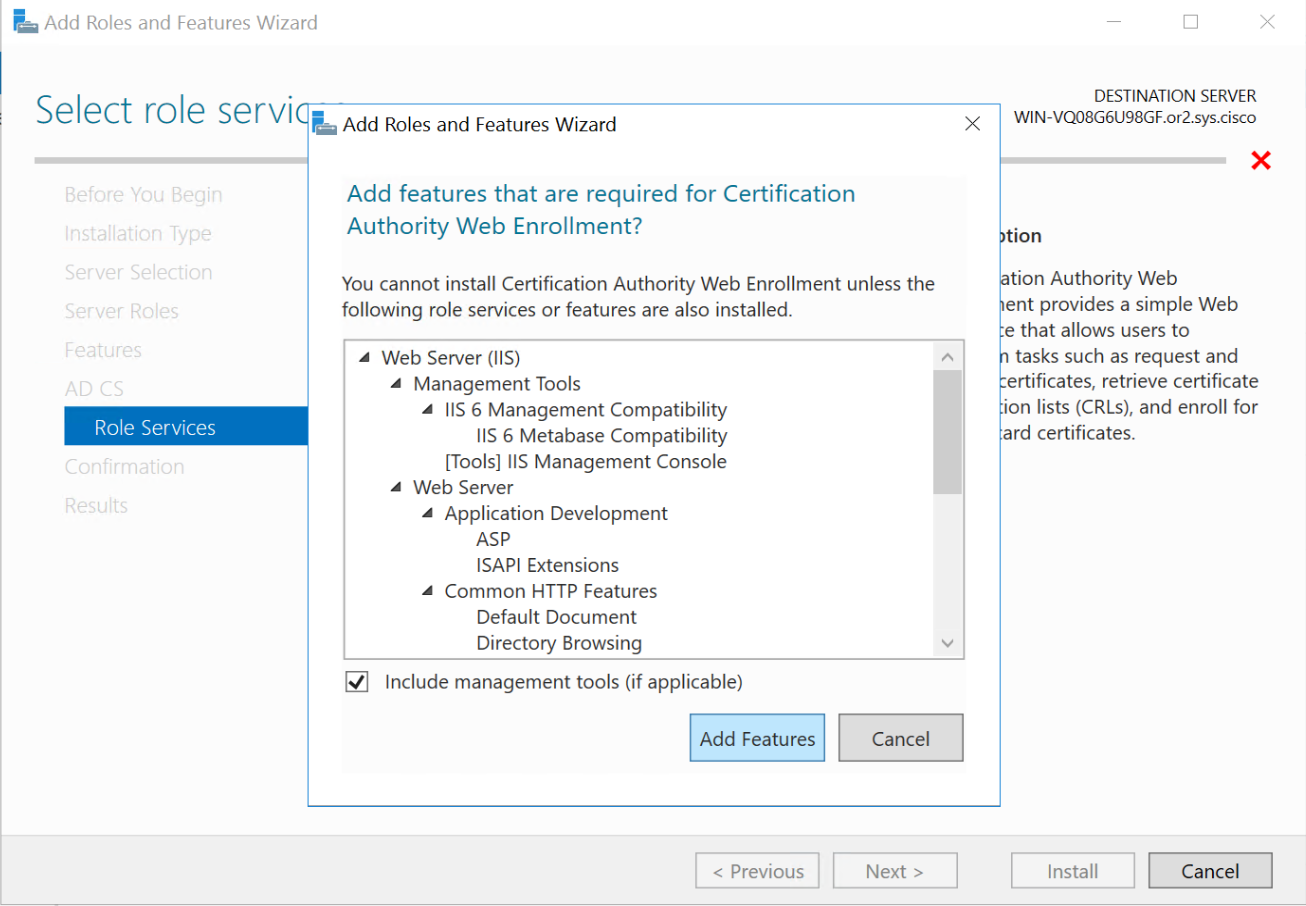
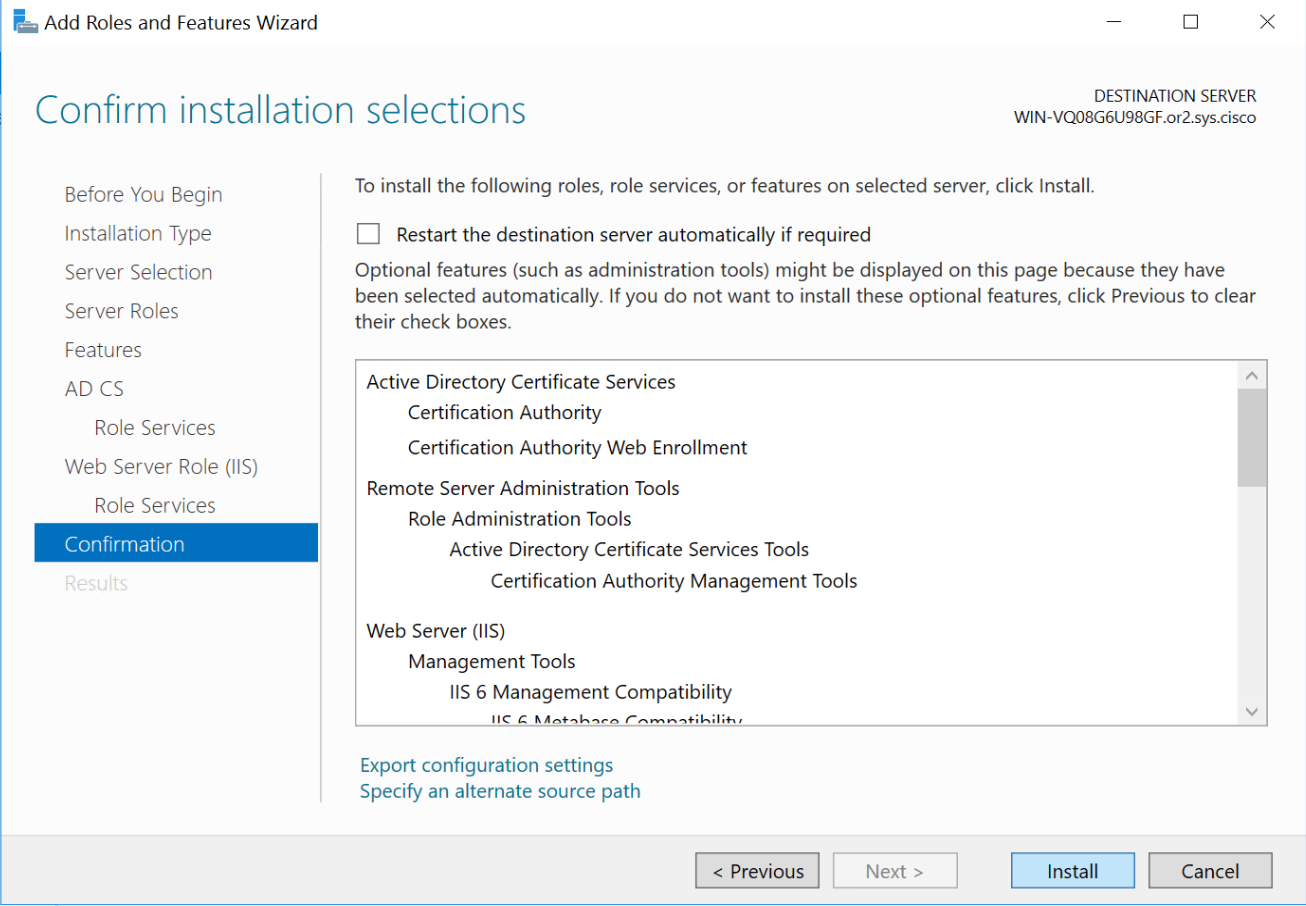
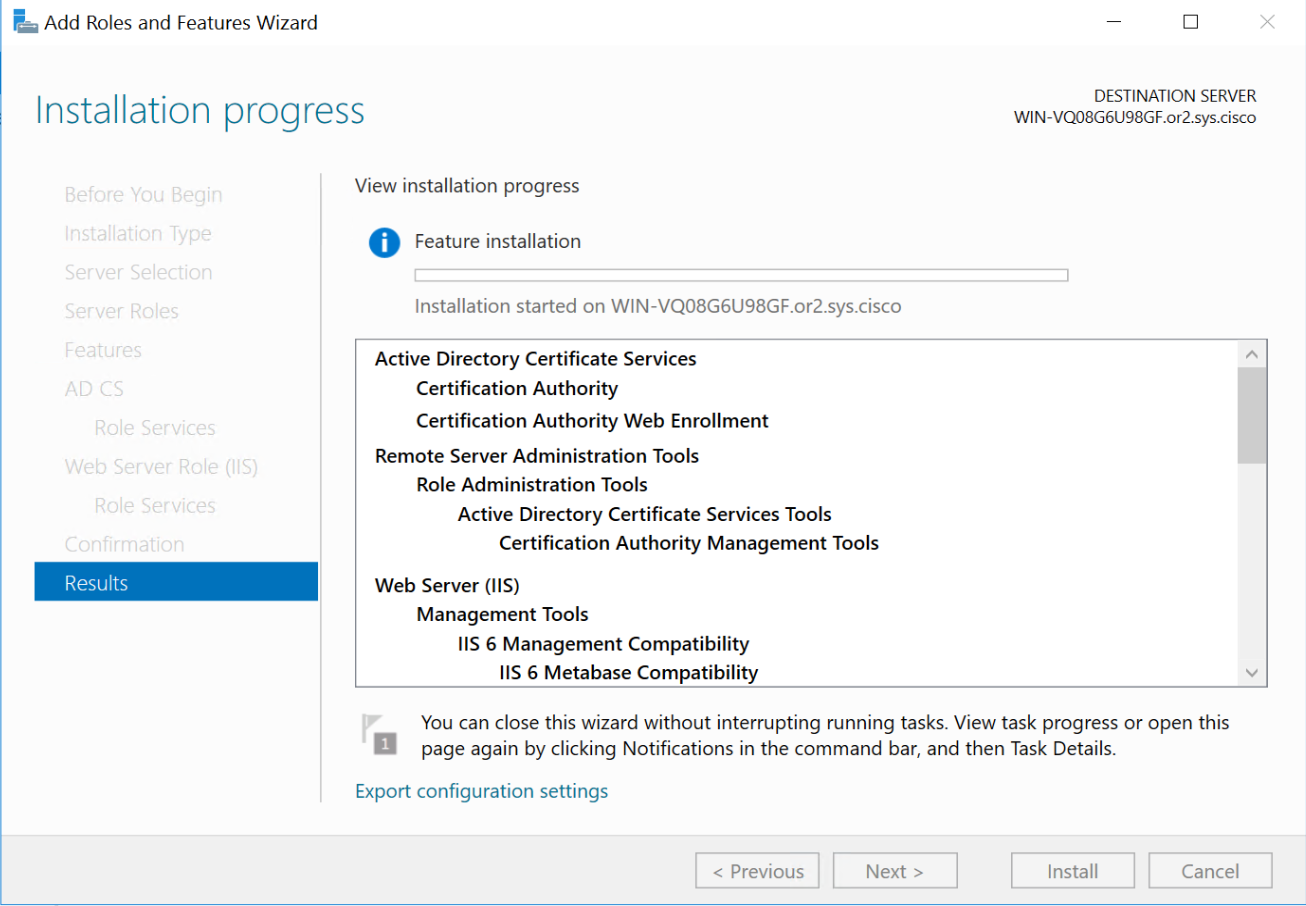


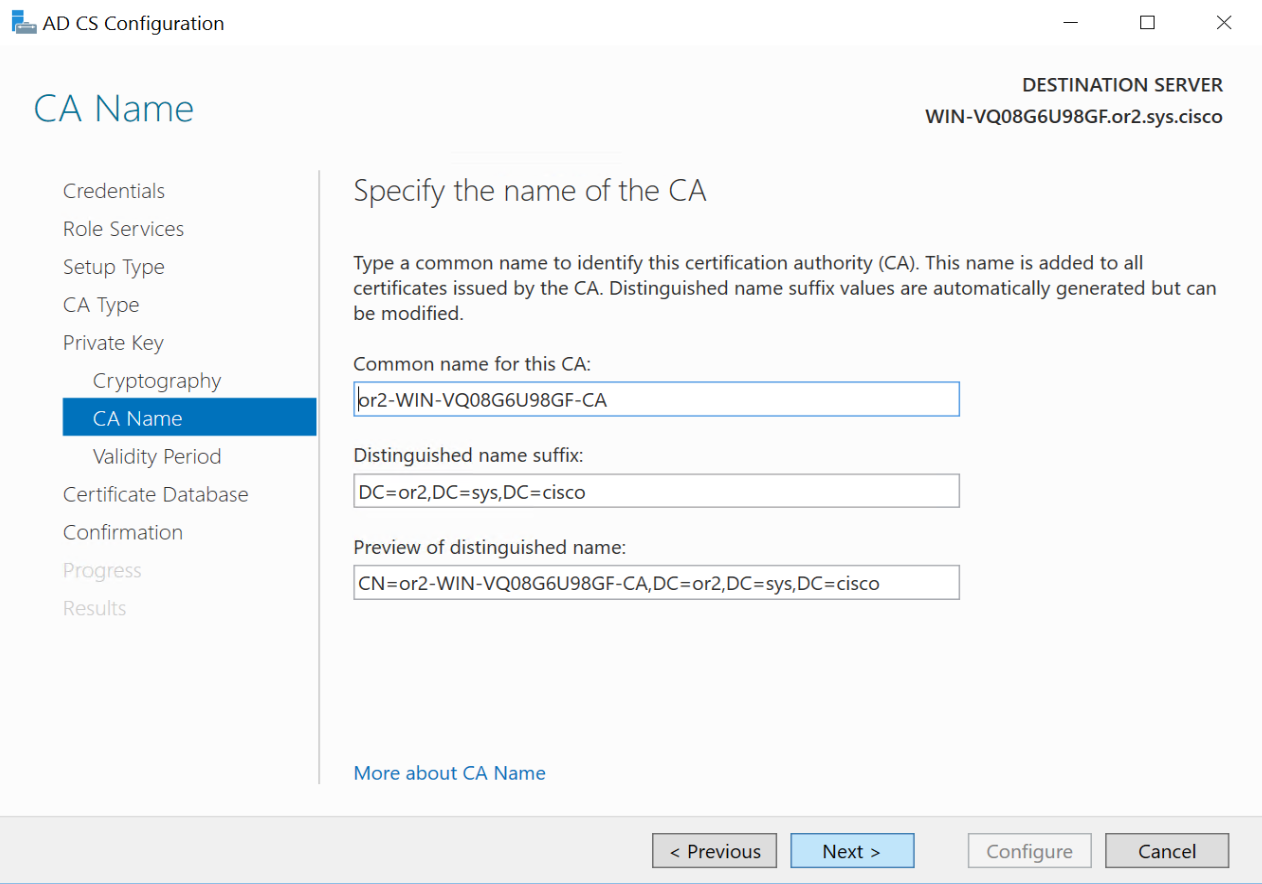
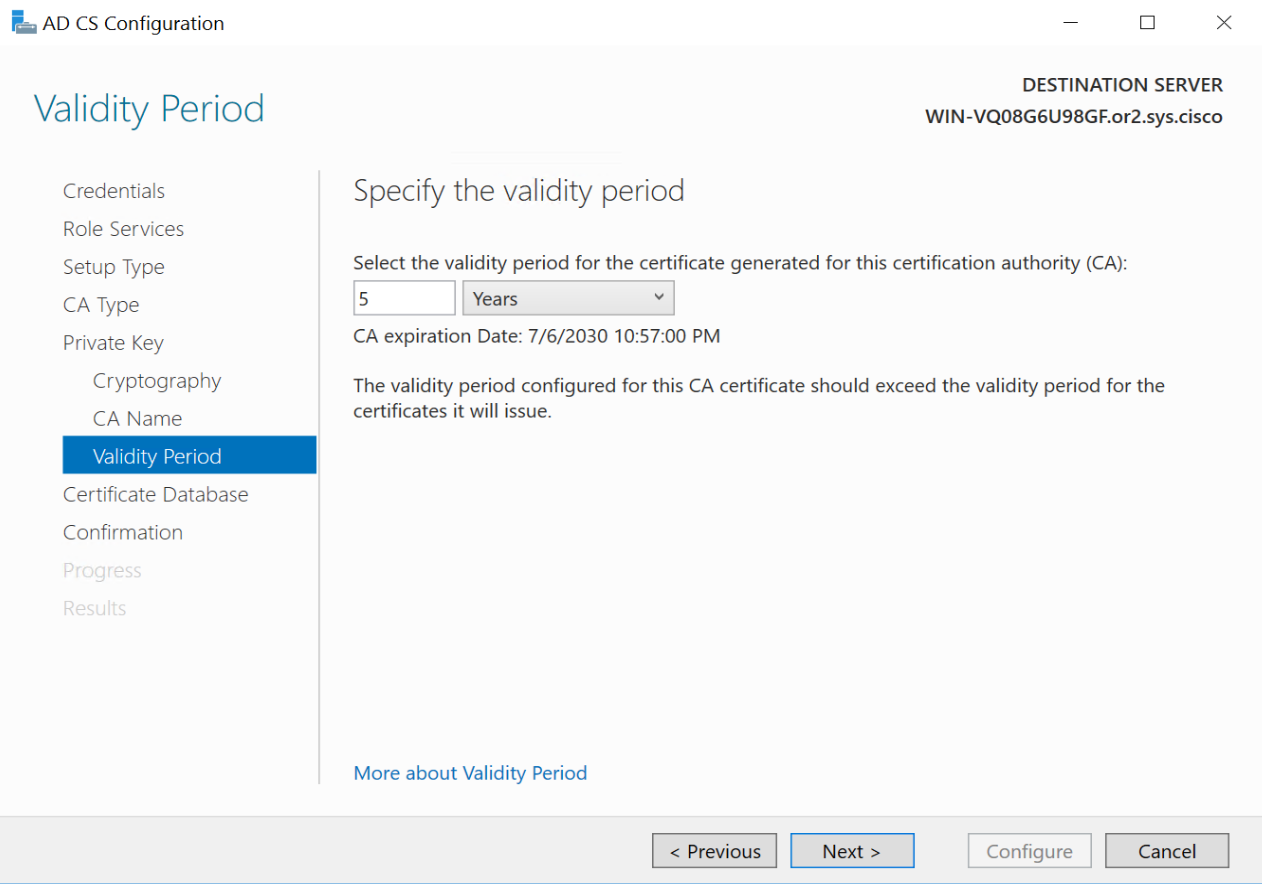
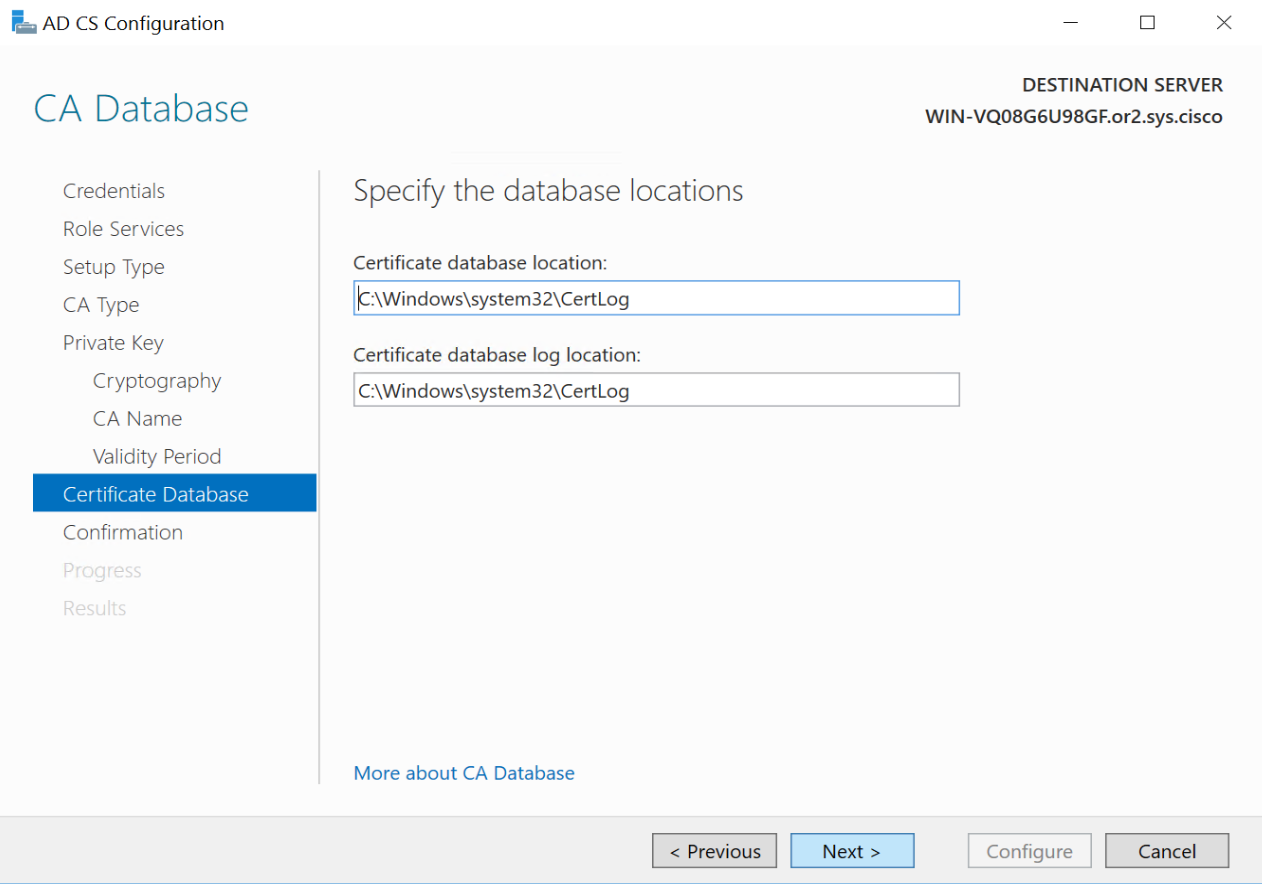
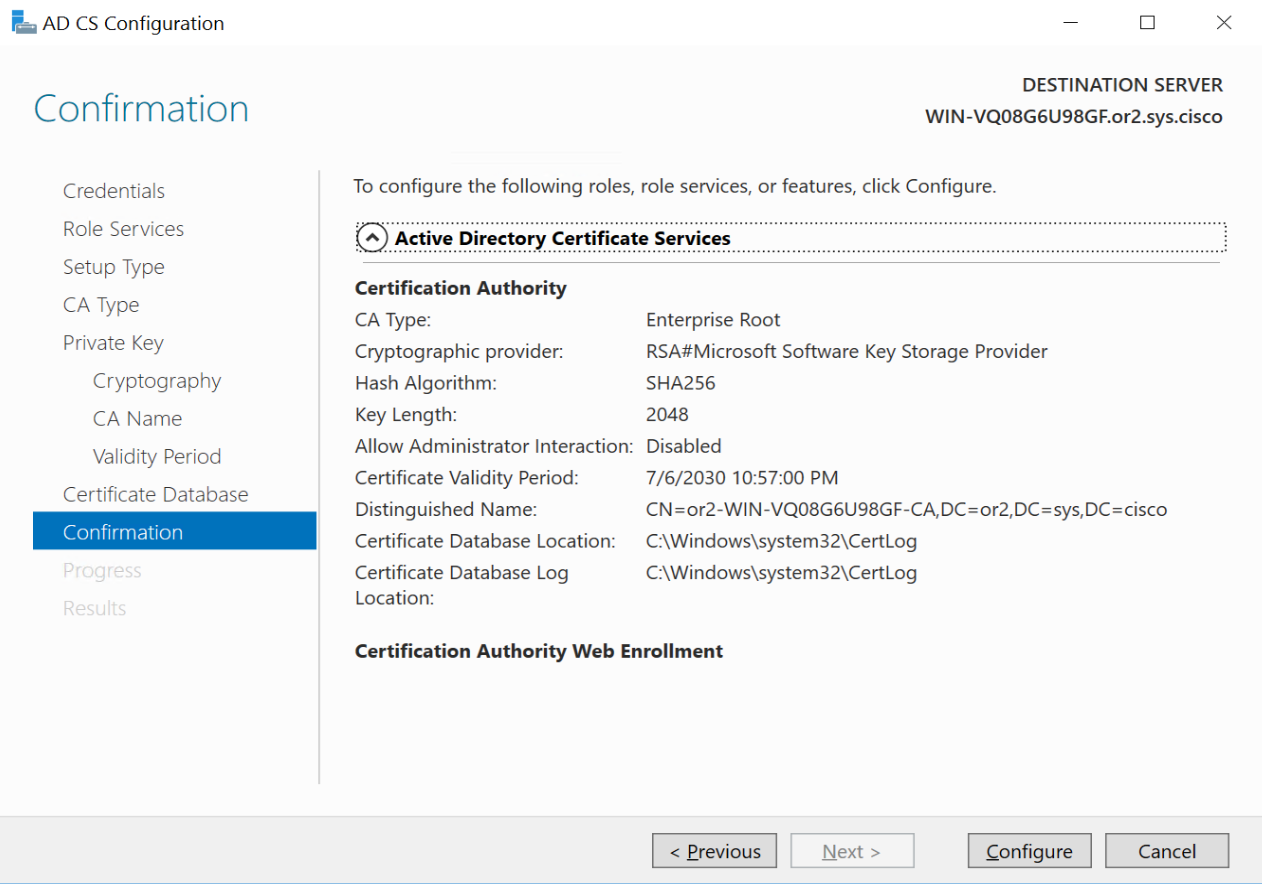
now visit http://[serverFQDN]/certsrv
http://win-vq08g6u98gf.or2.sys.cisco/certsrv/
SDWAN Standup
default username and password for vbond is admin/adminvManage requires second hard disk in vCenter
We should know this if we are deploying for onprem environment

it needs to be 100G minimum
Make sure it is the master
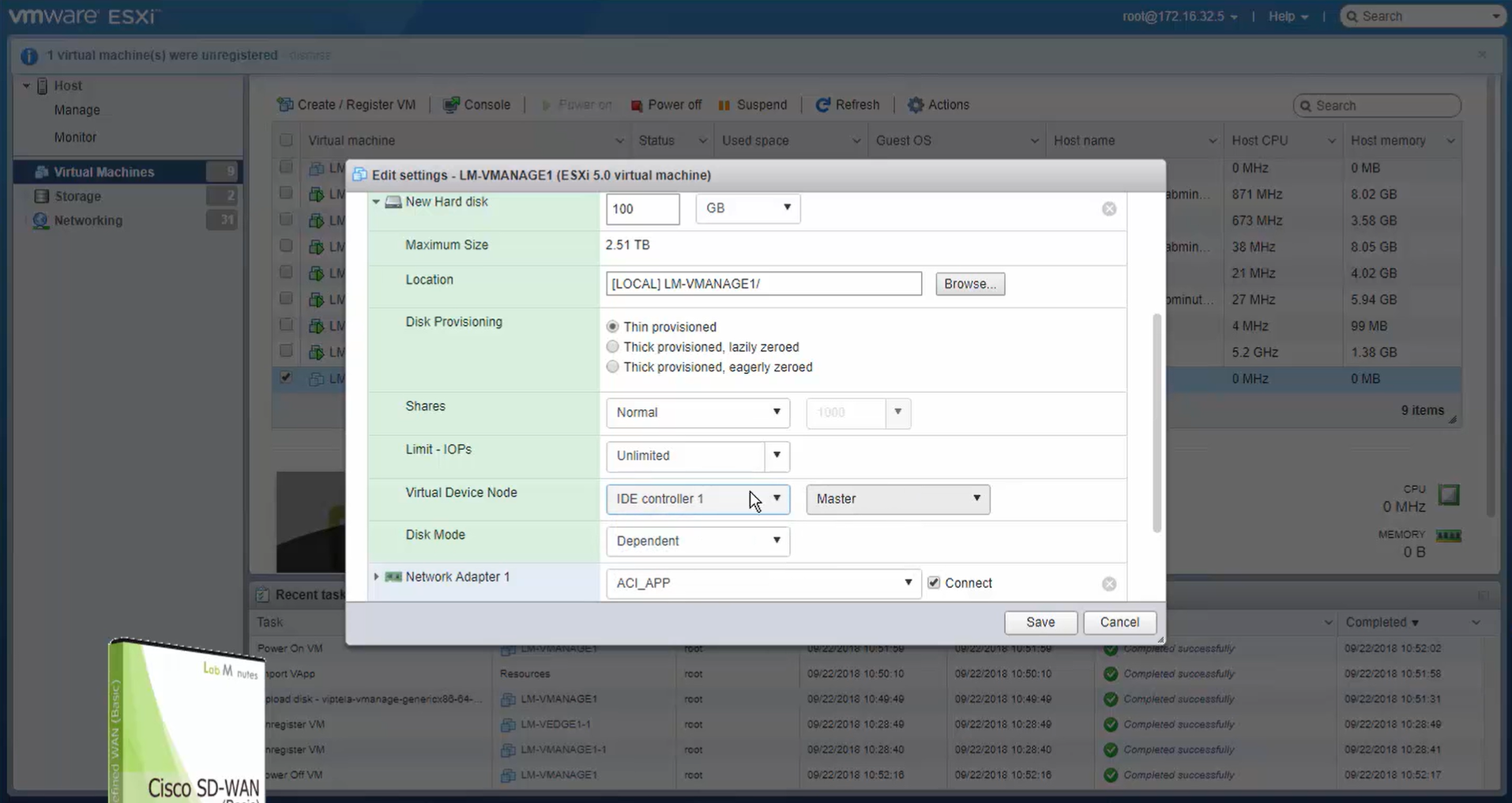
During setup we can see the additional disk we added
vManage system configuration
Assign vmanage second hard drive , if this has not been done already
cd /opt/unetlab/addons/qemu/vtmgmt-20.9.1
/opt/qemu/bin/qemu-img create -f qcow2 virtiob.qcow2 100G
/opt/unetlab/wrappers/unl_wrapper -a fixpermissionsshow version
conf t
system
host-name vManage
system-ip 1.1.255.11
clock timezone Europe/London
site-id 255
organization-name or2.sys.cisco
vbond vbond.or.sys.cisco
ntp server ntp.or2.sys.cisco
! it is important to have ntp server and
! have all controllers and devices with same
! time because we are doing a lot of certificate
! based authentication
! vbond IP is the only controller that you
! define on each all SDWAN devices whether
! controllers or vedge if you have 2 vBond
! then it is good to add FQDN otherwise IP
! address is ok, reason is that on controllers
! we cannot define two different vbond IP addresses
! always commit the configuration
commitshow running-configvmanage(config-ntp)# do show running-config ! to see the commmitted configuration
system
host-name vmanage
admin-tech-on-failure
no vrrp-advt-with-phymac
aaa
auth-order local radius tacacs
usergroup basic
task system read
task interface read
!
usergroup global
!
usergroup netadmin
!
usergroup operator
task system read
task interface read
task policy read
task routing read
task security read
!
usergroup resource_group_admin
task system read
task interface read
!
usergroup resource_group_basic
task system read
task interface read
!
usergroup resource_group_operator! check configuration of a section while in that section
vmanage(config)# system
vmanage(config-system)# show configuration ! t show uncommitted configuration but only under system section
system
host-name vManage
system-ip 1.1.255.11
site-id 255
organization-name or2.sys.cisco
clock timezone Europe/London
vbond vbond.or.sys.cisco
ntp
server ntp.or2.sys.cisco
version 4
exit
!vSmart system configuration
conf t
system
host-name vSmart
system-ip 1.1.255.13
clock timezone Europe/London
site-id 255
organization-name or2.sys.cisco
vbond vbond.or.sys.cisco
ntp server ntp.or2.sys.ciscovBond system configuration
conf t
system
host-name vBond
system-ip 1.1.255.12
clock timezone Europe/London
site-id 255
organization-name or2.sys.cisco
vbond vbond.or.sys.cisco local
! this local keyword converts the vedge to vbond role
ntp server ntp.or2.sys.cisco
DNS server on Windows Server
Then create DNS A records
Add A record for vbond in or.sys.cisco domain
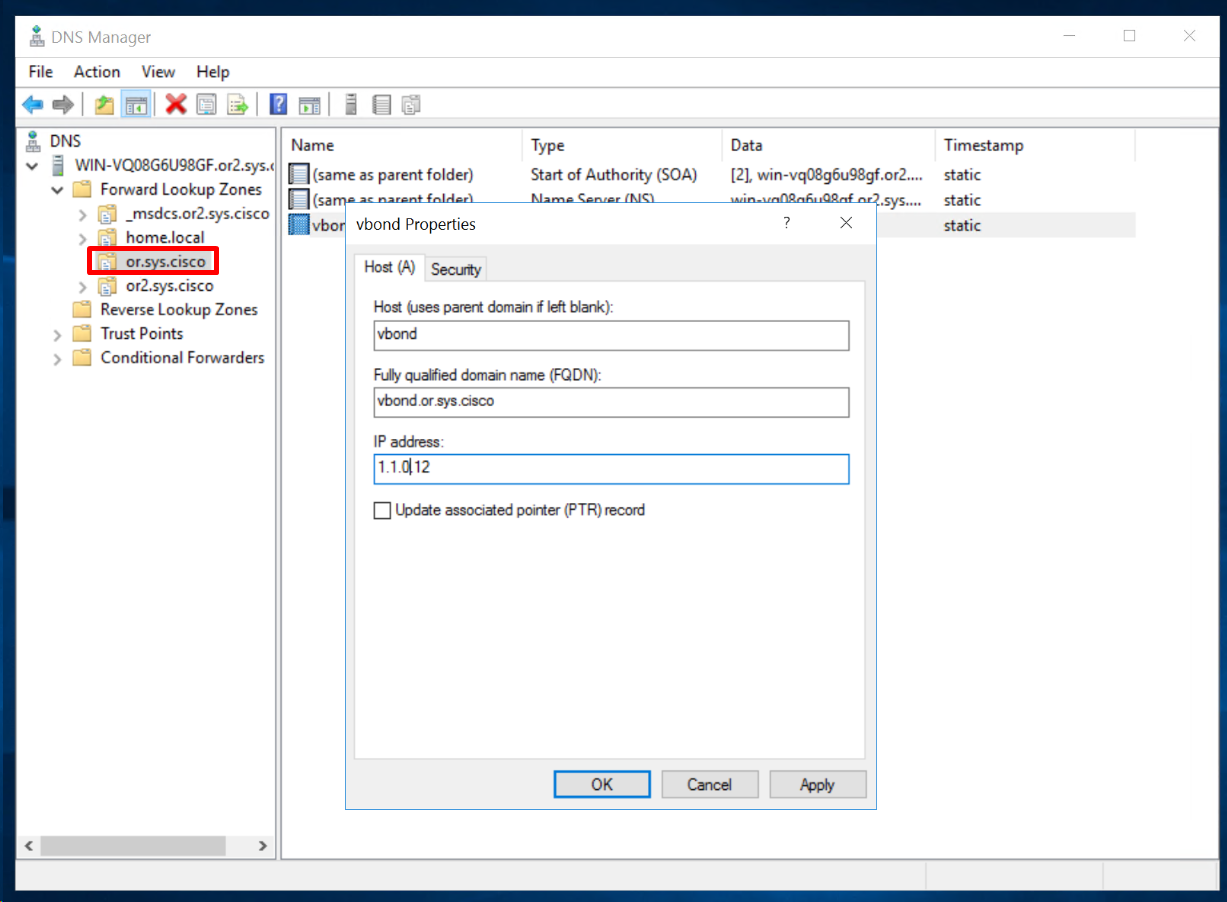
If we have a second vbond and it needs to be added then add another entry for “vbond” same as above but with different IP, multiple vbonds or vbond redundancy is supported by DNS roundrobin (default)
Add A record for ntp in or”2″.sys.cisco
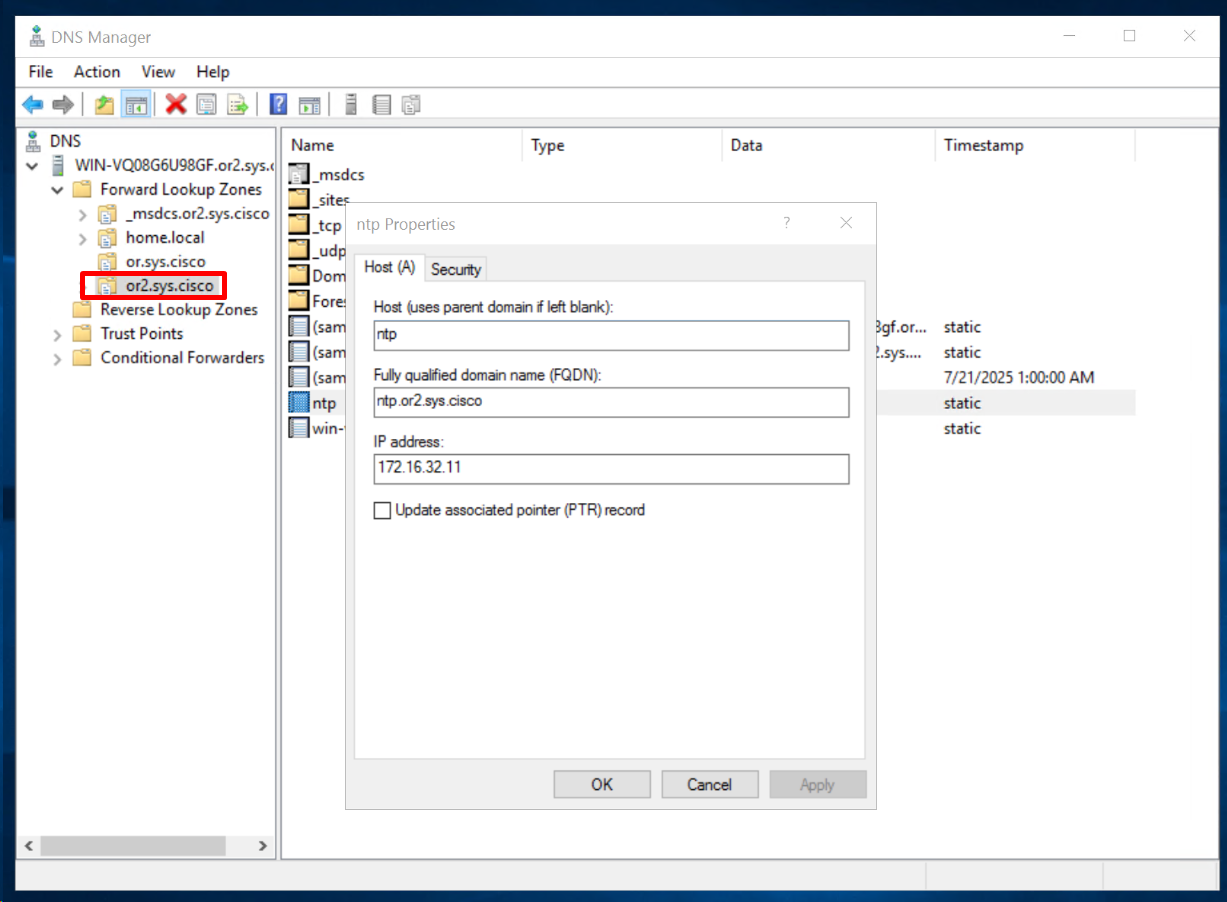
Configure the (WAN , Transport) interface of SDWAN controllers
These interfaces are configured under VPN 0 and they are used to access the GUI by admins and outbound to edge routers communication using NETCONF (vmanage), for OMP peering (vsmart) and onboarding (vbond)
There is no such thing as LAN interface for these controllers
In Cisco cedge devices we do not have VPN0 instead transport uses Global routing table or default non vrf routing table
Configure vmanage vpn0 Transport Interface (vpn0)
conf t
vpn 0
interface eth0
ip address 1.1.0.11/24
no shutdown
no tunn
! we keep the tunnel interface down for now as it is used to deal with overlay or fabric till we have basic connectivity up
! while within the vpn0 configure default route
ip route 0.0.0.0/0 1.1.0.1
dns 172.16.32.11 ! configure this DNS if your vmanage has reachability to internet for automatic sync of device serial numbers from internet rather than offline import of serial number file, "Sync Smart Account" button rather than "Upload WAN Edge List" buttonYou cannot have interface ip same as system ip so they both need to be different
vManage(config)# commit
Aborted: ‘vpn 0 interface eth0 ip address’: Interface eth0 with address 1.1.0.11/24 & System IP 1.1.0.11 cannot be same in vpn 0
Configure vsmart Transport Interface (vpn0)
conf t
vpn 0
interface eth0
ip address 1.1.0.13/24
no shutdown
no tunn
! we keep the tunnel interface down for now as it is used to deal with overlay or fabric
! while within the vpn0 configure default route
ip route 0.0.0.0/0 1.1.0.1
dns 172.16.32.11Configure vbond Transport Interface (vpn0)
conf t
vpn 0
interface ge0/0
! Option 1: we need to keep this tunnel interface down for vbond's own onboarding to work
no tunnel-interface
! or
! Option 2: bring up tunnel interface but allow some services on it
vpn 0
interface ge0/0
tunnel-interface
allow-service sshd
allow-service dns
allow-service ntp
Allowed service are both inbound and outbound
such as NTP will be outbound but SSH will be inbound
!--------------------------------
vpn 0
interface ge0/0
no tunnel-interface
ip address 1.1.0.12/24
no shutdown
! while within the vpn0 router, configure default route
ip route 0.0.0.0/0 1.1.0.1
dns 172.16.32.11
ping vbond.or.sys.ciscoDownload CA Certificate

Download in Base64 format
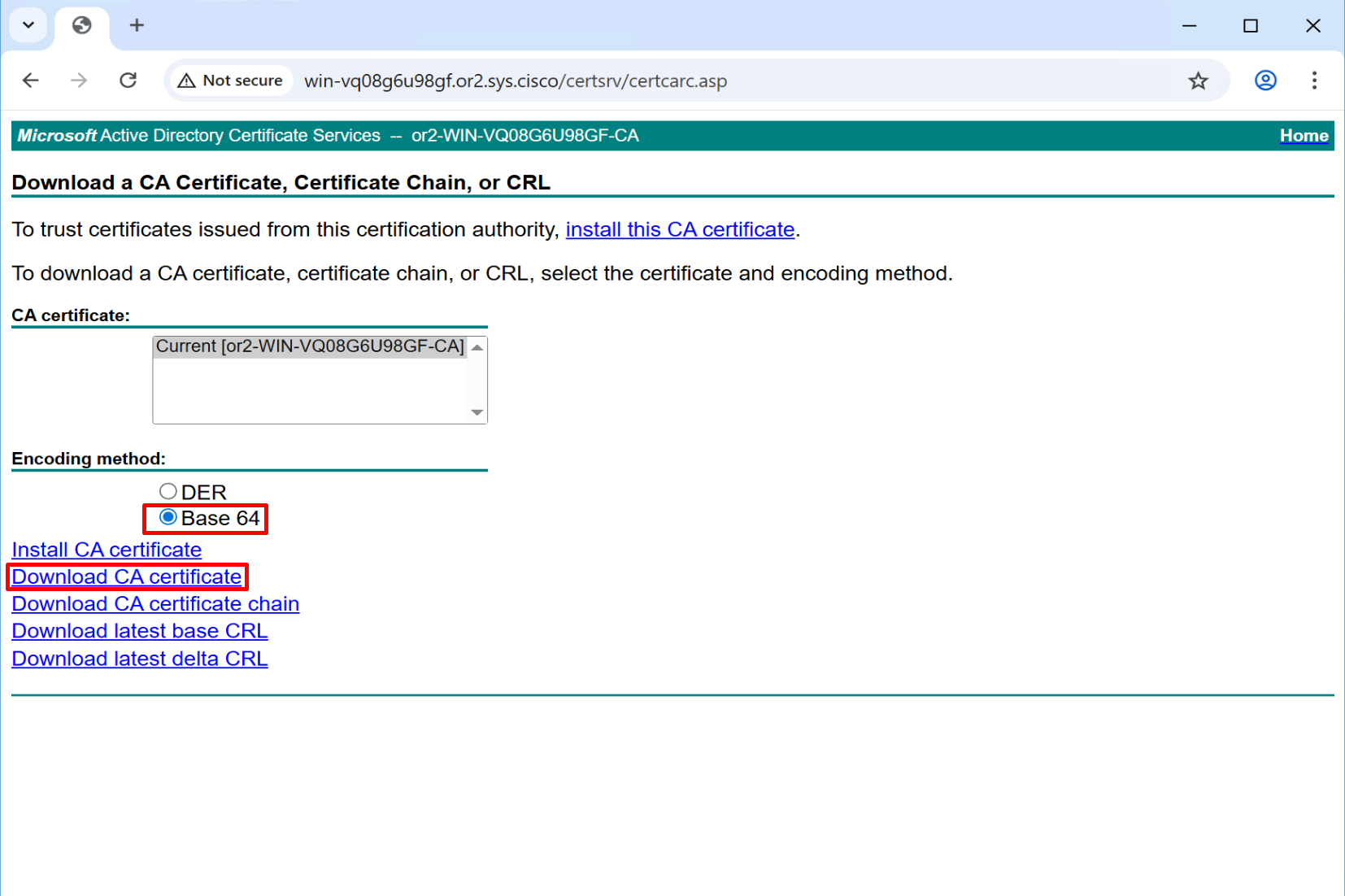
Rename this to root_ca
Access vmanage GUI but make sure you do using IP address and not FQDN, using FQDN it does not work and simply spins and comes back to login screen

Login as admin/Cisco123@
There is only one vmanage that is why we only see one on top summary
Upload root CA to all controllers’ trust store
WinSCP SFTP to the vManage
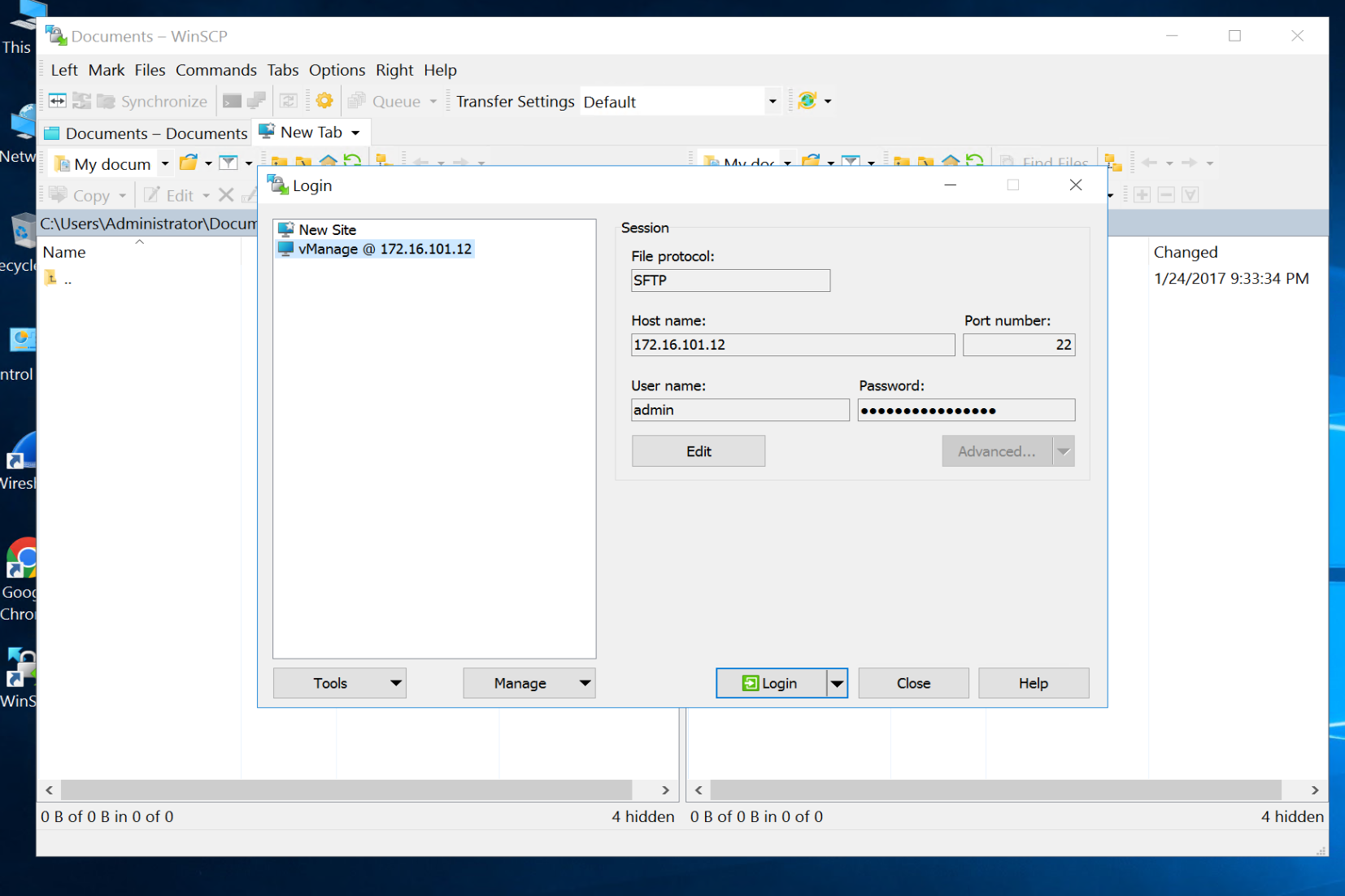
drag root.ca file to /home/admin folder
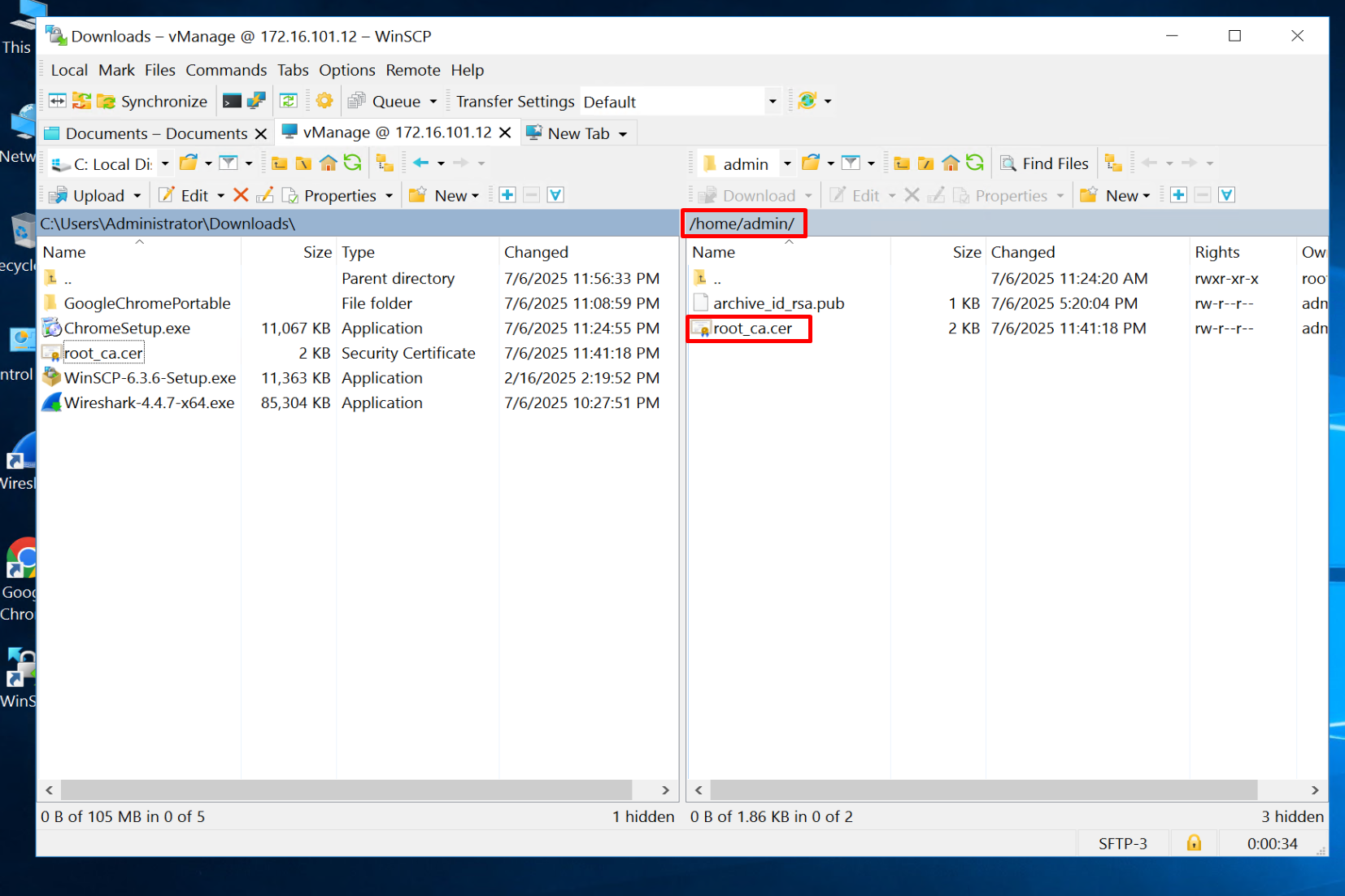
Do same for vSmart and vBond
Before adding certificate, make sure that basic system config is in place
the configuration that we configured earlier
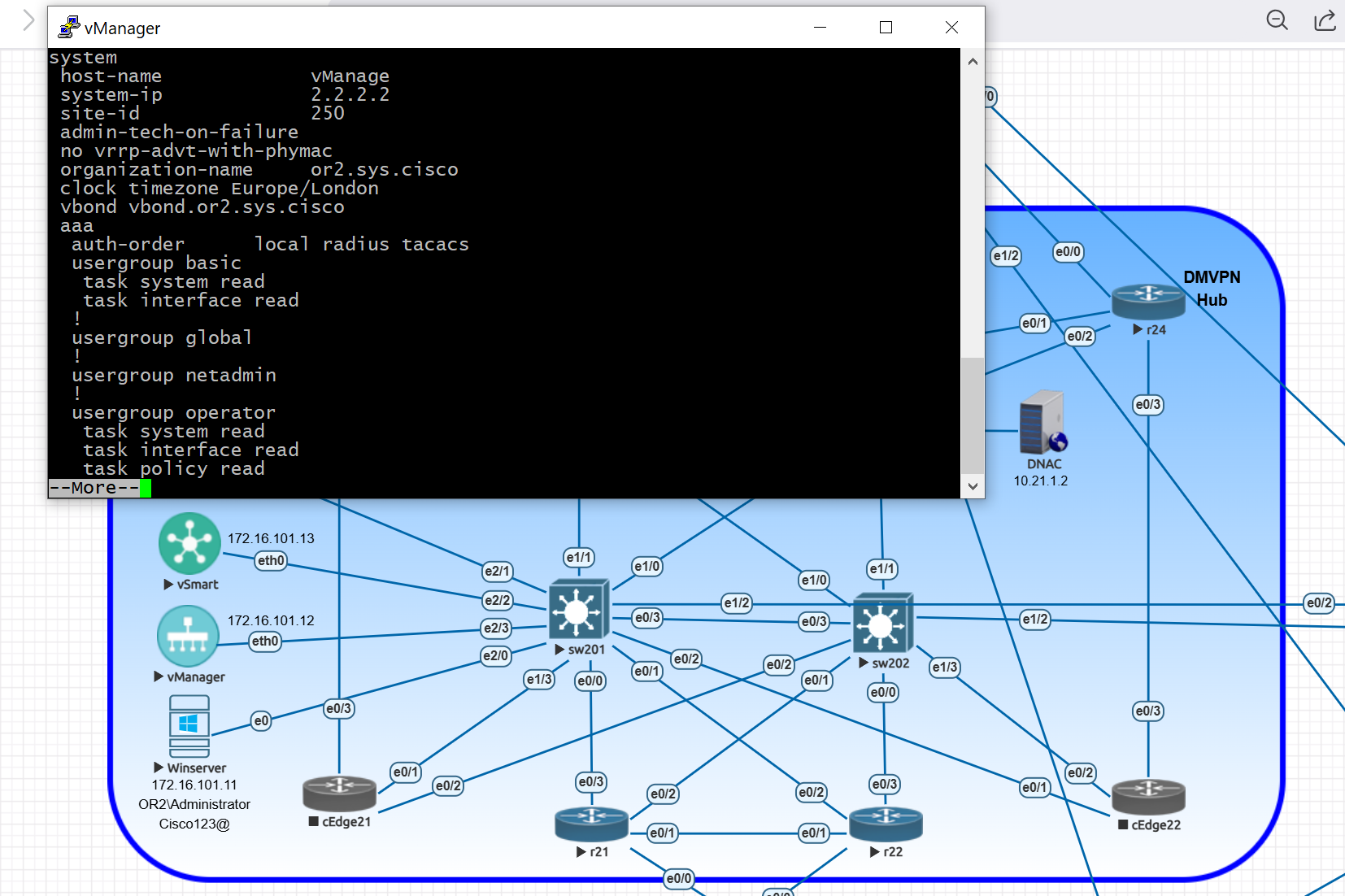
Install root CA certificate chain in Trust store of Controllers
request root-cert-chain install /home/admin/root_ca.cervManage# request root-cert-chain install /home/admin/root_ca.cer
Uploading root-ca-cert-chain via VPN 0
Copying ... /home/admin/root_ca.cer via VPN 0
Updating the root certificate chain..
Successfully installed the root certificate chainvSmart# request root-cert-chain install /home/admin/root_ca.cer
Uploading root-ca-cert-chain via VPN 0
Copying ... /home/admin/root_ca.cer via VPN 0
Updating the root certificate chain..
Successfully installed the root certificate chainvBond# request root-cert-chain install /home/admin/root_ca.cer
Uploading root-ca-cert-chain via VPN 0
Copying ... /home/admin/root_ca.cer via VPN 0
Updating the root certificate chain..
Successfully installed the root certificate chainSync the root cert chain database on vmanage
https://1.1.0.11/dataservice/system/device/sync/rootcertchain
Add controllers to vManage
Add vsmart (credential managed)
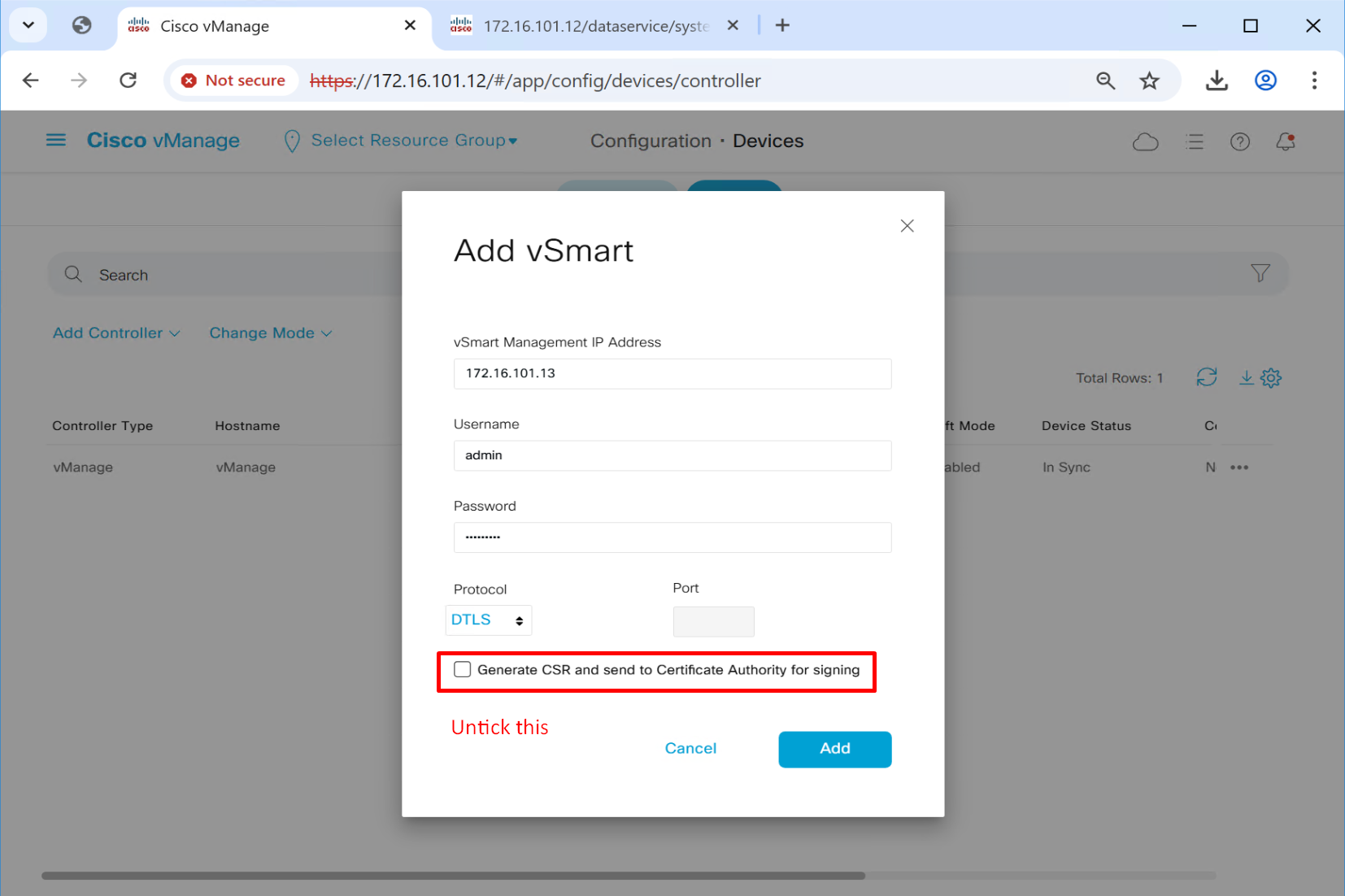
Add vbond (credential managed)
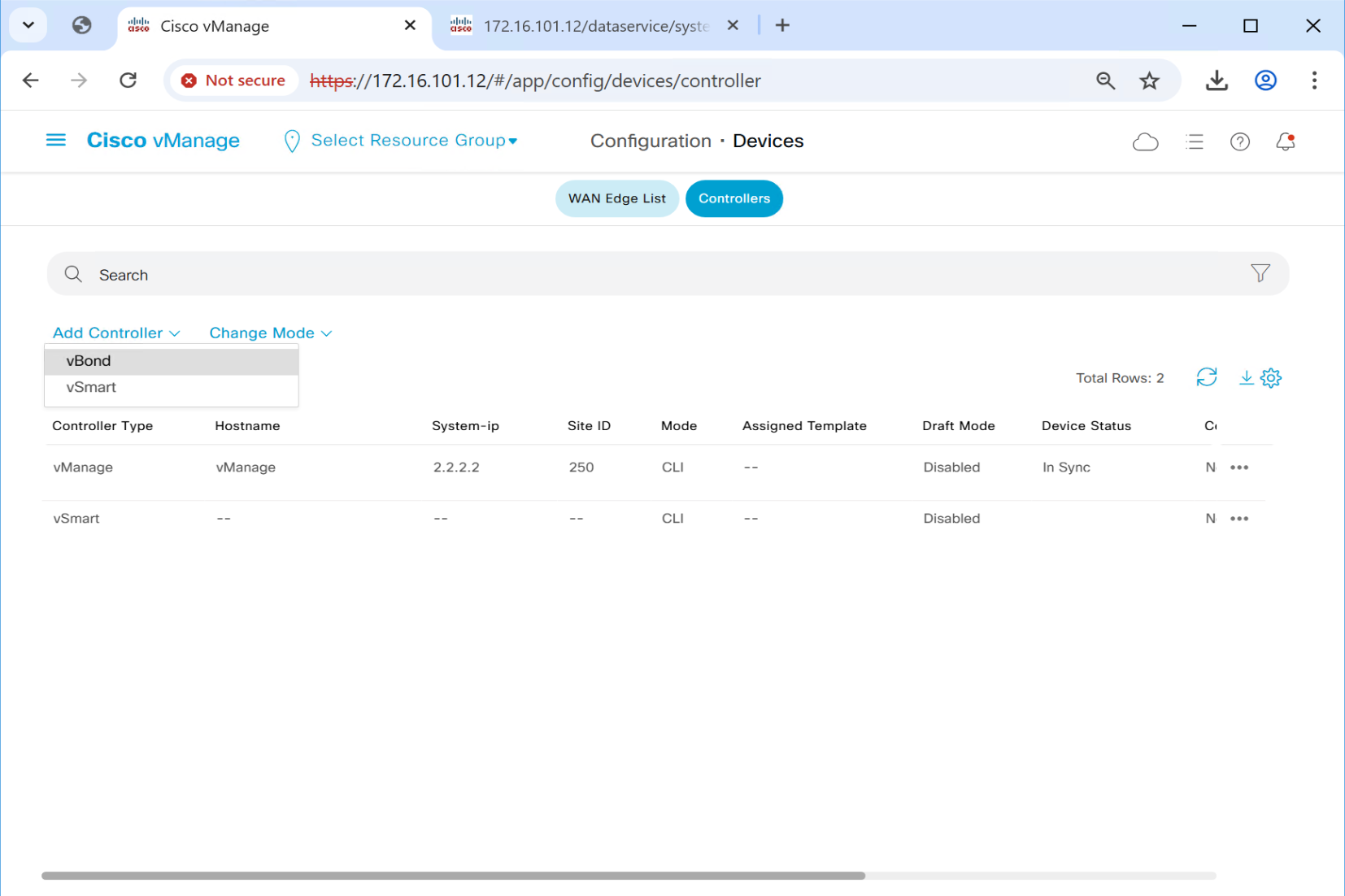
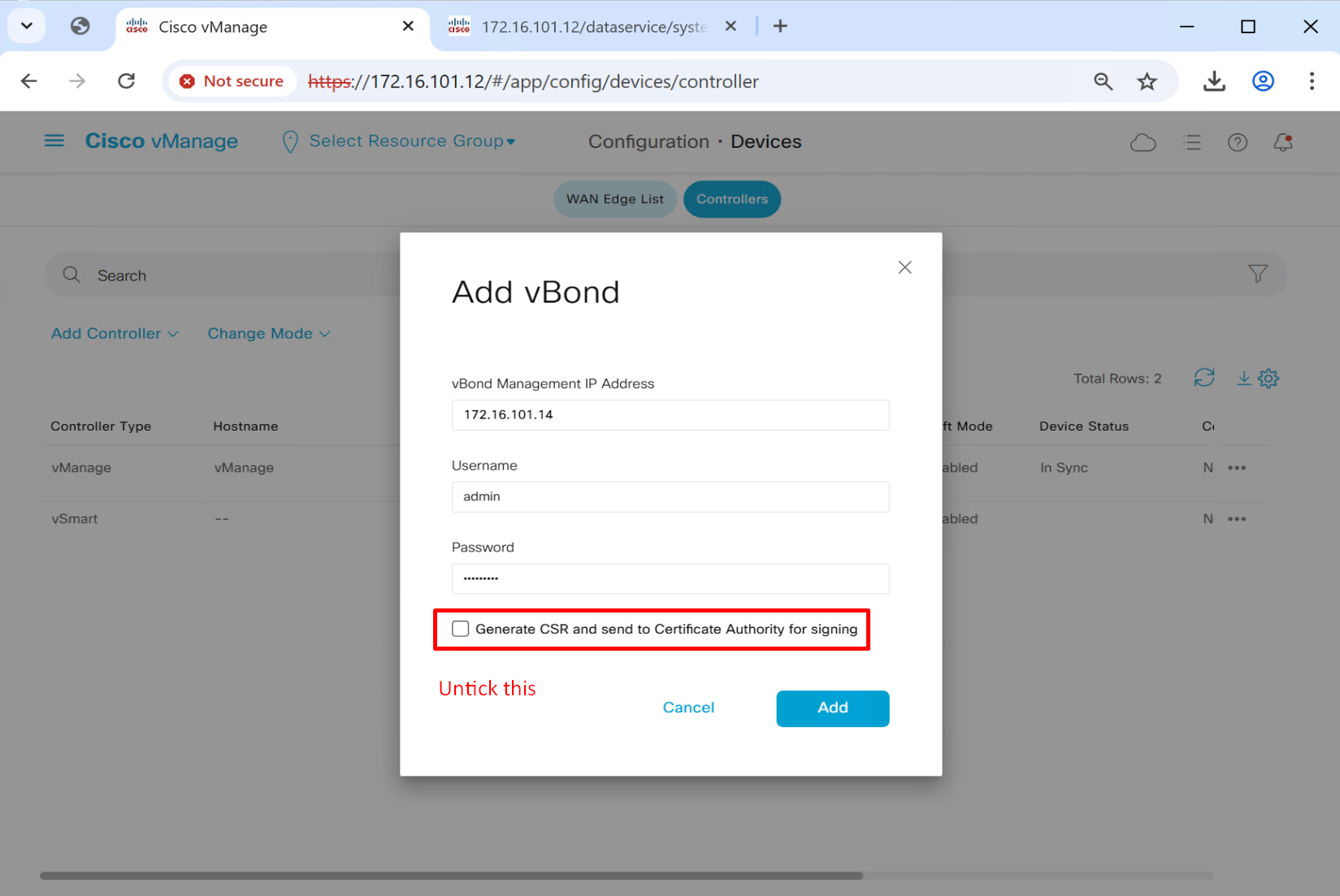
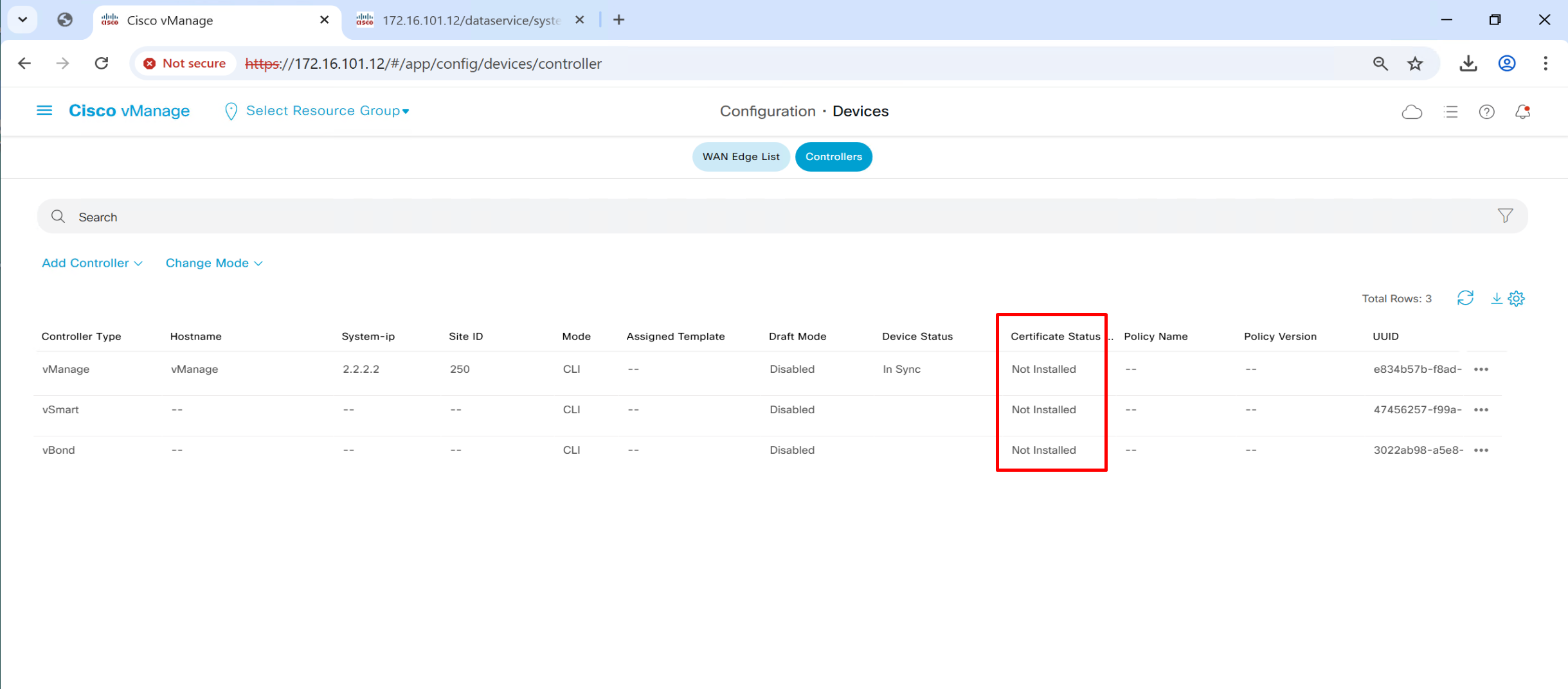
so controllers are configured but we are missing very important bit
even though we configured Org name in command line, it does not get picked up automatically, so click edit to configure it


Add Organisation Name
or2.sys.cisco

Add vBond FQDN
vbond.or.sys.cisco
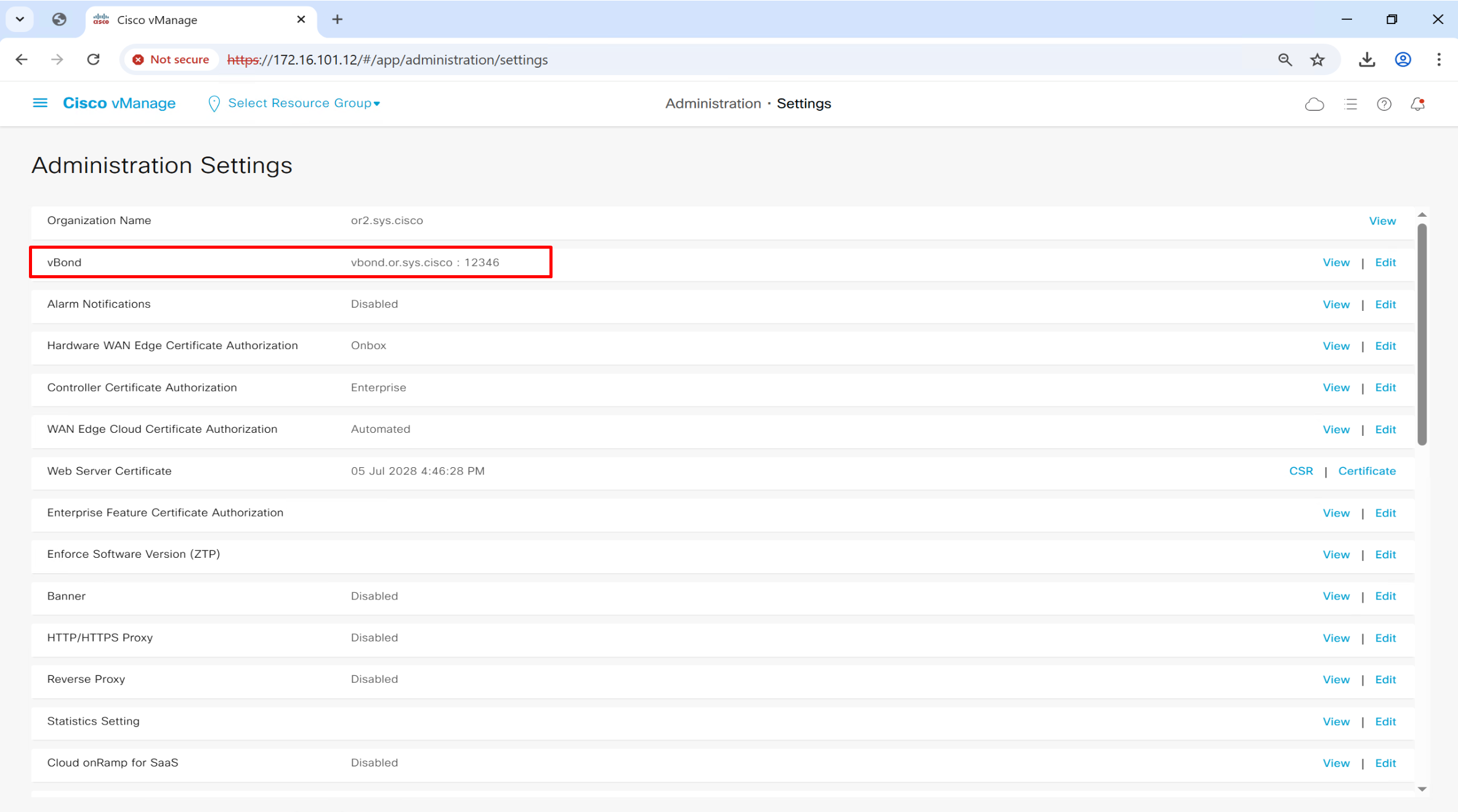
Controller Certificate Authorization mode
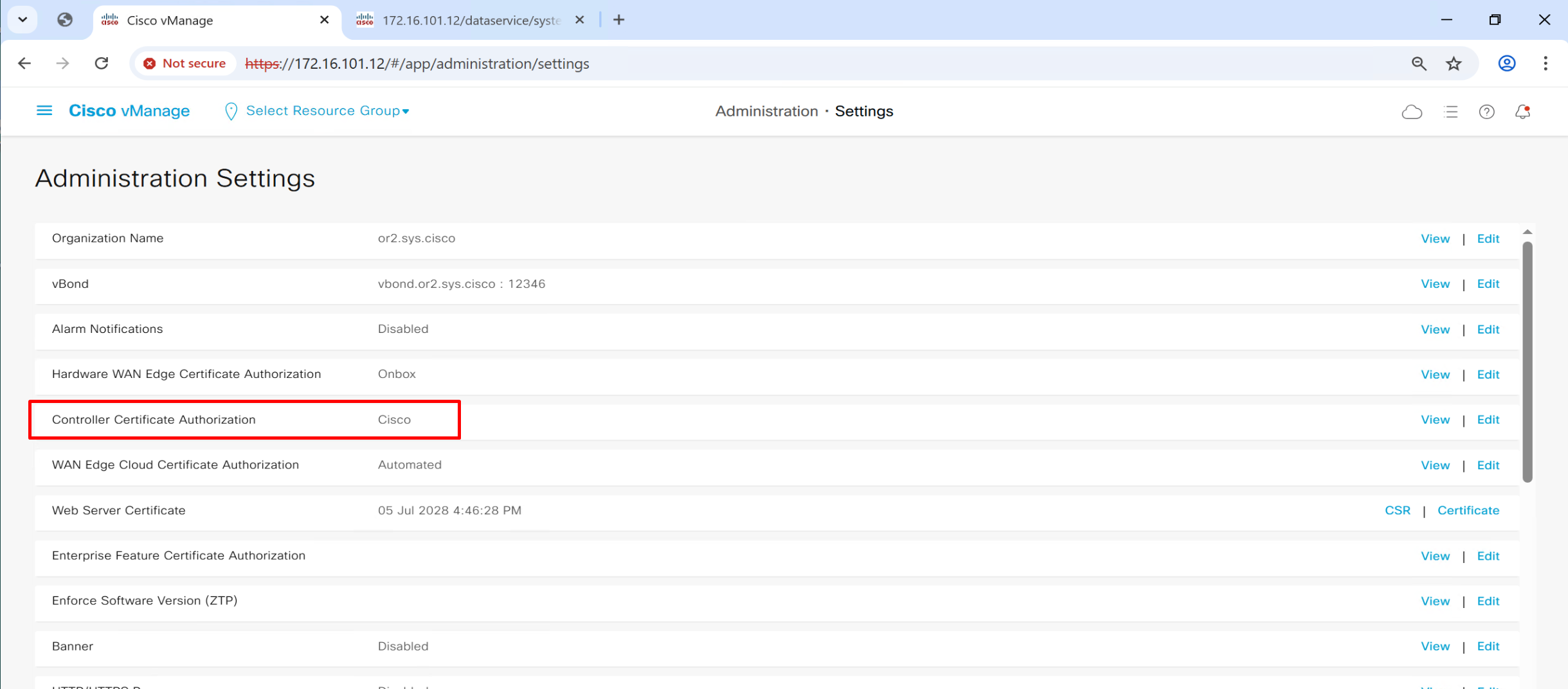
This is much simpler method as it uses Cisco’s Pre-installed Certificates

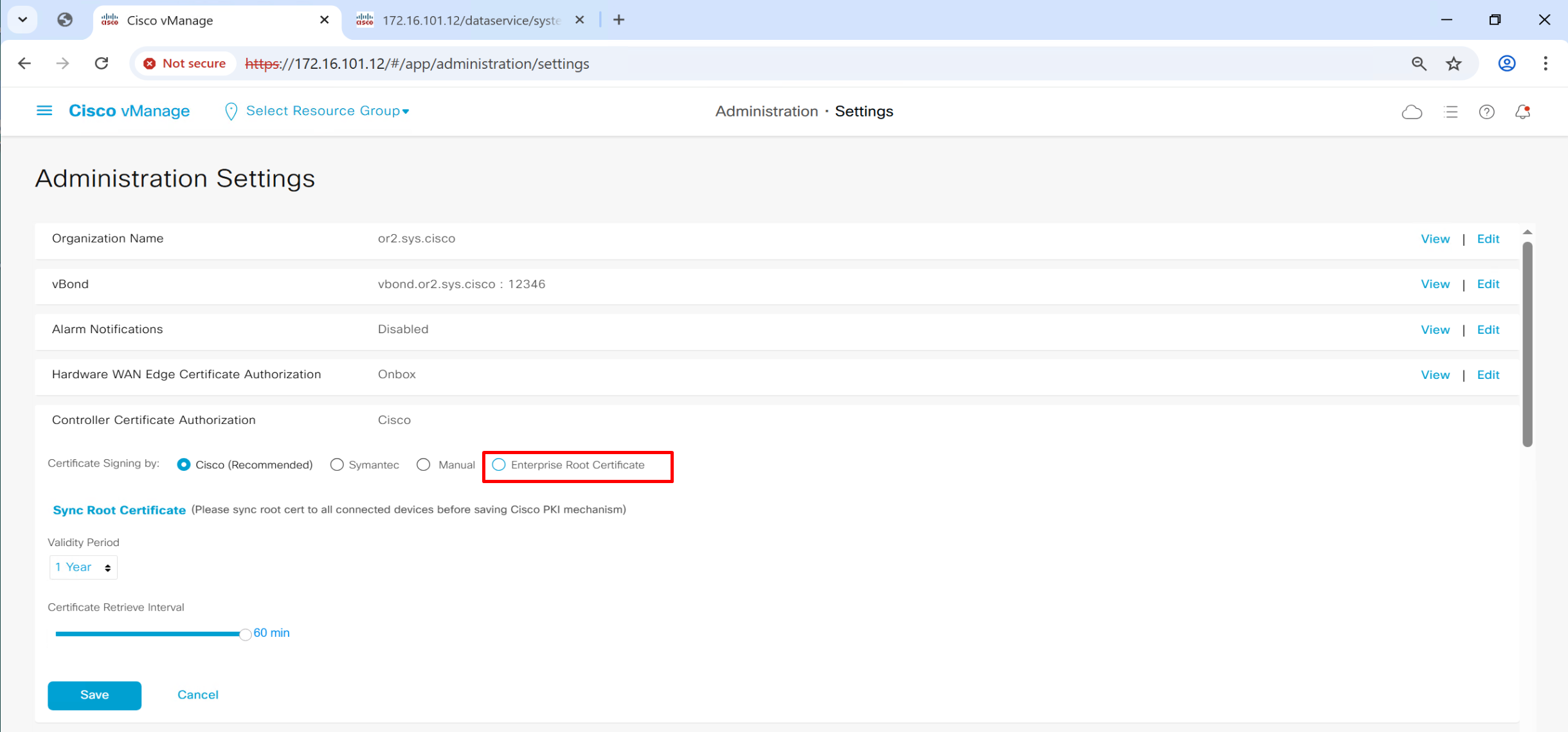
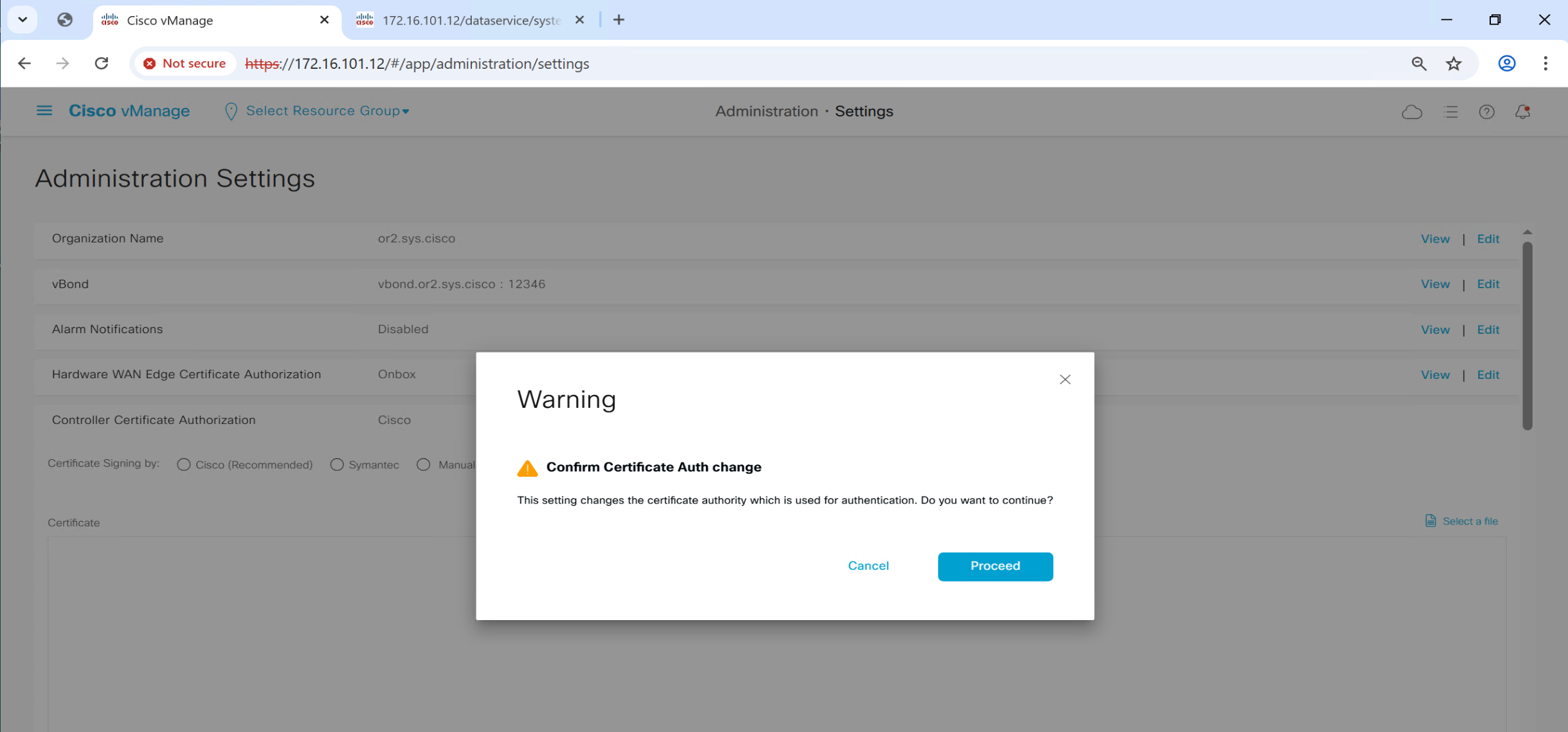
This root certificate can be same as the one added in the “trust store” earlier as this option is asking us to provide a root CA which will be used for “Authentication” for devices
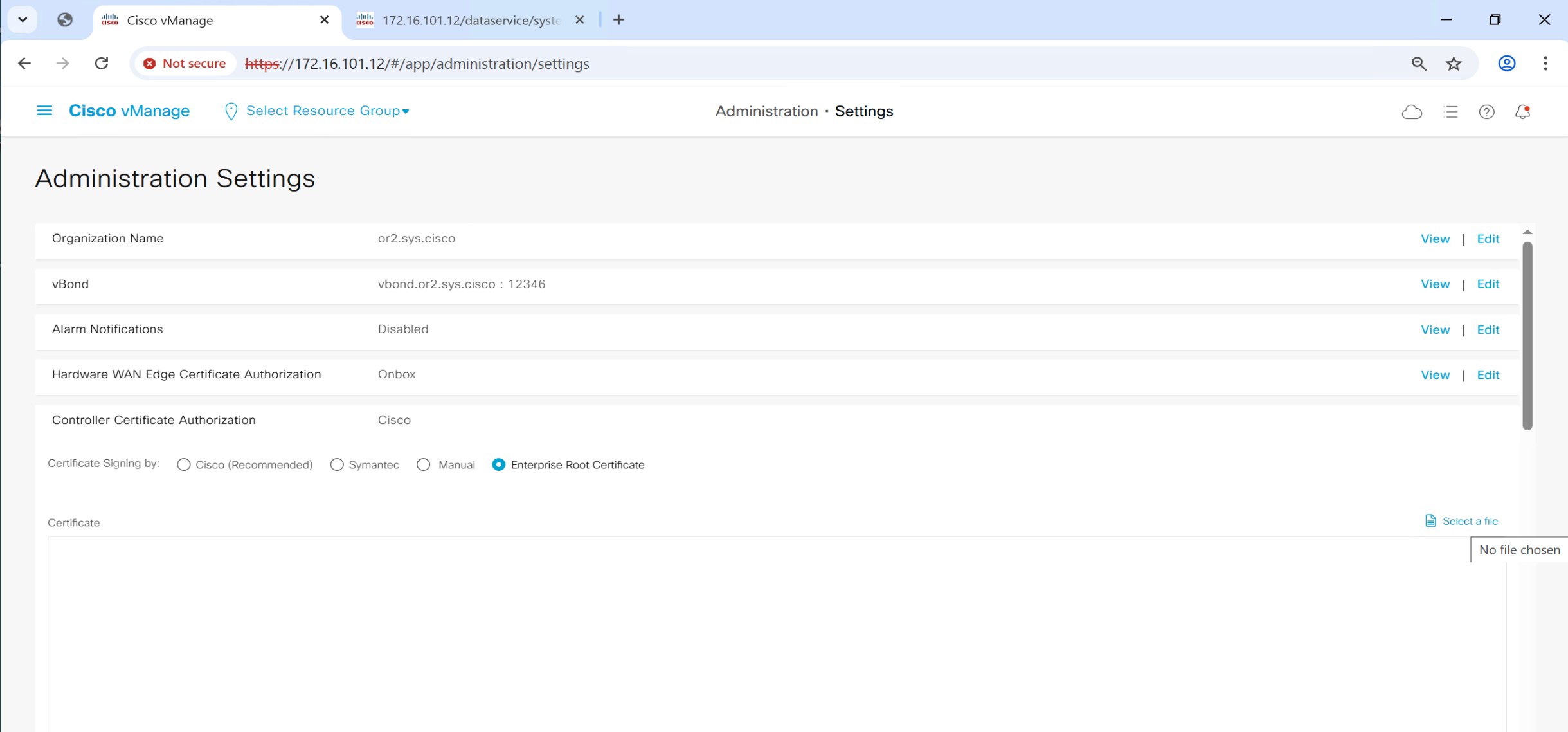
this will tell other controllers vbond and vsmart to authenticate using this certificate

Now vmanage knows about the IP addresses of the controllers like authorization or whitelisting but they are not onboarded yet, before they can be onboarded on to fabric they need certificate that is signed by CA and this will be done using each controller CSR
Install certificates on vSmart and vBond through vManage
Generate CSR per controller from vmanage

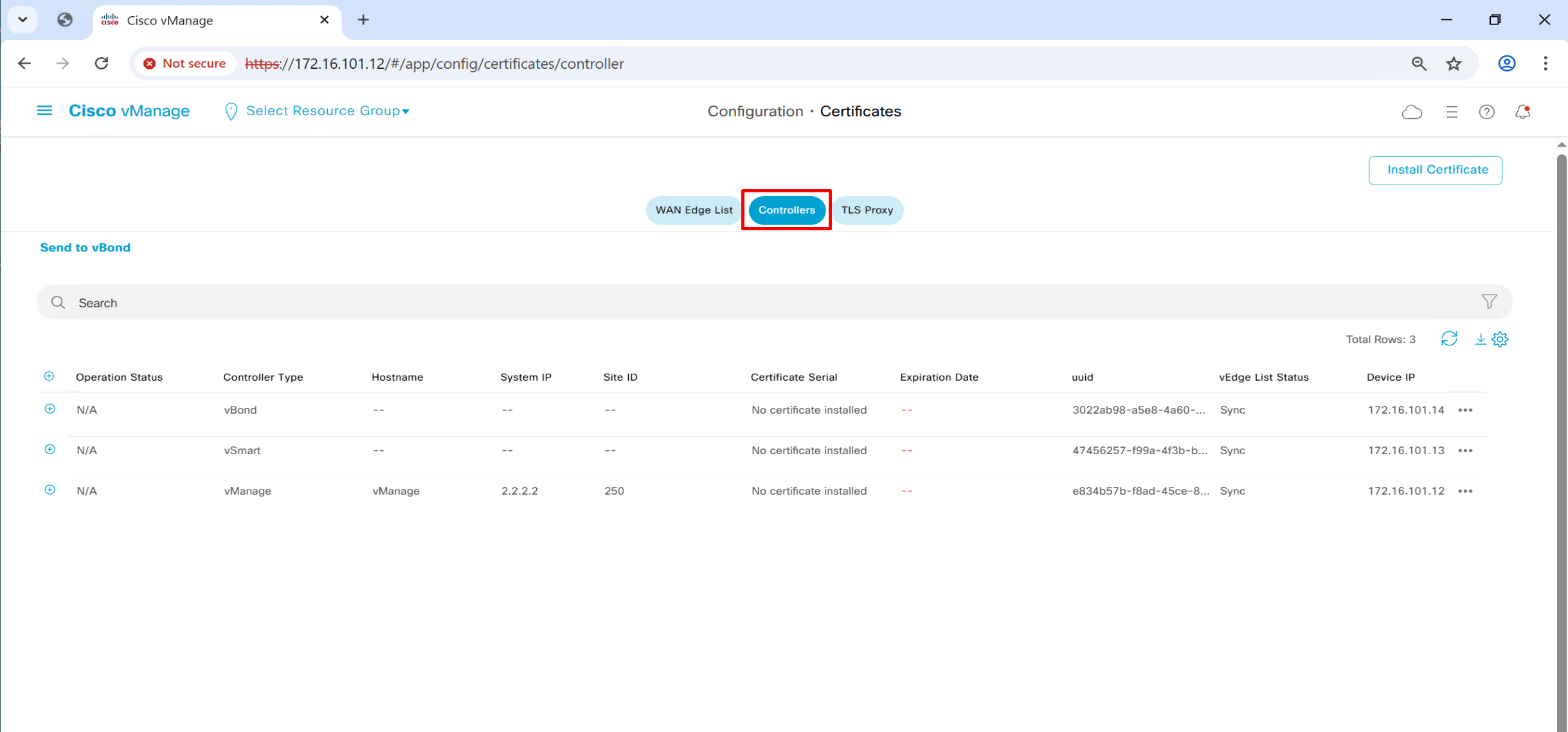
Click on vManage three dots > generate CSR
even vManage itself needs a certificate
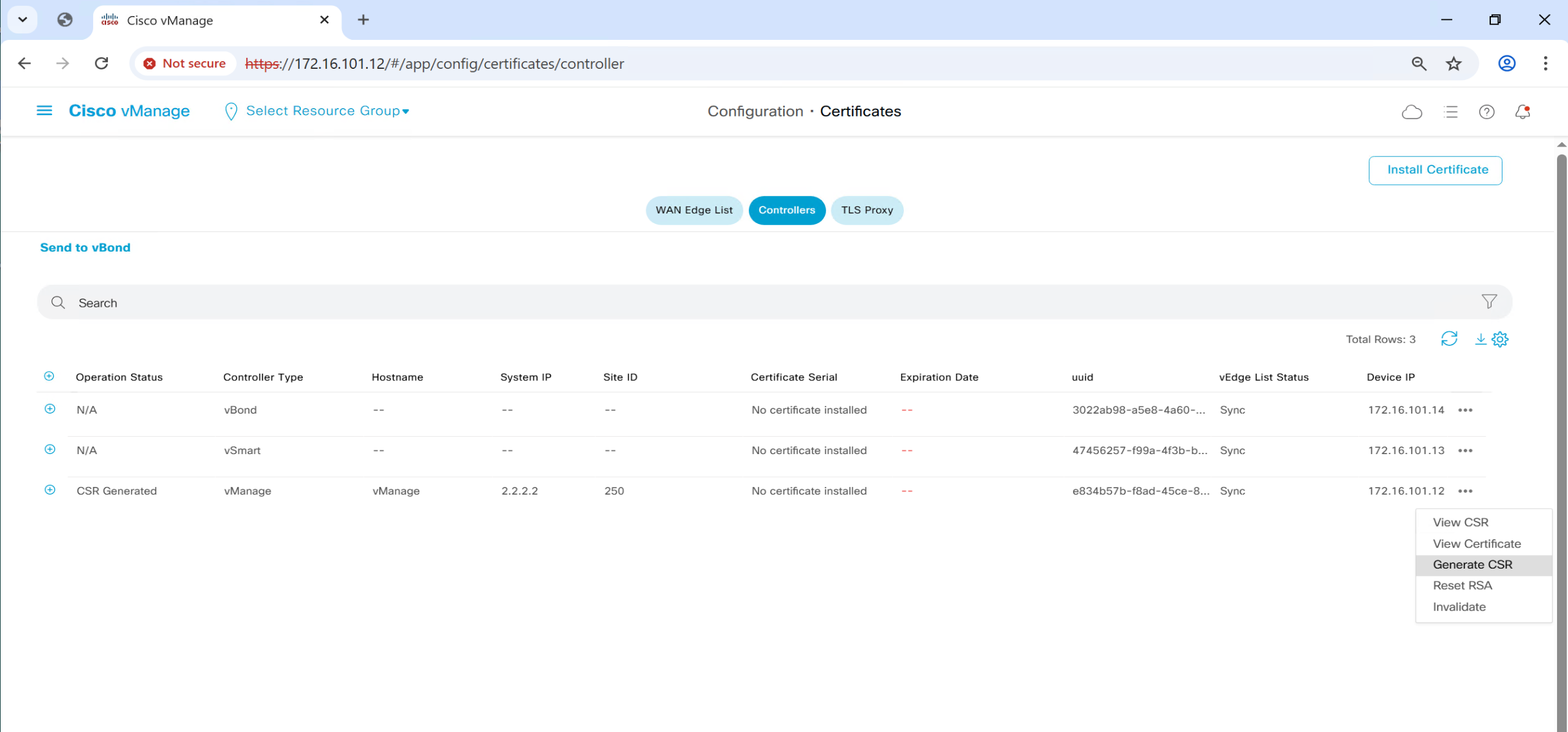
CSR for vSmart and vBond is generated and installed on vSmart and vBond
and it is then signed by our windows server CA, so when this cert is presented to vmanage, it can trust the presented cert
and once certificates are “issued” by vmanage to vbond and vsmart,
a certificate based mutual authentication will take place before controllers are added to fabric in vmanage

Click on download
same process is required for vmanage as well because vmanage also needs to issue certificate to itself
Copy and paste it to certsrv
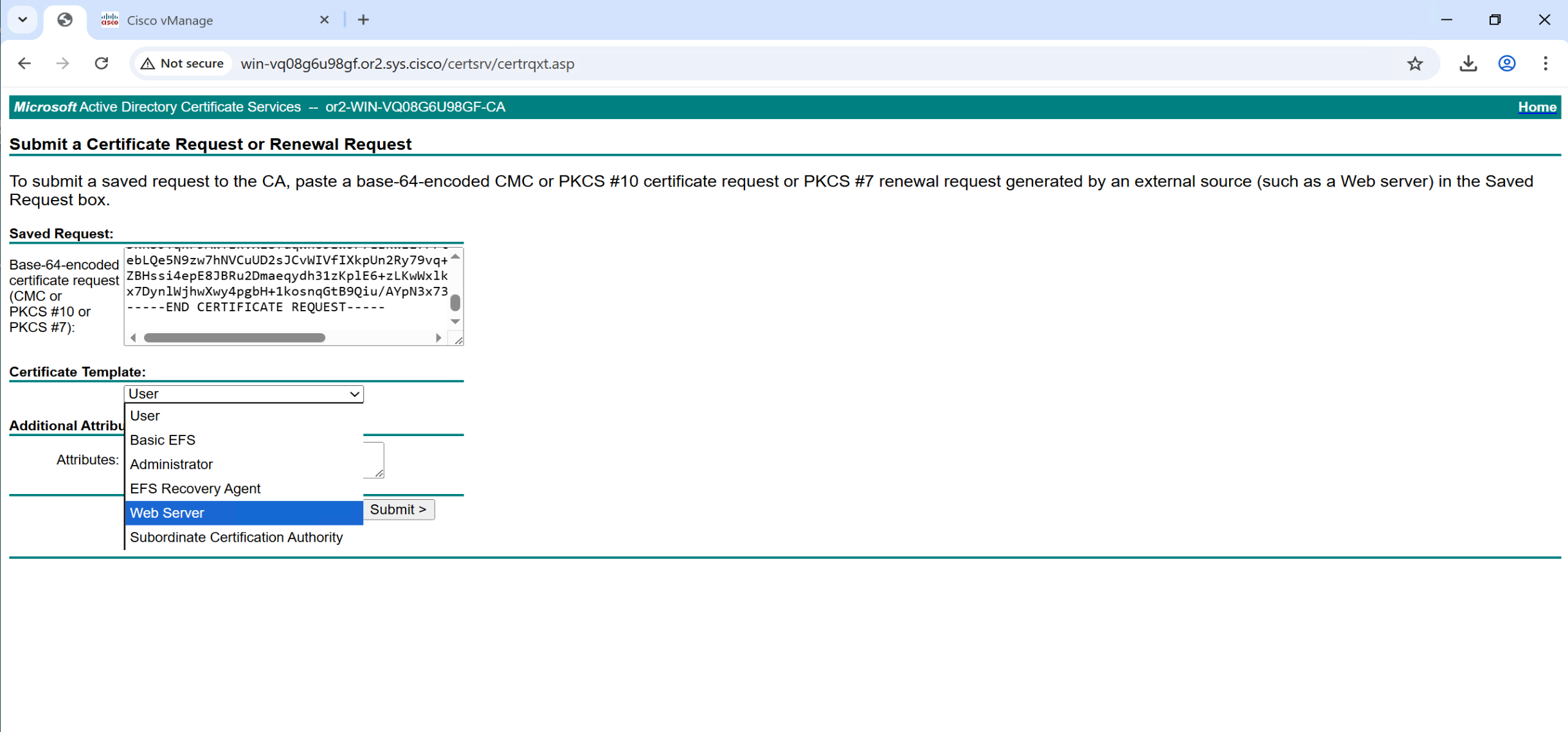

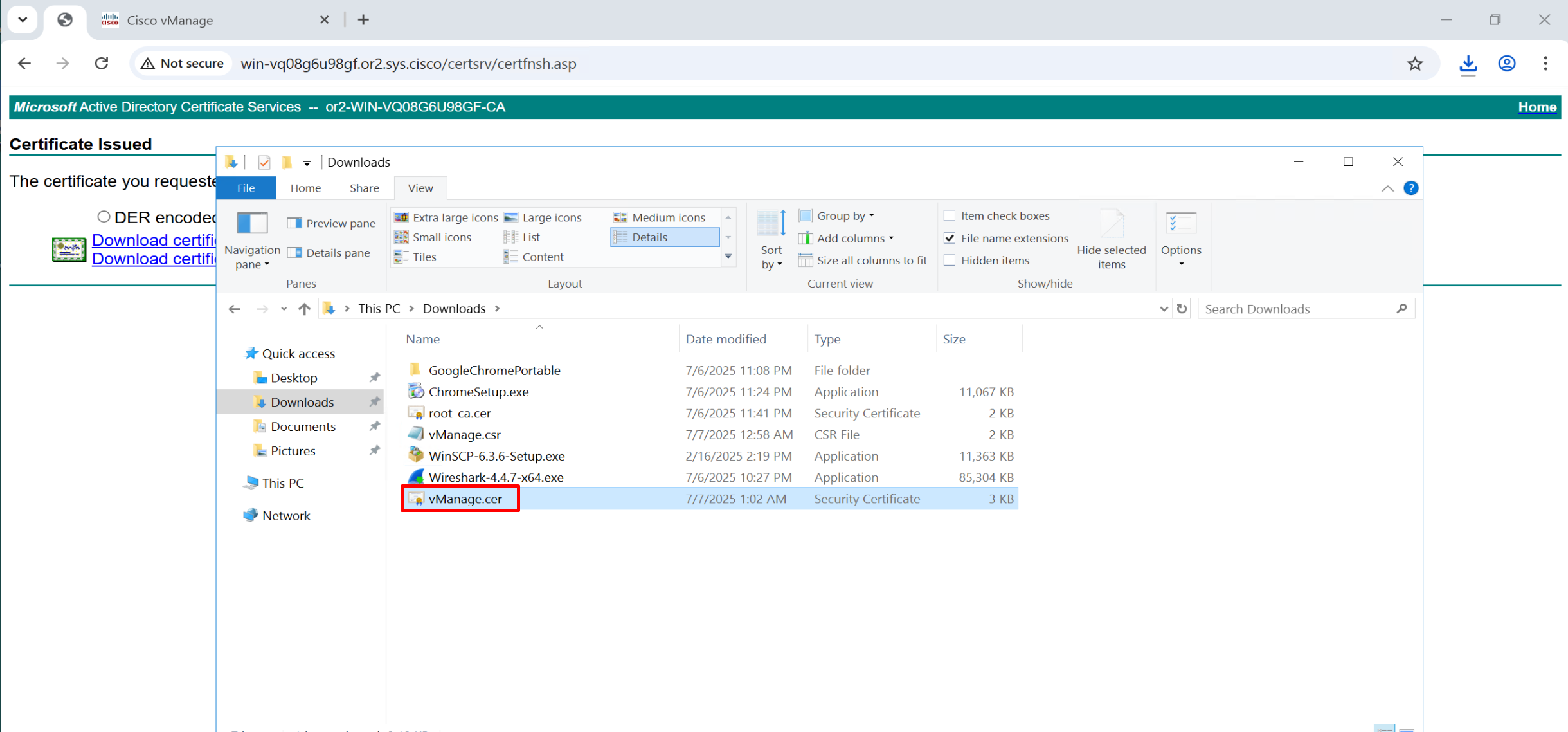
Repeat same process of CSR generate for vsmart and vbond as well
Install Certificates
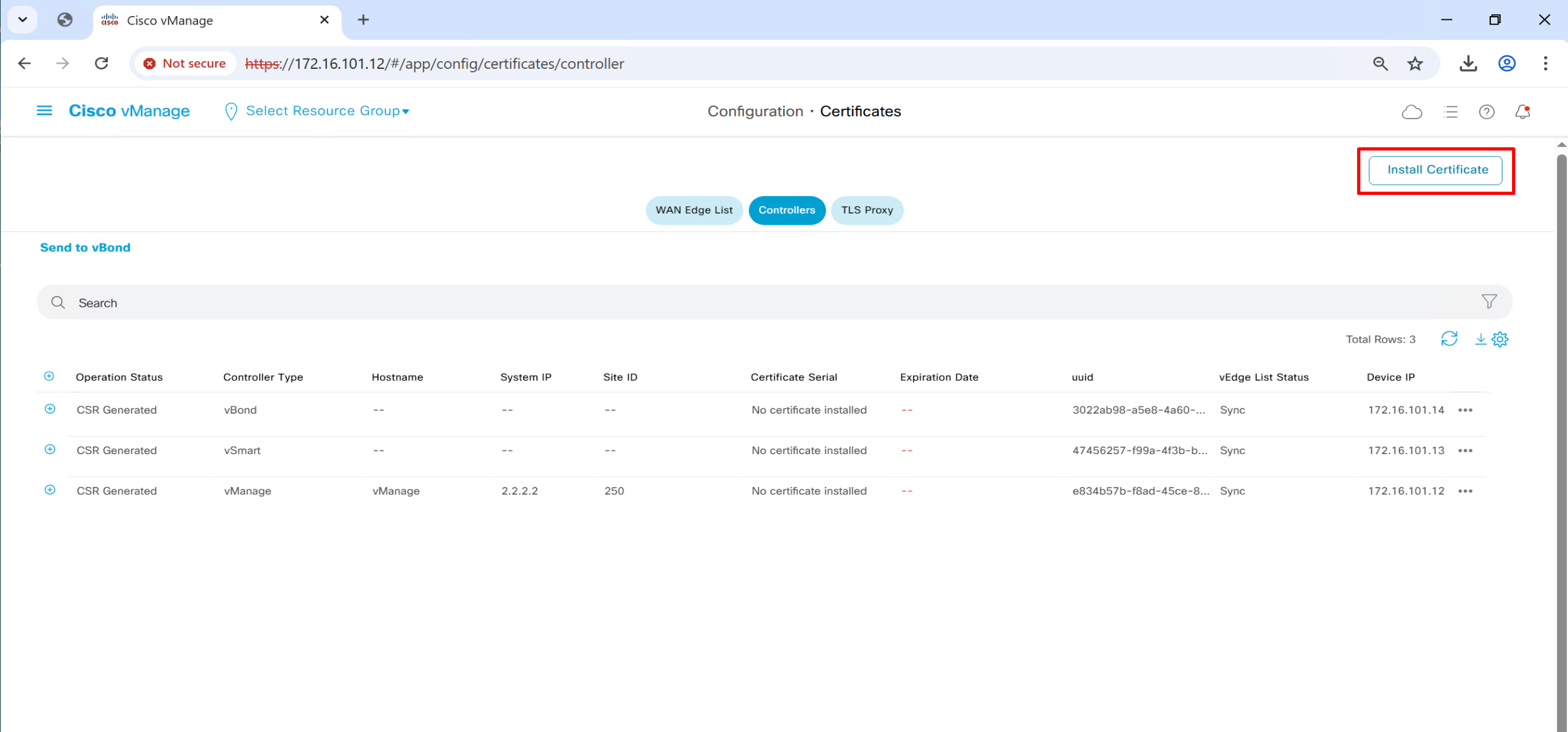
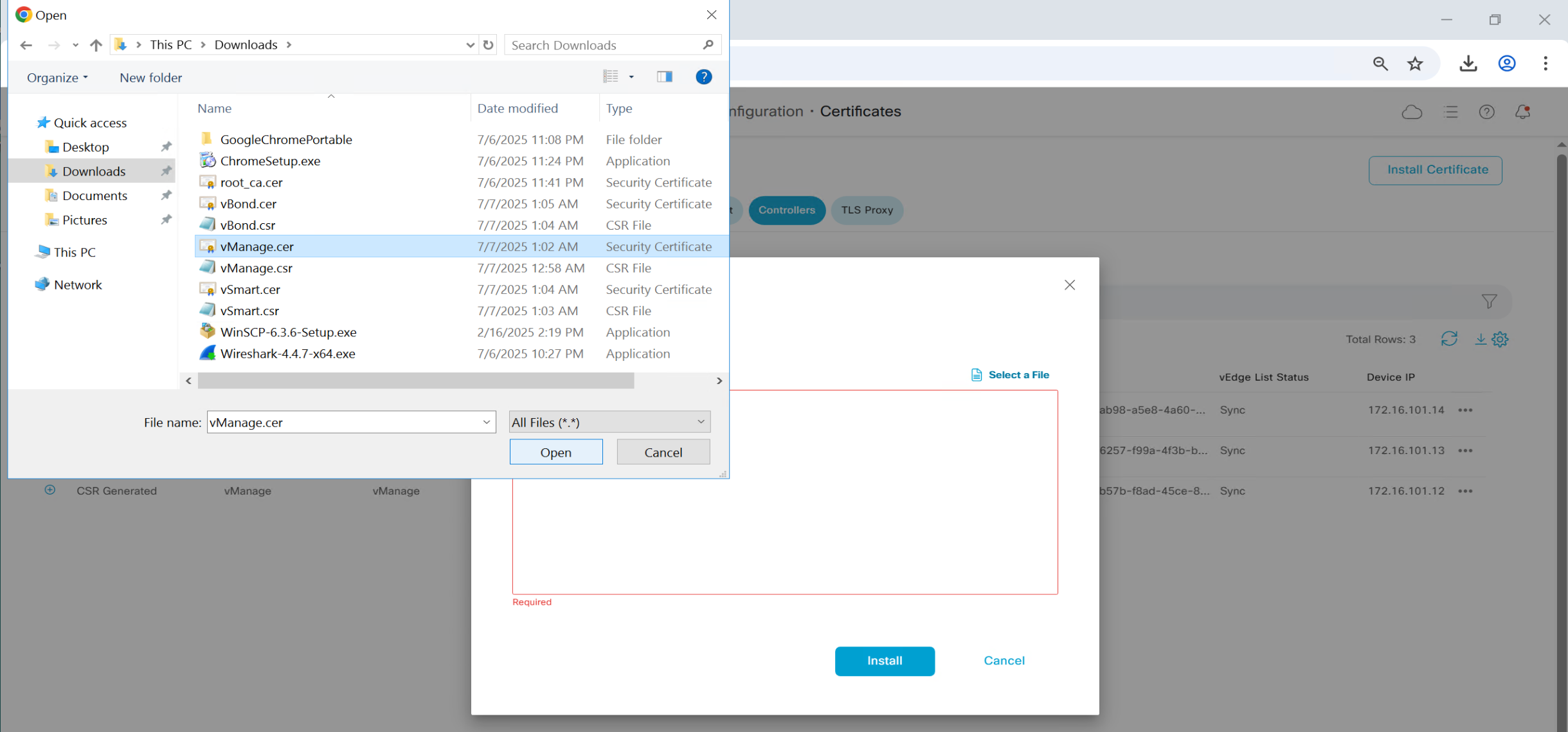



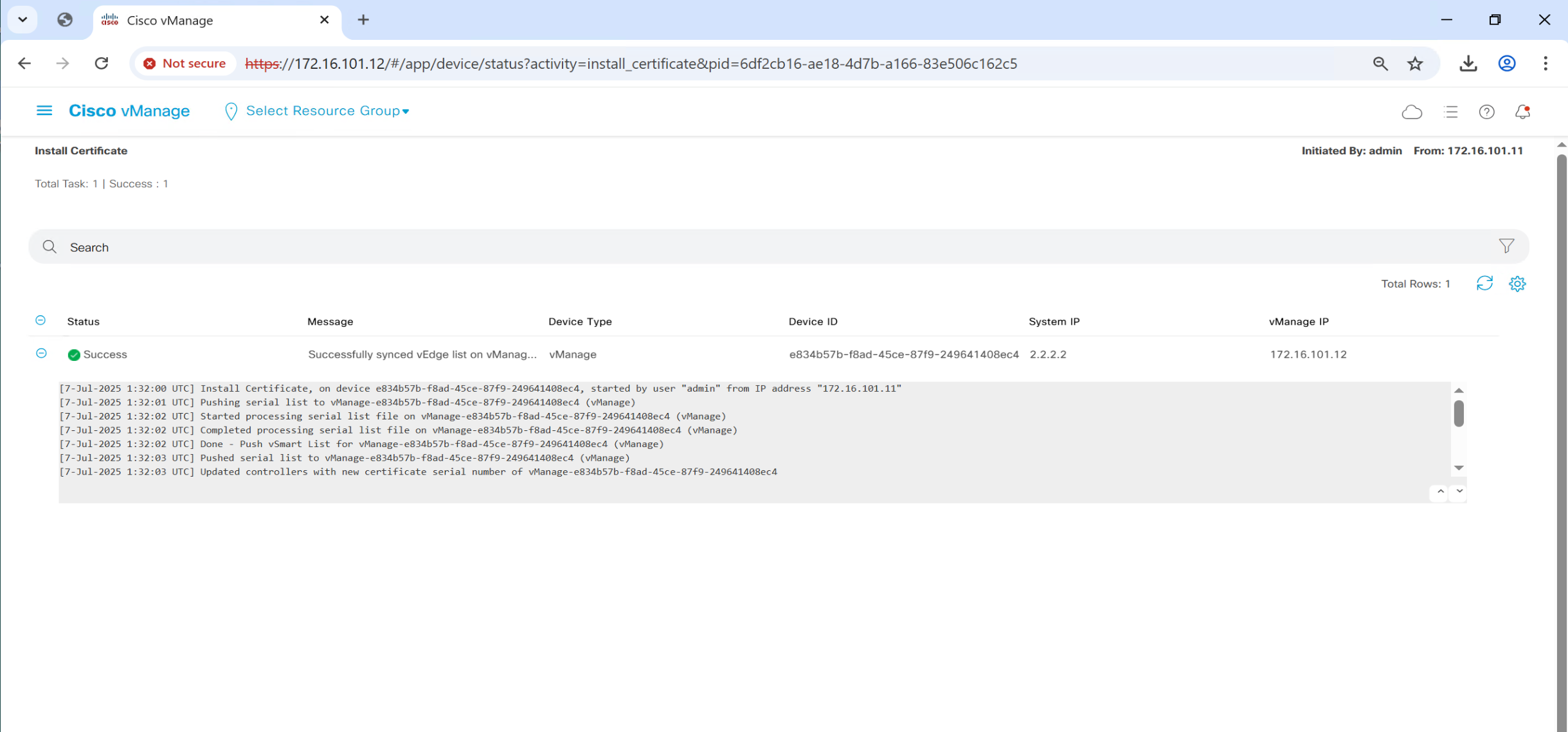

Follow same steps to install certificates on other controllers

in above screenshot we can see that “site ID” is still missing and “System IP” also
This has to do with tunnel interface, as the “site ID and System IP” are exchanged over fabric
so we need to bring up the tunnel interface with allowed services which are safe over WAN or internet such as HTTP and icmp etc, Allowed service are both inbound and outbound
such as NTP will be outbound but SSH will be inbound
vManage tunnel interface
vpn 0
interface eth0
tunnel-interface ! DTLS tunnel
allow-service all ! only use all in lab for prod restrict services
allow-service sshd
allow-service ntp
allow-service dns
allow-service httpsvSmart tunnel interface
vpn 0
interface eth0
tunnel-interface ! DTLS tunnel
allow-service all ! only use all in lab for prod restrict services
allow-service sshd
allow-service ntp
allow-service dns
allow-service httpsvBond tunnel interface
vpn 0
interface ge0/0
tunnel-interface ! DTLS tunnel
encapsulation ipsec ! this is also required in case of vbond
allow-service allafter bringing up the tunnel interface we can see that system IP, hostname and site ID are present
we have successfully onboarded the controllers
vManage commands
show runn
conf t
system
show configuration
commit
show certificate root-ca-cert ! to see installed root-ca cert
show ntp associations
show run vpn 0
show control local-properties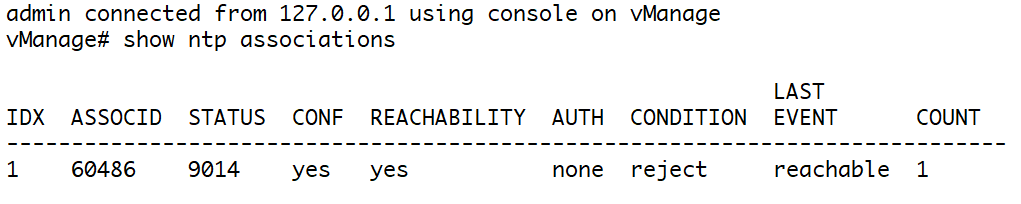
vbond commands
show orchestrator connections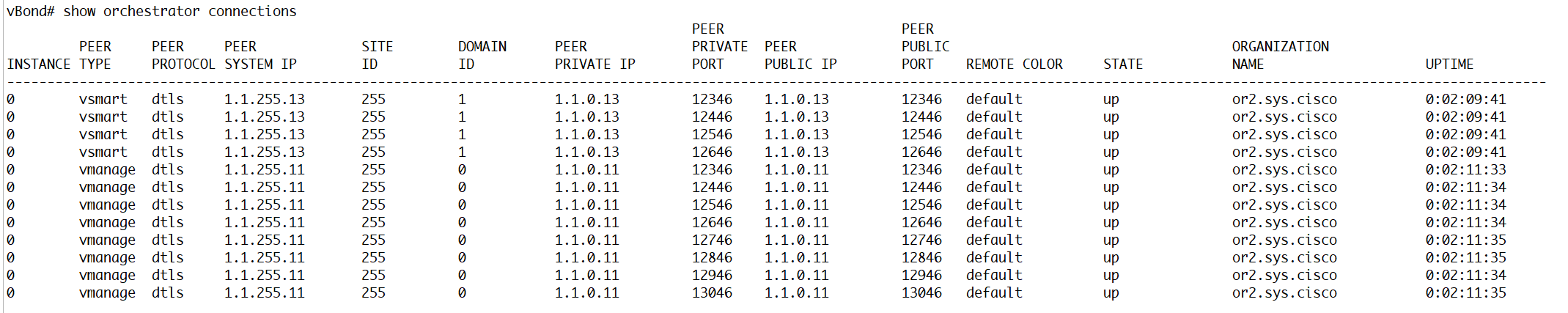
one DTLS connection per vmanage CPU core with vmanage
show orchestrator valid-vsmarts
first one is vmanage and other one is vsmart
vsmart commands
show control connections 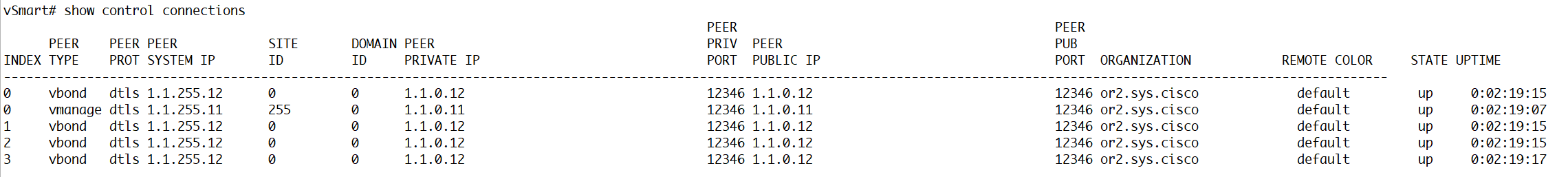
Web certificate for vmanage
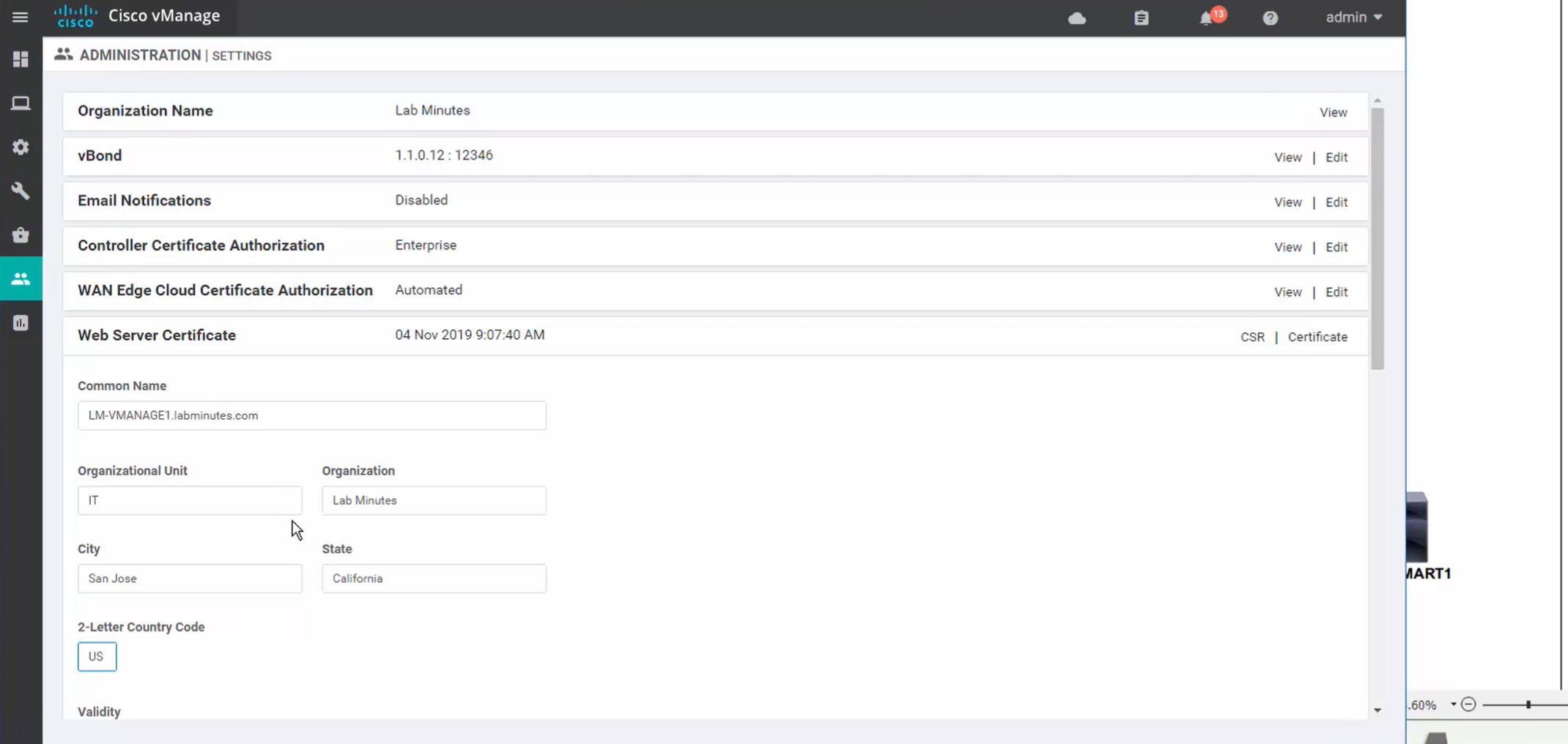
We will get the CSR

it needs to be signed by CA


for certificate to take effect, we need to reboot the vmanage
under maintenance, device reboot

Edge device onboarding
Virtual cEdge devices themselves do not have any chassis numbers,
in order to get those chassis number we need to go to software.cisco.com, on the portal we need to define the vbond IP (best to define FQDN for flexibility in serial file) and Org name.
There is a different process for hardware edge devices,
For Virtual devices we specify how many virtual devices we want to generate chassis numbers for.
If we have hardware routers then we have to enter the serial numbers, PID and certificate serial number from routers into the portal
Extracted serialFile_new.viptela
The file appears to be in a compressed binary format, starting with the byte sequence \x1f\x8b\x08, which is the standard signature for a GZIP-compressed file.
I’ll attempt to decompress the file and then read its contents. Let’s proceed.
The decompressed file starts with the text viptela_serial_file, which suggests it is a Viptela serial file (used in SD-WAN deployments). However, the rest of the content contains what looks like binary padding and possibly a tar archive header, indicated by terms like ustar.
This means the GZIP file likely contains a tar archive, not a plain text file. Let me try extracting the tar contents and see what files it contains.
The archive contains the following files:
viptela_serial_file– likely the main serial/license file.viptela_serial_file.sig– likely a digital signature file to verify authenticity.cisco_cert.cer– a Cisco certificate, probably used for validation.
I’ll extract and display the contents of the main viptela_serial_file first.
The viptela_serial_file contains JSON data representing serial information for Cisco SD-WAN devices. Here’s a summary of what’s inside:
✅ Key Information Extracted:
- Version: 1.1
- Organization:
or2.sys.cisco
- Organization:
- Overlay Network:
SD-WAN-3 - 388033 - vBond Controller:
vbond.or.sys.cisco(DTLS port 12346) - Timestamp: 2022-02-25 00:06:49
✅ Chassis & Serial Numbers:
The file lists multiple devices, each with:
- Chassis ID (example:
4567A82E-54D1-FA17-E1A4-302781B96194) - SKU: (e.g.,
VEDGE-CLOUD-DNA,C8000V,CSR1KV) - HWPID: Hardware Product ID
- Serial Number: matches the chassis ID in each case
- No SUDI (Secure Unique Device Identifier) certificates included (fields are empty).
Create new DNS zone
Since the .viptella serial file contains org name as or2.sys.cisco but it vbond profile has vbond FQDN as vbond.or.sys.cisco, we will create another DNS zone
Right-click on “Forward Lookup Zones” (or Reverse Lookup Zones if needed) ➔ New Zone…
In the New Zone Wizard:
- Select Primary zone (if this is the main copy).
- Choose whether to store the zone in Active Directory (recommended).
- Select the replication scope – all DNS servers in the forest.
- Enter your zone name or.sys.cisco
- Choose how to handle dynamic updates – secure and non-secure.
- Complete the wizard.

Generate .viptela serial file
These devices PID and serial numbers will be empty when you first create Smart account and virtual account, once have been assigned chassis numbers and associated to the org show up as green and “provisioned”
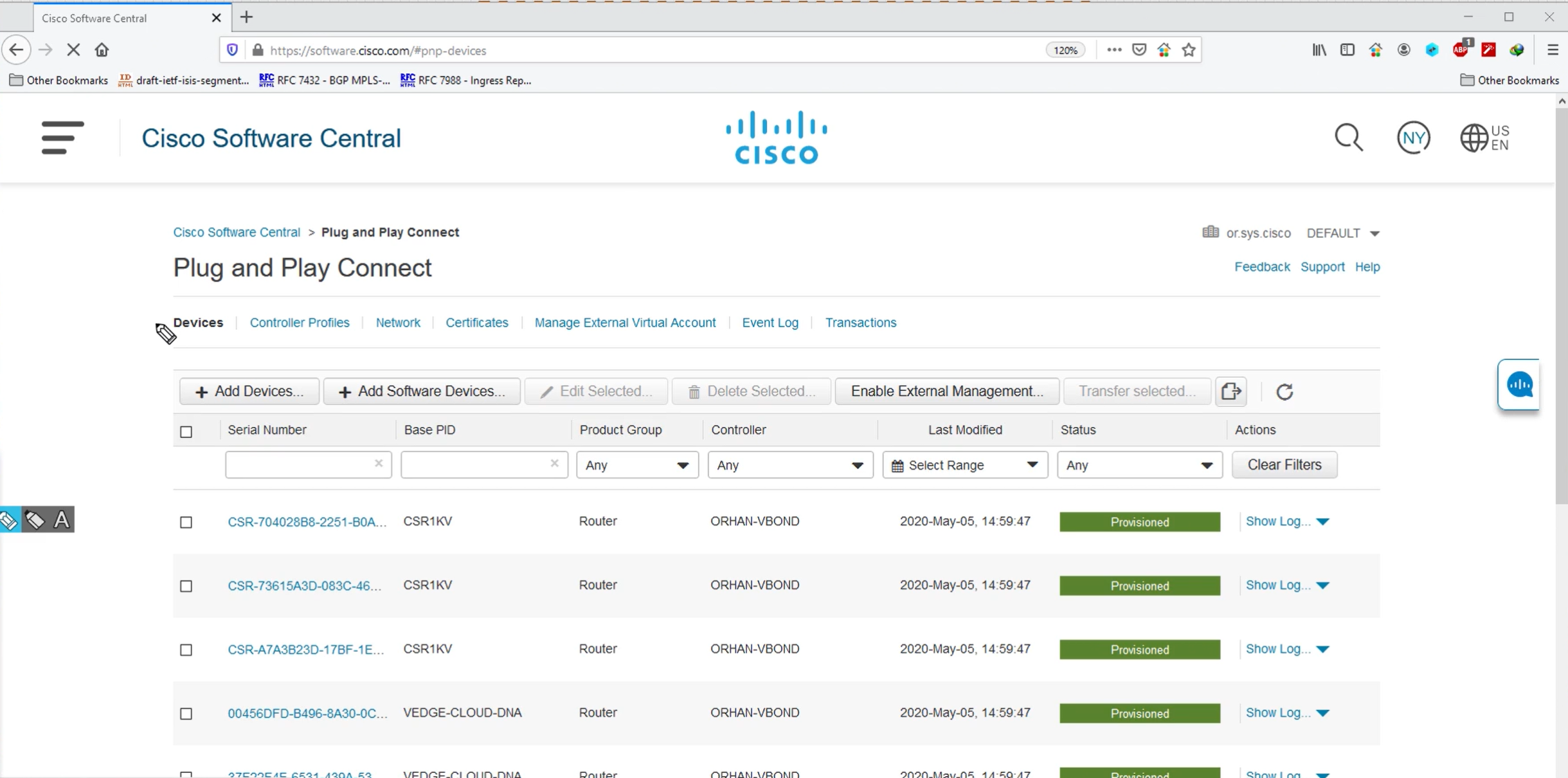
This section is where we define the vBond info with FQDN or IP and Org info
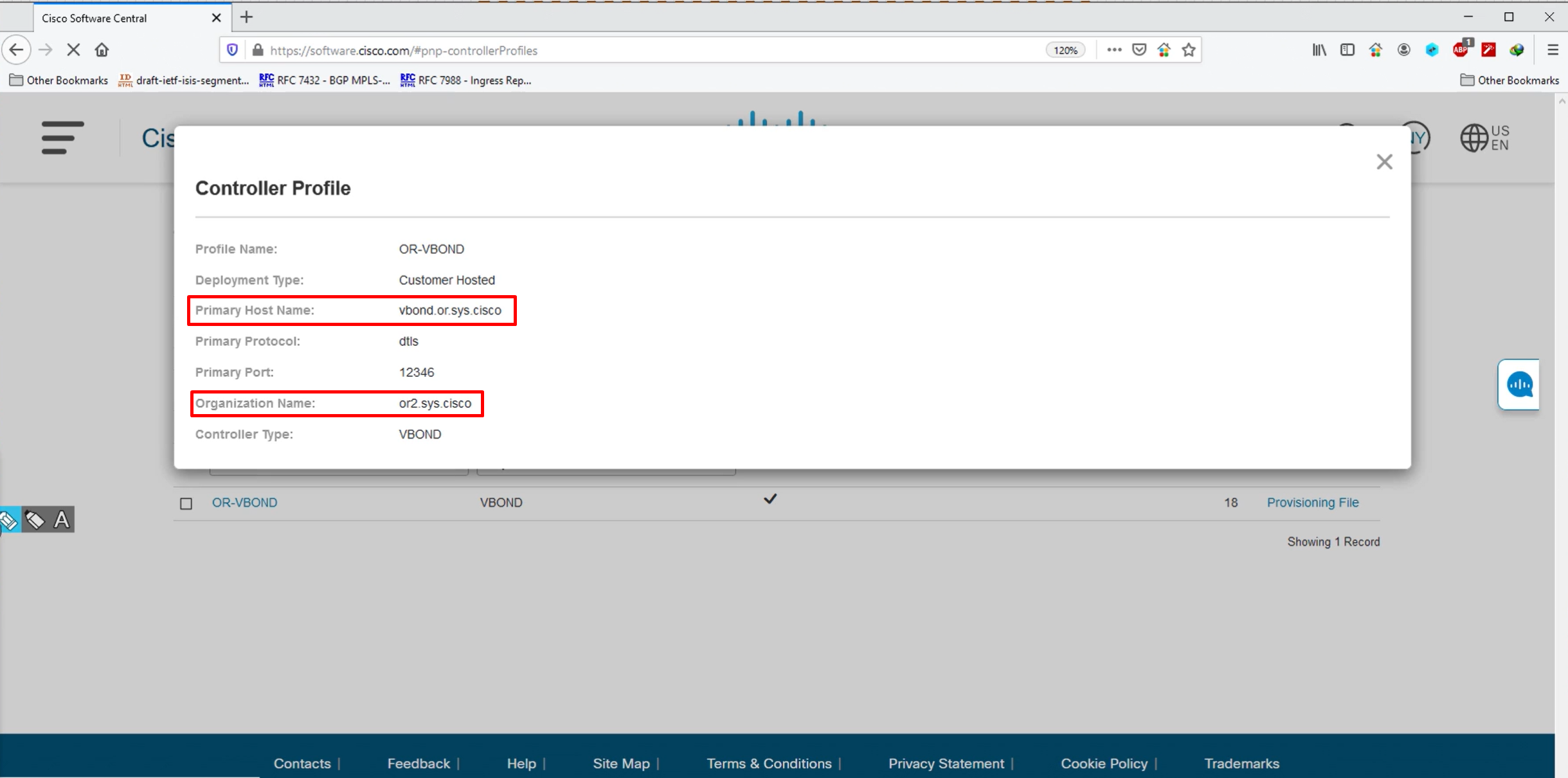
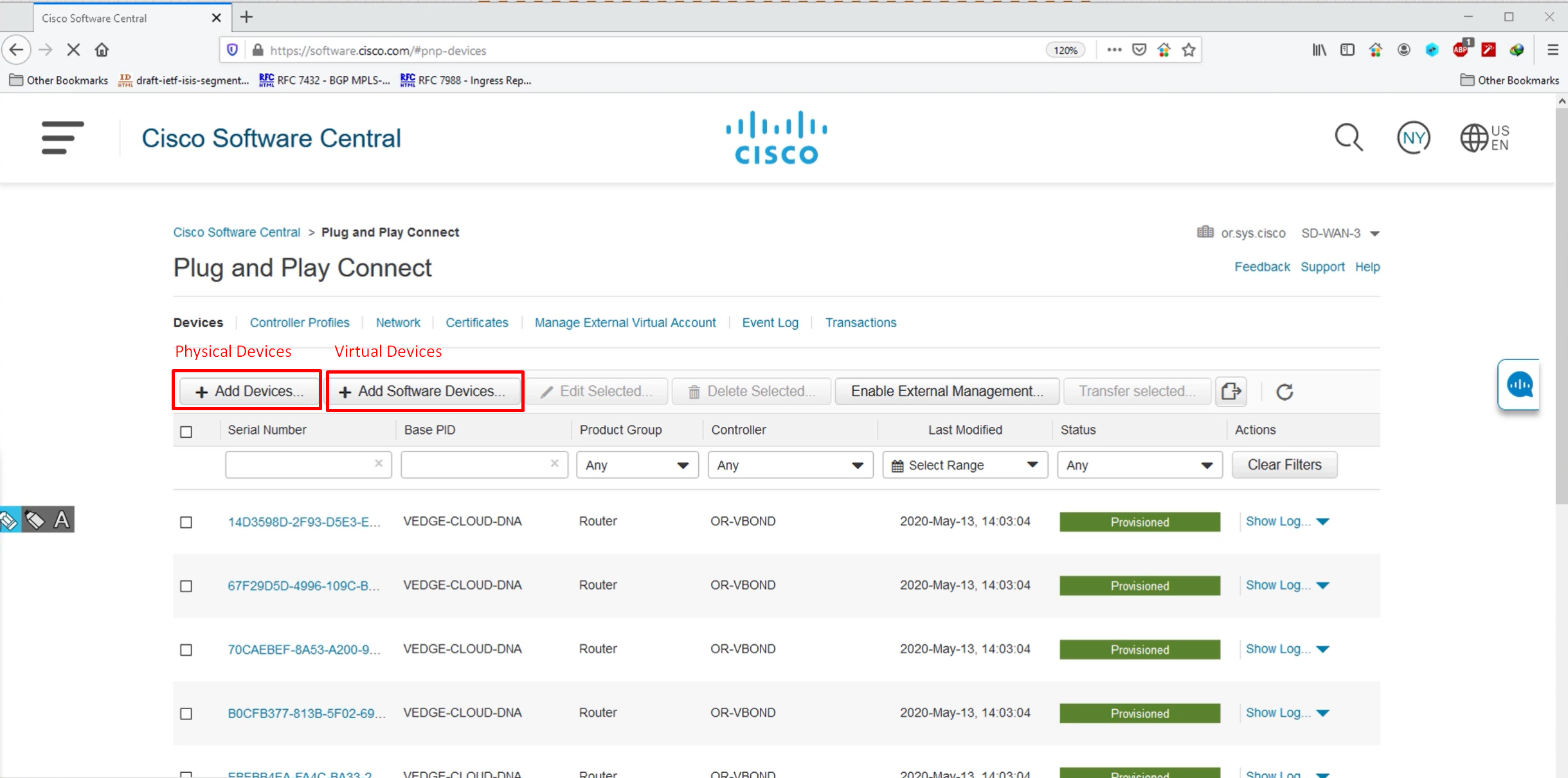

You define the PID of the device, quantity of devices and the vbond profile – this allowance will be added to our .viptela serial file


After submitting this wait for devices to be provisioned status

once all devices are provisioned, click on Controller profiles

Select the controller version

Upload .viptela serial file
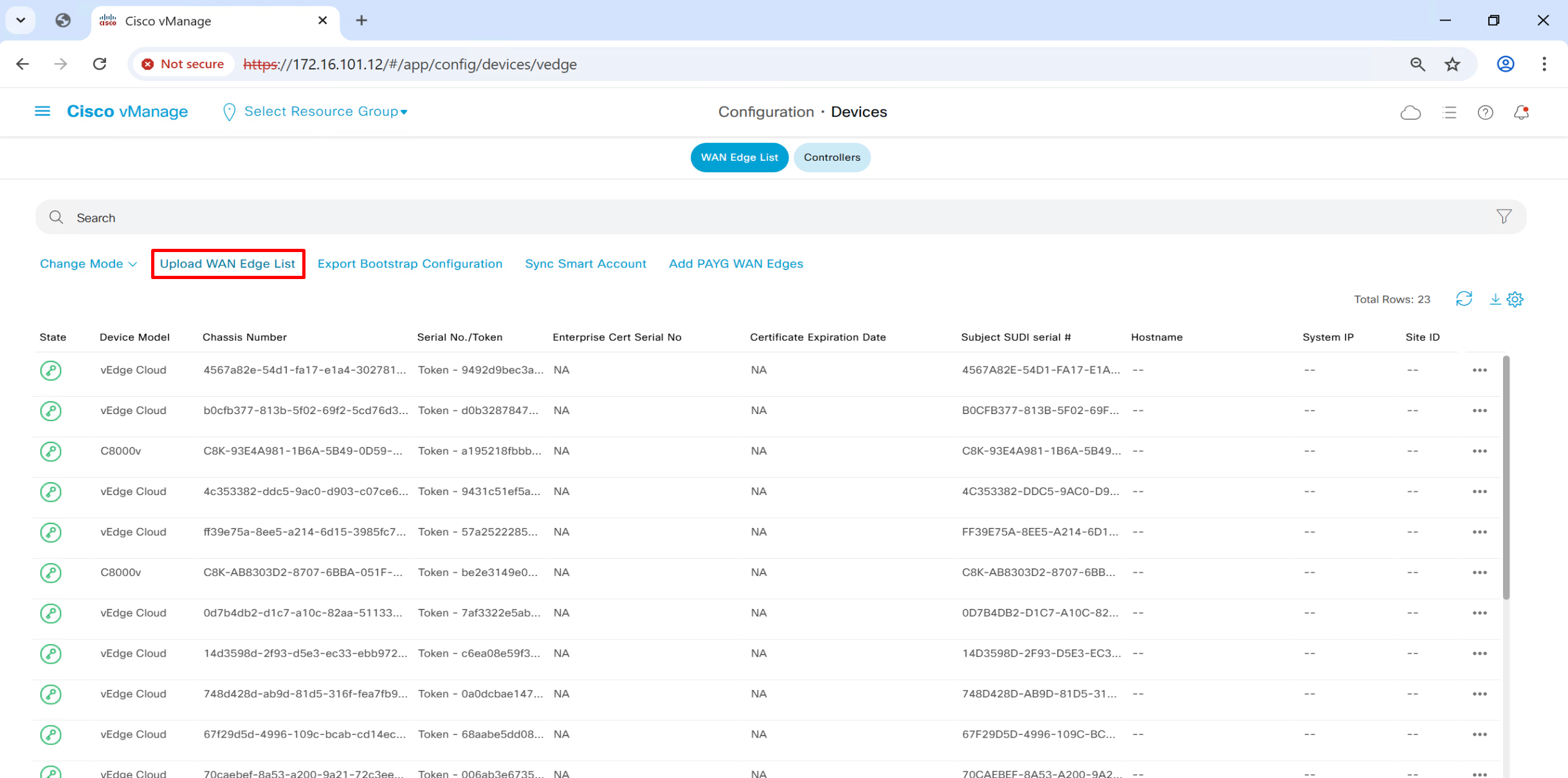

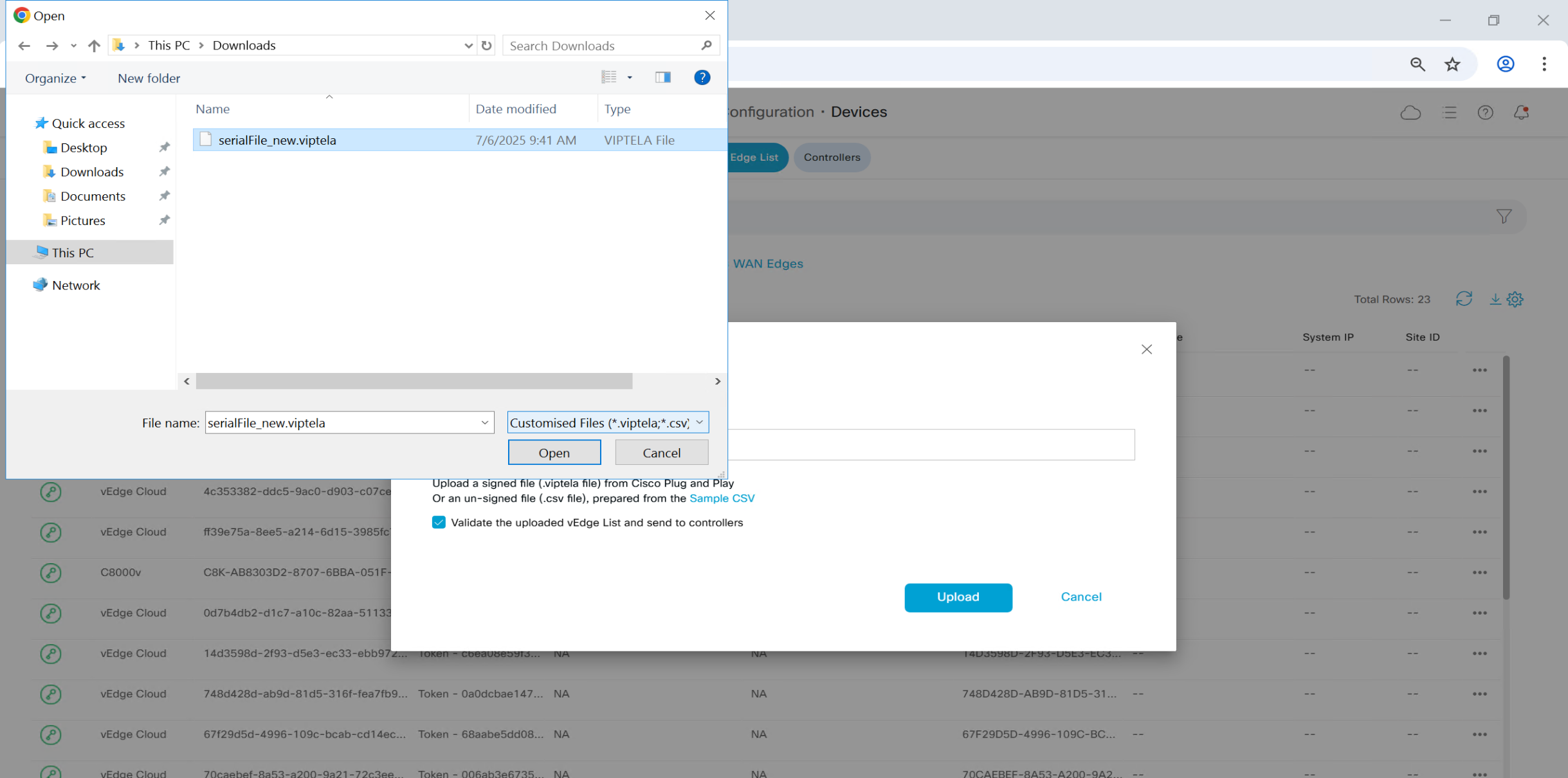
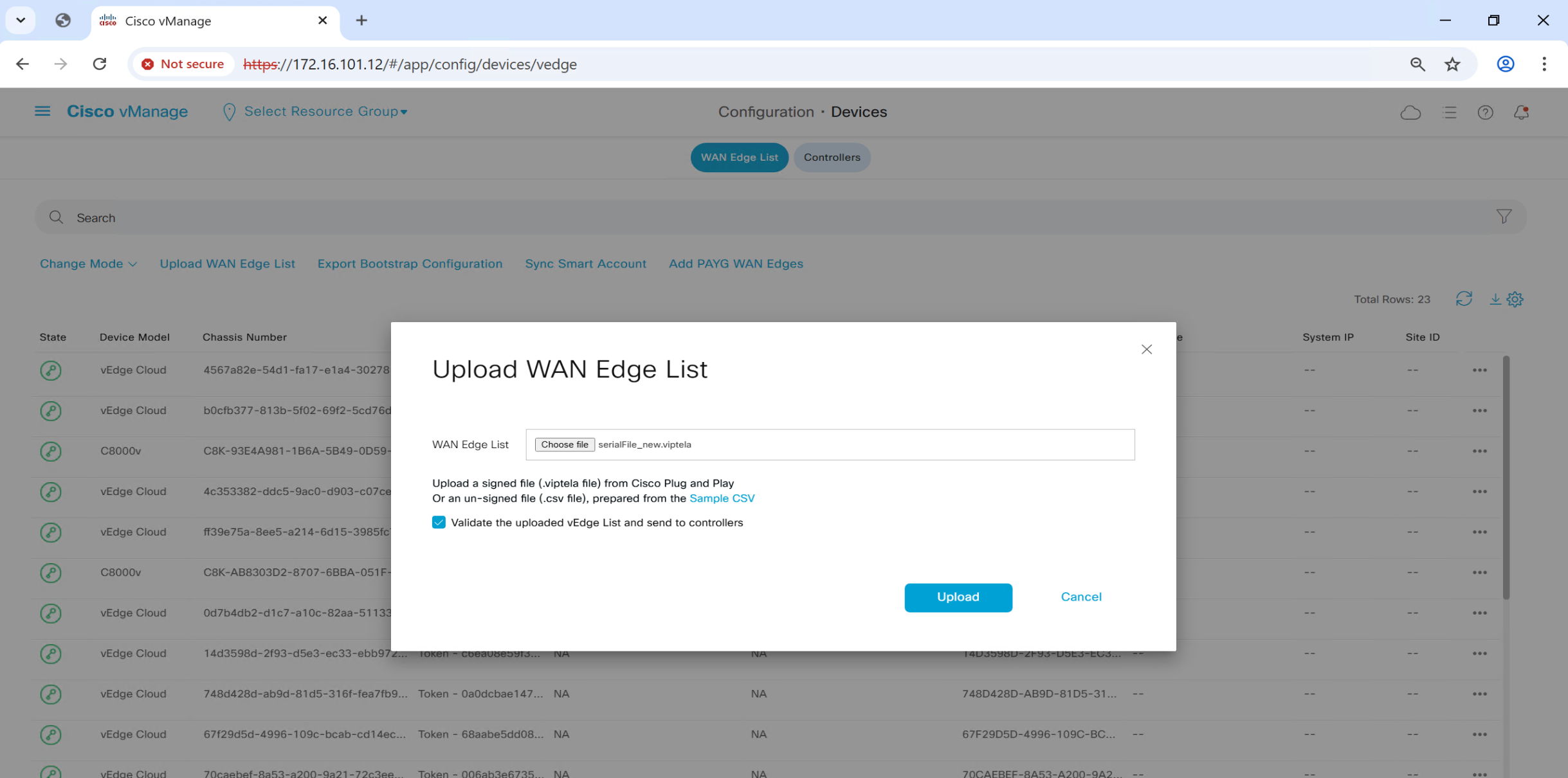
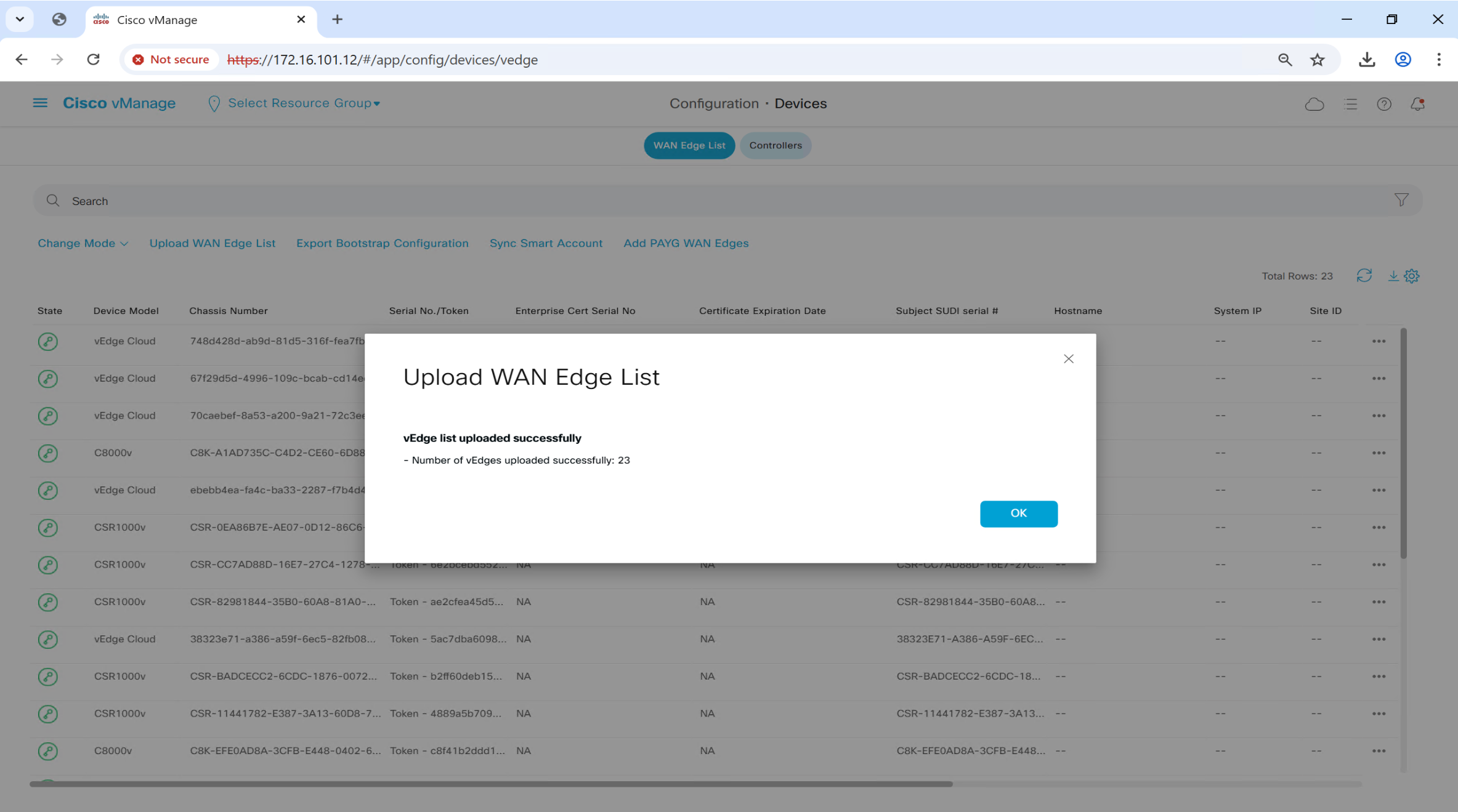
once file is uploaded, it will be pushed by vmanage to all other controllers
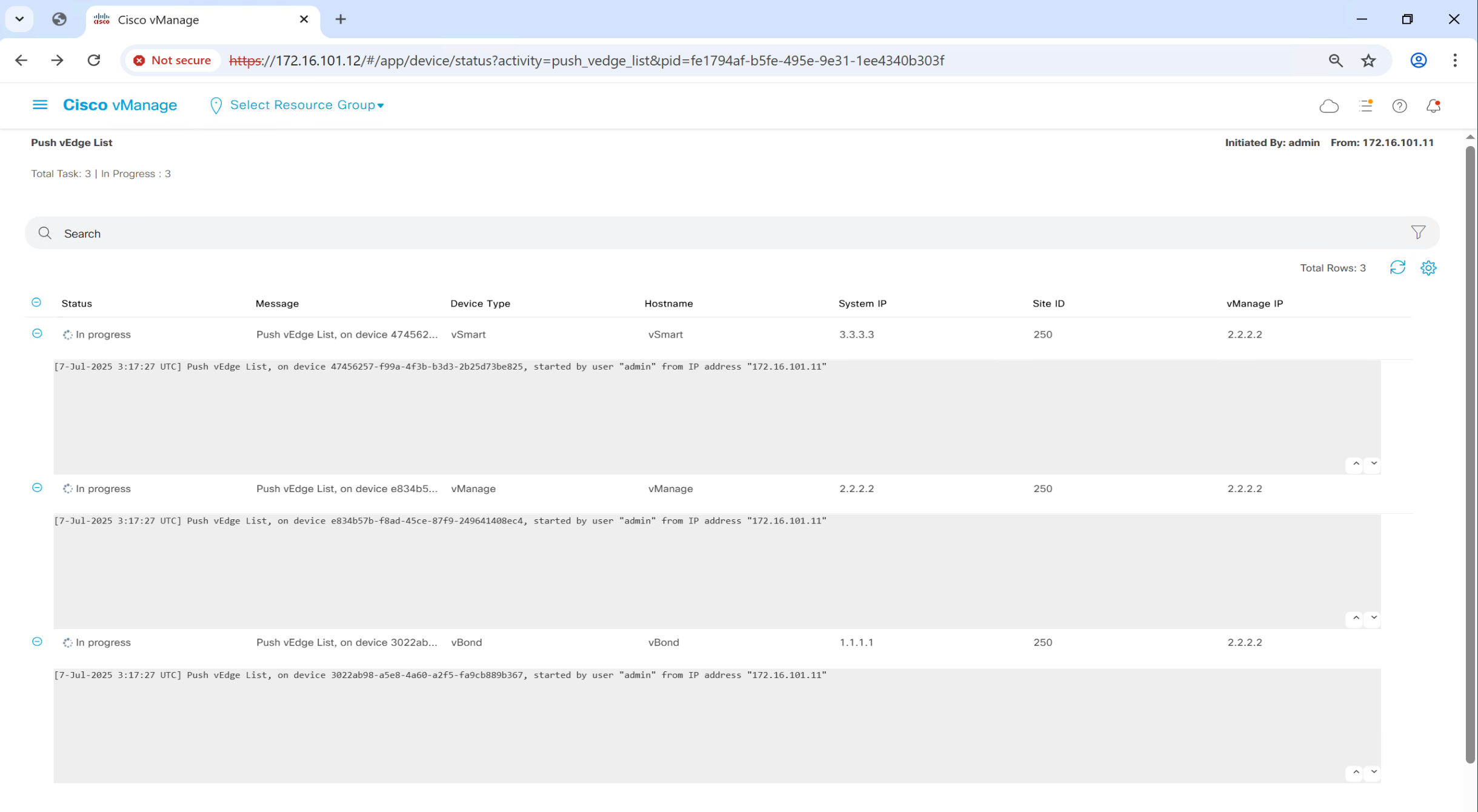
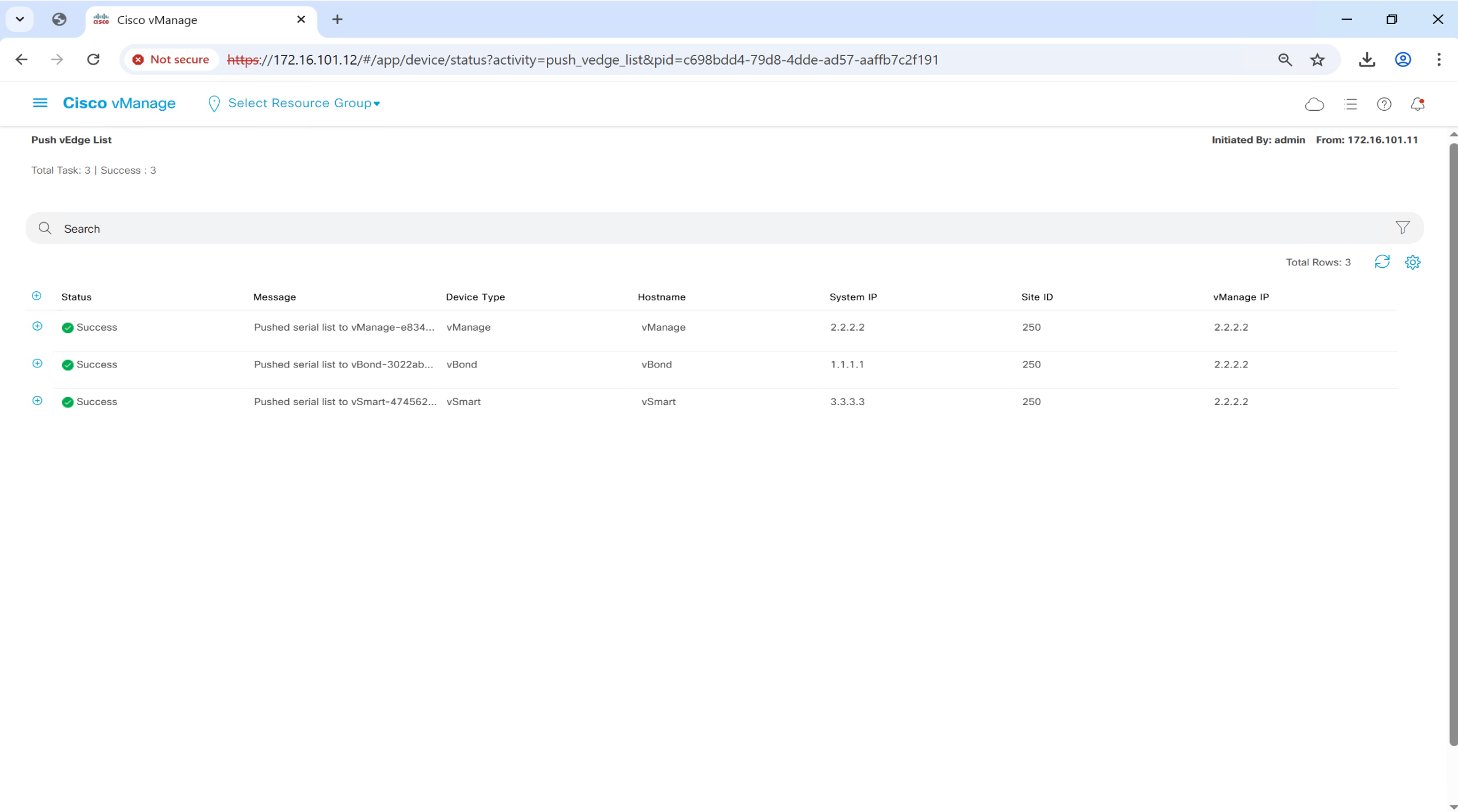
If we go to devices now
you will see available devices, this serial file has some C8000v and vEdge devices
Get rid of this annoying error message
Login to vmanage CLI
vManage# request nms configuration-db update-admin-user
Enter current user name:neo4j
Enter current user password:password
Enter new user name:admin
Enter new user password:C0mplex30
configuration-db
WARNING: sun.reflect.Reflection.getCallerClass is not supported. This will impact performance.
Successfully updated configuration database admin user
Successfully restarted NMS application server
Successfully restarted NMS data collection agent
vManage# Setting up watches.
Watches established.This will restart the vmanage
LM Topology with Wan Edge devices
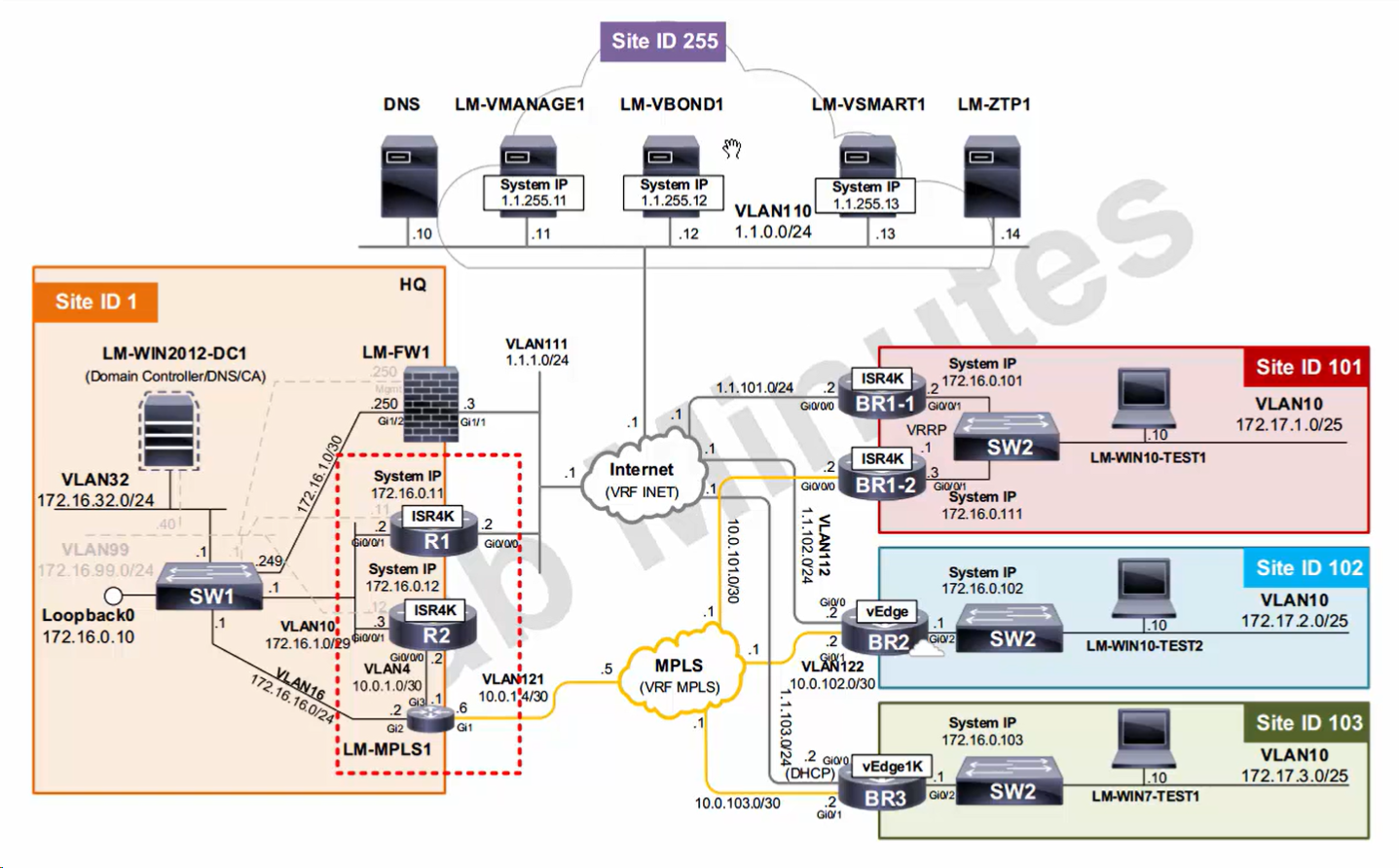
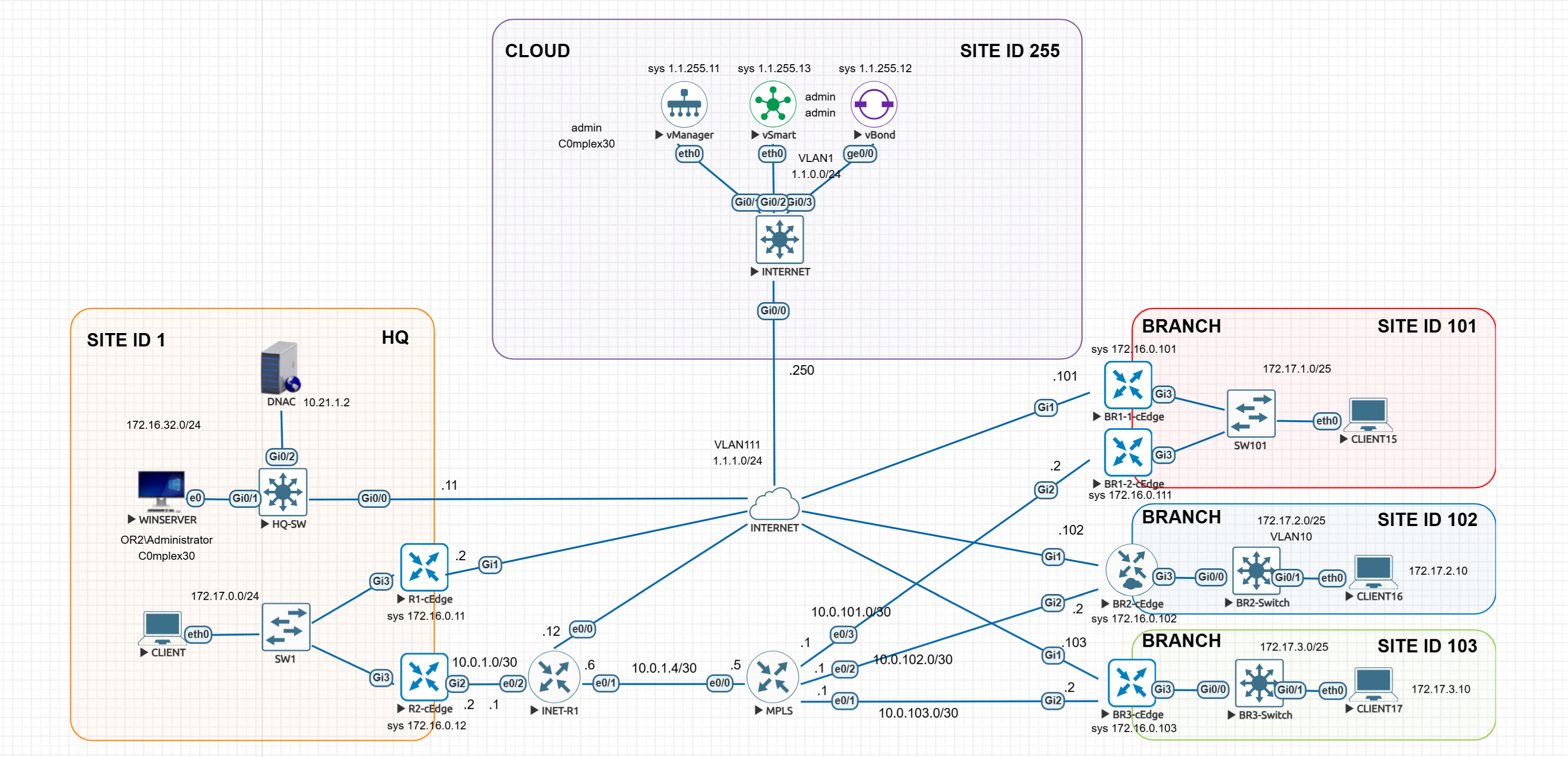
Onboard cEdge devices
https://www.networkacademy.io/ccie-enterprise/sdwan/onboarding-cedge-c8000v
Prepare the software image
When a Catalyst 8000V router is powered on for the first time, it boots up in AUTONOMOUS mode, as seen in the output below.
%BOOT-5-OPMODE_LOG: R0/0: binos: System booted in AUTONOMOUS modeThe router asks if you would like to enter the initial config dialog. We answer no. Just provide enable password and save configuration to NVRAM
% Please answer 'yes' or 'no'.
Would you like to enter the initial configuration dialog? [yes/no]: no
The enable secret is a password used to protect
access to privileged EXEC and configuration modes.
This password, after entered, becomes encrypted in
the configuration.
-------------------------------------------------
secret should be of minimum 10 characters and maximum 32 characters with
at least 1 upper case, 1 lower case, 1 digit and
should not contain [cisco]
-------------------------------------------------
Enter enable secret: ************
Confirm enable secret: ************
The following configuration command script was created:
enable secret 9 $9$uYATfwi9sBtruU$A4/FPncLMnru9Oo4oQjaF89yHqrCXDJBp**********
!
end
[0] Go to the IOS command prompt without saving this config.
[1] Return back to the setup without saving this config.
[2] Save this configuration to nvram and exit.
Enter your selection [2]: 2
Building configuration...
Guestshell destroyed successfully ommand to modify this configuration.
Press RETURN to get started!Install root ca cert on edge just like controllers – so it can mutually authenticate the certificate that is presented by remote device
You should have the Root CA certificate on vBond named root_ca.cer
The easiest way to install the root certificate on a Catalyst 8000v router is by creating a local file directly on the router using TCLSH, as shown in the following example.
In the highlighted section, you should paste the root_ca.cer using the “cat root_ca.cer” command in vshell mode from vBond.
cEdge# tclsh
cEdge(tcl)# puts [open "bootflash:root_ca.cer" w+] {
+> paste root-cert-here
+> }
cEdge-1(tcl)# exitIn the end, you should have the root certificate in the cEdge router’s bootflash, as shown below.
Router# dir bootflash:
Directory of bootflash:/
31 -rw- 1315 Sep 3 2022 08:19:25 +00:00 ROOTCA.pem
131078 drwx 4096 Sep 3 2022 08:18:48 +00:00 tracelogs
131073 drwx 4096 Sep 3 2022 08:16:36 +00:00 .installer
28 -rw- 618 Sep 3 2022 08:16:25 +00:00 cvac.log
131112 drwx 4096 Sep 3 2022 08:16:24 +00:00 license_evlog
29 -rw- 157 Sep 3 2022 08:16:23 +00:00 csrlxc-cfg.log
...
...
5183766528 bytes total (3968655360 bytes free)Now, it is time to reboot the router in CONTROLLER mode, which is required for SD-WAN. The router will notify you that a bootstrap configuration isn’t available, but we will continue anyway.
Router# controller-mode enable
Enabling controller mode will erase the nvram filesystem, remove all configuration files, and reload the box!
Ensure the BOOT variable points to a valid image
Continue? [confirm]
% Warning: Bootstrap config file needed for Day-0 boot is missing
Do you want to abort? (yes/[no]): no
Mode change successAfter the reboot, the router will boot up in CONTROLLER mode, as shown in the output below.
Oct 22 16:30:59.812: %BOOT-5-OPMODE_LOG: R0/0: binos: System booted in CONTROLLER modeThe last step is to install the root certificate using the following command.
cEdge# request platform software sdwan root-cert-chain install bootflash:root_ca.cer
Uploading root-ca-cert-chain via VPN 0
Copying ... /bootflash/ROOTCA.pem via VPN 0
Updating the root certificate chain..
Successfully installed the root certificate chainIf everything has gone smoothly, you should see our Enterprise CA Root certificate installed on the router.
cEdge# show sdwan certificate root-ca-cert | in network
Issuer: C=US, ST=NY, L=NY, O=networkacademy-io, CN=root.certificate
Subject: C=US, ST=NY, L=NY, O=networkacademy-io, CN=root.certificateNow we need vManage to issue certificate to vEdge
Pick on C8000v device from the devices, click on three dots and click on “Generate Bootstrap Configuration”

#cloud-config
vinitparam:
- uuid : C8K-A1AD735C-C4D2-CE60-6D88-01686AD4ED52
- rcc : true
- otp : 4a3a1eb353fc4b3b9a9c94baf06fd1f5
- org : or2.sys.cisco
- vbond : vbond.or.sys.cisco
ca-certs:
remove-defaults: false
trusted:
- |
-----BEGIN CERTIFICATE-----
MIIDnzCCAoegAwIBAgIQYJ1ACvIQRIlBAEITkoGNuzANBgkqhkiG9w0BAQsFADBi
MRUwEwYKCZImiZPyLGQBGRYFY2lzY28xEzARBgoJkiaJk/IsZAEZFgNzeXMxEzAR
BgoJkiaJk/IsZAEZFgNvcjIxHzAdBgNVBAMTFm9yMi1XSU4tVlEwOEc2VTk4R0Yt
Q0EwHhcNMjUwNzA2MjE1MjA1WhcNMzAwNzA2MjIwMjA1WjBiMRUwEwYKCZImiZPy
LGQBGRYFY2lzY28xEzARBgoJkiaJk/IsZAEZFgNzeXMxEzARBgoJkiaJk/IsZAEZ
FgNvcjIxHzAdBgNVBAMTFm9yMi1XSU4tVlEwOEc2VTk4R0YtQ0EwggEiMA0GCSqG
SIb3DQEBAQUAA4IBDwAwggEKAoIBAQCr6cjaoJz3vzgHlQ1hzhuy5WfIL/Ao0isM
ltIaGL+Z+9WftM1hNh10YECbxR71+lIpQKyBQTXQz8Of4nycxHjoI3dQdUvEYb8H
fysDXh4lYjQ60x82e5c7f1KPbD+AOhC31Zw1dgReMlPIuaa9LK903+z0FRnuCHaI
EG/Z9uCmv3JC22NgL69hscZc+NUGymMy1iBPN8G4EBkgqNVZ+zlRf/adW0JxEdc6
Sy53bp586/fXziRTW++jgdnhvfpn+VJ+BdG88/rEgMl7PUQE95lq4dih7qx0+OXu
ihFwQQvFxvi3dyqWWc0C1RKHPHtYQFz8rRuBJrR+uzgc0lVhrNHdAgMBAAGjUTBP
MAsGA1UdDwQEAwIBhjAPBgNVHRMBAf8EBTADAQH/MB0GA1UdDgQWBBQ/bI8yZeKD
fgjmmeWorjGo25t5hzAQBgkrBgEEAYI3FQEEAwIBADANBgkqhkiG9w0BAQsFAAOC
AQEAdtt6aiABkDDg/mAlcZfFPHcqmEEvQaMPeBaUqvfZKNrFVO8GMb9kingZJ62n
K05x5wE3tHy3jBmAl6eHZ/nUjXS11C06NwZMHpcDhty5BcDN08oEYdLF24upisNA
aRLOBhyEtKI9VKLAWfMkpWYEd/dqgVWs67GjAFT0Osgva9QHbz24iT6/c09jbZMt
41opmxacw8FFZcHMH9Afv1fIW9PwscrdlgjSSHR4XQLyDbyuDGsolzeh9PUVyPOd
f+/LYkLwH9jVcHlxl4Oy7MHRPtcbG9T3+vQGLjSAXu3Ybrl2R9Tn/sz5lYs44EEB
mqCxT00LxB3et6jAxJlEyE5vCw==
-----END CERTIFICATE-----We have to configure basic IP addressesing and default route and system configuration
we will also configure a DNS name for vBond, as recommended by Cisco.
config-transaction
hostname R1-cEdge
!
int GigabitEthernet1
ip address 1.1.1.1 255.255.255.0
no shut
!
ip route 0.0.0.0 0.0.0.0 1.1.1.250
!
system
system-ip 172.16.0.11
site-id 1
ip host vbond.or.sys.cisco 1.1.0.12 ! cisco recommends adding this host entry
organization-name or2.sys.cisco
vbond vbond.or.sys.cisco
commitYou should be able to ping the controllers at this point, If there is no IP connectivity between the WAN edge router and the controllers, there is no point in continuing further. You should troubleshoot the problem first.
sdwan
int GigabitEthernet1
tunnel-interface
color biz-internet
encapsulation ipsec
!
interface Tunnel 1 !----> this tunnel interface number should be same as physical interface
ip unnumbered GigabitEthernet1
tunnel source GigabitEthernet1
tunnel mode sdwan
!
int GigabitEthernet2
tunnel-interface
color mpls restrict
encapsulation ipsec
!
interface Tunnel 2
ip unnumbered GigabitEthernet2
tunnel source GigabitEthernet2
tunnel mode sdwanRouter is now ready to join overlay fabric
Before the cEdge router can be able to join the SD-WAN fabric, it must have a device certificate signed and installed by vManage
this is the common rule for both controllers and edge devices, anything that needs to join fabric, requires a certificate issued from vmanage and mutual authentication
request platform software sdwan vedge_cloud activate chassis-number C8K-A1AD735C-C4D2-CE60-6D88-01686AD4ED52 token 4a3a1eb353fc4b3b9a9c94baf06fd1f5Once you’ve done, you should see in the logs that vManage logs into the cEdge using NETCONF over SSH, generates a CSR, then signs it and install a device certificate. Then the cEdge router should establish an OMP peering with vSmart and start receiving TLOCs and OMP routes.
R1-cEdge#
*Jul 21 20:27:09.257: %SYS-5-CONFIG_P: Configured programmatically by process iosp_dmiauthd_conn_100001_vty_100001 from consol6
*Jul 21 20:27:09.523: %SYS-5-CONFIG_P: Configured programmatically by process iosp_dmiauthd_conn_100001_vty_100001 from console as admin on vty42946
*Jul 21 20:27:09.503: %DMI-5-CONFIG_I: R0/0: dmiauthd: Configured from NETCONF/RESTCONF by admin, transaction-id 558pong
*Jul 21 20:27:17.068: %SYS-5-CONFIG_P: Configured programmatically by process iosp_dmiauthd_conn_100001_vty_100001 from console as admin on vty4294l
*Jul 21 20:28:03.534: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:36606 for netconf over s:
*Jul 21 20:28:29.847: %Cisco-SDWAN-R1-cEdge-action_notifier-6-INFO-1400002: Notification: 7/21/2025 20:28:29 security-install-rcc severity-level:mi1
*Jul 21 20:28:30.030: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:36688 for netconf over s:
*Jul 21 20:28:43.152: %Cisco-SDWAN-R1-cEdge-action_notifier-6-INFO-1400002: Notification: 7/21/2025 20:28:43 security-install-certificate severity-1
*Jul 21 20:29:25.117: %Cisco-SDWAN-Router-OMPD-3-ERRO-400002: vSmart peer 1.1.255.13 state changed to Init
*Jul 21 20:29:25.343: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:36822 for netconf over ss
*Jul 21 20:29:27.205: %Cisco-SDWAN-Router-OMPD-6-INFO-400002: vSmart peer 1.1.255.13 state changed to Handshake
*Jul 21 20:29:27.218: %Cisco-SDWAN-Router-OMPD-5-NTCE-400002: vSmart peer 1.1.255.13 state changed to Up
*Jul 21 20:29:27.218: %Cisco-SDWAN-Router-OMPD-6-INFO-400005: Number of vSmarts connected : 1
*Jul 21 20:29:41.535: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:36882 for netconf over s:
*Jul 21 20:30:01.736: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:36928 for netconf over s:
*Jul 21 20:30:23.576: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:37006 for netconf over s:
*Jul 21 20:30:33.557: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:37052 for netconf over s:
*Jul 21 20:30:43.535: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:37078 for netconf over s:
*Jul 21 20:30:48.611: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:37108 for netconf over s:
R1-cEdge#show sdwan control connections
PEER PEER
PEER PEER PEER SITE DOMAIN PEER PRIV PEER PUB
TYPE PROT SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT ORGANIZA
----------------------------------------------------------------------------------------------------------------------------------------------------
vsmart dtls 1.1.255.13 255 1 1.1.0.13 12446 1.1.0.13 12446 or2.sys.
vbond dtls 0.0.0.0 0 0 1.1.0.12 12346 1.1.0.12 12346 or2.sys.
vmanage dtls 1.1.255.11 255 0 1.1.0.11 12846 1.1.0.11 12846 or2.sys.
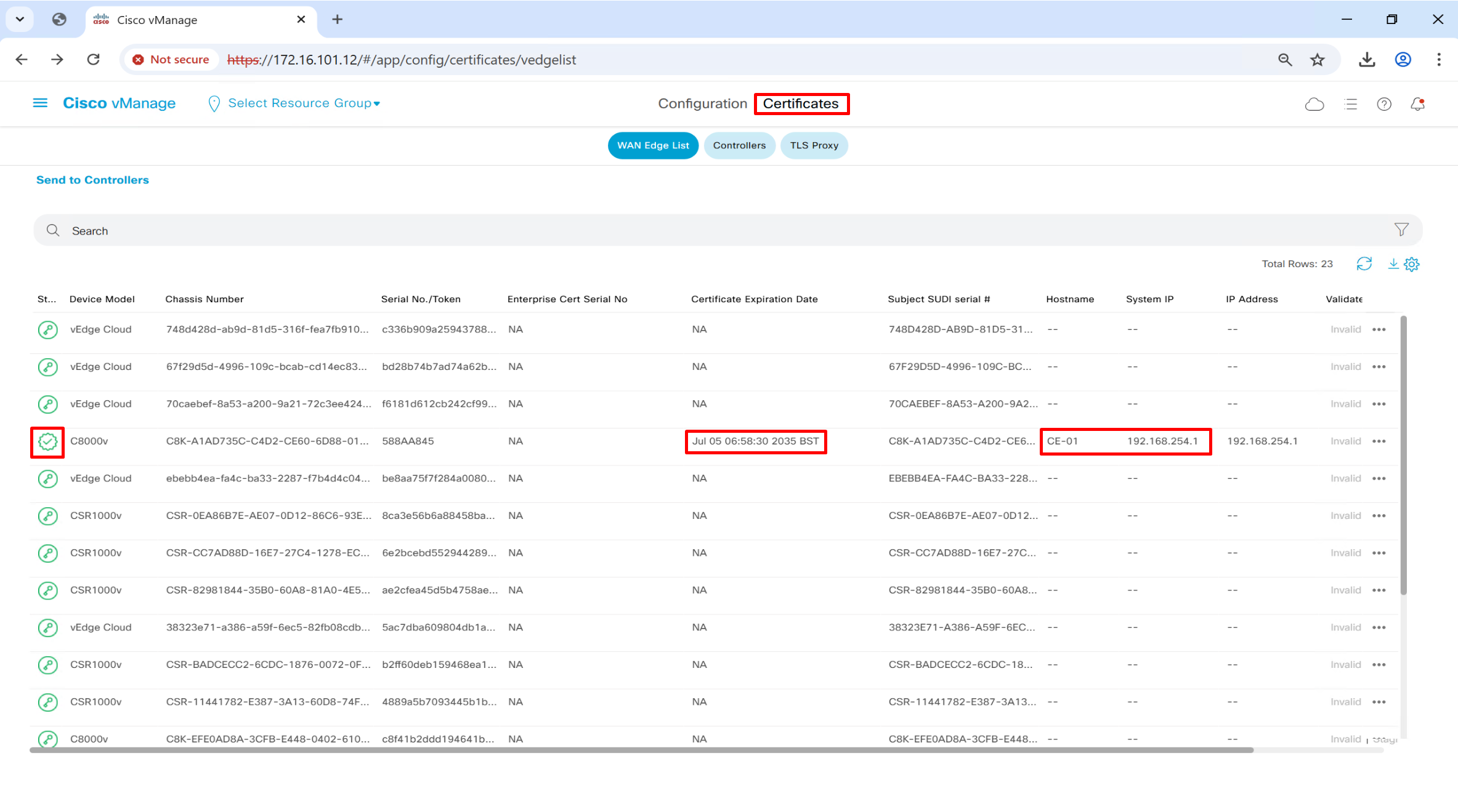

R1-cEdge#
*Jul 21 20:27:09.257: %SYS-5-CONFIG_P: Configured programmatically by process iosp_dmiauthd_conn_100001_vty_100001 from consol6
*Jul 21 20:27:09.523: %SYS-5-CONFIG_P: Configured programmatically by process iosp_dmiauthd_conn_100001_vty_100001 from console as admin on vty42946
*Jul 21 20:27:09.503: %DMI-5-CONFIG_I: R0/0: dmiauthd: Configured from NETCONF/RESTCONF by admin, transaction-id 558pong
*Jul 21 20:27:17.068: %SYS-5-CONFIG_P: Configured programmatically by process iosp_dmiauthd_conn_100001_vty_100001 from console as admin on vty4294l
*Jul 21 20:28:03.534: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:36606 for netconf over s:
*Jul 21 20:28:29.847: %Cisco-SDWAN-R1-cEdge-action_notifier-6-INFO-1400002: Notification: 7/21/2025 20:28:29 security-install-rcc severity-level:mi1
*Jul 21 20:28:30.030: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:36688 for netconf over s:
*Jul 21 20:28:43.152: %Cisco-SDWAN-R1-cEdge-action_notifier-6-INFO-1400002: Notification: 7/21/2025 20:28:43 security-install-certificate severity-1
*Jul 21 20:29:25.117: %Cisco-SDWAN-Router-OMPD-3-ERRO-400002: vSmart peer 1.1.255.13 state changed to Init
*Jul 21 20:29:25.343: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:36822 for netconf over ss
*Jul 21 20:29:27.205: %Cisco-SDWAN-Router-OMPD-6-INFO-400002: vSmart peer 1.1.255.13 state changed to Handshake
*Jul 21 20:29:27.218: %Cisco-SDWAN-Router-OMPD-5-NTCE-400002: vSmart peer 1.1.255.13 state changed to Up
*Jul 21 20:29:27.218: %Cisco-SDWAN-Router-OMPD-6-INFO-400005: Number of vSmarts connected : 1
*Jul 21 20:29:41.535: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:36882 for netconf over s:
*Jul 21 20:30:01.736: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:36928 for netconf over s:
*Jul 21 20:30:23.576: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:37006 for netconf over s:
*Jul 21 20:30:33.557: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:37052 for netconf over s:
*Jul 21 20:30:43.535: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:37078 for netconf over s:
*Jul 21 20:30:48.611: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:37108 for netconf over s:CE-01#show sdwan control local-properties
personality vedge
sp-organization-name or2.sys.cisco
organization-name or2.sys.cisco
root-ca-chain-status Installed
certificate-status Installed
certificate-validity Valid
certificate-not-valid-before Jul 7 05:58:30 2025 GMT
certificate-not-valid-after Jul 5 05:58:30 2035 GMT
enterprise-cert-status Not-Applicable
enterprise-cert-validity Not Applicable
enterprise-cert-not-valid-before Not Applicable
enterprise-cert-not-valid-after Not Applicable
dns-name vbond.or.sys.cisco
site-id 250
domain-id 1
protocol dtls
tls-port 0
system-ip 192.168.254.1
chassis-num/unique-id C8K-A1AD735C-C4D2-CE60-6D88-01686AD4ED52
serial-num 588AA845
subject-serial-num N/A
enterprise-serial-num No certificate installed
token Invalid
keygen-interval 1:00:00:00
retry-interval 0:00:00:16
no-activity-exp-interval 0:00:00:20
dns-cache-ttl 0:00:02:00
port-hopped TRUE
time-since-last-port-hop 0:00:30:51
embargo-check success
number-vbond-peers 1
INDEX IP PORT
-----------------------------------------------------
0 172.16.101.14 12346
number-active-wan-interfaces 1
NAT TYPE: E -- indicates End-point independent mapping
A -- indicates Address-port dependent mapping
N -- indicates Not learned
Note: Requires minimum two vbonds to learn the NAT type
PUBLIC PUBLIC PRIVATE PRIVATE PRIVATE MAX RESTRICT/ LAM
INTERFACE IPv4 PORT IPv4 IPv6 PORT VS/VM COLOR STATE CNTRL CONTROL/ LR/LB CON
STUN F
--------------------------------------------------------------------------------------------------------------------------------------------------------------------------
GigabitEthernet1 172.16.101.200 12366 172.16.101.200 :: 12366 1/1 biz-internet up 2 no/yes/no No/R1-cEdge#show sdwan control connections
PEER PEER
PEER PEER PEER SITE DOMAIN PEER PRIV PEER PUB
TYPE PROT SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT ORGANIZA
----------------------------------------------------------------------------------------------------------------------------------------------------
vsmart dtls 1.1.255.13 255 1 1.1.0.13 12446 1.1.0.13 12446 or2.sys.
vbond dtls 0.0.0.0 0 0 1.1.0.12 12346 1.1.0.12 12346 or2.sys.
vmanage dtls 1.1.255.11 255 0 1.1.0.11 12846 1.1.0.11 12846 or2.sys.show run ! still works
show sdwan running-config
vbond command: show orchestrator valid-vedges
Platform Console
The last thing in running Catalyst 8000V in a virtual EVE-NG environment is to change the console method after attaching a device template.
Depending on your lab, you will most likely end up attaching a device template to the 8000V edge routers. What typically happens is that you lose access to the device via the console. This happens because, by default, the device boot up configured with the following command.
platform console serialHowever, after you attach a template, vManage changes the console method to
platform console virtualThe “virtual” option defines that the 8000V router is accessed through the virtual VGA console of the hypervisor. To change the console method back to “serial,” you must configure a CLI add-on feature template and add it to the respective device template the router is attached to.
Changing IP address on WAN side of the edge device
I changed IP address on R1-cEdge on its WAN transport interface and it re-established connections to controllers and all control connections came up, I did not have to edit or change addresses in any of the controllers, that is good. I changed IP address from 1.1.1.1 to 1.1.1.2
ISR 4000 Conversion and Standup as SDWAN router for CCIE Hardware router provisioning exam topic
Do all below videos in their accordion sections
RS0138 – SD-WAN ISR 4K Installation (Part 1)
RS0138 – SD-WAN ISR 4K Installation (Part 2)
RS0138 – SD-WAN ISR 4K Installation (Part 3)
RS0138 – SD-WAN ISR 4K Installation (Part 4)
ZTP and PnP videos
RS0140 – SD-WAN ZTP and PnP (Part 1)
RS0140 – SD-WAN ZTP and PnP (Part 2)
RS0140 – SD-WAN ZTP and PnP (Part 3)
RS0140 – SD-WAN ZTP and PnP (Part 4)
R2-cEdge standup over MPLS (apparent no reachability to controllers)

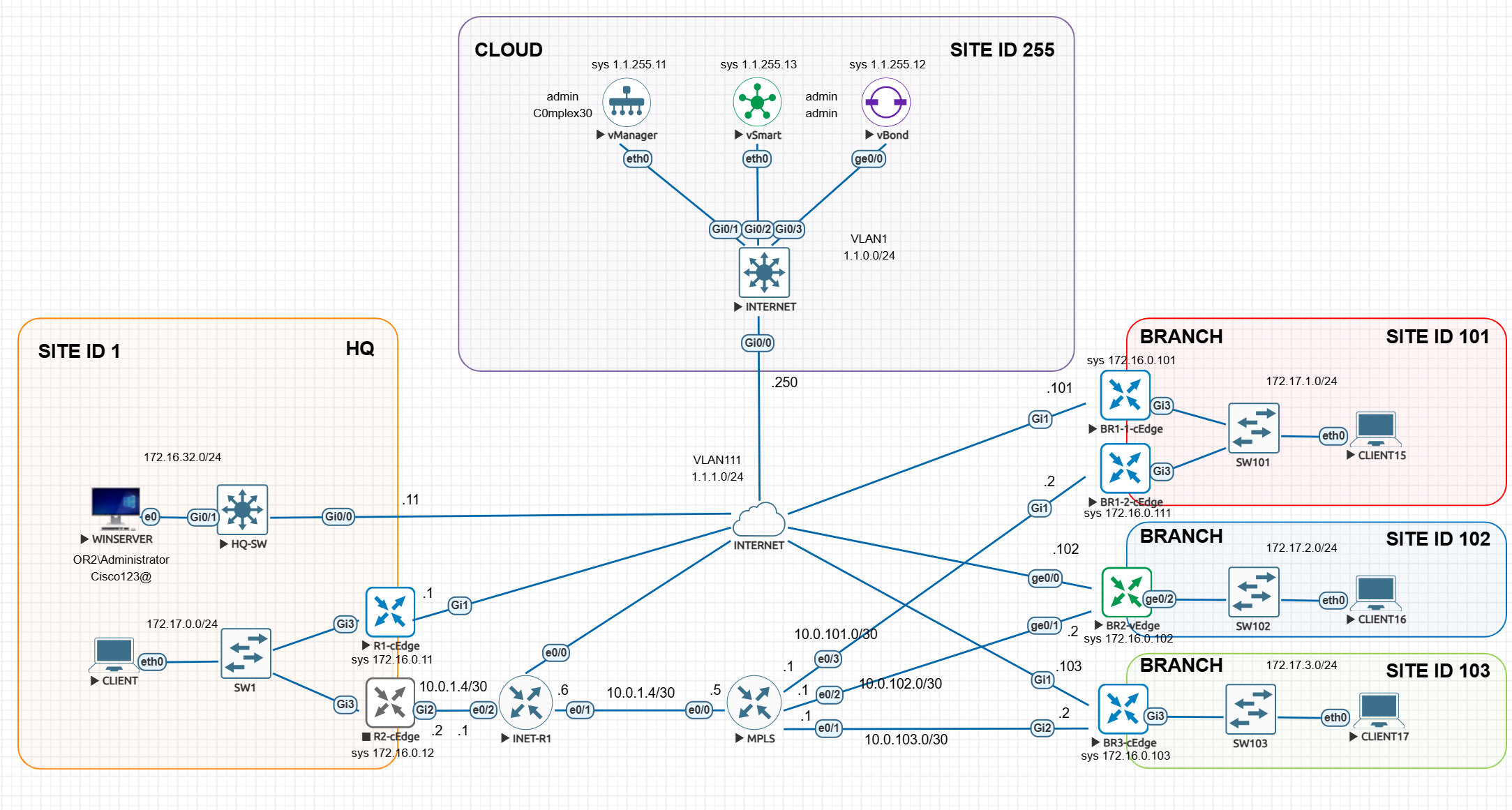
Most MPLS setup do not have the internet access unless you pay for it and then provider can provide default route from MPLS, it will have an INET-R1 router that will route traffic for 0.0.0.0/0 towards internet cloud and allow connectivity to controllers on internet to be reached via MPLS network
Traffic for MPLS prefixes will be routed towards MPLS router and for internet connectivity will be routed to internet
Add basic configuration on R2-cEdge
system
system-ip 172.16.0.12
site-id 1
organization-name or2.sys.cisco
vbond vbond.or.sys.cisco
hostname R2-cEdge
username admin privilege 15 secret 5 $1$dYK8$TukpN4hzNpia/JRlBkEjG.
ip host vbond.or.sys.cisco 1.1.0.12
ip route 0.0.0.0 0.0.0.0 10.0.1.1
interface GigabitEthernet2
ip address 10.0.1.2 255.255.255.252
no shutdown
no mop enabled
no mop sysid
negotiation auto
exit
interface Tunnel2
no shutdown
ip unnumbered GigabitEthernet2
tunnel source GigabitEthernet2
tunnel mode sdwan
exit
sdwan
interface GigabitEthernet2
tunnel-interface
encapsulation ipsec
color mpls
allow-service all
exit
exit
commit
Untick validate – this validate option will make device status as valid directly skipping invalid and staging state, if you dont want to bring device in production straight away then untick validate
#cloud-config
vinitparam:
- vbond : vbond.or.sys.cisco
- rcc : true
- uuid : C8K-AB8303D2-8707-6BBA-051F-8BB318E56660
- org : or2.sys.cisco
- otp : 5505e0f36e3e45e181c862471c35f18d
ca-certs:
remove-defaults: false
trusted:
- |
-----BEGIN CERTIFICATE-----
MIIDnzCCAoegAwIBAgIQYJ1ACvIQRIlBAEITkoGNuzANBgkqhkiG9w0BAQsFADBi
MRUwEwYKCZImiZPyLGQBGRYFY2lzY28xEzARBgoJkiaJk/IsZAEZFgNzeXMxEzAR
BgoJkiaJk/IsZAEZFgNvcjIxHzAdBgNVBAMTFm9yMi1XSU4tVlEwOEc2VTk4R0Yt
Q0EwHhcNMjUwNzA2MjE1MjA1WhcNMzAwNzA2MjIwMjA1WjBiMRUwEwYKCZImiZPy
LGQBGRYFY2lzY28xEzARBgoJkiaJk/IsZAEZFgNzeXMxEzARBgoJkiaJk/IsZAEZ
FgNvcjIxHzAdBgNVBAMTFm9yMi1XSU4tVlEwOEc2VTk4R0YtQ0EwggEiMA0GCSqG
SIb3DQEBAQUAA4IBDwAwggEKAoIBAQCr6cjaoJz3vzgHlQ1hzhuy5WfIL/Ao0isM
ltIaGL+Z+9WftM1hNh10YECbxR71+lIpQKyBQTXQz8Of4nycxHjoI3dQdUvEYb8H
fysDXh4lYjQ60x82e5c7f1KPbD+AOhC31Zw1dgReMlPIuaa9LK903+z0FRnuCHaI
EG/Z9uCmv3JC22NgL69hscZc+NUGymMy1iBPN8G4EBkgqNVZ+zlRf/adW0JxEdc6
Sy53bp586/fXziRTW++jgdnhvfpn+VJ+BdG88/rEgMl7PUQE95lq4dih7qx0+OXu
ihFwQQvFxvi3dyqWWc0C1RKHPHtYQFz8rRuBJrR+uzgc0lVhrNHdAgMBAAGjUTBP
MAsGA1UdDwQEAwIBhjAPBgNVHRMBAf8EBTADAQH/MB0GA1UdDgQWBBQ/bI8yZeKD
fgjmmeWorjGo25t5hzAQBgkrBgEEAYI3FQEEAwIBADANBgkqhkiG9w0BAQsFAAOC
AQEAdtt6aiABkDDg/mAlcZfFPHcqmEEvQaMPeBaUqvfZKNrFVO8GMb9kingZJ62n
K05x5wE3tHy3jBmAl6eHZ/nUjXS11C06NwZMHpcDhty5BcDN08oEYdLF24upisNA
aRLOBhyEtKI9VKLAWfMkpWYEd/dqgVWs67GjAFT0Osgva9QHbz24iT6/c09jbZMt
41opmxacw8FFZcHMH9Afv1fIW9PwscrdlgjSSHR4XQLyDbyuDGsolzeh9PUVyPOd
f+/LYkLwH9jVcHlxl4Oy7MHRPtcbG9T3+vQGLjSAXu3Ybrl2R9Tn/sz5lYs44EEB
mqCxT00LxB3et6jAxJlEyE5vCw==
-----END CERTIFICATE-----on R2-cEdge
request platform software sdwan vedge_cloud activate chassis-number C8K-AB8303D2-8707-6BBA-051F-8BB318E56660 token 5505e0f36e3e45e181c862471c35f18d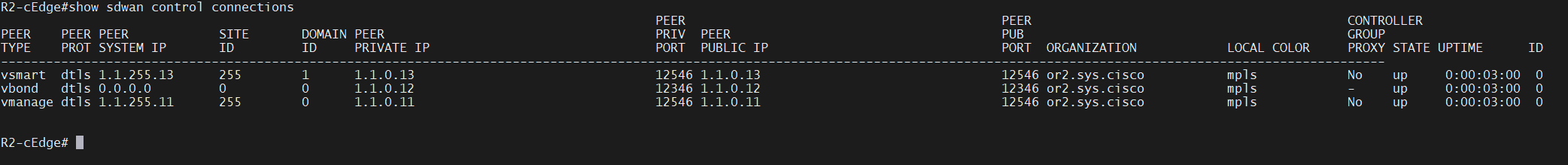

vEdge onboarding and configuration
Every time a new device is added to the WAN edge list, either via syncing from smart account or viptella serial file, we need to “send to controllers”, verify on vbond that new device is added to it
vBond# show orchestrator valid-vedges | tab
HARDWARE
INSTALLED SUBJECT
SERIAL SERIAL
CHASSIS NUMBER SERIAL NUMBER VALIDITY ORG NUMBER NUMBER
-----------------------------------------------------------------------------------------------------------------------------
0d7b4db2-d1c7-a10c-82aa-51133e50a3ad 56831d0a459a4d11adbebfb844115fe0 valid or2.sys.cisco N/A 0D7B4DB2-D1
14d3598d-2f93-d5e3-ec33-ebb972a54a96 07b454f7f0694a1a8fdc3f59915d8e97 valid or2.sys.cisco N/A 14D3598D-2F
38323e71-a386-a59f-6ec5-82fb08cdbc0c 6b81257104424bdc928e4c2fabfc0967 valid or2.sys.cisco N/A 38323E71-A3
4567a82e-54d1-fa17-e1a4-302781b96194 eca16978e13744e2ac2edda6e33c9373 valid or2.sys.cisco N/A 4567A82E-54
4c353382-ddc5-9ac0-d903-c07ce6fc19ac e56d759ca369422c842d5ff98b370293 valid or2.sys.cisco N/A 4C353382-DD
67f29d5d-4996-109c-bcab-cd14ec837a33 6950d355072b452bb0c3c6ee348e684d valid or2.sys.cisco N/A 67F29D5D-49
70caebef-8a53-a200-9a21-72c3ee424737 25936ef5caa74cff8a30118cba2e5595 valid or2.sys.cisco N/A 70CAEBEF-8A
748d428d-ab9d-81d5-316f-fea7fb910d6d 2b31d2d21dc141b0b0b31cf87a028ddf valid or2.sys.cisco N/A 748D428D-AB
aafa211d-aee9-6dc7-ce14-829e5a025225 cc51993a8cfb46b588def2f923e09e66 valid or2.sys.cisco N/A AAFA211D-AE
b0cfb377-813b-5f02-69f2-5cd76d3c261f 930d0e37929f49f2ad1fbe3d23cc7c5a valid or2.sys.cisco N/A B0CFB377-81
C8K-93E4A981-1B6A-5B49-0D59-4818588CA46A 9B10218D valid or2.sys.cisco N/A N/A
C8K-A1AD735C-C4D2-CE60-6D88-01686AD4ED52 aac6851892a546edbc6c6b50b182ae96 valid or2.sys.cisco N/A C8K-A1AD735
C8K-AB8303D2-8707-6BBA-051F-8BB318E56660 1250E1E5 valid or2.sys.cisco N/A C8K-AB8303D
C8K-EFE0AD8A-3CFB-E448-0402-6108A06678C2 88c4c032d1d1413cbf66c72166e4b070 valid or2.sys.cisco N/A C8K-EFE0AD8
C8K-FF74B9C0-47EC-6B46-6F06-B63A33303C0F 3d4817593d9e42d19092a8a7804051aa valid or2.sys.cisco N/A C8K-FF74B9C
CSR-0EA86B7E-AE07-0D12-86C6-93E64EA24C46 d843a0b45dbf4b7982c930e6c5c120c6 valid or2.sys.cisco N/A CSR-0EA86B7
CSR-11441782-E387-3A13-60D8-74FFCE54D959 7b5690b9065e44e1943c3e74e336625e valid or2.sys.cisco N/A CSR-1144178
CSR-82981844-35B0-60A8-81A0-4E511A9FF6FA 08086272a4174295b0ec03095b39492e valid or2.sys.cisco N/A CSR-8298184
CSR-BADCECC2-6CDC-1876-0072-0F9EAE28D879 fb7abe09c58e48daab91c73fe59a1bc1 valid or2.sys.cisco N/A CSR-BADCECC
CSR-CC7AD88D-16E7-27C4-1278-EC9520C8CCD4 d58d1b454b0f45a2a16bfbeeca1b1f28 valid or2.sys.cisco N/A CSR-CC7AD88
CSR-ED63ADBC-750F-E08A-5C4D-0DDEE109E9D1 46a30397d6b04e43a2b8d5cfa370126e valid or2.sys.cisco N/A CSR-ED63ADB
ebebb4ea-fa4c-ba33-2287-f7b4d4c04b74 f6a307a61d4d4fceac7e2d45a45dc528 valid or2.sys.cisco N/A EBEBB4EA-FA
ff39e75a-8ee5-a214-6d15-3985fc7a9273 5718fec846484ba0b9fb0243c90fc62e valid or2.sys.cisco N/A FF39E75A-8EFor non cisco viptella based vedge onboarding this section works, this settings allows vManage to issue the cert or vedge to use the vManage as the CA and we will keep it to default setting vManage signed

configure BR2-vEdge
conf t
system
system-ip 172.16.0.102
site-id 102
organization-name or2.sys.cisco
vbond 1.1.0.12
host-name BR2-vEdge
commit
vpn 0
int ge0/0
ip address 1.1.1.102/24
no shut
tunnel-interface
allow-service all
no shut
exit
ip route 0.0.0.0/0 1.1.1.250
commit Make sure that we can ping hops and controllers
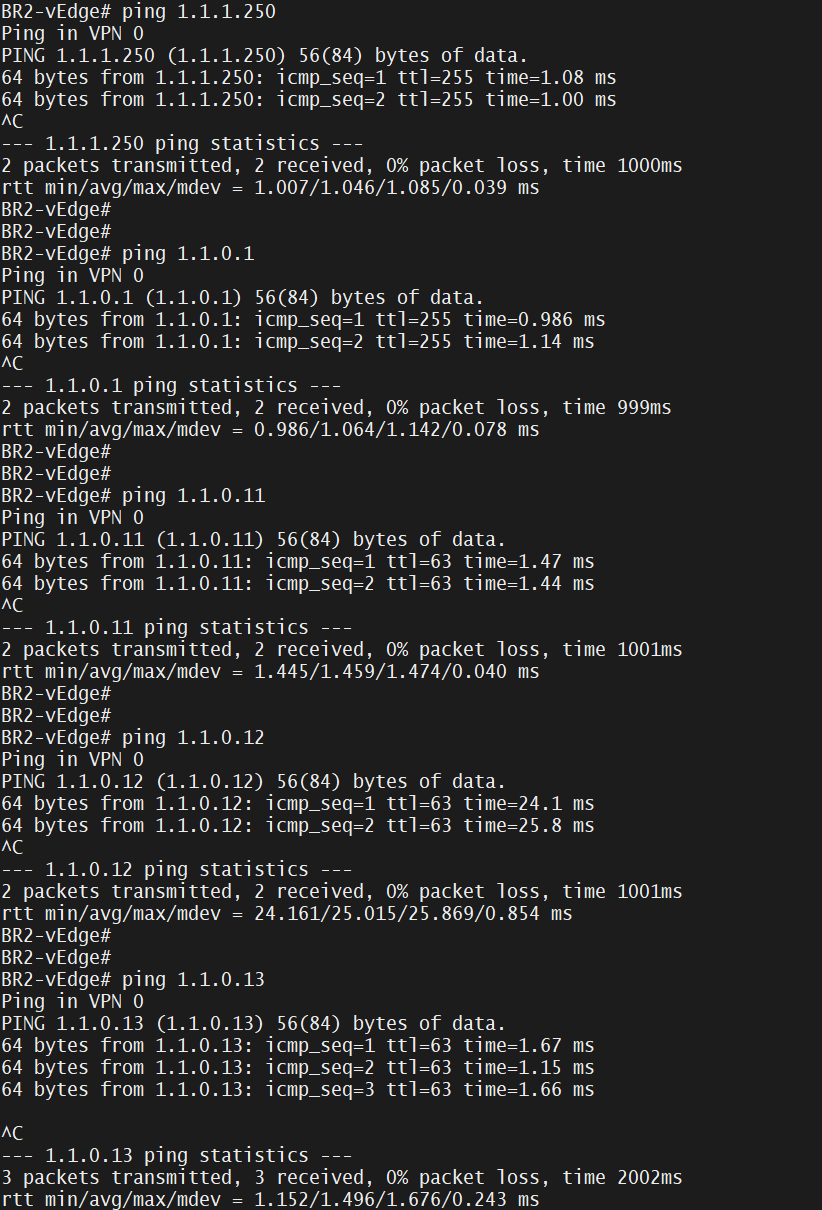
SFTP to vedge router and drag root.cer into it
because with SFTP you dont have to worry about the CLI prompt to be linux


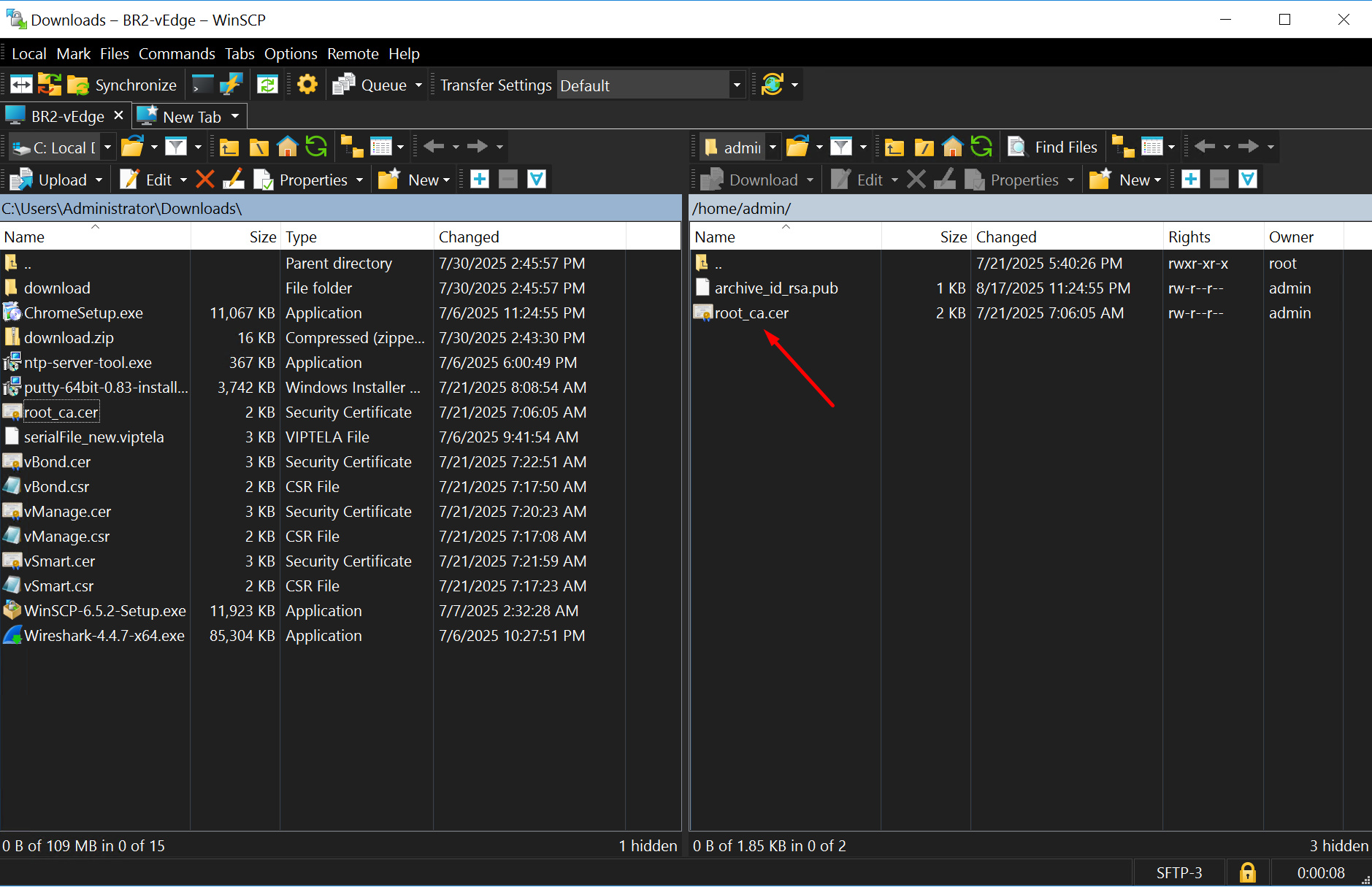
Enter vshell and make sure that root ca cert is present as a result of the previous transfer
BR2-vEdge#
BR2-vEdge# vshell
BR2-vEdge:~$ ls -lapsh
total 32K
4.0K drwxr-x--- 3 admin admin 4.0K Aug 17 22:31 ./
4.0K drwxr-xr-x 14 root root 4.0K Jul 21 16:40 ../
4.0K -rw------- 1 admin admin 5 Aug 17 22:31 .bash_history
4.0K -rwxr-xr-x 1 admin admin 476 Aug 17 22:24 .bashrc
4.0K -rwxr-xr-x 1 admin admin 241 Aug 24 2021 .profile
4.0K drwx------ 2 admin admin 4.0K Jul 21 16:40 .ssh/
4.0K -rw-r--r-- 1 admin admin 564 Aug 17 22:24 archive_id_rsa.pub
4.0K -rw-r--r-- 1 admin admin 1.4K Jul 21 06:06 root_ca.cerInstall root ca cert on vedge
BR2-vEdge# request root-cert-chain install /home/admin/root_ca.cer
Uploading root-ca-cert-chain via VPN 0
Copying ... /home/admin/root_ca.cer via VPN 0
Updating the root certificate chain..
Successfully installed the root certificate chainVerify the root ca cert installation
BR2-vEdge# show certificate root-ca-cert | inc Subject
Subject: DC=cisco, DC=sys, DC=or2, CN=or2-WIN-VQ08G6U98GF-CA
Subject Public Key Info:
X509v3 Subject Key Identifier:We want vManage to install the certificate as it is not installed
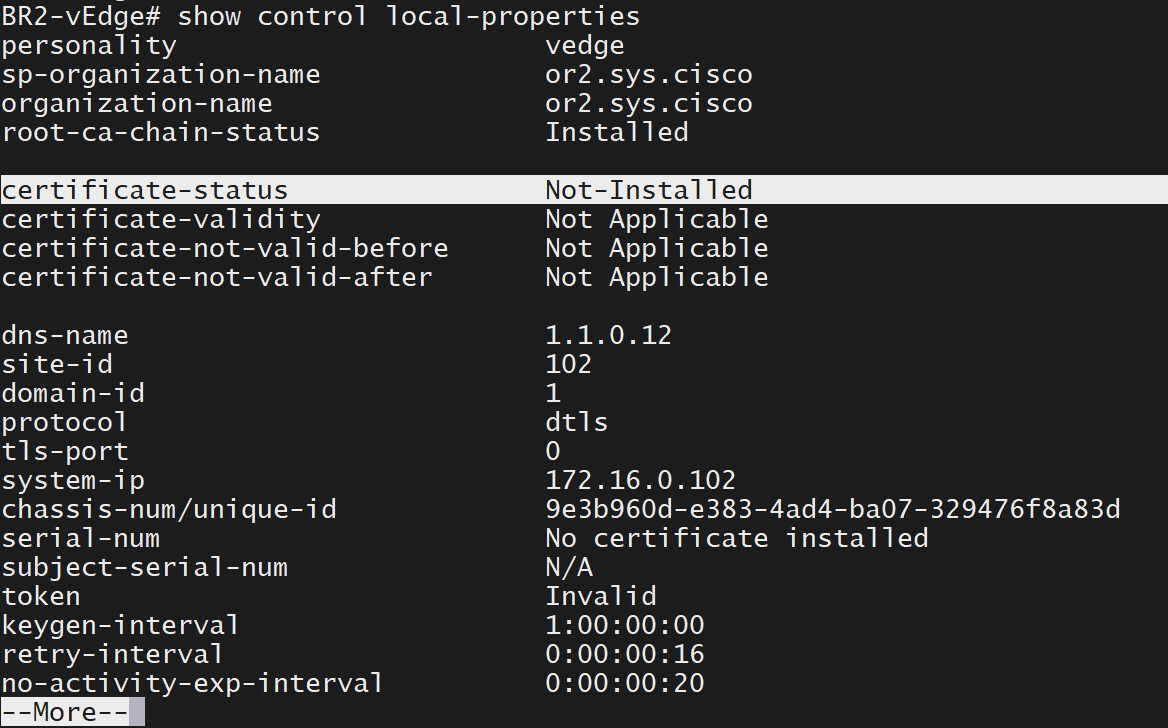
now we need to obtain the chassis number and token from vManage for one of the devices of type vEdge
request vedge-cloud activate chassis-number 4567a82e-54d1-fa17-e1a4-302781b96194 token eca16978e13744e2ac2edda6e33c9373
show certificate installed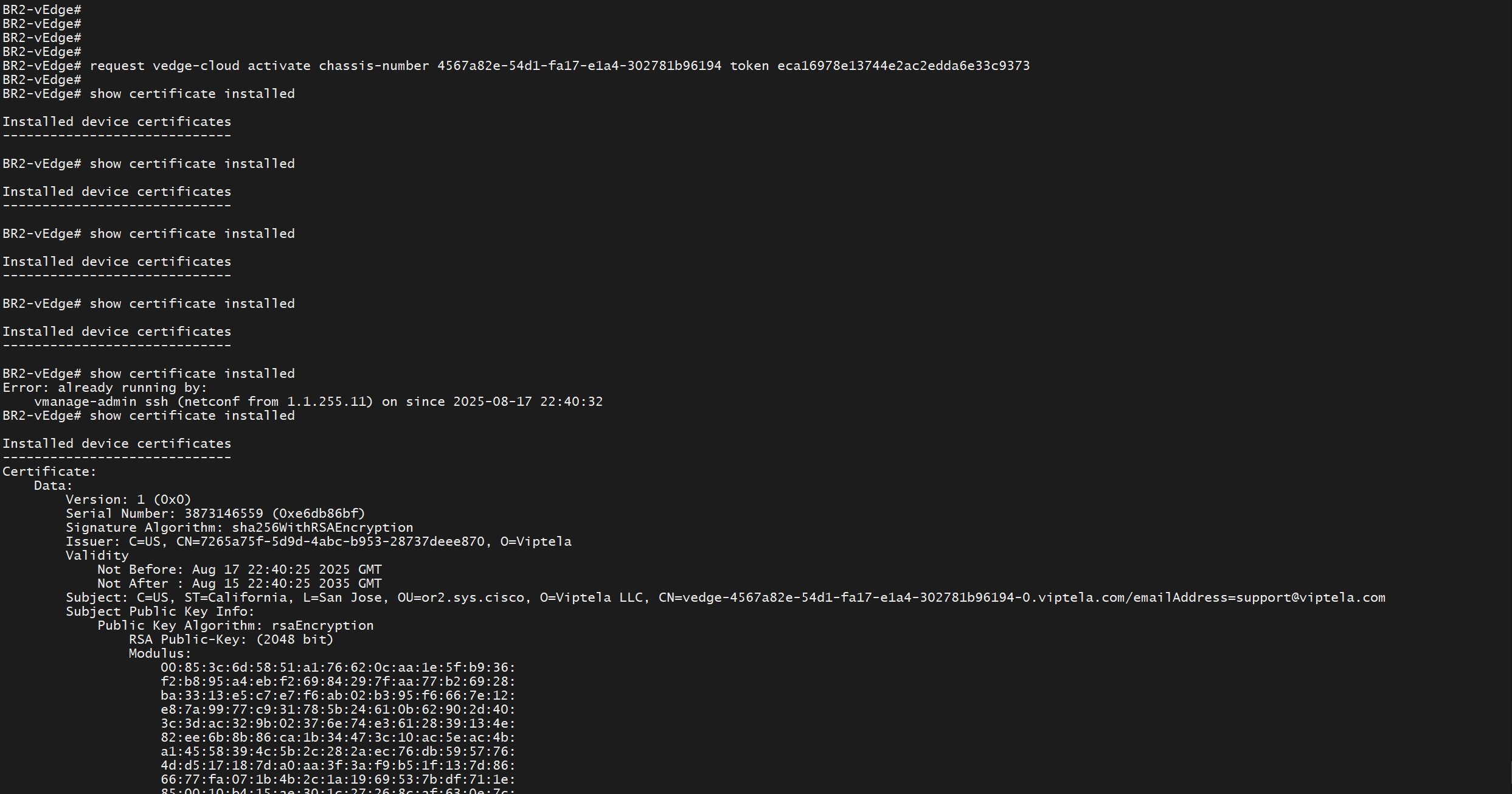
show control connections 
sort by state to see the installed edges and we will see latest vedge in there
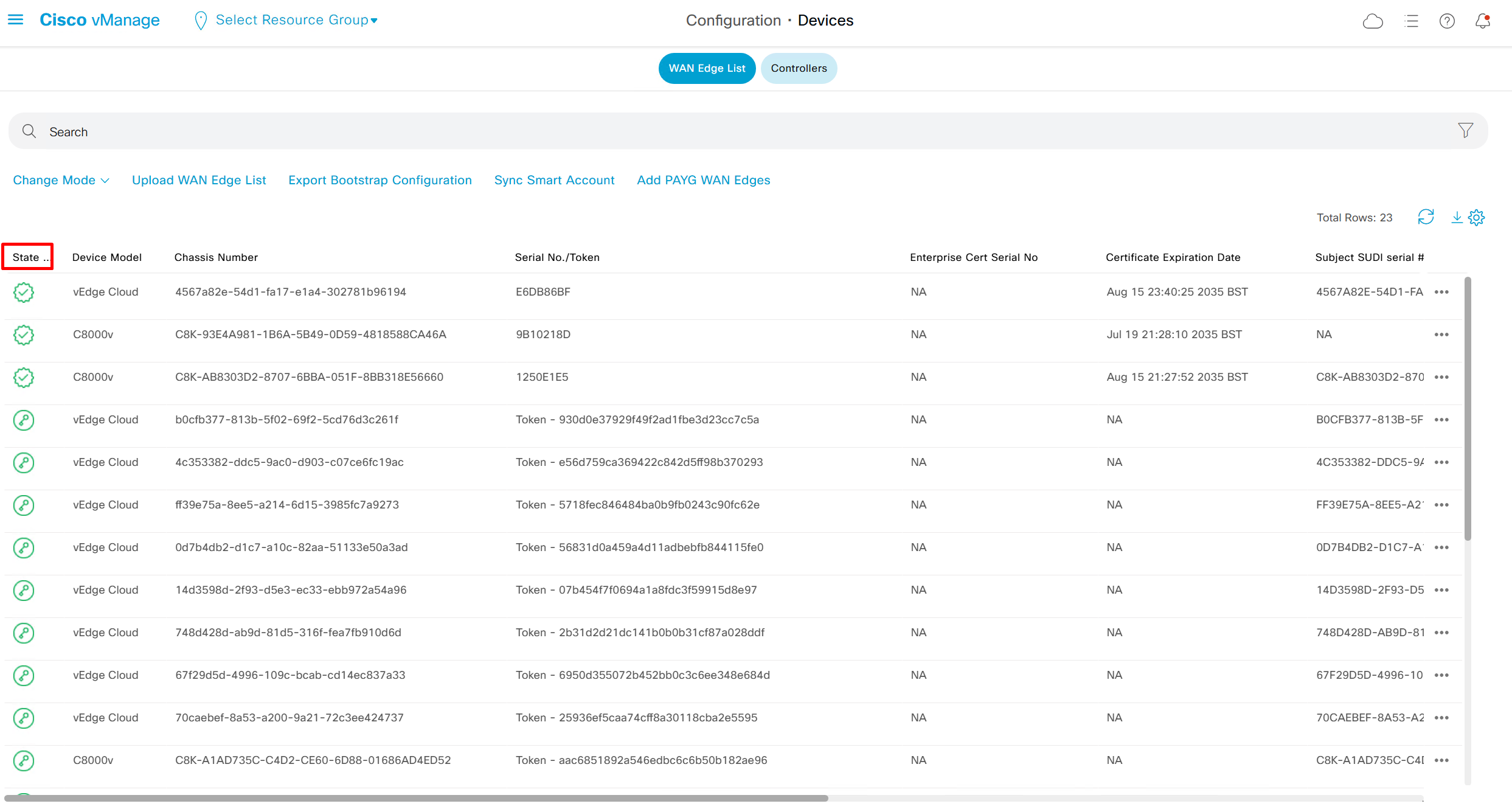
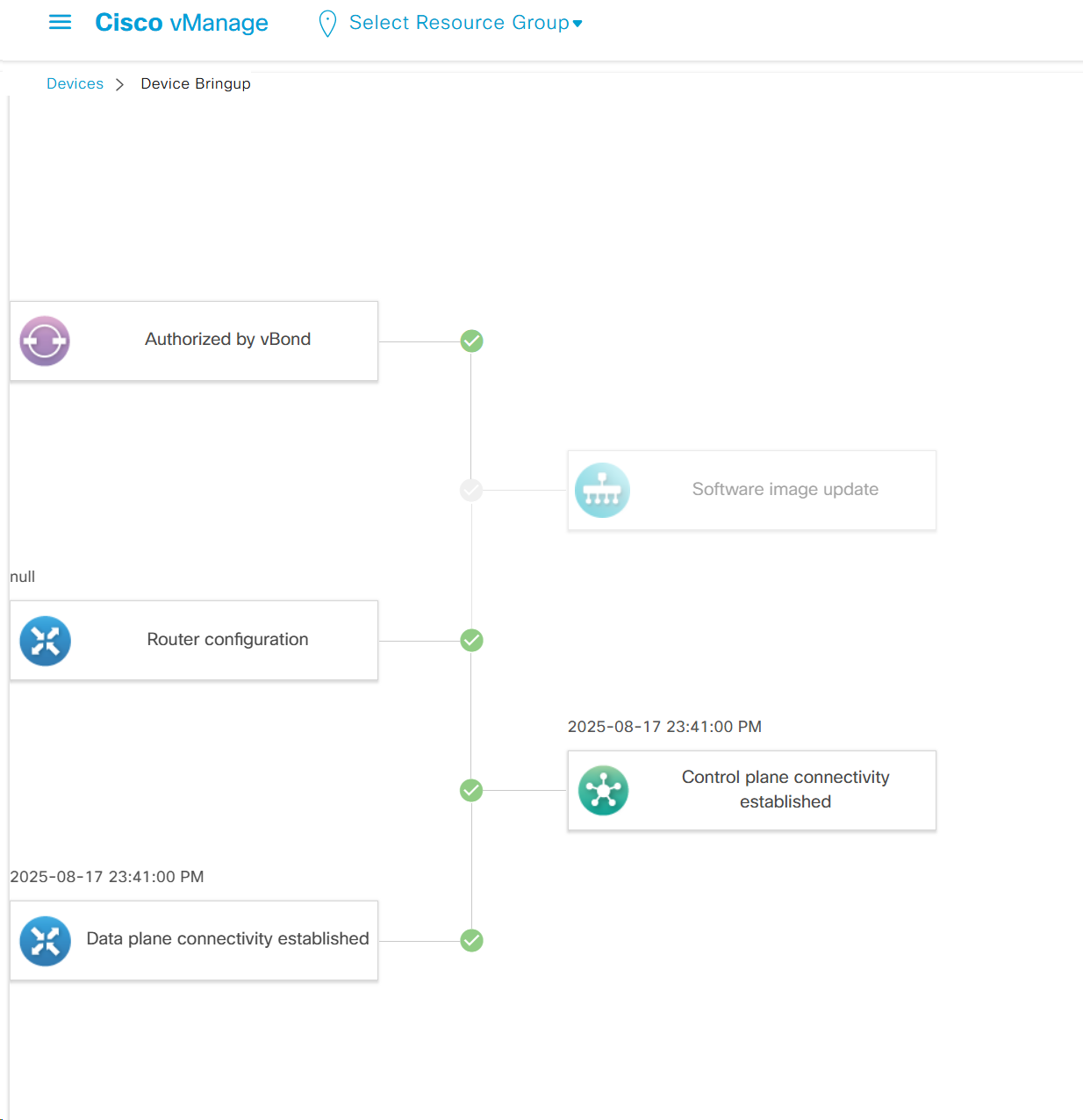
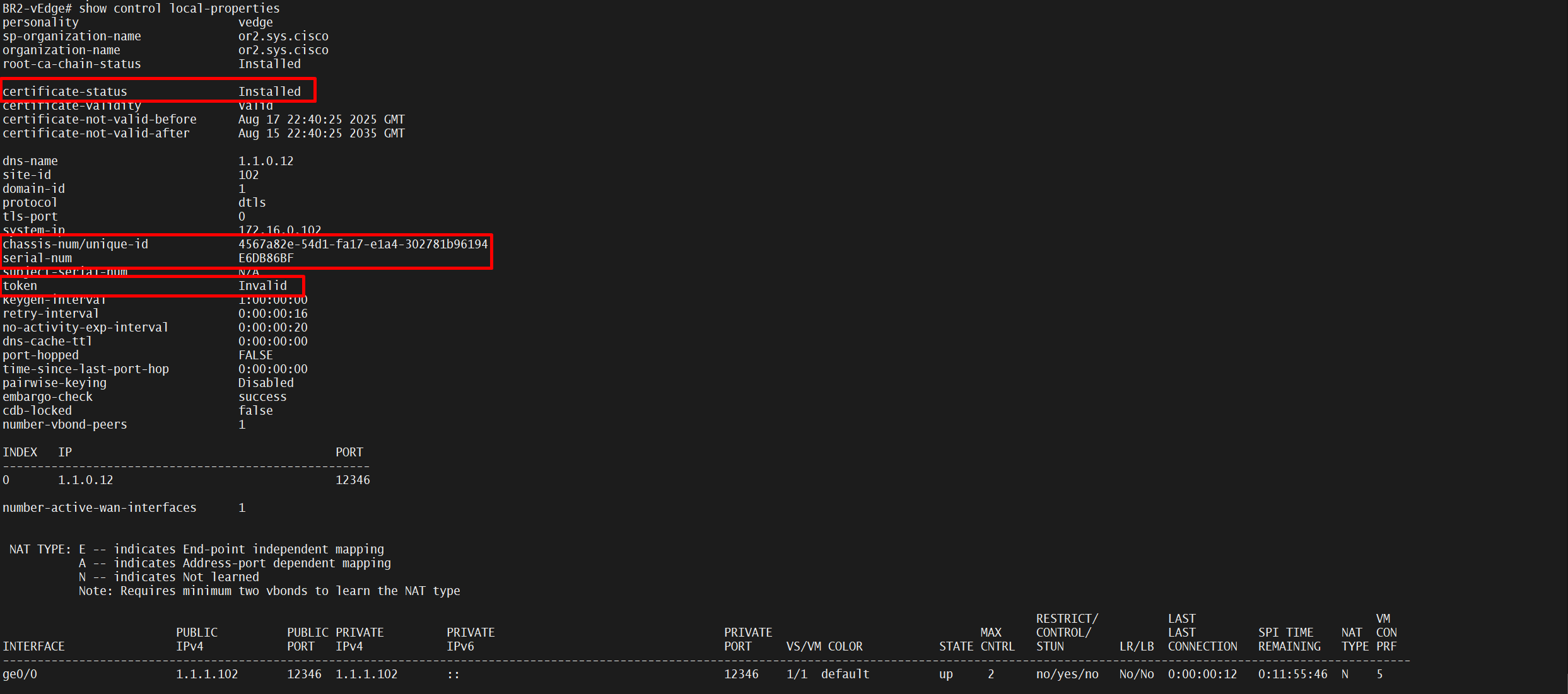
color is set to default so we will set it to biz-internet

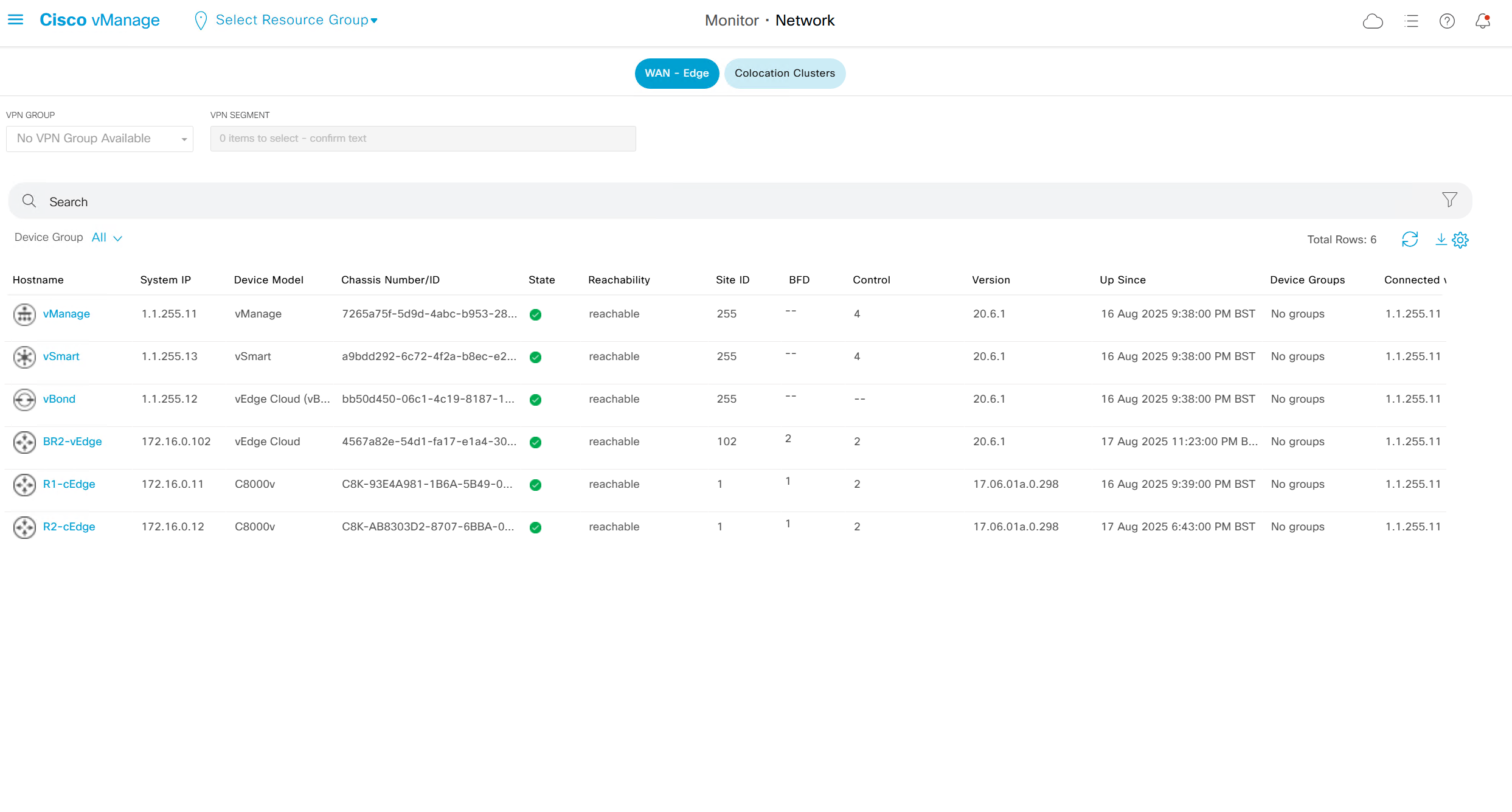
Control connections to vsmart and vmanage
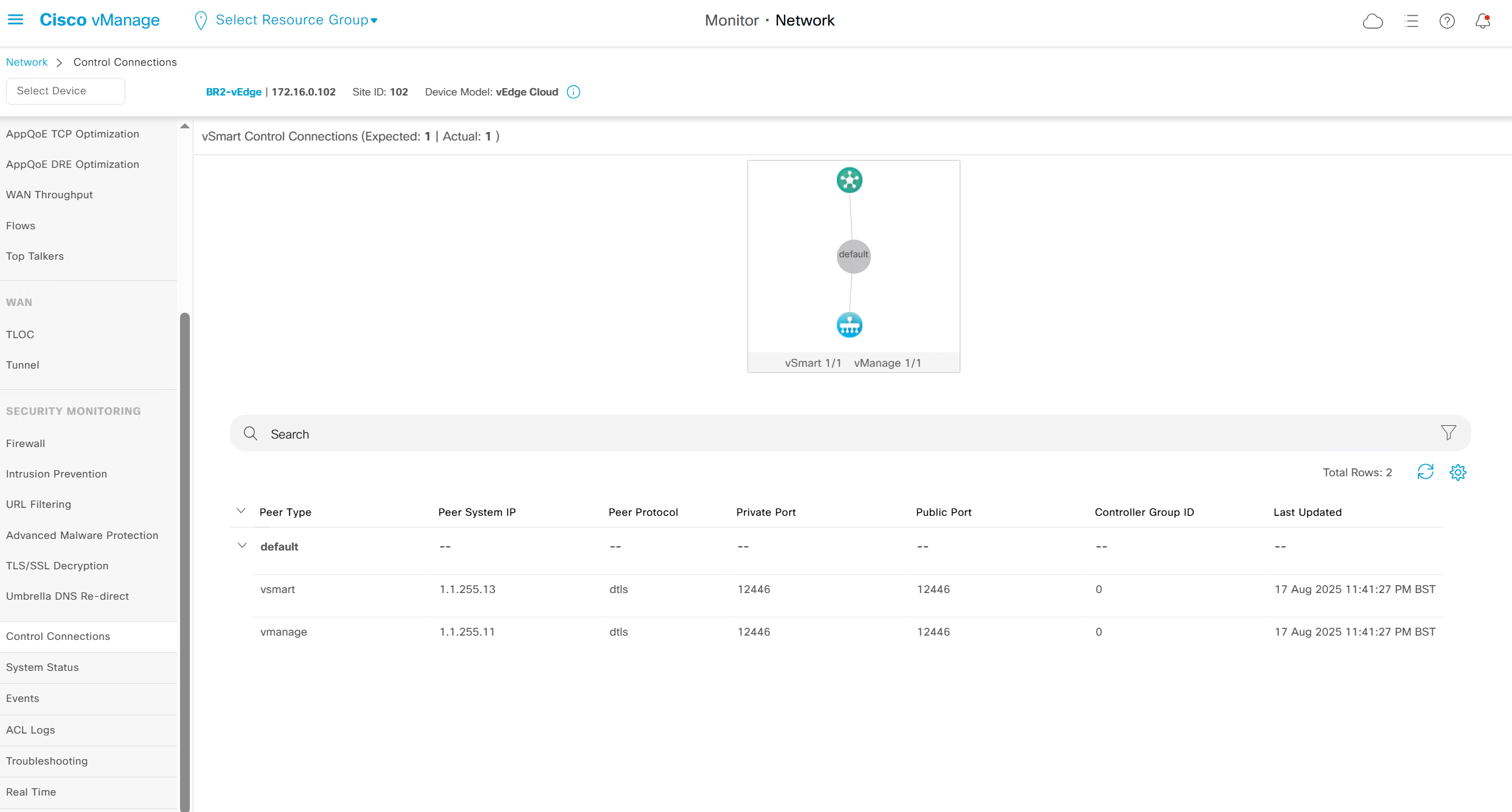
BR3-cEdge
tclsh
puts [open "bootflash:root_ca.cer" w+] {
-----BEGIN CERTIFICATE-----
MIIDnzCCAoegAwIBAgIQYJ1ACvIQRIlBAEITkoGNuzANBgkqhkiG9w0BAQsFADBi
MRUwEwYKCZImiZPyLGQBGRYFY2lzY28xEzARBgoJkiaJk/IsZAEZFgNzeXMxEzAR
BgoJkiaJk/IsZAEZFgNvcjIxHzAdBgNVBAMTFm9yMi1XSU4tVlEwOEc2VTk4R0Yt
Q0EwHhcNMjUwNzA2MjE1MjA1WhcNMzAwNzA2MjIwMjA1WjBiMRUwEwYKCZImiZPy
LGQBGRYFY2lzY28xEzARBgoJkiaJk/IsZAEZFgNzeXMxEzARBgoJkiaJk/IsZAEZ
FgNvcjIxHzAdBgNVBAMTFm9yMi1XSU4tVlEwOEc2VTk4R0YtQ0EwggEiMA0GCSqG
SIb3DQEBAQUAA4IBDwAwggEKAoIBAQCr6cjaoJz3vzgHlQ1hzhuy5WfIL/Ao0isM
ltIaGL+Z+9WftM1hNh10YECbxR71+lIpQKyBQTXQz8Of4nycxHjoI3dQdUvEYb8H
fysDXh4lYjQ60x82e5c7f1KPbD+AOhC31Zw1dgReMlPIuaa9LK903+z0FRnuCHaI
EG/Z9uCmv3JC22NgL69hscZc+NUGymMy1iBPN8G4EBkgqNVZ+zlRf/adW0JxEdc6
Sy53bp586/fXziRTW++jgdnhvfpn+VJ+BdG88/rEgMl7PUQE95lq4dih7qx0+OXu
ihFwQQvFxvi3dyqWWc0C1RKHPHtYQFz8rRuBJrR+uzgc0lVhrNHdAgMBAAGjUTBP
MAsGA1UdDwQEAwIBhjAPBgNVHRMBAf8EBTADAQH/MB0GA1UdDgQWBBQ/bI8yZeKD
fgjmmeWorjGo25t5hzAQBgkrBgEEAYI3FQEEAwIBADANBgkqhkiG9w0BAQsFAAOC
AQEAdtt6aiABkDDg/mAlcZfFPHcqmEEvQaMPeBaUqvfZKNrFVO8GMb9kingZJ62n
K05x5wE3tHy3jBmAl6eHZ/nUjXS11C06NwZMHpcDhty5BcDN08oEYdLF24upisNA
aRLOBhyEtKI9VKLAWfMkpWYEd/dqgVWs67GjAFT0Osgva9QHbz24iT6/c09jbZMt
41opmxacw8FFZcHMH9Afv1fIW9PwscrdlgjSSHR4XQLyDbyuDGsolzeh9PUVyPOd
f+/LYkLwH9jVcHlxl4Oy7MHRPtcbG9T3+vQGLjSAXu3Ybrl2R9Tn/sz5lYs44EEB
mqCxT00LxB3et6jAxJlEyE5vCw==
-----END CERTIFICATE-----
}
exit
controller-mode enable
request platform software sdwan root-cert-chain install bootflash:root_ca.cer
hostname BR3-cEdge
system
system-ip 172.16.0.103
site-id 103
organization-name or2.sys.cisco
vbond vbond.or.sys.cisco
ip host vbond.or.sys.cisco 1.1.0.12
ip route 0.0.0.0 0.0.0.0 1.1.1.250
interface GigabitEthernet1
ip address 1.1.1.103 255.255.255.0
no shutdown
no mop enabled
no mop sysid
negotiation auto
interface Tunnel1
no shutdown
ip unnumbered GigabitEthernet1
tunnel source GigabitEthernet1
tunnel mode sdwan
exit
sdwan
interface GigabitEthernet1
tunnel-interface
encapsulation ipsec
color biz-internet
allow-service all
exit
exit
commit
request platform software sdwan vedge_cloud activate chassis-number C8K-FF74B9C0-47EC-6B46-6F06-B63A33303C0F token 3d4817593d9e42d19092a8a7804051aaFilter Onboarded Nodes
Type “In Sync” in filter on top however it is typed such as “in ync” and onboarded nodes will show
Web Interface

Control Status tells us about the down control connections
Site health shows us status of all the IPSec VPN tunnels between sites
This tells us that BR1-cEdge has 3 tunnels up out of 4, one is down due to BR2-vEdge being down
R1-cEdge and R2-cEdge has 2 tunnels since both are part of same site and they have tunnels to internet based 2 branch sites (out of 3 as site 102 is down)
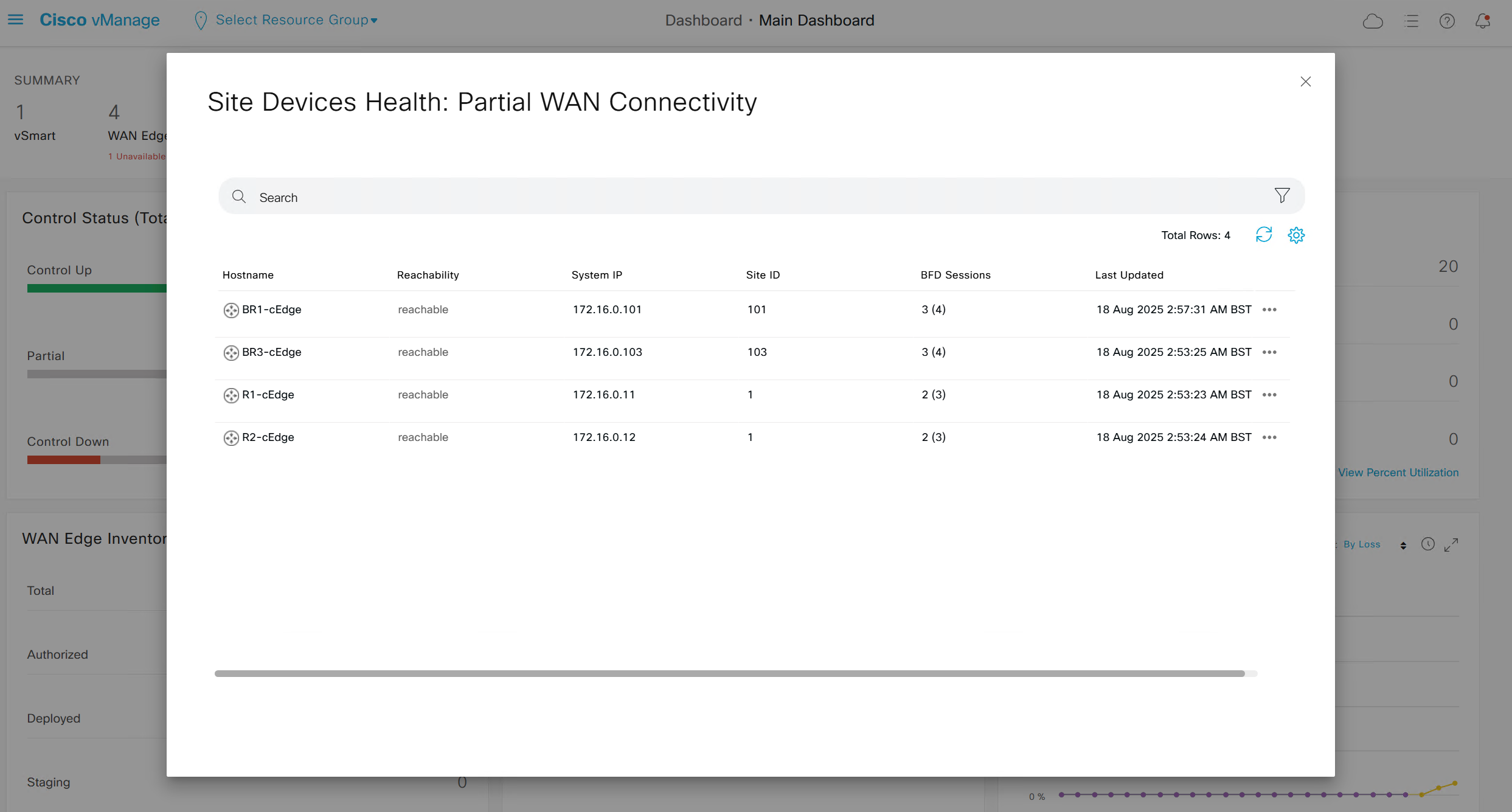
If we click on number 4 we see
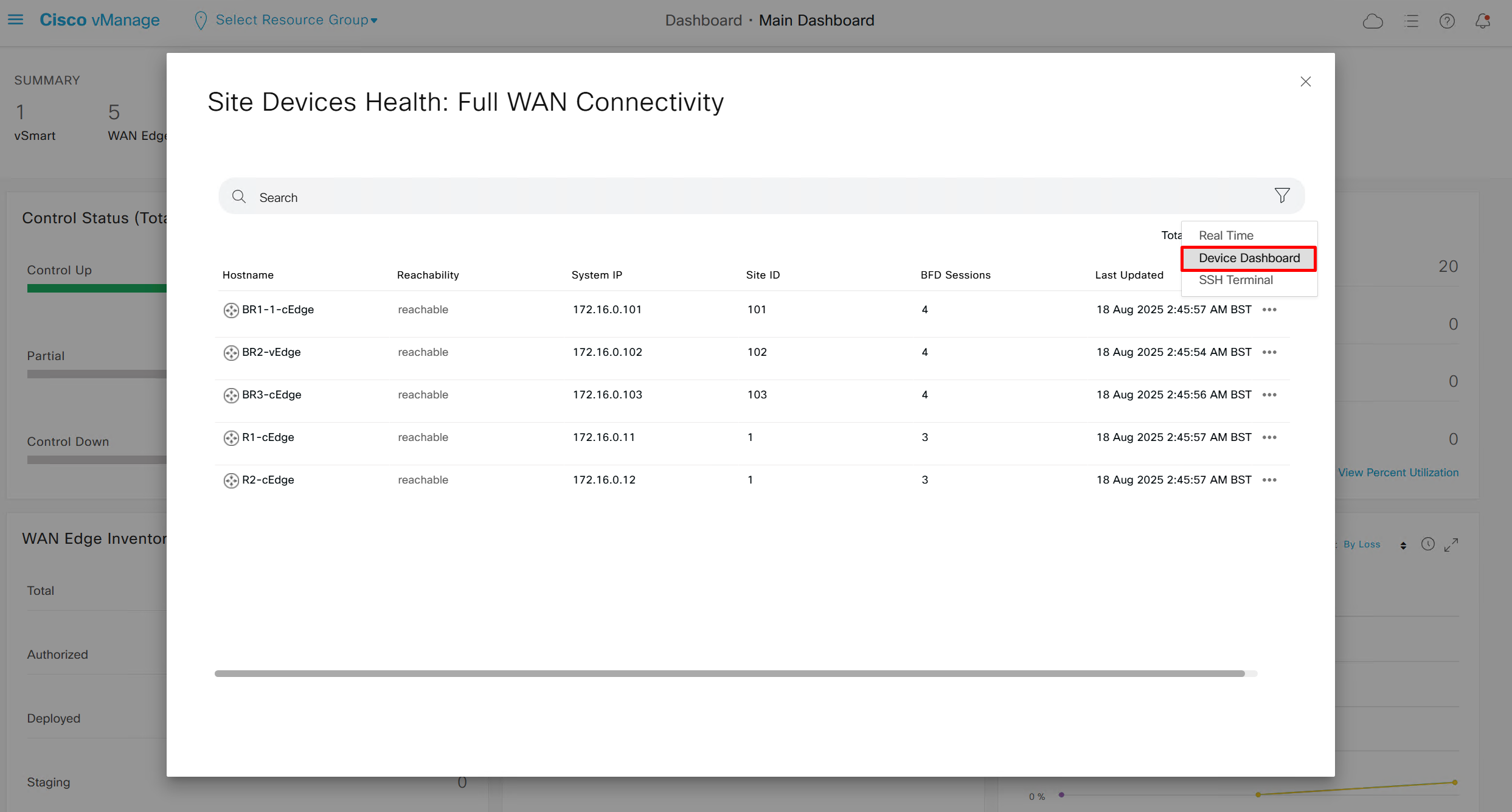
then navigate to “Tunnels” and you will see all the tunnels from one router to remote routers

Navigate to “Real Time” > Device Options: Tunnel BFD Statistics

Inventory and CPU, memory and hardware health
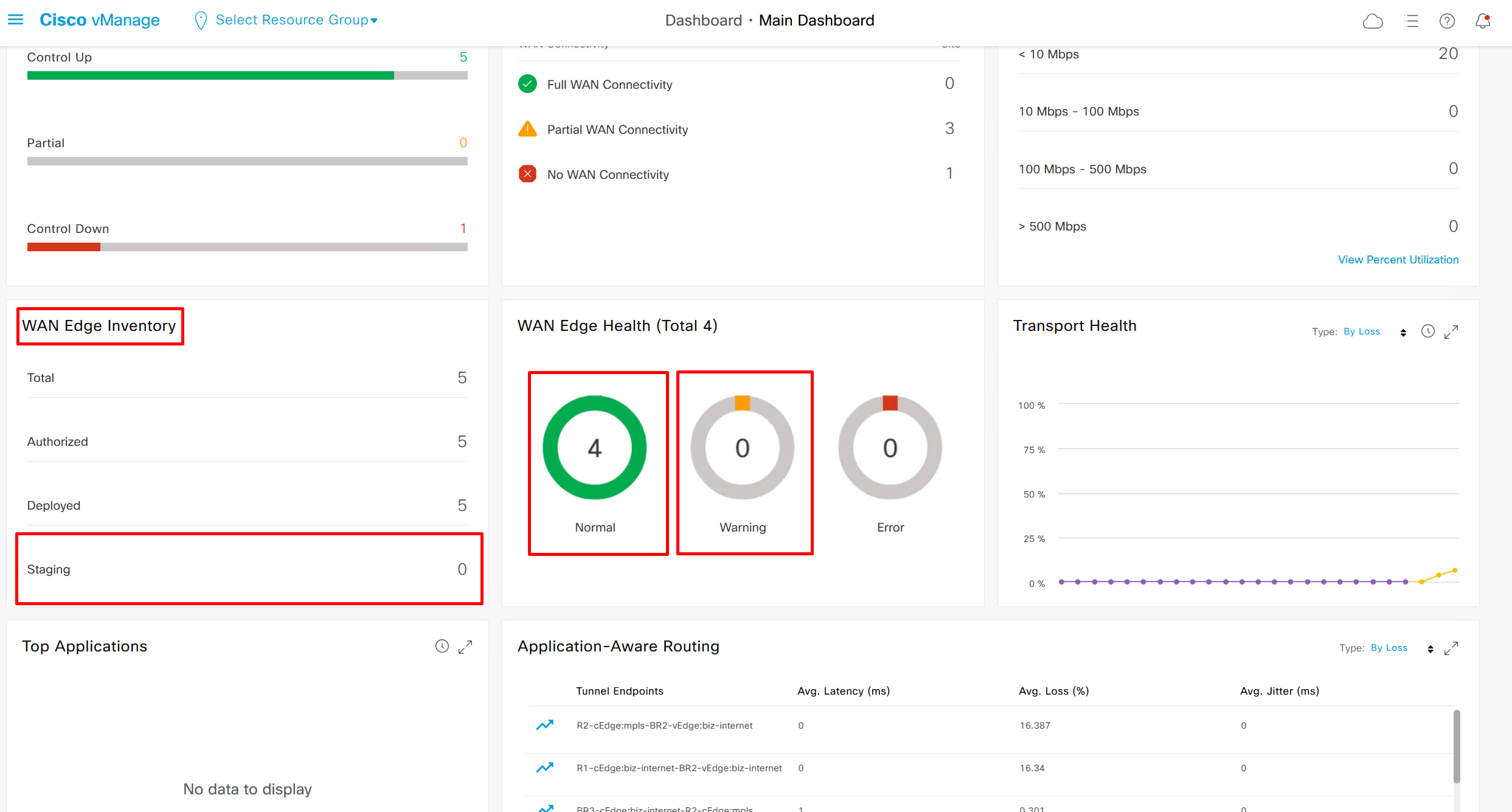
If we click on 4 we see this
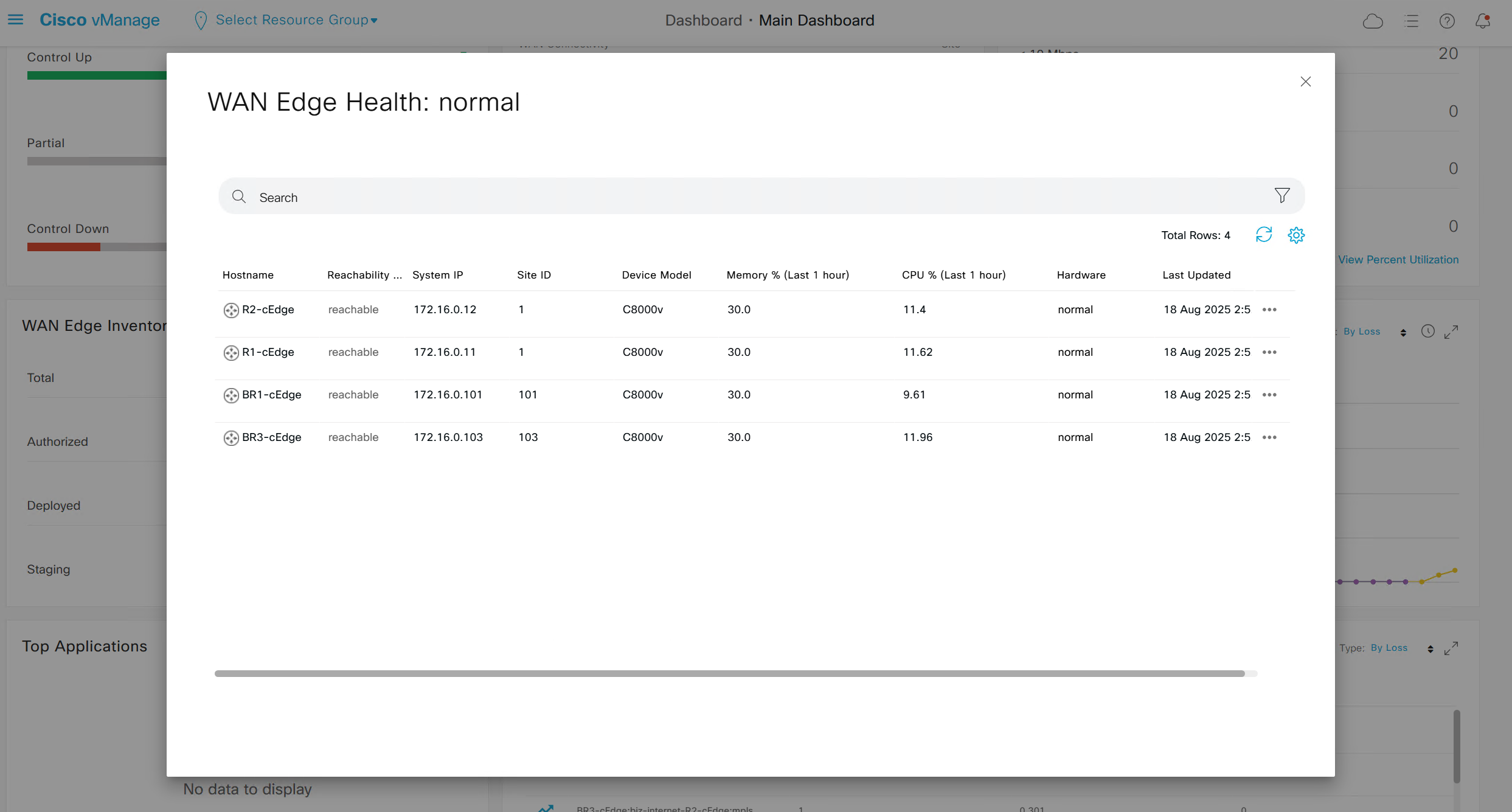
Onboarding cEdge “CSR1K” because vEdge is crashing, may be because of version 20.6.1, download new version
Router(tcl)#puts [open "bootflash:root_ca.cer" w+] {
+>-----BEGIN CERTIFICATE-----
+>MIIDnzCCAoegAwIBAgIQYJ1ACvIQRIlBAEITkoGNuzANBgkqhkiG9w0BAQsFADBi
+>MRUwEwYKCZImiZPyLGQBGRYFY2lzY28xEzARBgoJkiaJk/IsZAEZFgNzeXMxEzAR
+>BgoJkiaJk/IsZAEZFgNvcjIxHzAdBgNVBAMTFm9yMi1XSU4tVlEwOEc2VTk4R0Yt
+>Q0EwHhcNMjUwNzA2MjE1MjA1WhcNMzAwNzA2MjIwMjA1WjBiMRUwEwYKCZImiZPy
+>LGQBGRYFY2lzY28xEzARBgoJkiaJk/IsZAEZFgNzeXMxEzARBgoJkiaJk/IsZAEZ
+>FgNvcjIxHzAdBgNVBAMTFm9yMi1XSU4tVlEwOEc2VTk4R0YtQ0EwggEiMA0GCSqG
+>SIb3DQEBAQUAA4IBDwAwggEKAoIBAQCr6cjaoJz3vzgHlQ1hzhuy5WfIL/Ao0isM
+>ltIaGL+Z+9WftM1hNh10YECbxR71+lIpQKyBQTXQz8Of4nycxHjoI3dQdUvEYb8H
+>fysDXh4lYjQ60x82e5c7f1KPbD+AOhC31Zw1dgReMlPIuaa9LK903+z0FRnuCHaI
+>EG/Z9uCmv3JC22NgL69hscZc+NUGymMy1iBPN8G4EBkgqNVZ+zlRf/adW0JxEdc6
+>Sy53bp586/fXziRTW++jgdnhvfpn+VJ+BdG88/rEgMl7PUQE95lq4dih7qx0+OXu
+>ihFwQQvFxvi3dyqWWc0C1RKHPHtYQFz8rRuBJrR+uzgc0lVhrNHdAgMBAAGjUTBP
+>MAsGA1UdDwQEAwIBhjAPBgNVHRMBAf8EBTADAQH/MB0GA1UdDgQWBBQ/bI8yZeKD
+>fgjmmeWorjGo25t5hzAQBgkrBgEEAYI3FQEEAwIBADANBgkqhkiG9w0BAQsFAAOC
+>AQEAdtt6aiABkDDg/mAlcZfFPHcqmEEvQaMPeBaUqvfZKNrFVO8GMb9kingZJ62n
+>K05x5wE3tHy3jBmAl6eHZ/nUjXS11C06NwZMHpcDhty5BcDN08oEYdLF24upisNA
+>aRLOBhyEtKI9VKLAWfMkpWYEd/dqgVWs67GjAFT0Osgva9QHbz24iT6/c09jbZMt
+>41opmxacw8FFZcHMH9Afv1fIW9PwscrdlgjSSHR4XQLyDbyuDGsolzeh9PUVyPOd
+>f+/LYkLwH9jVcHlxl4Oy7MHRPtcbG9T3+vQGLjSAXu3Ybrl2R9Tn/sz5lYs44EEB
+>mqCxT00LxB3et6jAxJlEyE5vCw==
+>-----END CERTIFICATE-----
+>}
Router(tcl)#exitFirst stop the PnP service so that the SD-WAN software packages can install
pnpa service discovery stopOnce the PnP service has been stopped, we tell the router to install all underlying SD-WAN packages if necessary. Depending on the CSR1k software image, this may not be necessary.
request platform software sdwan software resetThe last step is to verify the software image using the following command
request platform software sdwan software upgrade-confirmsee that the sdwan software is ACTIVE and CONFIRMED as highlighted below.
show sdwan soft
VERSION ACTIVE DEFAULT PREVIOUS CONFIRMED TIMESTAMP
---------------------------------------------------------------------------------
16.12.4.0.4480 true true false user 2022-04-03T08:20:13-00:00
Total Space:388M Used Space:87M Available Space:297Min newer CSR1000v versions we dont have to do above and we can directly do
controller-mode enableOnce the router loads up with the SD-WAN software, we can go ahead and configure the minimal configuration required to join the SD-WAN overlay fabric. Notice that when the cEdge router runs in Controller mode (basically SD-WAN mode), we enter the configuration mode using the “config-transaction” command instead of the well-known “configure terminal” or simply “conf t”.
Notice something very important – the Tunnel keyword in the “interface Tunnel” command should always be with a capital T. It is not like in a regular Cisco IOS where you can create a new tunnel using the “interface tunnel 1” command.
config-transaction
hostname cEdge
!
int GigabitEthernet1
ip address 39.3.1.1 255.255.255.0
no shut
!
int GigabitEthernet2
ip address 10.10.1.1 255.255.255.0
no shut
!
ip route 0.0.0.0 0.0.0.0 39.3.1.254
ip route 0.0.0.0 0.0.0.0 10.10.1.254
ip host vbond.networkacademy.io 10.1.1.10
!
system
system-ip 1.1.1.1
site-id 1
organization-name "networkacademy-io"
vbond vbond.networkacademy.io
commitsdwan
int GigabitEthernet1
tunnel-interface
color biz-internet
encapsulation ipsec
!
int GigabitEthernet2
tunnel-interface
color mpls restrict
encapsulation ipsec
!
interface Tunnel 1
ip unnumbered GigabitEthernet1
tunnel source GigabitEthernet1
tunnel mode sdwan
!
interface Tunnel 2
ip unnumbered GigabitEthernet2
tunnel source GigabitEthernet2
tunnel mode sdwan
commitInstall root ca cert through tclsh and same steps can be followed as C8000v
Template Configuration on Edges and Controllers
Highlighted config is the one we need to configure the template
Each “section” will need a “feature template”
Remember that we need to configure system, vpn 0 (routing table for transport) and interface feature templates
BR1-1-cEdge#show sdwan running-config
system
system-ip 172.16.0.101
site-id 101
admin-tech-on-failure
organization-name or2.sys.cisco
vbond vbond.or.sys.cisco
!
memory free low-watermark processor 68484
no service tcp-small-servers
no service udp-small-servers
platform console serial
platform qfp utilization monitor load 80
platform punt-keepalive disable-kernel-core
hostname BR1-1-cEdge
username admin privilege 15 secret 5 $1$3/FD$EA4V.gZeQ6hMyUG2ct/ax.
no ip finger
no ip rcmd rcp-enable
no ip rcmd rsh-enable
no ip dhcp use class
ip host vbond.or.sys.cisco 1.1.0.12
ip route 0.0.0.0 0.0.0.0 1.1.1.250
ip ssh version 2
no ip http server
ip http secure-server
ip nat settings central-policy
ip nat settings gatekeeper-size 1024
interface GigabitEthernet1
no shutdown
ip address 1.1.1.101 255.255.255.0
no mop enabled
no mop sysid
negotiation auto
exit
interface GigabitEthernet2
no shutdown
no mop enabled
no mop sysid
negotiation auto
exit
interface GigabitEthernet3
no shutdown
no mop enabled
no mop sysid
negotiation auto
exit
interface GigabitEthernet4
no shutdown
no mop enabled
no mop sysid
negotiation auto
exit
interface Tunnel1
no shutdown
ip unnumbered GigabitEthernet1
tunnel source GigabitEthernet1
tunnel mode sdwan
exit
aaa authentication enable default enable
aaa authentication login default local
aaa authorization console
aaa authorization exec default local
login on-success log
line aux 0
!
line con 0
stopbits 1
!
line vty 0 4
!
line vty 5 80
!
sdwan
interface GigabitEthernet1
tunnel-interface
encapsulation ipsec
color biz-internet
allow-service all
no allow-service bgp
allow-service dhcp
allow-service dns
allow-service icmp
no allow-service sshd
no allow-service netconf
no allow-service ntp
no allow-service ospf
no allow-service stun
allow-service https
no allow-service snmp
no allow-service bfd
exit
exit
appqoe
no tcpopt enable
no dreopt enable
!
omp
no shutdown
graceful-restart
no as-dot-notation
address-family ipv4
advertise connected
advertise static
!
address-family ipv6
advertise connected
advertise static
!
!
!
licensing config enable false
licensing config privacy hostname false
licensing config privacy version false
licensing config utility utility-enable false
security
ipsec
integrity-type ip-udp-esp esp
!
!
sslproxy
no enable
rsa-key-modulus 2048
certificate-lifetime 730
eckey-type P256
ca-tp-label PROXY-SIGNING-CA
settings expired-certificate drop
settings untrusted-certificate drop
settings unknown-status drop
settings certificate-revocation-check none
settings unsupported-protocol-versions drop
settings unsupported-cipher-suites drop
settings failure-mode close
settings minimum-tls-ver TLSv1
dual-side optimization enable
!

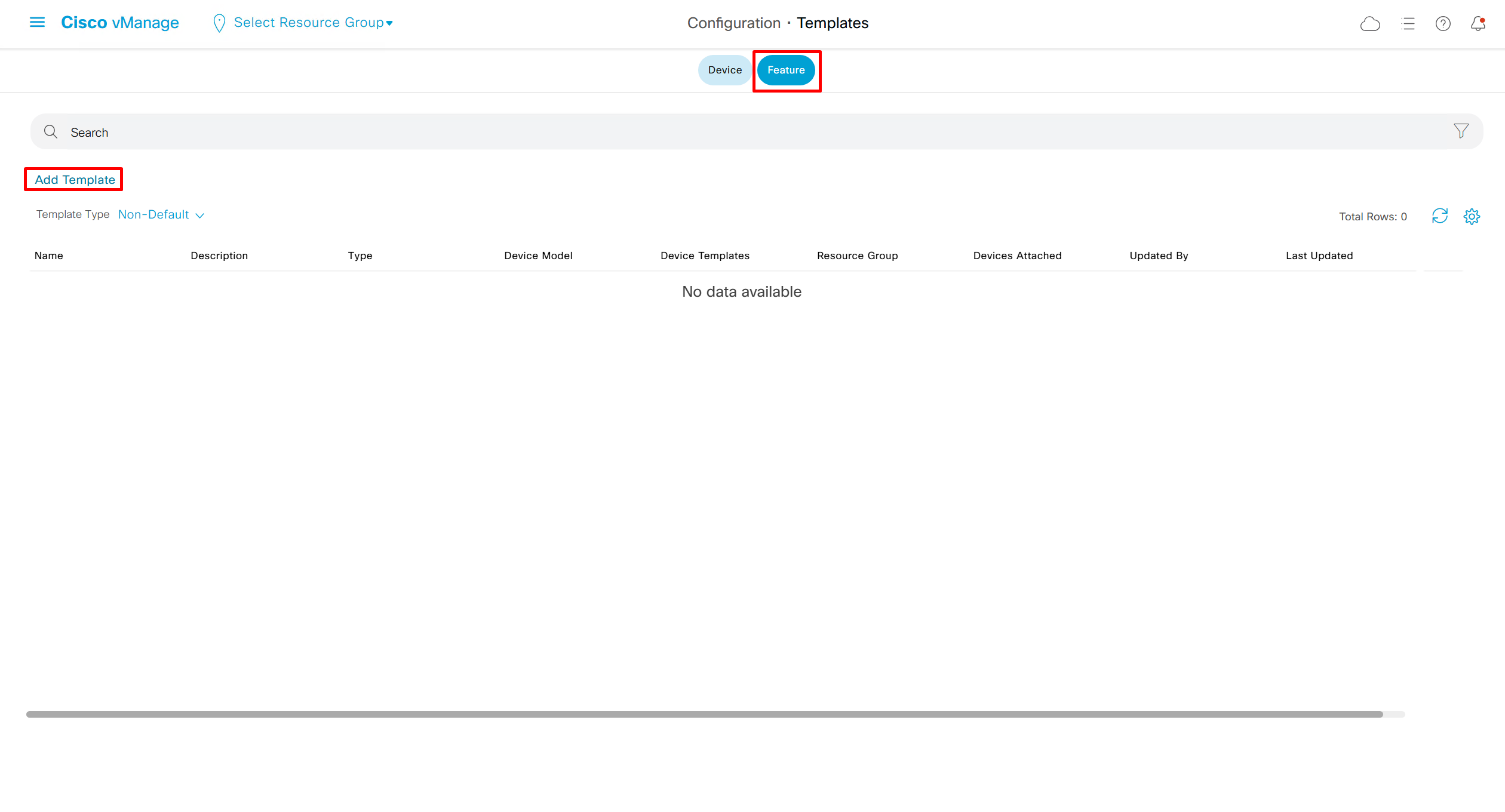
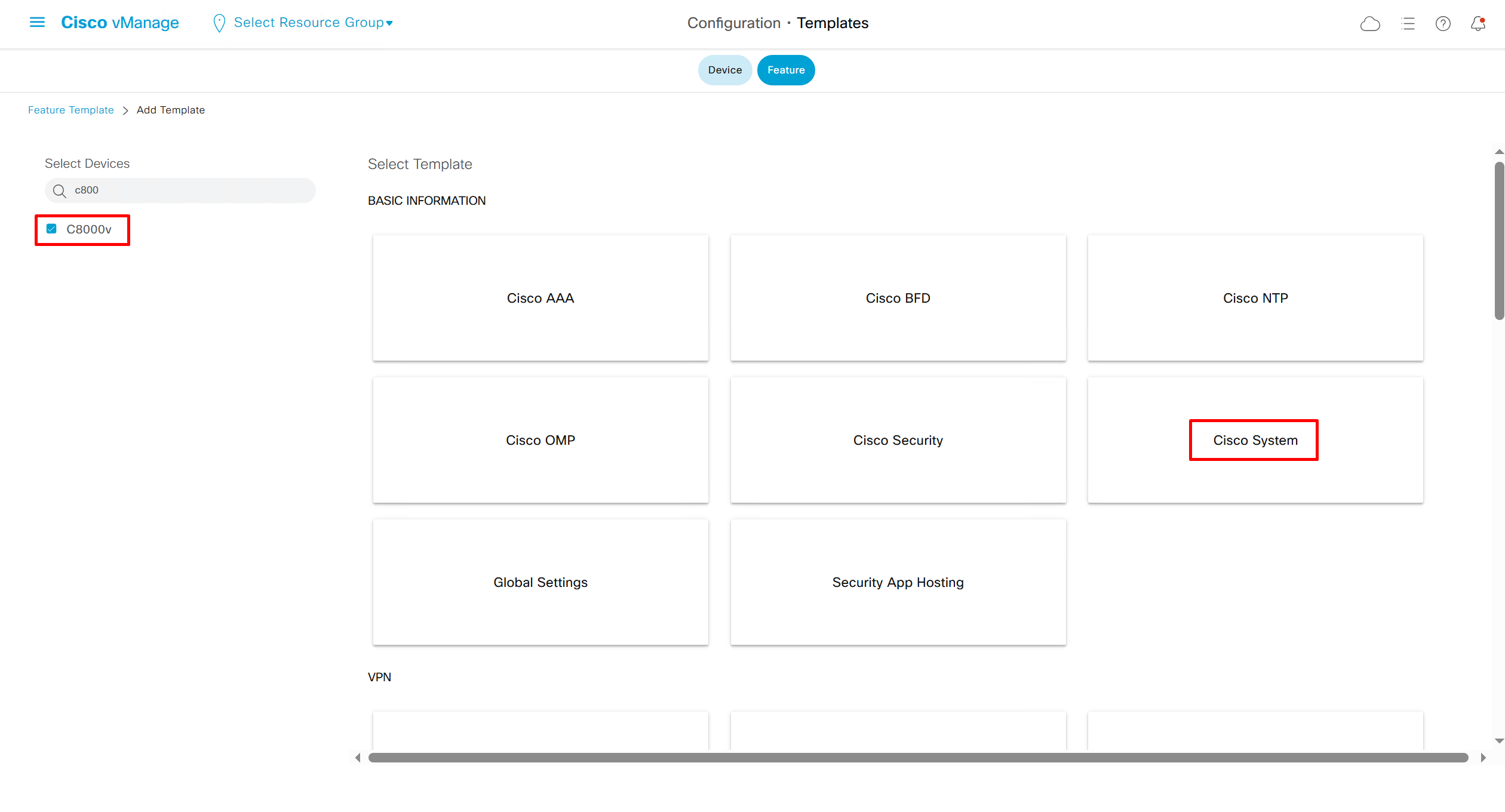
Device Specific variables mean that value will be taken from us at the time when we attach the template to device
Global means that all the devices that are attached to this template will inherit same static value
Each section of the running-config will require a feature template

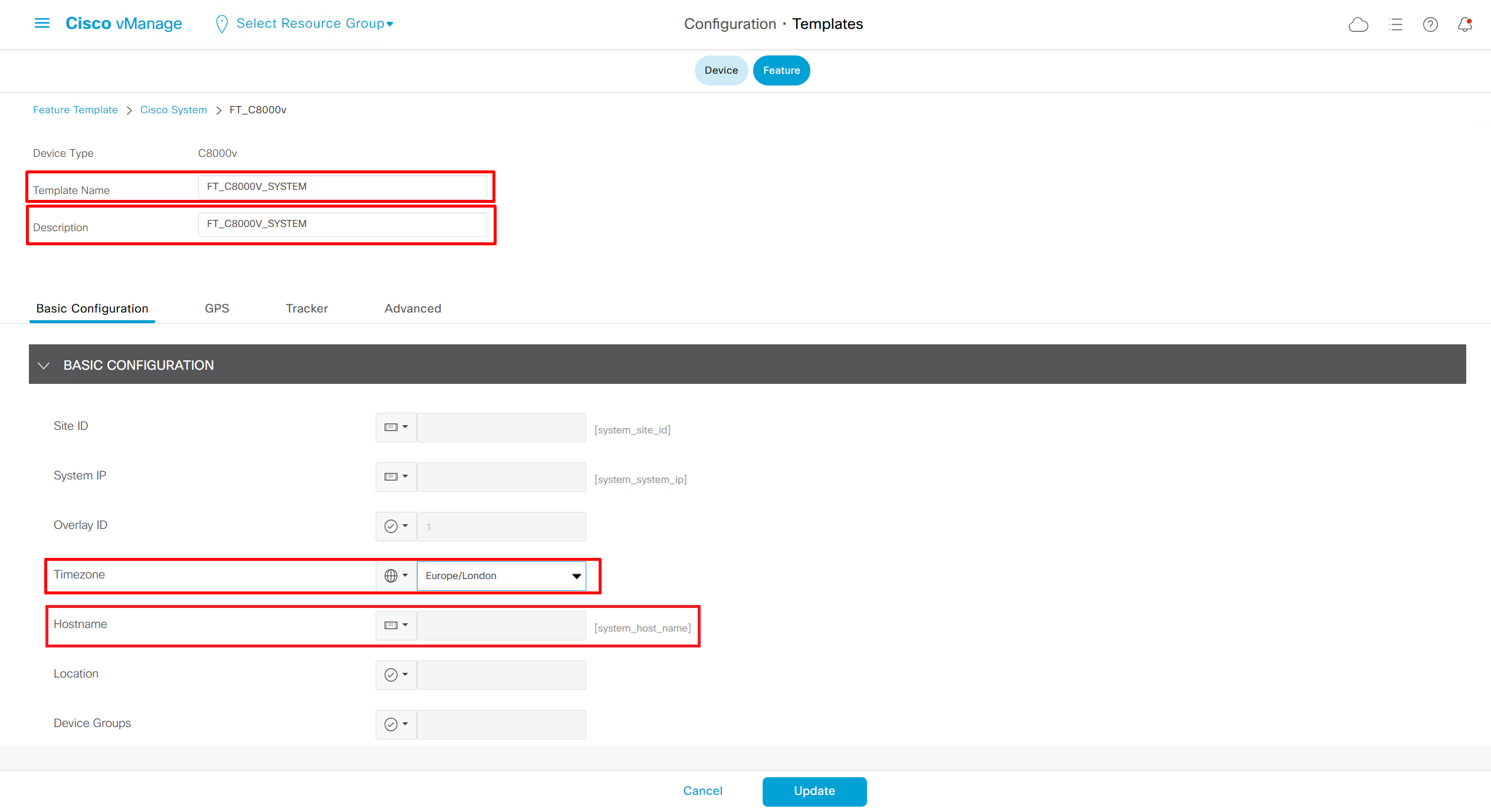
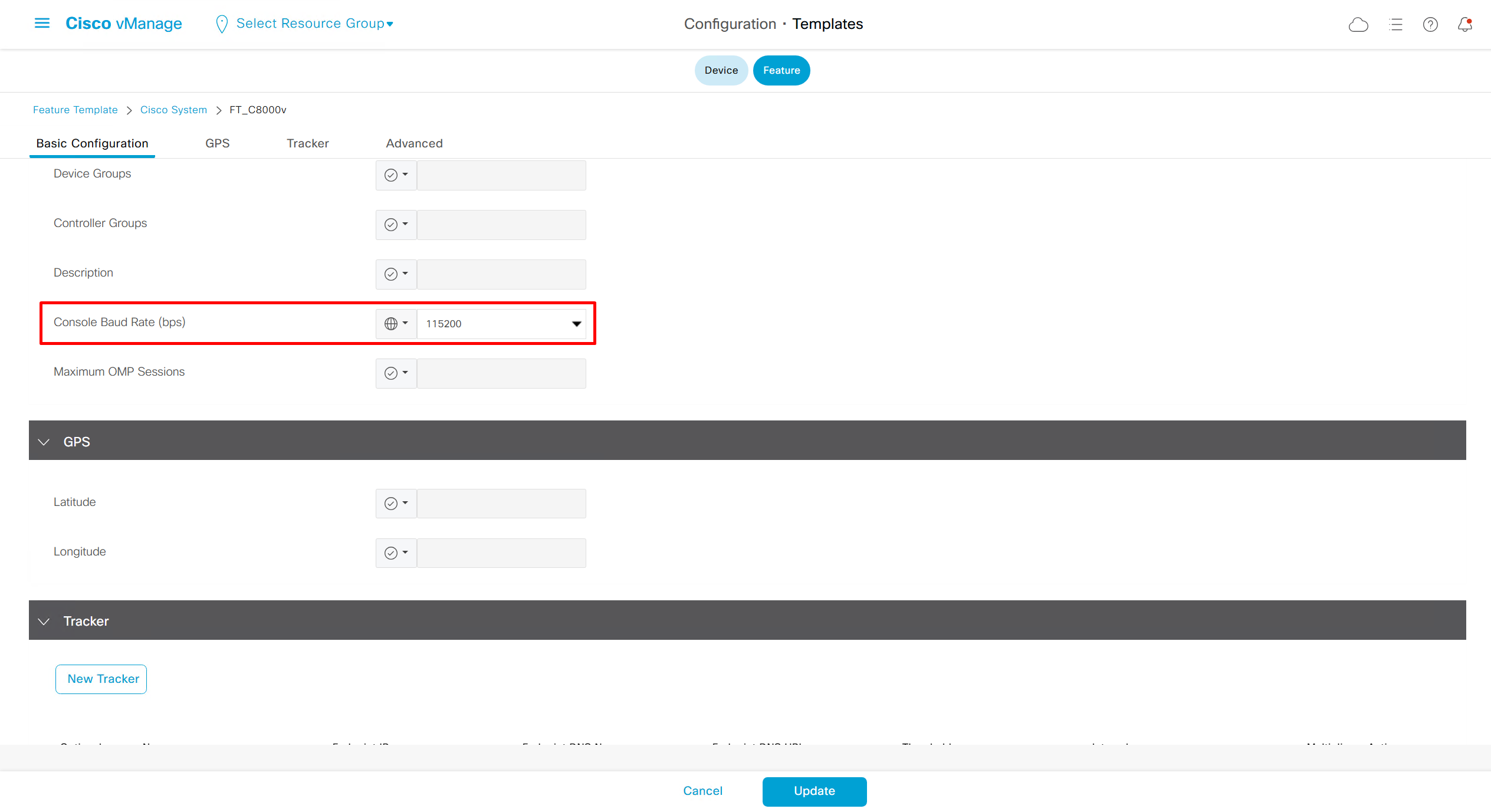
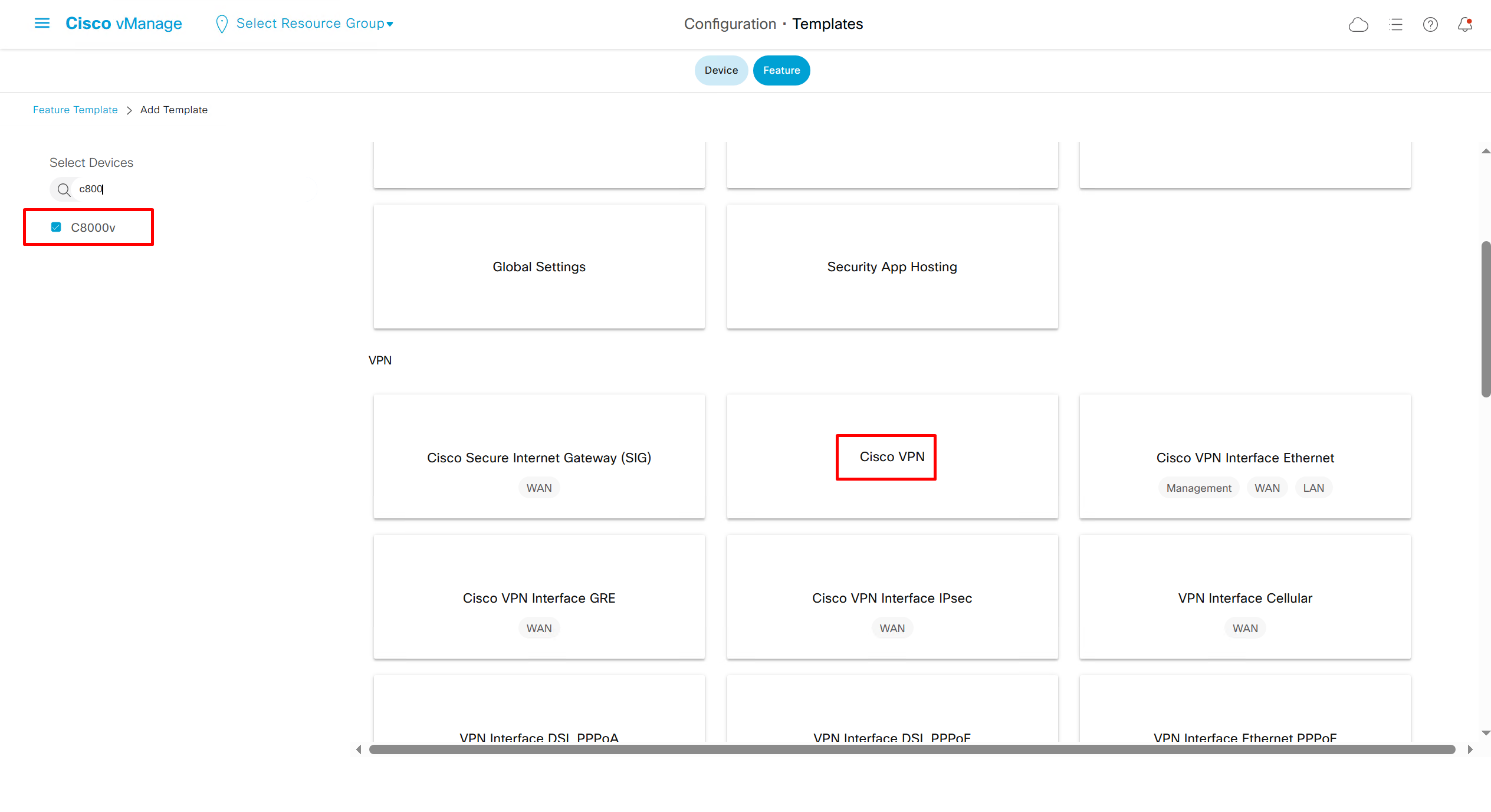
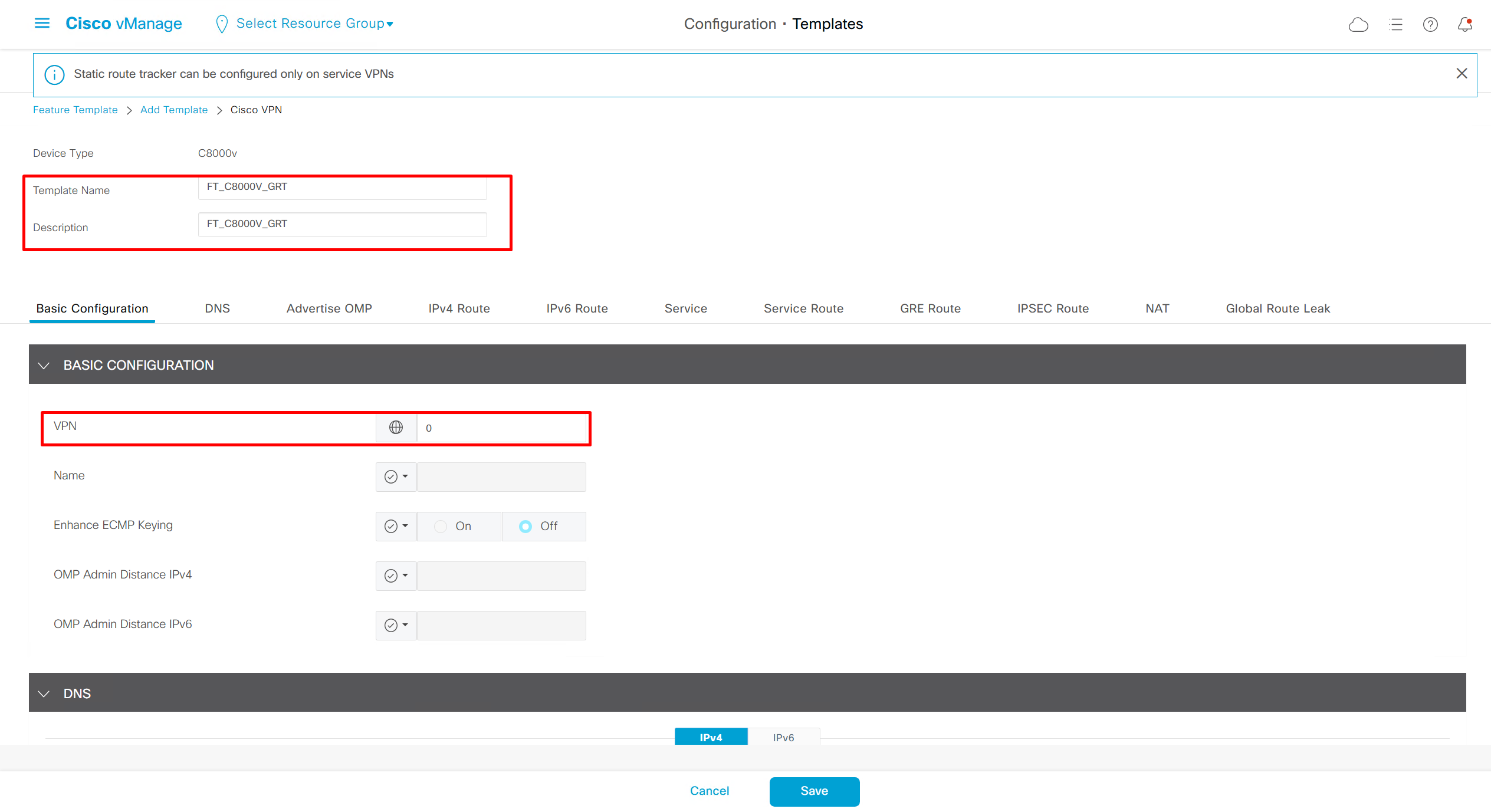
Enhance ECMP Keyring when turned on, also considers the source and destination port to calculate the ECMP
DNS and Static IPv4 routes will come under the GRT
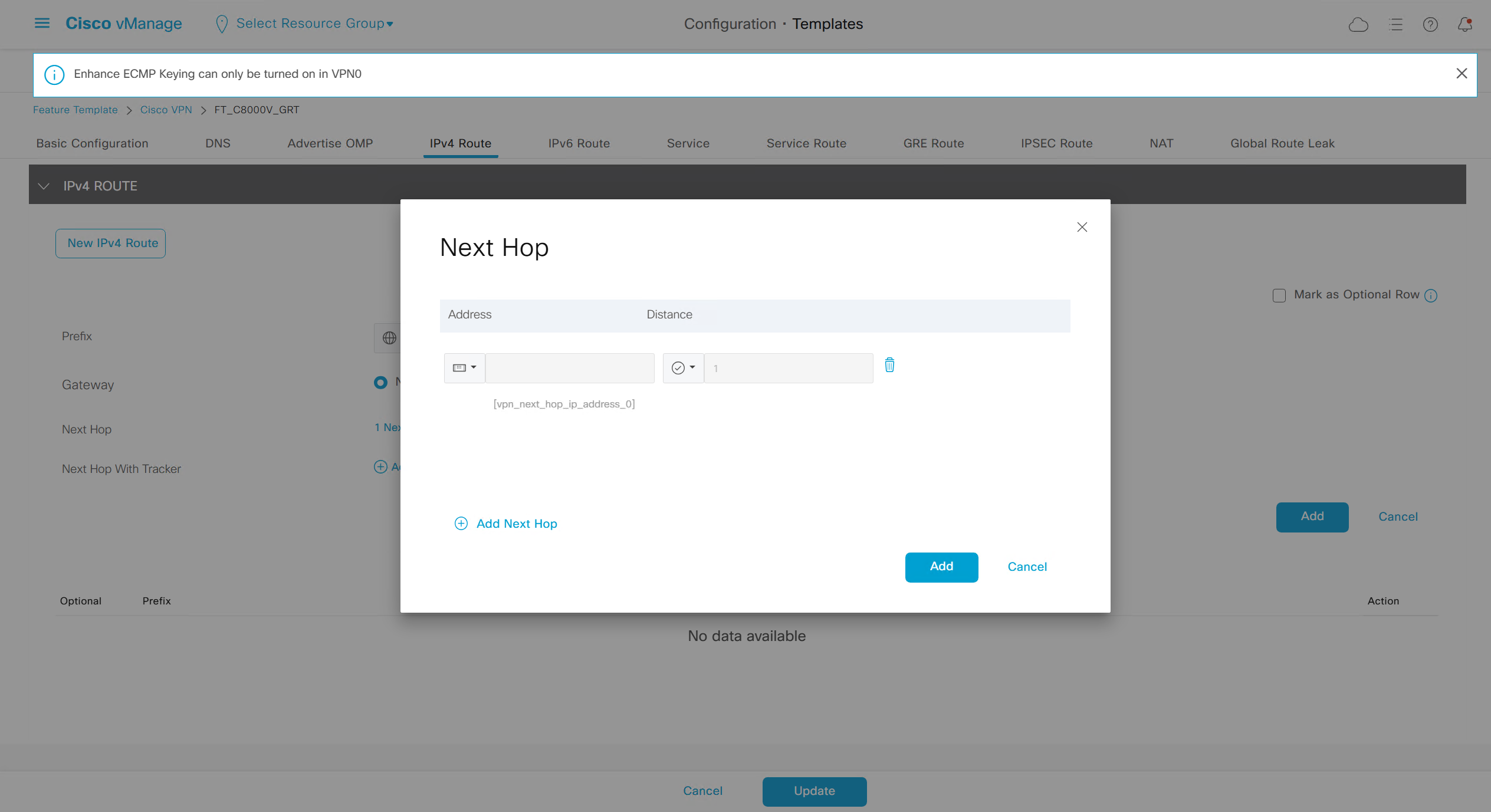
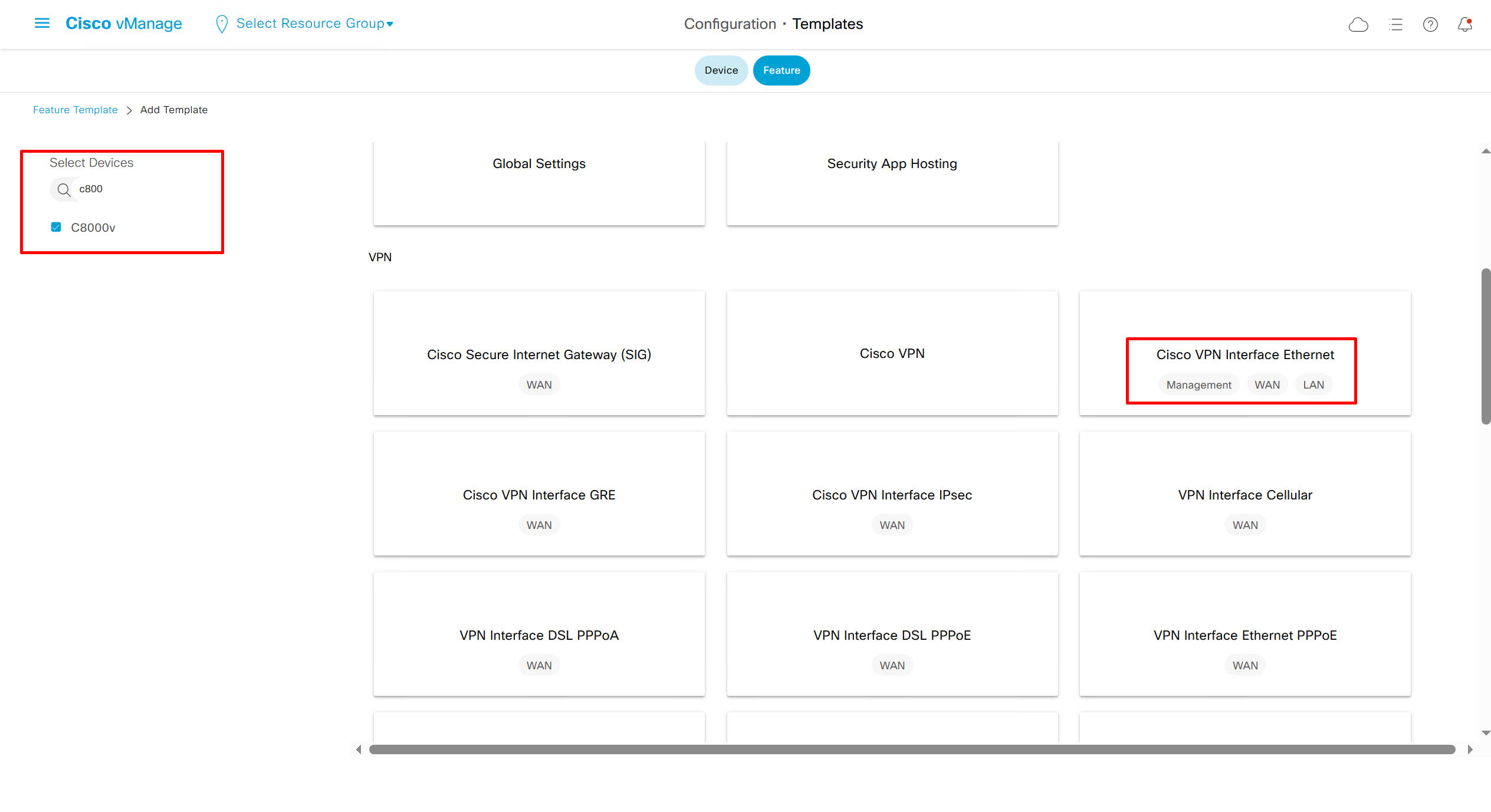
If devices models are different then each device model will need its own feature due to difference in interface names > Cisco VPN interface ethernet template
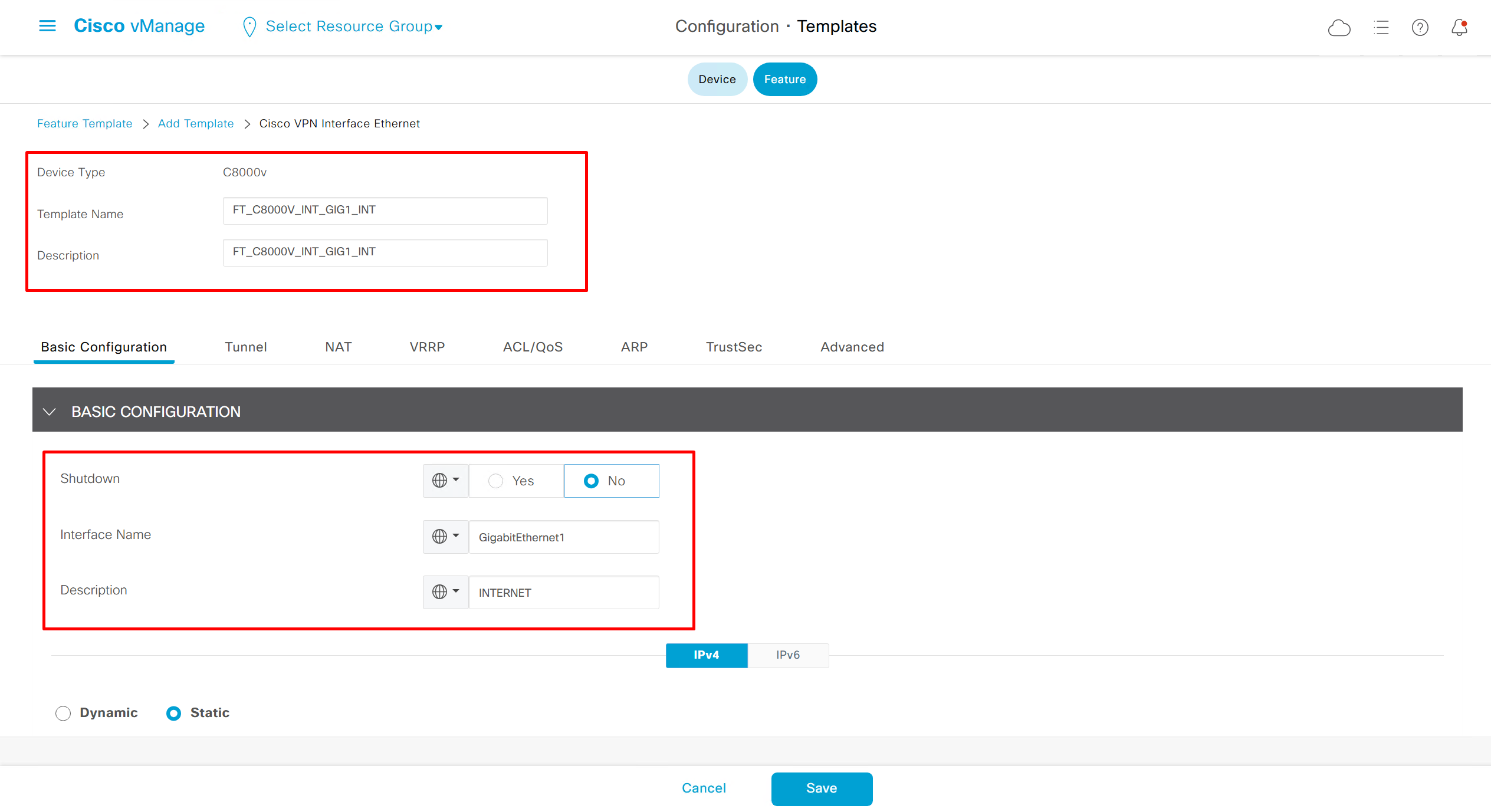
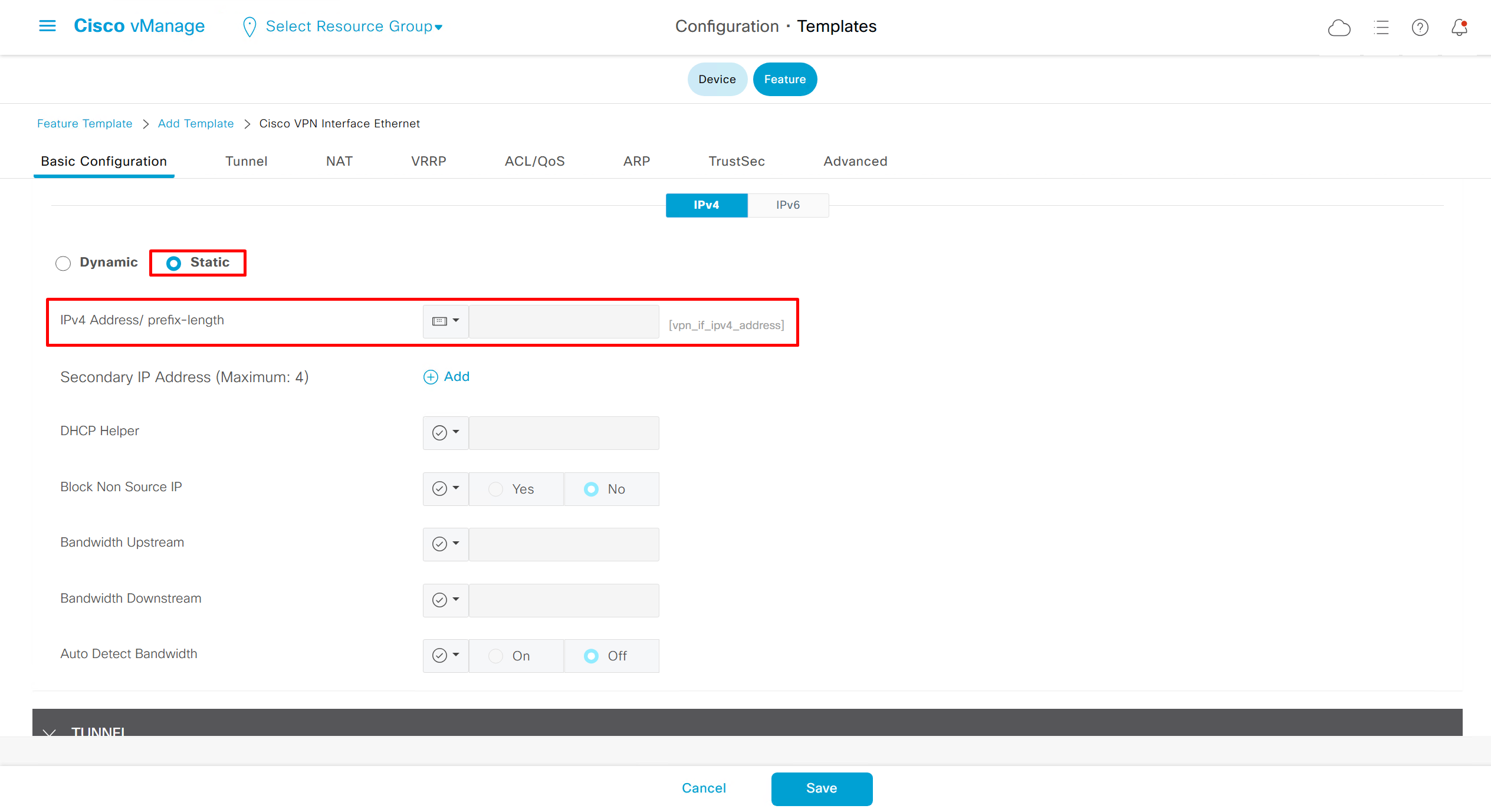

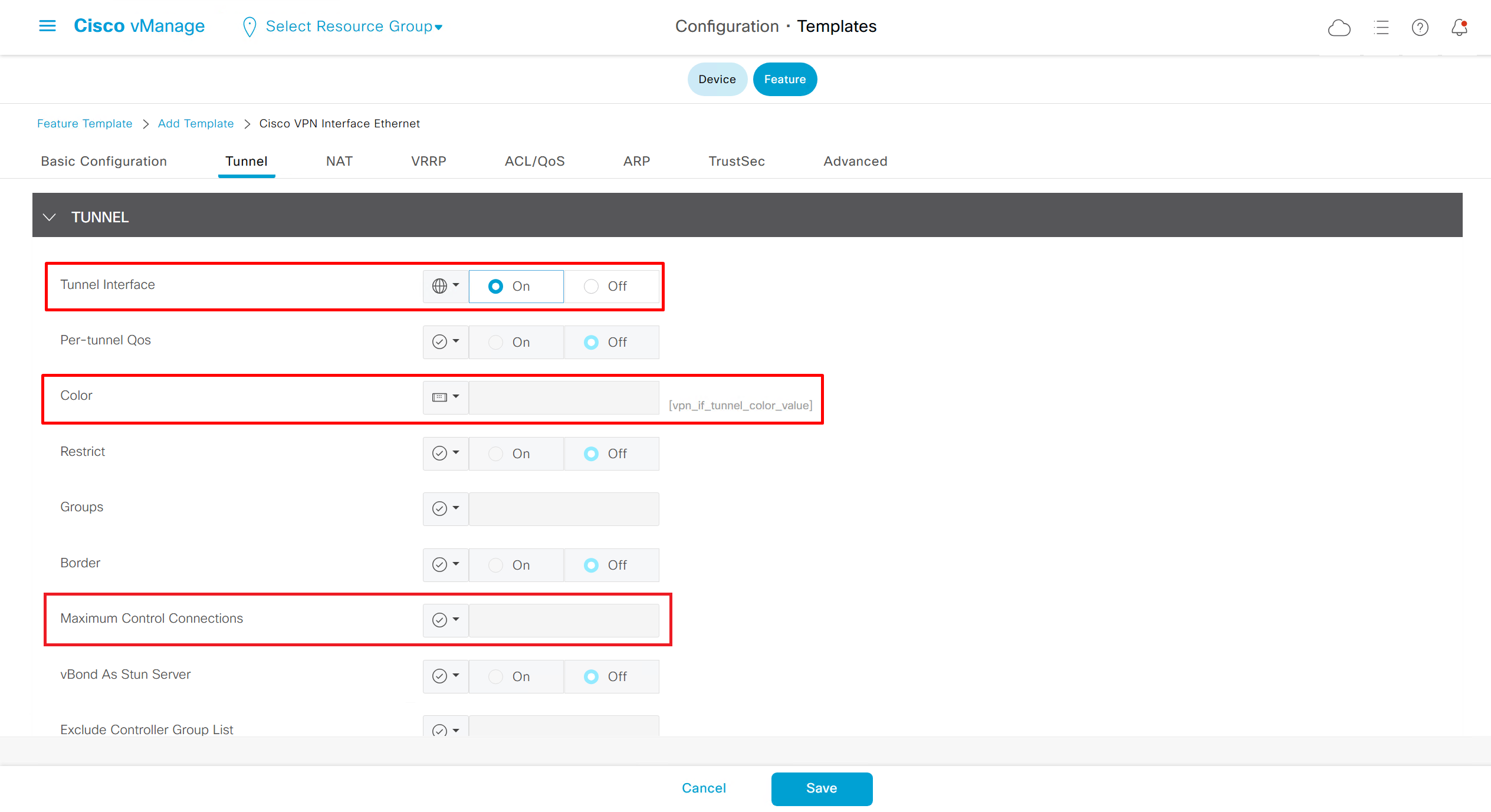
if this color does not have reachability to controllers such as MPLS connection then make Maximum Control Connections to 0
Setting Maximum Control Connections to 0 on MPLS only sites caused loss of control connections to all controllers and because of loss of connections caused rollback because MPLS was only connection to site
Maximum control connections allow sites to have no connection to controllers (not just vmanage, but vsmart and vbond also) from that color, but still have “data tunnels” from that color
Exclude Controller Group List: This is group of controllers that you dont want the edge to connect to, this is important when we dont want edge to connect to vsmart in far regions.
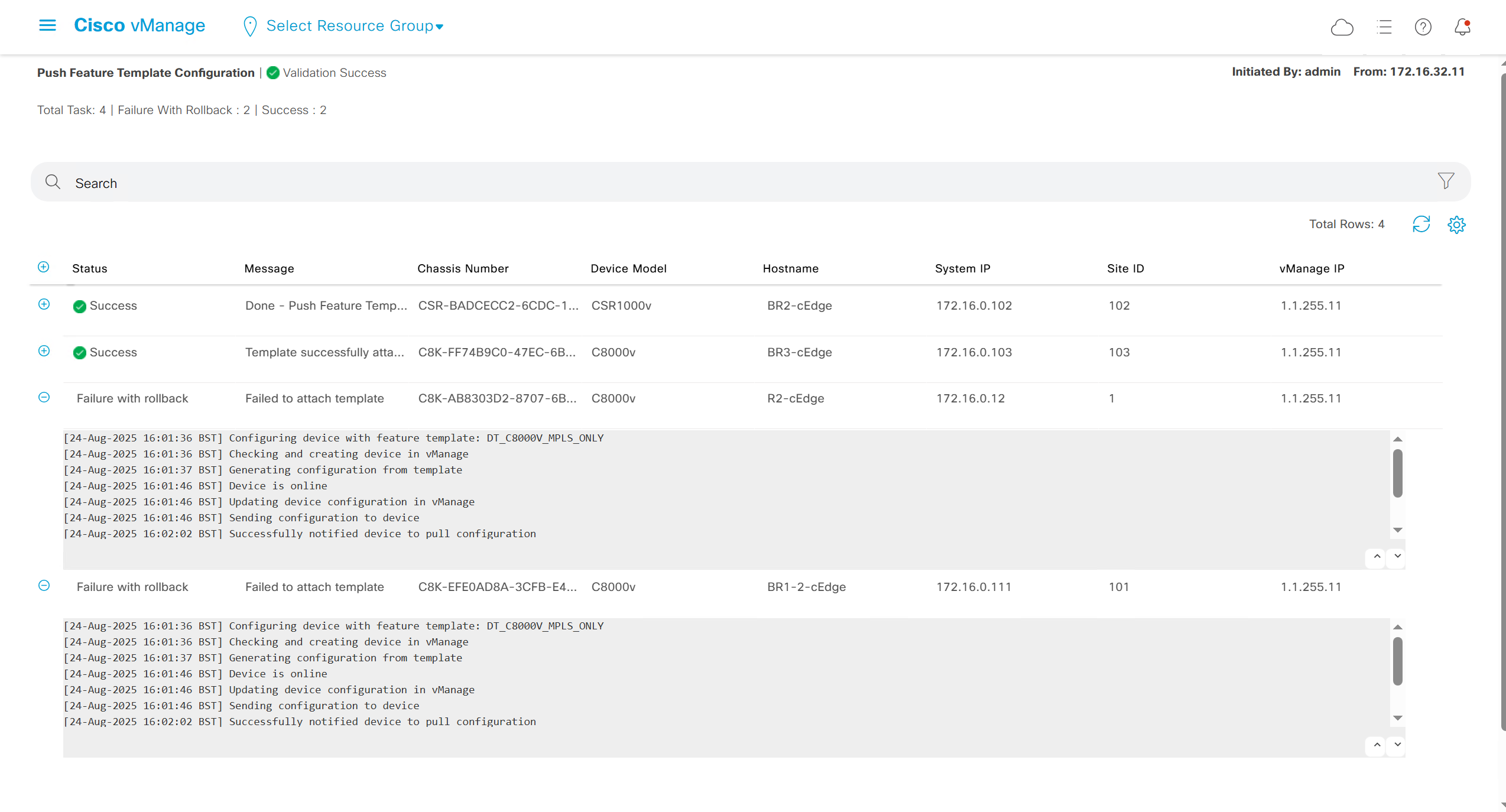

vManage Connection Preference: by default is 5, a link with higher preference is used to connect to vmanage in case we have 2x transports because only one vmanage connection is established
Port hop
By default, WAN Edge devices (vEdge, C8000V) form control connections with controllers (vBond, vSmart, vManage) using:
DTLS (UDP 12346)
TLS (TCP 443)
So normally, traffic will keep using those fixed ports.
When Port Hop is enabled, the “WAN Edge” will not stick to just a single fixed port. Instead, it will cycle through a range of ports if a connection attempt fails.
- DTLS (UDP):
- Starts with UDP/12346.
- If blocked, it will try other ports in the UDP range 12346–12846.
- It keeps retrying until it finds an open port.
- TLS (TCP):
- Starts with TCP/443.
- If blocked, it will try other ports in the TCP range 443–12443.
- Again, hops until success.
This makes control connections much more resilient in restrictive or dynamic network environments where firewalls are doing inspections and rate limiting traffic
Sometimes port hop can be issue
Control connections on the router, you see it is up from last 4 mins and 12 seconds. It will again retrigger after completing 5 mins
NDNA_c8000v#sh sdwan control connections
PEER PEER CONTROLLER
PEER PEER PEER SITE DOMAIN PEER PRIV PEER PUB GROUP
TYPE PROT SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT ORGANIZATION LOCAL COLOR PROXY STATE UPTIME ID
------------------------------------------------------------------------------------------------------------------------------------------------------------
vsmart dtls 10.10.10.11 1 1 10.10.3.5 12646 17.23.12.11 12646 NDNA-111 gold No up 0:00:04:12 0
vsmart dtls 10.10.10.12 2 1 10.10.3.15 12646 17.23.12.25 12646 NDNA-111 gold No up 0:00:04:12 0
vmanage dtls 10.10.10.10 1 0 10.10.3.12 13046 17.23.12.88 13046 NDNA-111 gold No up 0:00:04:12 0 checked again after like a minute now and you will notice, it is showing 8 seconds now which means it is bounced again.
NDNA_c8000v#sh sdwan control connections
PEER PEER CONTROLLER
PEER PEER PEER SITE DOMAIN PEER PRIV PEER PUB GROUP
TYPE PROT SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT ORGANIZATION LOCAL COLOR PROXY STATE UPTIME ID
------------------------------------------------------------------------------------------------------------------------------------------------------------
vsmart dtls 10.10.10.11 1 1 10.10.3.5 12646 17.23.12.11 12646 NDNA-111 gold No up 0:00:00:08 0
vsmart dtls 10.10.10.12 2 1 10.10.3.15 12646 17.23.12.25 12646 NDNA-111 gold No up 0:00:00:08 0
vmanage dtls 10.10.10.10 1 0 10.10.3.12 13046 17.23.12.88 13046 NDNA-111 gold No up 0:00:00:08 0For troubleshooting, move the router to CLI mode
First check the mode in which router is working, if we see below in red, the template is attached to the router which means the router is in controller mode.
Personality: vEdge
Model name: C8000V
Device role: cEdge-SDWAN
Services: None
vManaged: true
Commit pending: false
Configuration template: AZURE-NDNA-V01
Chassis serial number: XXXXXXXXXXXXXXMove the router from controller mode to CLI mode in order to do packet captures on the router. Although it is recommended to capture using vmanage datastream mode
Once you moved, run the below script in order to capture the packets on the interface with the source and the destination IPs as shown below :
!
ip access-list extended CAP-Filter
10 permit ip host 10.10.1.23 host 17.23.12.88
20 permit ip host 17.23.12.88 host 10.10.1.23
exit
monitor capture CAP access-list CAP-Filter interface GigabitEthernet1 both buffer circular size 25
monitor capture CAP limit pps 1000000
monitor capture CAP access-list CAP-Filter both buffer circular size 25
monitor capture CAP start
monitor capture CAP stop
!Now run below commands to get debugs
NDNA_c8000v# debug platform software sdwan vdaemon all high
NDNA_c8000v# monitor logging process vdaemon internalOnce you run the above commands, you will see logs related to the interfaces
You will see that in debug logs , TLOC Disable … Why ?
2024/04/19 17:47:59.779970993 {vdaemon_R0-0}{255}: [event] [18342]: (debug): Disabling tloc GigabitEthernet1.
2024/04/19 17:47:59.780001093 {vdaemon_R0-0}{255}: [misc] [18342]: (ERR): Delta preference value added to TLOC pref.
2024/04/19 17:47:59.780003193 {vdaemon_R0-0}{255}: [misc] [18342]: (ERR): Sending TLOC: ifname:GigabitEthernet3 color:gold spi:18915 smarts:2 manages:1 state:DOWN LR encap:0 LR hold time:7000 bw:0, down-bw 0 range: 0-0,adapt period 0 up-bw range 0-0 up_fia 0 capability:0x3fCheck the interface for port-hop and you will see port-hop is enabled. Now disable the port hop and you will see the control connections will be stable
interface GigabitEthernet1
tunnel-interface
encapsulation ipsec weight 1
no border
color gold restrict
no last-resort-circuit
no low-bandwidth-link
no vbond-as-stun-server
vmanage-connection-preference 5
port-hopCheck the control connection after disabling port-hop on the interface , you will see it is up from last 19 min. and stable.
NDNA_c8000v#sh sdwan control connections
PEER PEER CONTROLLER
PEER PEER PEER SITE DOMAIN PEER PRIV PEER PUB GROUP
TYPE PROT SYSTEM IP ID ID PRIVATE IP PORT PUBLIC IP PORT ORGANIZATION LOCAL COLOR PROXY STATE UPTIME ID
------------------------------------------------------------------------------------------------------------------------------------------------------------
vsmart dtls 10.10.10.11 1 1 10.10.3.5 12646 17.23.12.11 12646 NDNA-111 gold No up 0:00:19:02 0
vsmart dtls 10.10.10.12 2 1 10.10.3.15 12646 17.23.12.25 12646 NDNA-111 gold No up 0:00:19:02 0
vmanage dtls 10.10.10.10 1 0 10.10.3.12 13046 17.23.12.88 13046 NDNA-111 gold No up 0:00:19:02 0 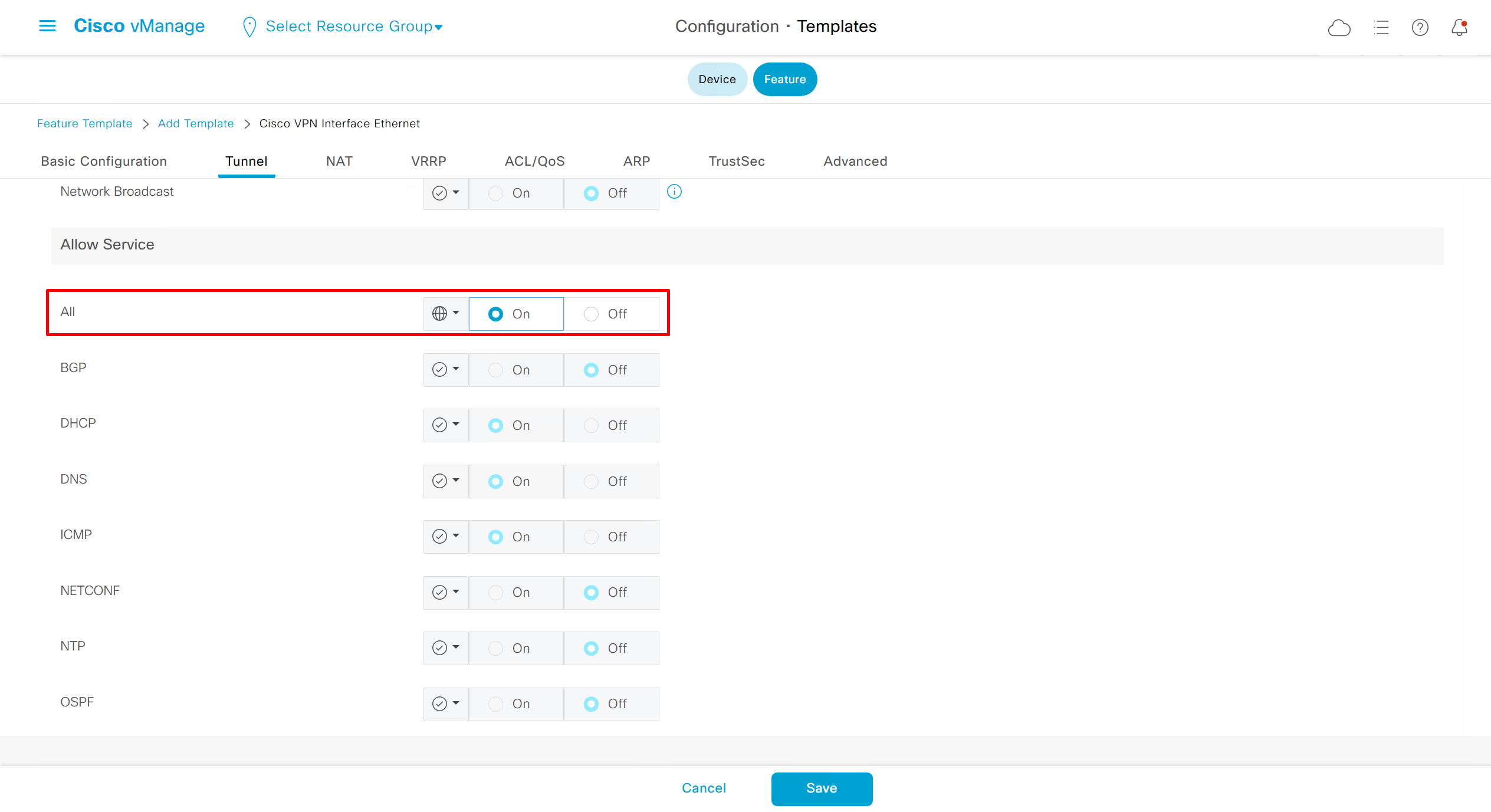
Now we can copy the template and also change its device model as well
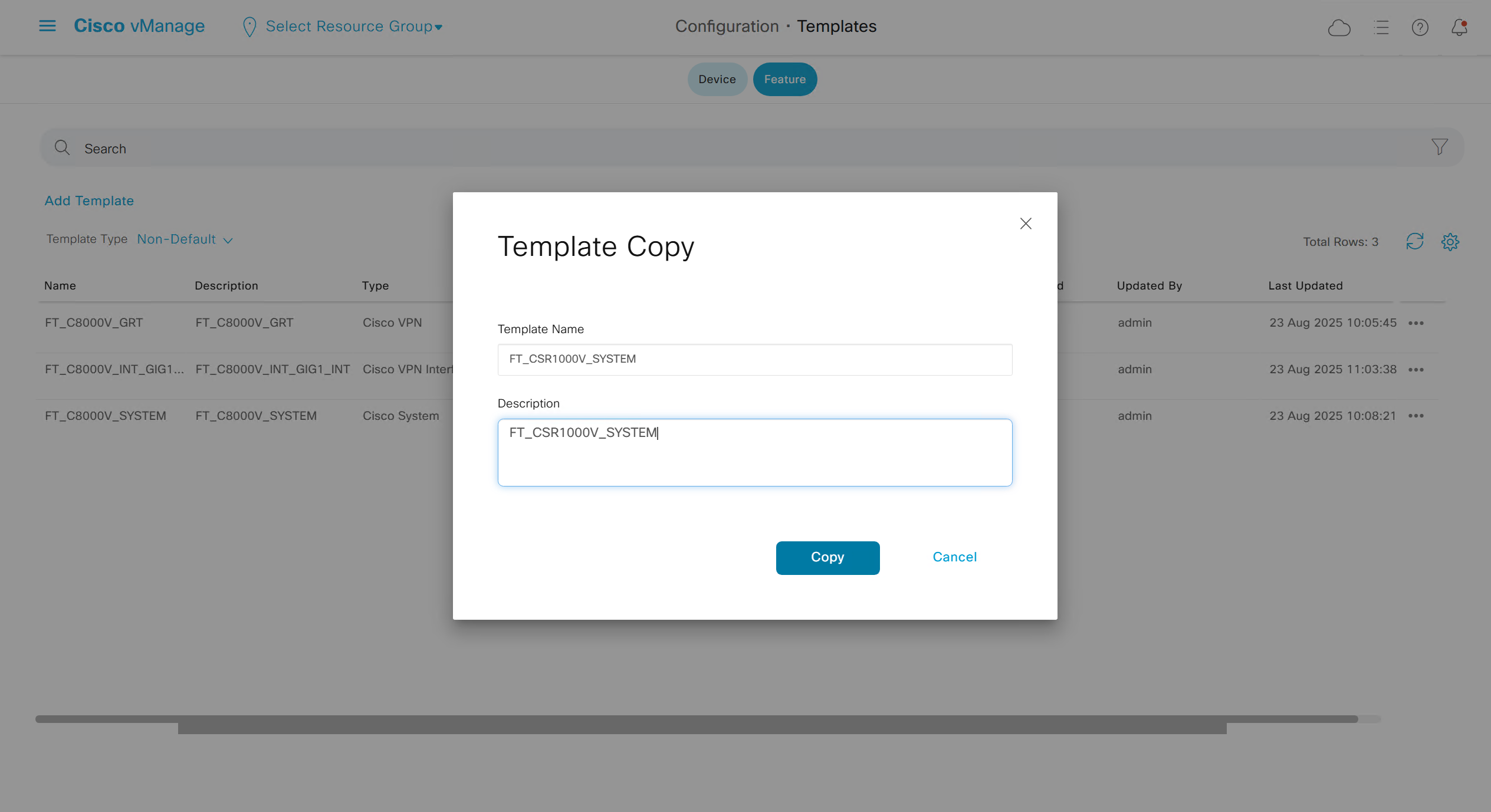
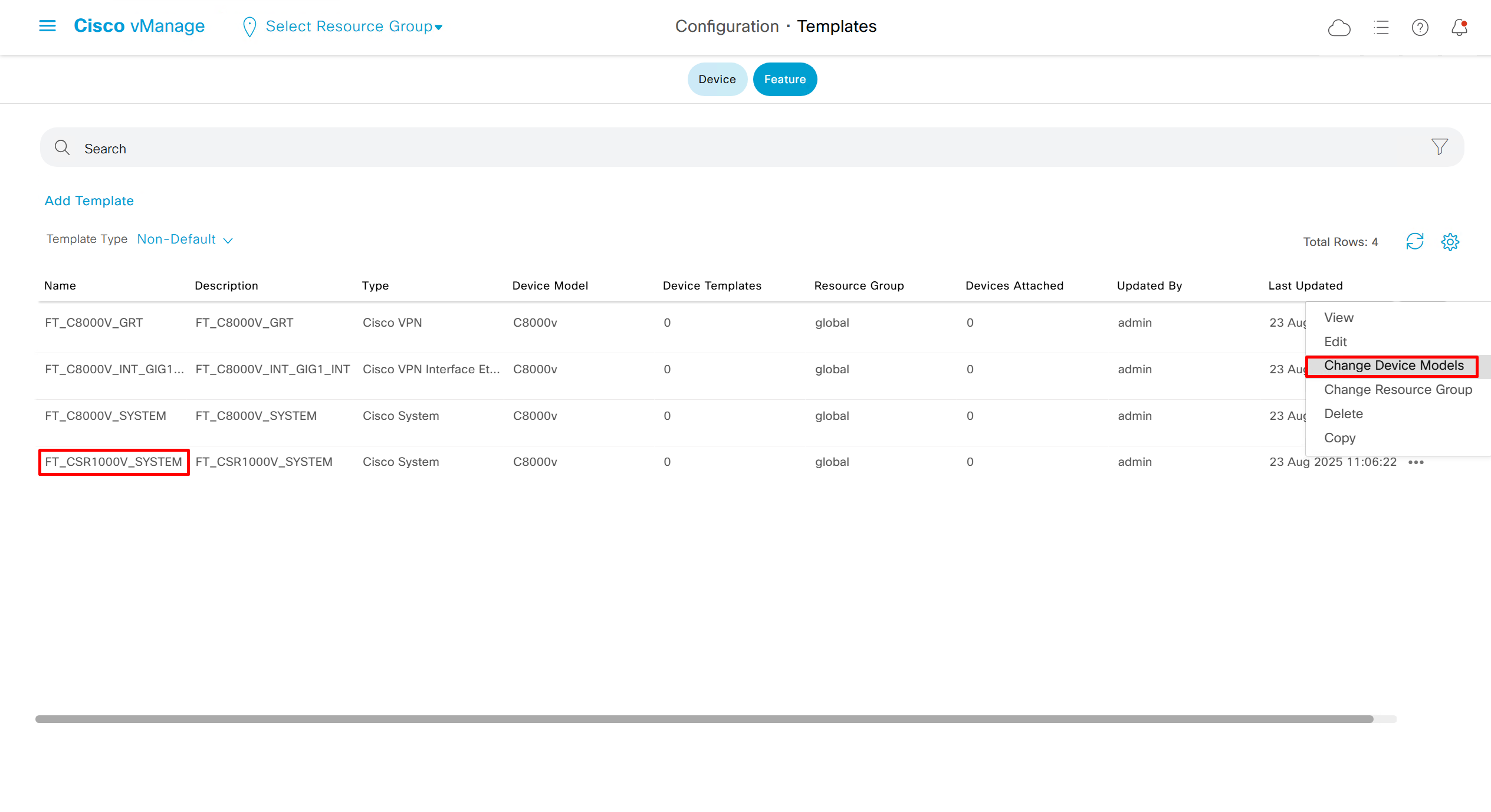
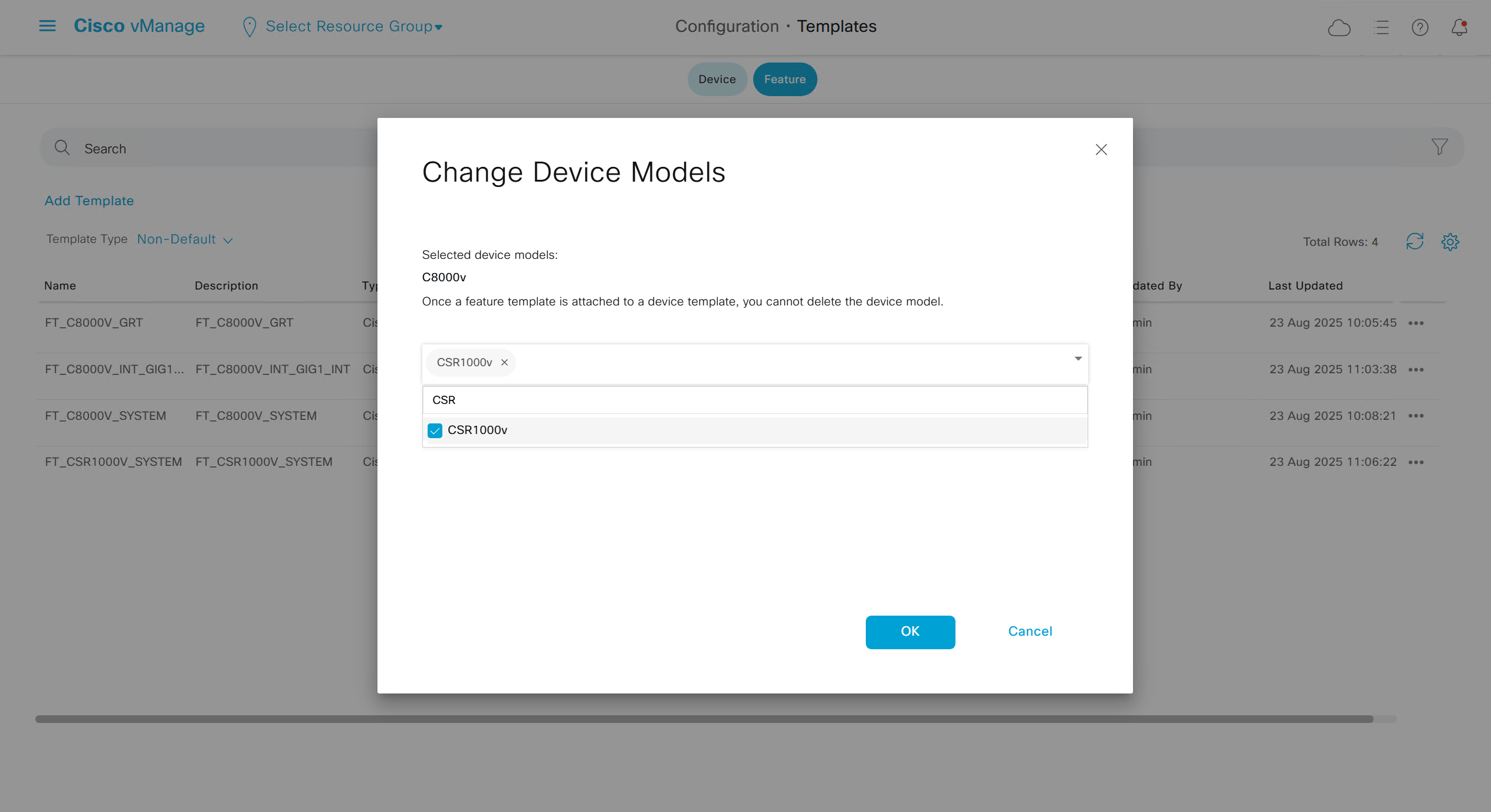
Once you have changed the device model, make sure that interface names match, such as make sure that interface name is not GigabitEthernet0/0/0 and GigabitEthernet1, if it is different then change it inside template as well
on hardware models we also need to make sure that we have template for management gig0 interface to satisfy the requirement for device template on hardware platforms otherwise deployment fails, for managemet gig0 interface same template “Cisco VPN Interface Ethernet” is used and input its name from “show ip int brief”
Now create device template
This template is device specific + transport connectivity types specific
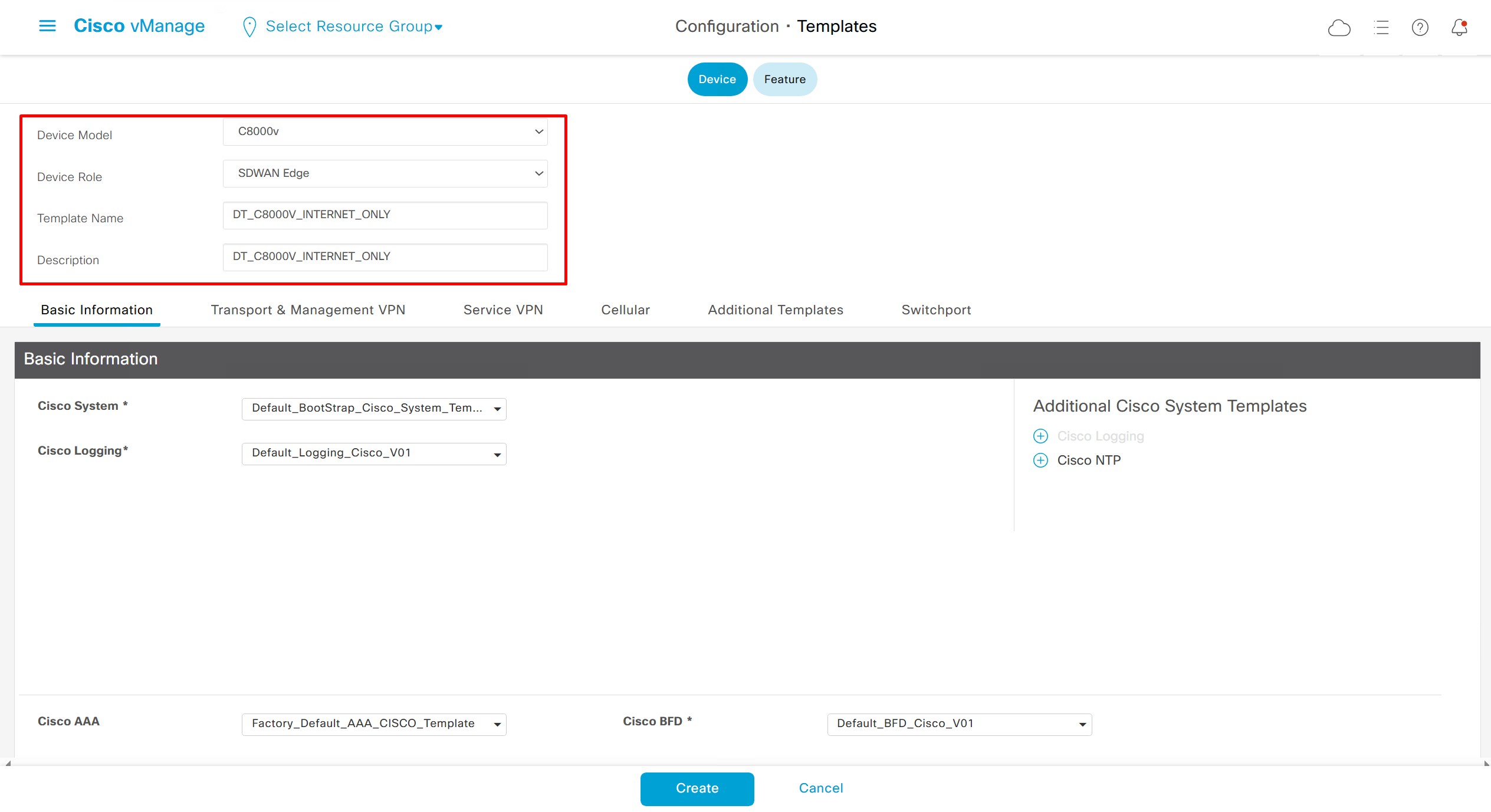
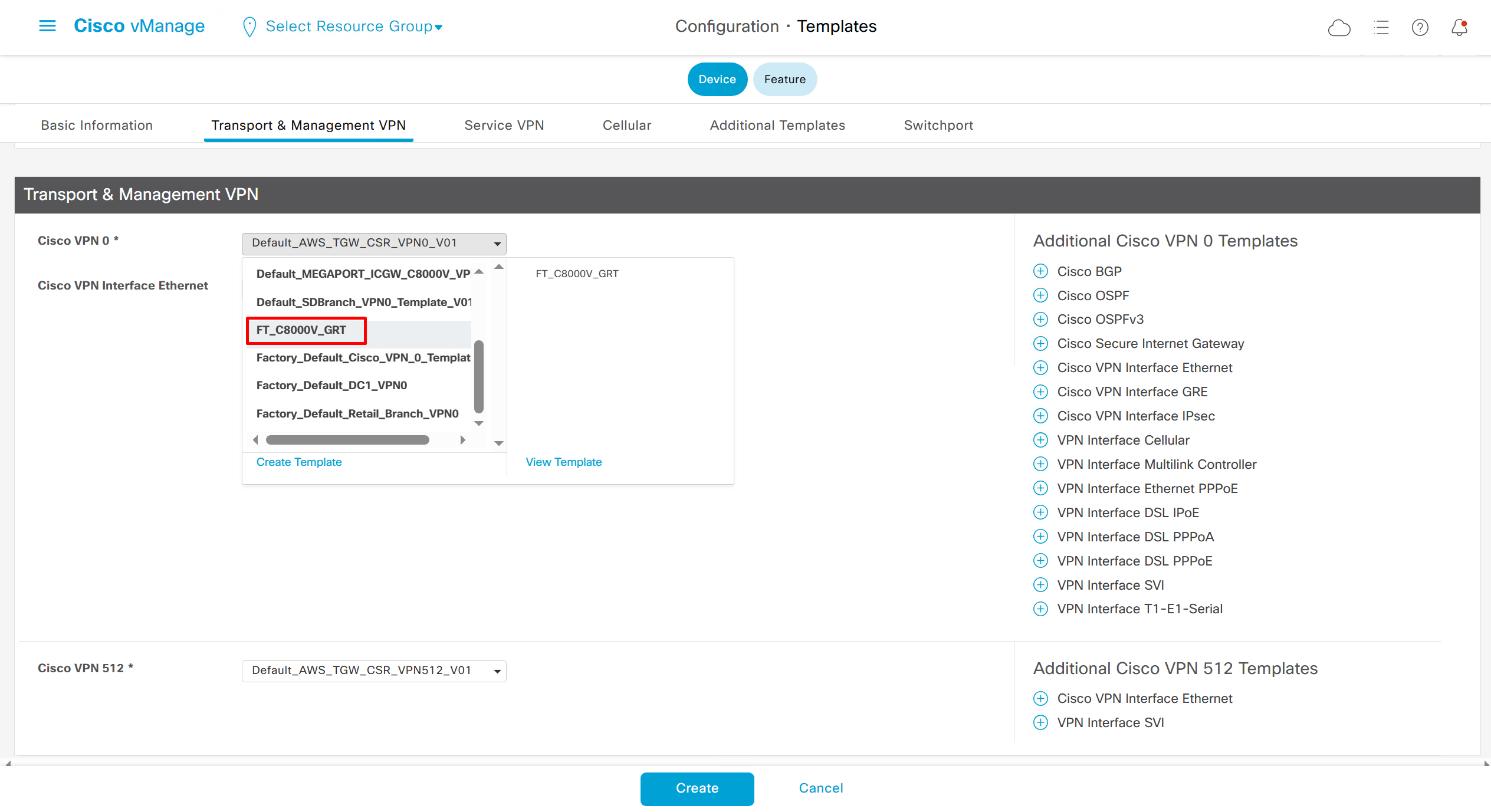
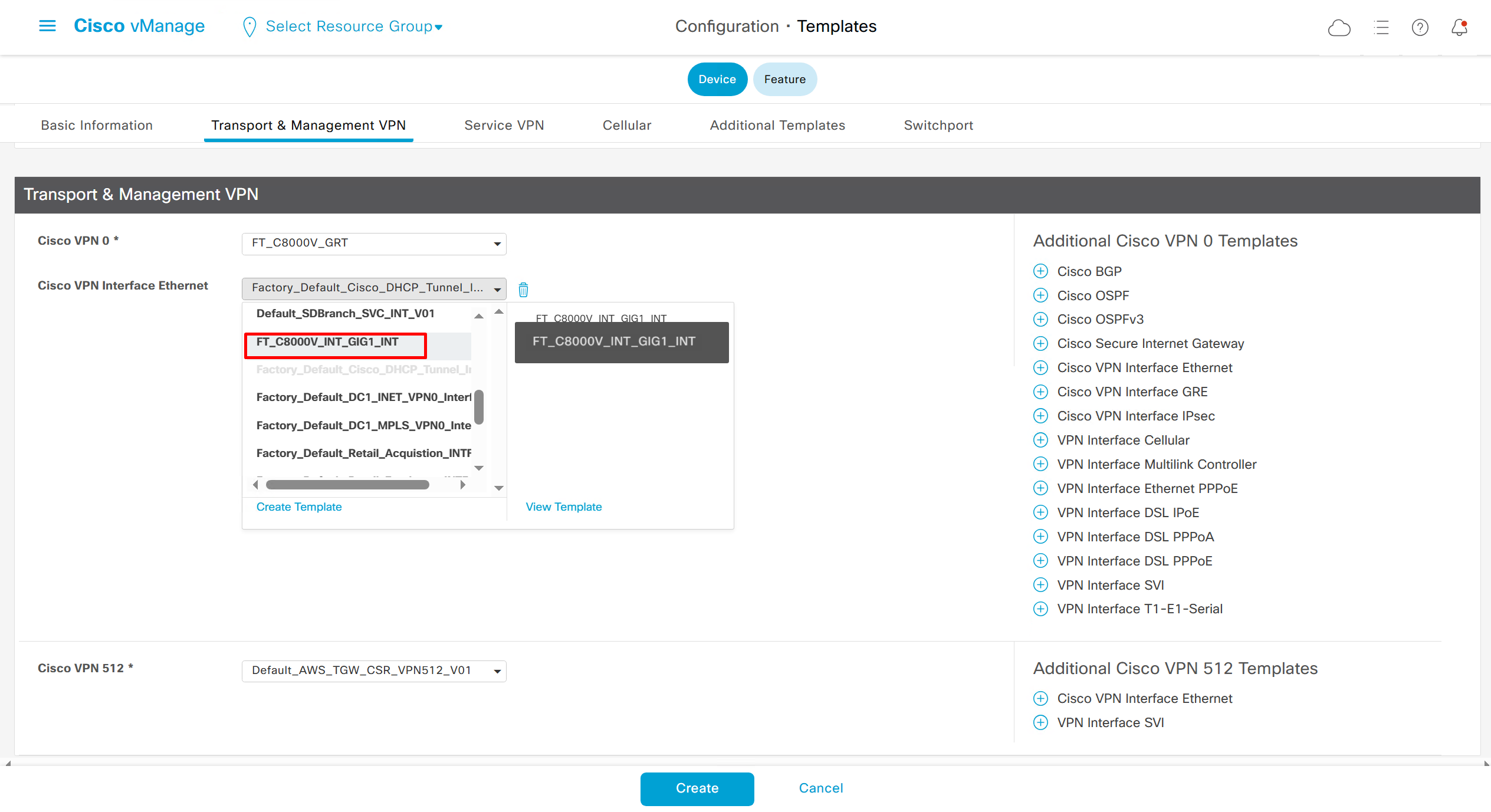
In case we have another transport interface, we can add another from plus icon next to the type of interface

In case we have to attach mgmt interface to avoid deployment errors on hardware device
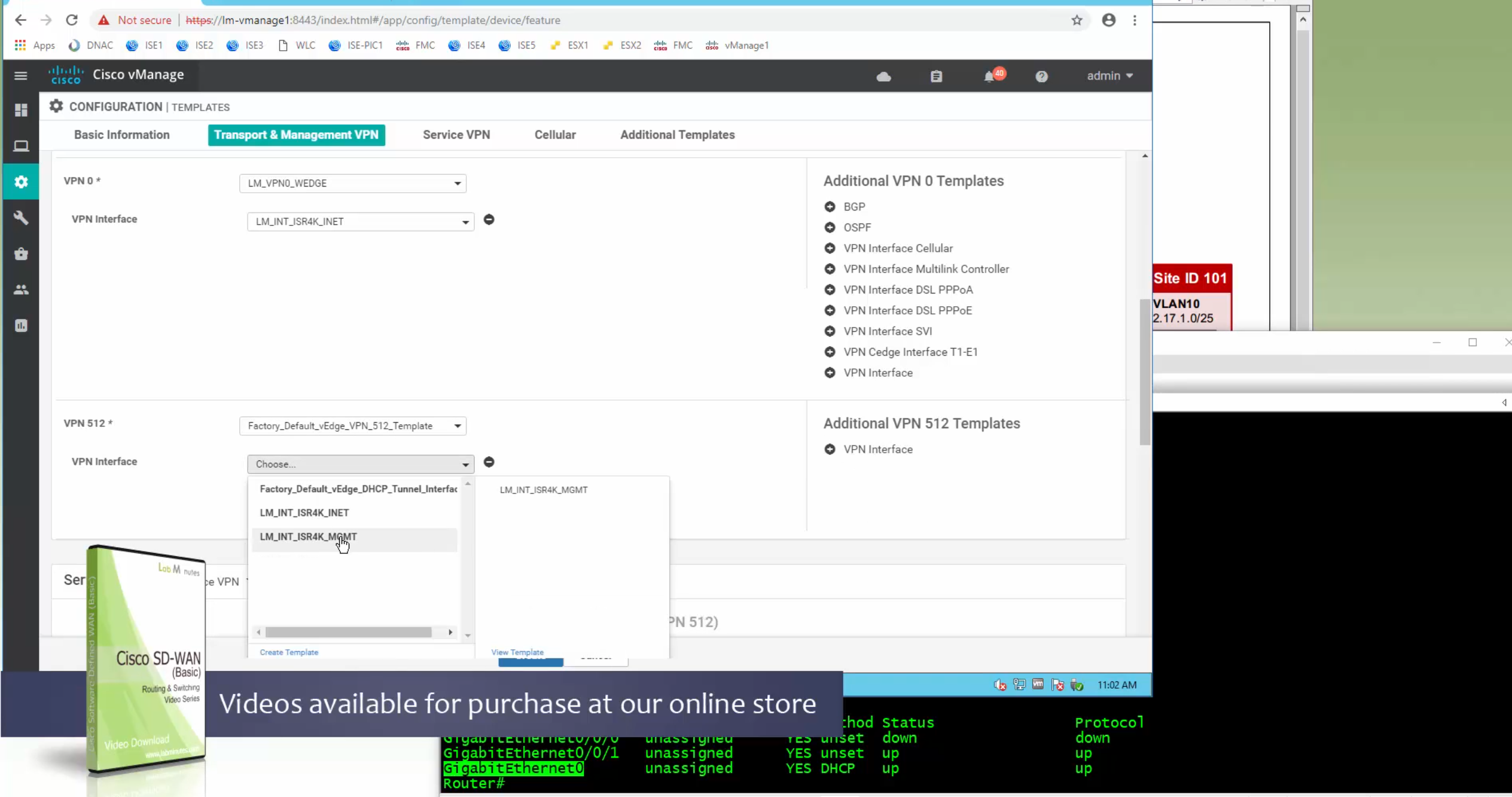
Now we need to attach the device template to a device – C8000v that has internet only connectivity
And you do that from the template itself
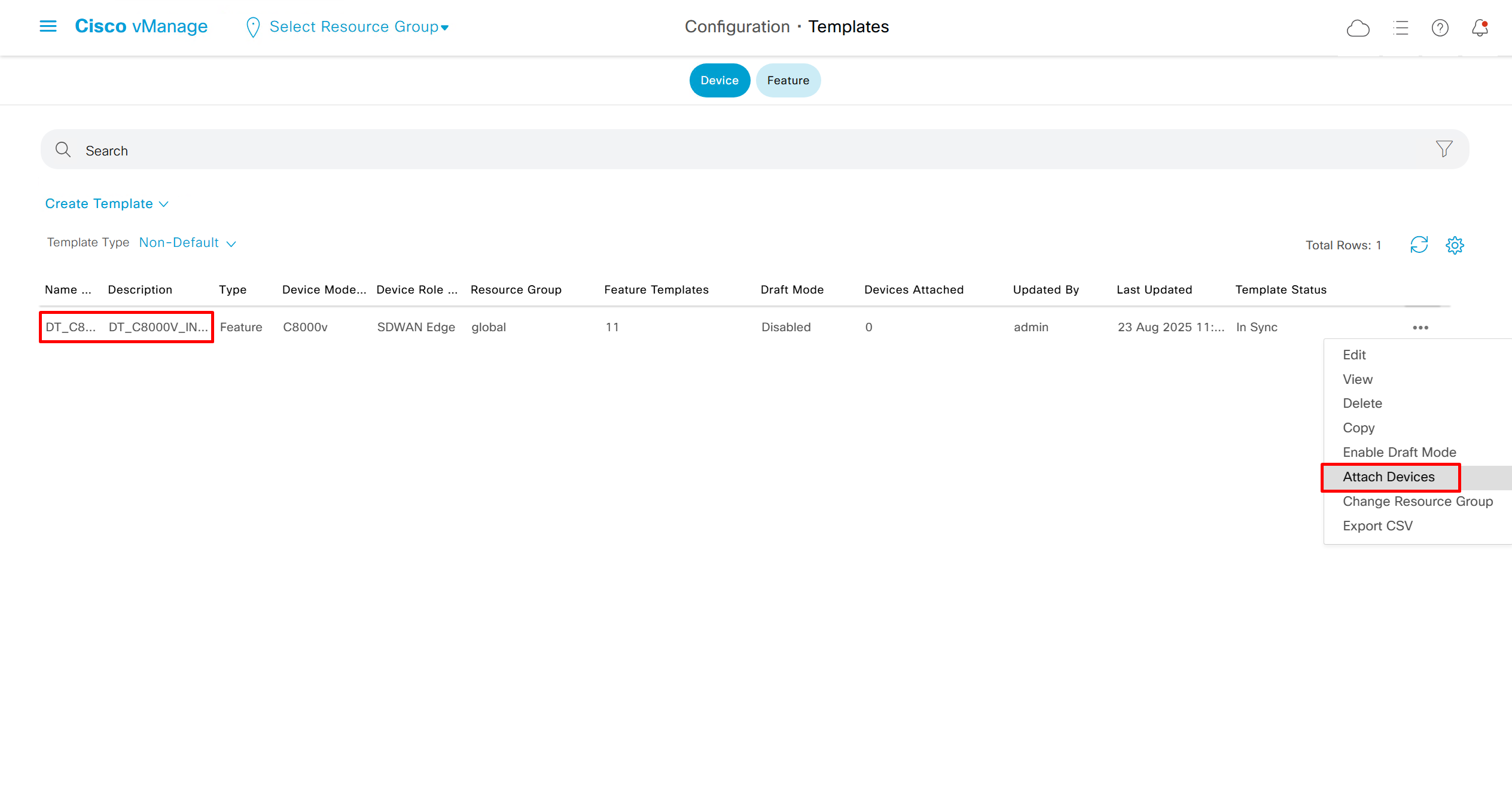
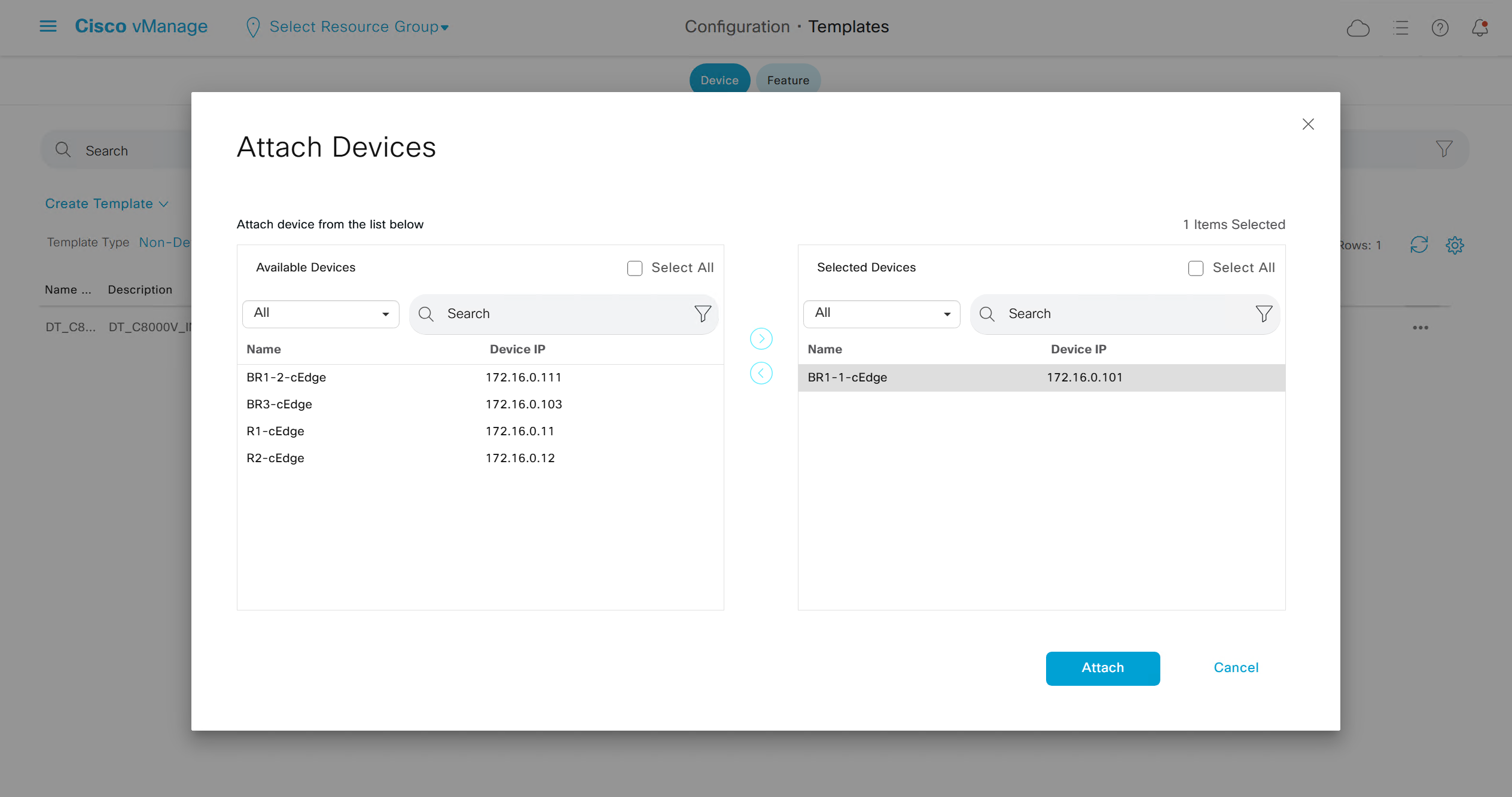
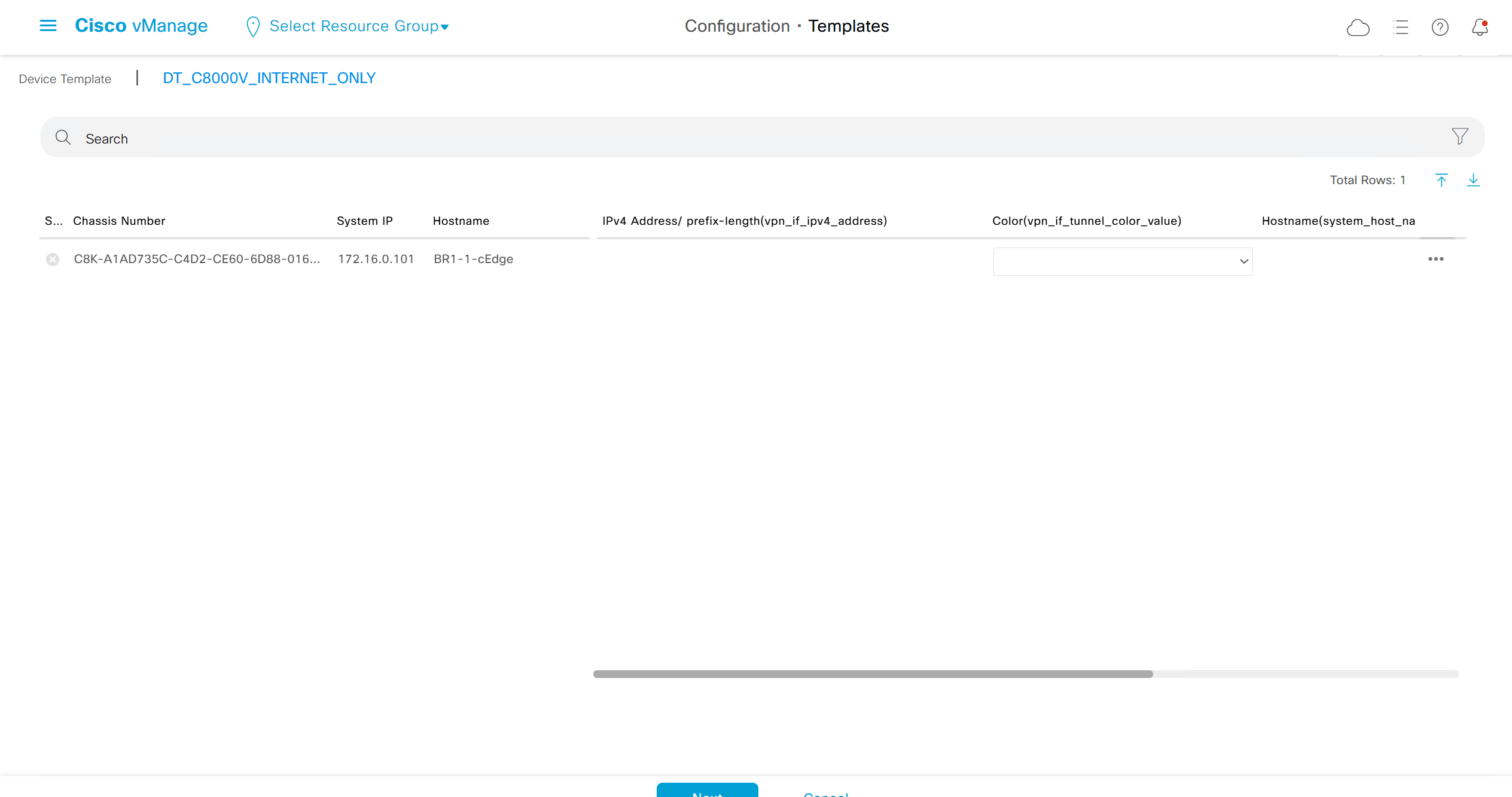
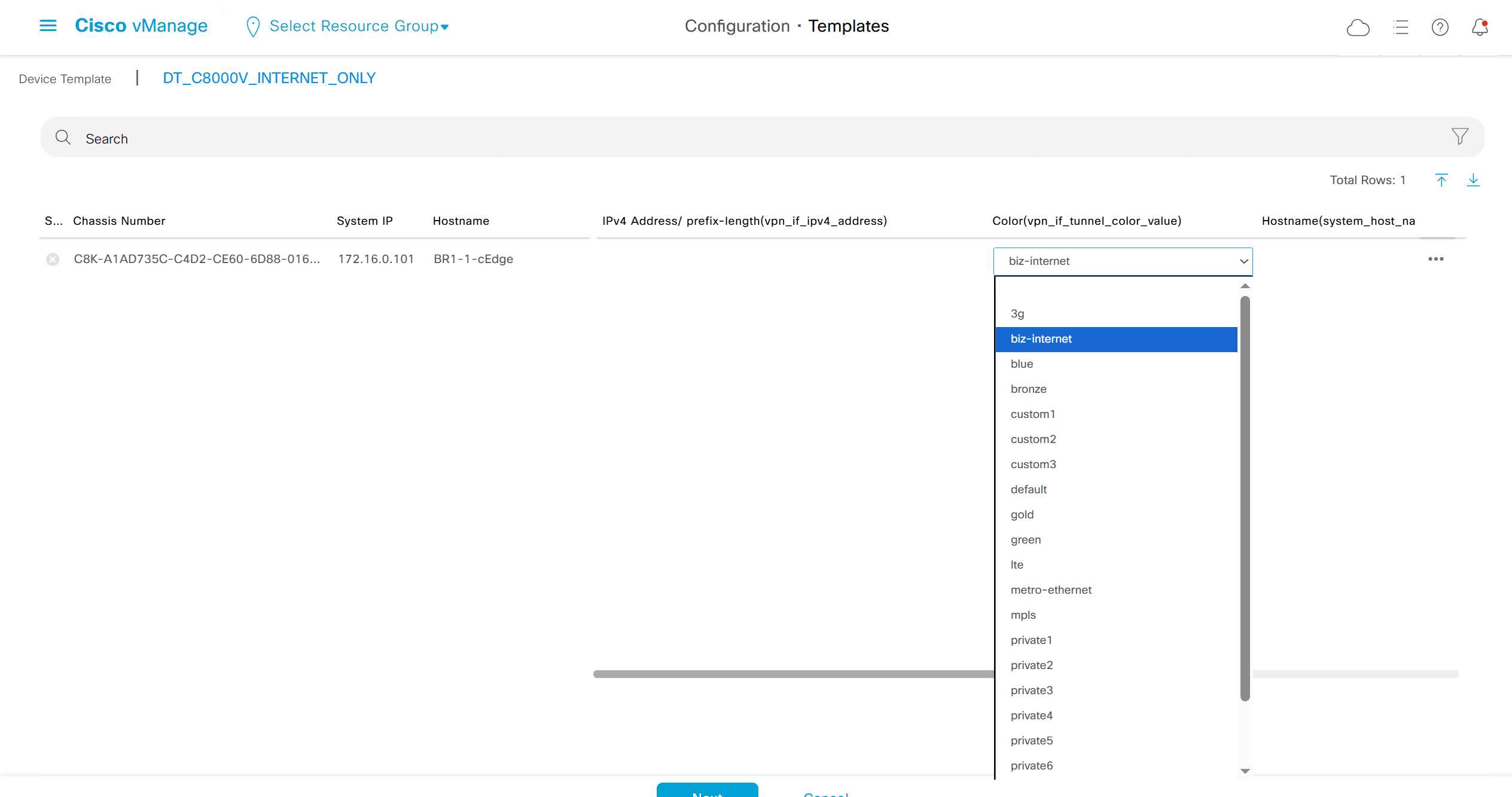

fill the variables with following information from the running-config of edge device


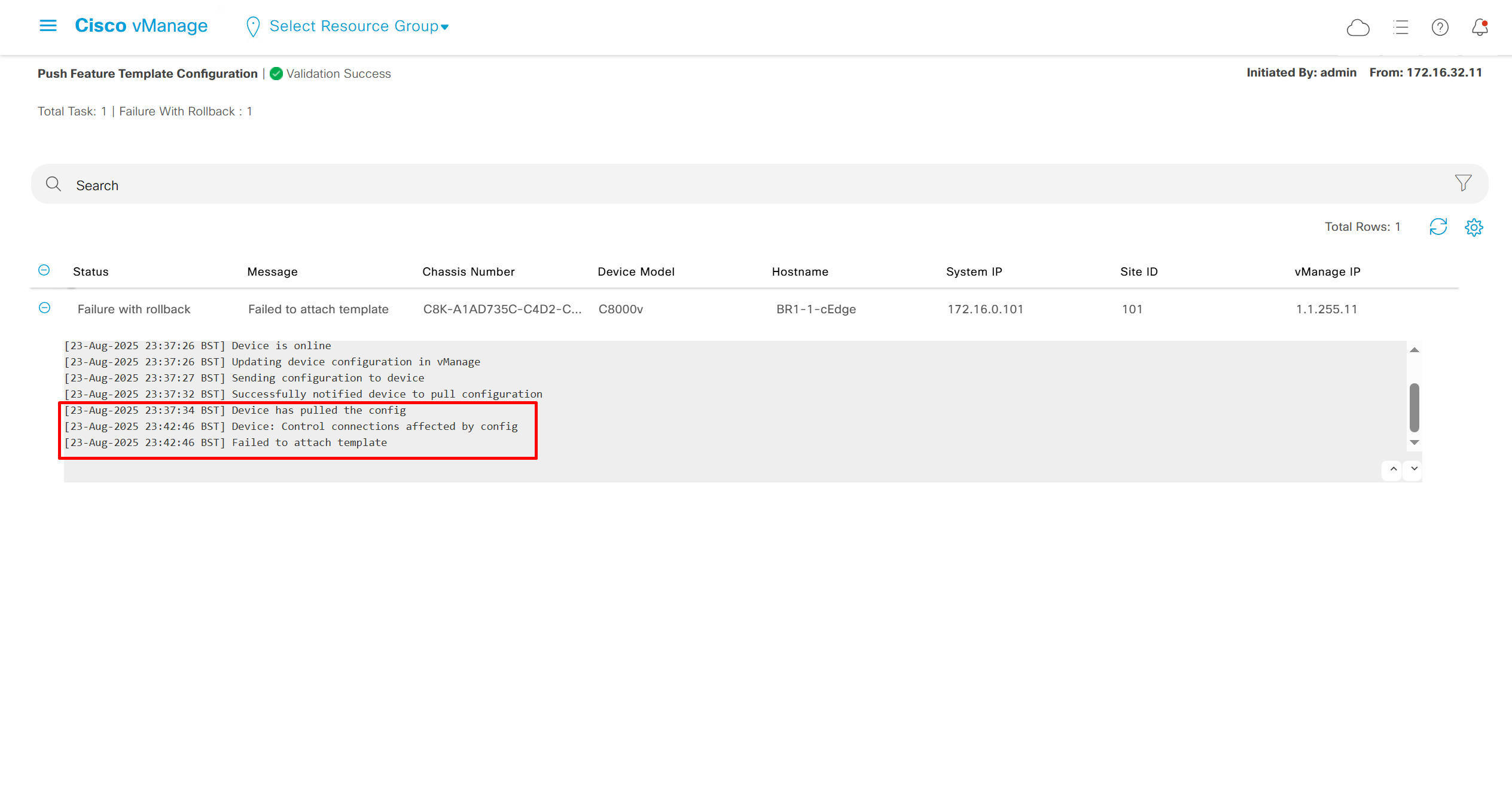
deployment failed and it rolled back to restore connectivity to vmanage as edge lost connectivity to vmanage and also other controllers
As I checked the template, the default route was missing from feature template FT_C8000V_GRT
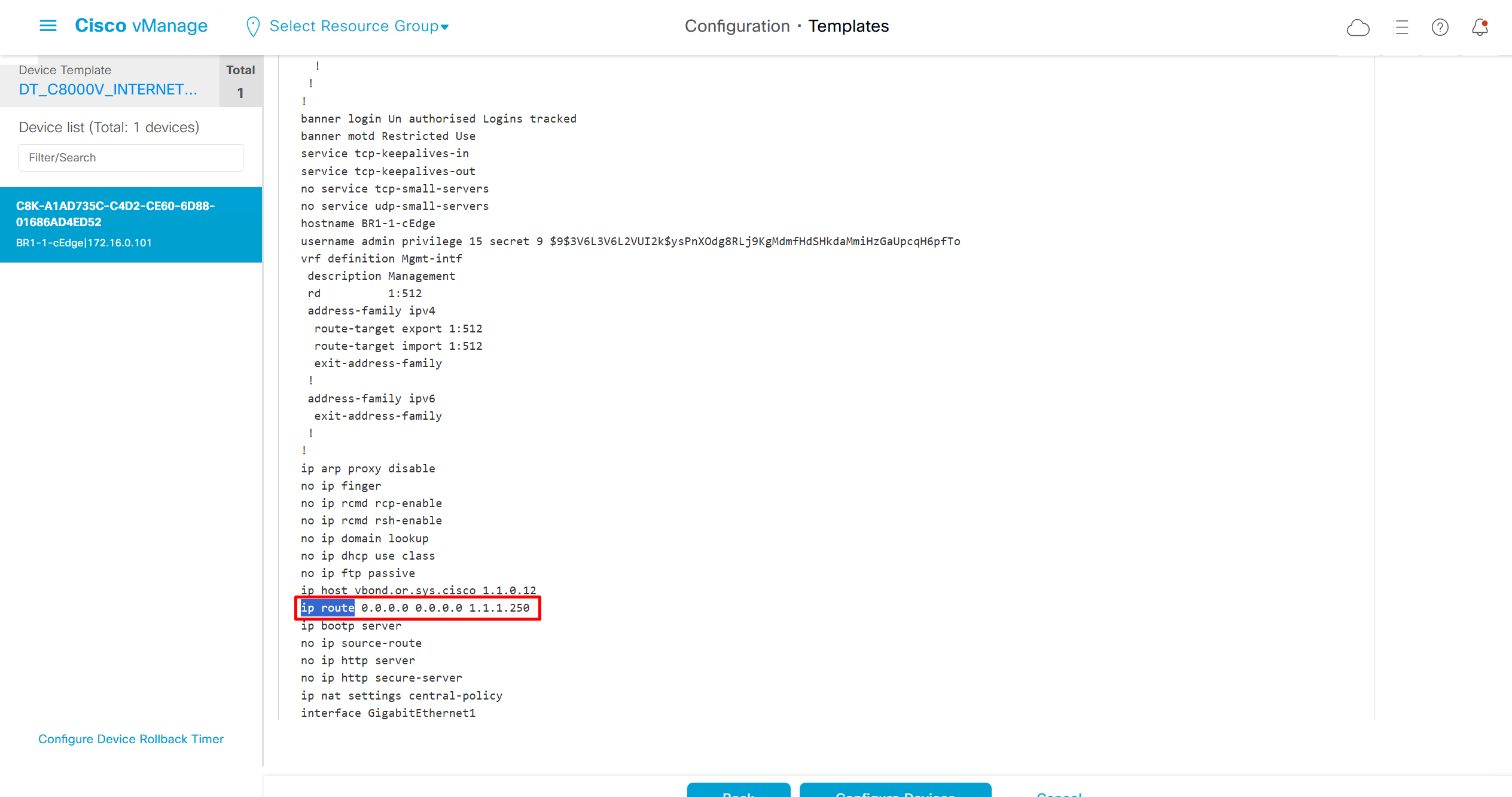
after successful deployment I was not able to login, so new AAA policy was attached
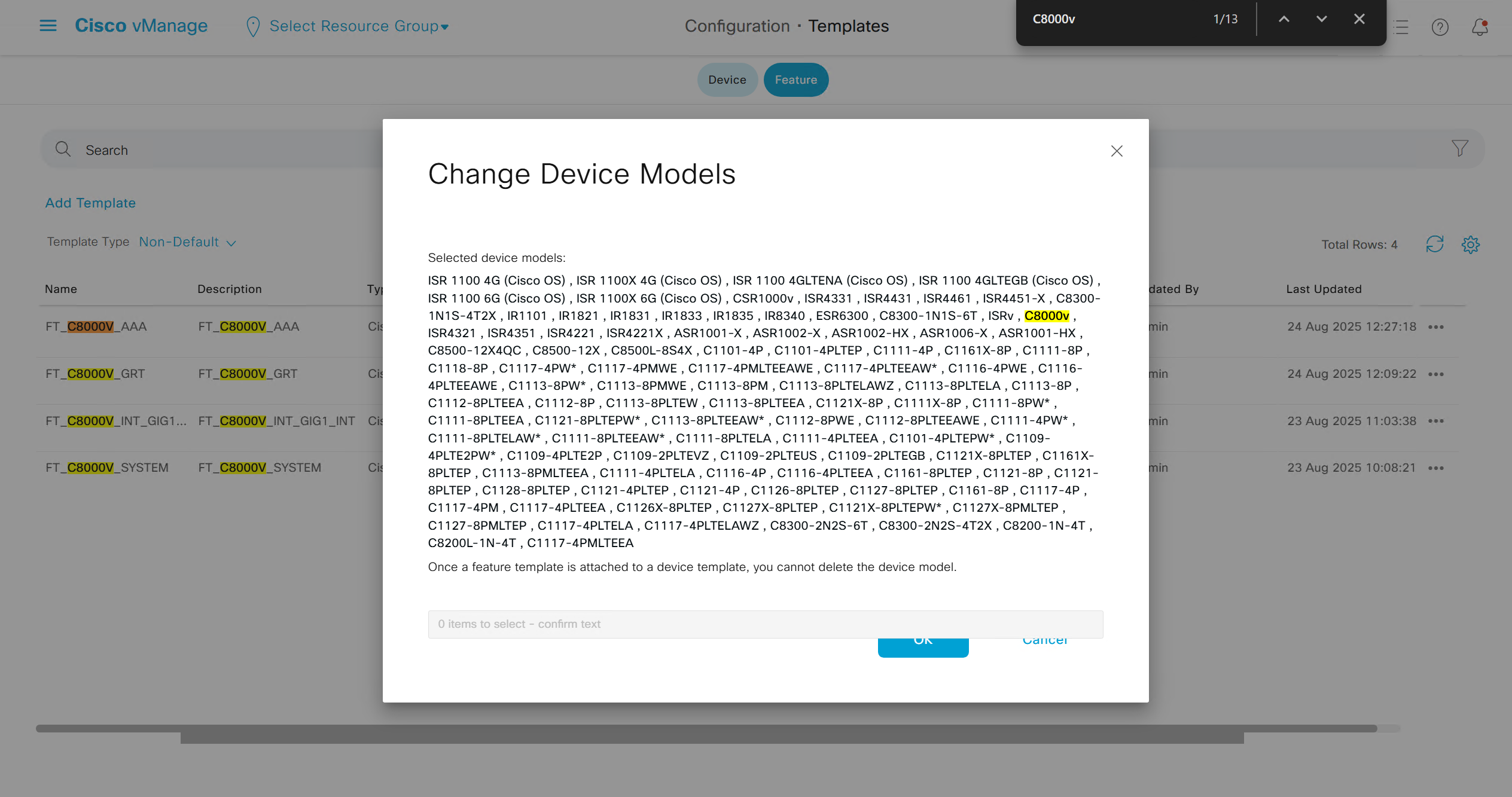

now I can login
Whenever there is a change made on templates, these changes need to be pushed to the devices
While making those changes there is an option to download the CSV and make bulk changes and then upload the CSV back
This is very useful when you have large number of devices
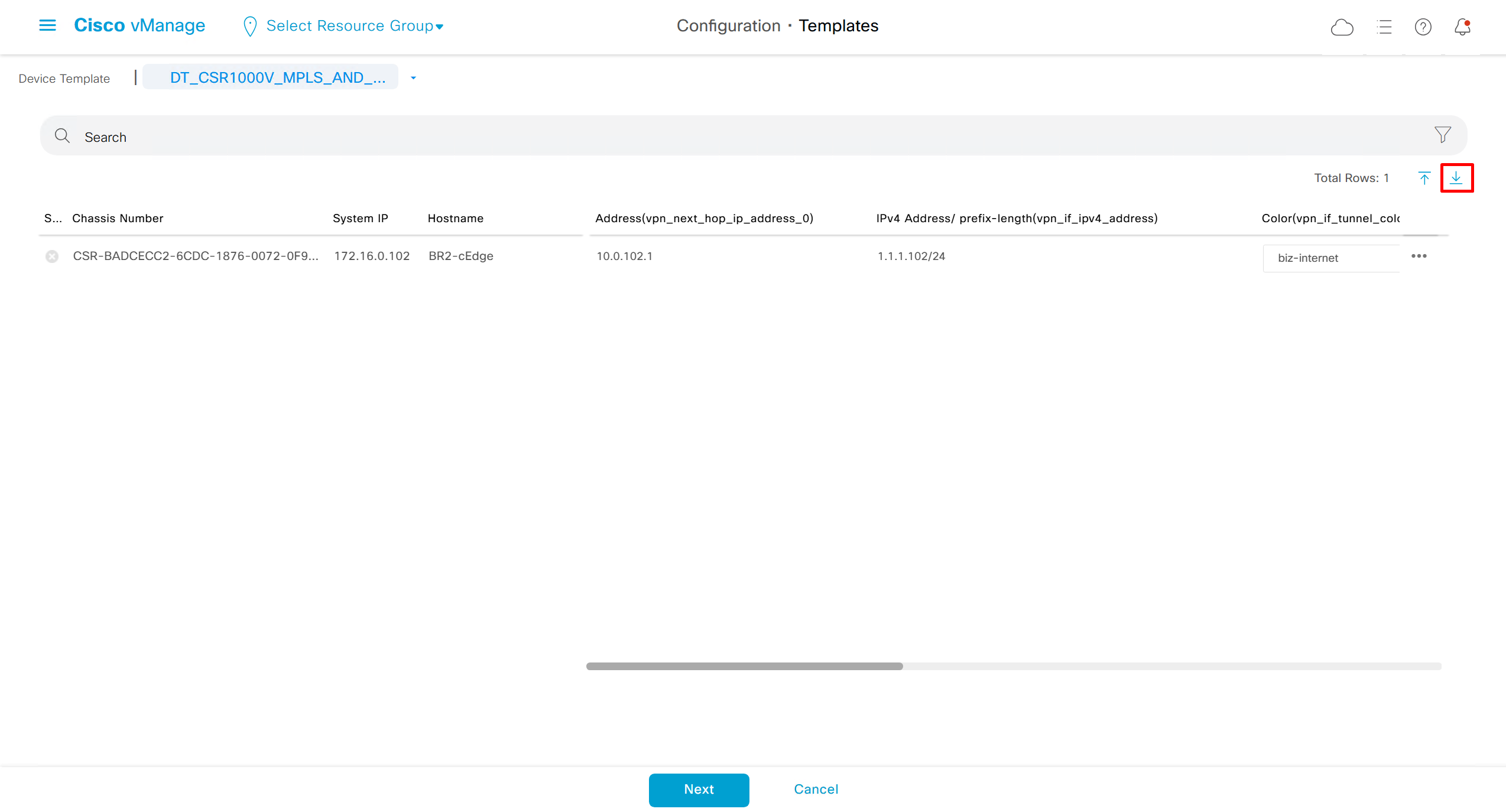
When making changes there is an option on the bottom left corner
Configure Device Rollback Timer
NTP Feature Template common for all edges
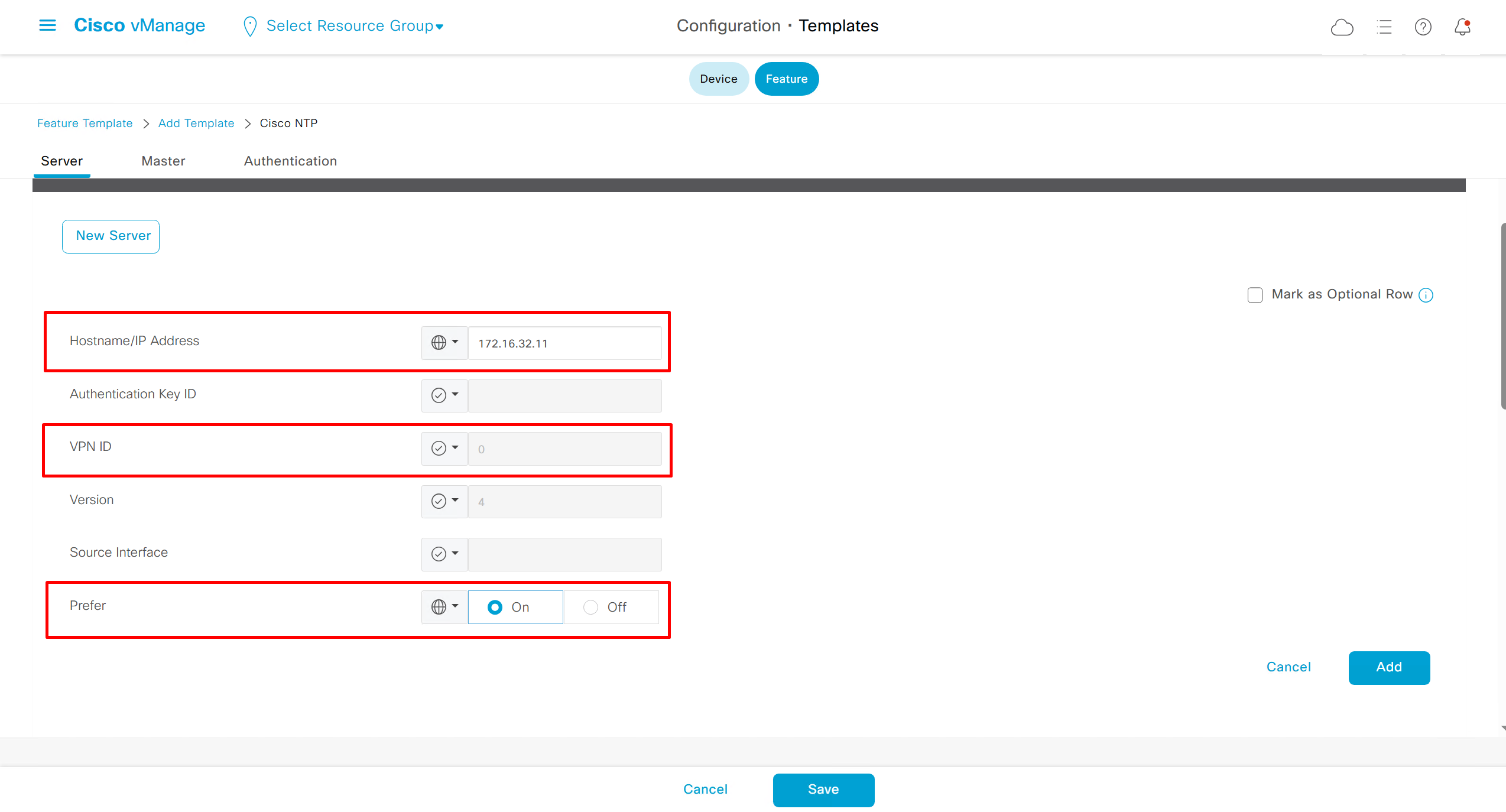

Login Banner Feature Template
Banner text new lines should be replaced with \n so it can be pasted in this box
************************************************************\n* *\n* WARNING: Authorized Access Only! *\n* *\n* This system is for the use of authorized users only. *\n* Any unauthorized access or use is prohibited and *\n* may be subject to criminal and civil penalties. *\n* *\n* All activities on this system are monitored. *\n* *\n************************************************************
Local Disk Logging Feature Template
As log messages are in /var/log for troubleshooting
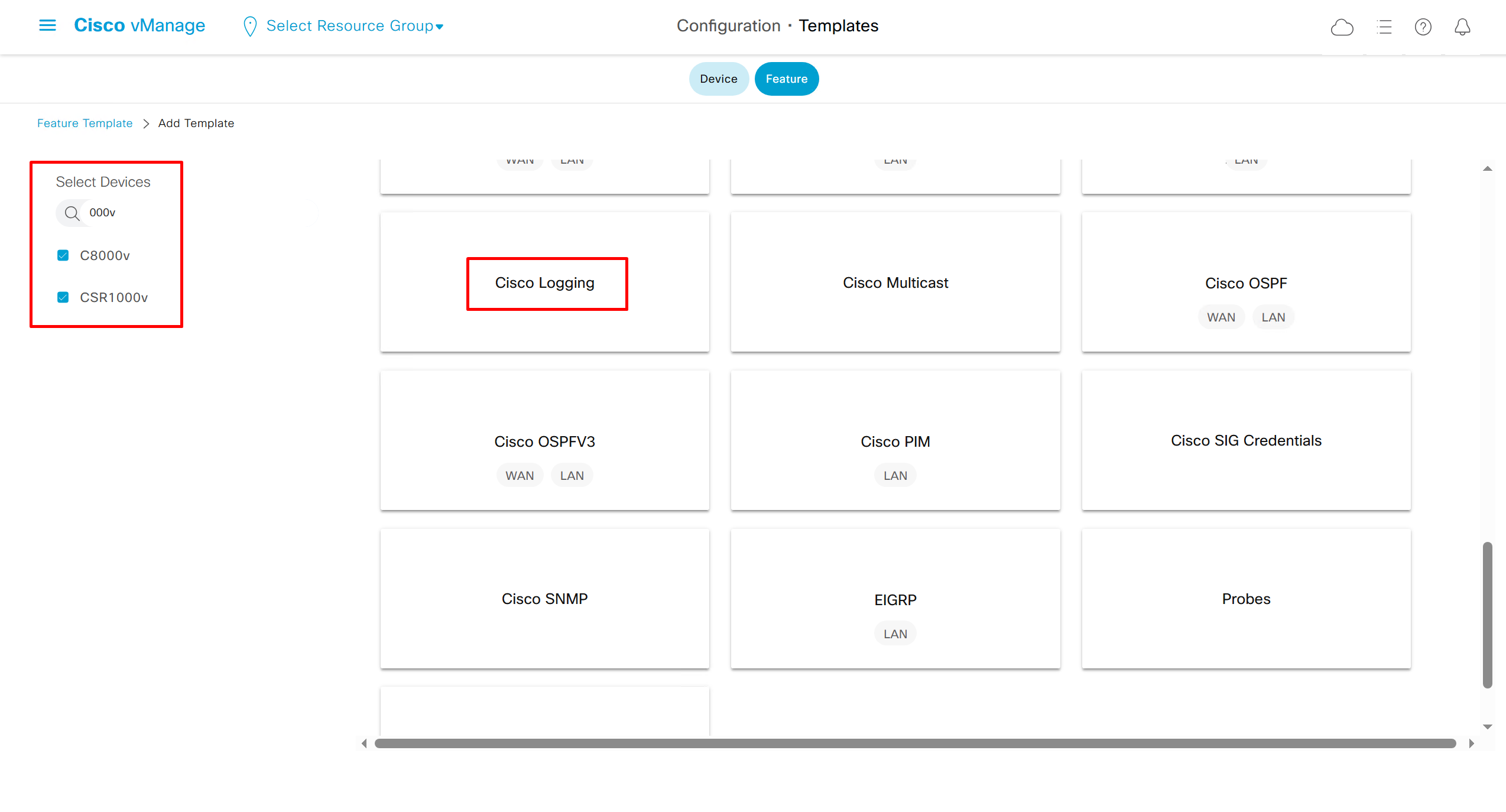
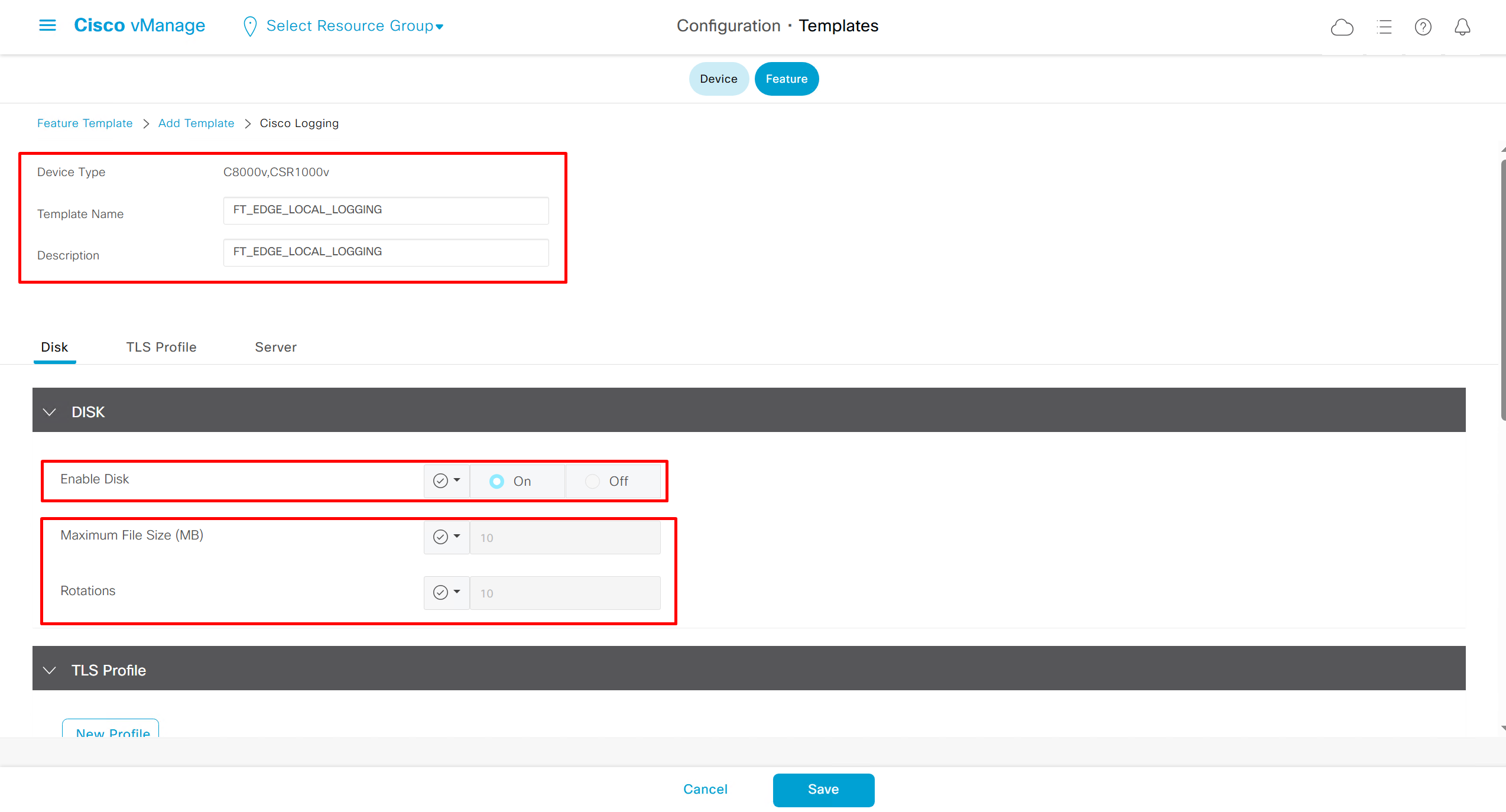
In case Syslog server is inside Datacenter and not over the WAN transport then we have to change the below VPN number and change it from 0 to service side VPN / VRF number of local site / datacenter in which Syslog server lives
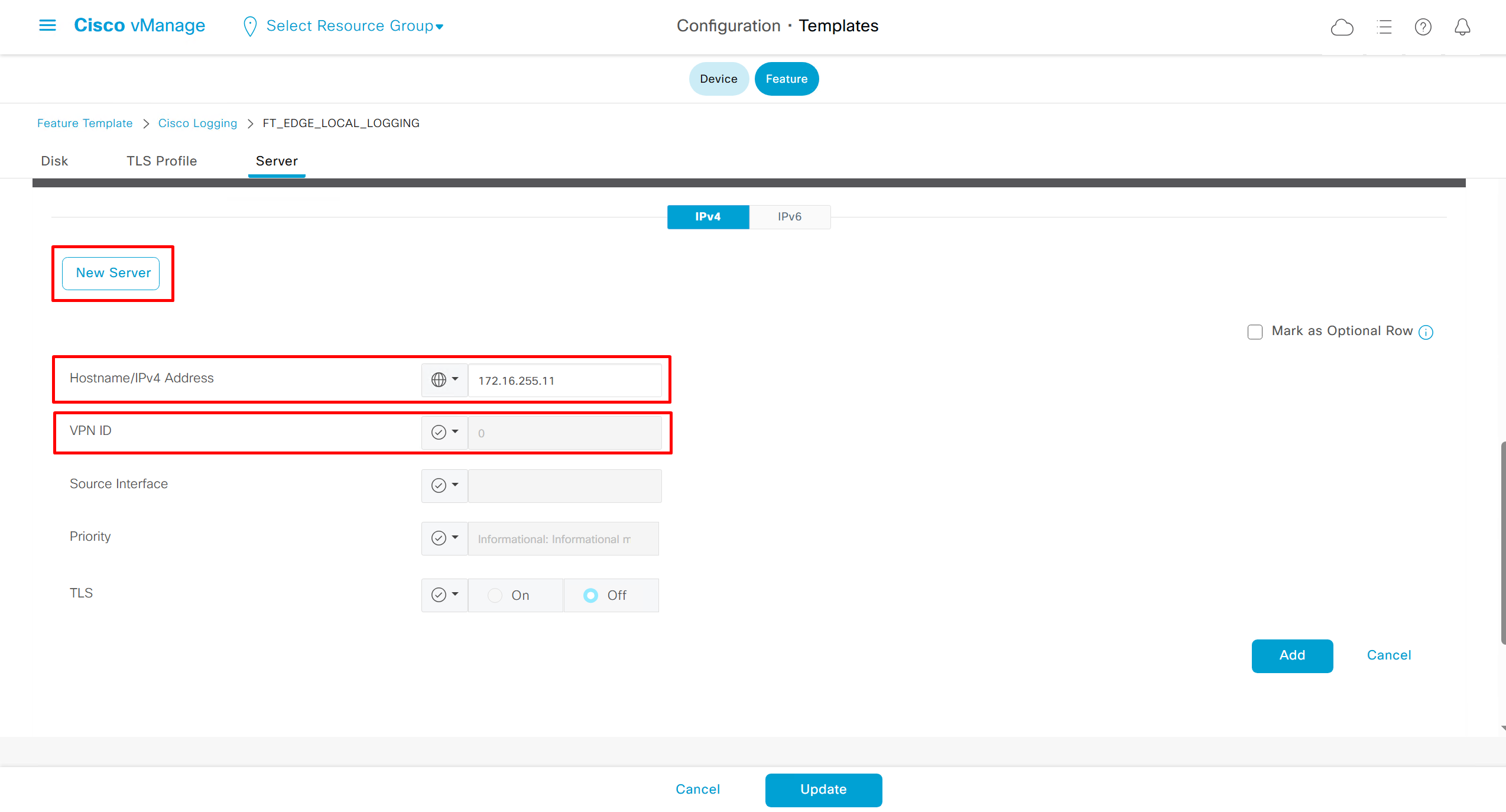
SNMP Feature Template
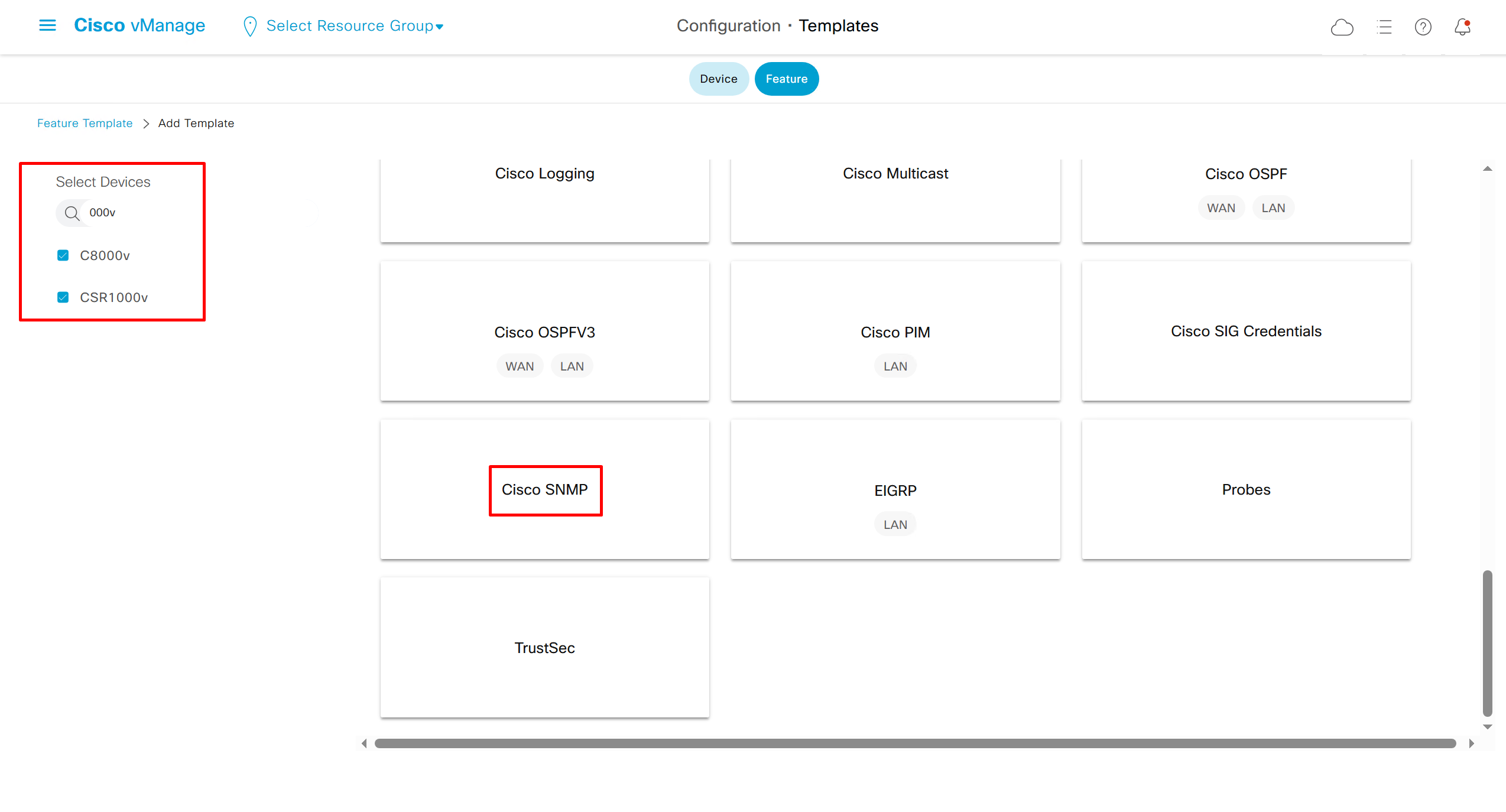

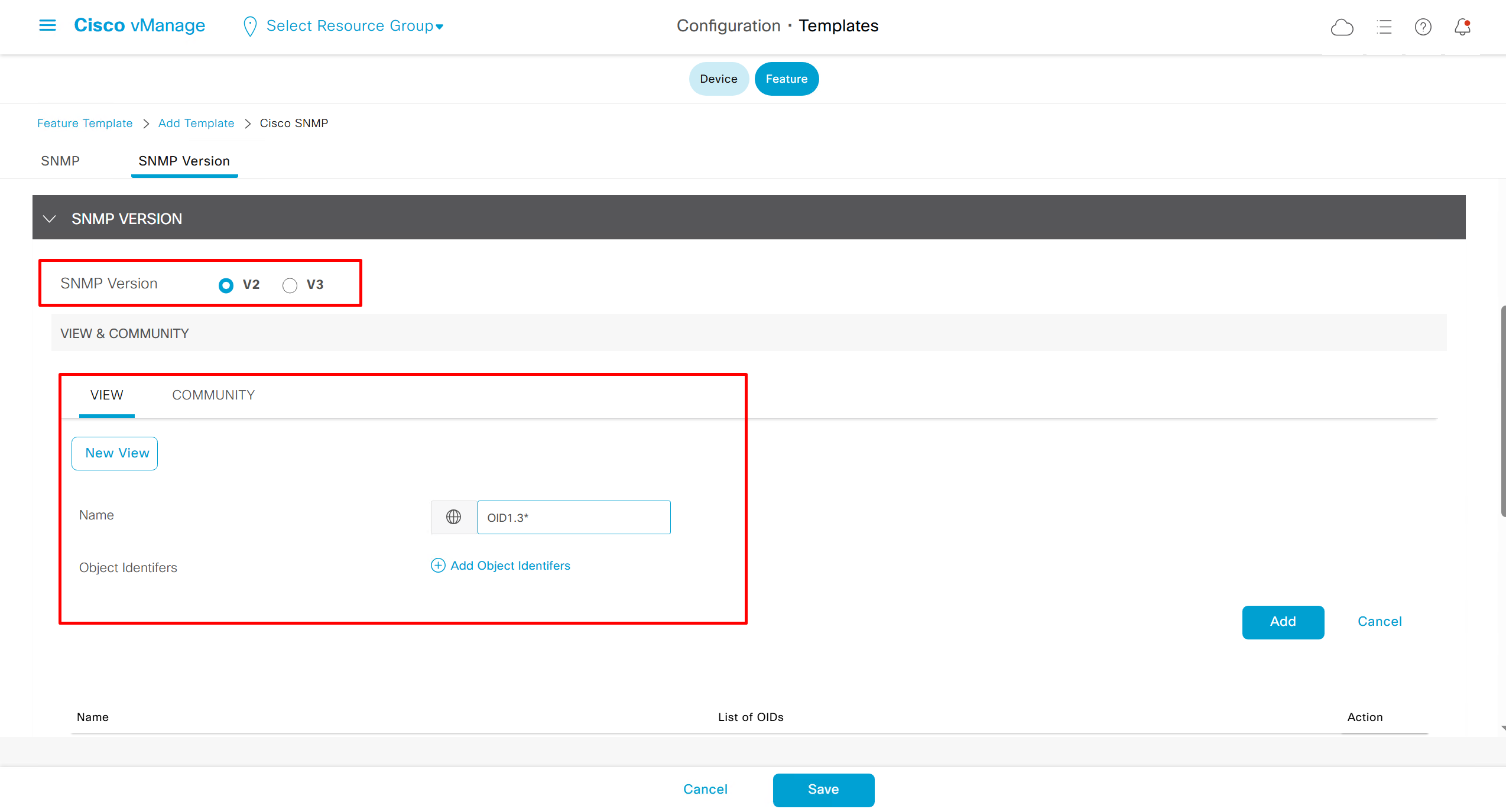
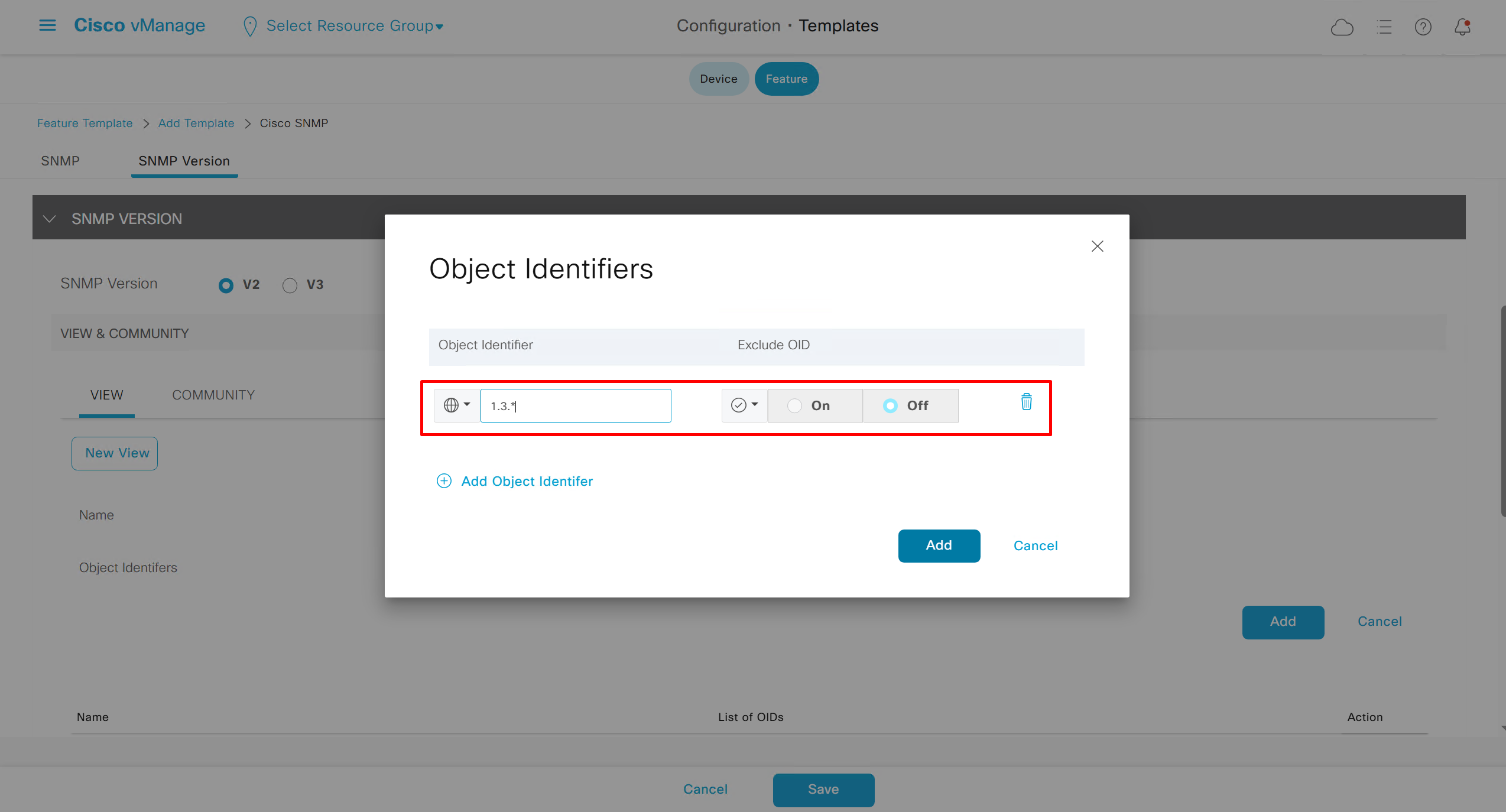
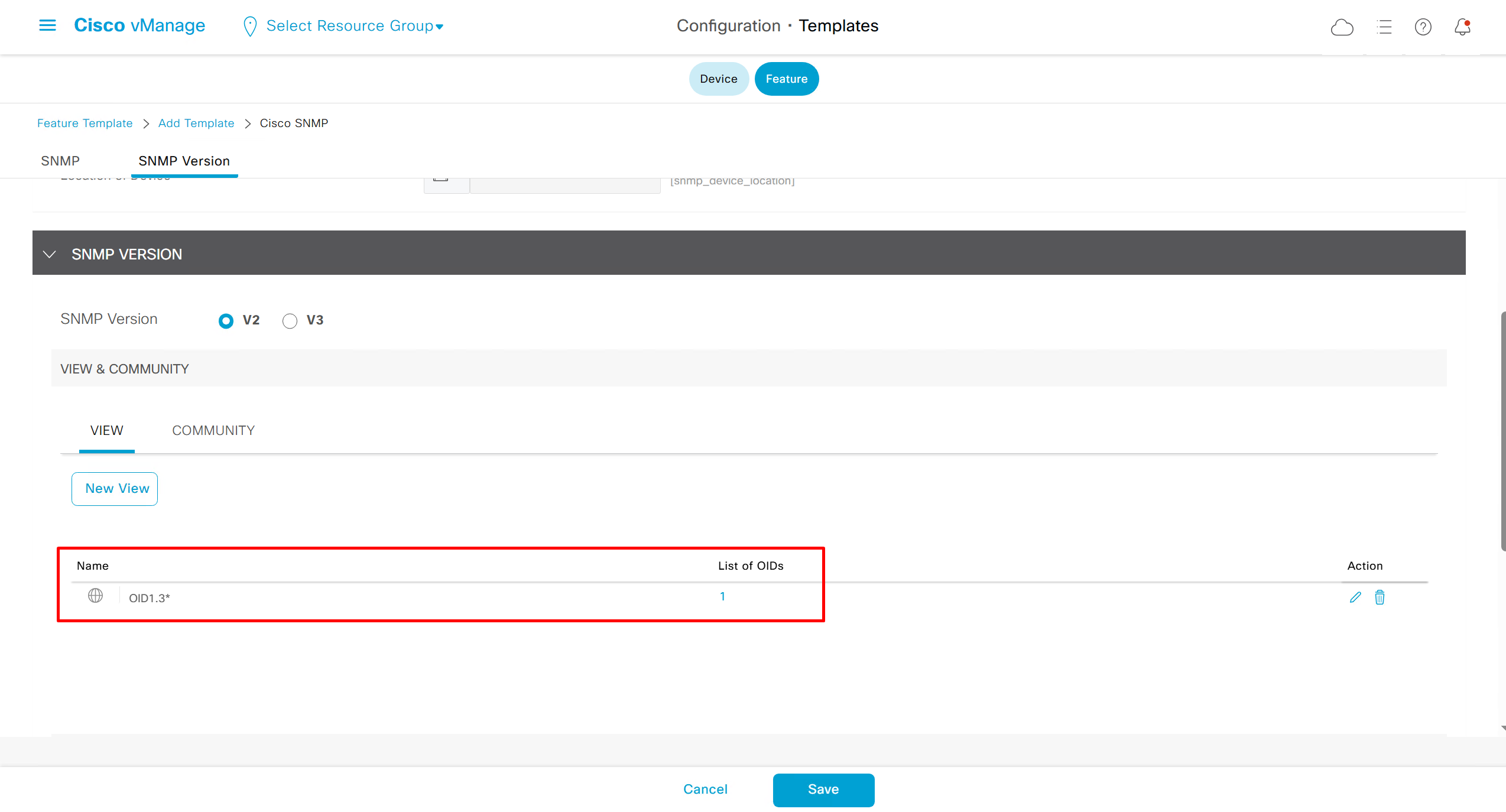
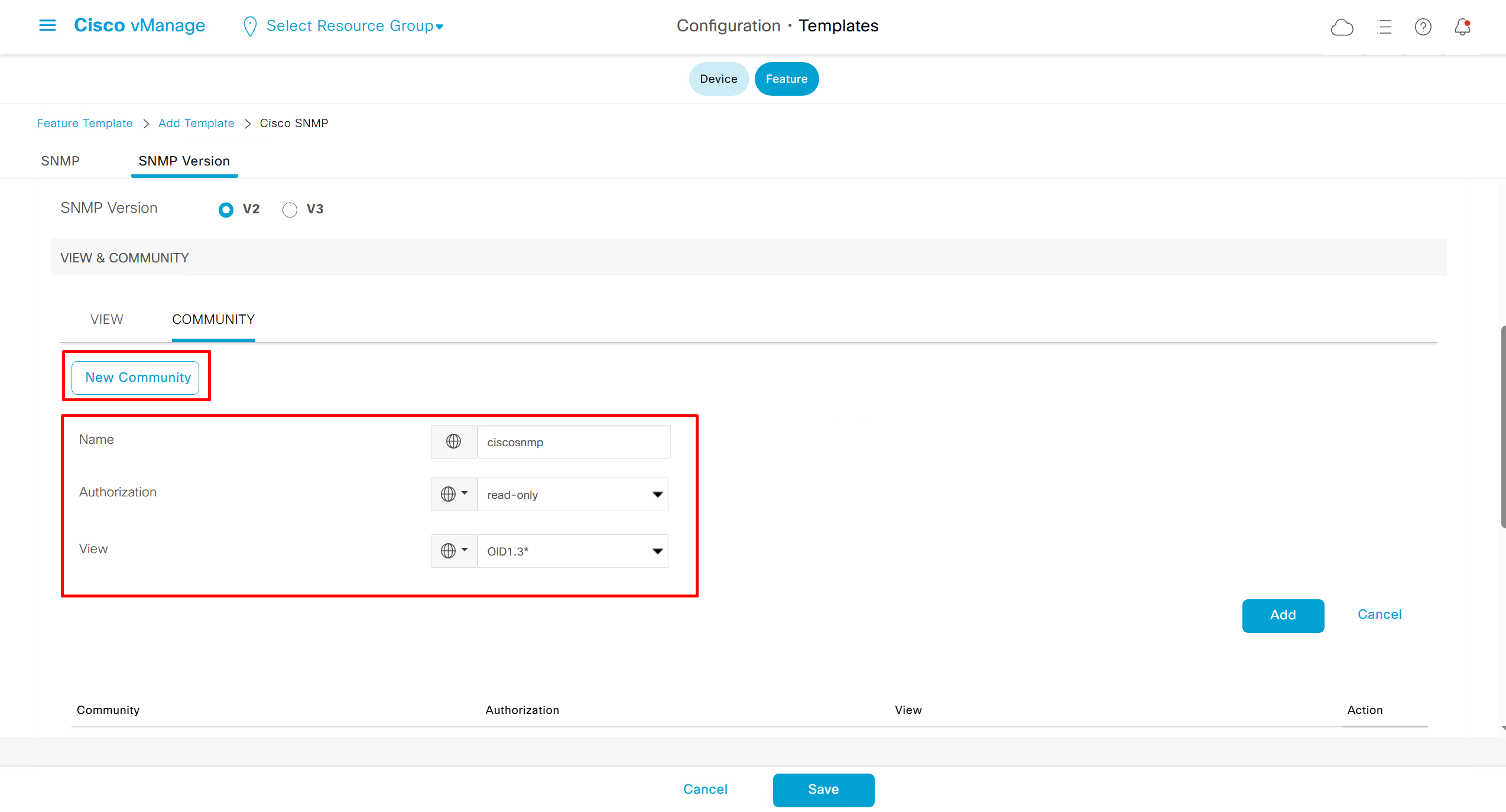

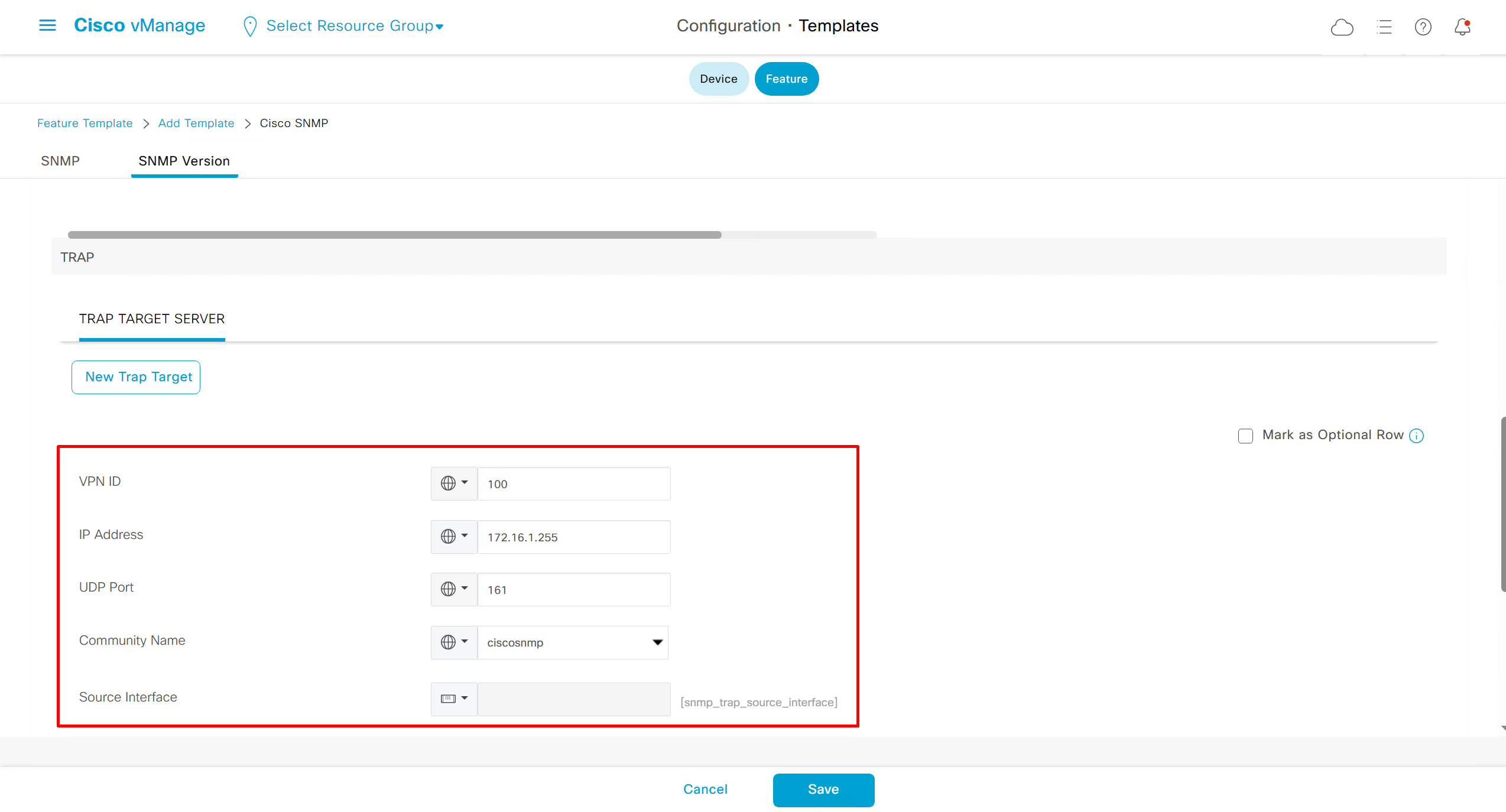
Templates on Controllers
Remember that we need to configure system, vpn 0 (routing table for transport) and interface feature templates
but when device type vManage and vSmart, template types are reduced

with vmanage and vsmart selected we can have common feature template for system and vpn
vedge cloud is applied on vbond
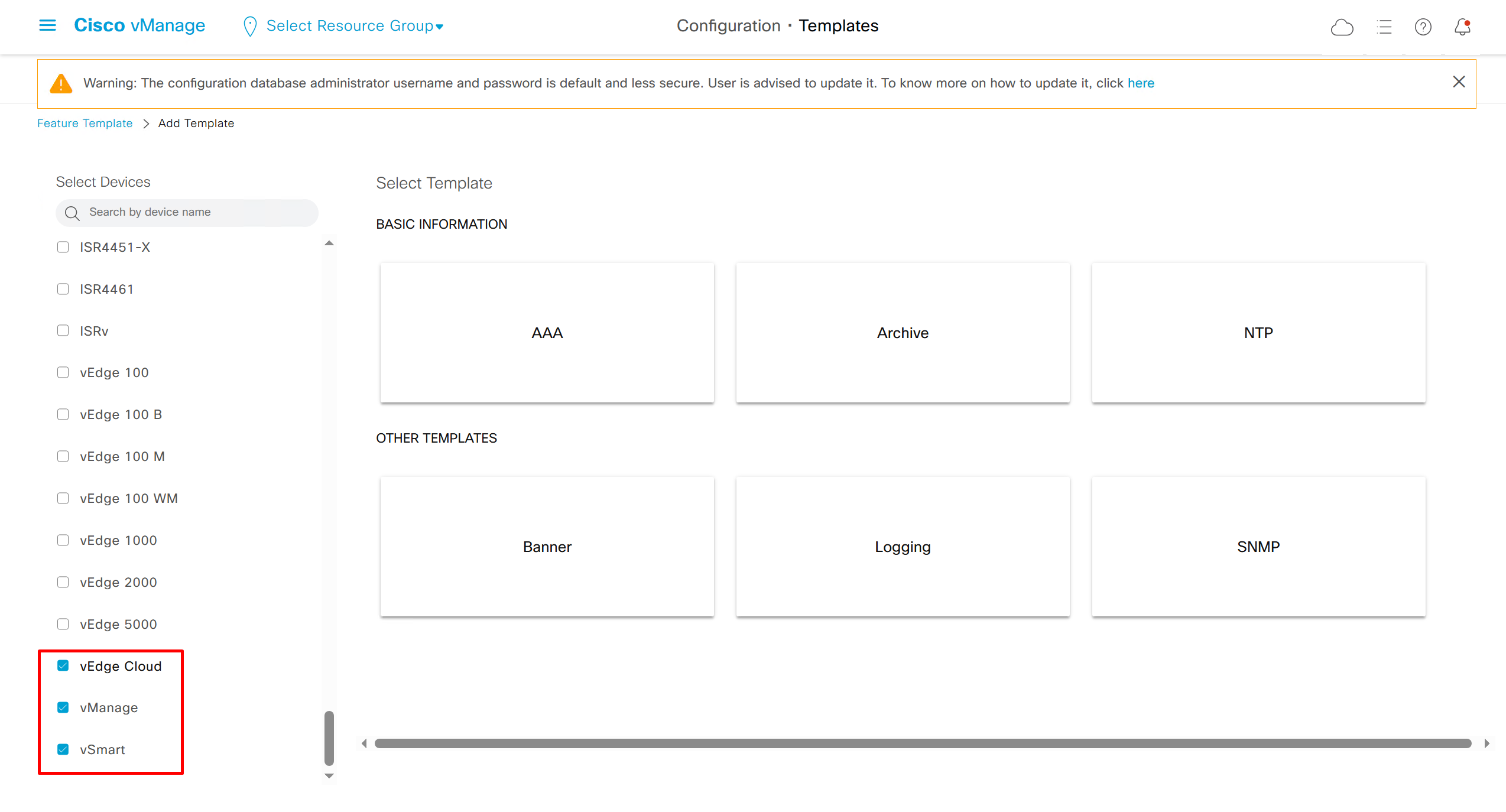
we are more limited in terms of template when we select vedge cloud, vmanage and vsmart
Lets configure template for vmanage
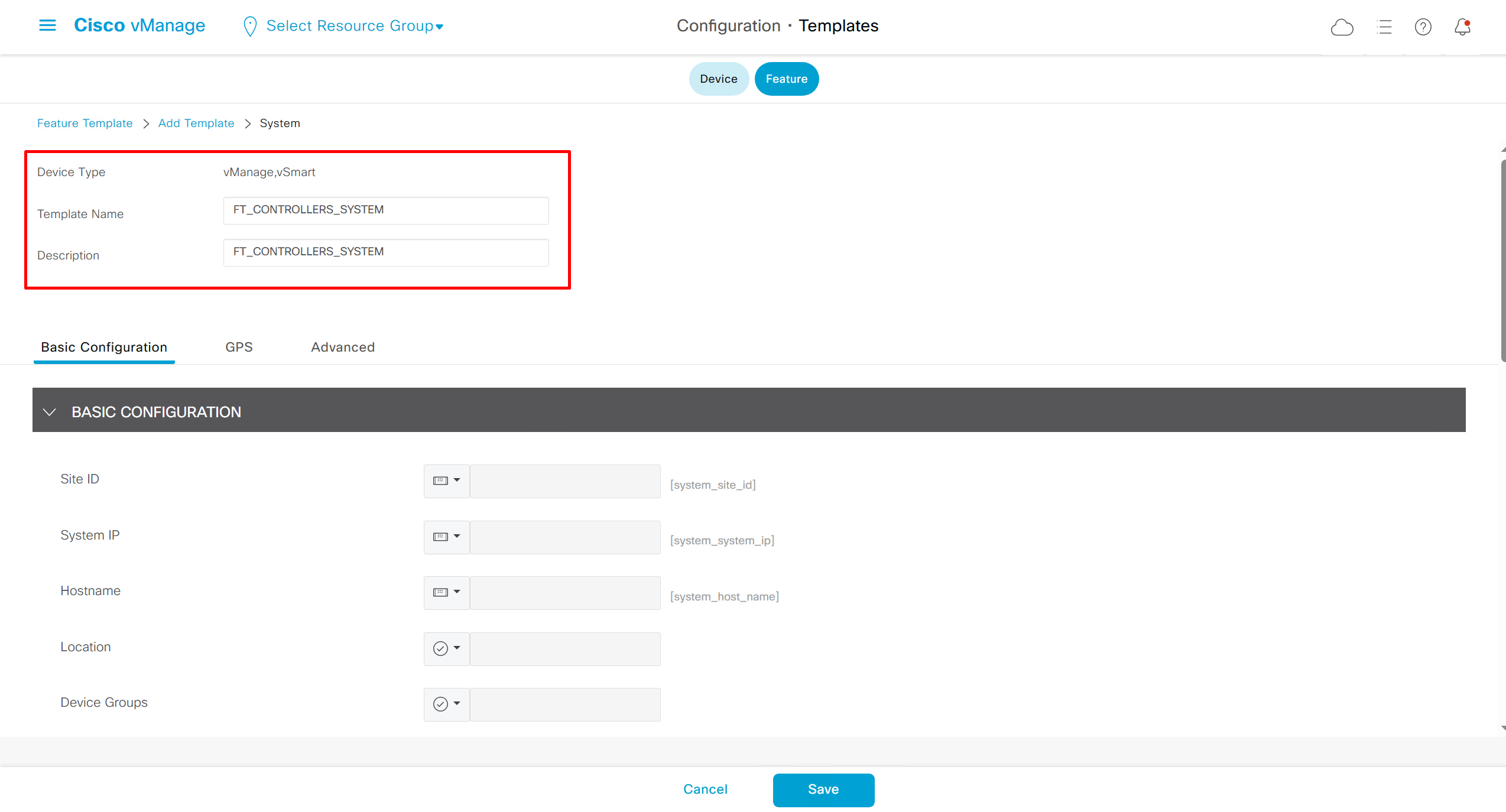
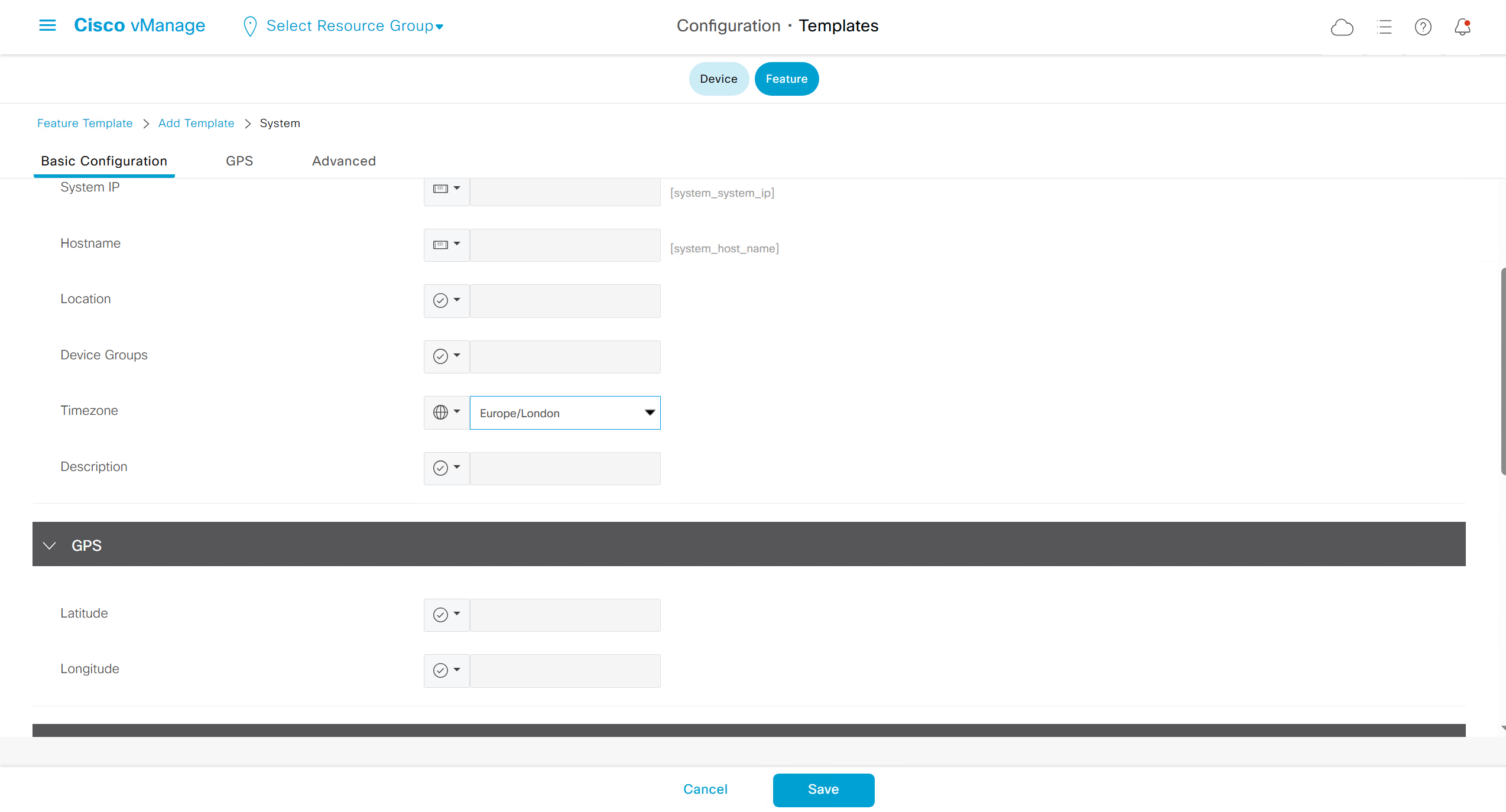
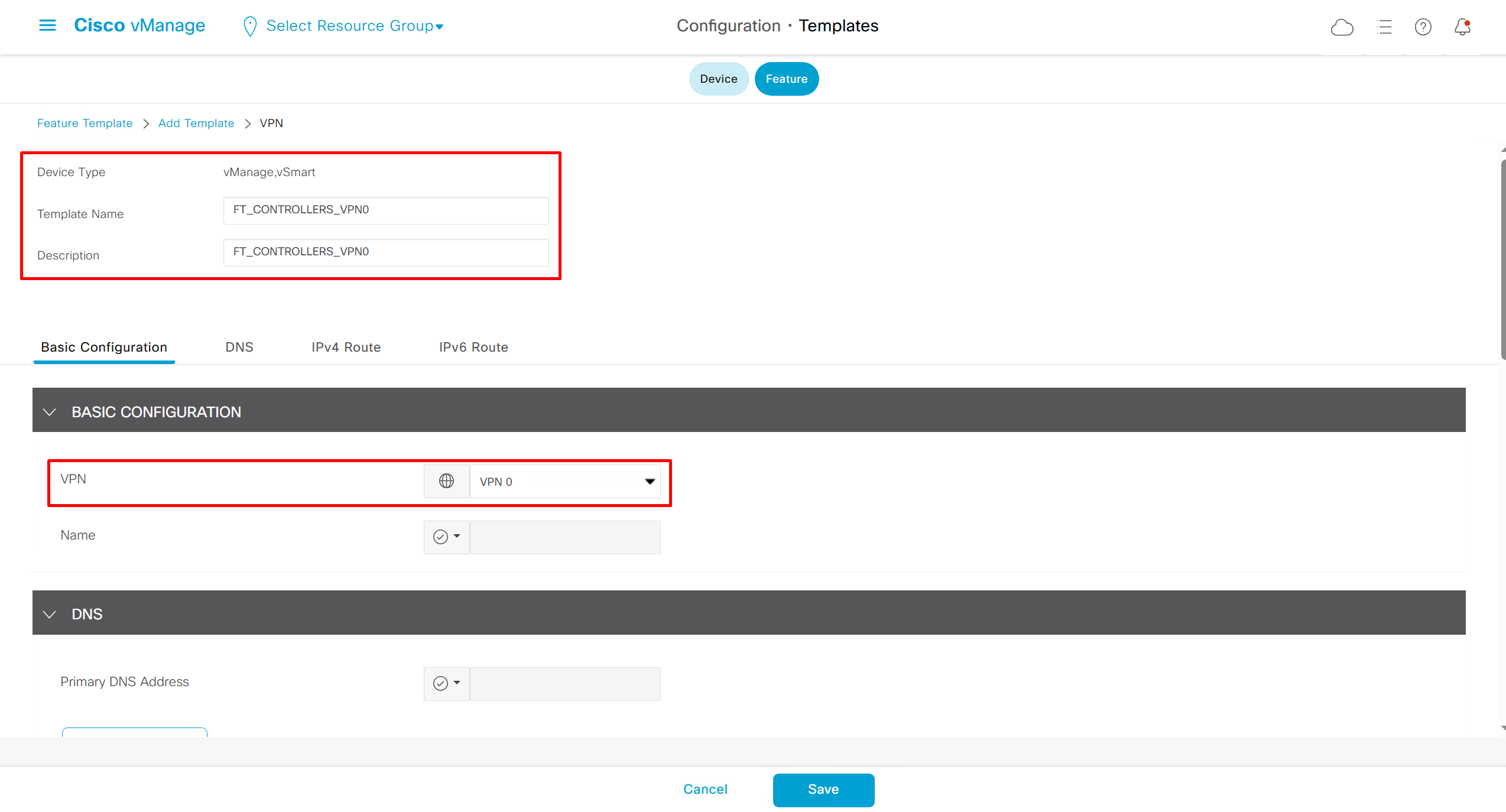

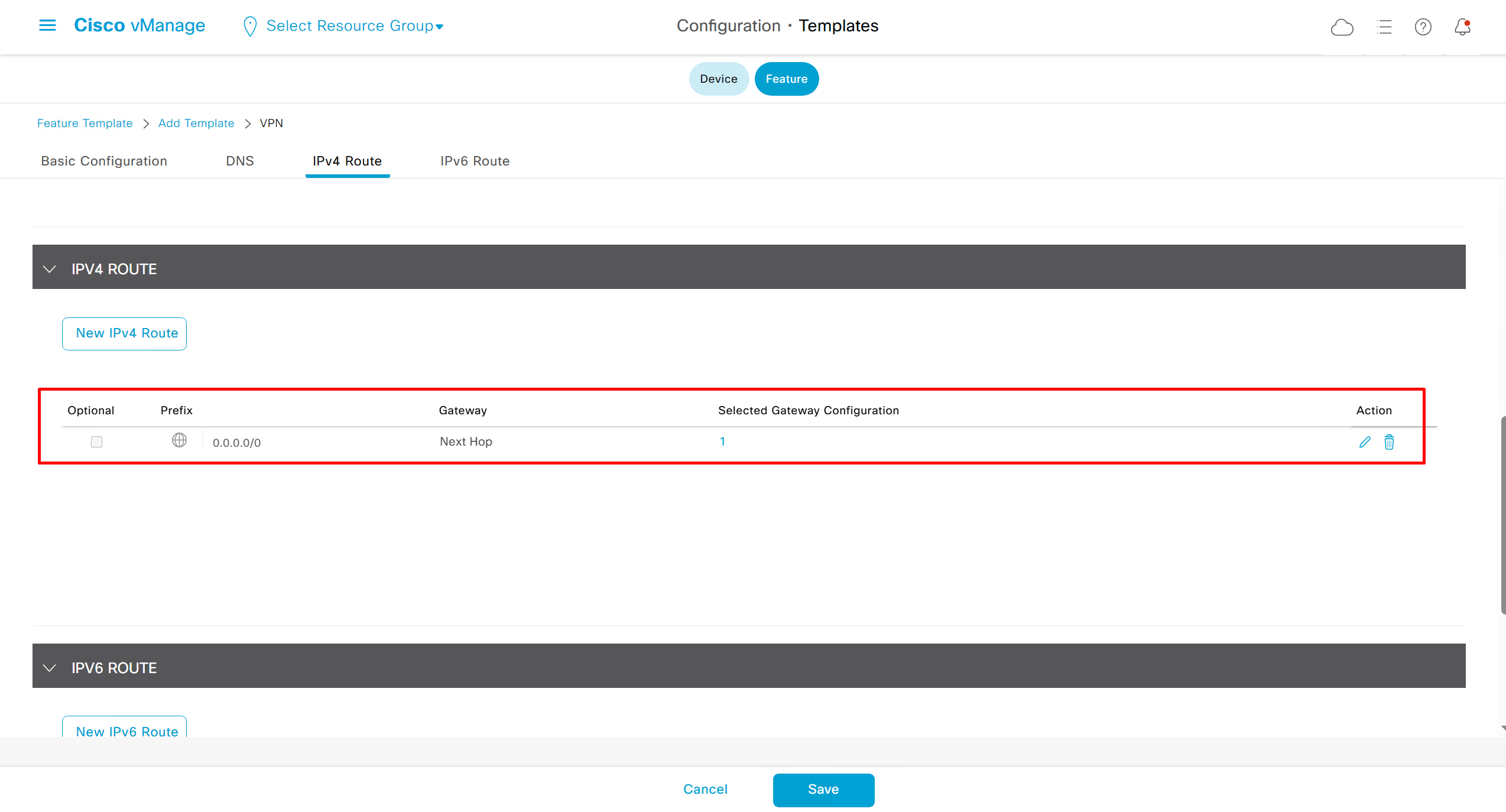
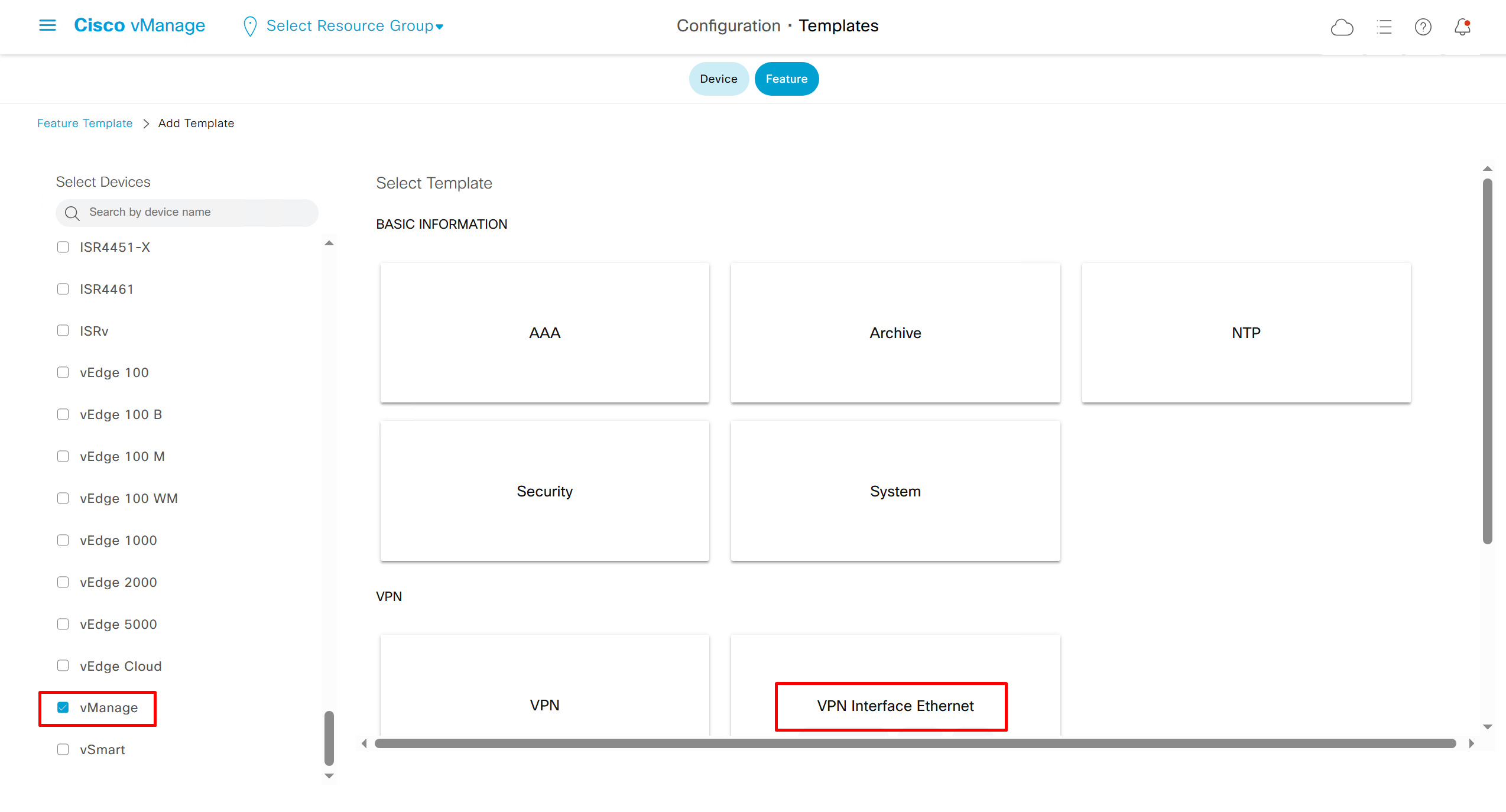
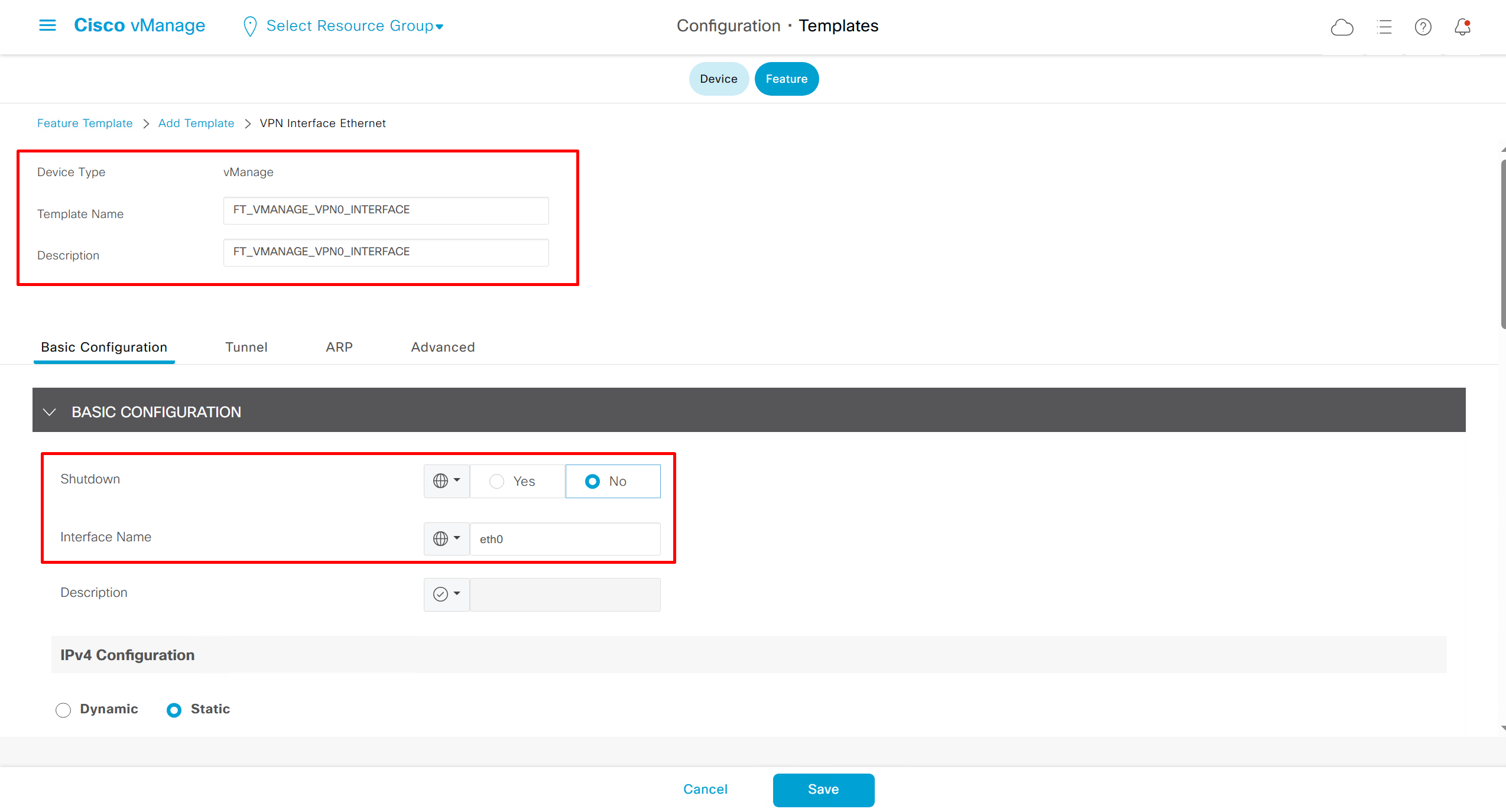

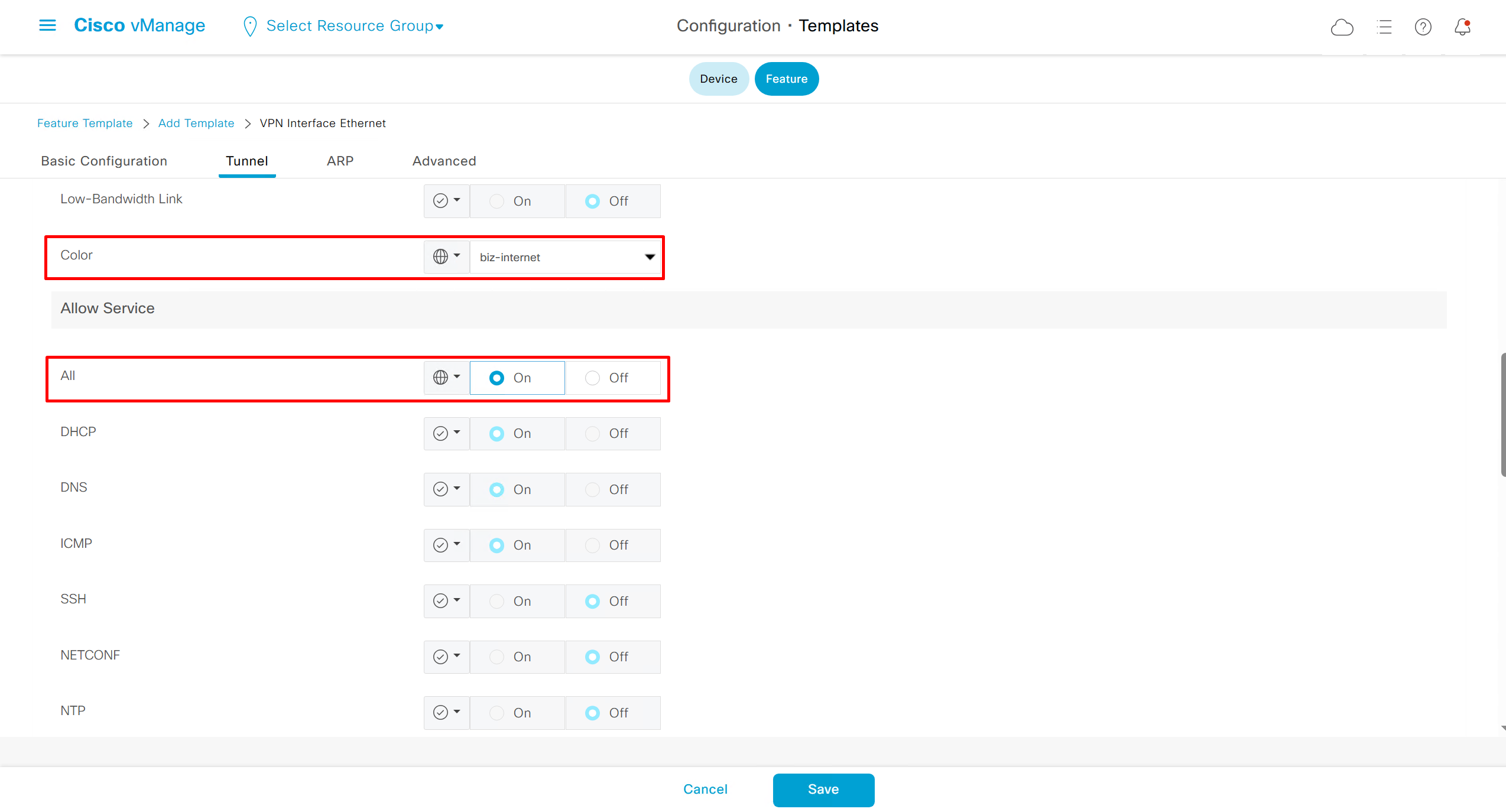


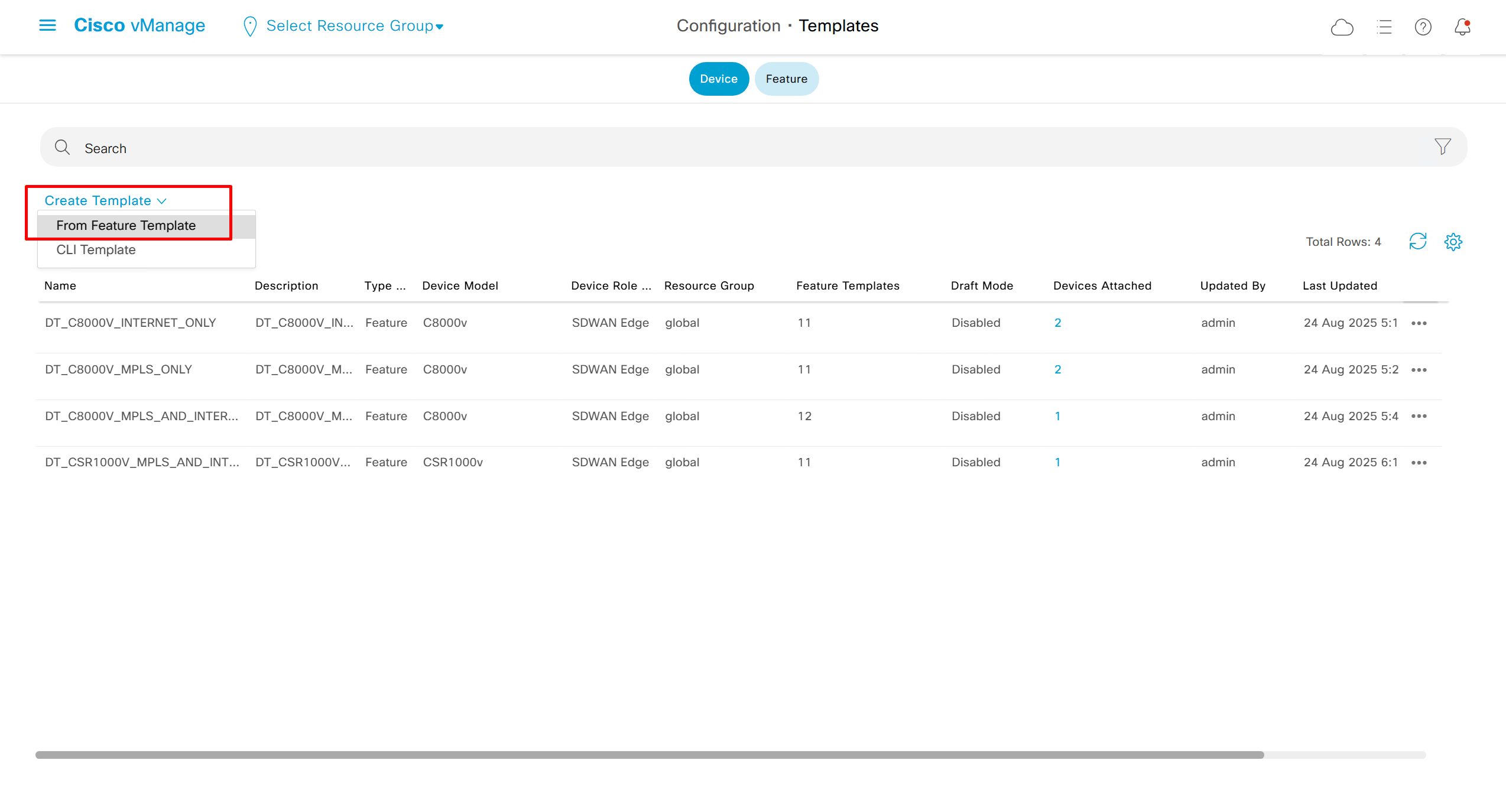

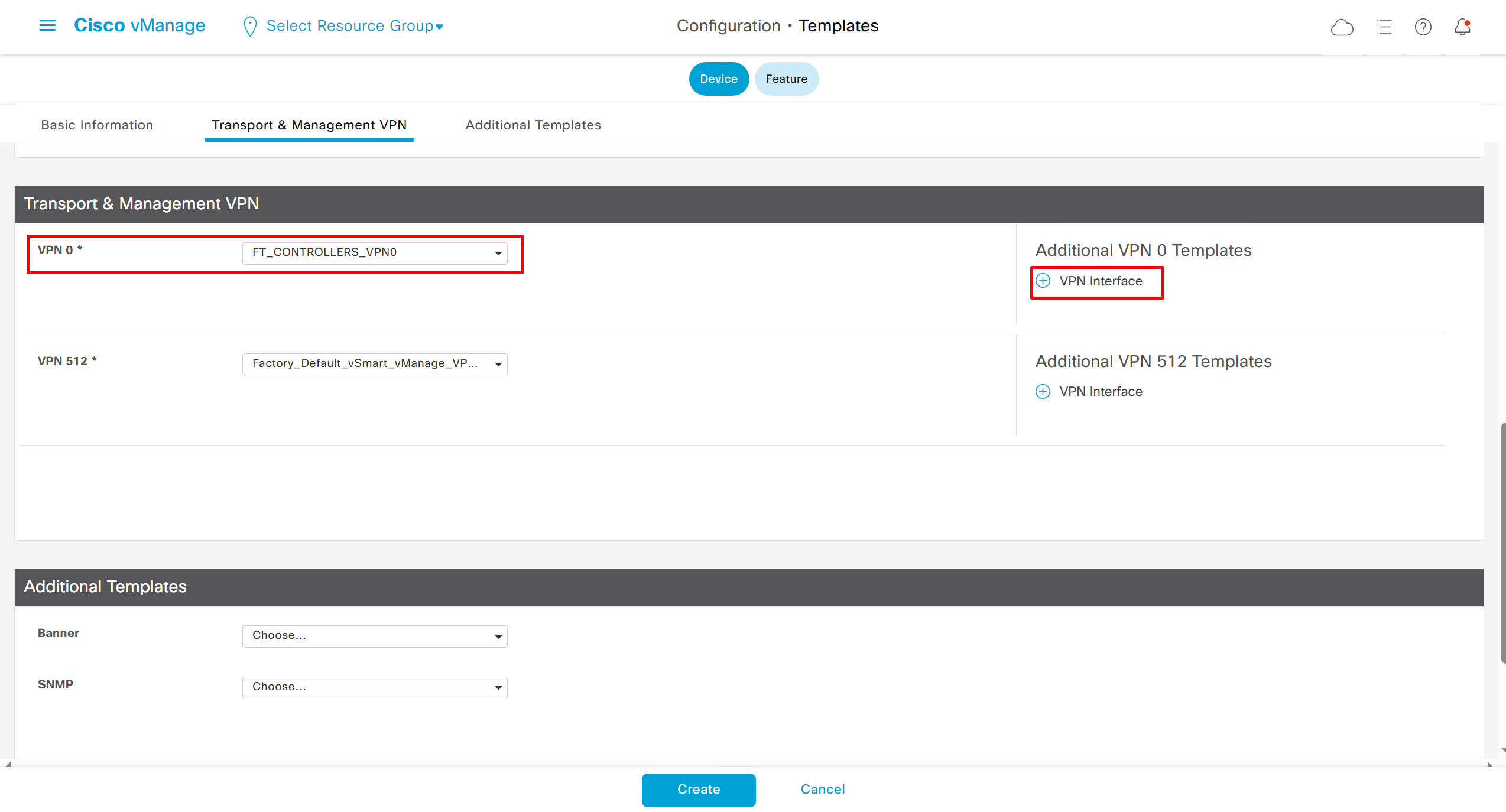
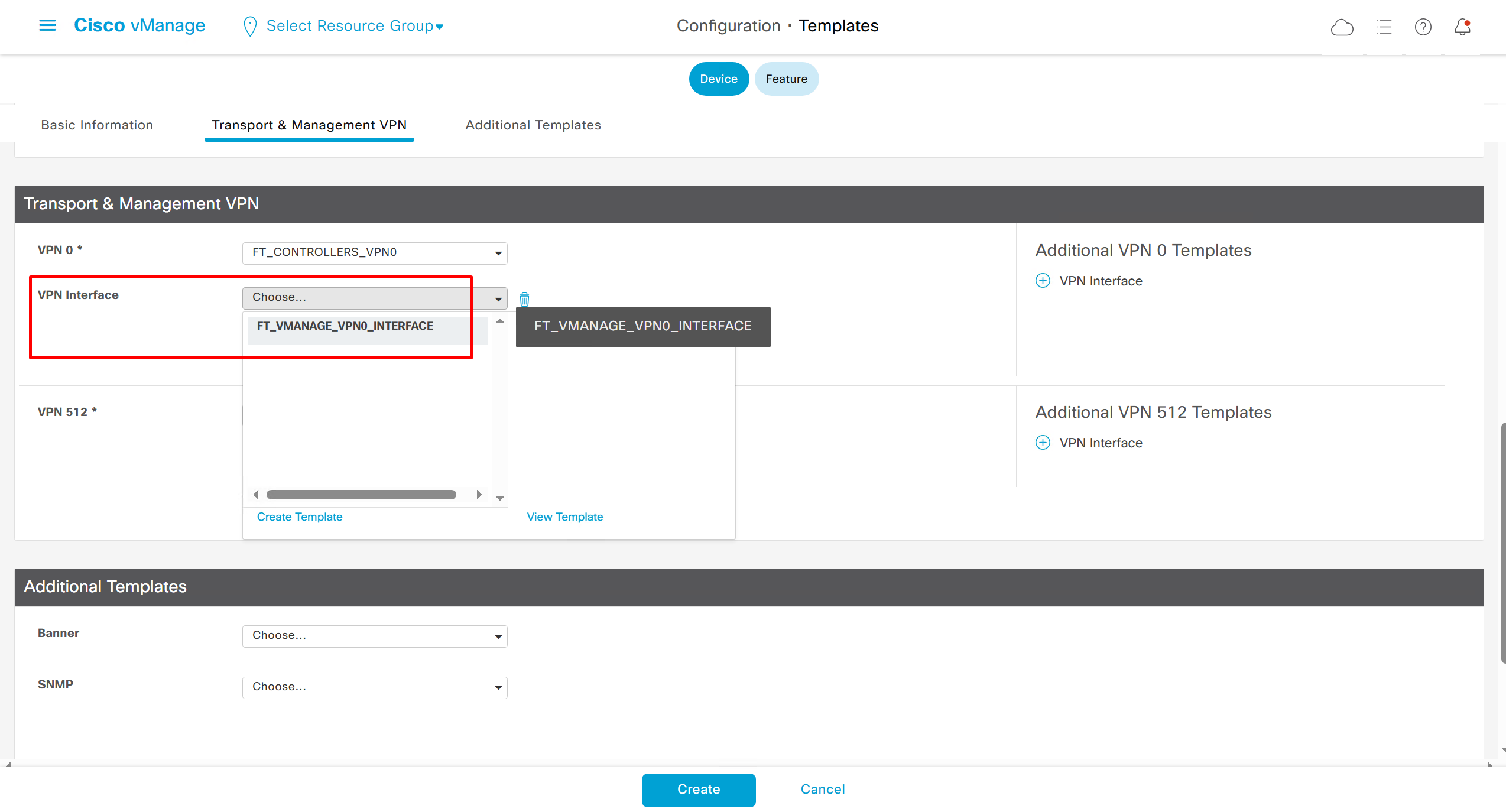
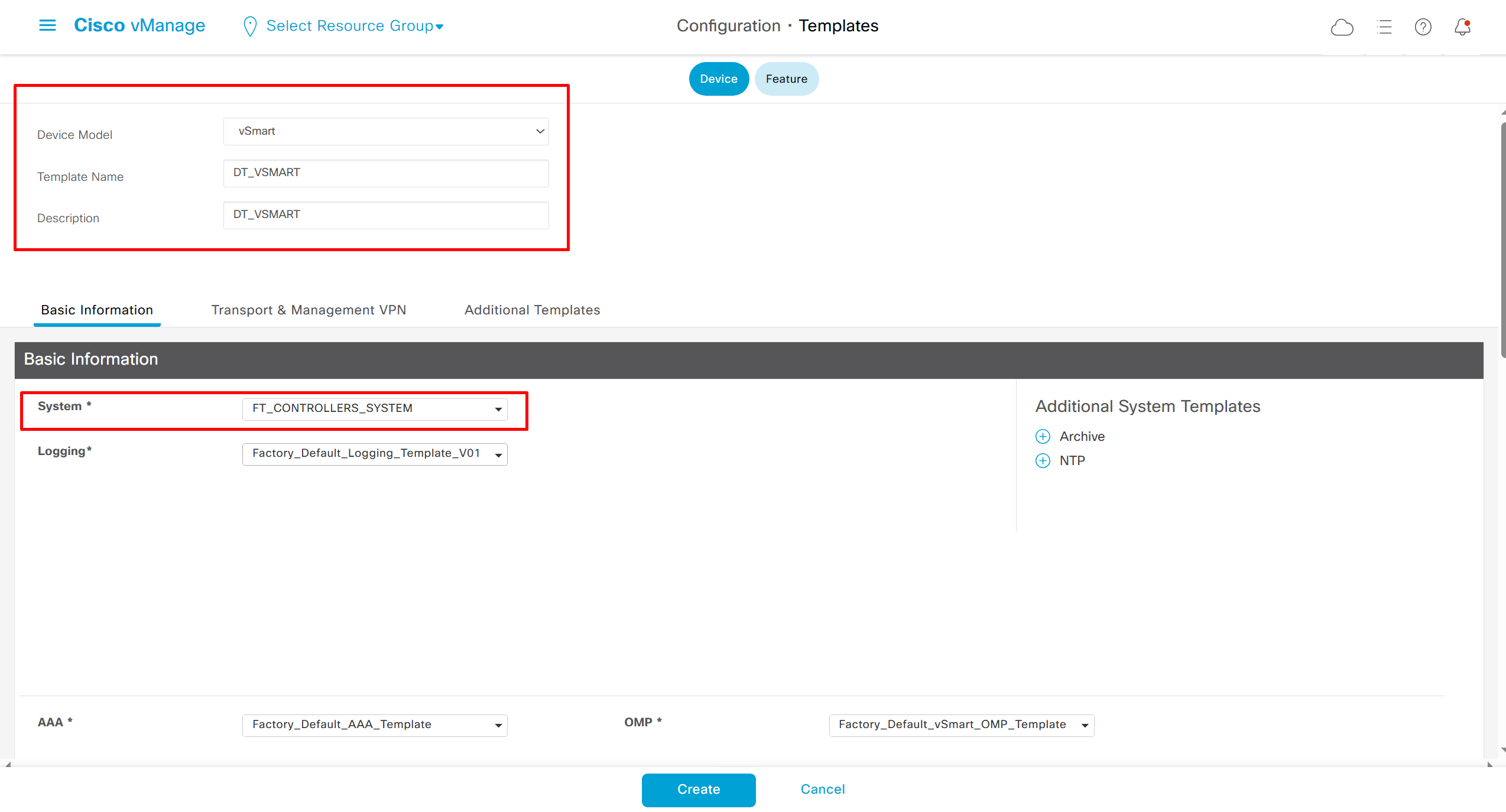
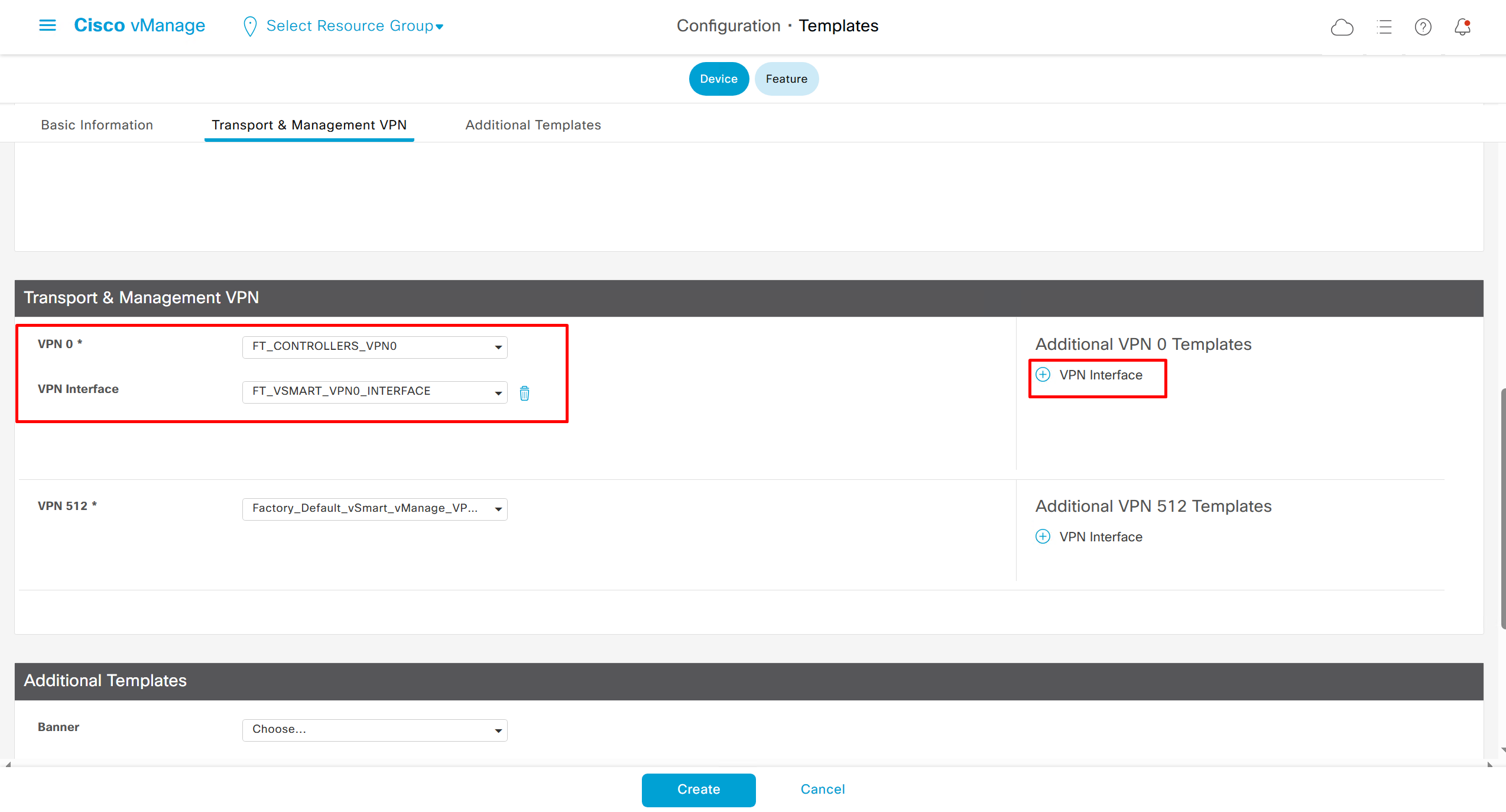
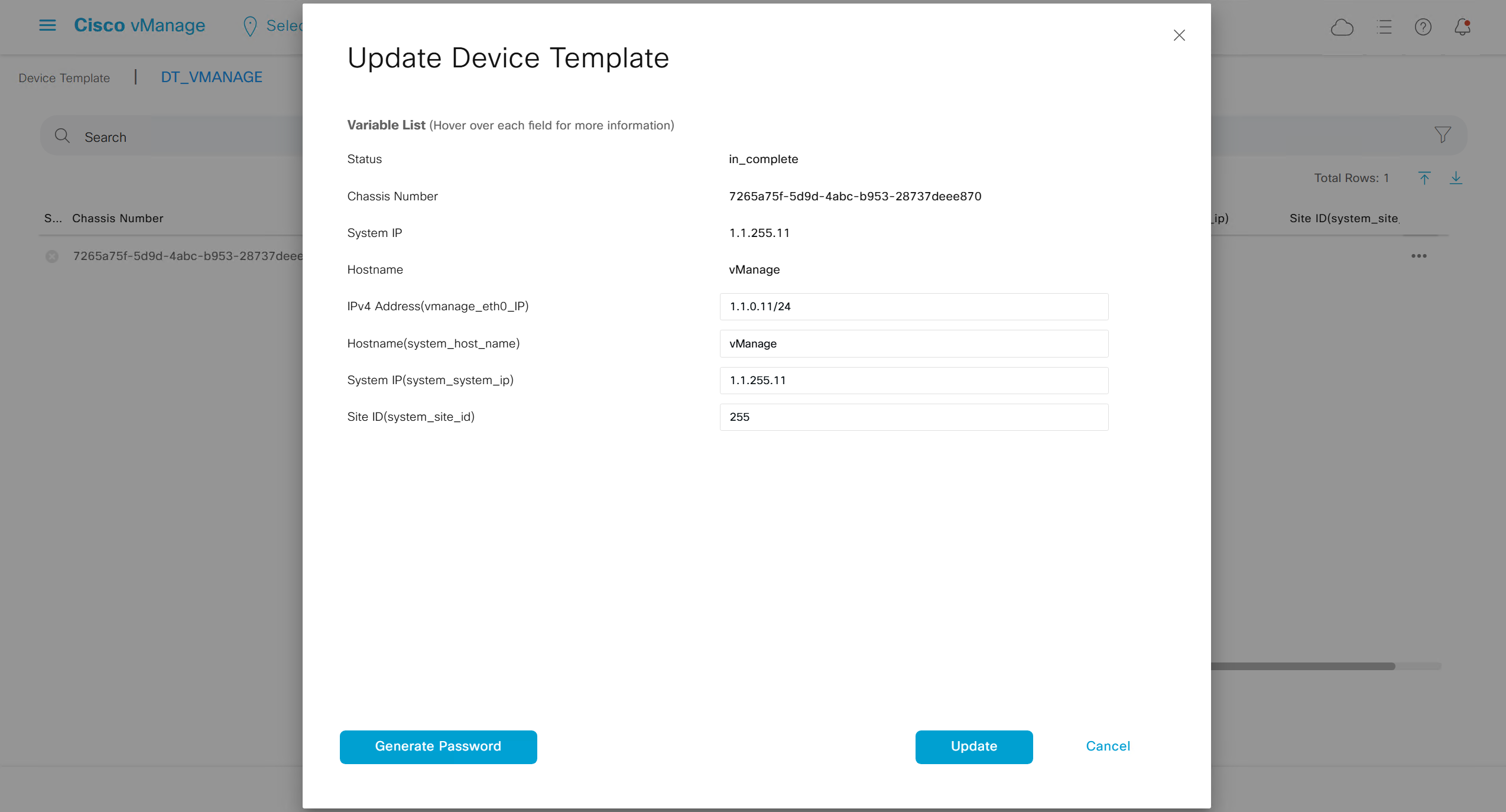
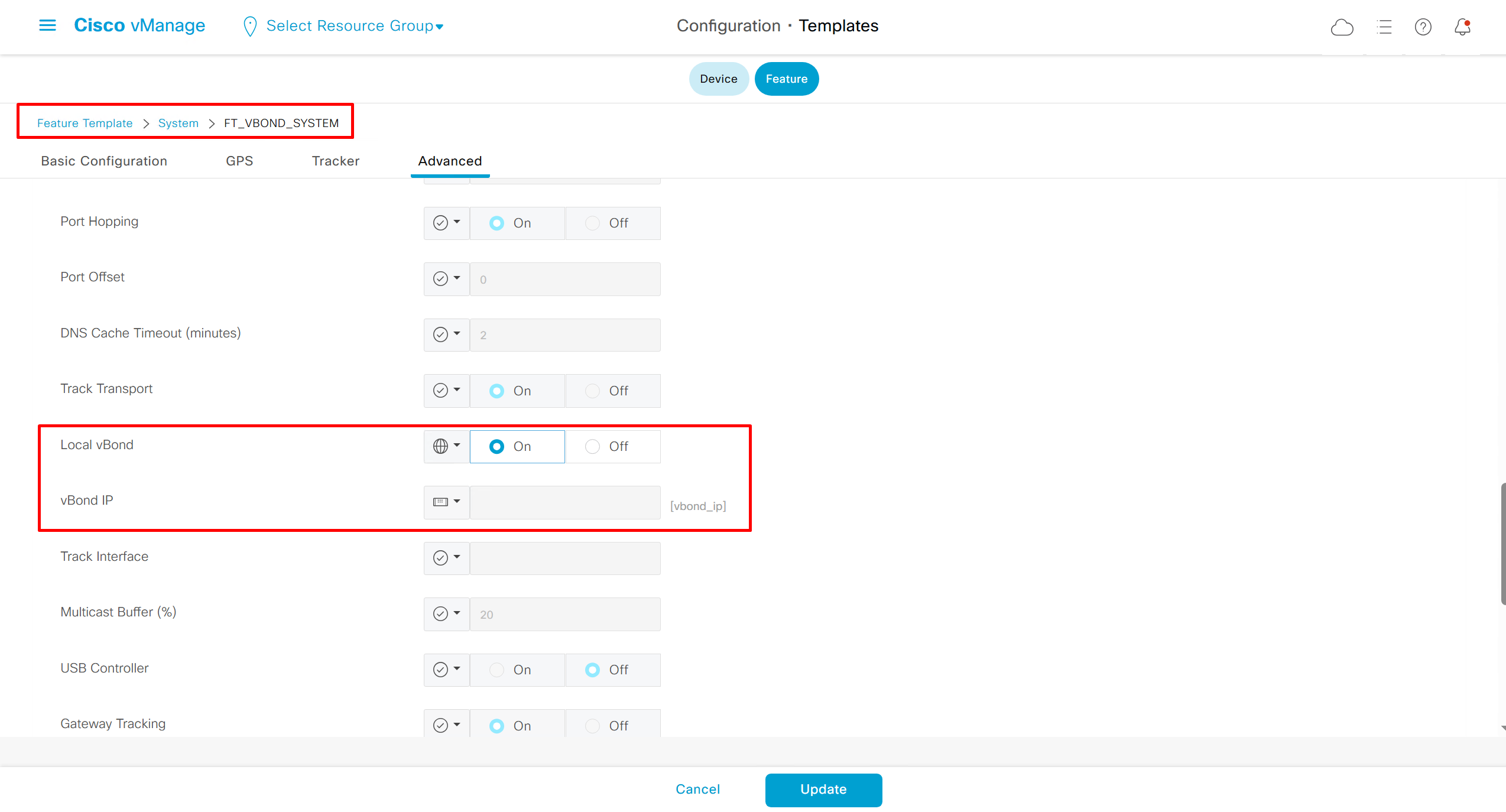
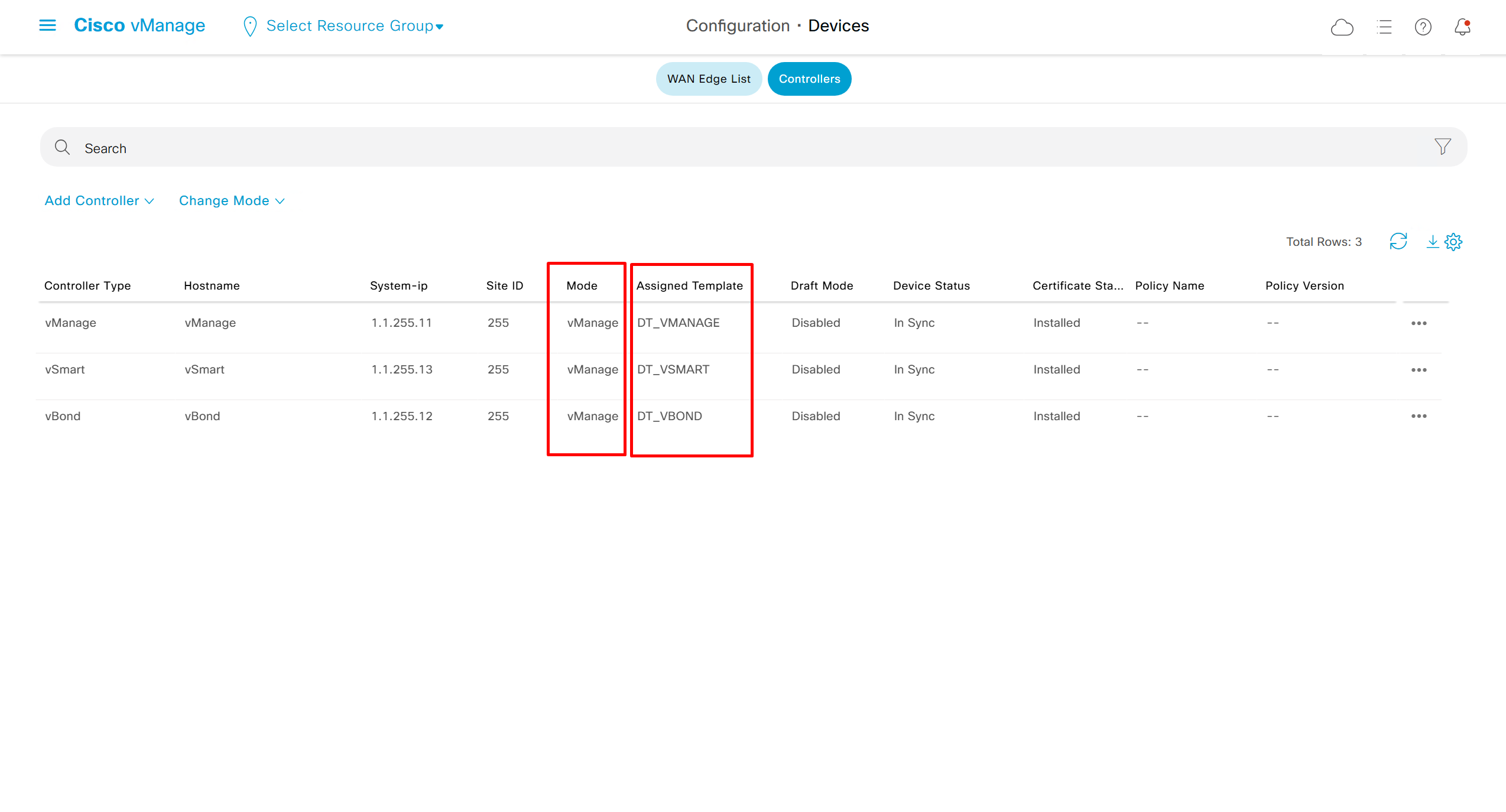
SDWAN – GUI
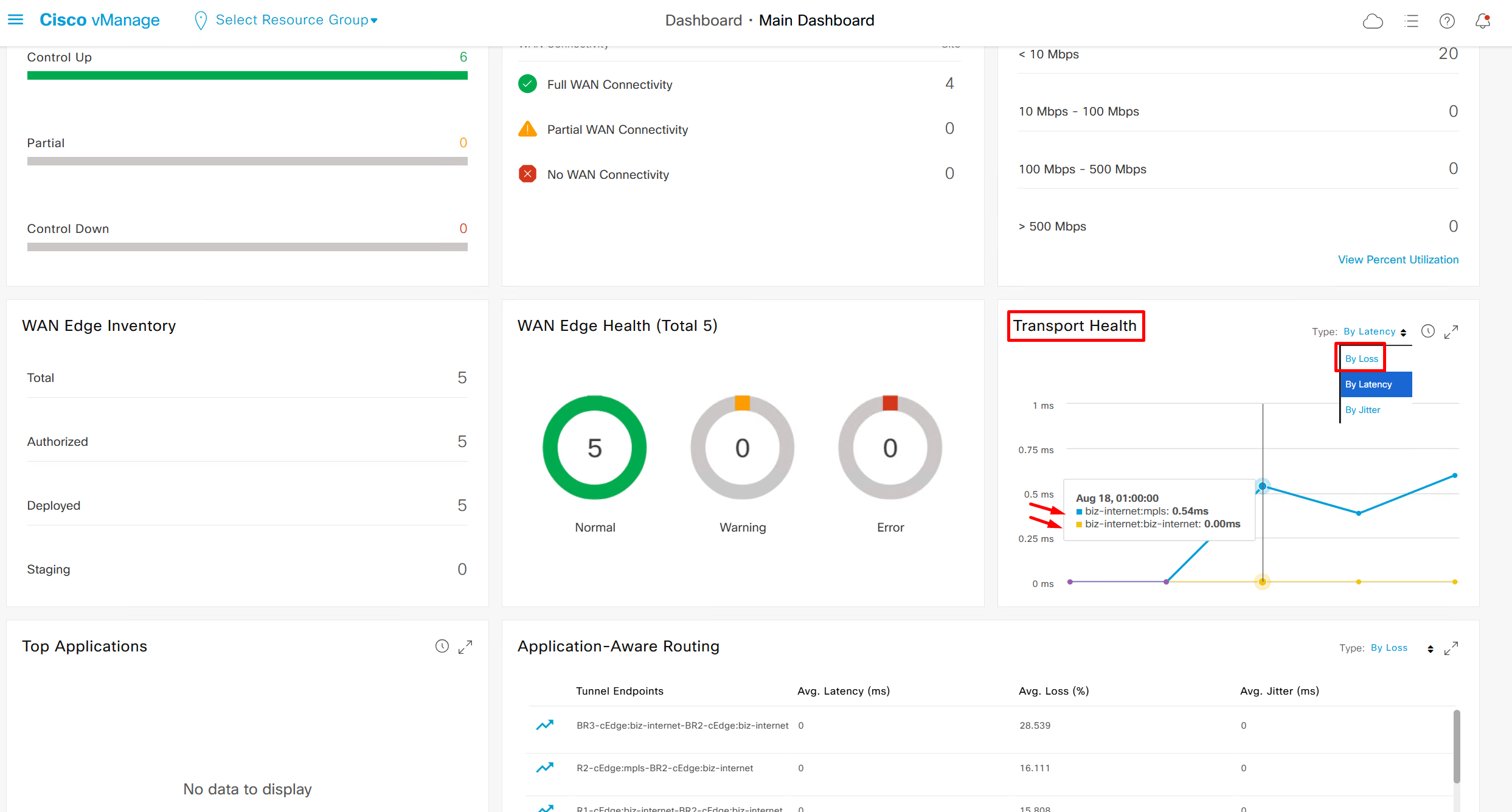
This transport health is of different transports to transports and by loss by default

We can see that these are BFD stats telling us that BR3-cEdge (branch 3) to BR2-cEdge (branch 2) there is Avg Loss of 28.539 %, this is per connection as compared to color to color stats shown in “Transport Health”
It is displayed by loss by default
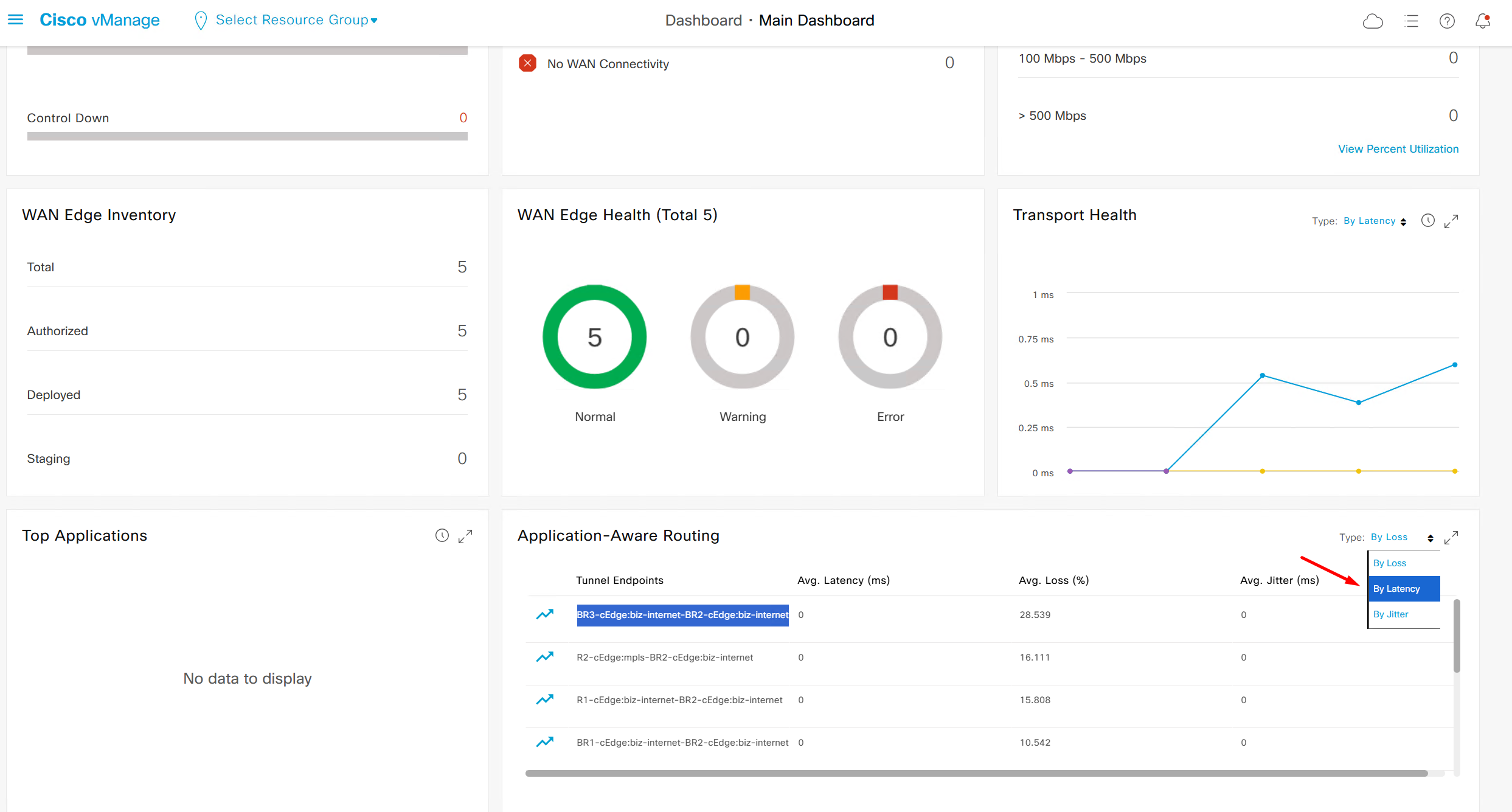
Monitor > Geography shows geographical location of our sites / edges
for now because we have not assigned any coordinates, it shows as blank
Monitor > Network
shows all network devices and all of their information such as names, states, system ip, reachability, site id, bfd tunnels, control DTLS sessions, version, up since, device groups etc
Clicking on one of the devices takes us into the device
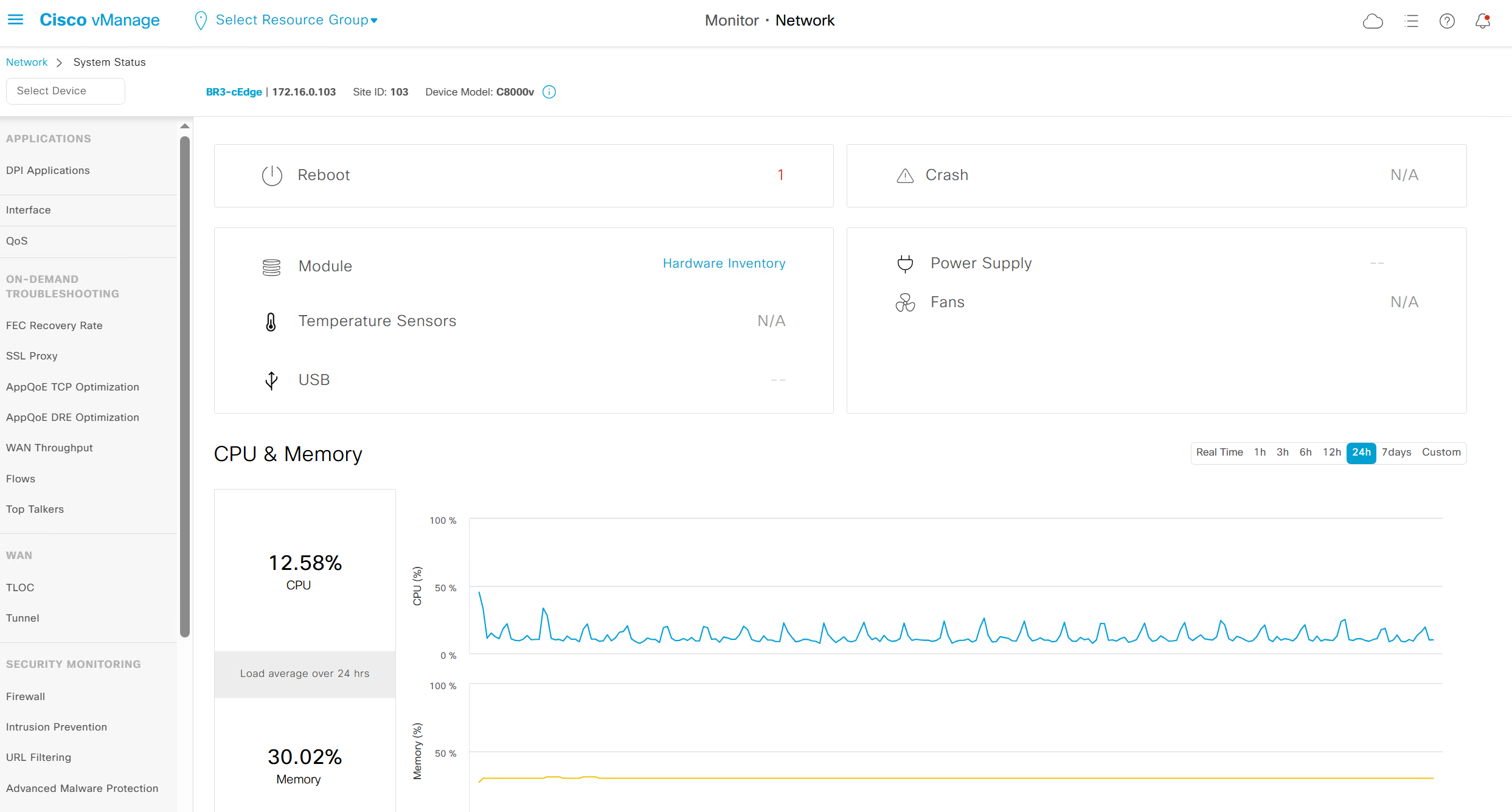
we can see hardware inventory, power supply and fan info – reboot menu – CPU and memory
Hardware Inventory
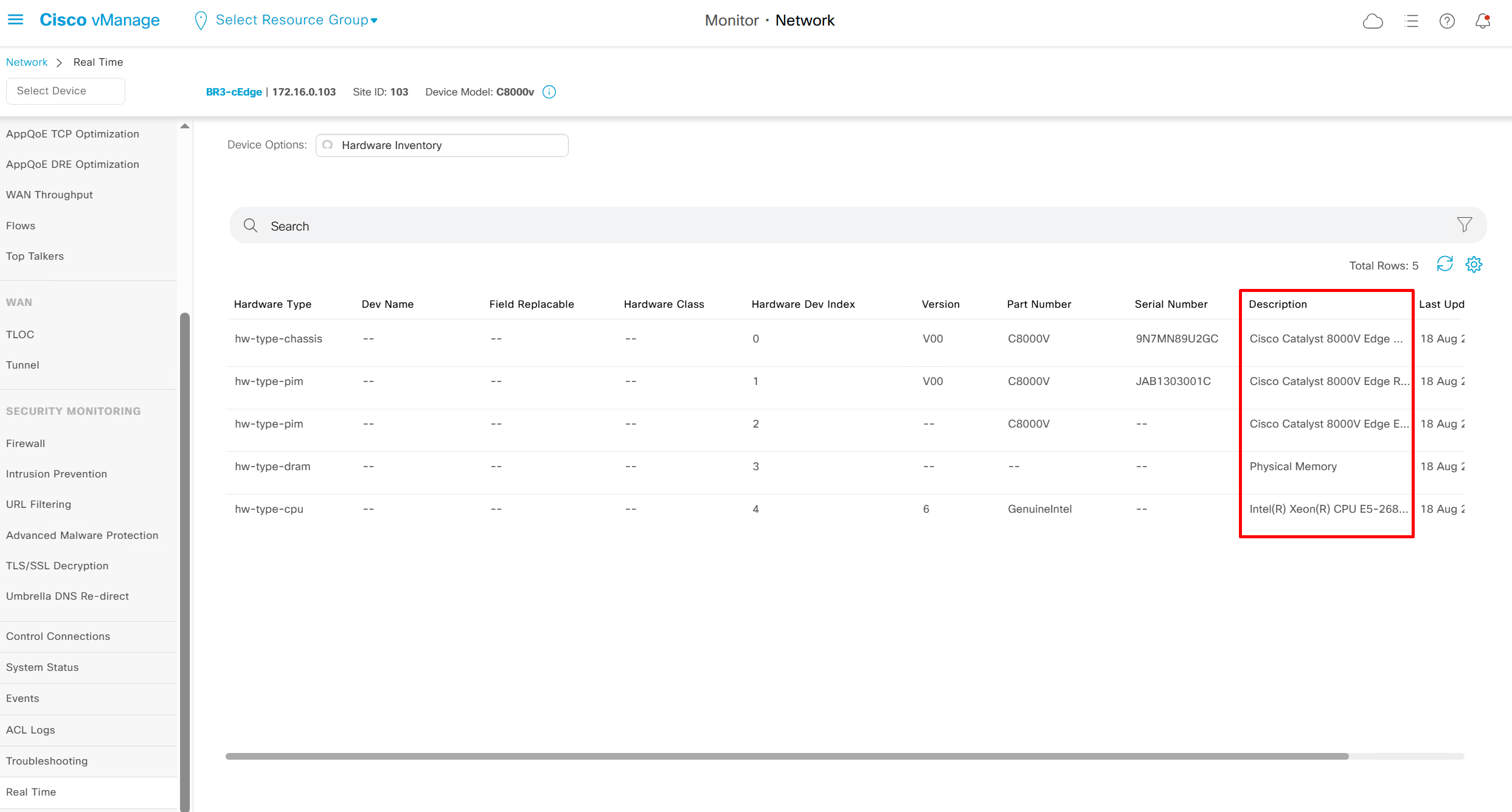
DPI Applications – when traffic passes through router, traffic discovered applications show here
it is not showing as no traffic is passing through router
Interface shows all stats on interfaces

This is good place to check the admin / operational status of the interfaces
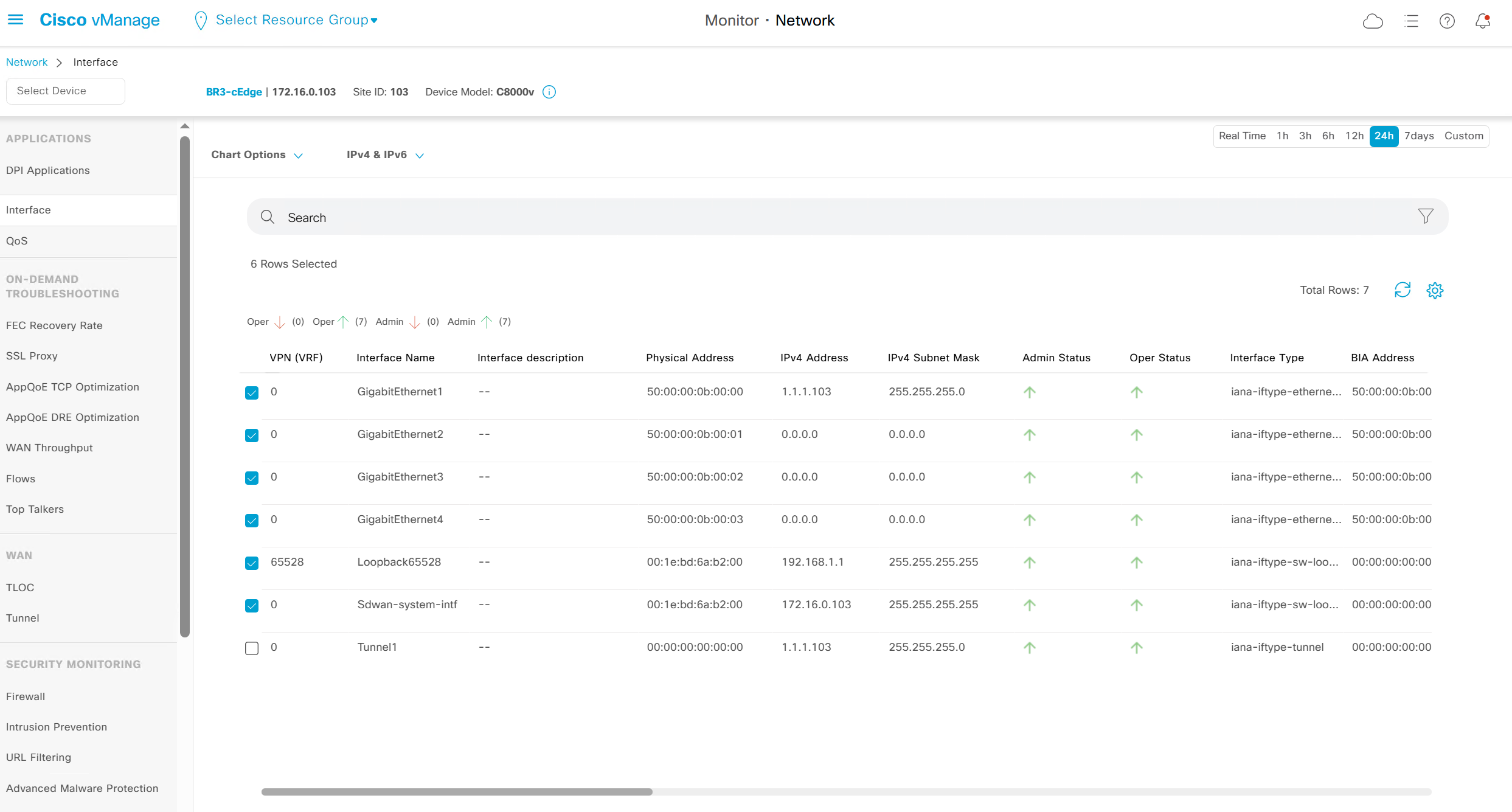
WAN throughput, Flows and Top Talkers as there are TCP optimisation features and are only available on hardware routers
It says “WAN Throughput is not applicable for C8000v”
It says “TCP Optimization Flows are not applicable for C8000v”
It says “Top Talkers is not applicable for C8000v”
WAN > TLOC

WAN > Tunnels
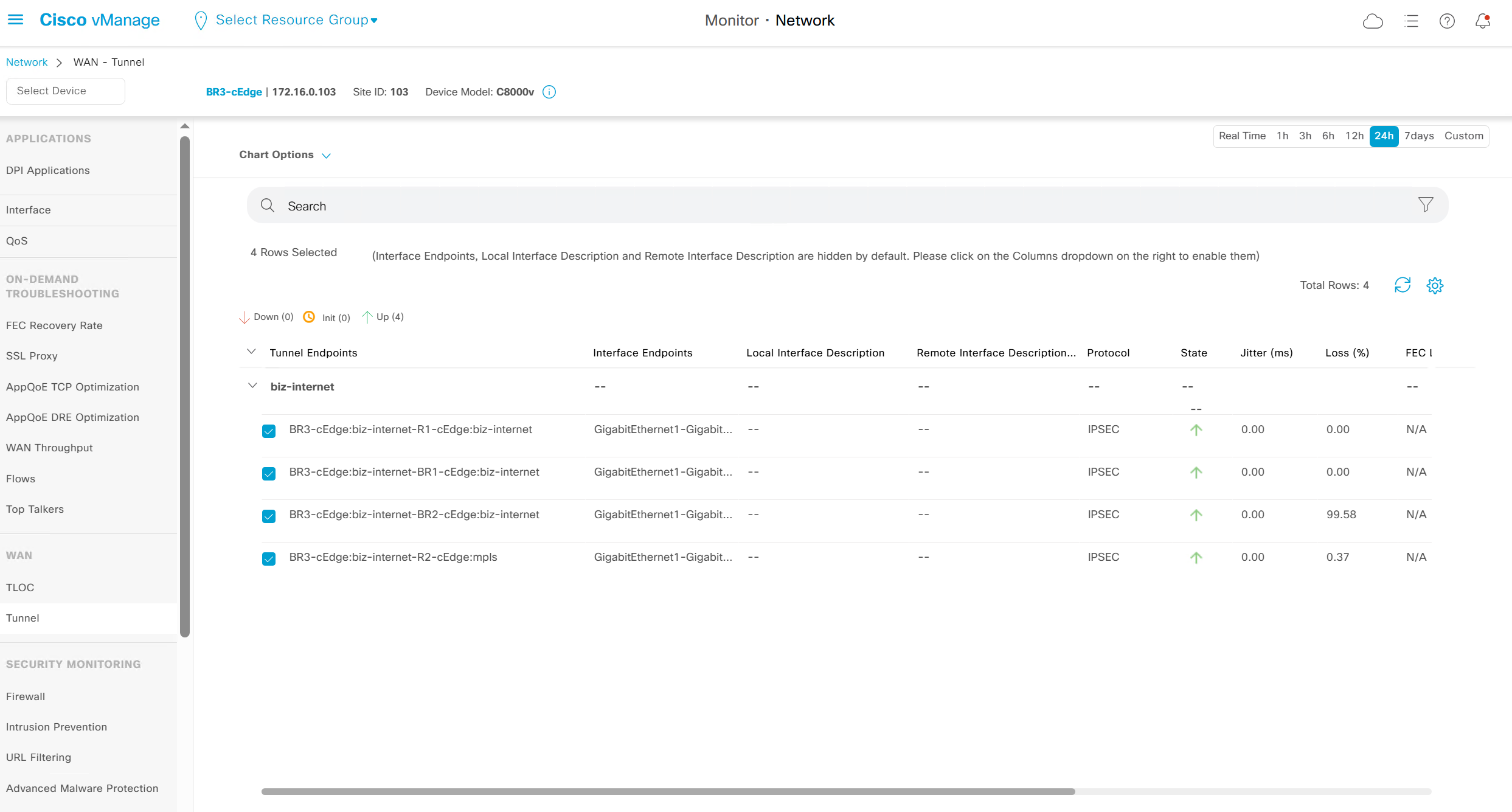
Control Connections
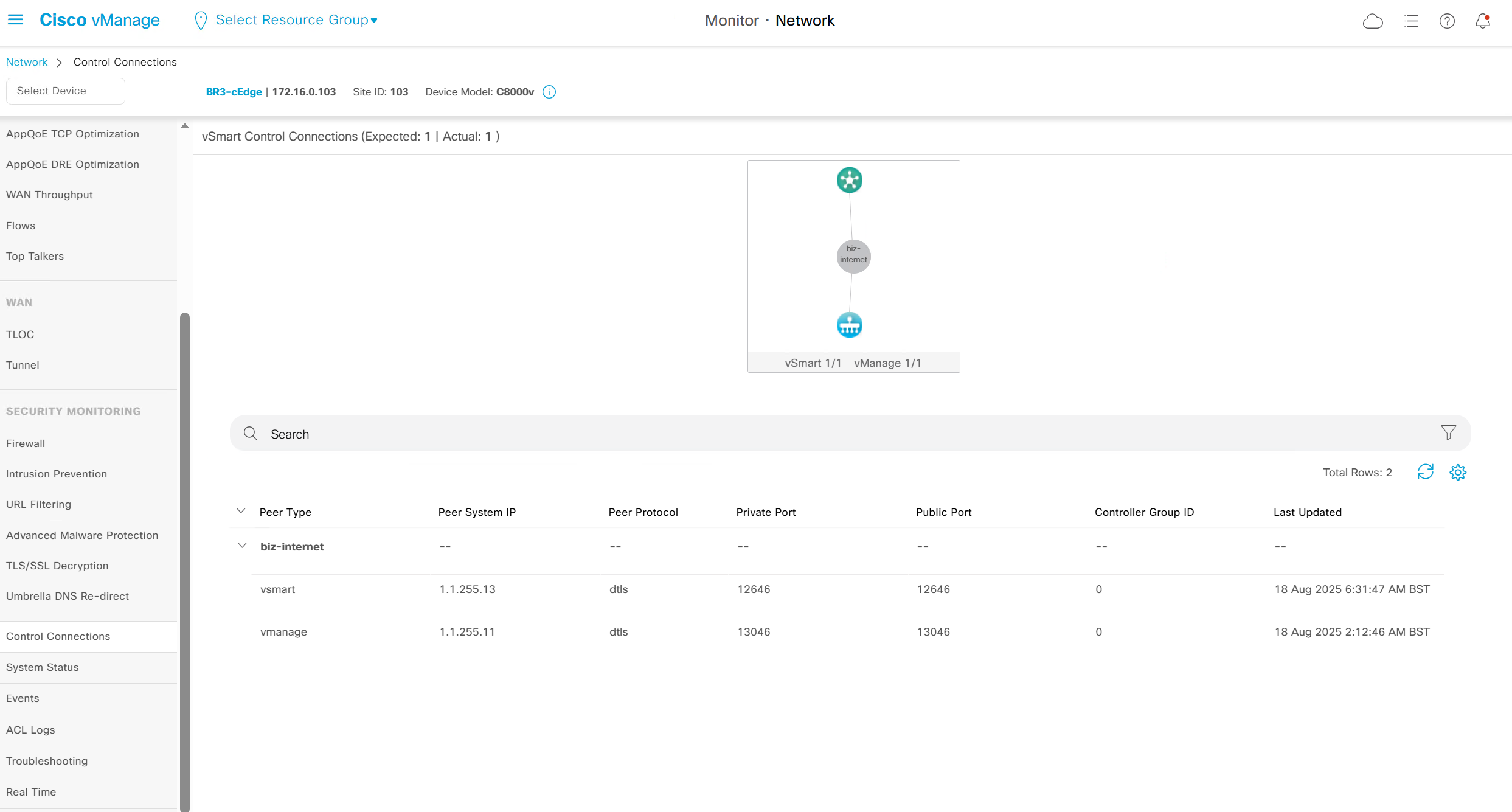
Events
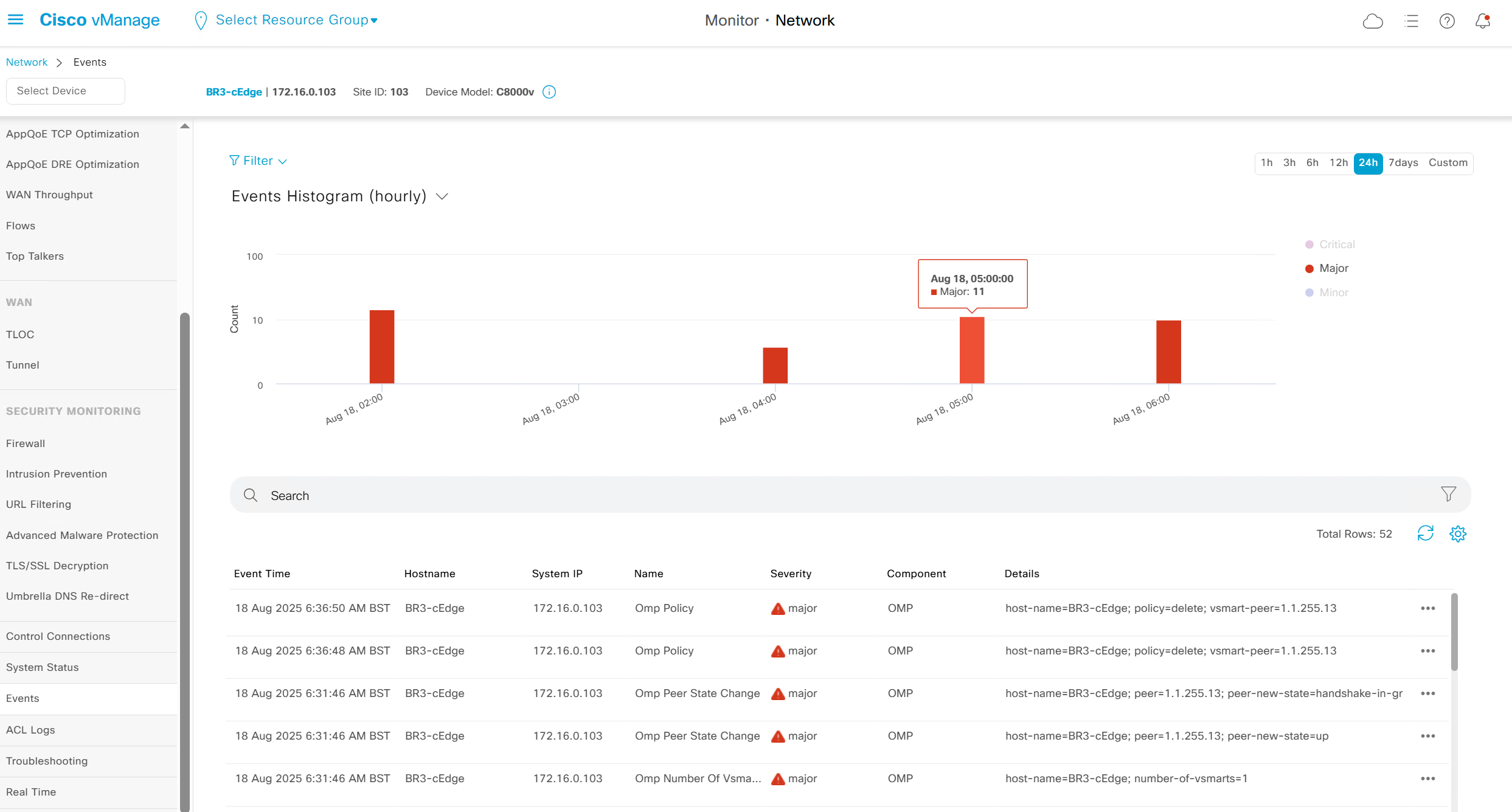
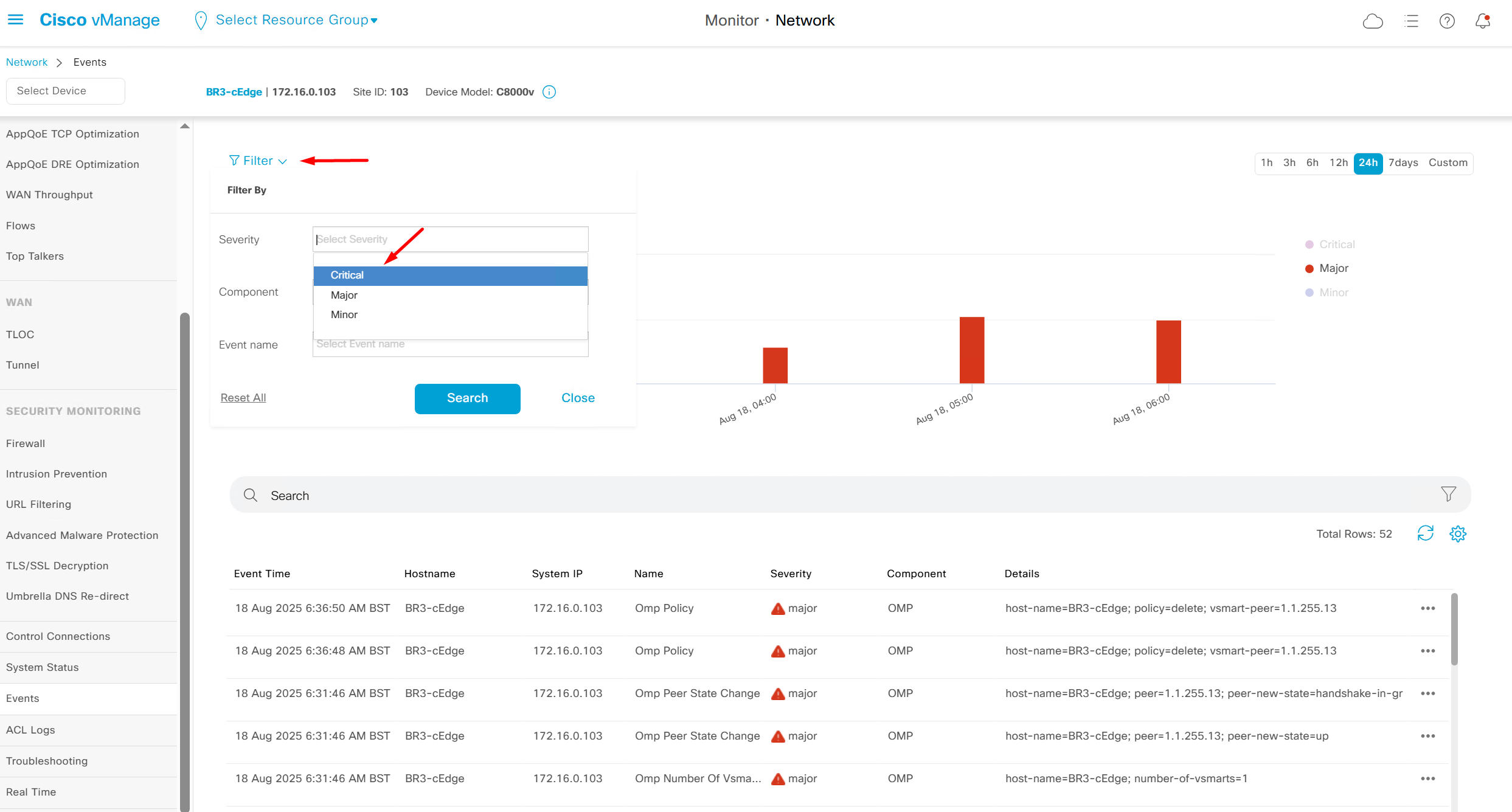
Troubleshooting
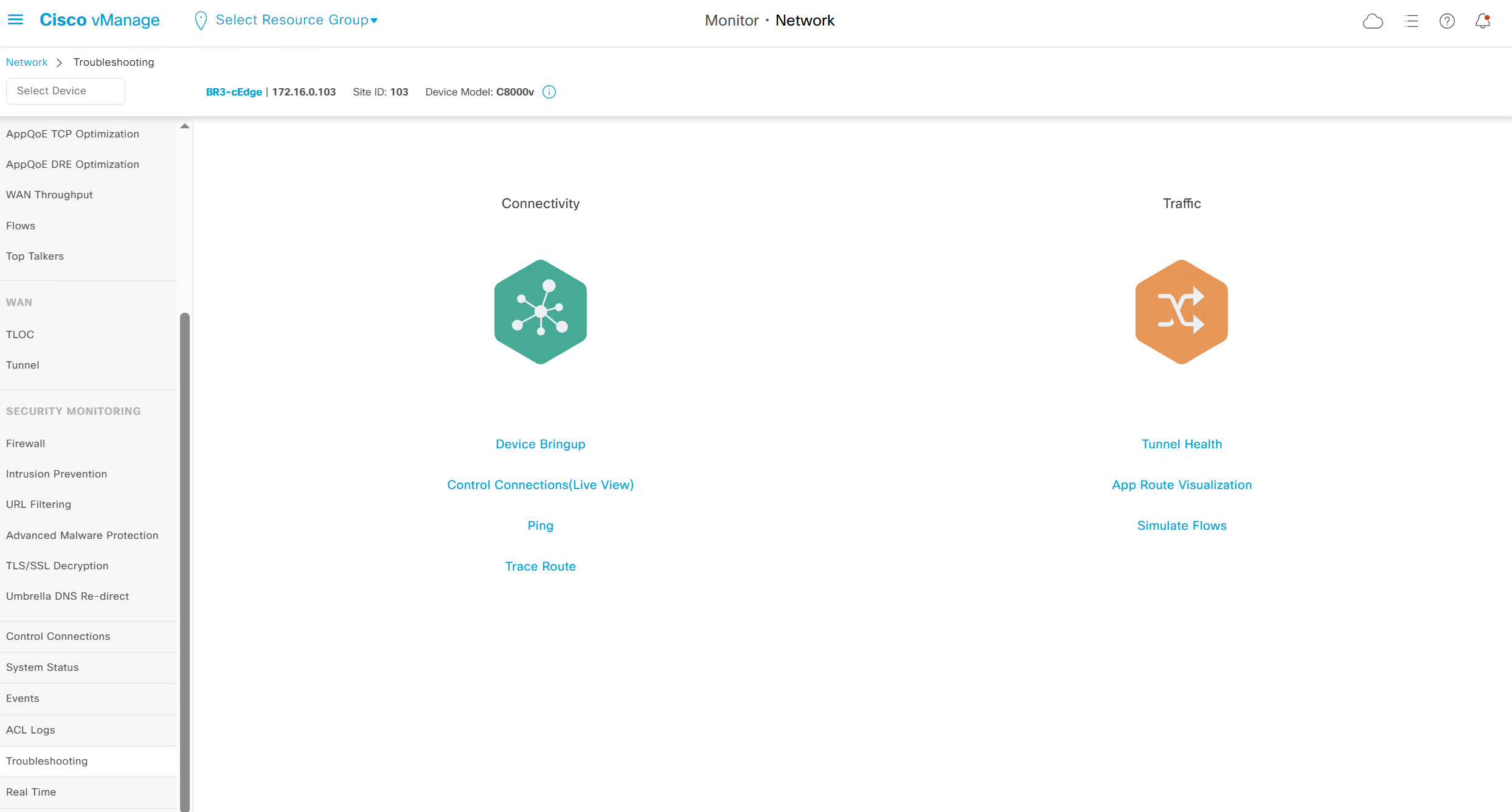
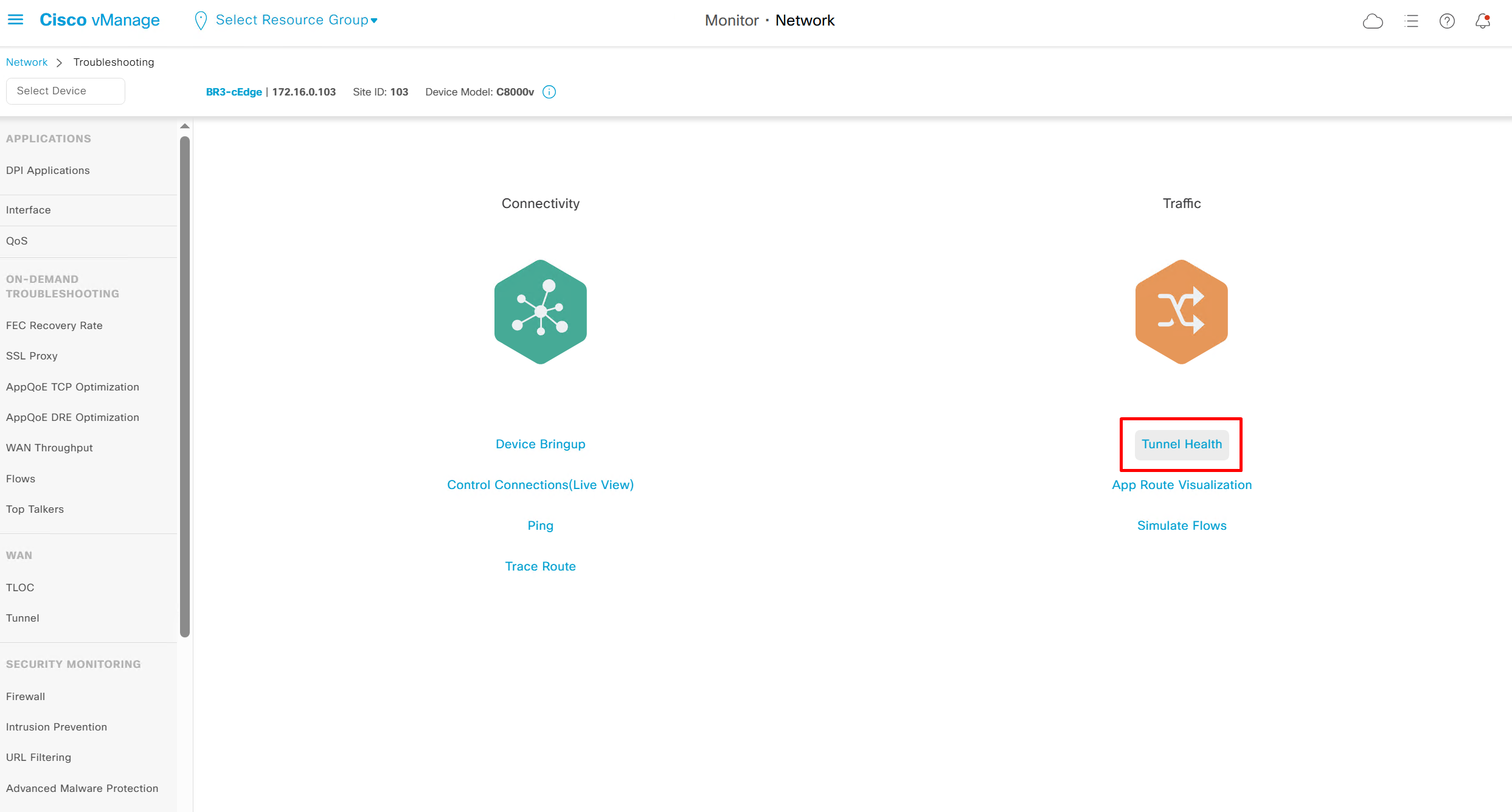
Tunnel Health
Good for troubleshooting per tunnel health
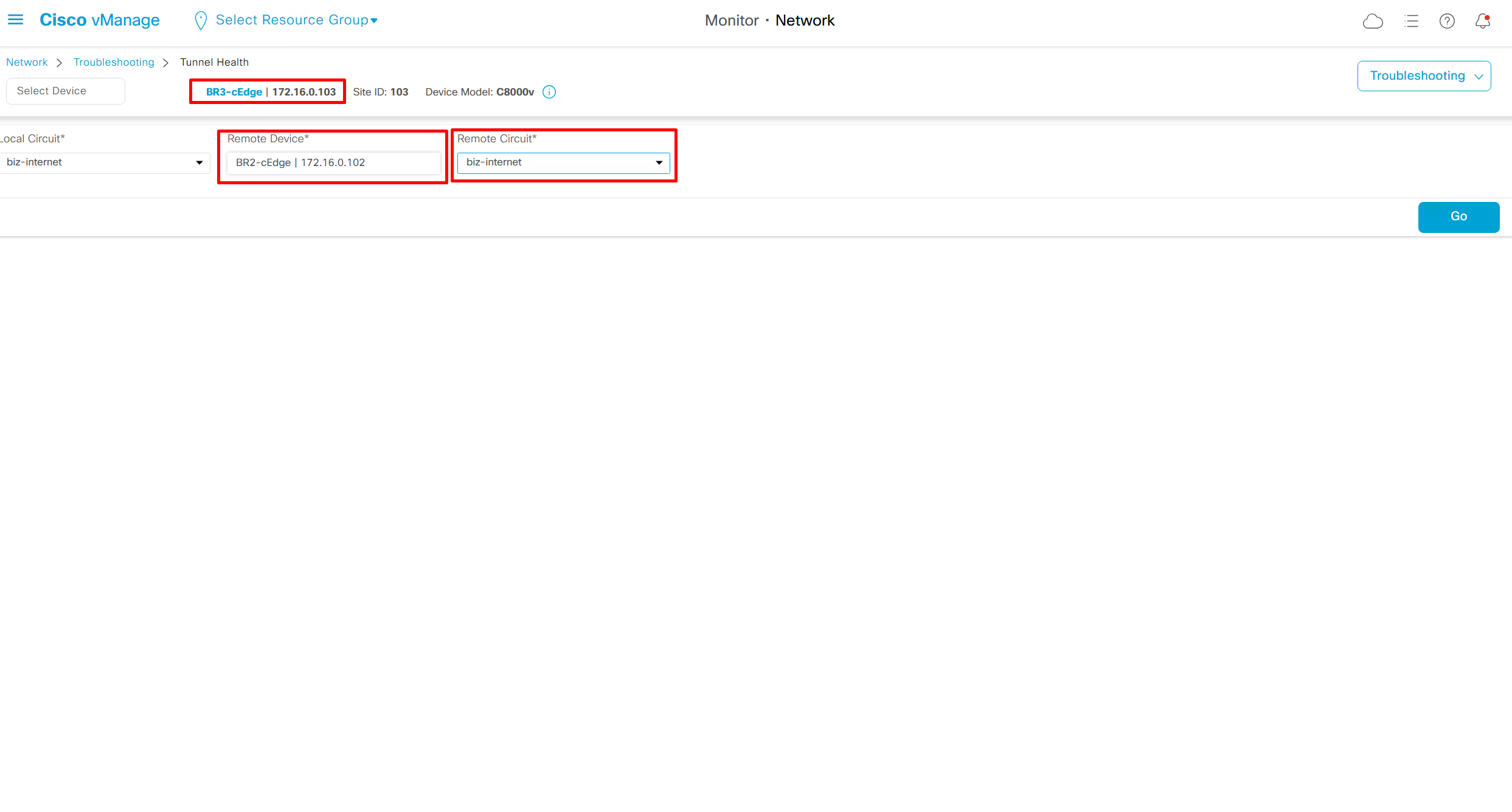
Per tunnel health check for loss, latency and octets or bytes

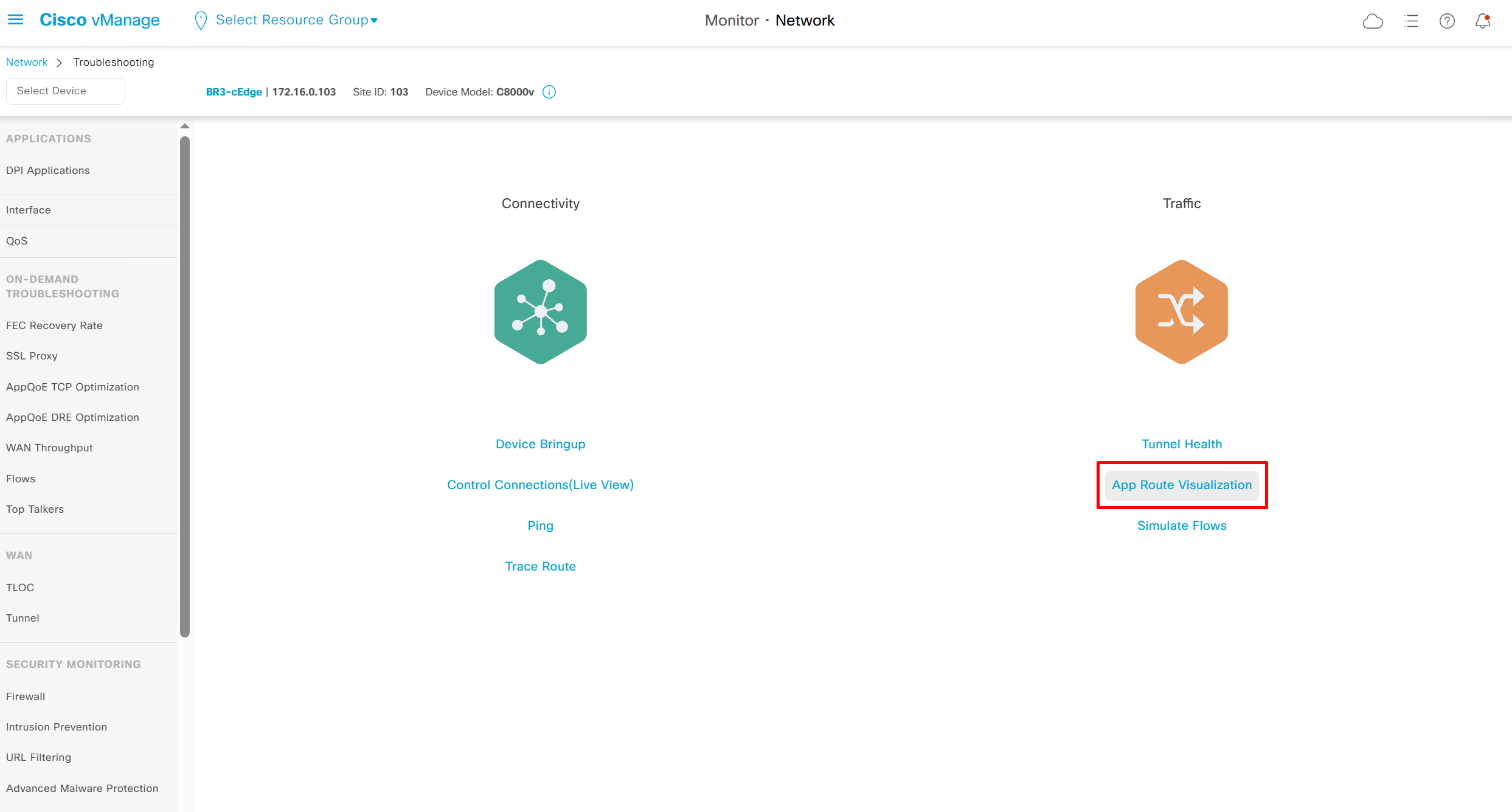
App route visualisation
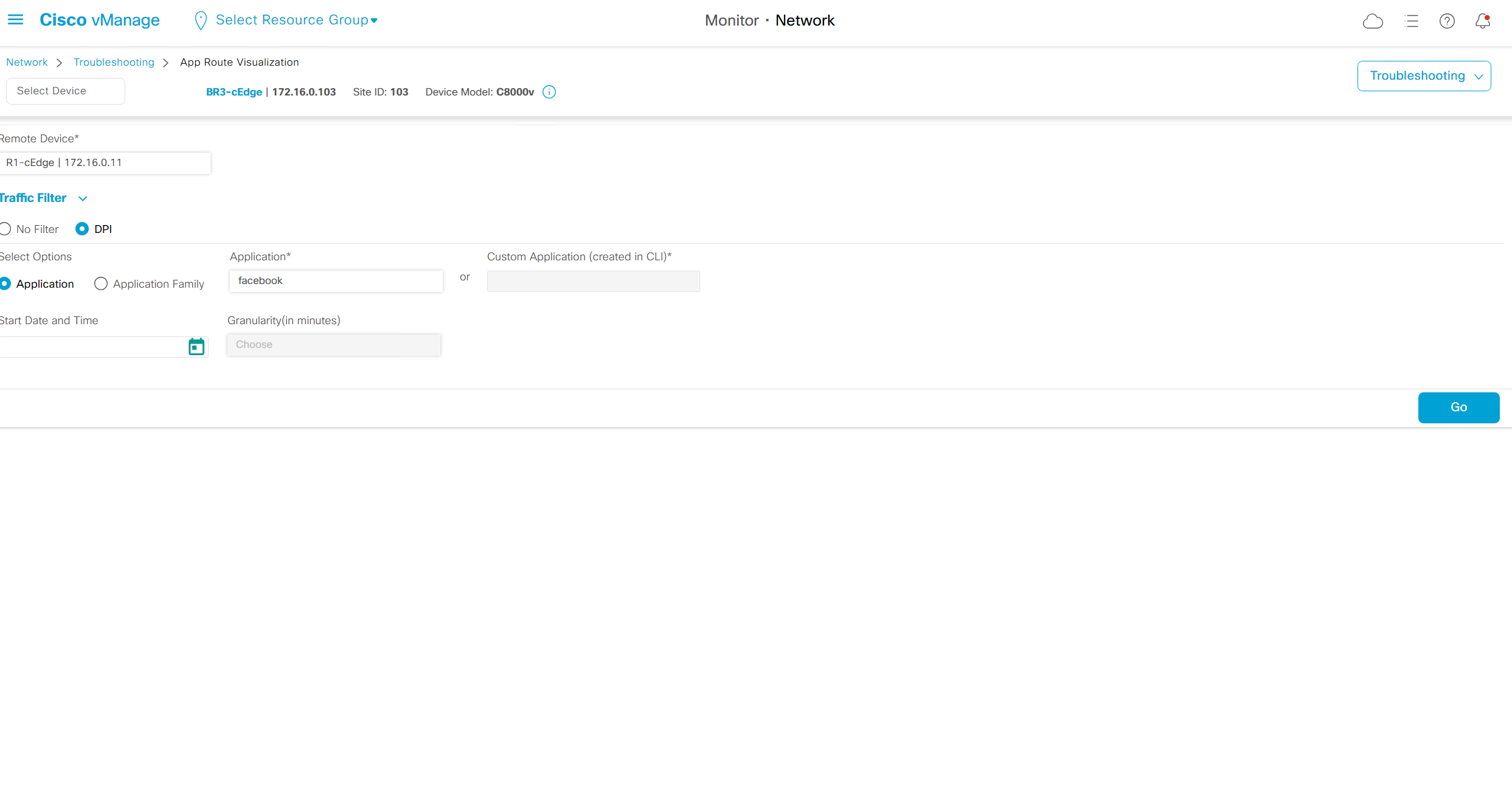
DPI is Deep Packet Inspection
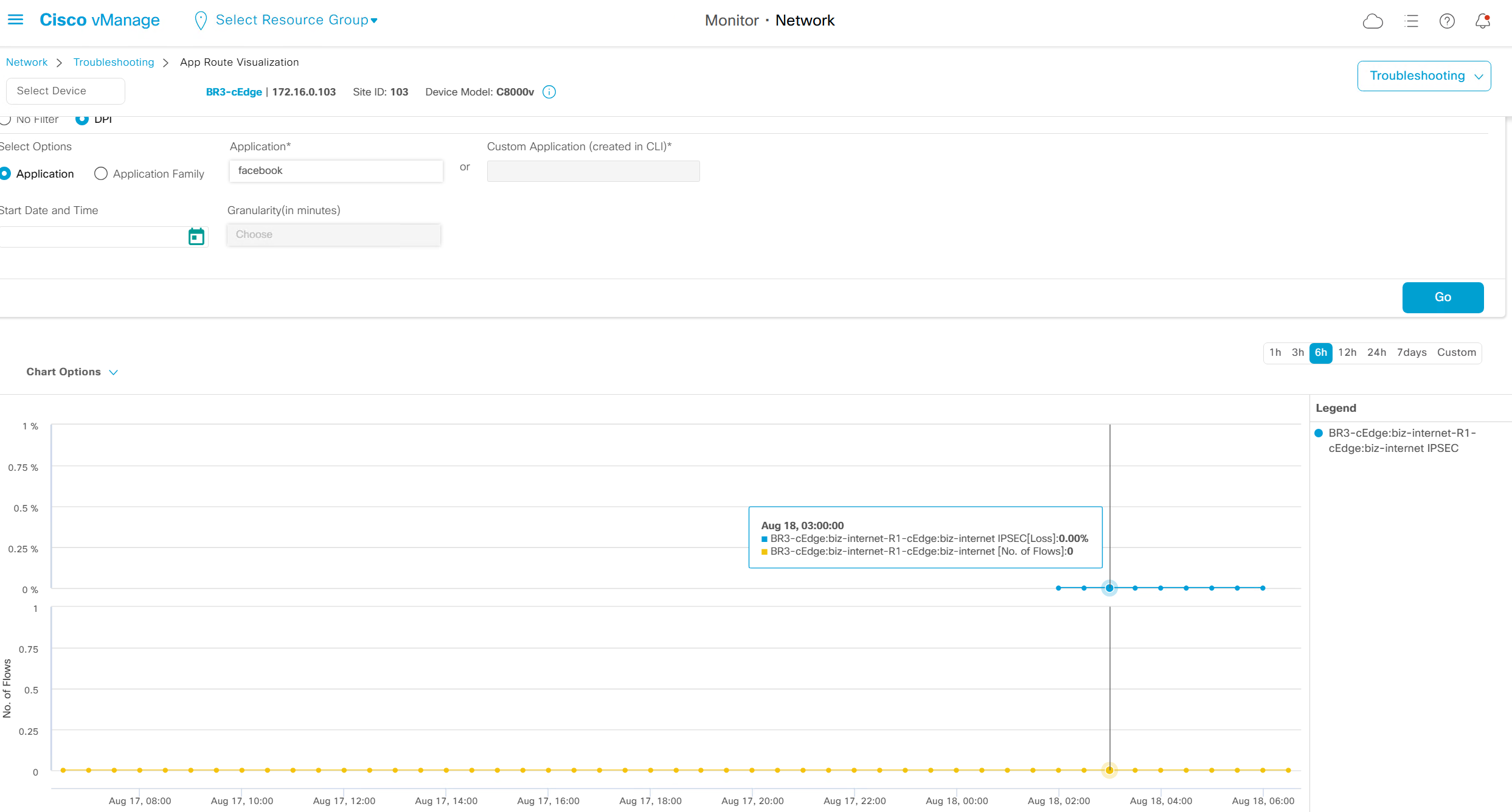
This shows applications stats from site to site as previously we say per tunnel health, this options allows us to check beyond tunnels and applications stats after the tunnel
No filter option will show us stats for all traffic
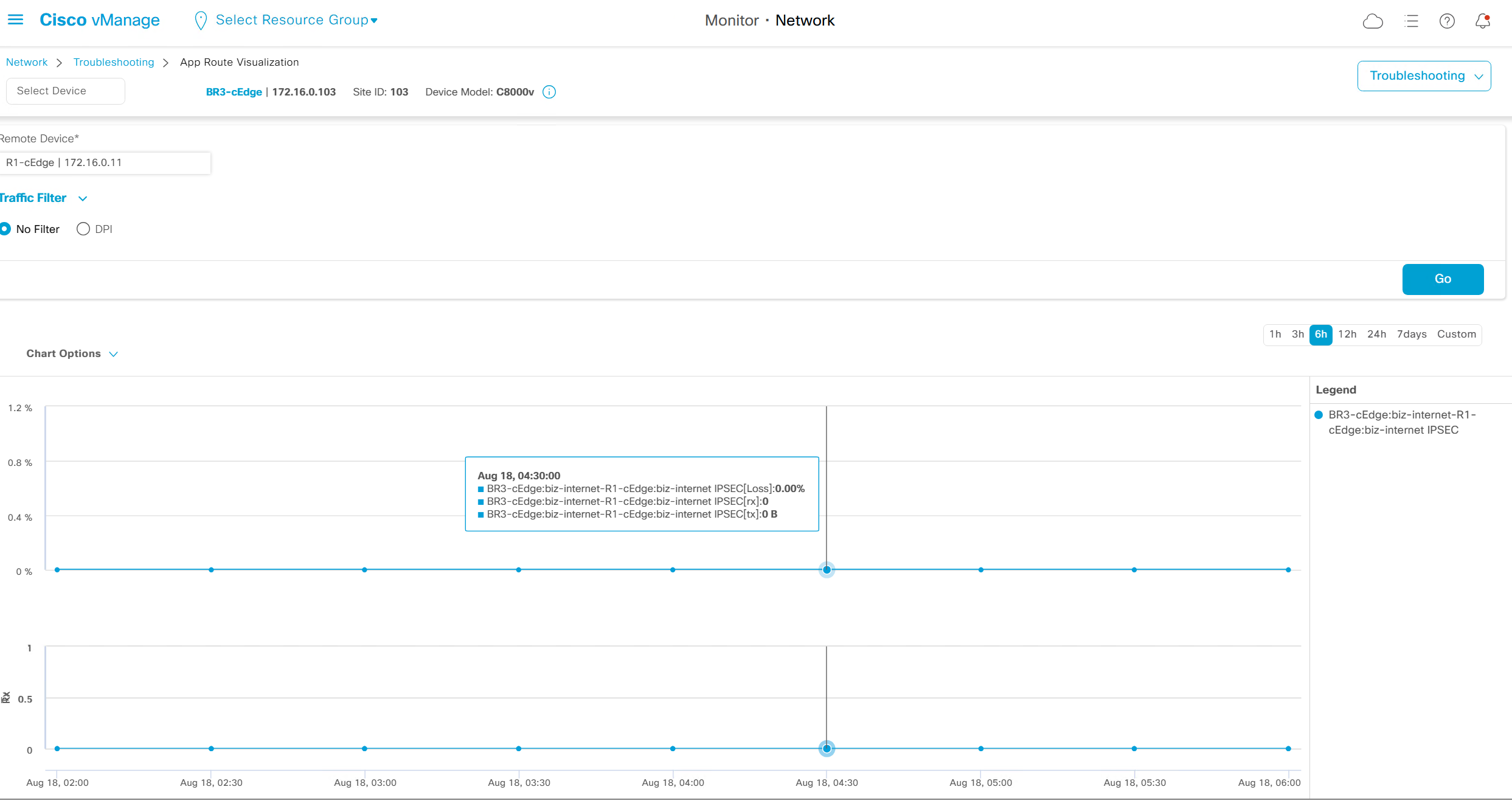
Troubleshooting

It shows us that
1. edge was authorized by vbond
2. Software image update
3. Router configuration
4. Control plane connectivity established
5. Data plane connectivity established
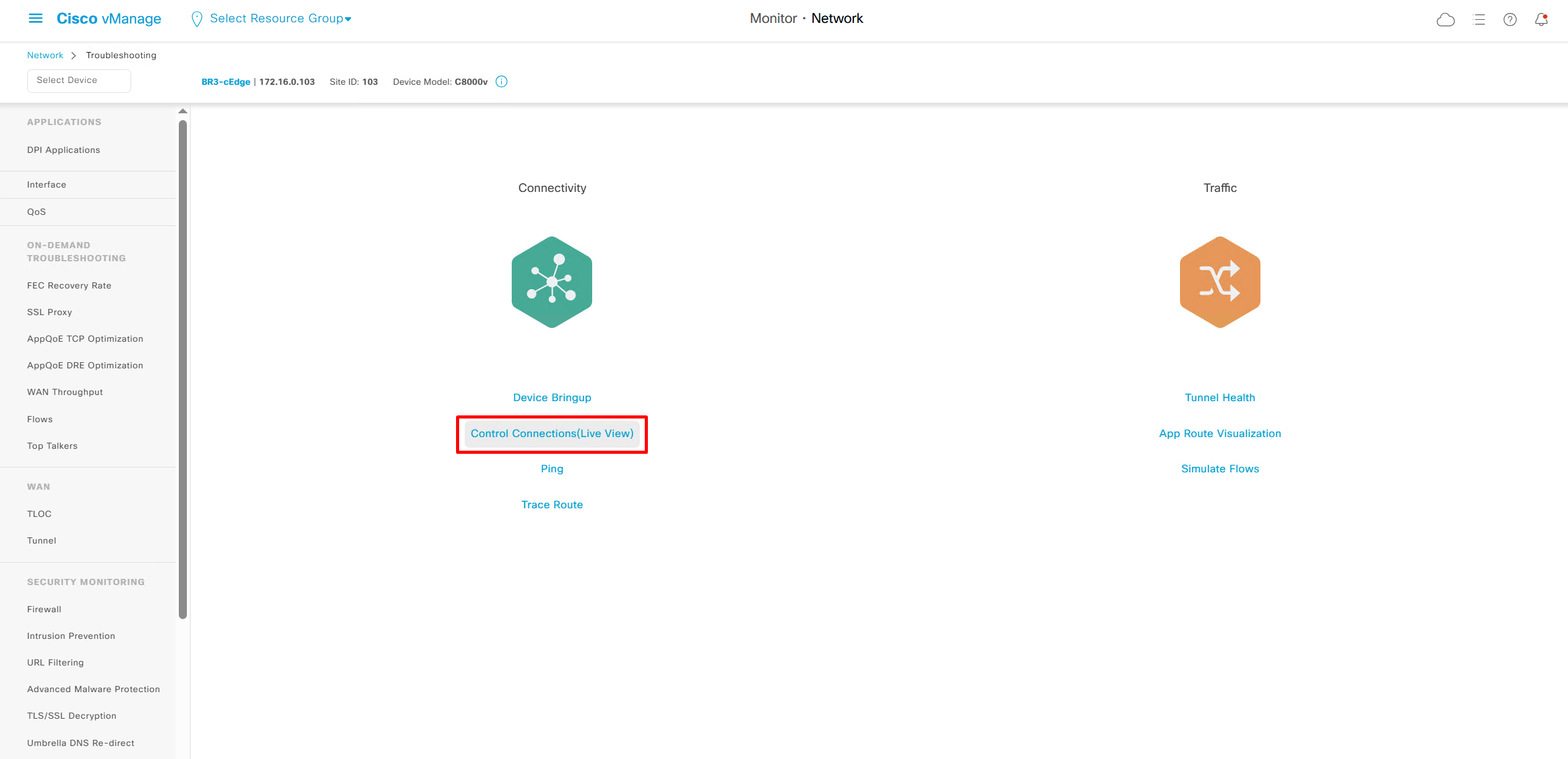
in case edge is behind the firewall and firewall is blocking control place connectivity

We also have option for ping and traceroute
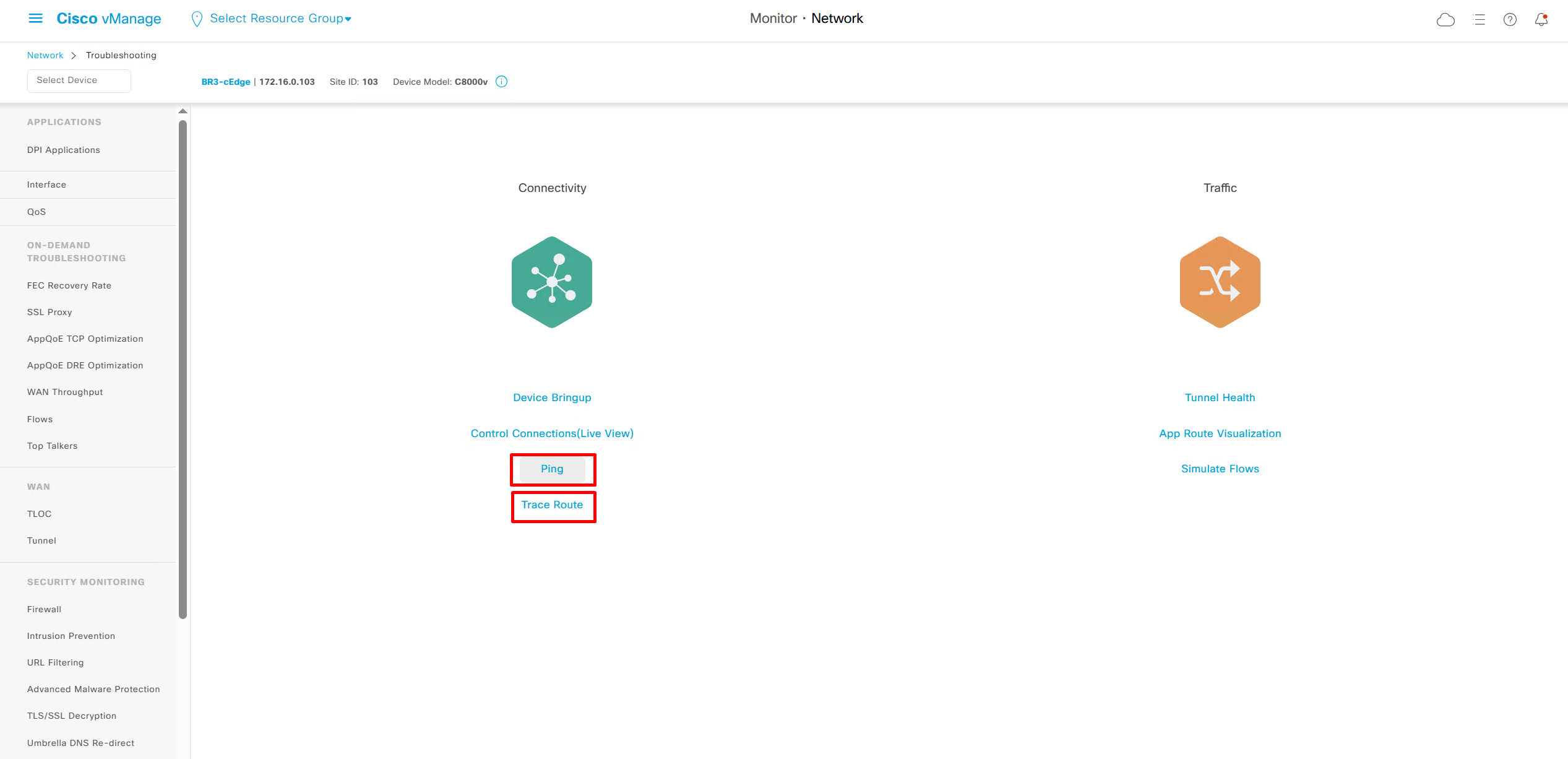
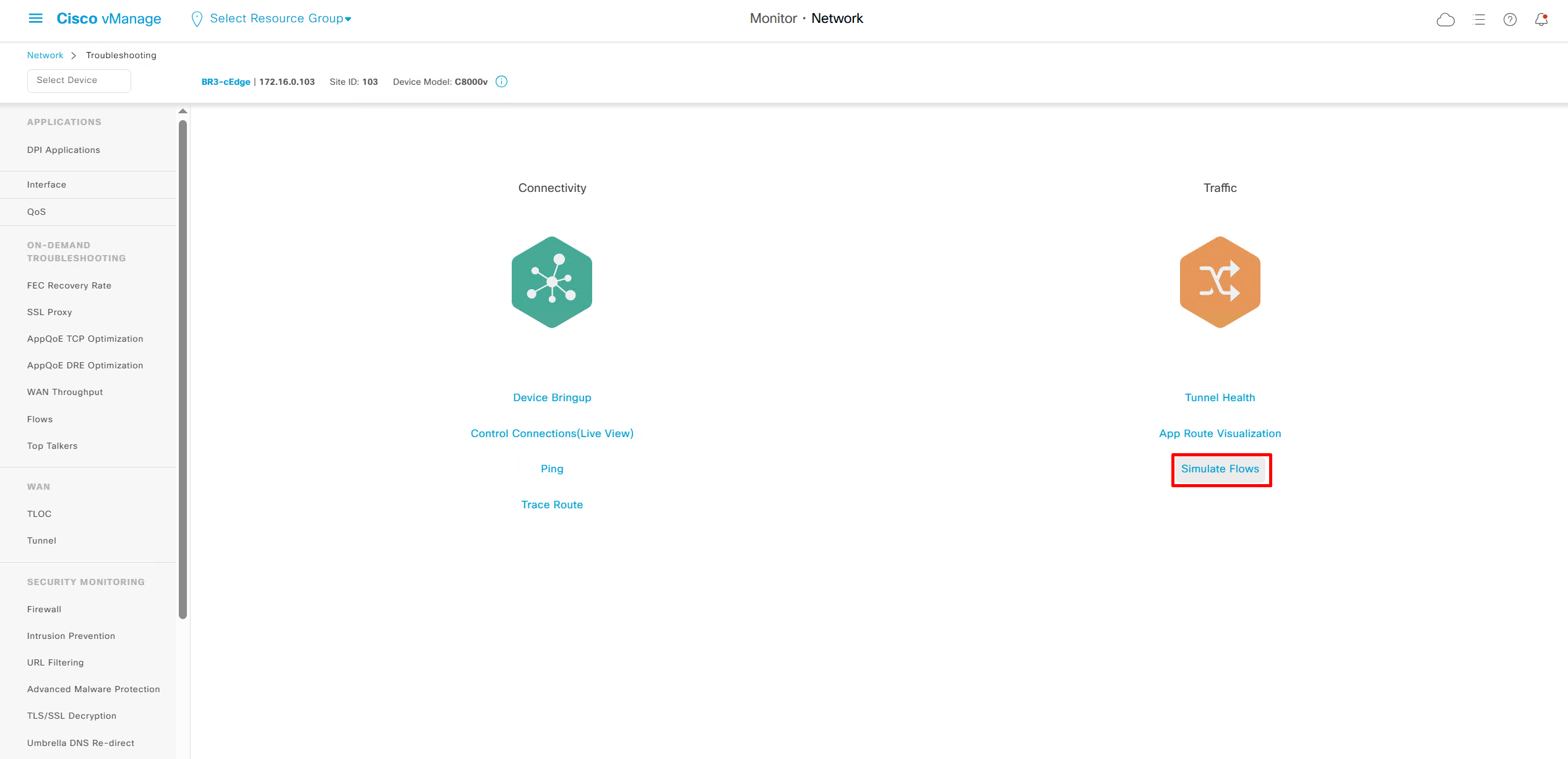
Simulate flow allows us to see how our applications will route and which TLOCs it will pass through
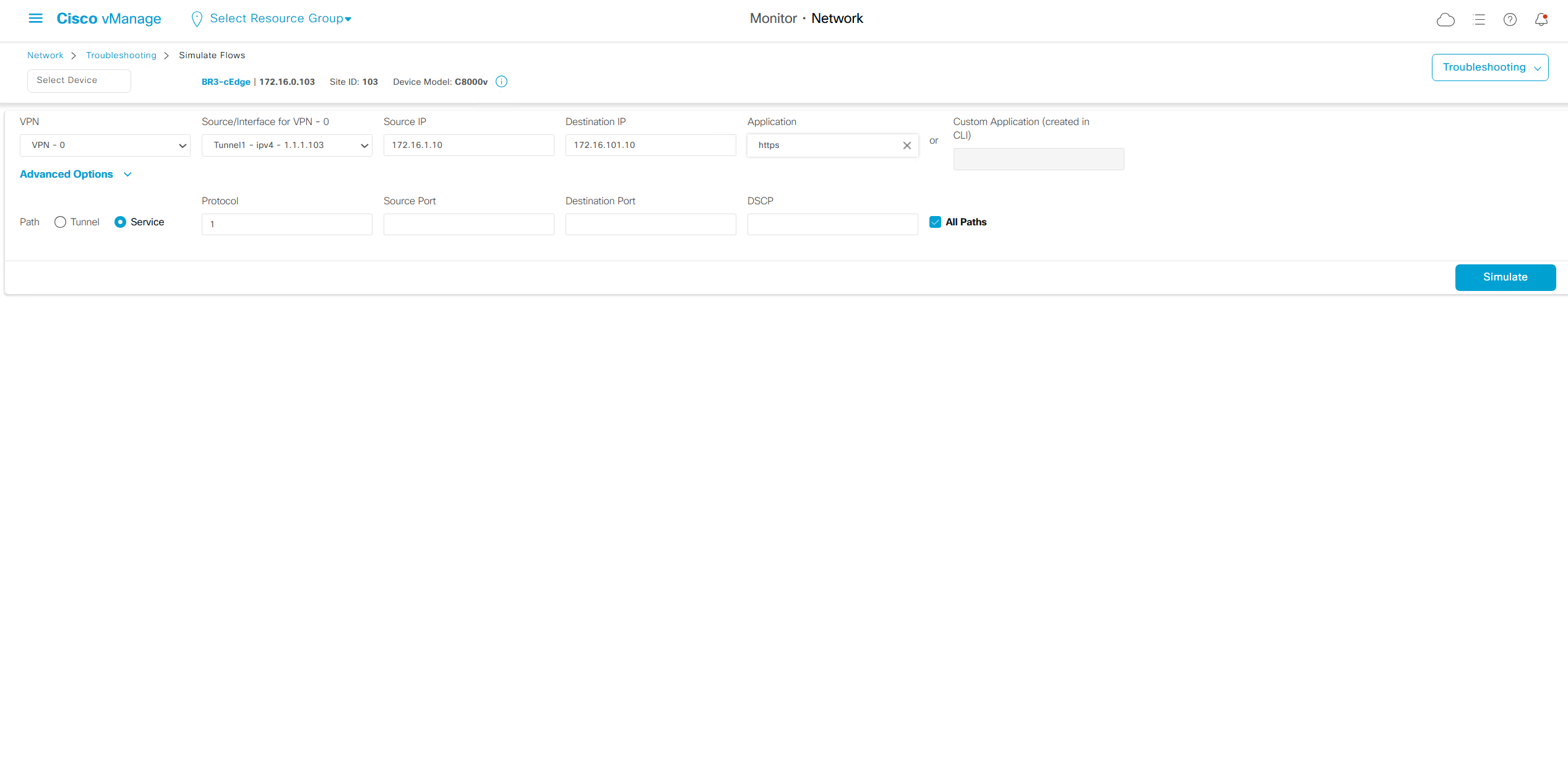
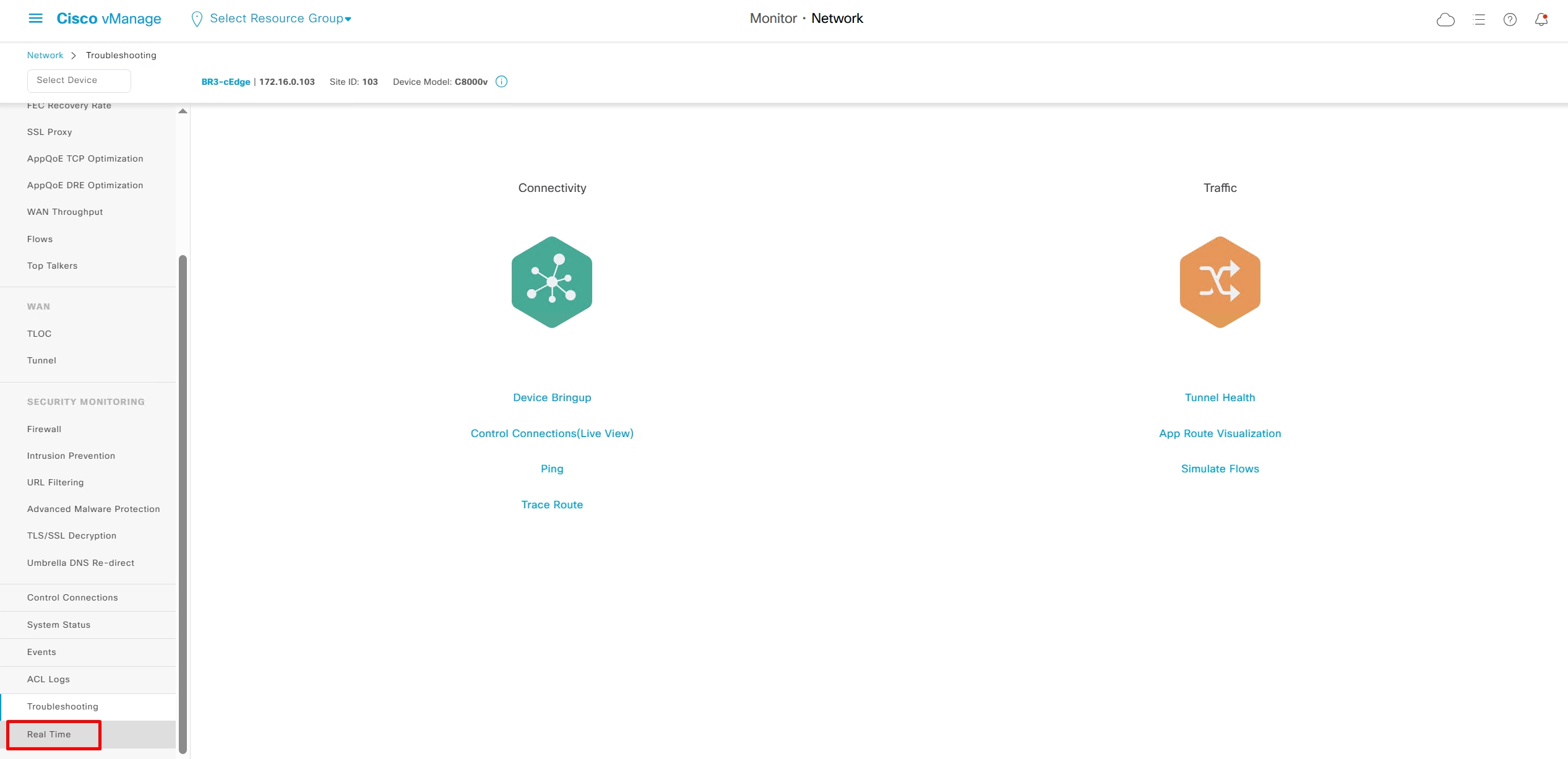
Real time shows us any information that we can see on command line also
Some troubleshooting options are not available as we dont have Data stream enabled such as Packet Capture, Speed Test, and Debug Logs
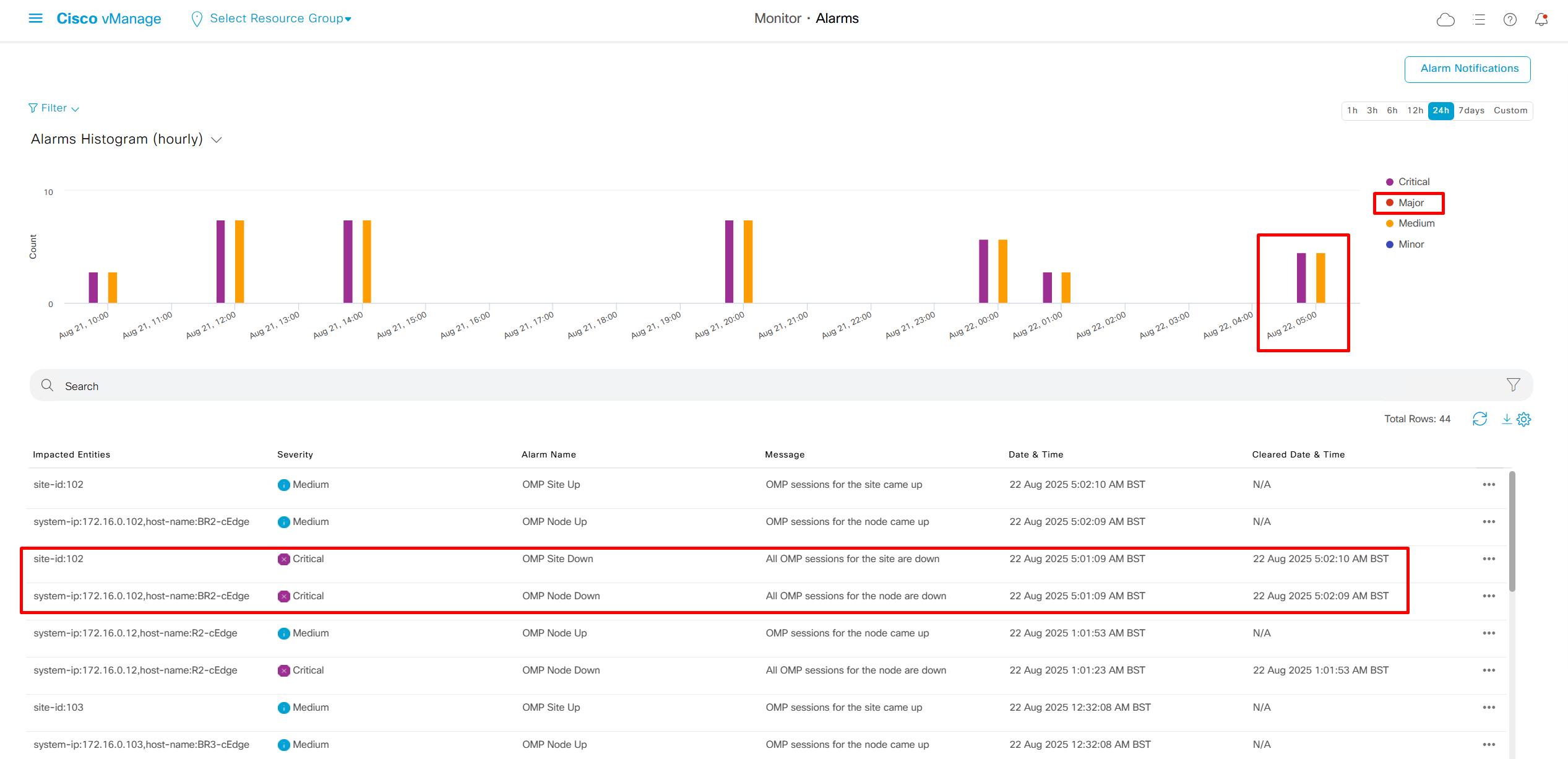
We can add Alarm notification email as well
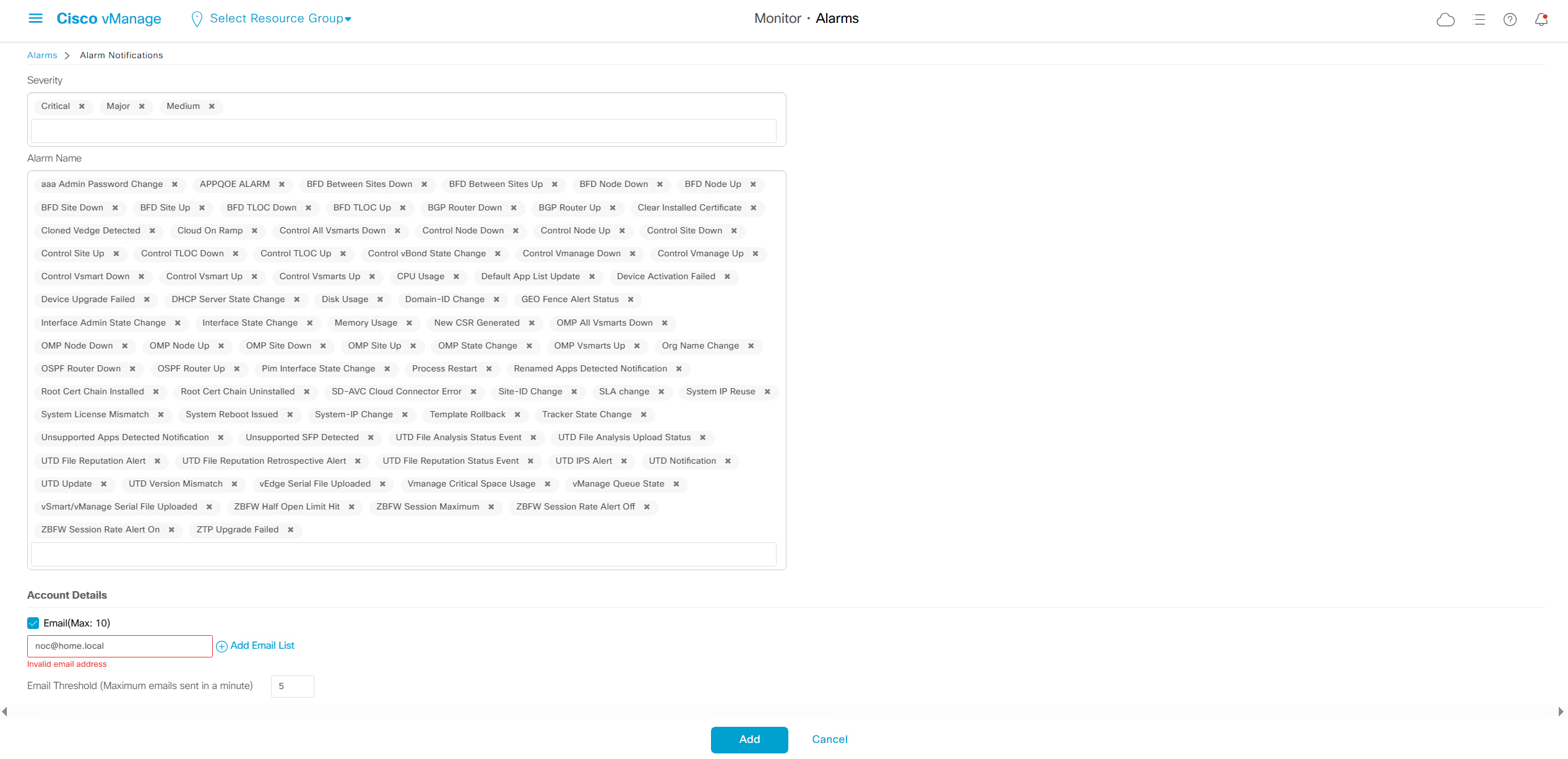
Now we move to events, Alarms are like syslogs generated and events are more detailed events
Audit log
We can see all the audit trail for who did what and what was pushed to which device
This comes in very handy as we can see ACL logs not just for one device but for the whole system
once a device is managed by vmanage, local CLI changes cannot be made on device
nodes which are PNP or ZTP enrolled are already in vmanage mode as at time of enrolment a template is applied and devices are vmanage managed
device manually enrolled are CLI managed as they are manually enrolled
one reason to convert from vmanage mode to CLI is to quickly test a command and then return device to vmanage mode, you dont even have to revert the changes made in CLI as we change back to vmanage mode, the changes made in CLI will disappear because configuration from template will be applied, if change test was successful then make that change part of the template
Device status must always be “In Sync”
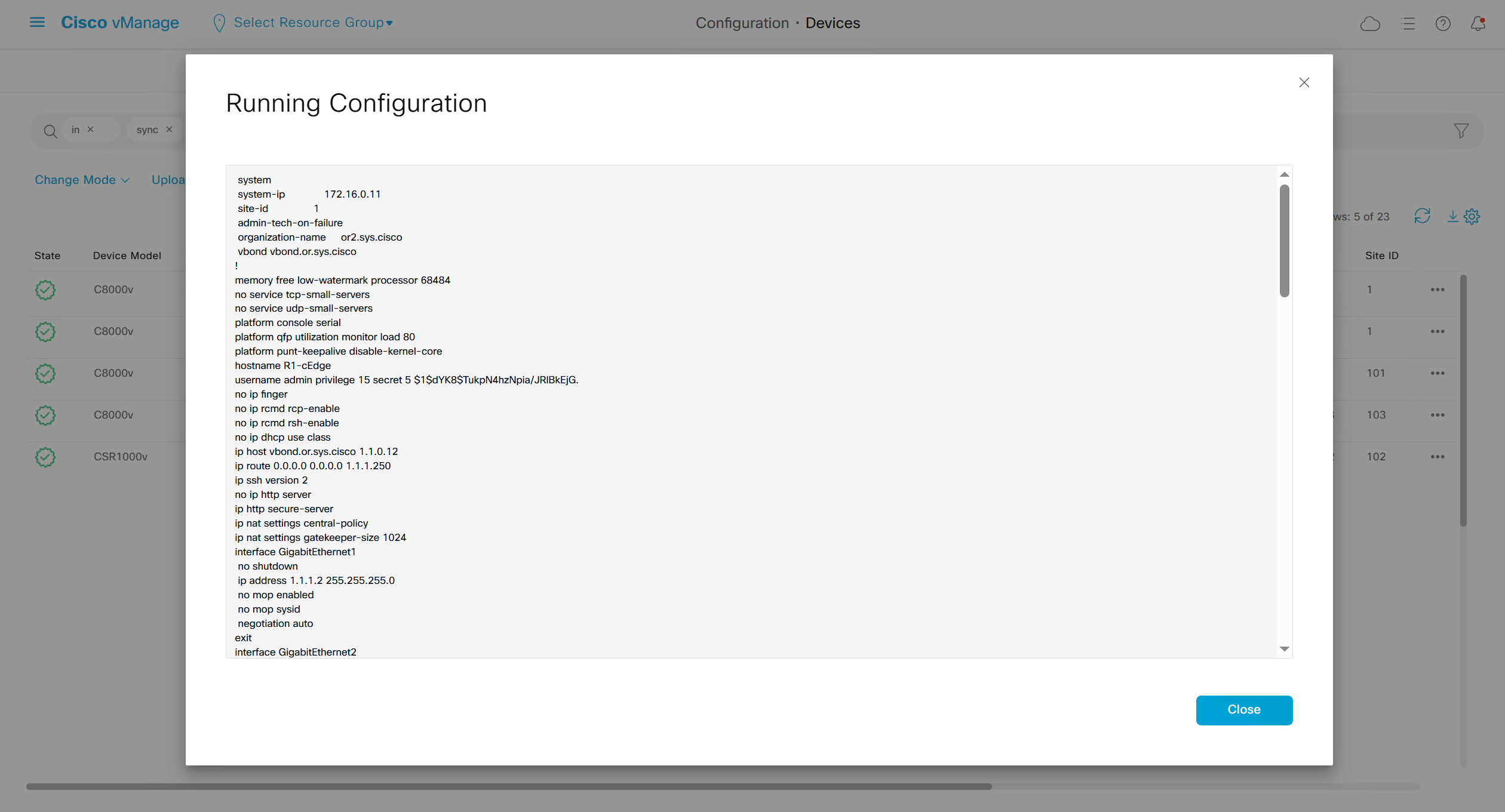
To see if device communication is working with vmanage, pull its running configuration, if it works then we know that netconf over DTLS (control connection) is working between vmanage and edge
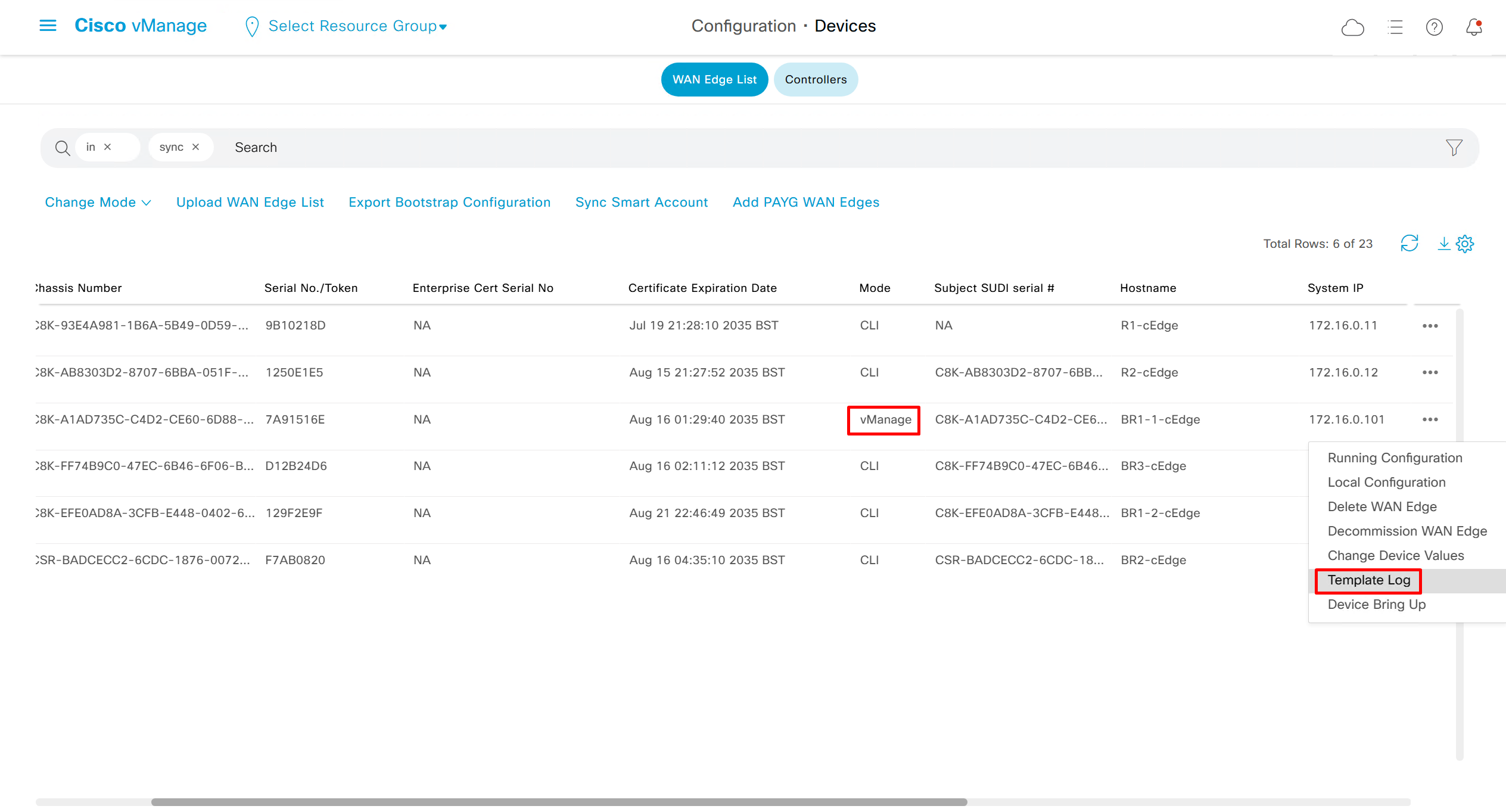
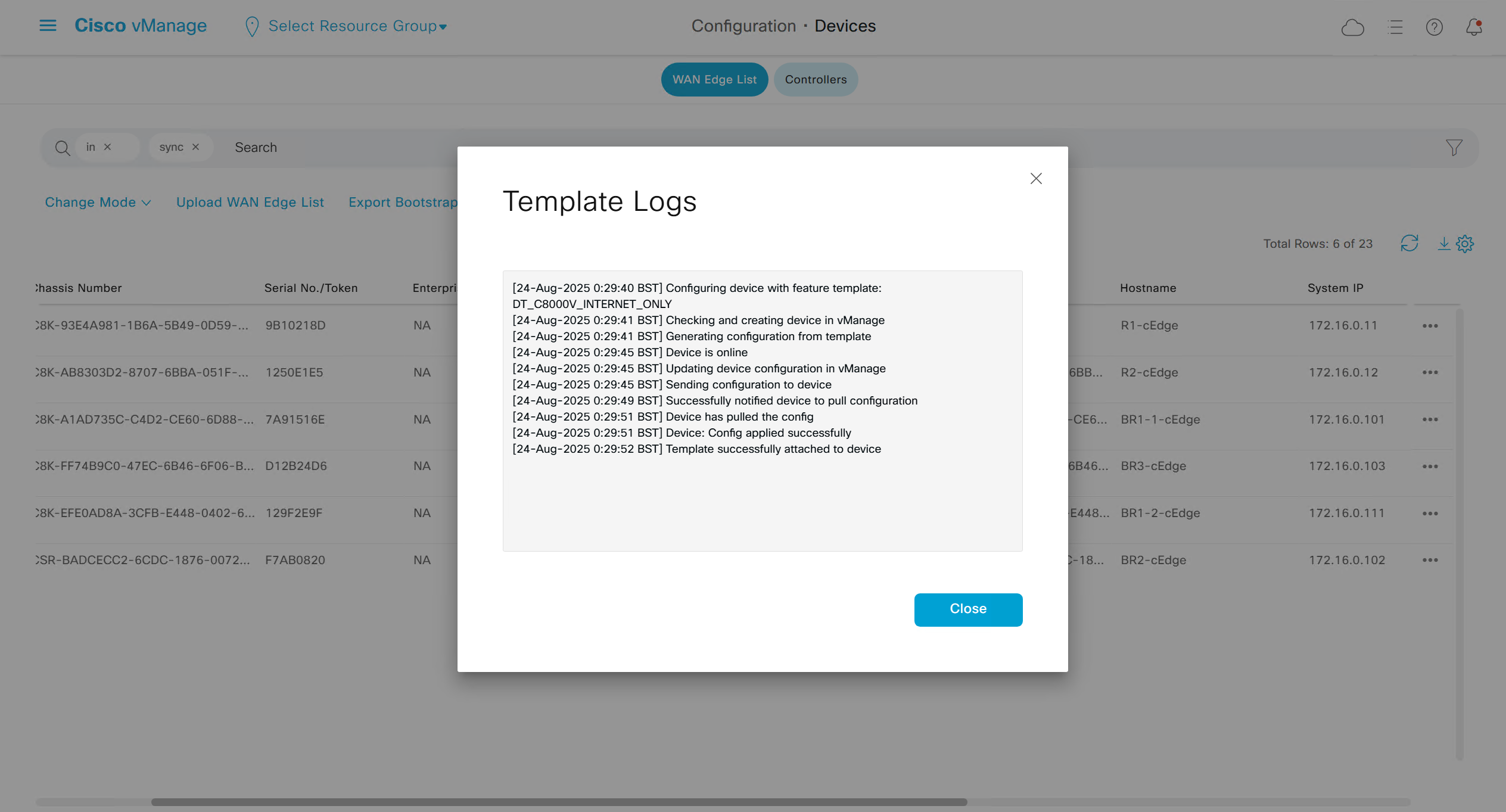
Template log is where we can see the changes
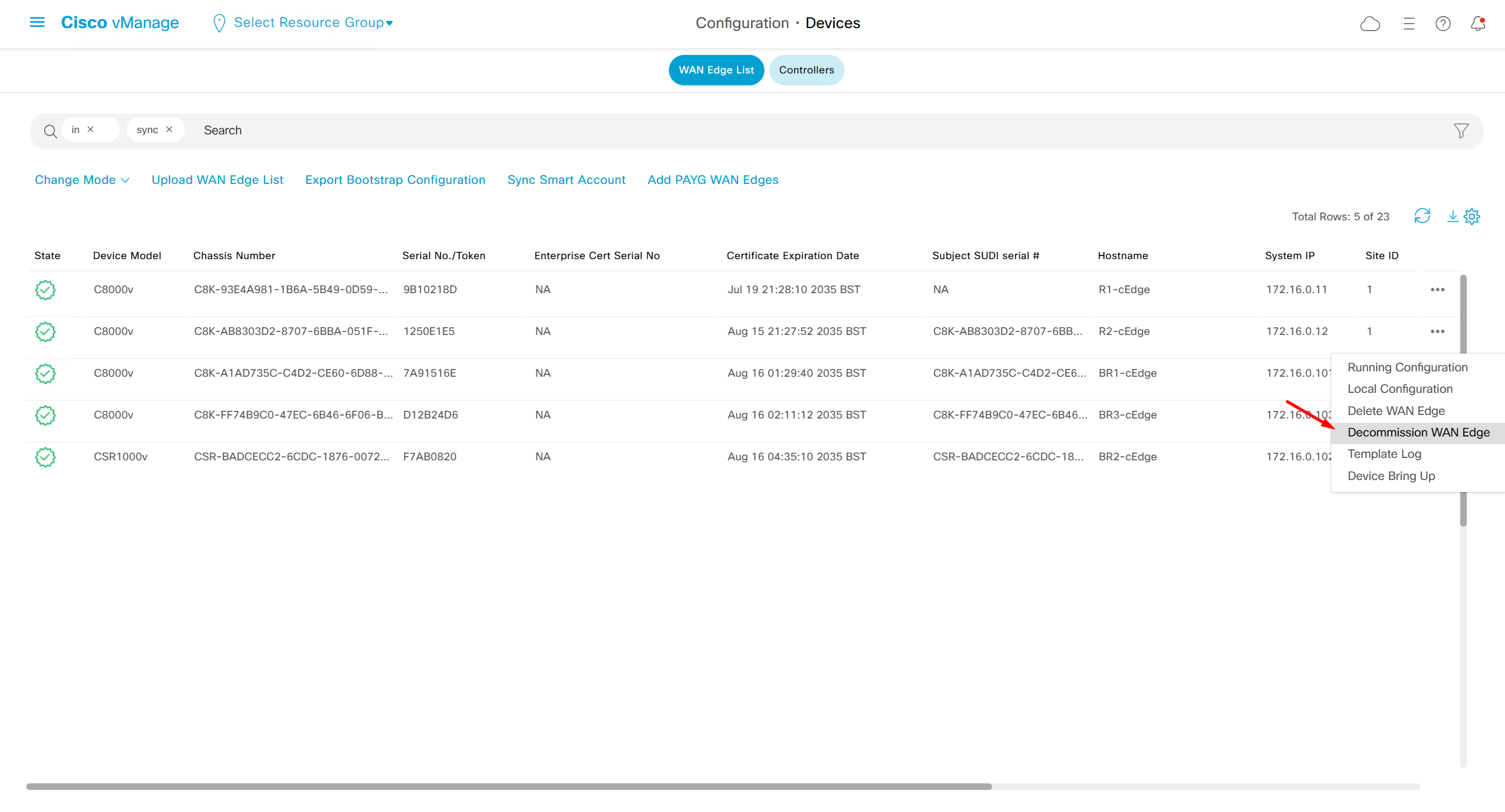
Decommission WAN edge – removes the edge device and puts chassis number back in the controllers so new virtual device can be assigned that chassis / token
Similar options for controllers
Templates
Device Templates
Feature Templates
Centralized Policy

Localized Policy
Security section where we can configure Zone Based Firewall etc


This is great when you want to quickly check something in SSH
Rediscover network if there is a difference in configuration between vmanage and edge device
Rediscover edge device to sync all those changes
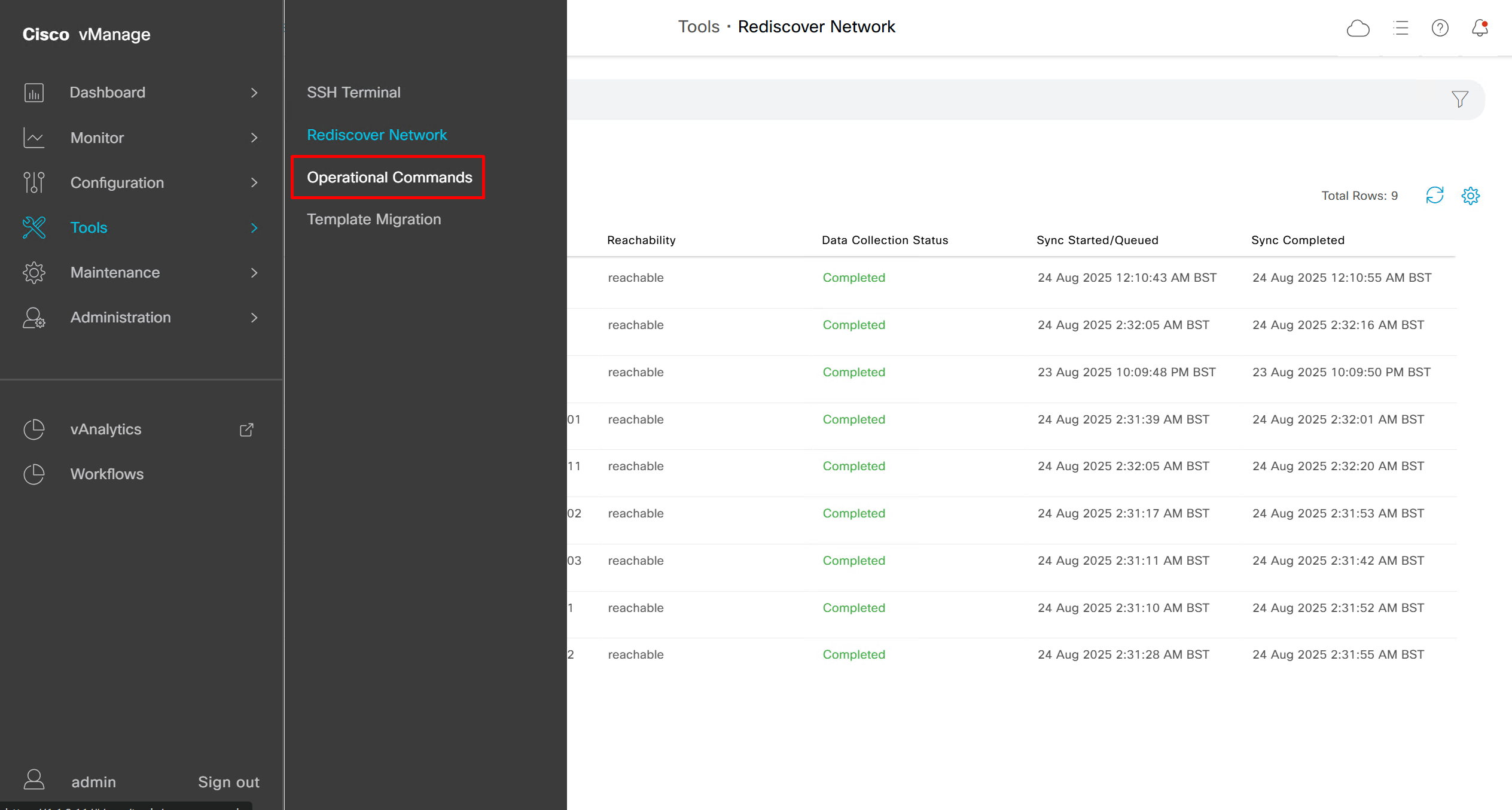
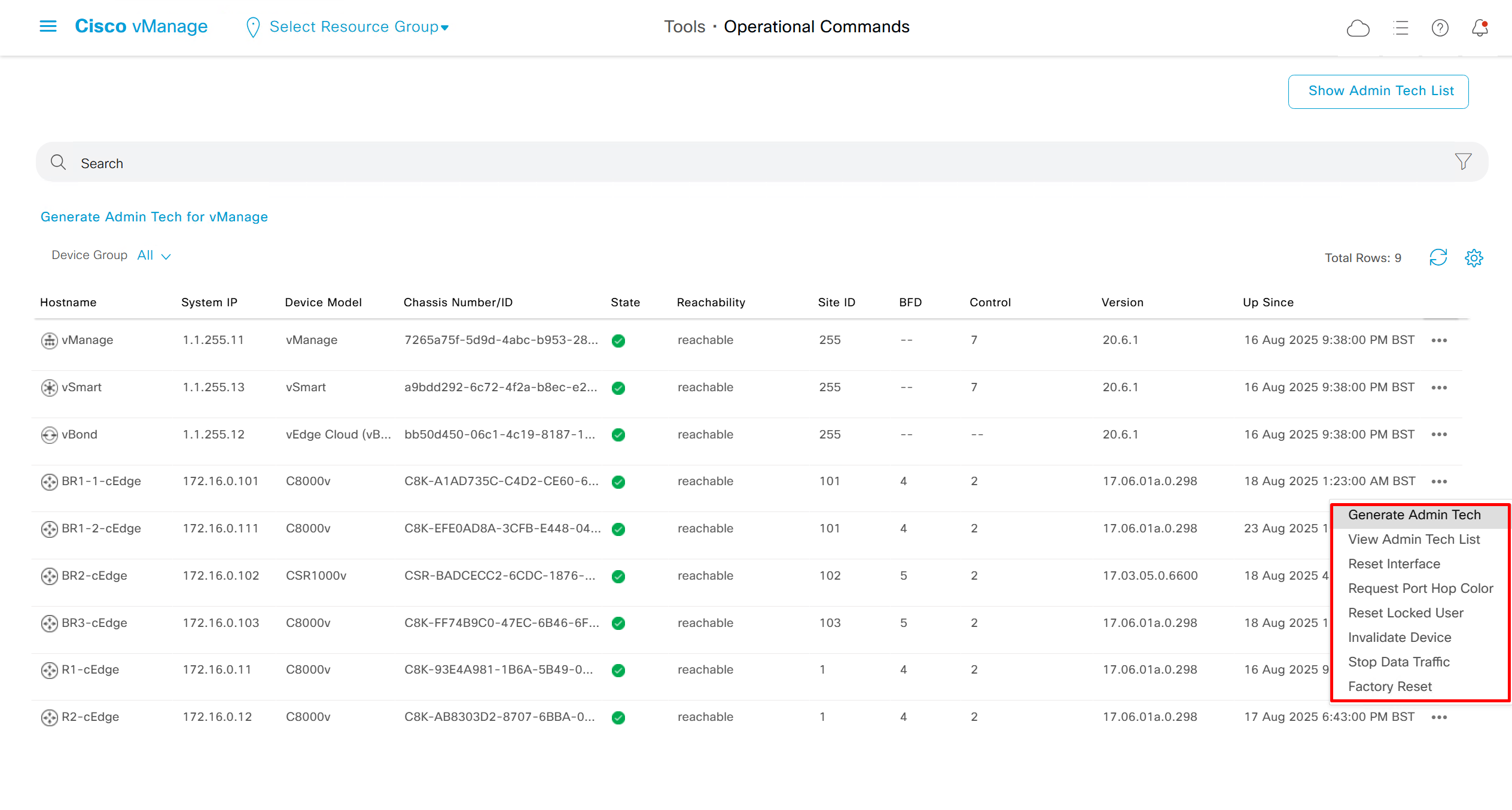
Generate Admin Tech for support
Reset interface is to bounce the port
BR1-1-cEdge#
*Aug 24 02:18:57.042: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:47394 for netconf over ssh. External groups:
BR1-1-cEdge#
*Aug 24 02:19:00.560: %Cisco-SDWAN-RP_0-VDAEMON-3-ERRO-500012: Device does not have an active connection to a vSmart controller
*Aug 24 02:19:04.058: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:47412 for netconf over ssh. External groups:
BR1-1-cEdge#
*Aug 24 02:19:13.388: %DMI-5-AUTH_PASSED: R0/0: dmiauthd: User 'vmanage-admin' authenticated successfully from 1.1.255.11:47468 for netconf over ssh. External groups:
BR1-1-cEdge#Request port hop color – Essentially, it forces a TLOC (Transport Locator) color hop so the device re-initiates connections using another WAN interface/color (for example: from biz-internet → public-internet, or mpls → lte).
This is mostly used for troubleshooting and validating policies (e.g., checking failover between MPLS and Internet links).
Reset locked user is used to unlock admin
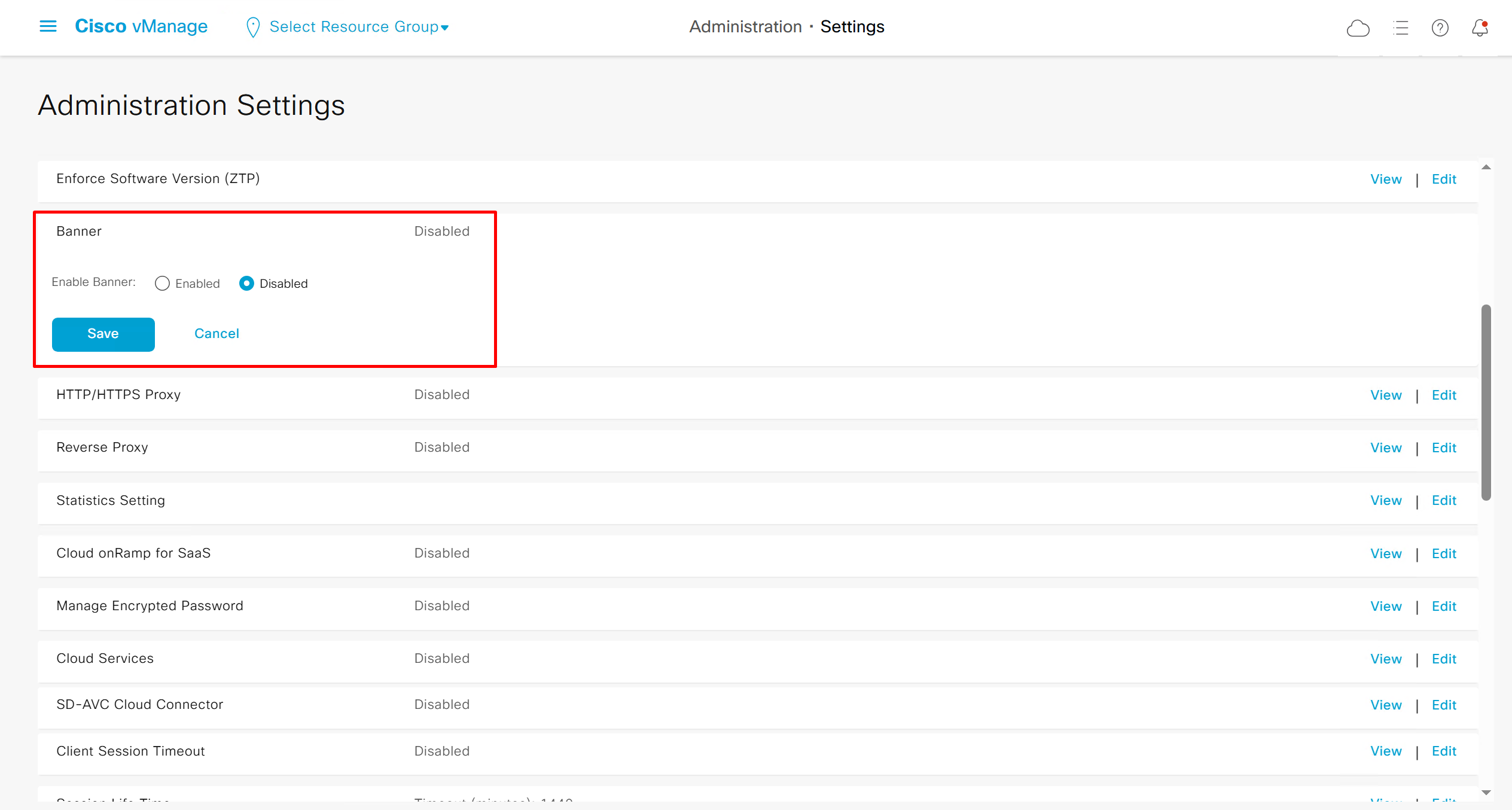


once a vmanage is switched from single tenant to multitenant then it cannot go back to single tenant
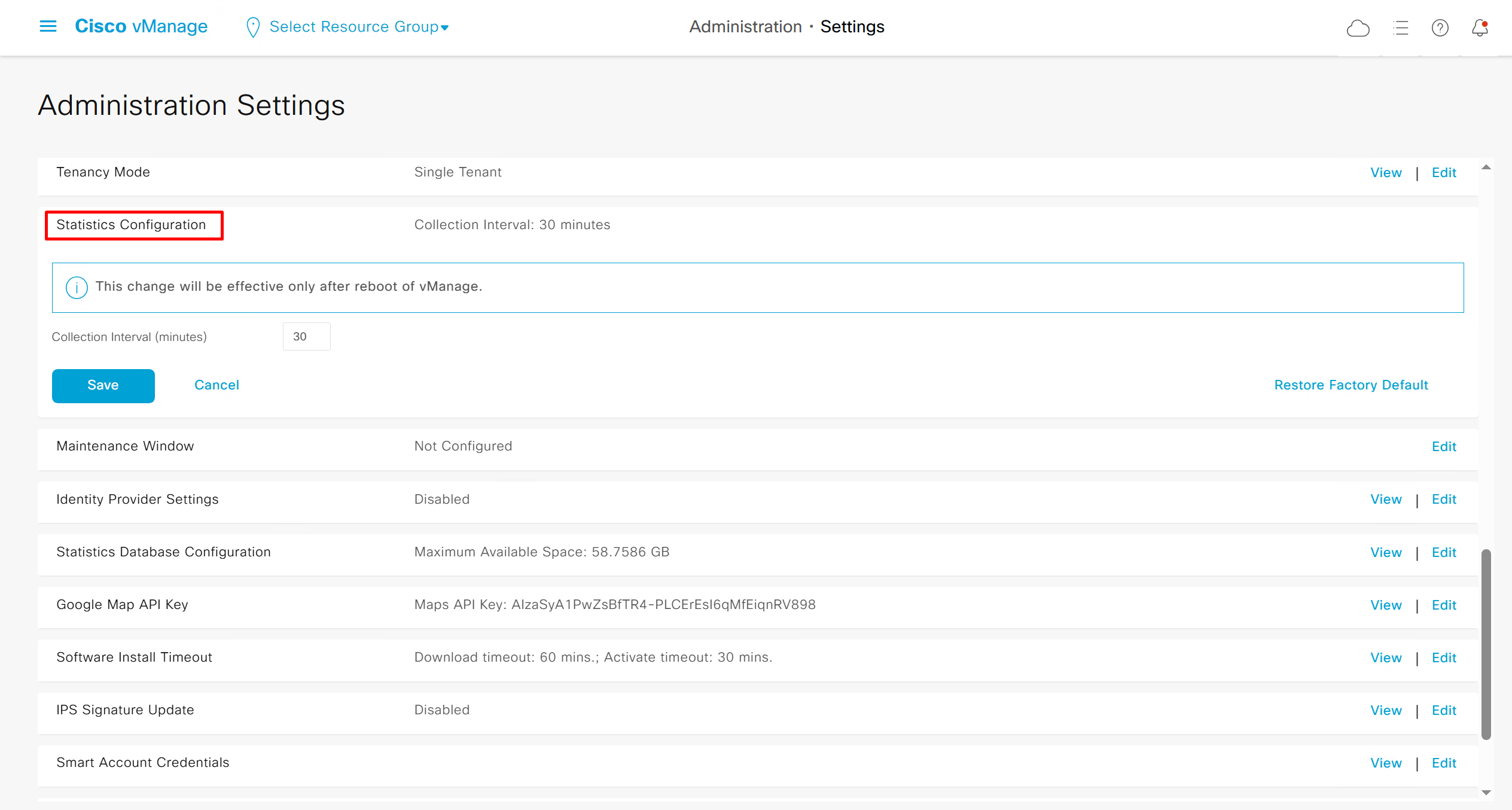


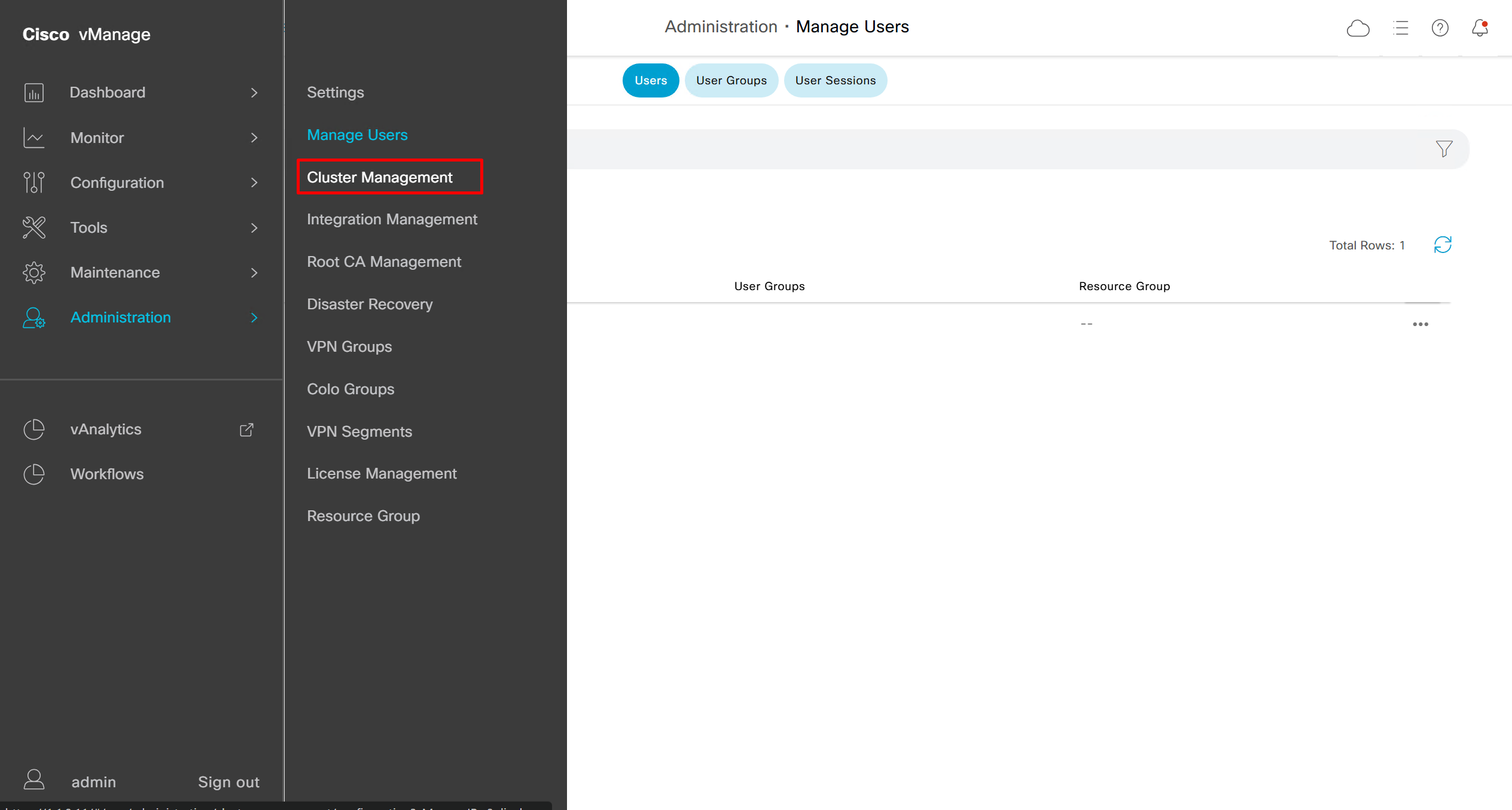
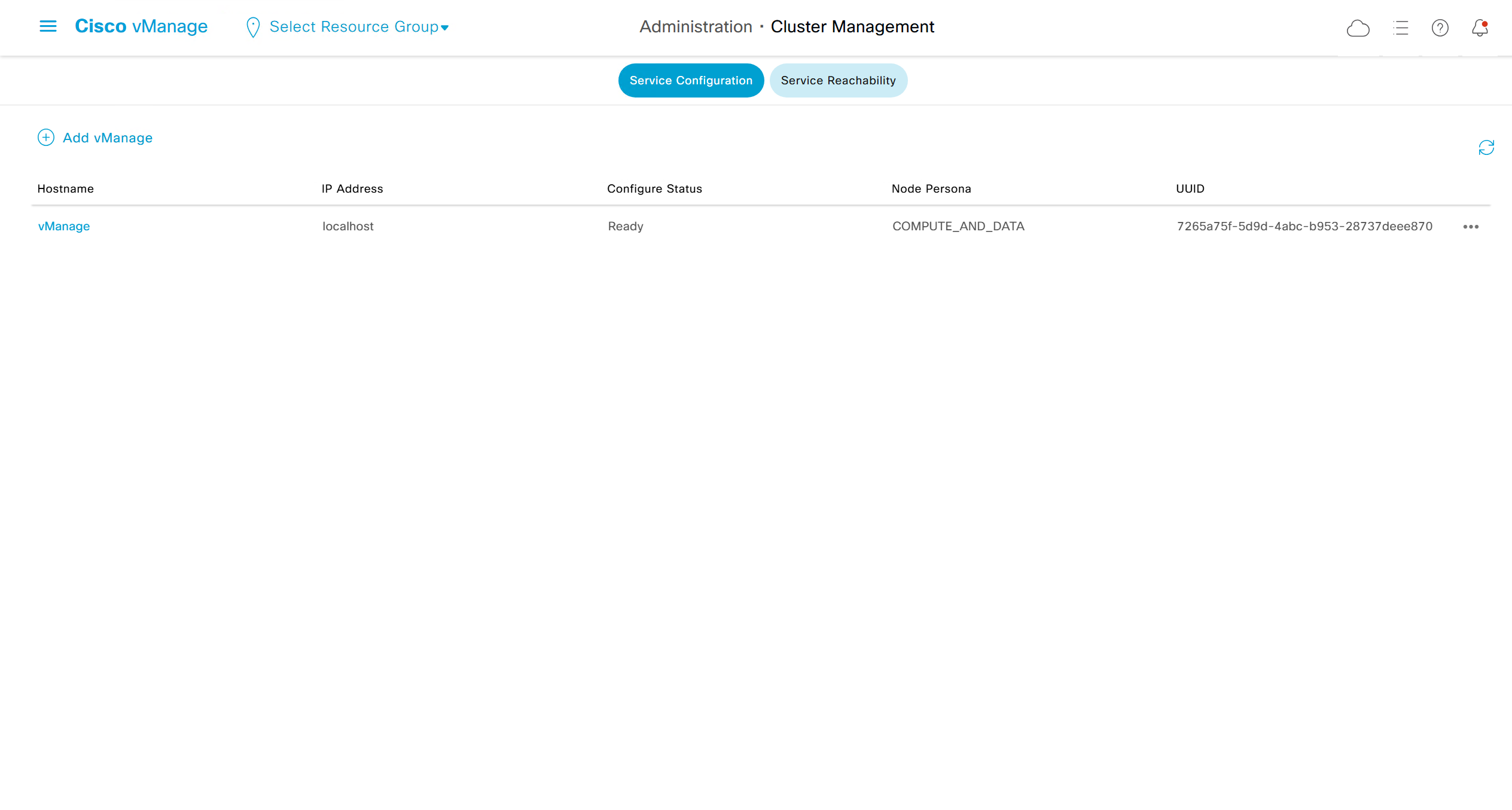
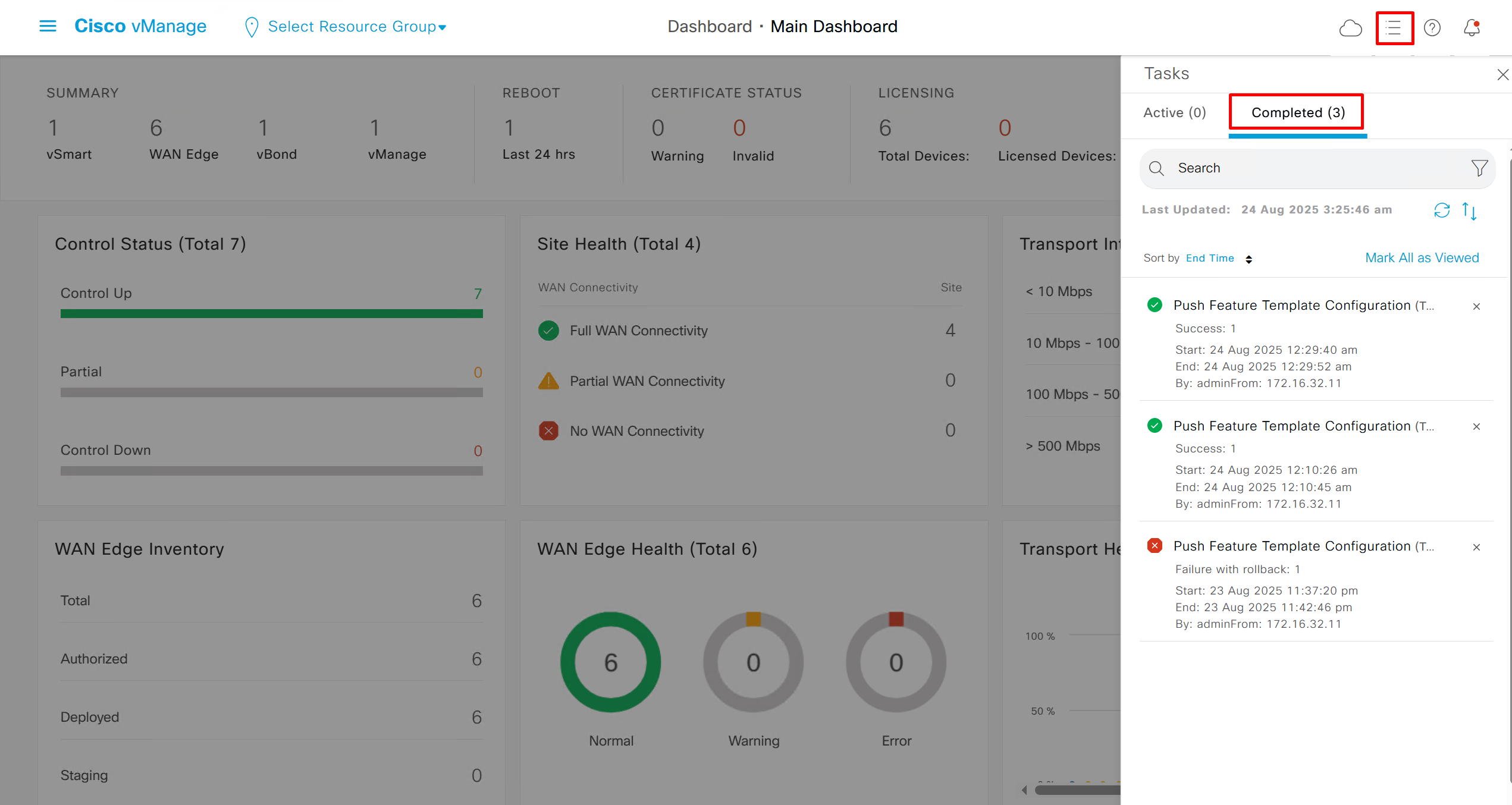
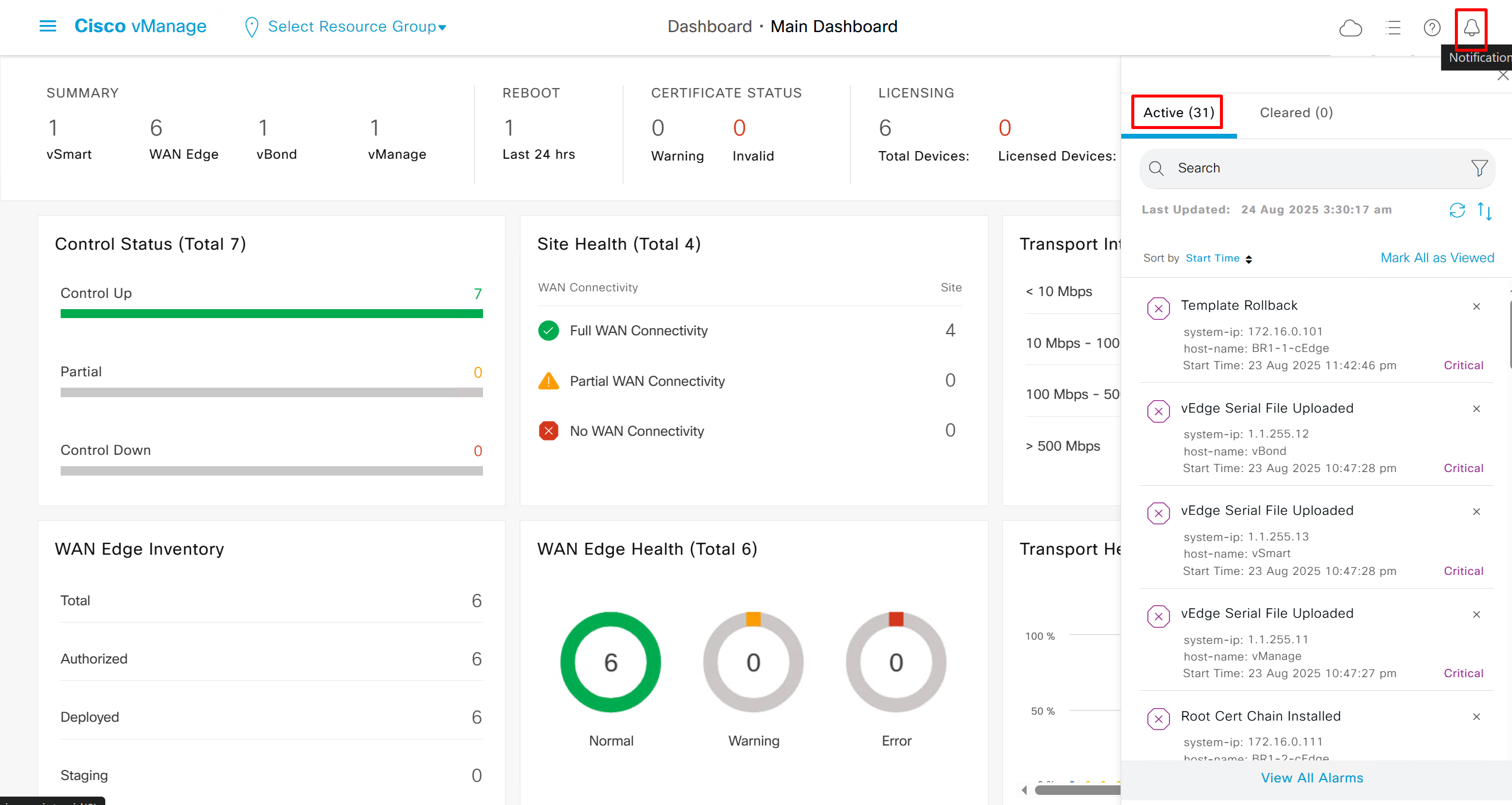
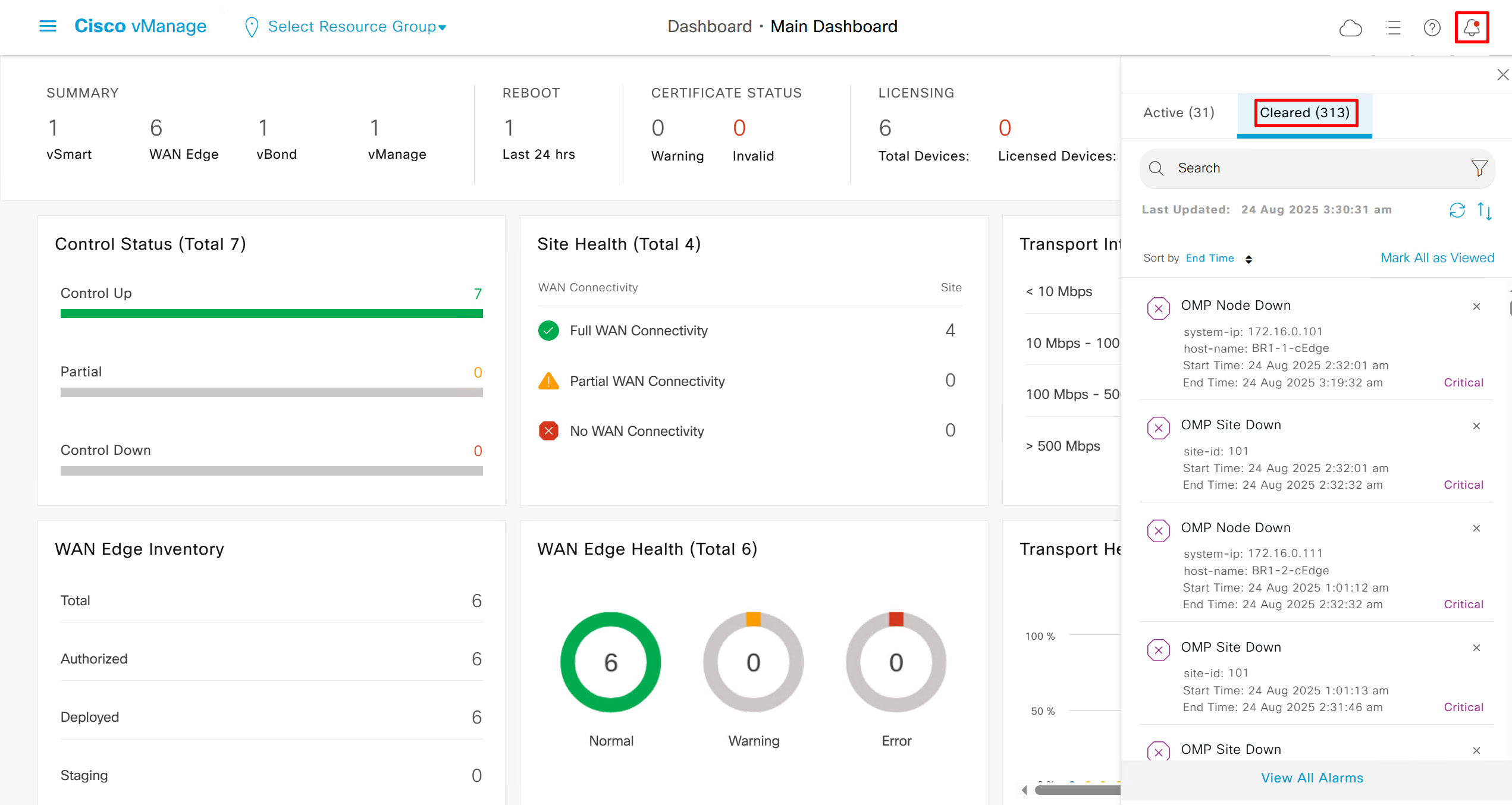



OMP , TLOCs and IPSec VPN
vSmart# show omp peers
R -> routes received
I -> routes installed
S -> routes sent
DOMAIN OVERLAY SITE
PEER TYPE ID ID ID STATE UPTIME R/I/S
------------------------------------------------------------------------------------------
172.16.0.11 vedge 1 1 1 up 0:04:15:03 0/0/0
172.16.0.12 vedge 1 1 1 up 0:03:16:13 0/0/0
172.16.0.101 vedge 1 1 101 up 0:02:45:09 0/0/0
172.16.0.102 vedge 1 1 102 up 0:04:15:21 0/0/0
172.16.0.103 vedge 1 1 103 up 0:04:14:59 0/0/0
172.16.0.111 vedge 1 1 101 up 0:02:45:31 0/0/0R1-cEdge#show sdwan omp peers
R -> routes received
I -> routes installed
S -> routes sent
DOMAIN OVERLAY SITE
PEER TYPE ID ID ID STATE UPTIME R/I/S
------------------------------------------------------------------------------------------
1.1.255.13 vsmart 1 1 255 up 0:04:17:40 0/0/0All the TLOCs known by router, two repeating system IPs means router has transports / colors
R1-cEdge#show sdwan omp tloc-paths
tloc-paths entries 172.16.0.11 biz-internet ipsec
tloc-paths entries 172.16.0.12 mpls ipsec
tloc-paths entries 172.16.0.101 biz-internet ipsec
tloc-paths entries 172.16.0.102 mpls ipsec
tloc-paths entries 172.16.0.102 biz-internet ipsec
tloc-paths entries 172.16.0.103 mpls ipsec
tloc-paths entries 172.16.0.103 biz-internet ipsec
tloc-paths entries 172.16.0.111 mpls ipsecFull TLOC details
R1-cEdge#show sdwan omp tlocs
---------------------------------------------------
tloc entries for 172.16.0.11
biz-internet
ipsec
---------------------------------------------------
RECEIVED FROM:
peer 0.0.0.0
status C,Red,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
attribute-type installed
encap-key not set
encap-proto 0
encap-spi 284
encap-auth sha1-hmac,ah-sha1-hmac
encap-encrypt aes256
public-ip 1.1.1.2
public-port 12366
private-ip 1.1.1.2
private-port 12366
public-ip ::
public-port 0
private-ip ::
private-port 0
bfd-status up << BFD status should be up
domain-id not set
site-id 1
overlay-id not set
preference 0
tag not set
stale not set
weight 1
version 3
gen-id 0x80000001
carrier default
restrict 0
on-demand 0
groups [ 0 ]
bandwidth 0
bandwidth-dmin 0
bandwidth-down 0
bandwidth-dmax 0
adapt-qos-period 0
adapt-qos-up 0
qos-group default-group
border not set
extended-ipsec-anti-replay not set
unknown-attr-len not set
---------------------------------------------------
tloc entries for 172.16.0.12
mpls
ipsec
---------------------------------------------------
RECEIVED FROM:
peer 1.1.255.13
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
attribute-type installed
encap-key not set
encap-proto 0
encap-spi 287
encap-auth sha1-hmac,ah-sha1-hmac
encap-encrypt aes256
public-ip 10.0.1.2
public-port 12406
private-ip 10.0.1.2
private-port 12406
public-ip ::
public-port 0
private-ip ::
private-port 0
bfd-status down
domain-id not set
site-id 1
overlay-id not set
preference 0
tag not set
stale not set
weight 1
version 3
gen-id 0x80000000
carrier default
restrict 0
on-demand 0
groups [ 0 ]
bandwidth 0
bandwidth-dmin 0
bandwidth-down 0
bandwidth-dmax 0
adapt-qos-period 0
adapt-qos-up 0
qos-group default-group
border not set
extended-ipsec-anti-replay not set
unknown-attr-len not set
---------------------------------------------------
tloc entries for 172.16.0.101
biz-internet
ipsec
---------------------------------------------------
RECEIVED FROM:
peer 1.1.255.13
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
attribute-type installed
encap-key not set
encap-proto 0
encap-spi 285
encap-auth sha1-hmac,ah-sha1-hmac
encap-encrypt aes256
public-ip 1.1.1.101
public-port 12386
private-ip 1.1.1.101
private-port 12386
public-ip ::
public-port 0
private-ip ::
private-port 0
bfd-status up
domain-id not set
site-id 101
overlay-id not set
preference 0
tag not set
stale not set
weight 1
version 3
gen-id 0x80000000
carrier default
restrict 0
on-demand 0
groups [ 0 ]
bandwidth 0
bandwidth-dmin 0
bandwidth-down 0
bandwidth-dmax 0
adapt-qos-period 0
adapt-qos-up 0
qos-group default-group
border not set
extended-ipsec-anti-replay not set
unknown-attr-len not set
---------------------------------------------------
tloc entries for 172.16.0.102
mpls
ipsec
---------------------------------------------------
RECEIVED FROM:
peer 1.1.255.13
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
attribute-type installed
encap-key not set
encap-proto 0
encap-spi 262
encap-auth sha1-hmac,ah-sha1-hmac
encap-encrypt aes256
public-ip 10.0.102.2
public-port 12426
private-ip 10.0.102.2
private-port 12426
public-ip ::
public-port 0
private-ip ::
private-port 0
bfd-status up
domain-id not set
site-id 102
overlay-id not set
preference 0
tag not set
stale not set
weight 1
version 3
gen-id 0x80000000
carrier default
restrict 0
on-demand 0
groups [ 0 ]
bandwidth 0
bandwidth-dmin 0
bandwidth-down 0
bandwidth-dmax 0
adapt-qos-period 0
adapt-qos-up 0
qos-group default-group
border not set
extended-ipsec-anti-replay not set
unknown-attr-len not set
---------------------------------------------------
tloc entries for 172.16.0.102
biz-internet
ipsec
---------------------------------------------------
RECEIVED FROM:
peer 1.1.255.13
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
attribute-type installed
encap-key not set
encap-proto 0
encap-spi 280
encap-auth sha1-hmac,ah-sha1-hmac
encap-encrypt aes256
public-ip 1.1.1.102
public-port 12366
private-ip 1.1.1.102
private-port 12366
public-ip ::
public-port 0
private-ip ::
private-port 0
bfd-status up
domain-id not set
site-id 102
overlay-id not set
preference 0
tag not set
stale not set
weight 1
version 3
gen-id 0x80000000
carrier default
restrict 0
on-demand 0
groups [ 0 ]
bandwidth 0
bandwidth-dmin 0
bandwidth-down 0
bandwidth-dmax 0
adapt-qos-period 0
adapt-qos-up 0
qos-group default-group
border not set
extended-ipsec-anti-replay not set
unknown-attr-len not set
---------------------------------------------------
tloc entries for 172.16.0.103
mpls
ipsec
---------------------------------------------------
RECEIVED FROM:
peer 1.1.255.13
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
attribute-type installed
encap-key not set
encap-proto 0
encap-spi 265
encap-auth sha1-hmac,ah-sha1-hmac
encap-encrypt aes256
public-ip 10.0.103.2
public-port 12366
private-ip 10.0.103.2
private-port 12366
public-ip ::
public-port 0
private-ip ::
private-port 0
bfd-status up
domain-id not set
site-id 103
overlay-id not set
preference 0
tag not set
stale not set
weight 1
version 3
gen-id 0x80000000
carrier default
restrict 0
on-demand 0
groups [ 0 ]
bandwidth 0
bandwidth-dmin 0
bandwidth-down 0
bandwidth-dmax 0
adapt-qos-period 0
adapt-qos-up 0
qos-group default-group
border not set
extended-ipsec-anti-replay not set
unknown-attr-len not set
---------------------------------------------------
tloc entries for 172.16.0.103
biz-internet
ipsec
---------------------------------------------------
RECEIVED FROM:
peer 1.1.255.13
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
attribute-type installed
encap-key not set
encap-proto 0
encap-spi 286
encap-auth sha1-hmac,ah-sha1-hmac
encap-encrypt aes256
public-ip 1.1.1.103
public-port 12426
private-ip 1.1.1.103
private-port 12426
public-ip ::
public-port 0
private-ip ::
private-port 0
bfd-status up
domain-id not set
site-id 103
overlay-id not set
preference 0
tag not set
stale not set
weight 1
version 3
gen-id 0x80000000
carrier default
restrict 0
on-demand 0
groups [ 0 ]
bandwidth 0
bandwidth-dmin 0
bandwidth-down 0
bandwidth-dmax 0
adapt-qos-period 0
adapt-qos-up 0
qos-group default-group
border not set
extended-ipsec-anti-replay not set
unknown-attr-len not set
---------------------------------------------------
tloc entries for 172.16.0.111
mpls
ipsec
---------------------------------------------------
RECEIVED FROM:
peer 1.1.255.13
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
attribute-type installed
encap-key not set
encap-proto 0
encap-spi 266
encap-auth sha1-hmac,ah-sha1-hmac
encap-encrypt aes256
public-ip 10.0.101.2
public-port 12406
private-ip 10.0.101.2
private-port 12406
public-ip ::
public-port 0
private-ip ::
private-port 0
bfd-status up
domain-id not set
site-id 101
overlay-id not set
preference 0
tag not set
stale not set
weight 1
version 3
gen-id 0x80000000
carrier default
restrict 0
on-demand 0
groups [ 0 ]
bandwidth 0
bandwidth-dmin 0
bandwidth-down 0
bandwidth-dmax 0
adapt-qos-period 0
adapt-qos-up 0
qos-group default-group
border not set
extended-ipsec-anti-replay not set
unknown-attr-len not setInterval for BFD session is 1000 msec
R1-cEdge#show sdwan bfd sessions
SOURCE TLOC REMOTE TLOC DST PUBLIC DST PUBLIC DETECT TX
SYSTEM IP SITE ID STATE COLOR COLOR SOURCE IP IP PORT ENCAP MULTIPLIER INTERVAL(msec UPTIME TRANSITIONS
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------
172.16.0.101 101 up biz-internet biz-internet 1.1.1.2 1.1.1.101 12386 ipsec 7 1000 10 0:23:51:18 0
172.16.0.102 102 up biz-internet biz-internet 1.1.1.2 1.1.1.102 12386 ipsec 7 1000 10 0:00:48:47 2
172.16.0.103 103 up biz-internet biz-internet 1.1.1.2 1.1.1.103 12426 ipsec 7 1000 10 0:03:48:08 0
172.16.0.111 101 up biz-internet mpls 1.1.1.2 10.0.101.2 12406 ipsec 7 1000 10 0:23:14:16 1
172.16.0.102 102 up biz-internet mpls 1.1.1.2 10.0.102.2 12426 ipsec 7 1000 10 0:13:47:48 0
172.16.0.103 103 up biz-internet mpls 1.1.1.2 10.0.103.2 12366 ipsec 7 1000 10 0:12:48:23 0
on ipsec outbound connections destination IP will be of remote routers
R1-cEdge#show sdwan ipsec outbound-connections
SOURCE SOURCE DEST DEST REMOTE REMOTE INTEGRITY NEGOTIATED
IP PORT IP PORT SPI TUNNEL MTU TLOC ADDRESS TLOC COLOR USED KEY HASH ENCRYPTION ALGORITHM TC SPIs
----------------------------------------------------------------------------------------------------------------------------------------------------------------
1.1.1.2 12366 1.1.1.101 12386 285 1438 172.16.0.101 biz-internet ip-udp-esp *****346f AES-GCM-256 8
1.1.1.2 12366 1.1.1.102 12386 281 1438 172.16.0.102 biz-internet ip-udp-esp *****60d6 AES-GCM-256 8
1.1.1.2 12366 1.1.1.103 12426 286 1438 172.16.0.103 biz-internet ip-udp-esp *****d535 AES-GCM-256 8
1.1.1.2 12366 10.0.101.2 12406 266 1438 172.16.0.111 mpls ip-udp-esp *****bf3e AES-GCM-256 8
1.1.1.2 12366 10.0.102.2 12426 262 1438 172.16.0.102 mpls ip-udp-esp *****8f3f AES-GCM-256 8
1.1.1.2 12366 10.0.103.2 12366 266 1438 172.16.0.103 mpls ip-udp-esp *****863f AES-GCM-256 8on the ipsec inbound connections, source IP will be of the remote routers
R1-cEdge#show sdwan ipsec inbound-connections
SOURCE SOURCE DEST DEST REMOTE REMOTE LOCAL LOCAL NEGOTIATED
IP PORT IP PORT TLOC ADDRESS TLOC COLOR TLOC ADDRESS TLOC COLOR ENCRYPTION ALGORITHM TC SPIs
--------------------------------------------------------------------------------------------------------------------------------------------------
1.1.1.101 12386 1.1.1.2 12366 172.16.0.101 biz-internet 172.16.0.11 biz-internet AES-GCM-256 8
10.0.102.2 12426 1.1.1.2 12366 172.16.0.102 mpls 172.16.0.11 biz-internet AES-GCM-256 8
1.1.1.102 12386 1.1.1.2 12366 172.16.0.102 biz-internet 172.16.0.11 biz-internet AES-GCM-256 8
10.0.103.2 12366 1.1.1.2 12366 172.16.0.103 mpls 172.16.0.11 biz-internet AES-GCM-256 8
1.1.1.103 12426 1.1.1.2 12366 172.16.0.103 biz-internet 172.16.0.11 biz-internet AES-GCM-256 8
10.0.101.2 12406 1.1.1.2 12366 172.16.0.111 mpls 172.16.0.11 biz-internet AES-GCM-256 Service Side VPN , Site Local LAN
Setup VPN 10 VRF
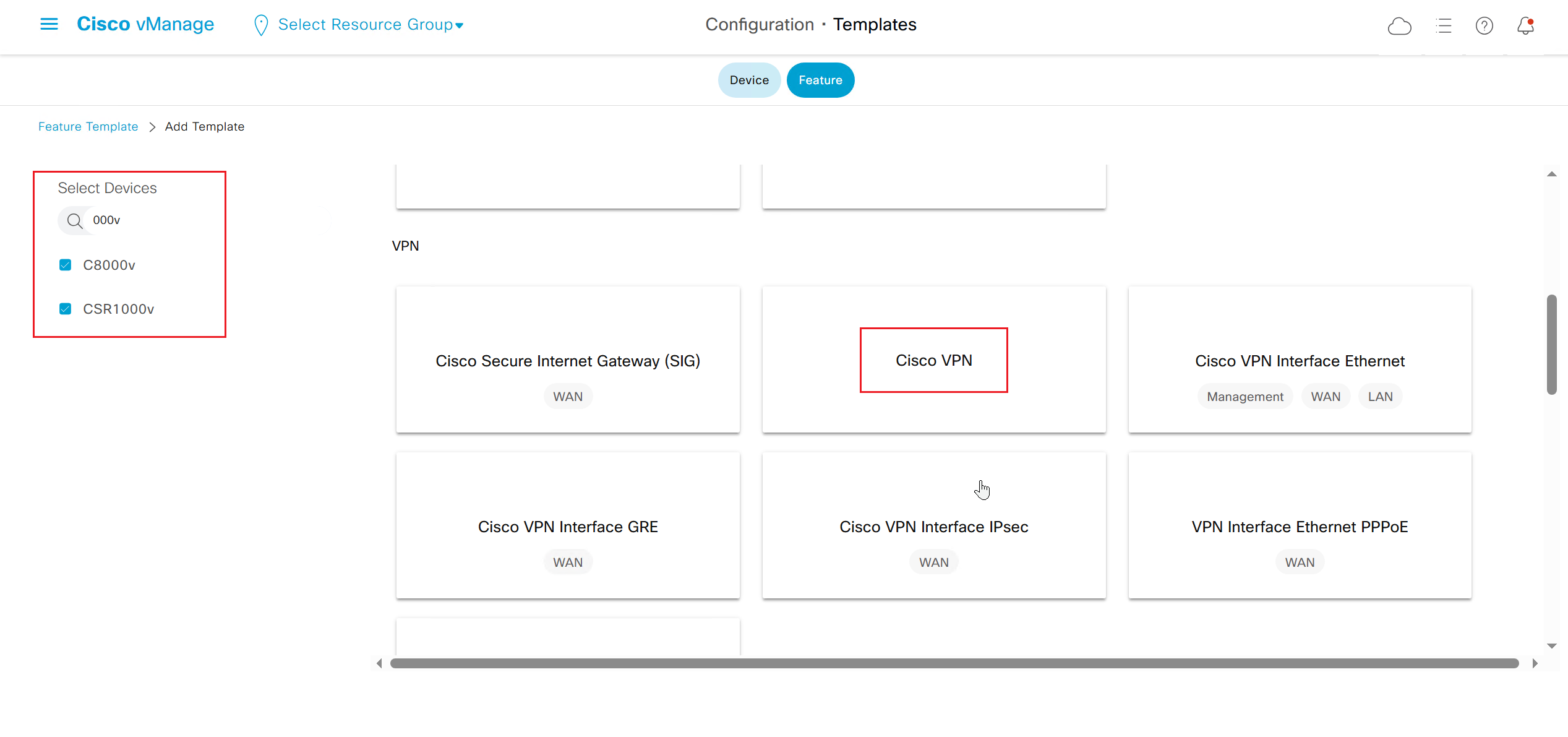
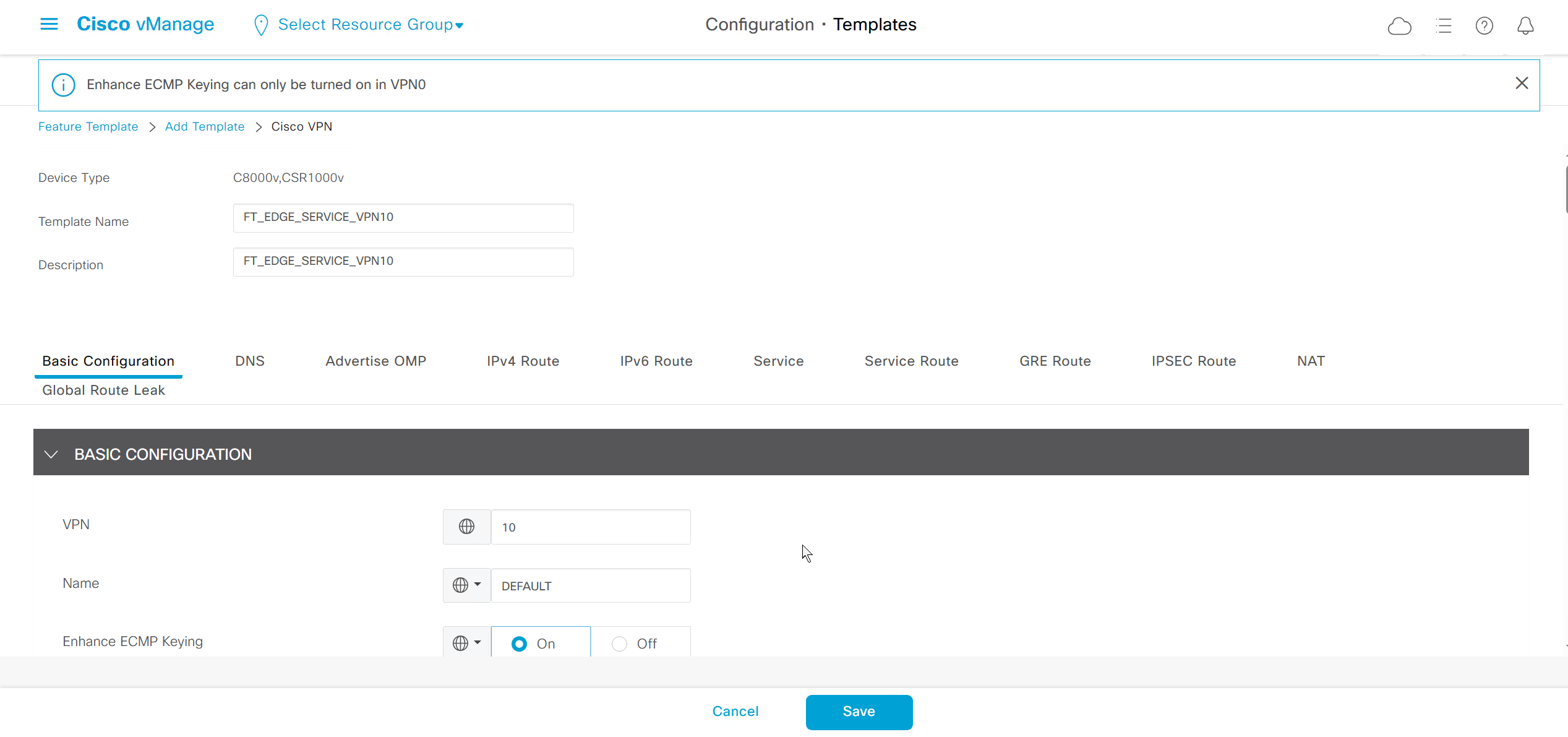
This is to redistribute connected routes in OMP
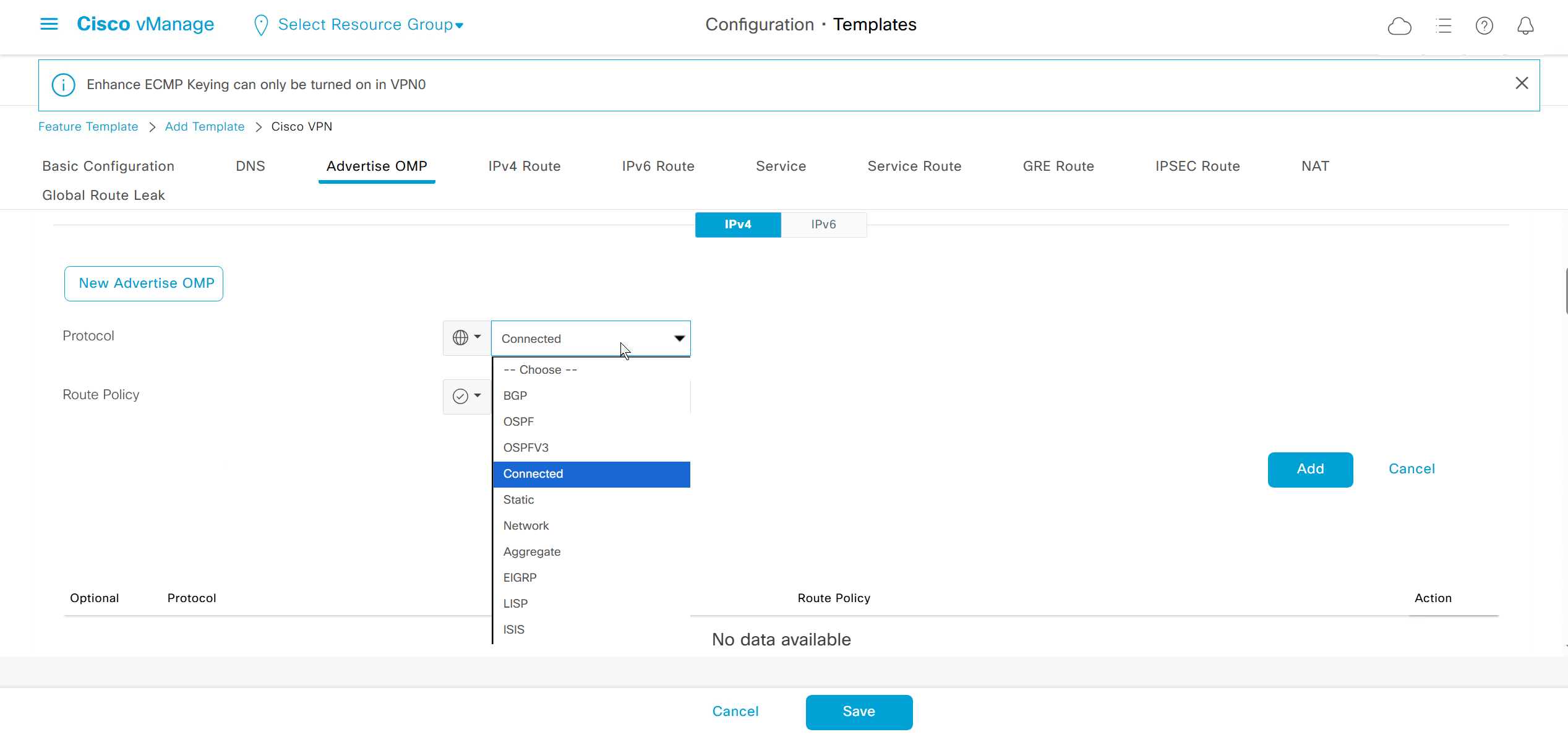
This is to redistribute static routes in OMP
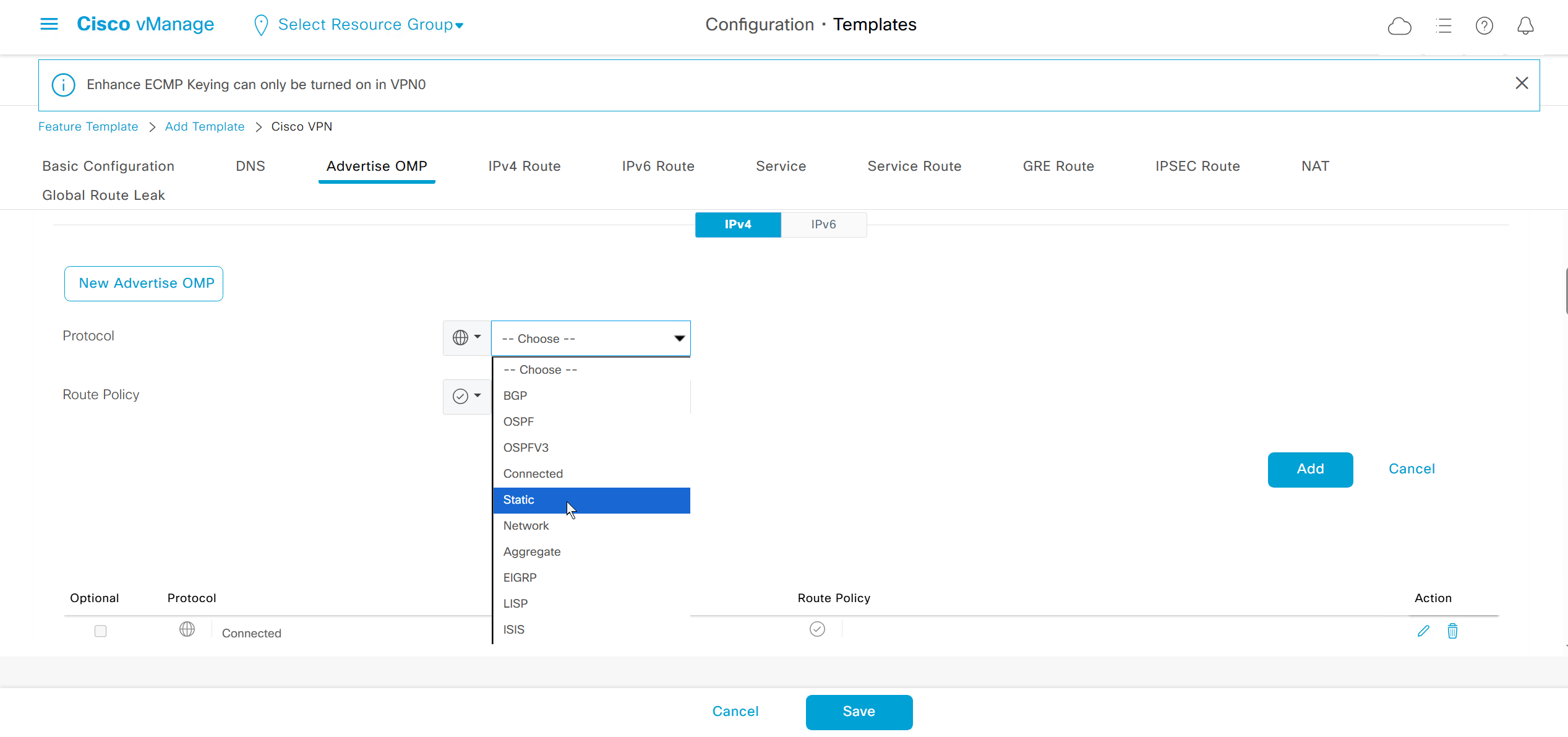
These IPv4 routes are for pointing at the LAN side networks
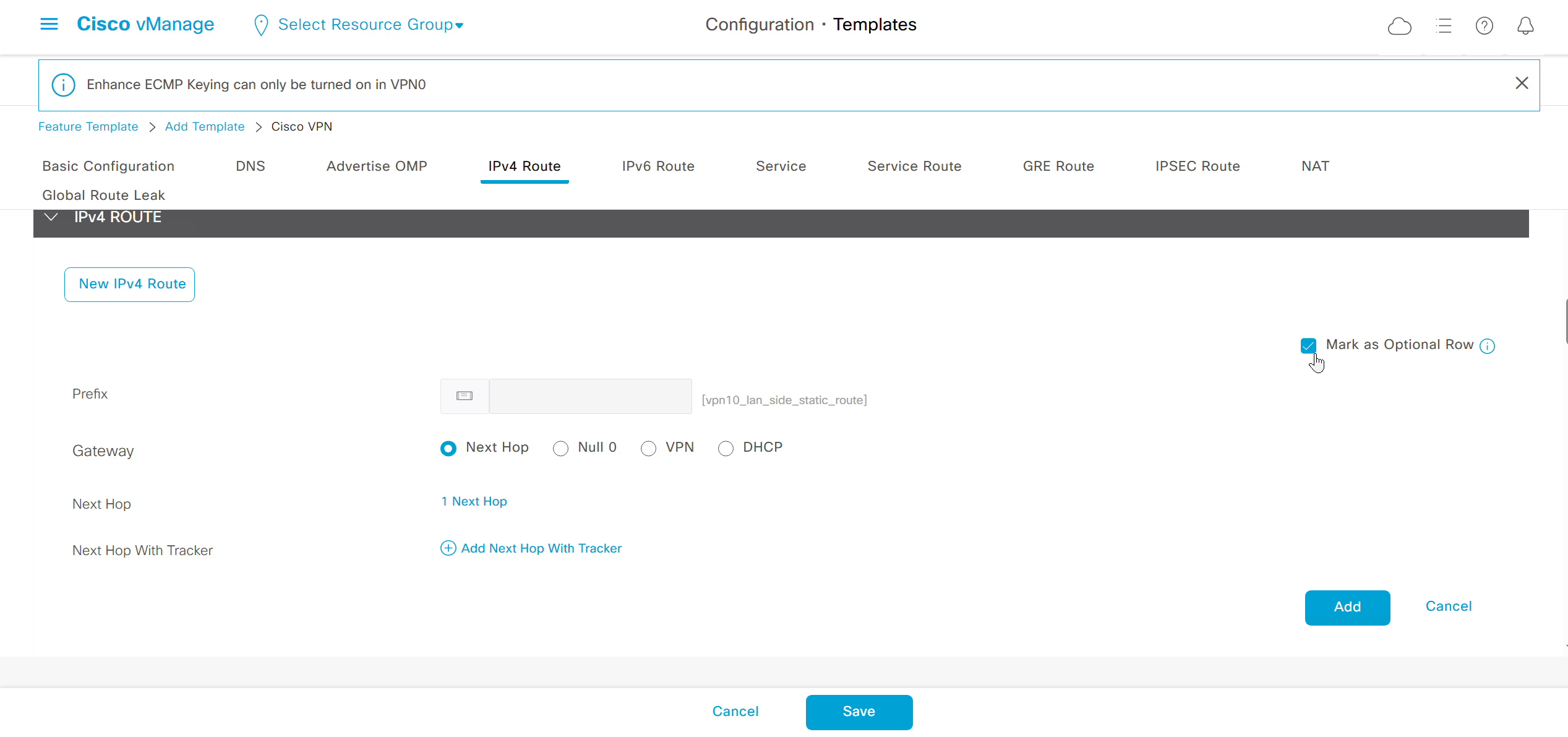
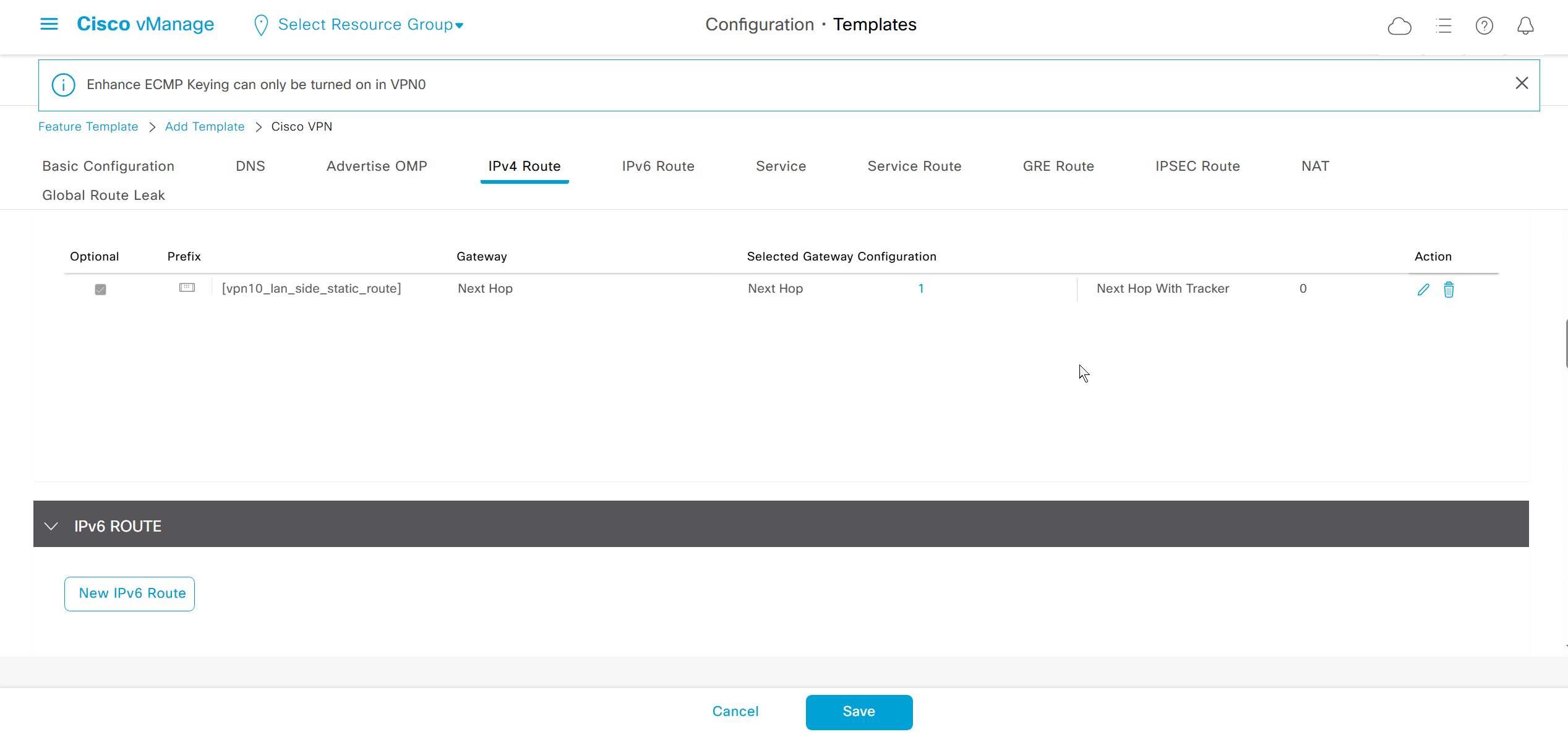
ECMP Keyring can only be turned on in VPN0
Create new VPN Ethernet Interface Feature templates
Physical Interface GIG3 with IP address variable (so sites without dot1q switch can operate such as Branch 1)
Physical Interface GIG3 without IP address so sites like Branch 2 and Branch 3 can do trunk interface on router with dot1q switch
dot1q interface for Vlan 10 with IP address and reduced MTU of 1496 to compensate for VLAN header on trunk
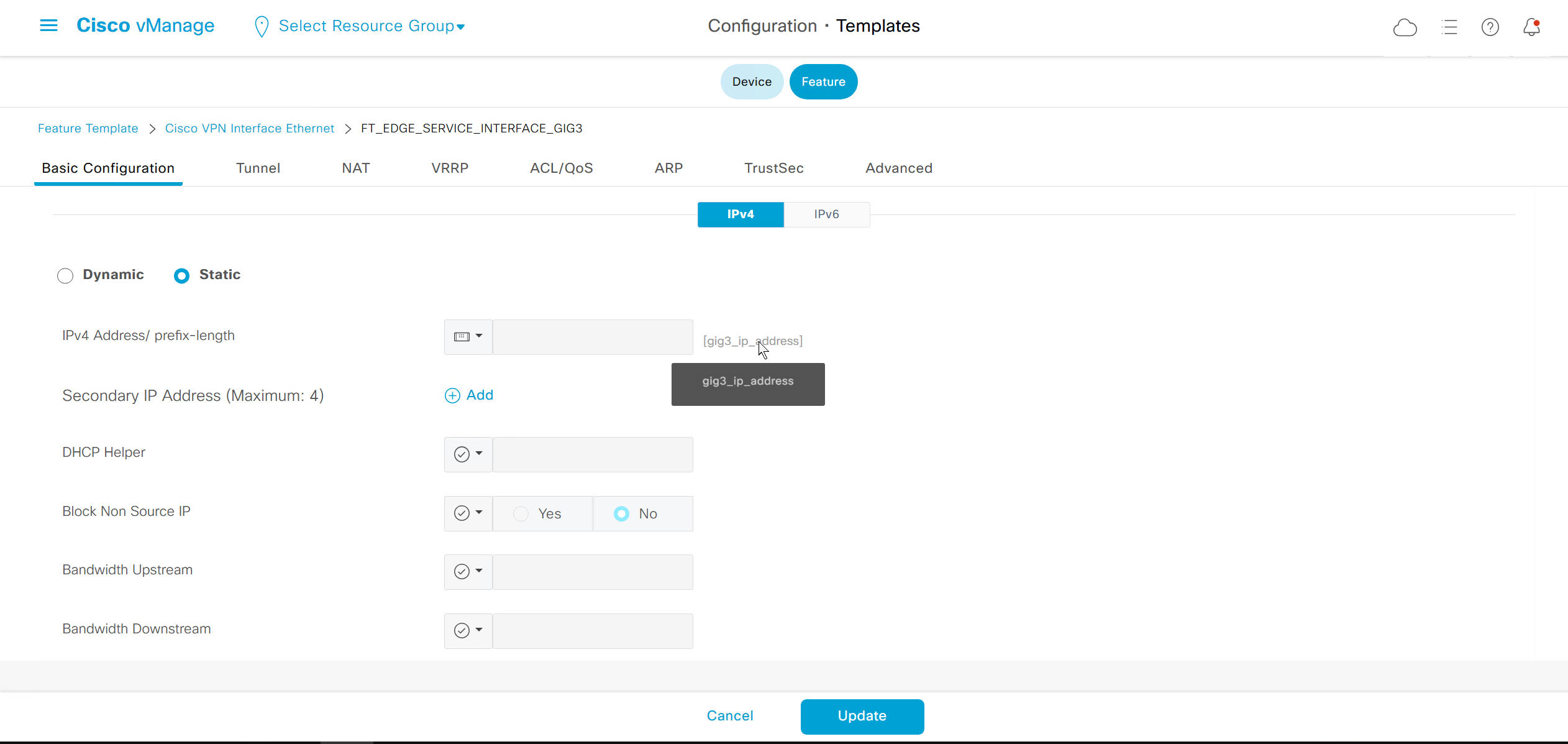
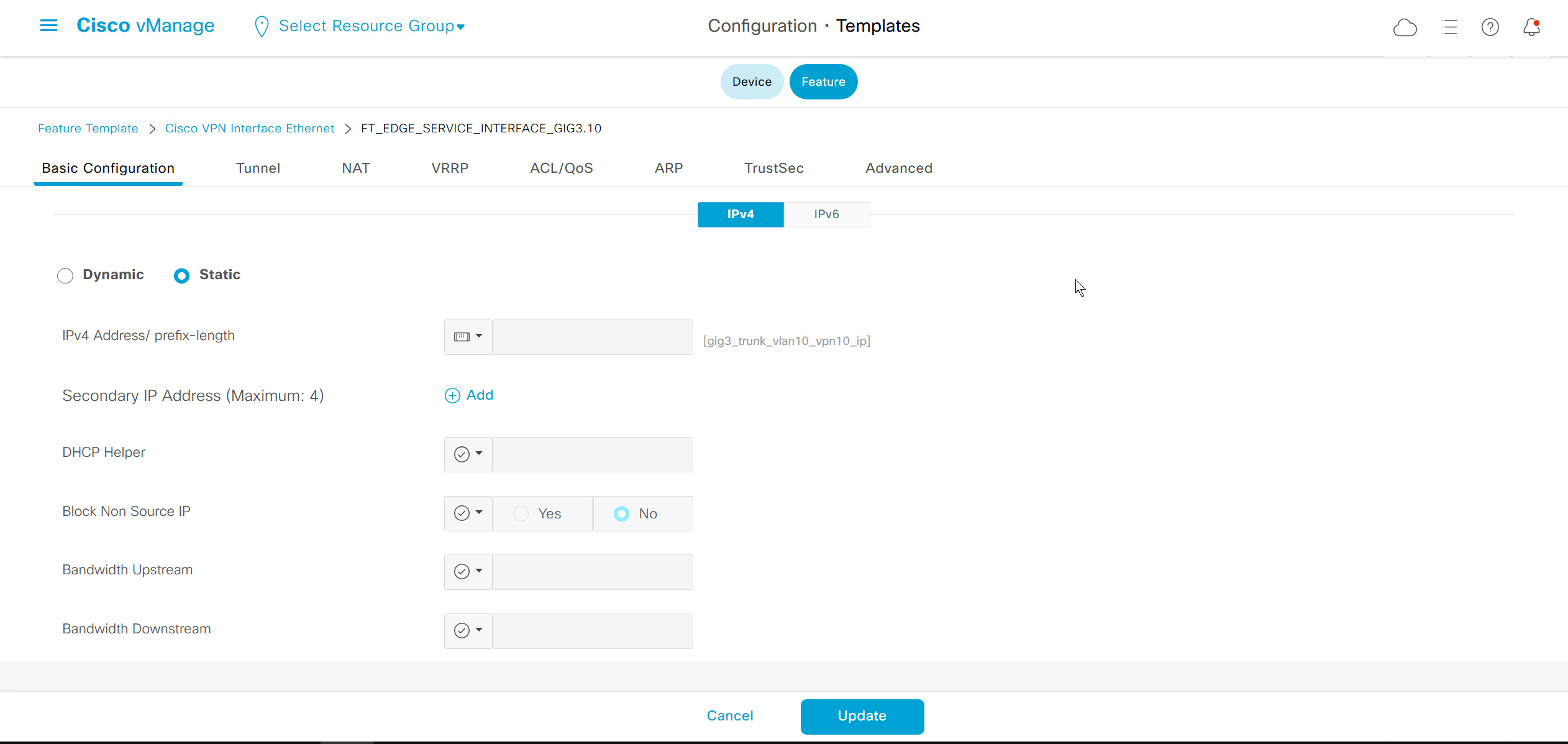
reduce the MTU to 1496
for dot1q interfaces we need to have Physical interface but without IP under VPN 0
and dot1q interface under service VPN
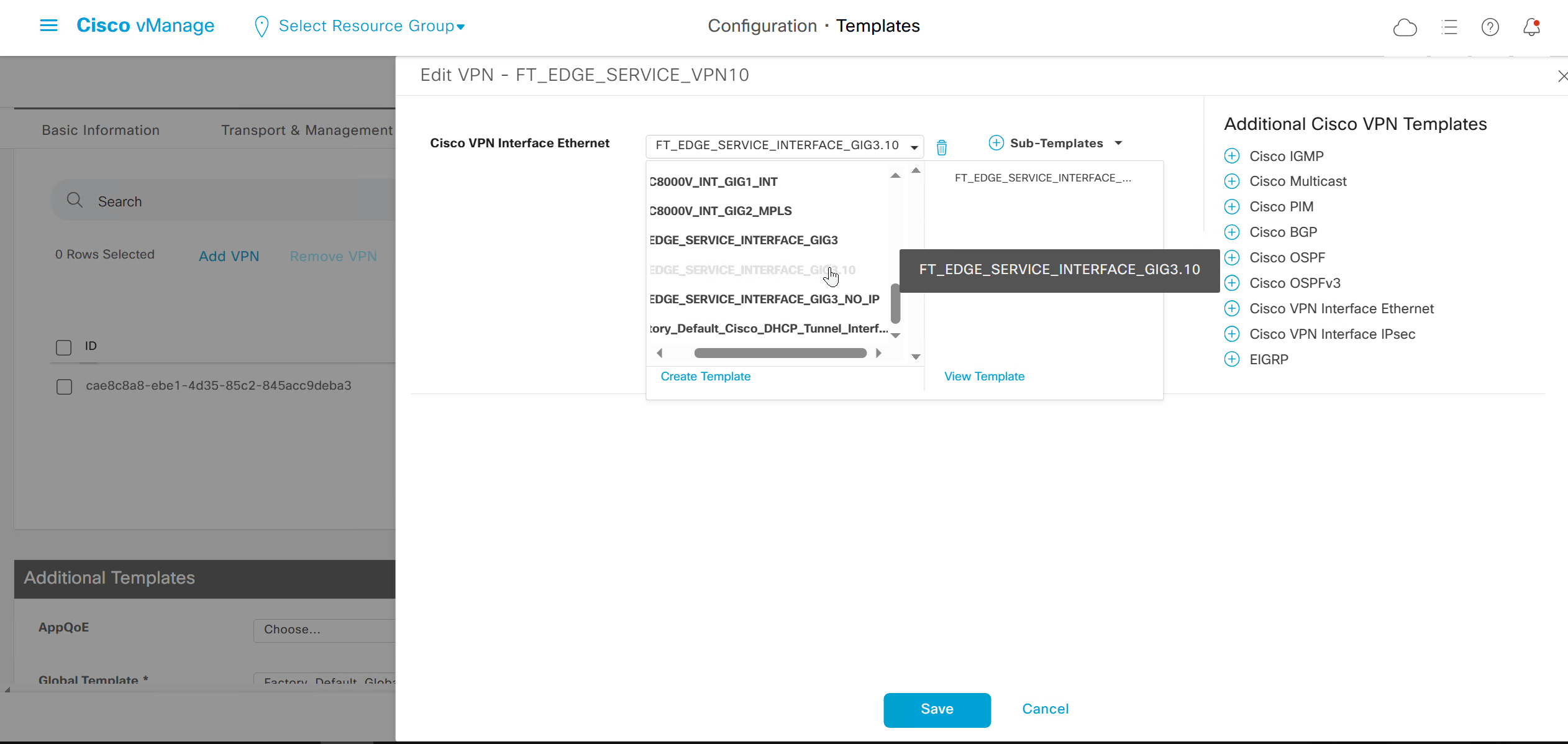
VPCS> ip 172.17.3.10 /25 172.17.3.1
Checking for duplicate address...
VPCS : 172.17.3.10 255.255.255.128 gateway 172.17.3.1
VPCS> ping 172.17.3.1
172.17.3.1 icmp_seq=1 timeout
84 bytes from 172.17.3.1 icmp_seq=2 ttl=255 time=1.393 ms
84 bytes from 172.17.3.1 icmp_seq=3 ttl=255 time=1.470 ms
84 bytes from 172.17.3.1 icmp_seq=4 ttl=255 time=1.429 ms
84 bytes from 172.17.3.1 icmp_seq=5 ttl=255 time=1.350 ms
VPCS> ping 172.17.3.10
172.17.3.10 icmp_seq=1 ttl=64 time=0.001 ms
172.17.3.10 icmp_seq=2 ttl=64 time=0.001 ms
172.17.3.10 icmp_seq=3 ttl=64 time=0.001 ms
172.17.3.10 icmp_seq=4 ttl=64 time=0.001 ms
172.17.3.10 icmp_seq=5 ttl=64 time=0.001 ms
VPCS> ping 172.17.2.1
84 bytes from 172.17.2.1 icmp_seq=1 ttl=254 time=6.716 ms
84 bytes from 172.17.2.1 icmp_seq=2 ttl=254 time=3.531 ms
84 bytes from 172.17.2.1 icmp_seq=3 ttl=254 time=2.678 ms
84 bytes from 172.17.2.1 icmp_seq=4 ttl=254 time=3.613 ms
84 bytes from 172.17.2.1 icmp_seq=5 ttl=254 time=3.625 ms
VPCS> ping 172.17.2.10
84 bytes from 172.17.2.10 icmp_seq=1 ttl=62 time=5.851 ms
84 bytes from 172.17.2.10 icmp_seq=2 ttl=62 time=2.274 ms
84 bytes from 172.17.2.10 icmp_seq=3 ttl=62 time=3.498 ms
84 bytes from 172.17.2.10 icmp_seq=4 ttl=62 time=3.398 ms
84 bytes from 172.17.2.10 icmp_seq=5 ttl=62 time=3.495 ms
VPCS>
VPCS> set pcname BR3-CLIENT
BR3-CLIENT>
BR3-CLIENT> save
Saving startup configuration to startup.vpc
. doneBR1-CLIENT> trace 172.17.2.10
trace to 172.17.2.10, 8 hops max, press Ctrl+C to stop
1 *172.17.1.1 0.351 ms 0.194 ms
2 *1.1.1.102 1.300 ms 1.543 ms
3 *172.17.2.10 5.741 ms (ICMP type:3, code:3, Destination port unreachable)BR3-cEdge#show sdwan omp routes
Generating output, this might take time, please wait ...
Code:
C -> chosen
I -> installed
Red -> redistributed
Rej -> rejected
L -> looped
R -> resolved
S -> stale
Ext -> extranet
Inv -> invalid
Stg -> staged
IA -> On-demand inactive
U -> TLOC unresolved
PATH ATTRIBUTE
VPN PREFIX FROM PEER ID LABEL STATUS TYPE TLOC IP COLOR ENCAP PREFERENCE
--------------------------------------------------------------------------------------------------------------------------------------
10 172.17.2.0/25 1.1.255.13 9 1003 C,I,R installed 172.16.0.102 mpls ipsec -
1.1.255.13 10 1003 C,I,R installed 172.16.0.102 biz-internet ipsec -
10 172.17.3.0/25 0.0.0.0 66 1003 C,Red,R installed 172.16.0.103 mpls ipsec -
0.0.0.0 68 1003 C,Red,R installed 172.16.0.103 biz-internet ipsec -BR3-cEdge#show sdwan omp routes 172.17.2.0/25 detail
---------------------------------------------------
omp route entries for vpn 10 route 172.17.2.0/25
---------------------------------------------------
RECEIVED FROM:
peer 1.1.255.13
path-id 9
label 1003
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 172.16.0.102
type installed
tloc 172.16.0.102, mpls, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 102
preference not set
tag not set
origin-proto connected
origin-metric 0
as-path not set
community not set
unknown-attr-len not set
RECEIVED FROM:
peer 1.1.255.13
path-id 10
label 1003
status C,I,R
loss-reason not set
lost-to-peer not set
lost-to-path-id not set
Attributes:
originator 172.16.0.102
type installed
tloc 172.16.0.102, biz-internet, ipsec
ultimate-tloc not set
domain-id not set
overlay-id 1
site-id 102
preference not set
tag not set
origin-proto connected
origin-metric 0
as-path not set
community not set
unknown-attr-len not setBR3-cEdge#routing-context vrf 10
BR3-cEdge%10#ping 172.17.3.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.17.3.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms
BR3-cEdge%10#ping 172.17.3.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.17.3.10, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/2 ms
BR3-cEdge%10#ping 172.17.2.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.17.2.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/3 ms
BR3-cEdge%10#ping 172.17.2.10
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.17.2.10, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/3/6 ms
BR3-cEdge%10#exitSDWAN Peering with OSPF and BGP
router bgp 10
template peer-policy CE
send-community both
exit-peer-policy
!
template peer-session CE
ebgp-multihop 5
timers 30 90
exit-peer-session
!
bgp log-neighbor-changes
neighbor 10.0.1.2 remote-as 65001
neighbor 10.0.1.2 inherit peer-session CE
neighbor 10.0.101.2 remote-as 65101
neighbor 10.0.101.2 inherit peer-session CE
neighbor 10.0.102.2 remote-as 65102
neighbor 10.0.102.2 inherit peer-session CE
neighbor 10.0.103.2 remote-as 65103
neighbor 10.0.103.2 inherit peer-session CE
!
address-family ipv4
network 10.0.101.0 mask 255.255.255.252
network 10.0.102.0 mask 255.255.255.252
network 10.0.103.0 mask 255.255.255.252
neighbor 10.0.1.2 activate
neighbor 10.0.1.2 inherit peer-policy CE
neighbor 10.0.101.2 activate
neighbor 10.0.101.2 inherit peer-policy CE
neighbor 10.0.102.2 activate
neighbor 10.0.102.2 inherit peer-policy CE
neighbor 10.0.103.2 activate
neighbor 10.0.103.2 inherit peer-policy CE
exit-address-family
!interface Loopback0
ip address 3.3.3.3 255.255.255.255
ip ospf network point-to-point
ip ospf 10 area 0
!
interface Loopback1
ip address 4.4.4.4 255.255.255.255
ip ospf network point-to-point
ip ospf 10 area 0
!
interface Loopback2
ip address 5.5.5.5 255.255.255.255
ip ospf network point-to-point
ip ospf 10 area 0
!
interface Loopback3
ip address 6.6.6.6 255.255.255.255
ip ospf network point-to-point
ip ospf 10 area 0
!
interface Loopback4
ip address 7.7.7.7 255.255.255.255
ip ospf network point-to-point
ip ospf 10 area 0
!
interface Loopback5
ip address 8.8.8.8 255.255.255.255
ip ospf network point-to-point
ip ospf 10 area 0
!
interface Loopback6
ip address 9.9.9.9 255.255.255.255
ip ospf network point-to-point
ip ospf 10 area 0
!
interface Loopback7
ip address 10.10.10.10 255.255.255.255
ip ospf network point-to-point
ip ospf 10 area 0
!
interface Vlan10
ip address 172.17.3.3 255.255.255.128
ip mtu 1496
ip ospf authentication message-digest
ip ospf message-digest-key 1 md5 cisco123
!
router ospf 10
router-id 3.3.3.3
no auto-cost
passive-interface Loopback0
network 172.17.3.3 0.0.0.0 area 0
!
We will configure ebgp with interfaces (point to point links) and not loopbacks
For fun we will create loopback interfaces with same IP address as system ID and then advertise them in BGP
for that we need to create Ethernet interface feature template
(while creating loopback0 interface on C8000v with same IP as system IP was not an issue, it was rejected on CSR1000v so loopback IP address on CSR1000v is set different from its system IP)
then we create BGP feature template

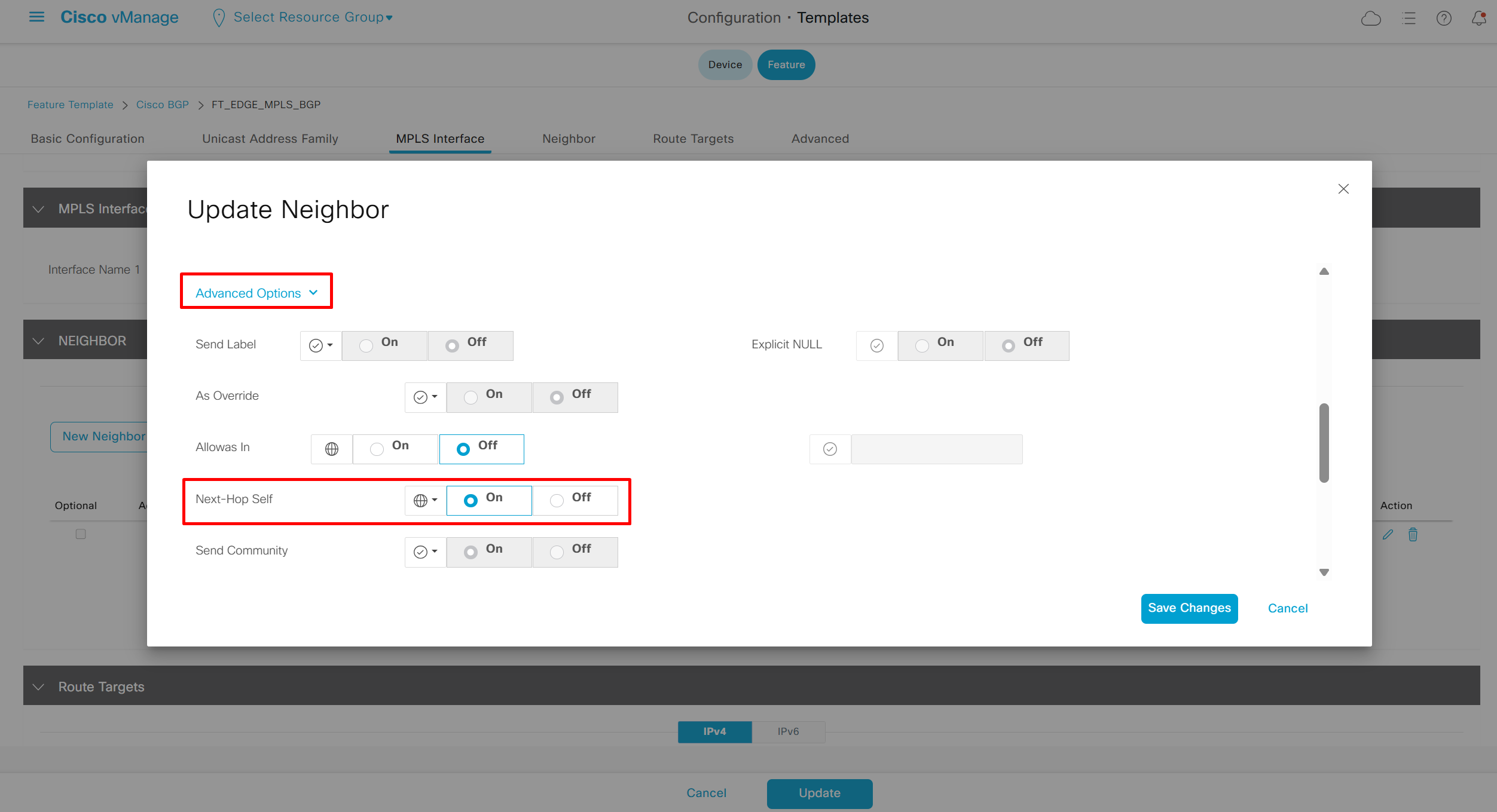
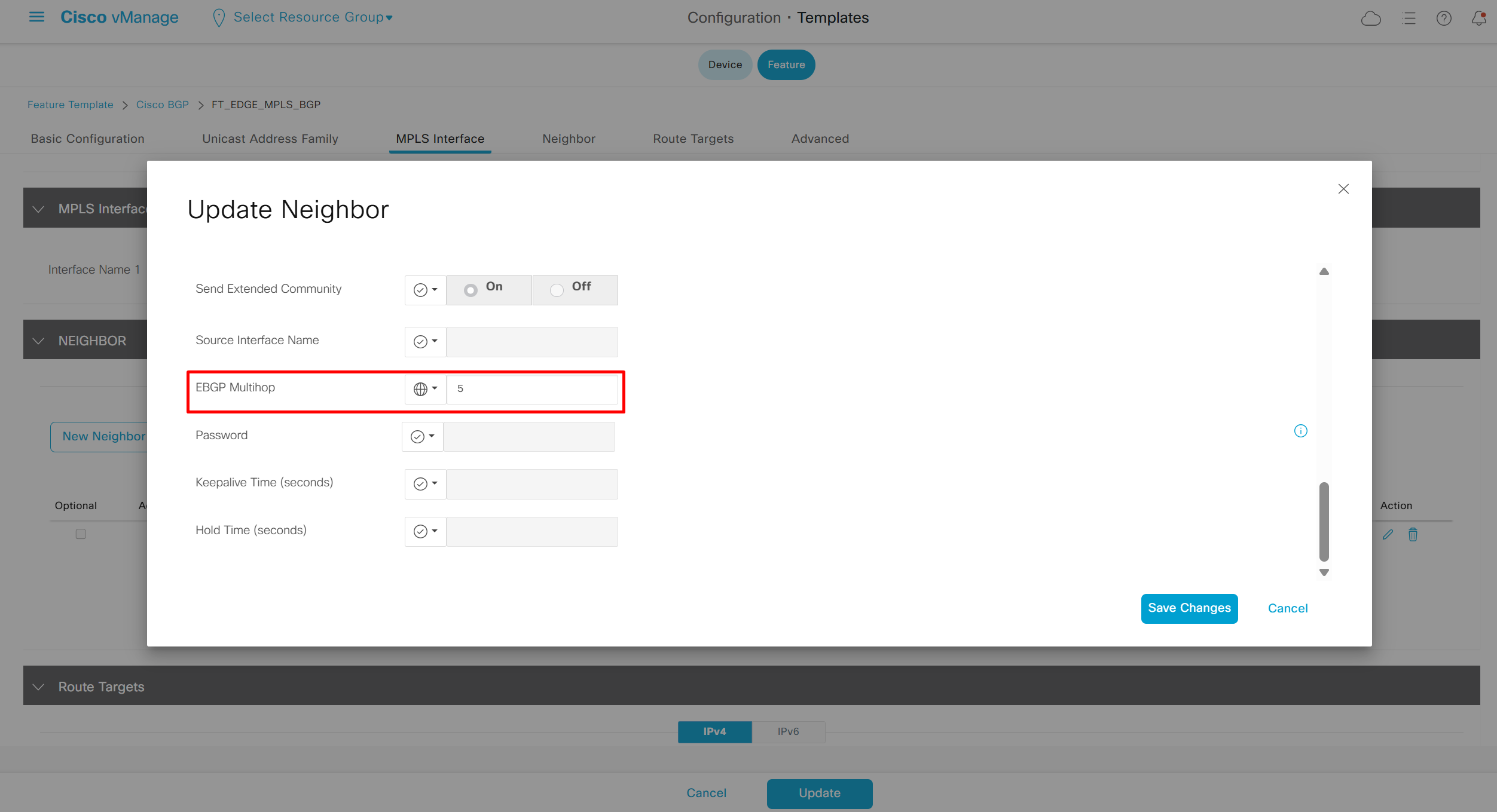
Policy Introduction
in our mind it can be laid out as
Centralized Control policy
Localized Control policy
Centralized Data policy
Localized Data policy
A way to think is
Centralized means that configuration is done on a central location vmanage and then pushed to vsmart (central control plane)
Localized means that configuration will be pushed directly to edge devices
Centralized Control policy (CCP)
Topology
VPN Membership
Centralized Control Topology policy – can be used to match routes and change it any way we like – for example we can use Topology Policy or centralized policy to prevent certain sites from reaching a certain subnet from central view of vsmart – if we think topology means that we are dealing with topology (Top view of network in OMP language – just like OSPF also does) and that view can be manipulated for certain routers so they do not reach certain subnets – it is not just used for filtering but also used for changing route’s next hop TLOC, or to change TLOC preference (from centralized view of vsmart) to prefer one tunnel / route over another – not part of the config instead as routes
Centralized Control VPN Membership policy – this is used to take a site from participating in a certain service / VPN
Centralized Control policies result in – routes, all edge devices see are resulting routes that are pushed to them by vsmart
Centralized Control policy can be applied inbound or outbound to vsmart
Inbound applied to vSmart will apply on all the routes – as inbound direction is vsmart
Outbound applied from vsmart will apply to a specific edge or group of edges – as outbound is always towards one edge or group of edges
Localized Control policy (LCP)
strictly deals with BGP and OSPF protocols local to the edge, turning on OSPF / BGP and redistribution is “turned on” only in feature templates, for applying route map and actions we need to configure localized control policy – becomes part of config
Centralized Data policy (CDP)
Centralized Data policy do not become part of config instead they are added to wan edge’s memory but not in the configuration
Deals with manipulation of actual data packets, it works by “matching” actual “packets” using ACL such as L3 and L4 header information, packets can also be matched using AVC or application visibility feature on edge and not just L3 – L4 information, after matching actions can be to either permit or deny packets just like normal ACL, QoS, we can send copy of the packet using cFlowd or event NAT (used in local DIA circuit) but because this is Centralized Data Policy this is all central vsmart perspective, NAT in a Centralized Data policy can do NAT for either traffic going out over Transport (DIA) known as Transport side NAT or NAT for traffic going towards service VPN (towards LAN on overlay) also called Service Side NAT
using Centralized Data policy we can also override next hop TLOC just like PBR also known as Traffic Data policy
AAR is also part of the Centralized Data policy and it keeps track of tunnel’s health such as Latency, Loss and Jitter (LLJ)
Zone Based Firewall, this is also part of the Centralized Data Policy, because it is Centralized Policy, it is from vSmart’s perspective and all those Centralized policies are pushed to vmanage -> vsmart and then passed as a policy in “WAN edge memory” but not in the wan edge’s config
Localized Data policy (LDP)
Localized Data policy is per interface and can do most things Centralized Data policy can do but not all of them
Localized Data policy cannot do Deep packet inspection for matching (can only do L3 / L4 matching), cFlowd, NAT and so on
On the other hand there are some things that can only be done through Localized Data policy such as Traffic shaping, scheduling and rewriting for QoS and Mirroring which are very local things
Configuration for Localized Data policy go on the edge
Because there is an overlap of ACL and QoS in Centralized (not cFlowd and NAT) and Localized policy (Mirroring, scheduling and traffic shaping etc) it is best to use Centralized Data policy first and if things cannot be accomplished using Central then use Localized Data policy
Packet Flow

as Packet moves from Ingress direction to Egress direction, Ingress can be any direction, from overlay (LAN) to transport (VPN) or from transport (VPN) to overlay (LAN)
if you look at the ingress and egress they are same in terms of order of operation but opposite from ingress
NAT > [ ACL > Qos ] <—router—> [ ACL > Qos ] > NAT
Ingress
NAT – Central (Data)
ACL – Localized (Data)
QoS (Classification , Policing) – Localized (Data)
In Chassis, Backplane
Once packet is in chassis and past the ingress interface
packet routing happens and here are three things that can happen
App route – Central (Data) – if an AAR is defined for application, packet matches to be that app, the router has to determine all eligible transports / tunnels over which this app “can be routed”. This is done using BFD performance of the tunnels
Data Policy – Central (Data) – If a packet matches a data policy from CDP this includes all (ACL/QoS/cFlowd/NAT/PBR/ZBFW) then packet will follow the action from CDP, for example if packet is matched by Data policy then it will even override previously matched AAR policy – this can happen when we have same packet matching criteria defined in both AAR and Data policy
OMP Routes – Central (Control) – If packet is not matched by either AAR Policy (CDP) or Data Policy (CDP) then packets will be routed based on routing table, packet could be routed to VPN (using OMP route) or could even be routed back to service side again (using local BGP or OSPF or static route) because routing table is being consulted
Egress
ZBFW
ACL – Local (Data)
QoS (Shaping , Policing , Scheduling / Shaping , Rewrite) – Local (Data)
NAT – Central (Data)
Local Control – Local Control Policy (BGP – Service Side)
BGP Route filter
172.16.0.0/24 le 32
10.0.0.0/16 le 30
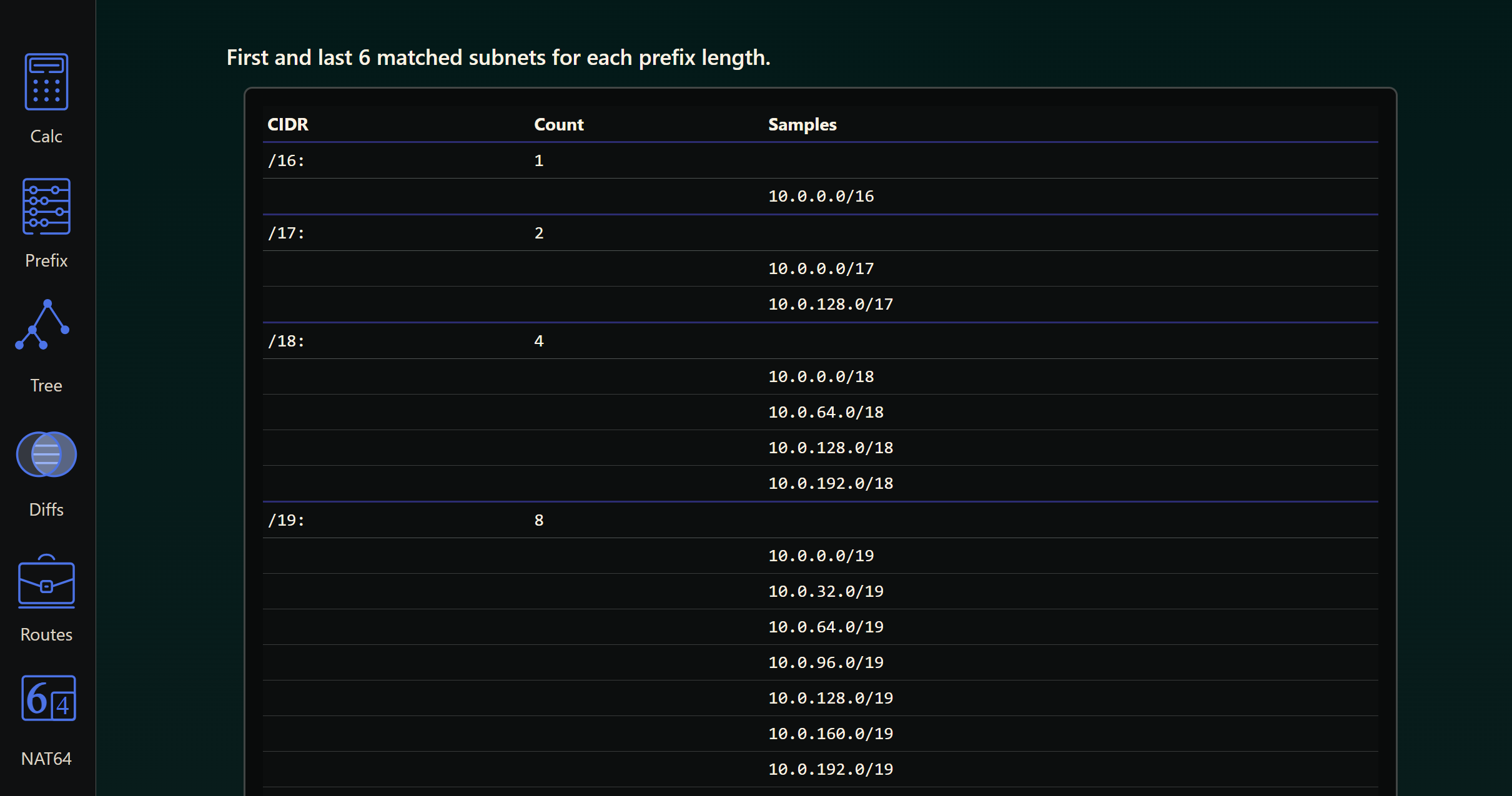
102.102.102.102/32
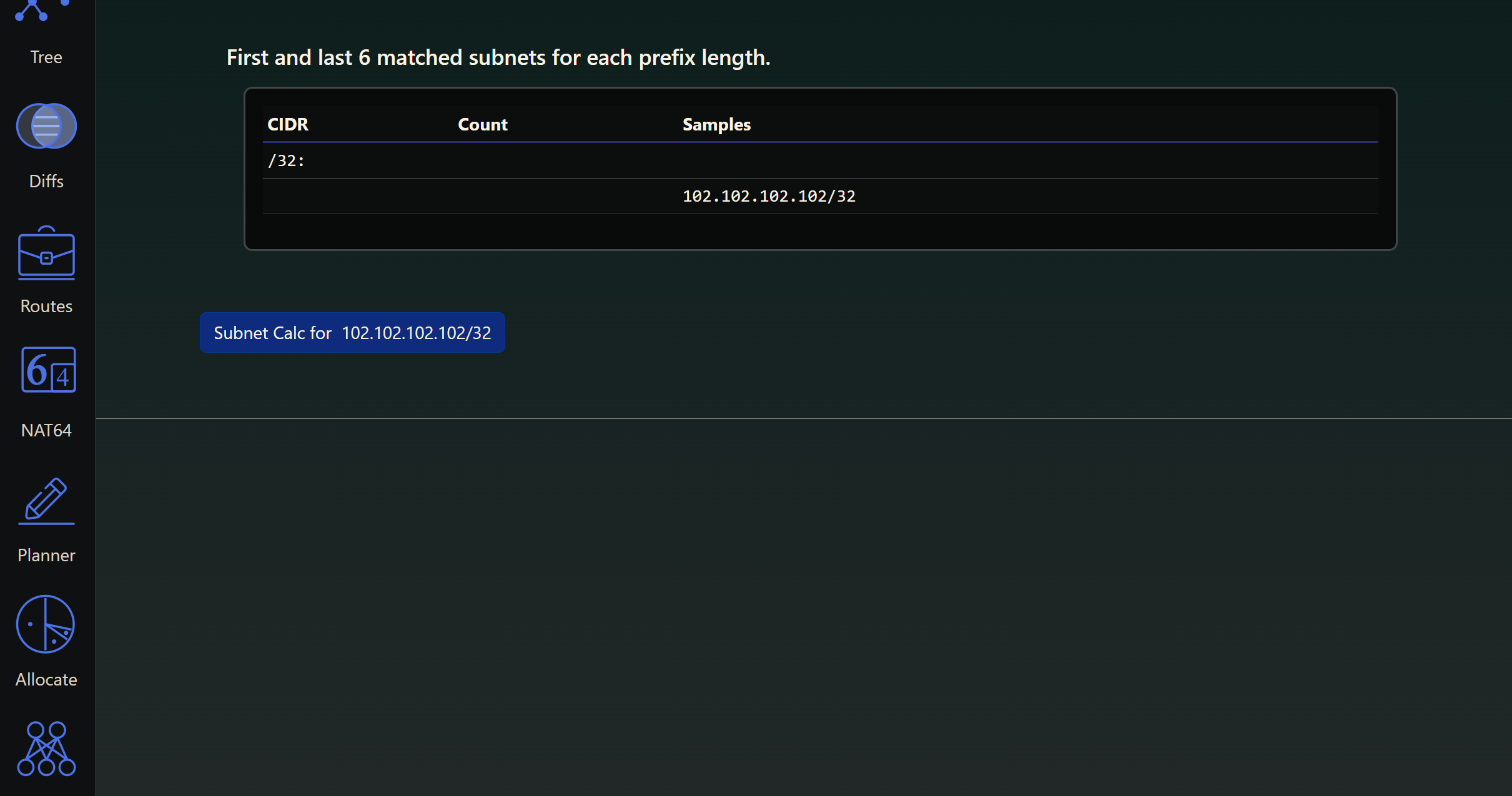
because we want to capture all those routes
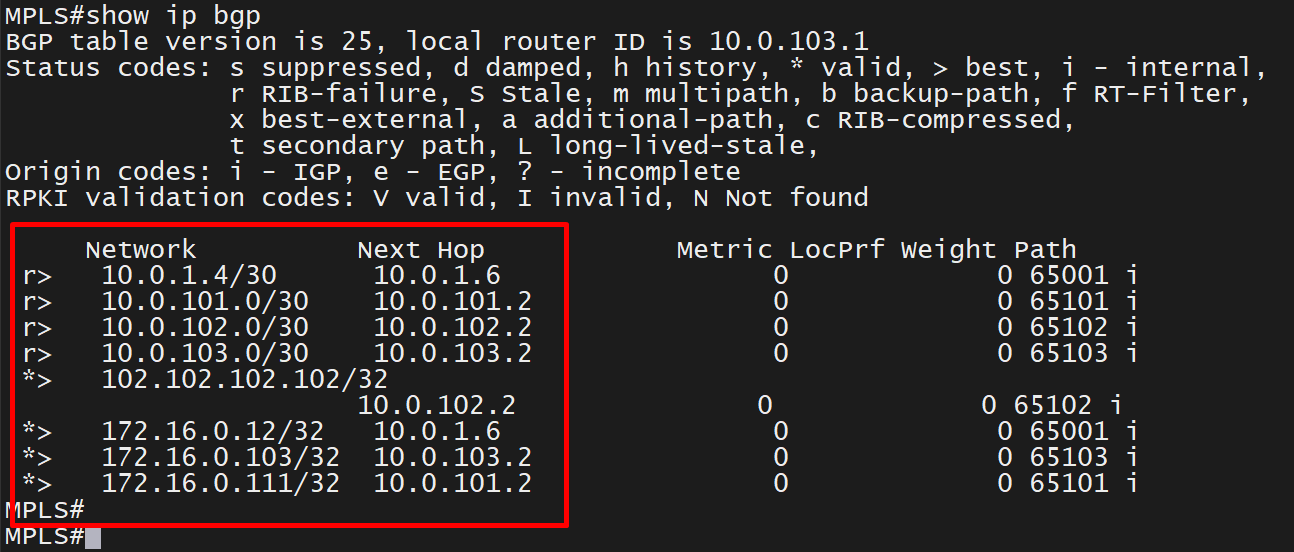
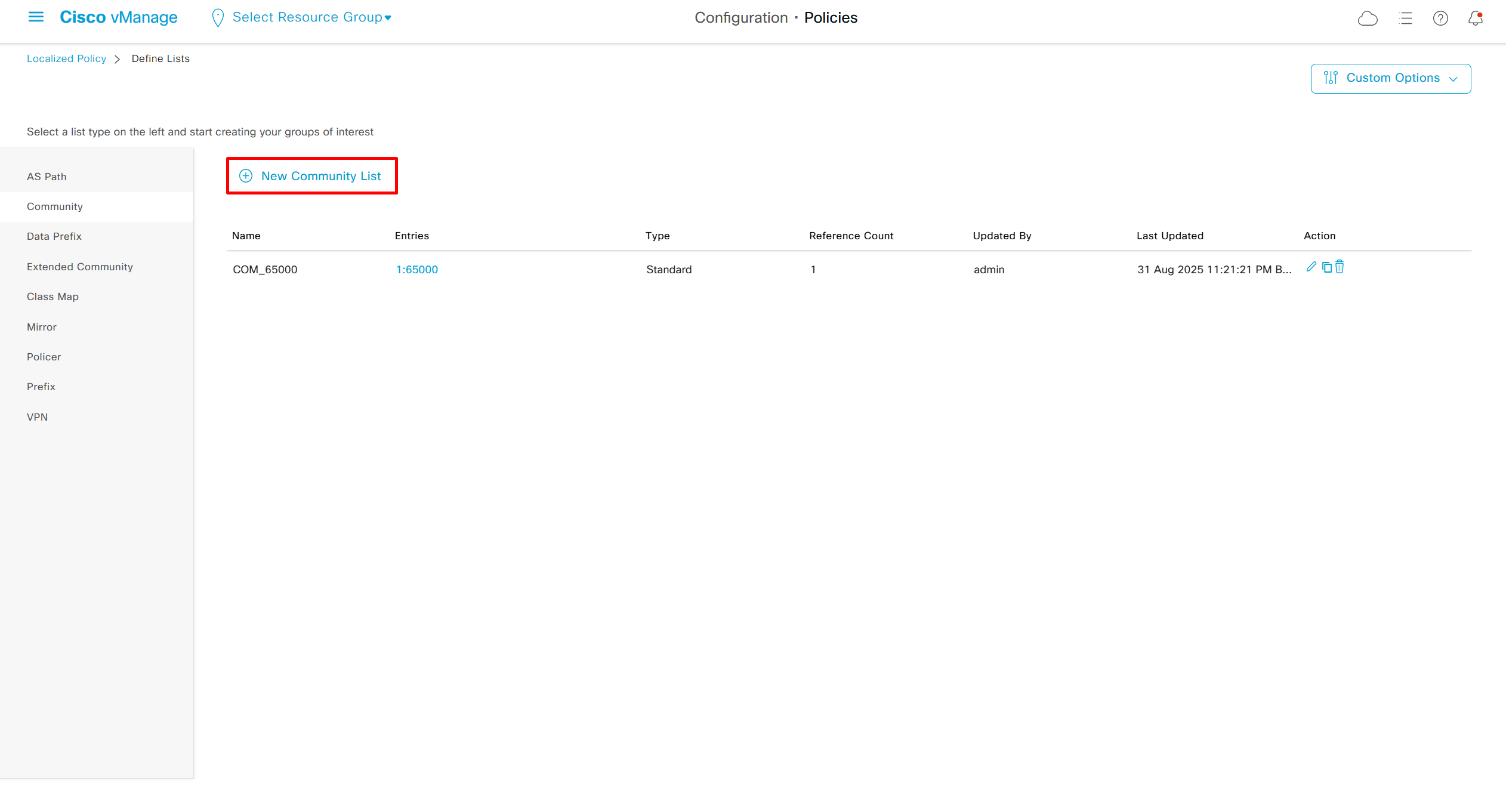
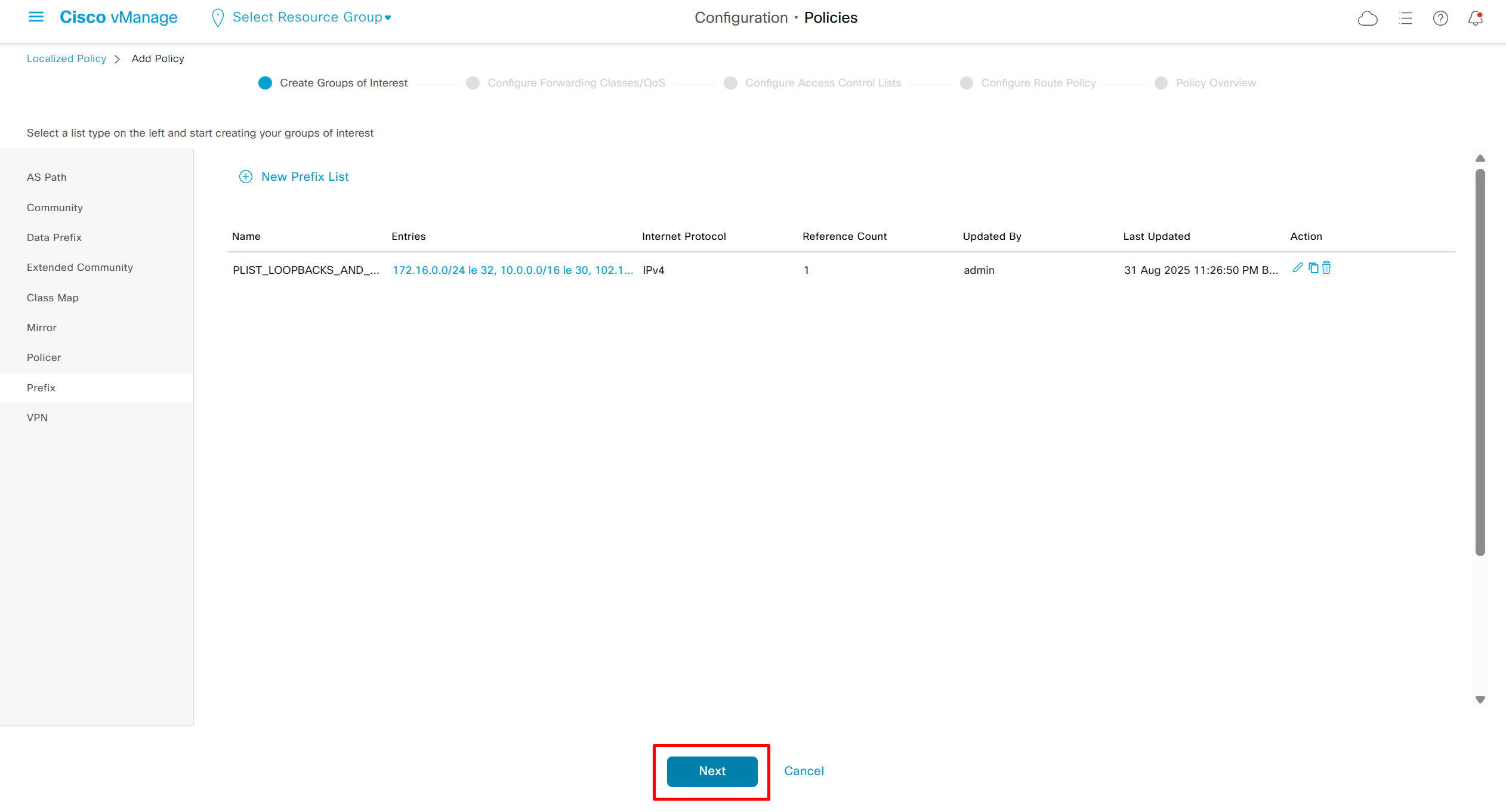
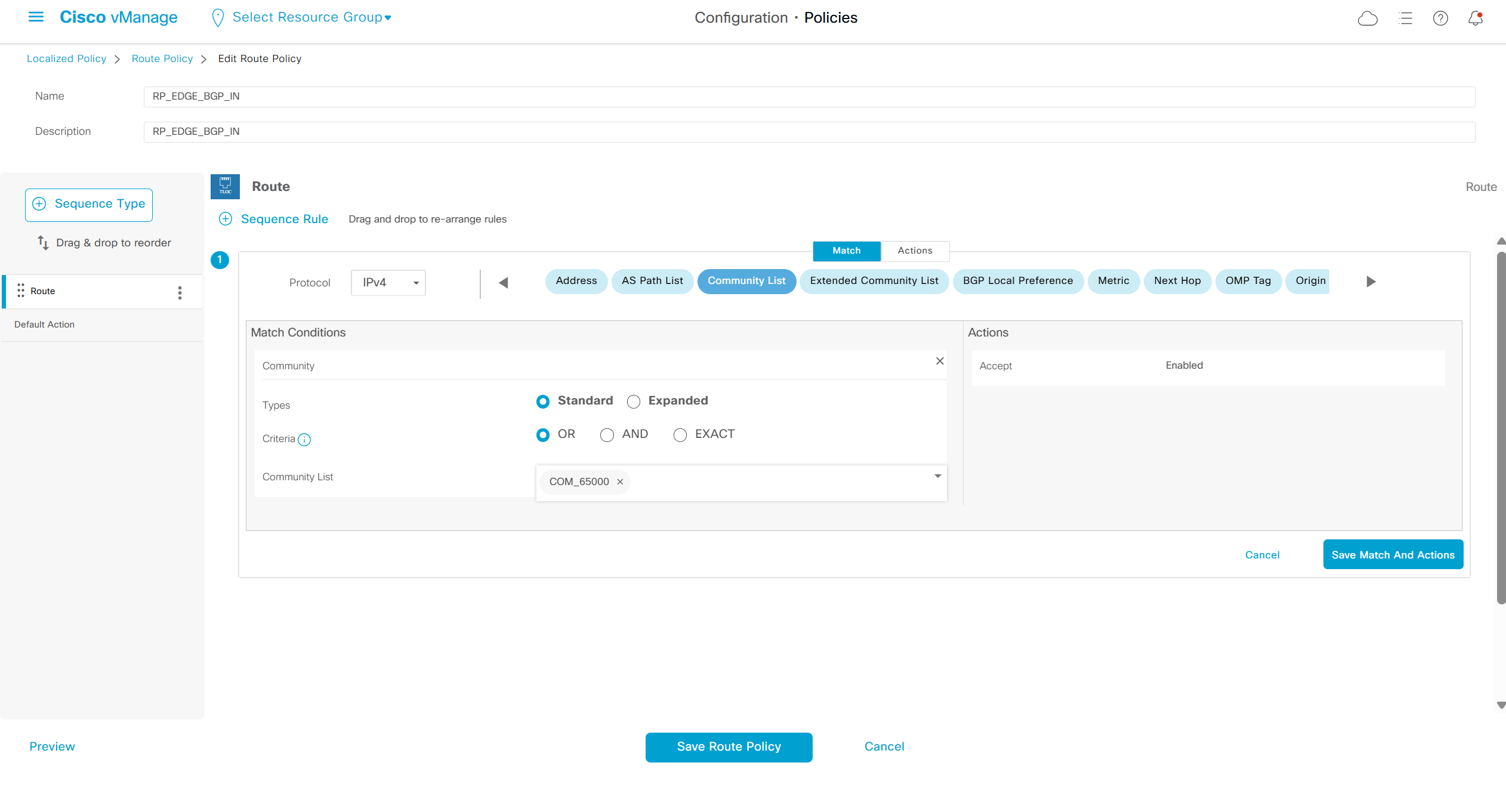
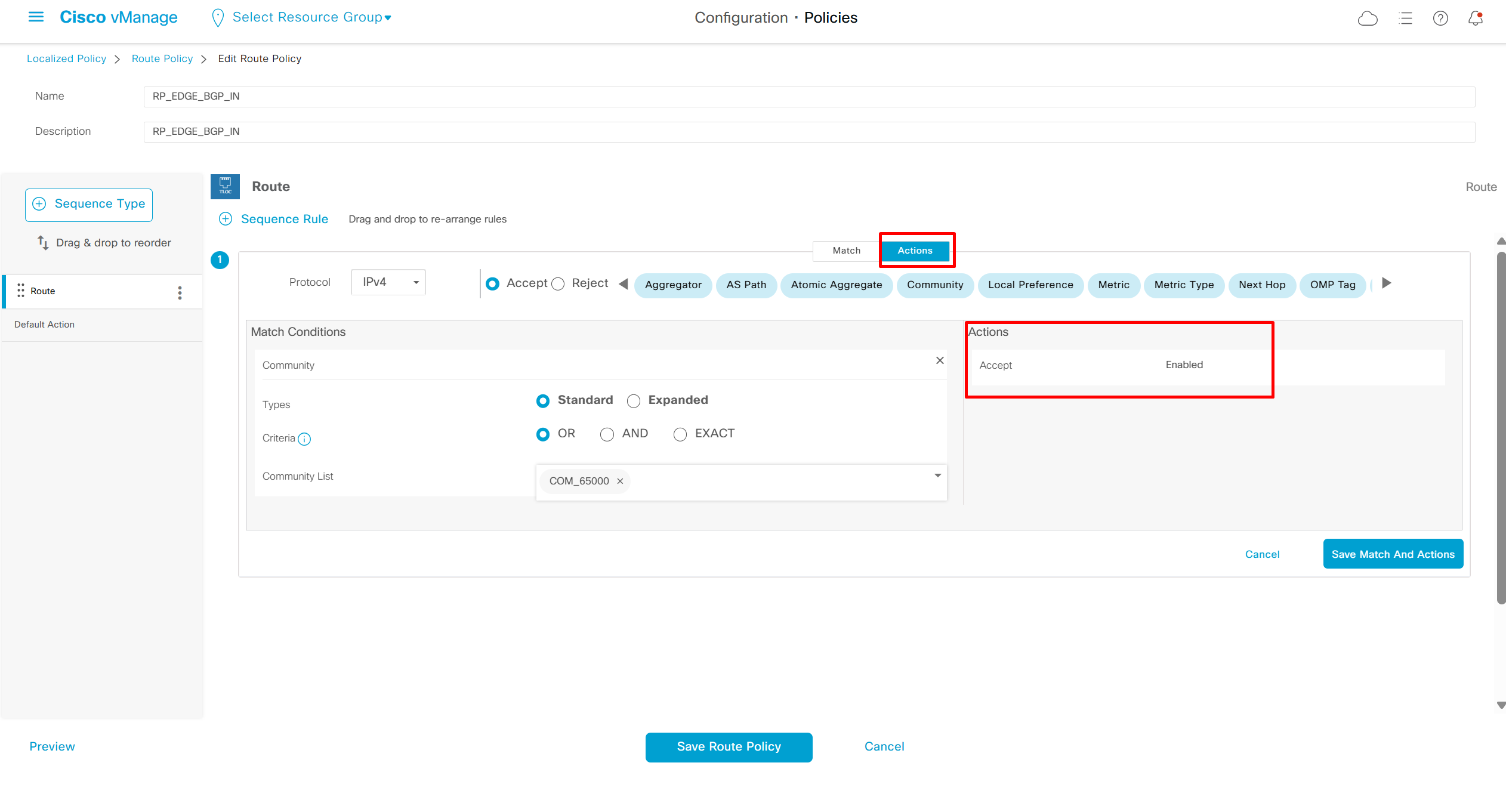
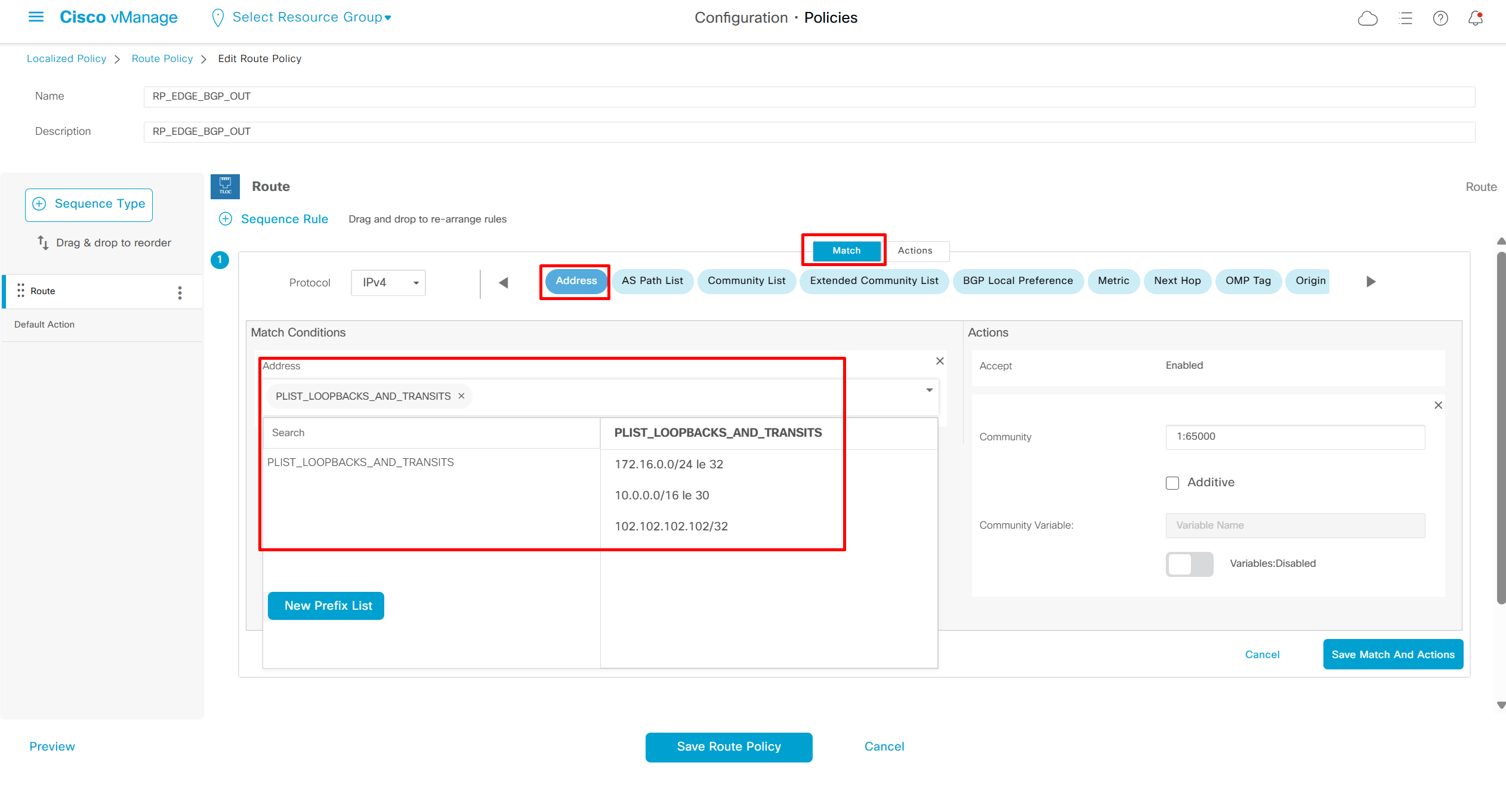
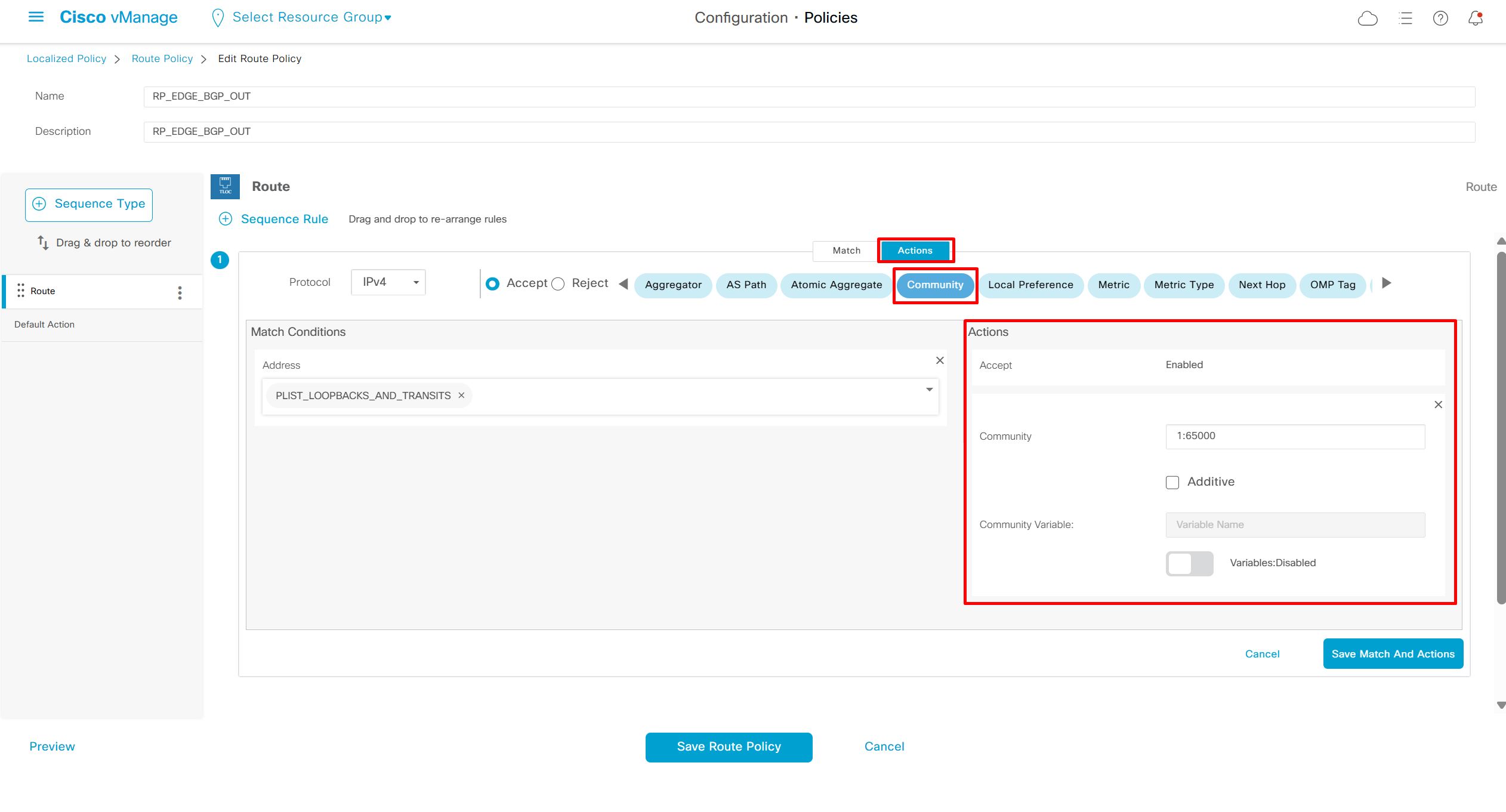
This was just policy definition
Now we need to first download this LCP policy on the routers before it can be applied on the neighbor
Local Control policy LCP is downloaded
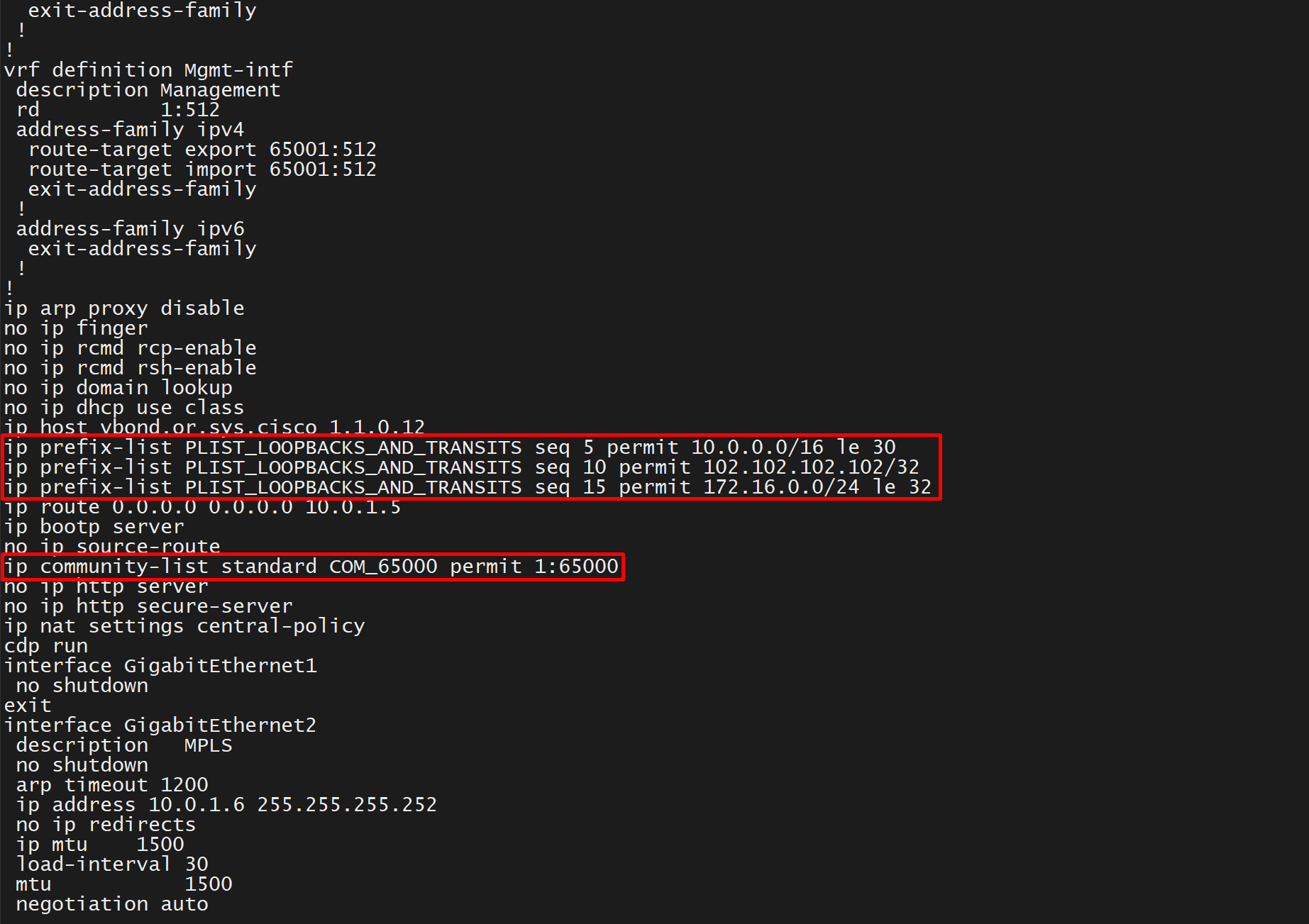
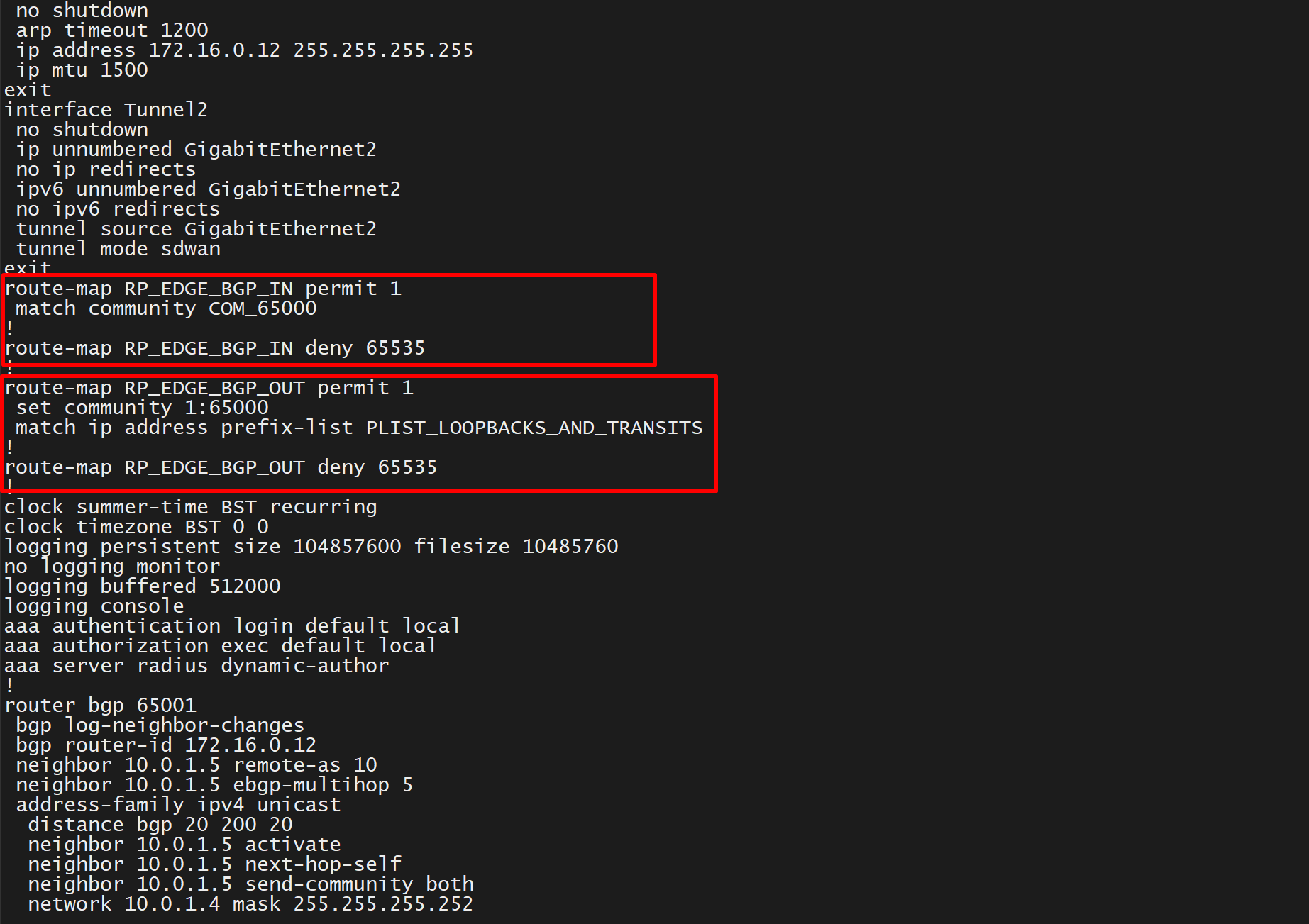
if LCP is not pushed to the edge device and if route policy is used then we can get this deployment error
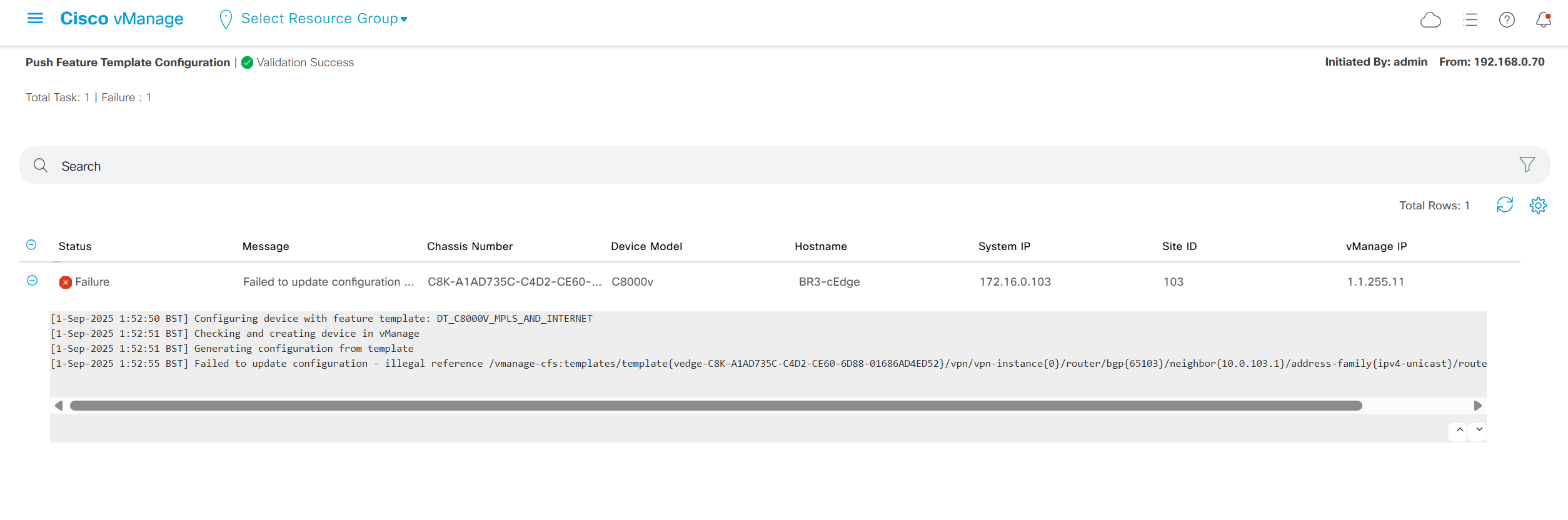
Now we need to assign it to BGP neighbors
We need to be careful when assigning the policy because there is no dropdown and you have to paste the name of route policy
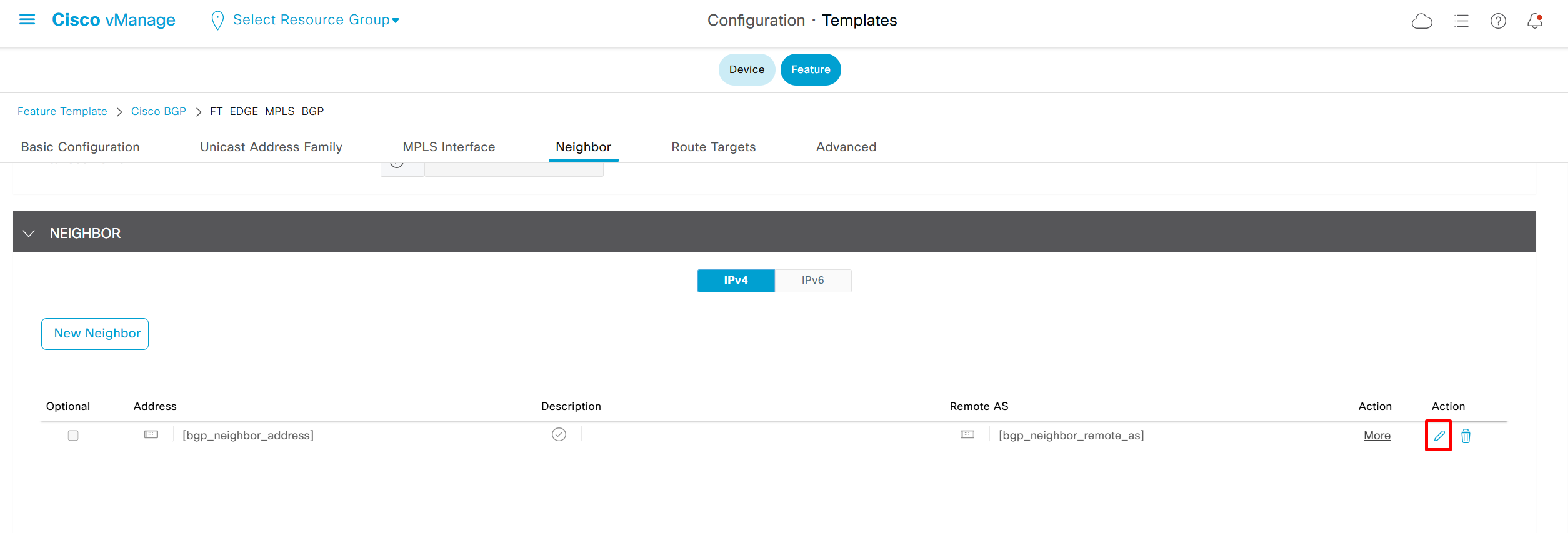
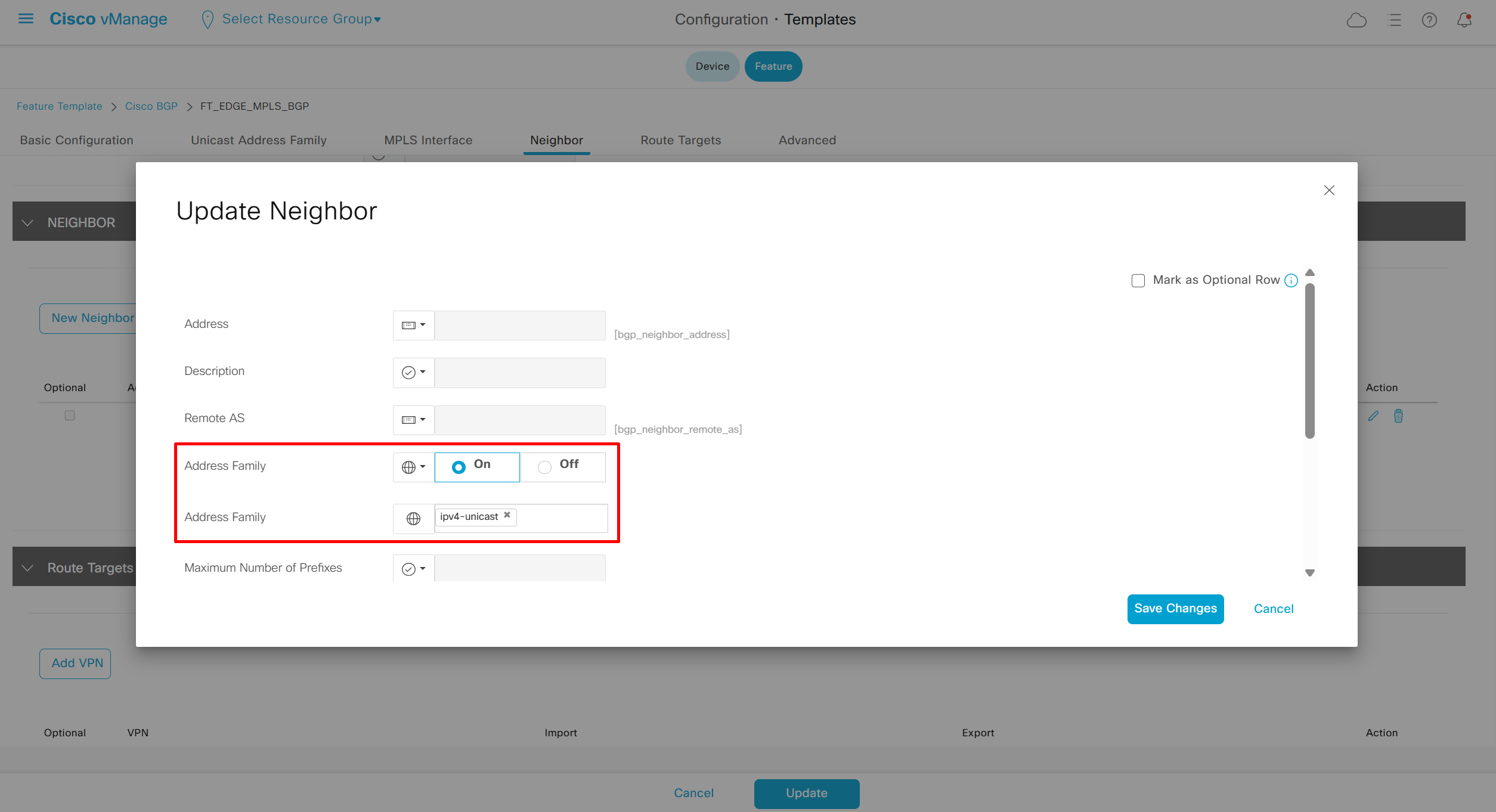
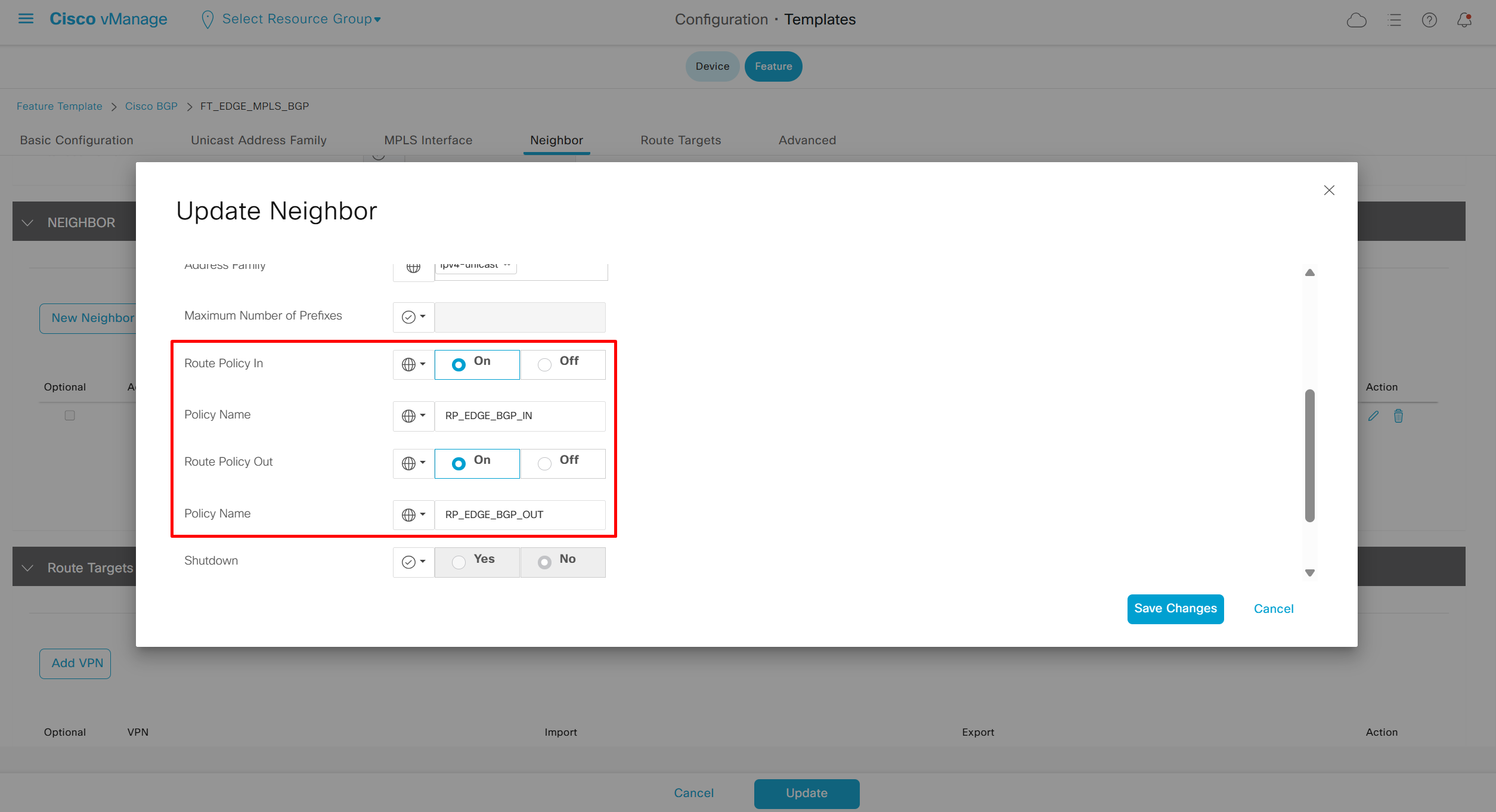
We can see community tagged on route
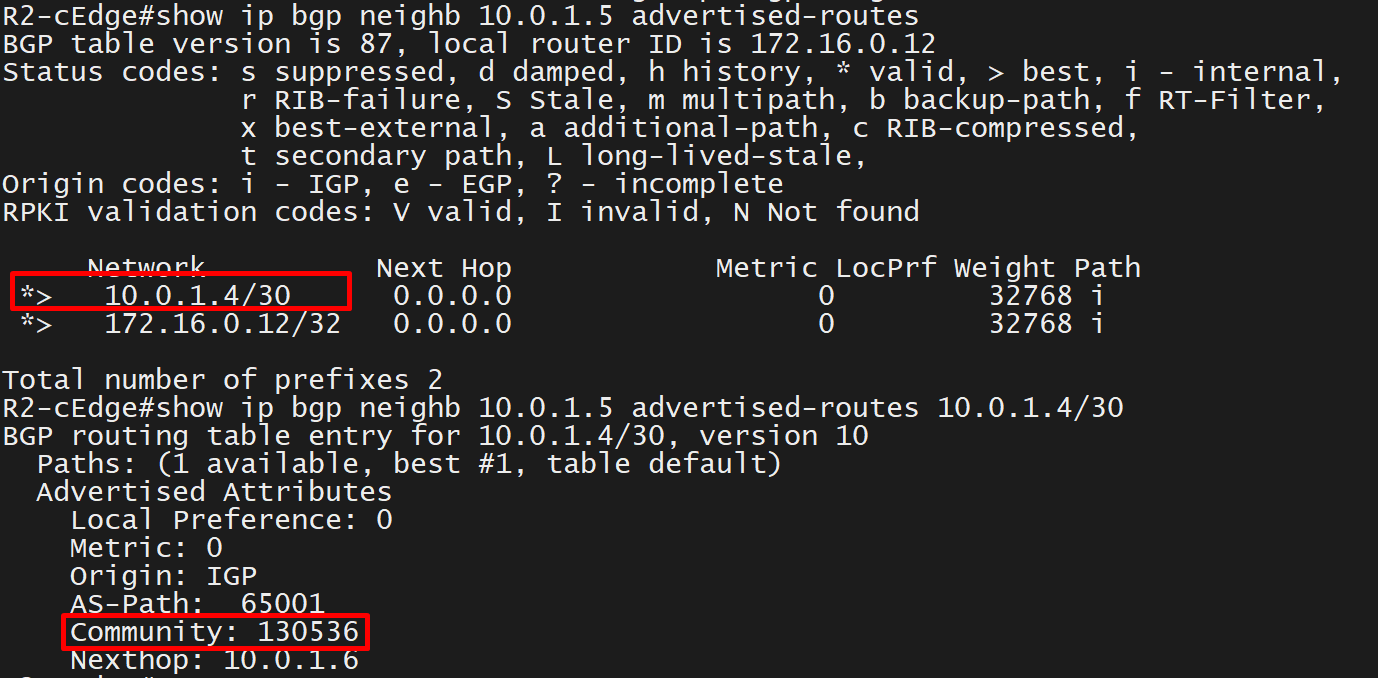
next post
SDA LM 1 – Initial Configuration & Setup
Videos
SDA – LISP and Routing introduction
Fabric spans from top of the border nodes (could be routers or switches) and down to the edge switches
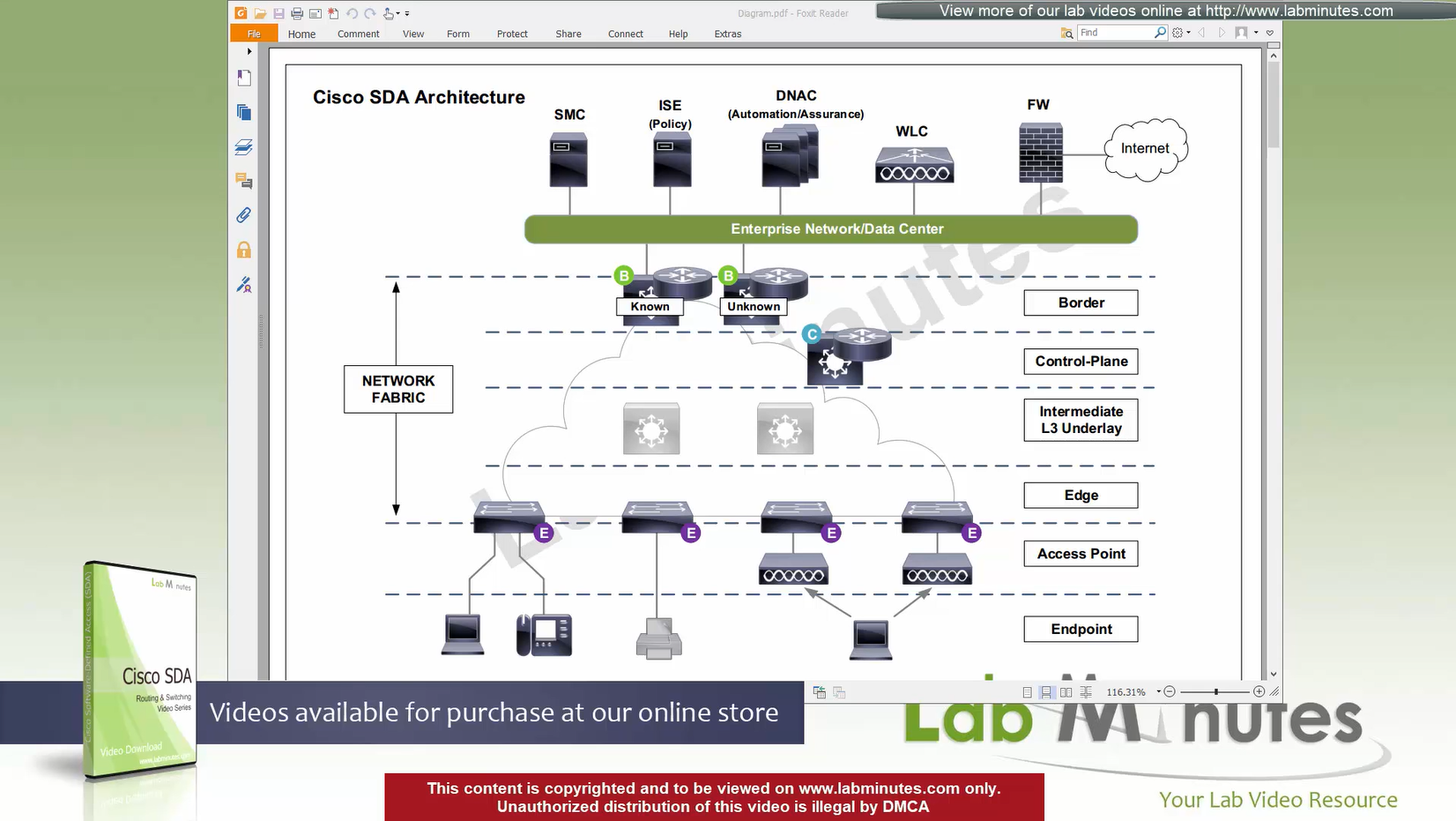
VXLAN (tunnel packets) routed across the point to point L3 (underlay)
Edge and border run L3 eliminating L2
Underlay routing is there for learning loopbacks on all switches in the domain
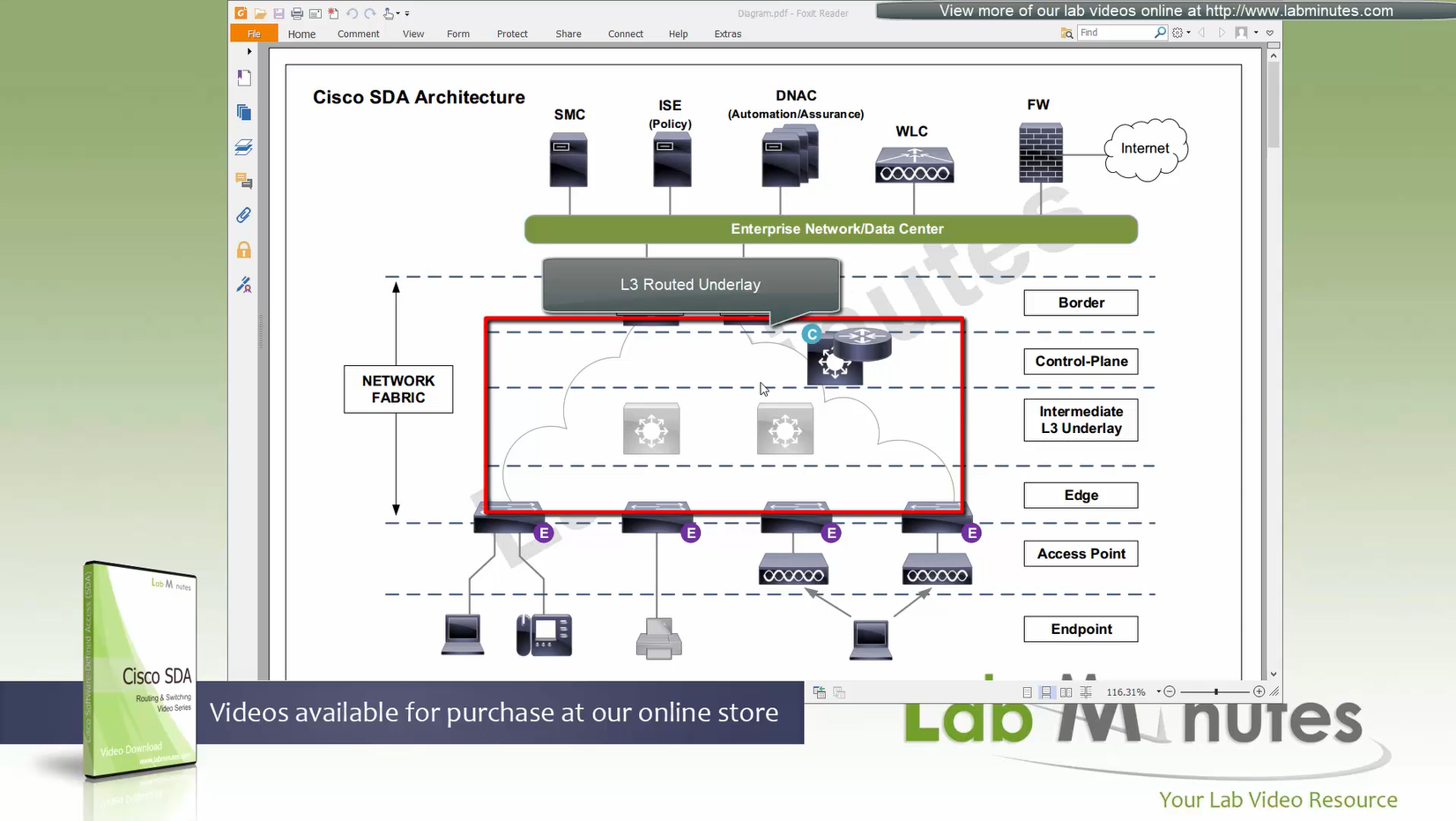
Client data can be vlan tagged or untagged
Edge switches once receive data from clients, if destination of the packet or frame is on another switch
or to outside world via border node then VXLAN encapsulation (tunnel) is created to other switch or border node
“Stretched” Layer 2 means that a client can roam from one location to another keeping their original IP address and L2 domain,
same subnets (SVIs and also vlans) are available in all edge switches for both wired and wireless
so we can say that SDA does L2 stretch within the fabric site by default
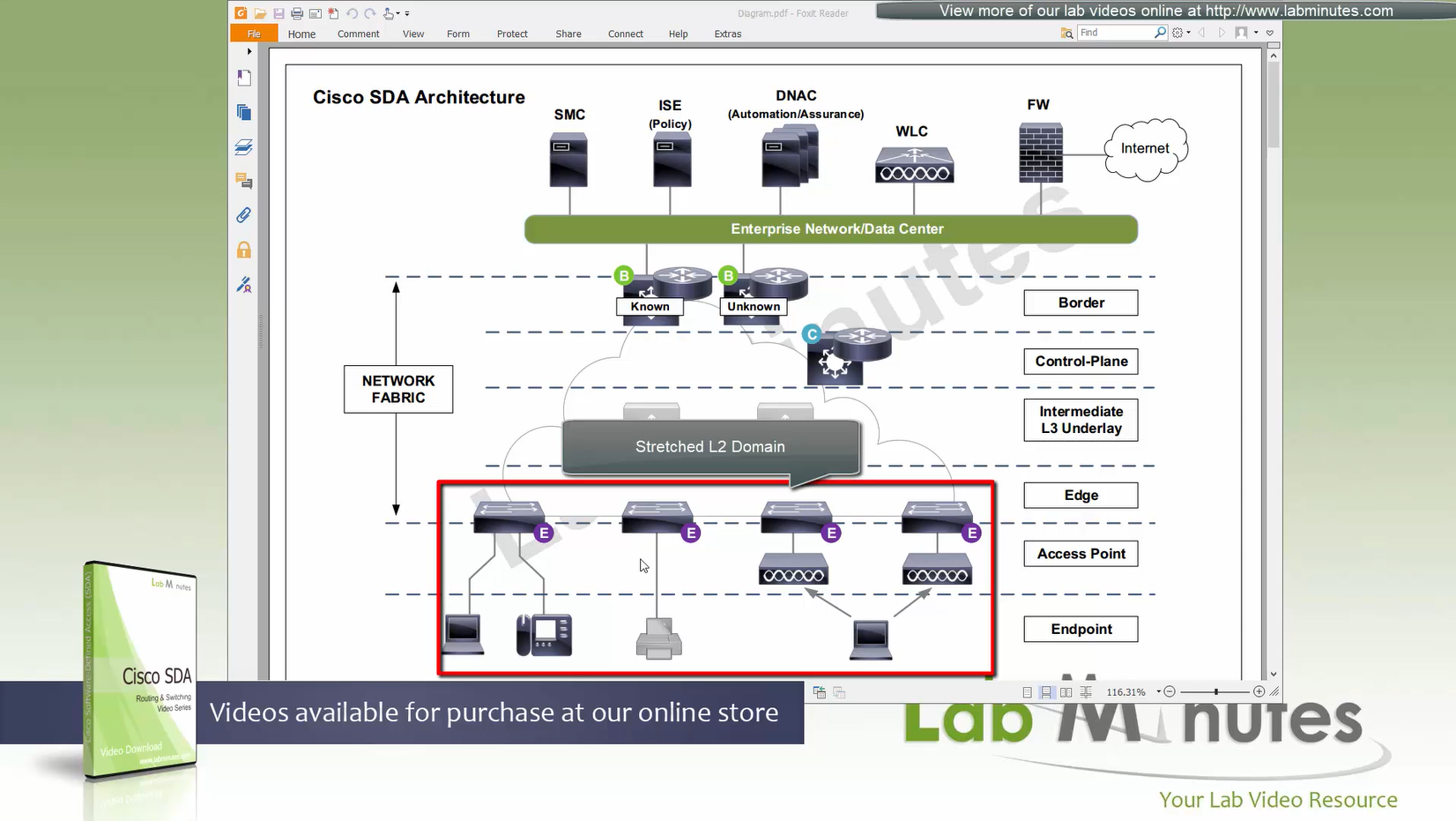
Network segmentation (different virtual networks) or Micro segmentation (using SGT tags and TrustSec)
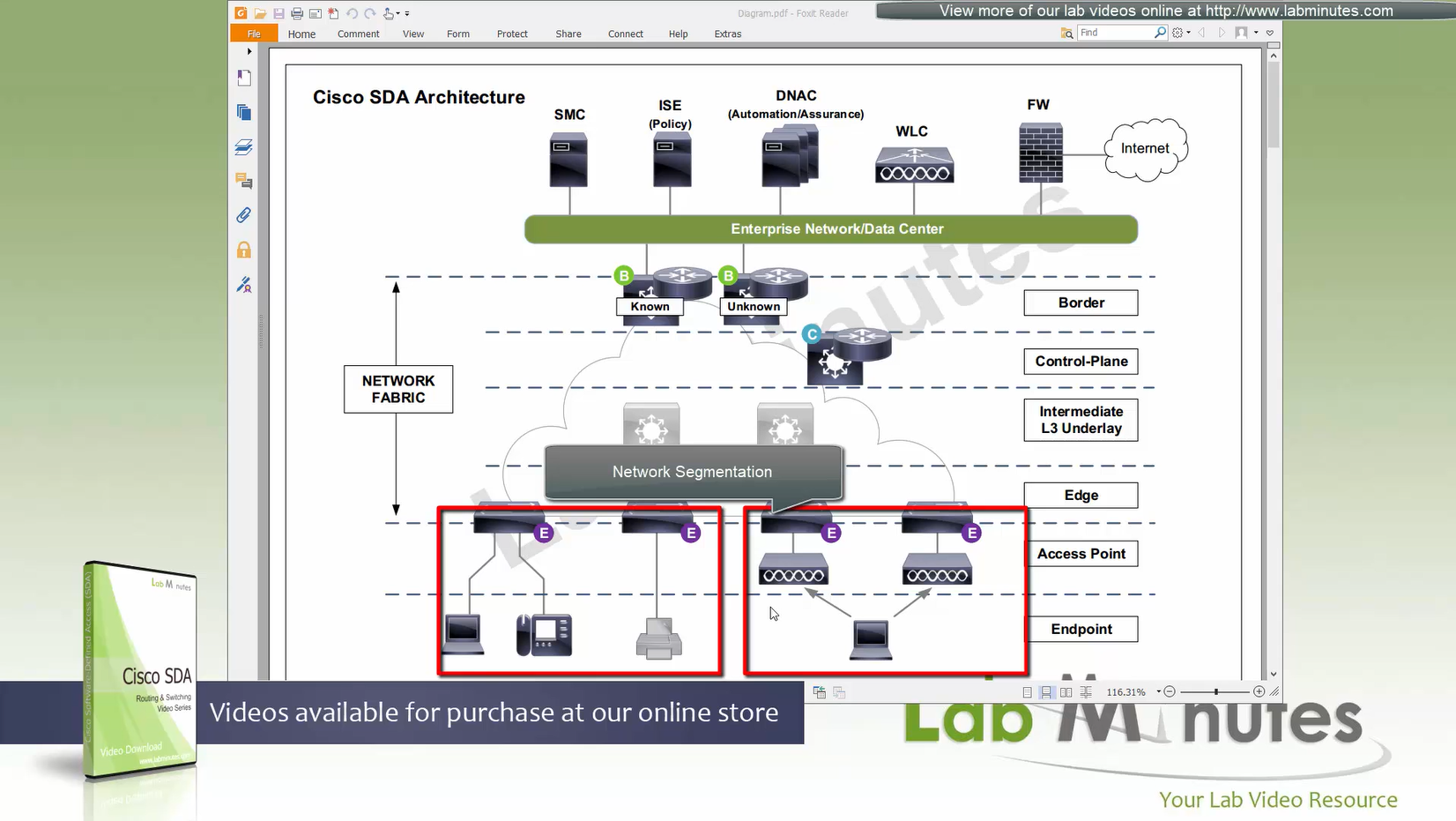
You can also have “Fabric” enabled WLC and AP, this makes wireless clients consistent policy wise in DNAC same as wired clients policies
Edge nodes detect the endpoints and updates the control plane about endpoints detected
Edge nodes are also responsible for VXLAN encapsulation and decapsulation
Control plane node is the brains of the Fabric and provides “Endpoint to Location mapping” to the edge nodes and border nodes using LISP
in following format:
Ethernet mac address of a PC -> behind this loopback (switch)
/32 IP address of a PC -> behind this loopback (switch)
Control plane node(s) is LISP Map Server (input of endpoint entries) and LISP Map Resolver (resolves them for edge switches like a DNS server – returns the loopback IP of the switch)
VXLAN can carry both Layer 2 frames and also Layer 3 packets also
Control plane node needs to be deployed with redundancy
Control plane nodes dont need to be in the data path, in most deployments this role lives on same device as border nodes.
Border node and control plane node should be deployed in pair (2x) to have redundancy in the network
Border and control nodes are usually combined on single physical device then there should be 2 of those devices in the network
Fabric border node – acts as a gateway to fabric world
Network traffic from Fabric will need to leave the fabric border node to access the rest of the enterprise network and internet
border node peers with external networks via Fusion router and advertise Fabric to fusion and also redistribute external networks into fabric.
Any external routes learned will be registered with control plane “so that those external destinations are reachable by fabric”
By virtue of control plane node “these external routes will be available to edge nodes once registered” and access those destinations.
When packets from edge needs to go out, edge queries the control plane and control plane needs to have that routes information, which will have edge make tunnels to the border node, same logic is for edge to edge packet / frame sending between hosts connected to edge nodes.
so control plane is consulted if any packets need to leave for destination other than local switch
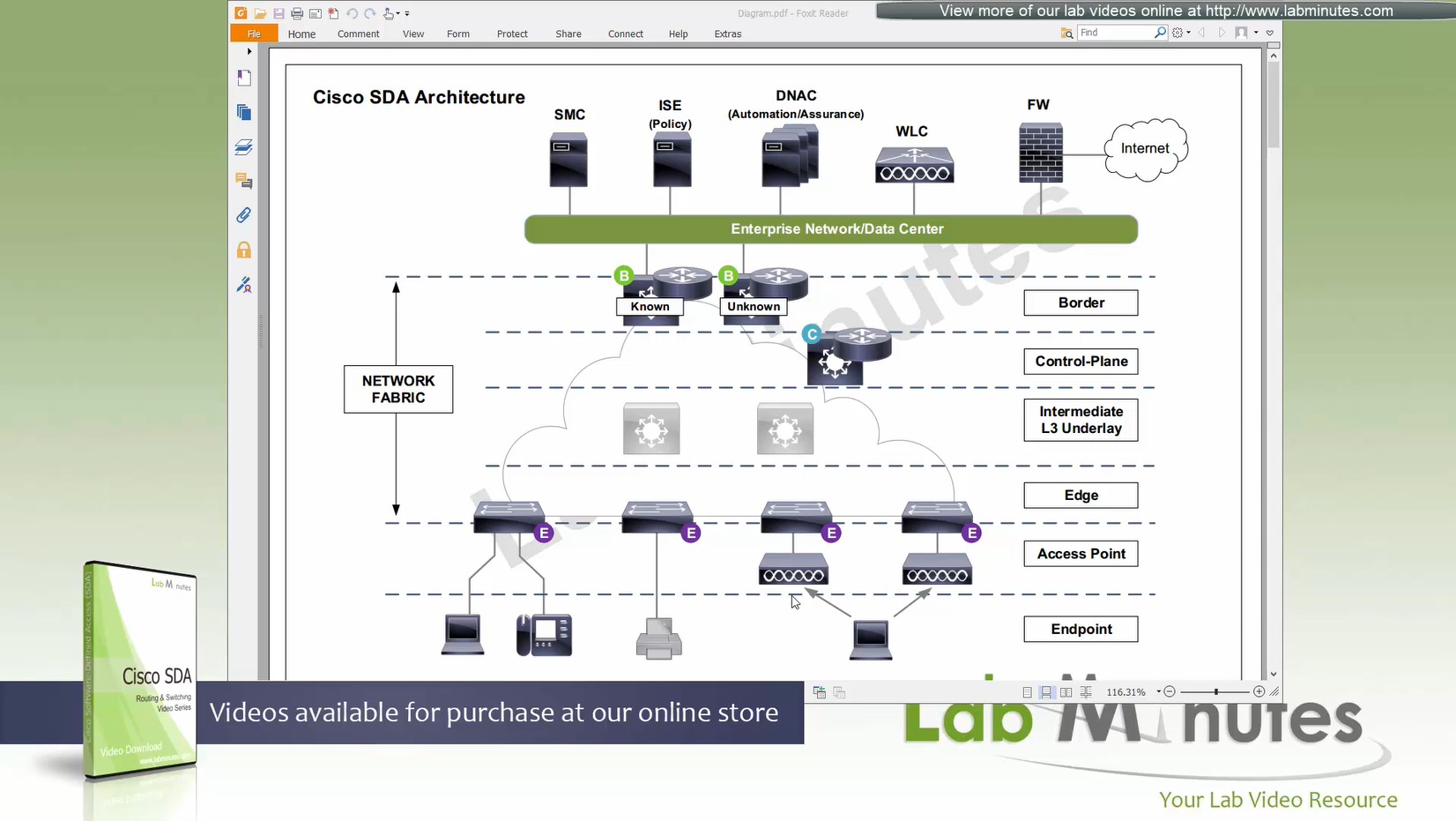
There are 2 types of border nodes
1. Known Border Node
2. “Default Border Node” or “Unknown Border Node”
Border node is for destinations that are known such as “subnets”, “server vlans” etc
Second type of border node is that deals with unknown routes and is also called Default Border, it is used as a last resort if there is no match to specific routes in Known Border, usually this is traffic for default route or internet,
When edge nodes consult control plane and control plane node does not know about the destination, Control plane answers (vxlan IP) loopback IP of default border node
Both Known Border and Unknown Border can live on same device or two different devices
but in this diagram they are shown to be 2 different devices
Now the role separation goes 2 levels on border
- control plane node
- border node
- known border node
- default border node
Intermediate Underlay device:
Intermediate Underlay devices need to be able to support the “Jumbo frame” and use ISIS
Cisco recommends this intermediate devices to participate ISIS (shortest path) with redundant links and there should be no spanning-tree or layer 2 in the “Fabric”.
Underlay Intermediate device has layer 3 interfaces and no spanning-tree or L2 port channels. Intermediate nodes are required to aggregate all the access edge nodes into something and then connect into border switch or router, direct connections to border are supported but should not be done for larger site due to scalability issues
“Fabric mode WLCs” still manages the AP and maintains client connection information also but like edge node
Fabric mode WLC reports to control plane node and lets it know about the client – this the main thing
communicates associations and communicates roamings to control plane, controller sits outside of the fabric and APs sit inside the fabric but at the host connection layer on the edge nodes
WLC can be connected outside the fabric as long as it has reachability to the border and control and APs
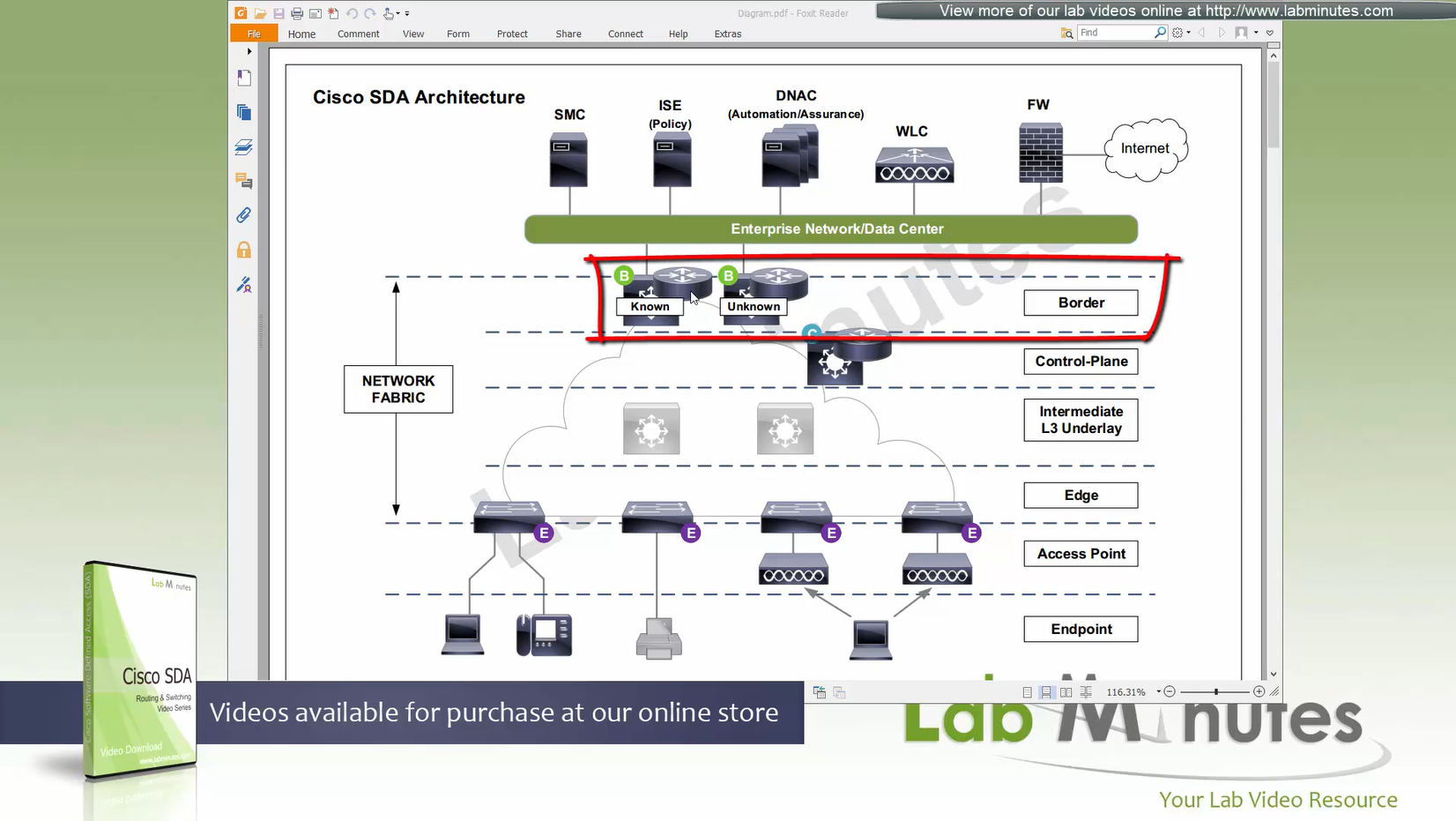
Fabric mode AP, there is one major difference from local mode AP, (Data tunnel) they will not send data to WLC for it to be centrally switched but exit data locally on the fabric via VXLAN tunnel > edge switch
Fabric AP participates in VXLAN encapsulation however they maintain CAPWAP tunnel (Control tunnel only) to the WLC at the same time,
so WLC can learn about the clients and relay same info to the control plane node
This allows wireless clients to be treated within the same system and policies of the fabric.
AP <–CAPWAP CONTROL–> WLC <–LISP–> Control node
AP <–VXLAN–> edge node
AP must connect to edge node “directly”, there should be no switches in between AP and Edge node
So WLC sites outside the fabric or Fabric border node and APs sits directly under the edge nodes
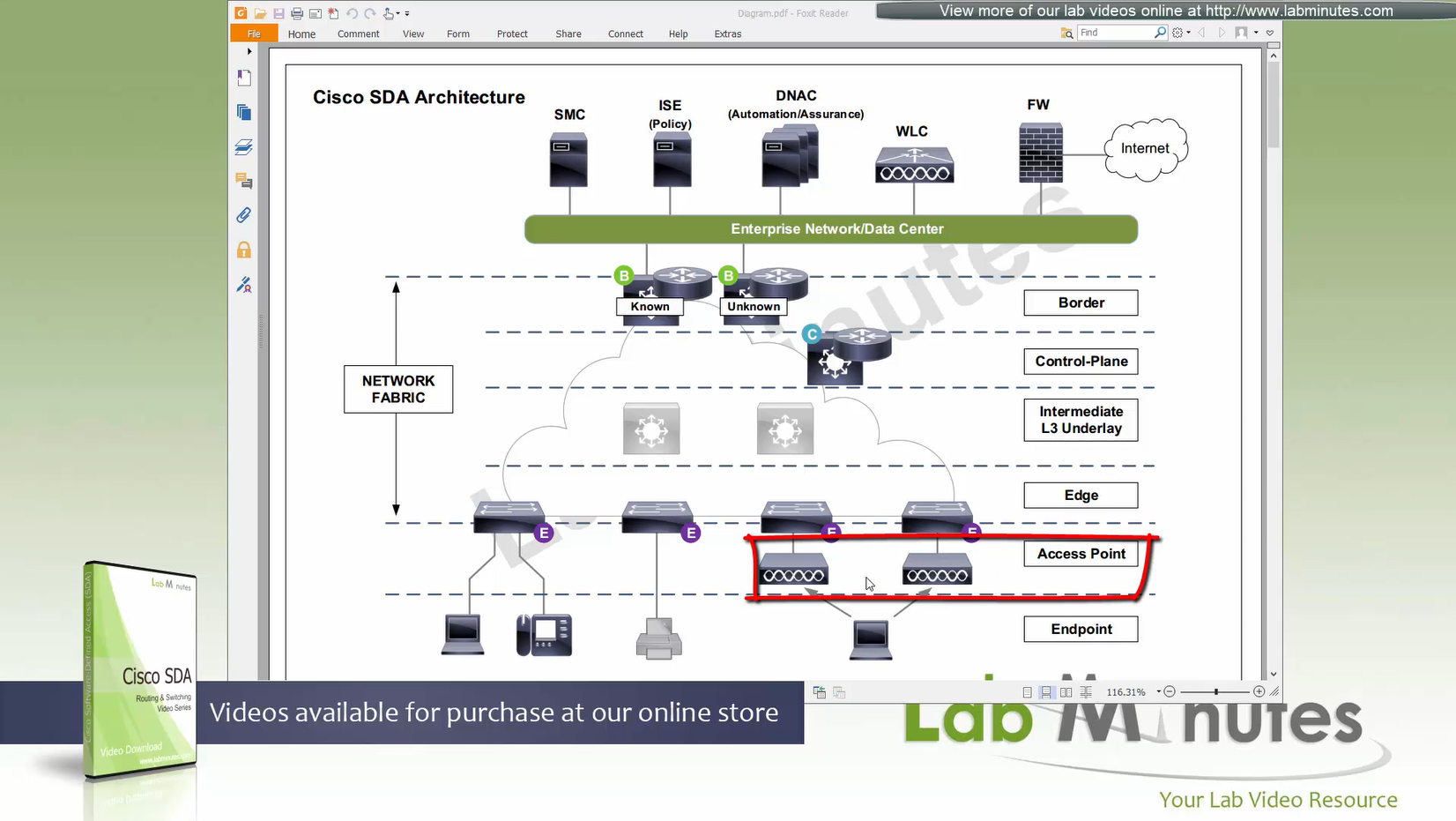
because Access points connect to edge nodes directly clients are connected like
Client <–Wireless–> AP <–VXLAN–> Edge node
DNAC
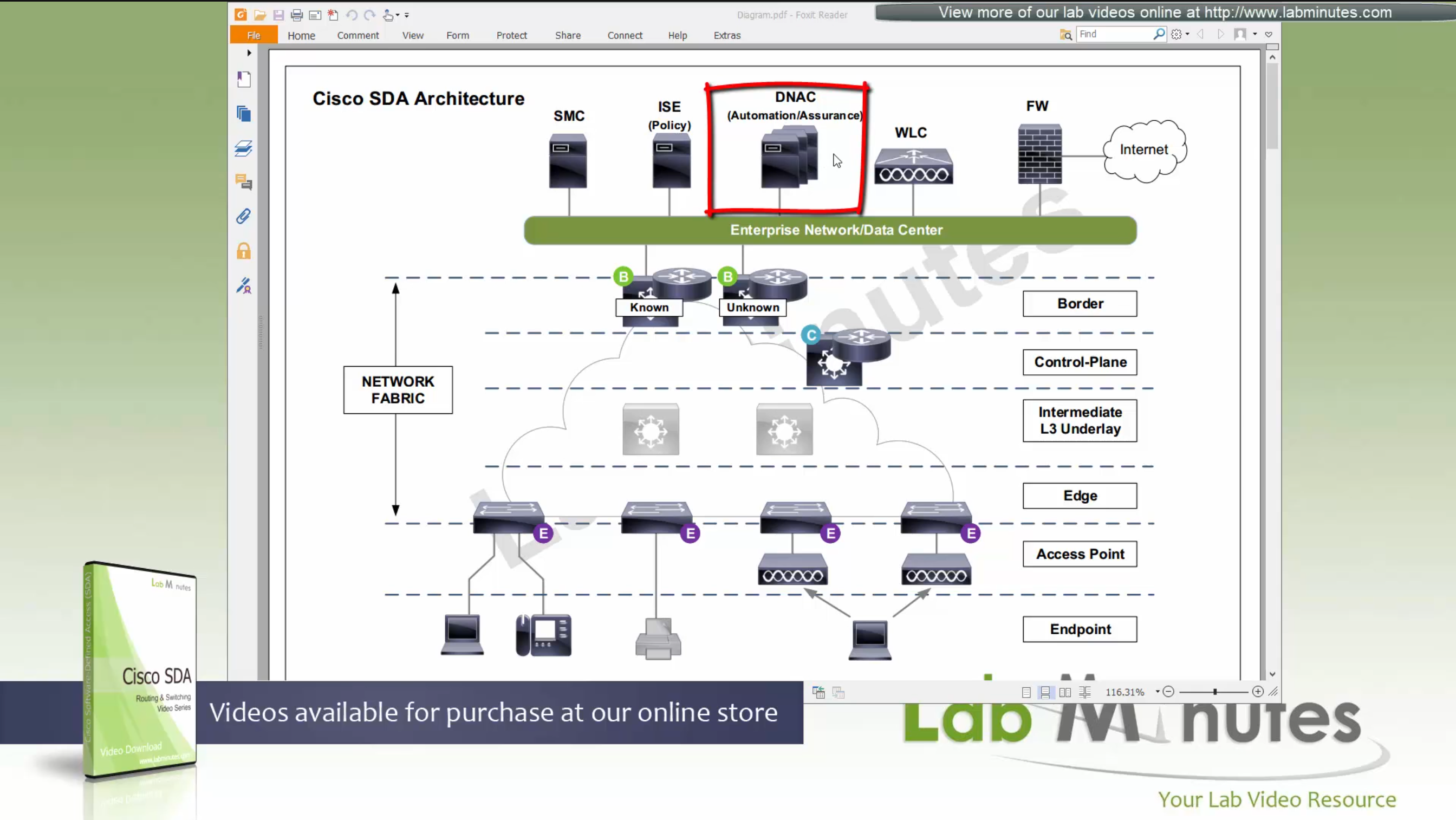
ISE maintains the security policy and contains Authentication / Authorization policy and also TrustSec related components
DNAC uses APIs to push configuration to ISE for SGT but ISE is separately managed
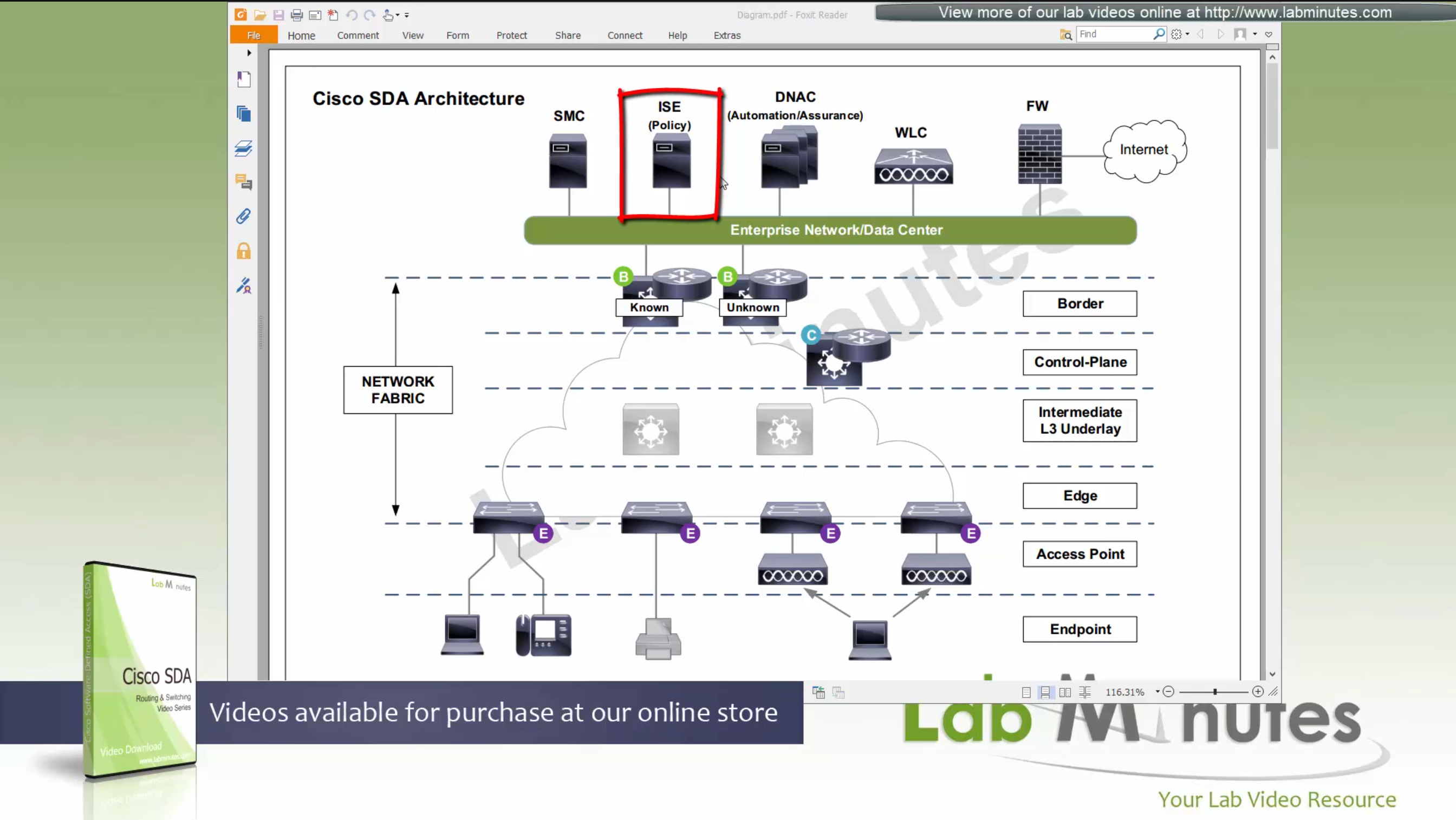
Management loosing network such as DNAC will keep the data forwarding and not cause outage
One thing to keep in mind is that we need to have high speed LAN like access between all fabric nodes and DNAC, that is why DNAC cannot be spanned across WAN, all Fabrics must have high speed access to DNAC
DNAC is available as C220-M4 which is same C series server as APIC for ACI
It is always recommended by Cisco to deploy DNAC in cluster of 3
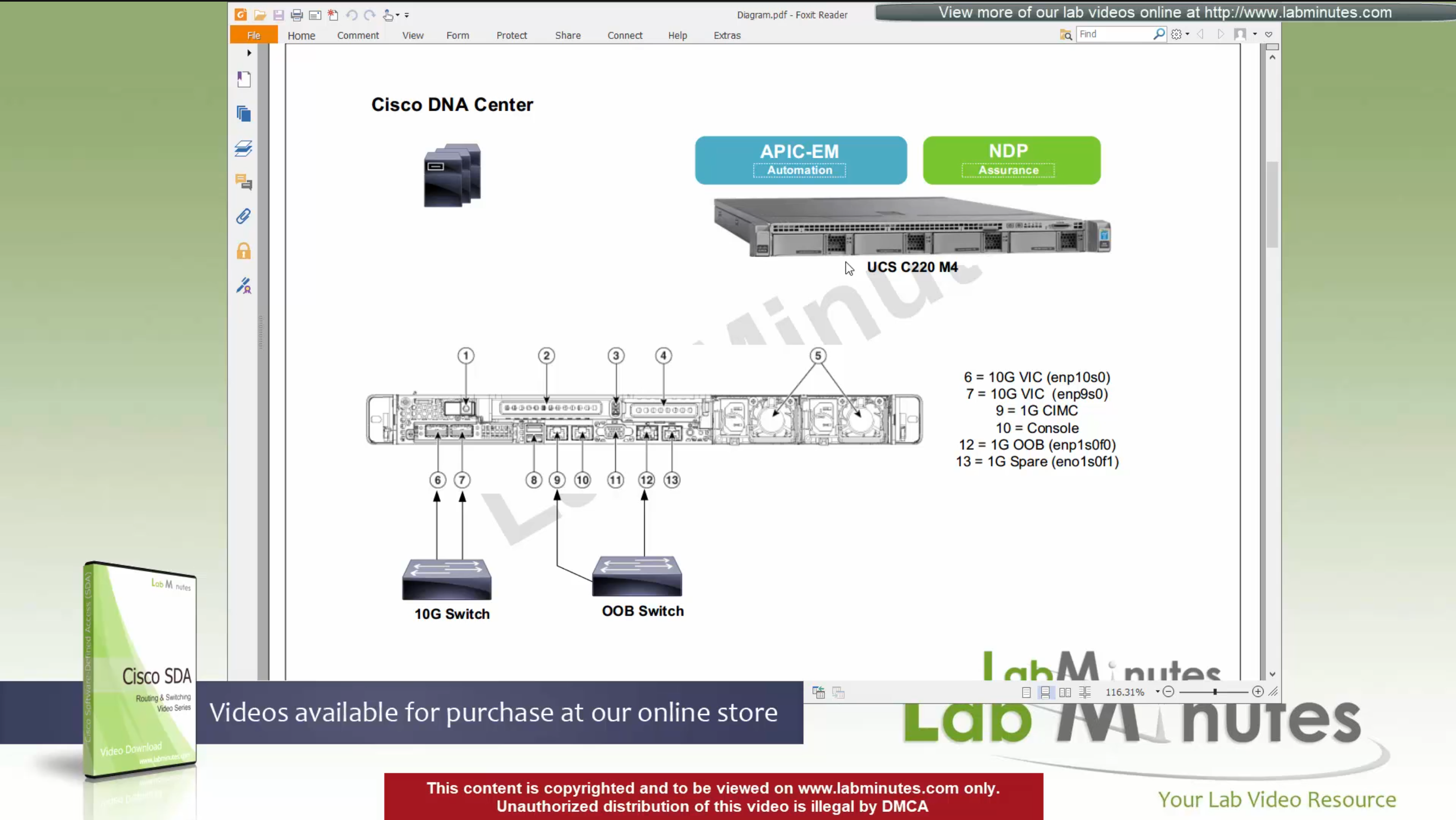
For connectivity DNAC has 2x (redundant) 10G VIC Cards – Data path for managing the fabric
for Management connections it is not mandatory to configure the OOB connection
Data port IP can be used for management unlike ACI, where GUI and SSH must strictly be done via OOB IP
CIMC interface – Server interface for KVM and firmware upgrades
Console interface – in case network connectivity is lost
(out of band) OOB Mgmt interface – optional for HTTP and SSH for DNAC but it is recommended so we have another path for accessing the GUI and SSH
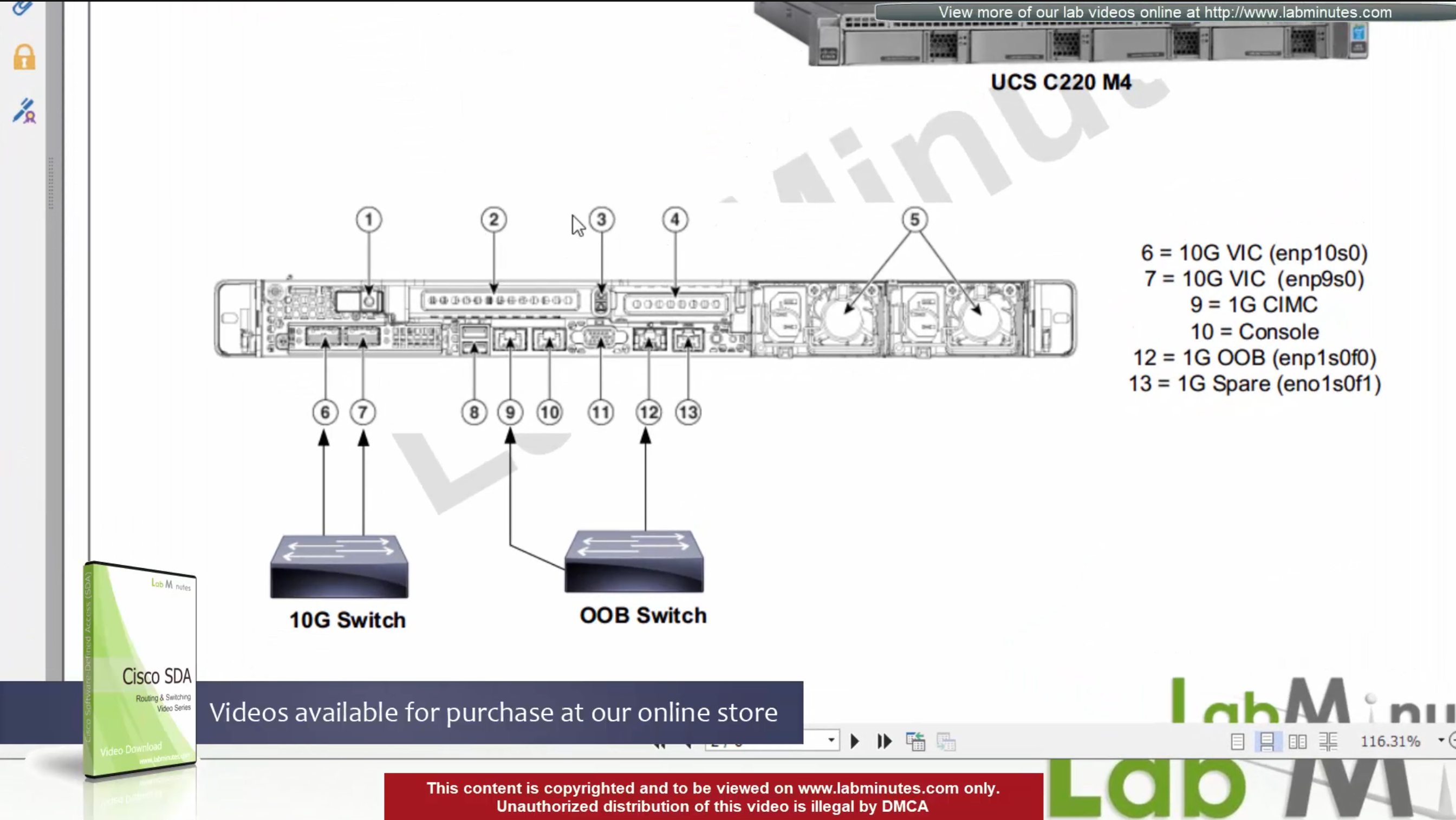
There are 2 engines running on DNAC,
APIC-EM
NDP
There is 3rd engine called policy engine but it does not run on DNAC but on ISE
APIC-EM shares a lot of features with APIC and helps with Network topology discovery, software management and upgrades aspect etc
APIC-EM is also responsible for the network automation
NDP stands for Network Data Platform – NDP takes care of the, end to end network “monitoring”, “telemetry”, “assurance” and “data analytics”, This is like NPM of Solarwinds
NDP is more with analysis and alerting
while the APIC-EM is like NCM for pushing changes and making changes
In NDP Assurance comes from the fact that it goes one level deep and not just polls network devices for system stats and health but it also gets the Client’s connectivity monitored from client and their experience perspective
Client connection stats and connection health and client experience is one of the big things, and it is client connectivity that “assures” that network is working because clients are live and using the network, so instead of SLA on the box, client data traversing the network is a better testament that network is working or not
NDP also has “machine learning” elements
DNAC Assurance or NDP collects data from various sources, once data is received, Assurance engine does correlation and provide information
This is the list of devices that are supported, some devices have some features supported and others fully support all the features. This sheet can be found on google, Y and N in column have been added, older hardware possibly cannot support those features
Most devices support basic functionality offered by APIC-EM such as inventory, topology, Image Management, plug and play, easy QoS and so on.
These things are marked in green color, but when it comes to SDA (green column) we can see that only limited set of new devices are supported
We can see that very first switch that can do SDA is 3650 Copper
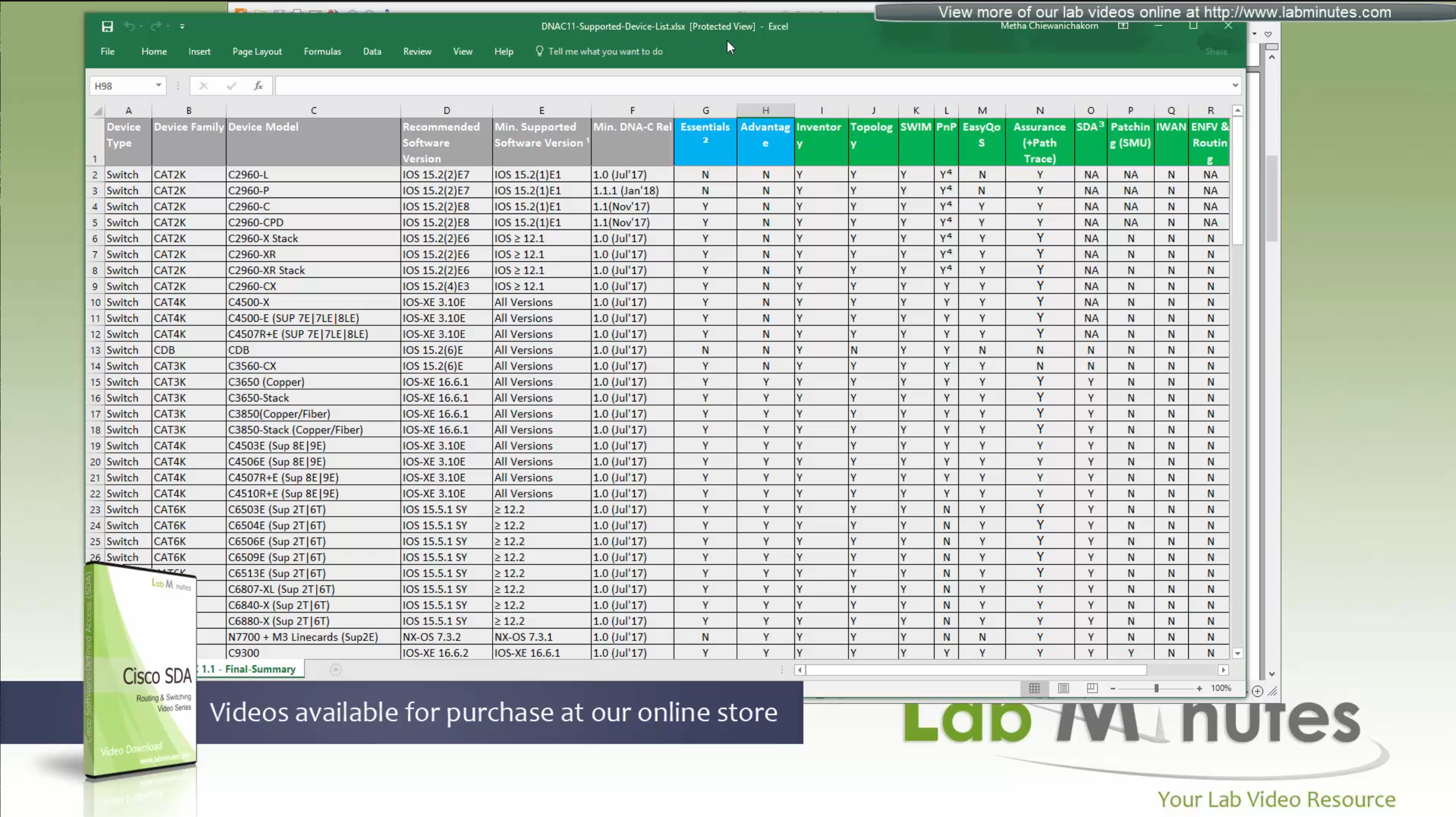
SDA deployment shows what is supported on which models based on the “node role such as edge node, border node, control nodes etc”,
“for example some cisco models can be the edge nodes only but not the border node or control node”.
So make sure that we order right kind of hardware before deployment.
If we are going for new hardware then Cat 9k will support most of the SDA features
If you are looking to “scale” for a lot “larger campus” then we can upgrade the “border or control nodes to routers which have bigger memory to deal with large number of routes which can get us bigger MAP server”
This list also includes routers, as routers are also supported in SDA for Border and control nodes
See how some devices can be edge and not border or control and then there are some devices which can be border and control but not the edge, that is why it is safe to go with 9300 and 9500 series Catalyst switches
3850 switches are supported for SDA but for small deployments
Similarly there are WLCs that are validated for SDA, be sure to check SDA hardware sheet
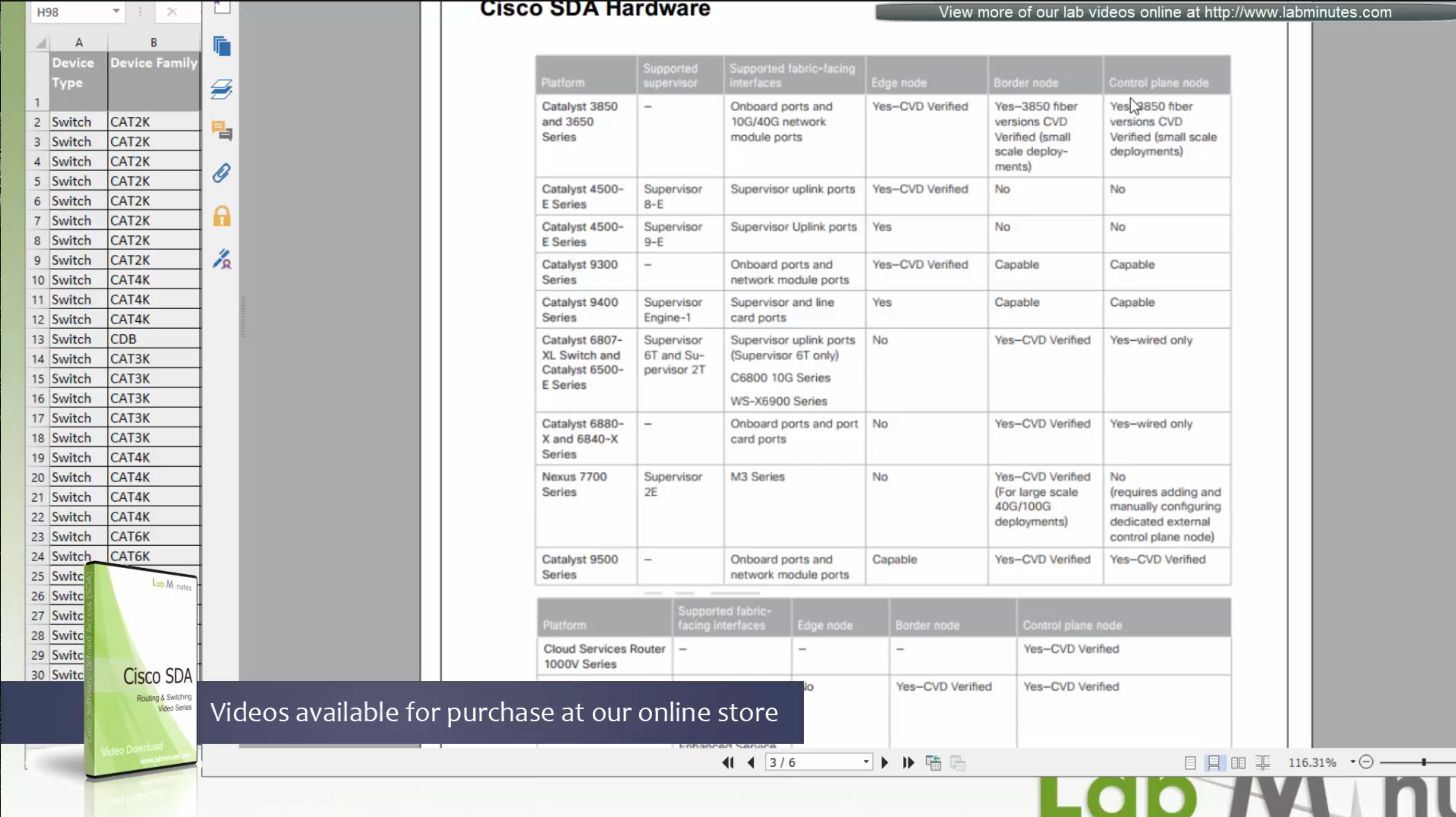
Always consult “ordering guide” for new deployments
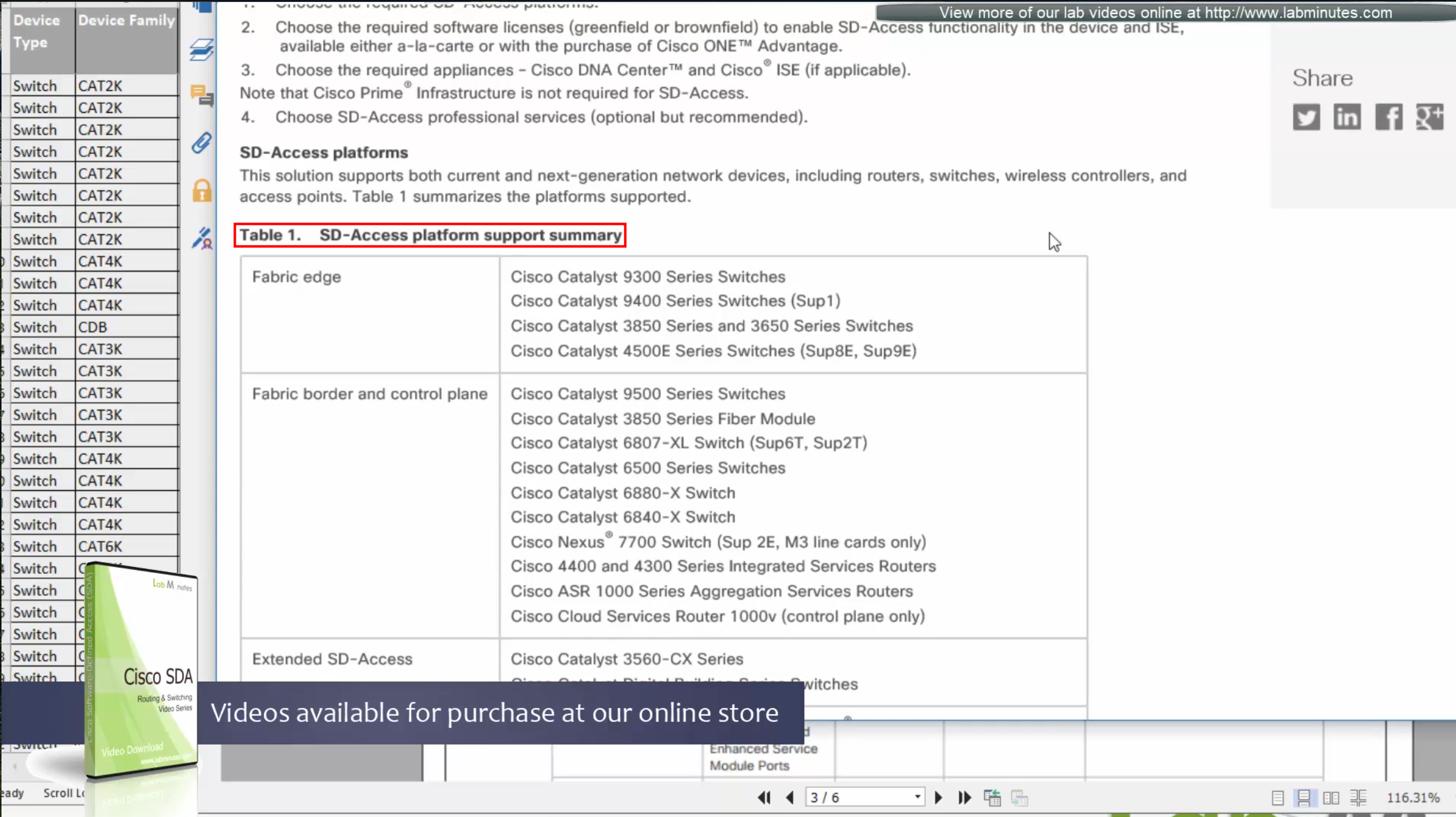
Fabric is consistent across the network and is not different unlike legacy network which can have different networks between different switches because of inconsistent configuration. Fabric on the other hand is consistent from L2 and L3 perspective.
All the underlay network is going to see is UDP packets


Fabric edge nodes tell the control plane about new endpoint by snooping the ARP response and DHCP offer packets (device tracking on edge), information told to control pane includes “MAC addresses”, “IP addresses”, “port connected to”, “Liveliness” (to see if host is there or not) and “VNI host belongs to” (VNI is equivalent of the VLAN in VXLAN world).
Edge node sends a “MAP register” message to control node
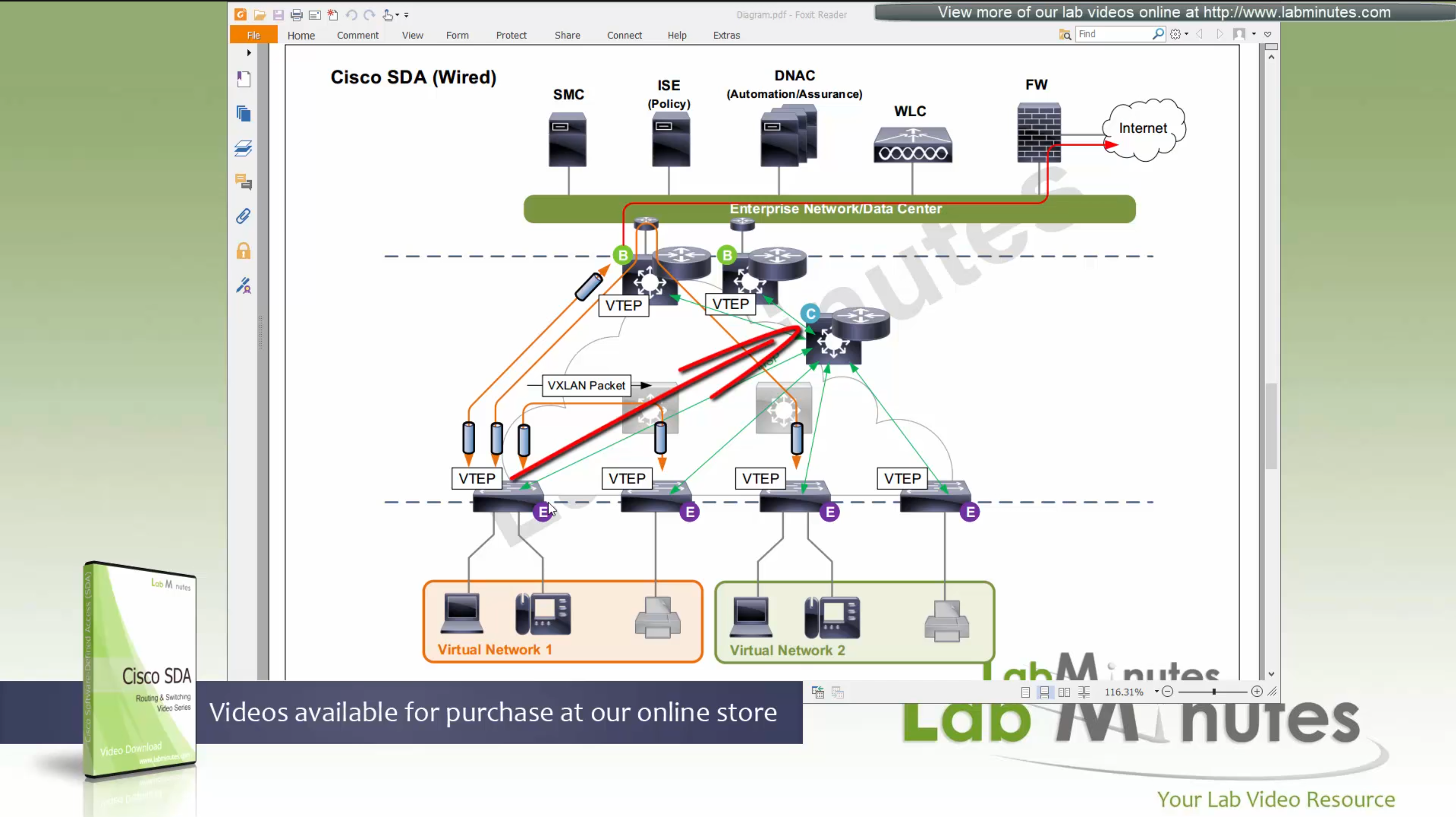
Control node creates an EID (Endpoint identifier) to RLOC (Routing locator) entry is created in database
VTEP and RLOC refers to same thing, the loopback IP address on the switch
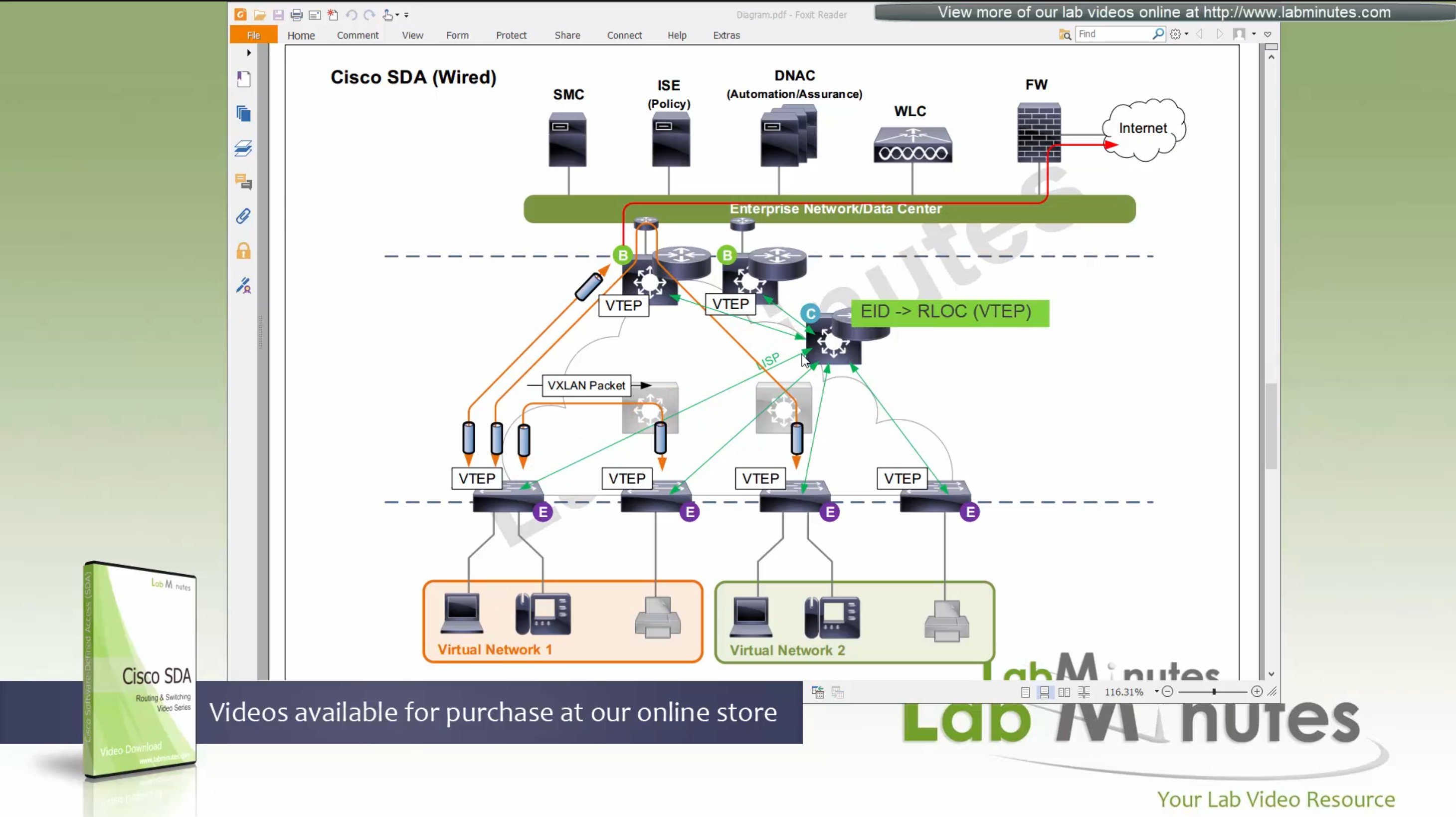
Border node does the same thing the edge nodes do with control node (if on same chassis, then it does that process internally), but instead of registering Endpoint IDs it has prefixes to deal with, prefixes it learns from Fusion for external networks (outside of fabric) as EIDs to Control node.

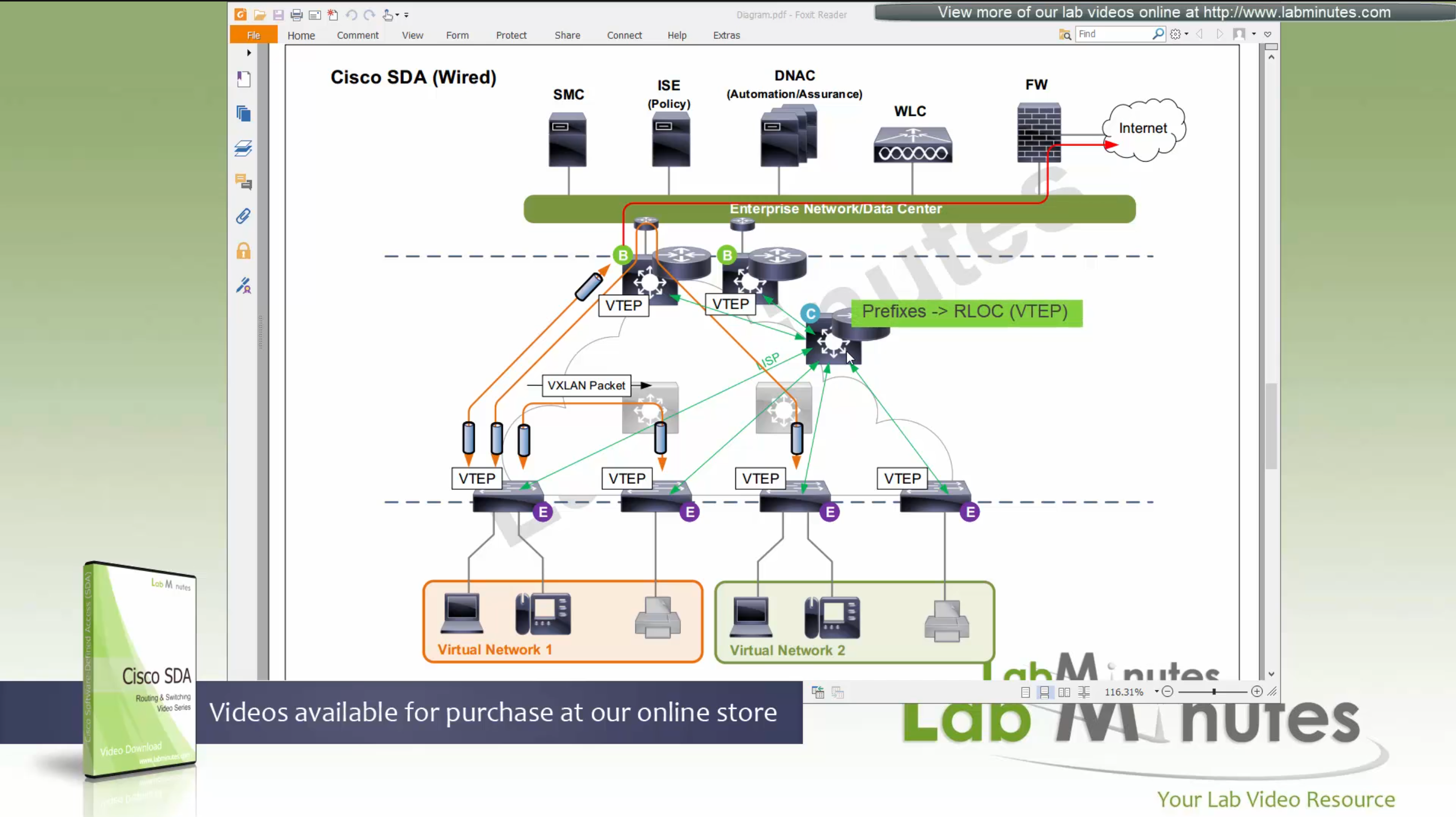
which means that control plane node not only maintains the EID but also the prefixes
border node needs to be redundant

Edge switches query the MAP server on control node
Similarly when border receives traffic destined to an EID in fabric (inbound)
or border receives traffic for networks outside of the fabric (outbound)
border node goes to control node and queries the MAP server on control node
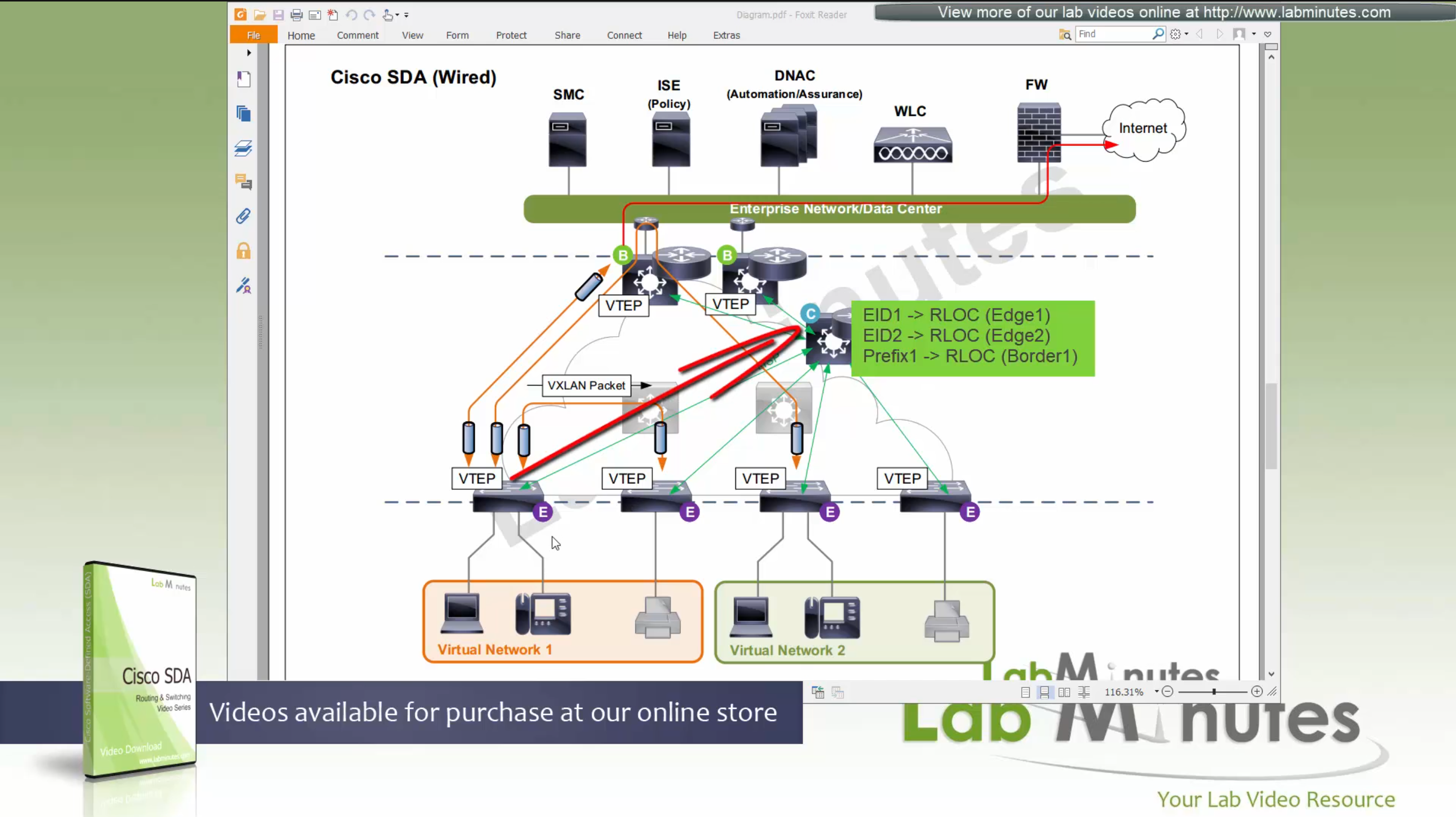
control plane node then responds with the RLOC,
Caching: border or edge node then caches in a local cache that RLOC entry for future use
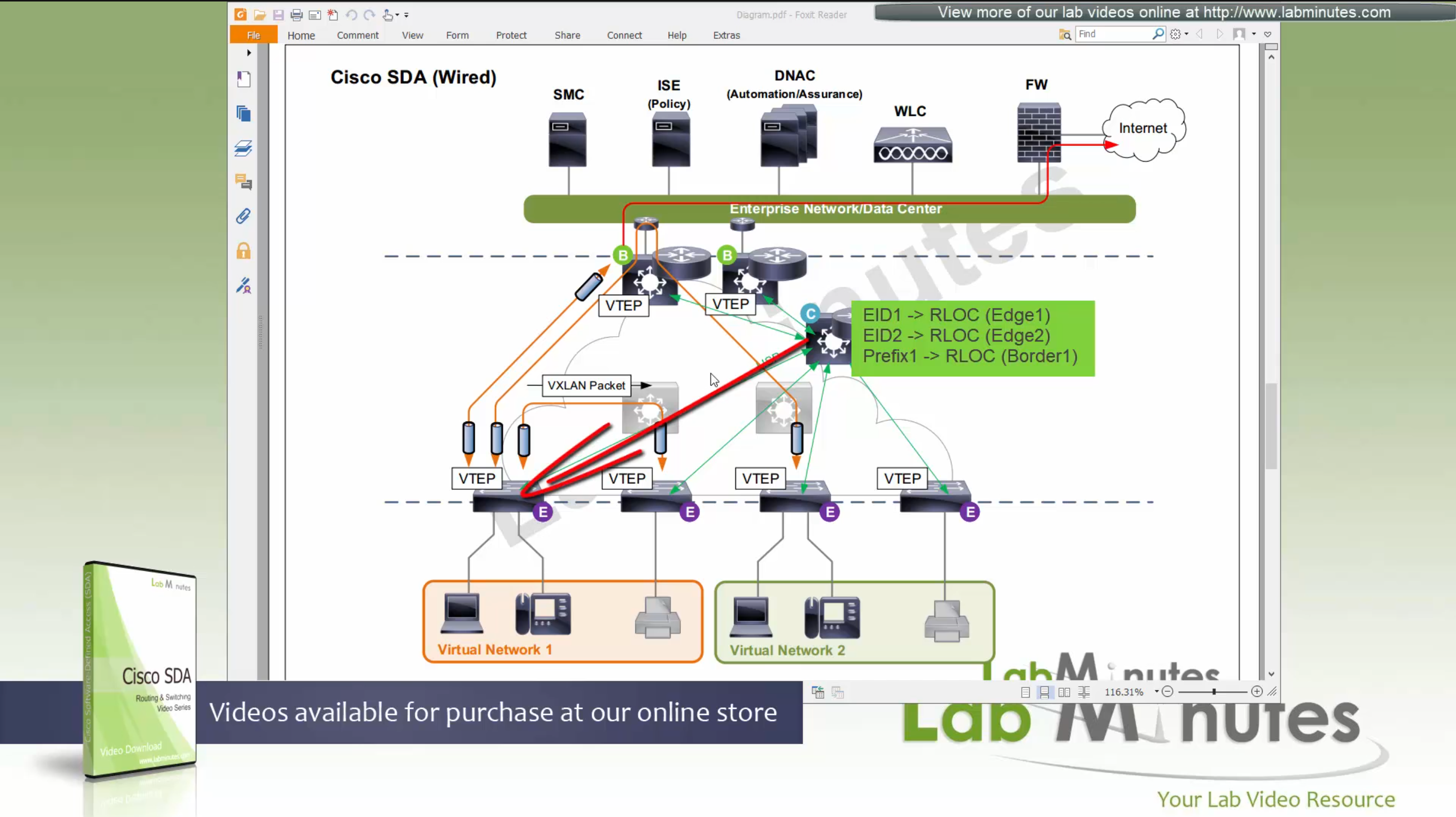
Edge node or border then makes VXLAN tunnel to that RLOC
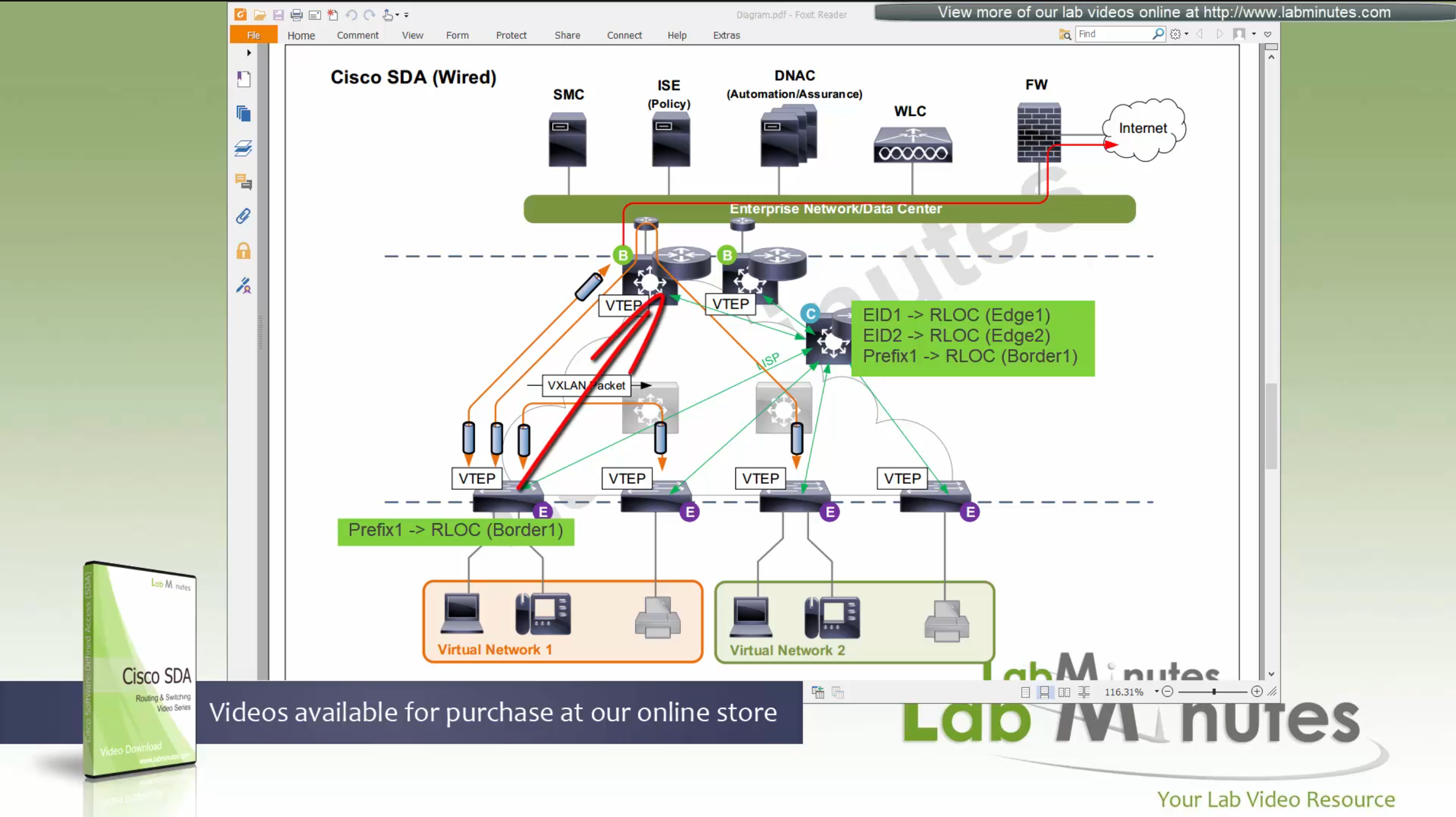
because edge and border receives and caches the RLOC entries on need to basis, it keeps their routing table or FIB small and this translates to scalability, that acts as a consulting table to route or switch over the fabric and not the routing table
Edge nodes also run something called Anycast gateway which makes SVI available on all the edge and border nodes
These SVIs also have same MAC addresses so when client roams from one node to another, it is seamless
despite presence of SVIs edge nodes always ask / consult control plane node and get the answer because these SVIs are available on edge nodes simply to offer seamless L3 gateway after roaming to new location
These SVI anycast gateways exist on both Border nodes and also on edge nodes
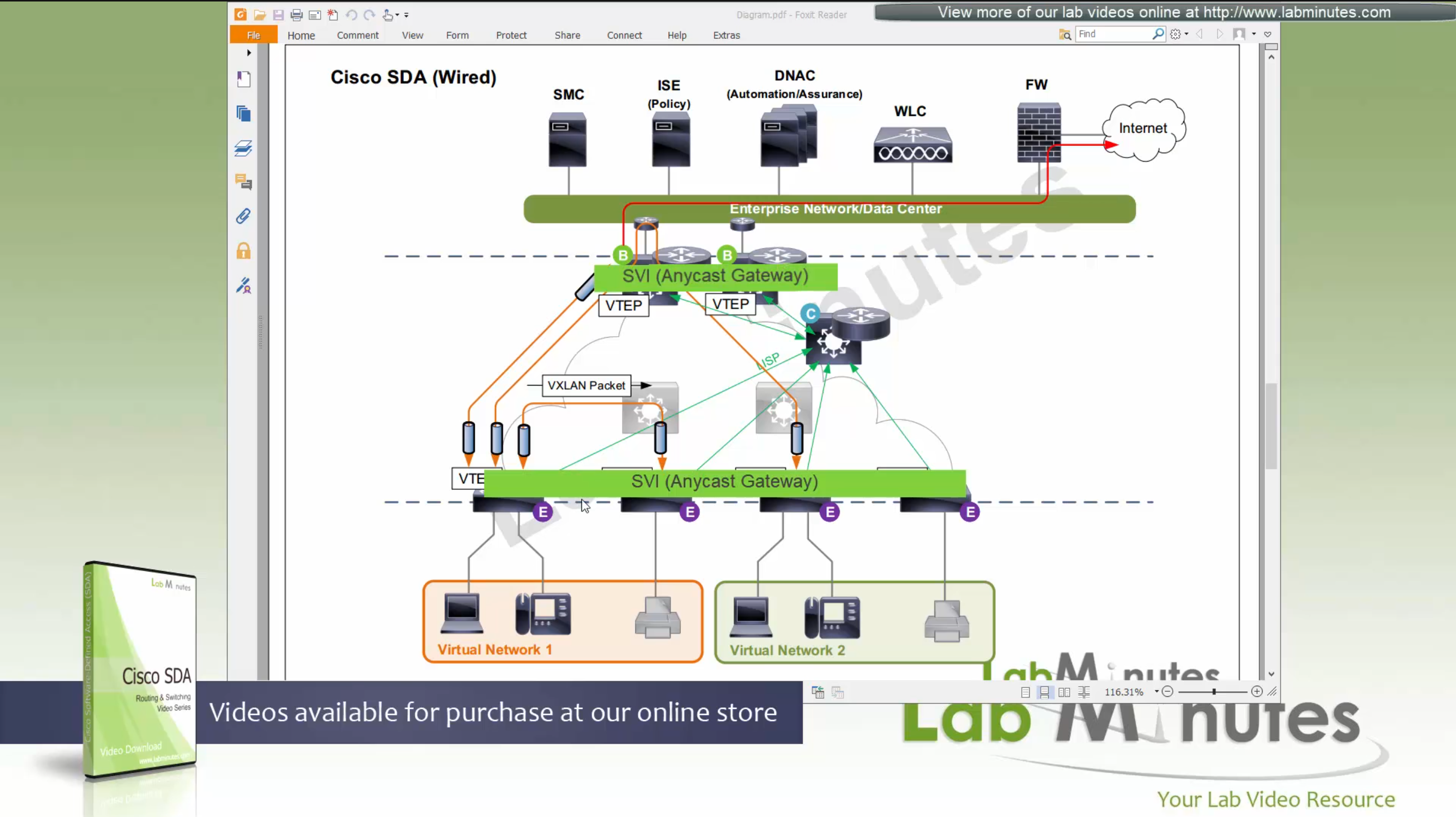
Here we have two different virtual networks or VRFs
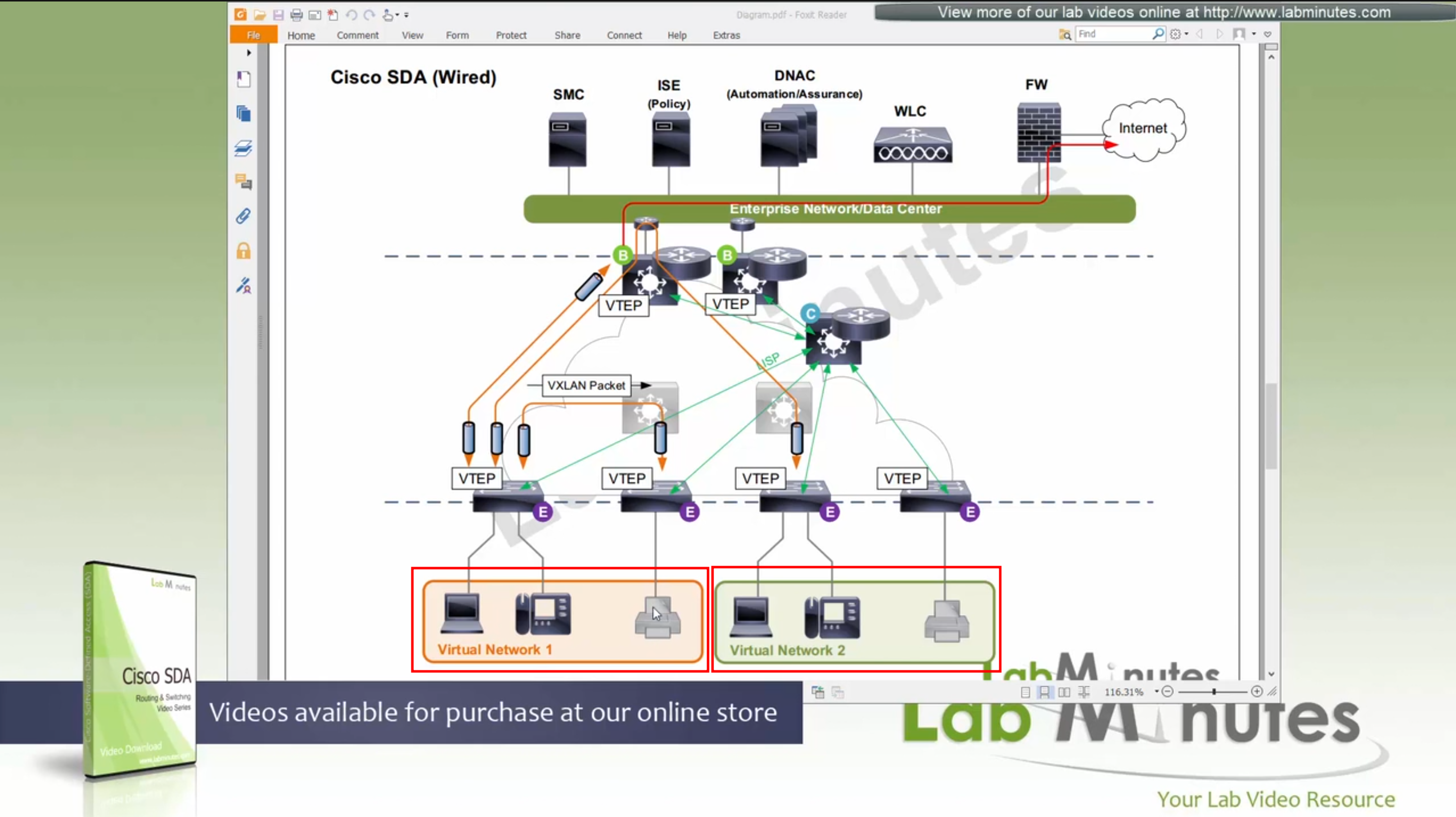
Scenario 1: Packet stays on same switch
In this scenario packet does not leave the switch and is switched from one port to another and that makes it fastest, if you have an ultra low latency requirement where even couple of milliseconds of latency such as 2 ms or latency of VXLAN packetization and encapsulation is not tolerable then place the hosts on same switch
Scenario 2: Packet stays within the Fabric, IntraVN (same VN) traffic
When PC needs to communicate to the printer, it speaks to control node (because printer is on another edge node) and obtains RLOC for that edge node where printer is attached,
it will create a vxlan packet with correct L2 VNI tag, and correct outer L3 RLOC destination IP address
and insert original IP packet into it as a payload and then send it out to the underlay to deliver.
Underlay will deliver
As seen in diagram, this VXLAN flow will not touch border node
As these VXLAN packets reach Intermediate Nodes, because they have loopbacks advertised in ISIS (shortest paths for loopbacks) VXLAN packets will be switched from “edge node to Intermediate node to edge node” Triangle: Edge <–> Intermediate <–> Edge
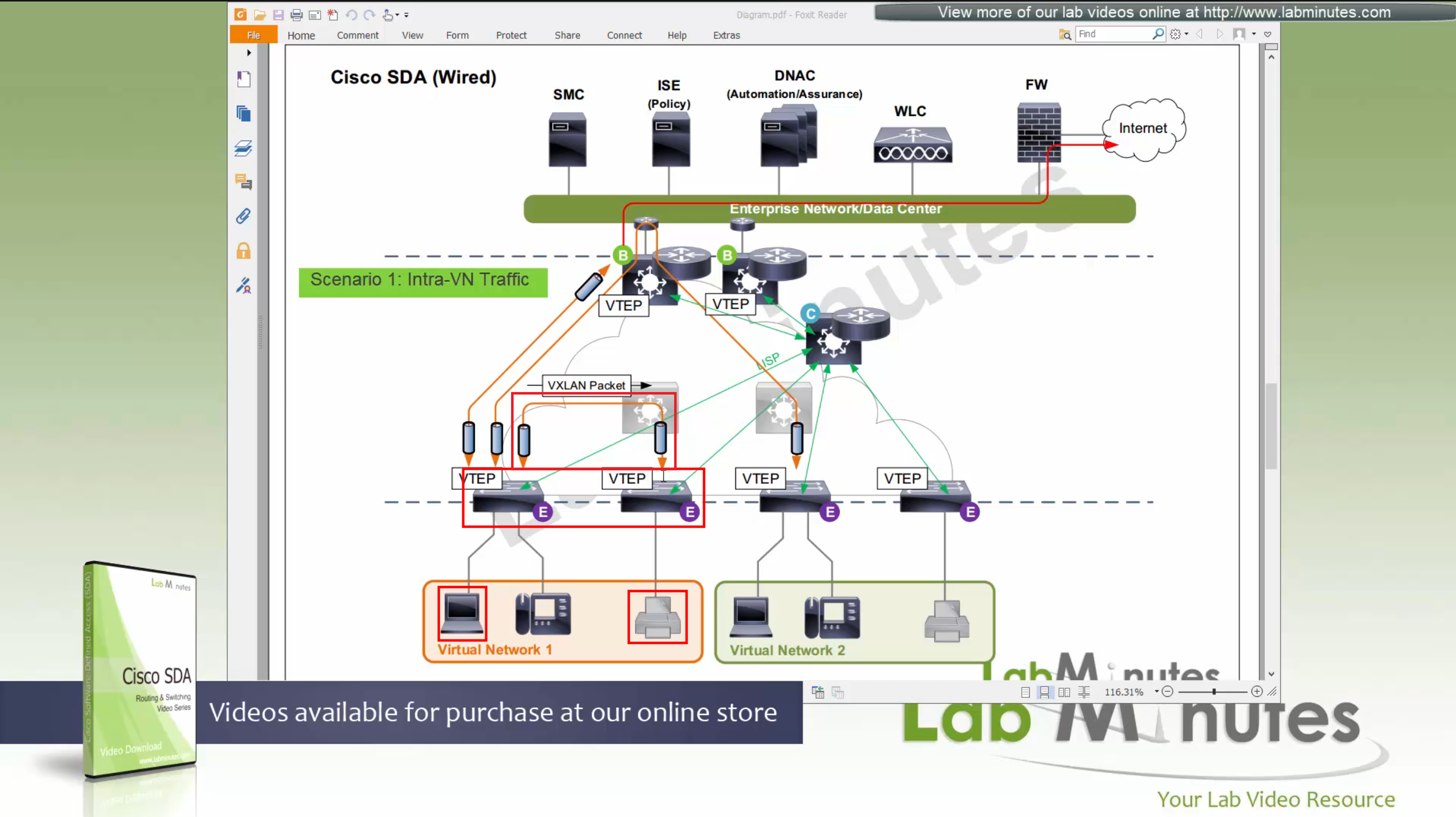
Scenario 3: Packet destined for “Known” external network outside the fabric.
Edge node inquires the control plane for “destination”, control plane returns the RLOC of the border node that registered the prefix and then edge sends the packet to border node,
it will create a vxlan packet with correct L2 VNI tag, and correct outer L3 RLOC destination IP address
and insert original IP packet into it as a carrier and its payload and then send it out to the underlay to deliver.
Underlay will deliver vxlan packets to the border node and border node will “decapsulate and deliver it out to the external network”
Packets will flow from edge node to intermediate node to border node and then fusion node to get to external networks
Edge <–> Intermediate <–> Border <–> Fusion <–> External destinations
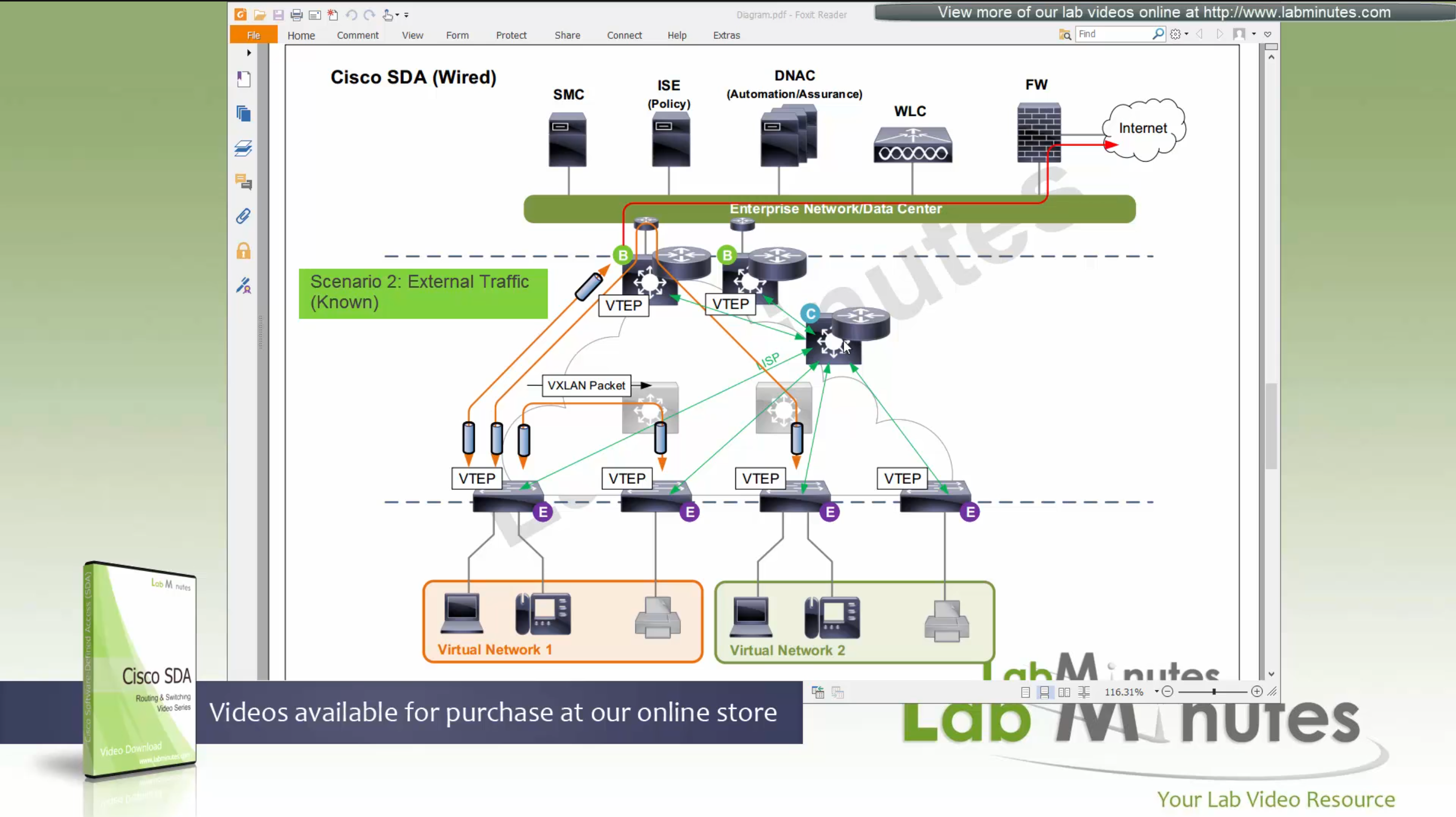
Scenario 4: Packet desitned for “Unknown” external network outside the fabric.
Edge node inquires the control plane for “destination”, control plane returns the RLOC of the “default” border node, in most networks Default Border Node and Known Border Node are the same device, then edge sends the packet to border node
it will create a vxlan packet with correct L2 VNI tag, and correct outer L3 RLOC destination IP address
and insert original IP packet into it as a carrier and its payload and then send it out to the underlay to deliver.
Underlay will deliver vxlan packets to the border node and border node will “decapsulate and deliver it out to the external network”
Packets will flow from edge node to intermediate node to border node and then fusion node to get to external networks

Scenario 5: Packet destined for another Virtual Network, InterVN (to another VN) traffic
This scenario applies when host in Virtual Network 1 needs to communicate with host inside Virtual Network 2 below, queries will still happen as in previous scenarios with control plane
Now this gets a bit trickier in these notes because this is an old video for an old release when SDA did not allow route leaking inside the Fabric, so that meant that packets will be routed all the way out of the fabric to the fusion router and routed back into the fabric, because border node cannot be routing “between” different Virtual Networks, and for this to work fusion router also needs one “transit” sub-interface per Virtual Network or VRF
Obviously this is not optimal as InterVN traffic will face more delays than IntraVN traffic and fusion router is also single point of failure
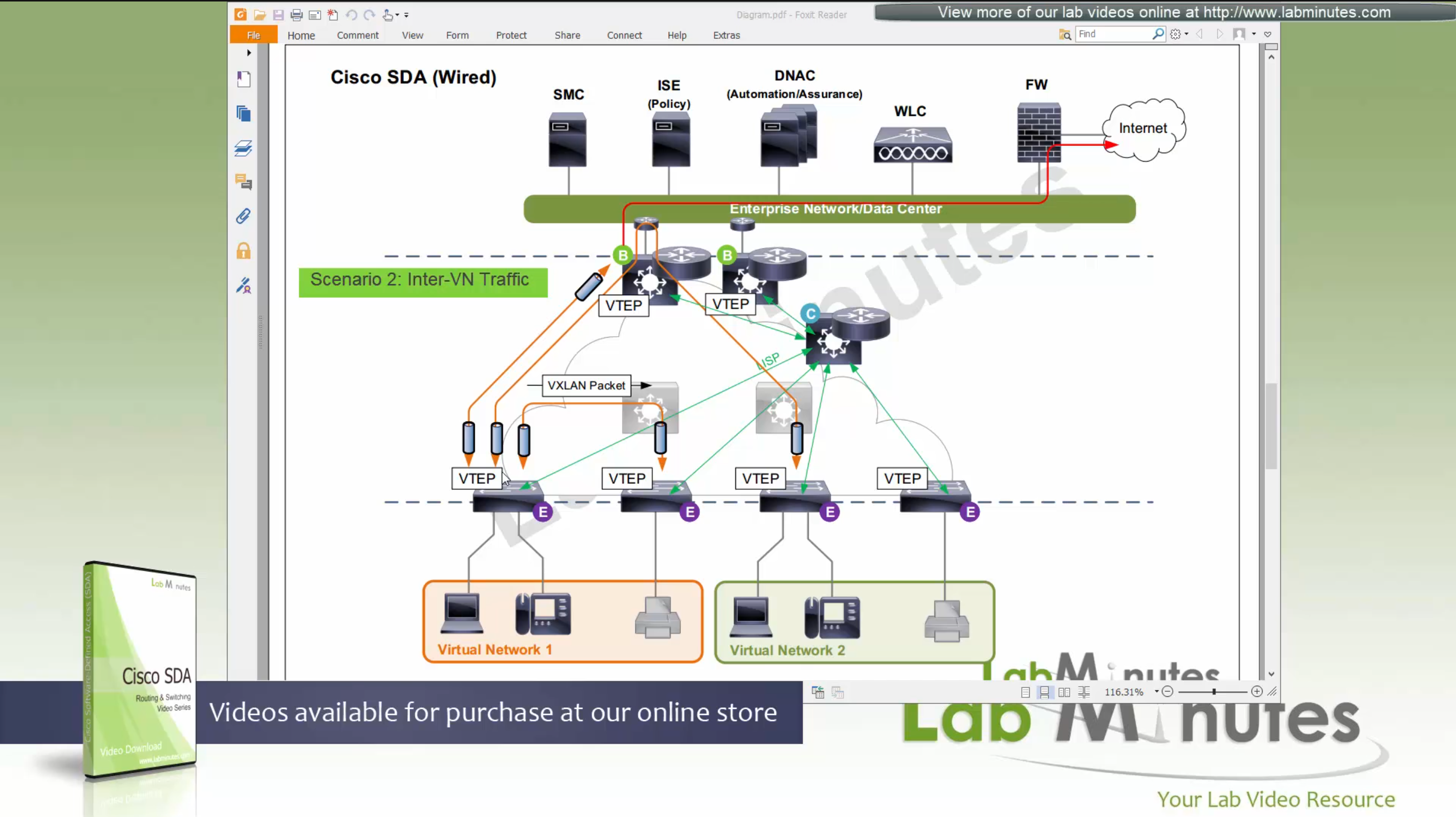
SDA wireless is next evolution from converged access mode and this is called “Fabric mode AP” and “Fabric mode WLC”, there are small differences now
WLC <—LISP session—> Control node
WLC speaks to control node using LISP session just like edge node and border node
WLC sends register EID (of wireless client) to control plane,
Control plane node has full view of the network including the EIDs from wired and EIDs from wireless as well
AP <—VXLAN Locally Switches Data—> Edge node
AP <—CAPWAP control connection only—> WLC
Second difference is that AP still maintains the CAPWAP to WLC but it is only for CAPWAP control connection, data is locally switched to the edge node over the mini VXLAN tunnel.
Data sent by Fabric mode AP to edge switches using VXLAN tunnel
this VXLAN tunnel between Fabric mode AP and edge is only between AP and edge that are directly connected, it does not extend from AP to remote edge switches
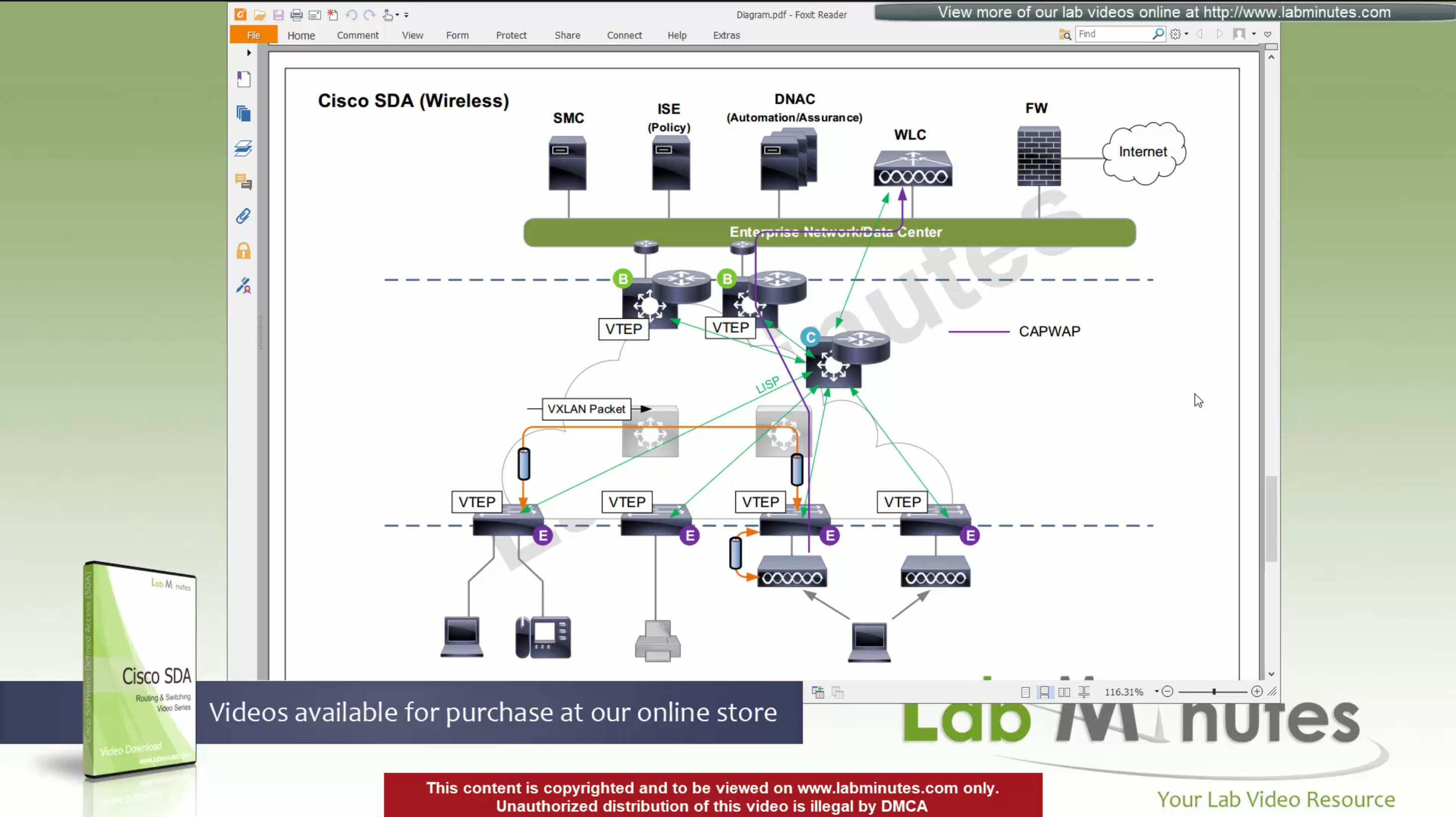
Client will associate and authenticate with the SSID, obtain IP address

“WLC will do MAP register with control plane node” and tell control plane node about the client as EID and which AP it belongs to (just like it does same for switchport)
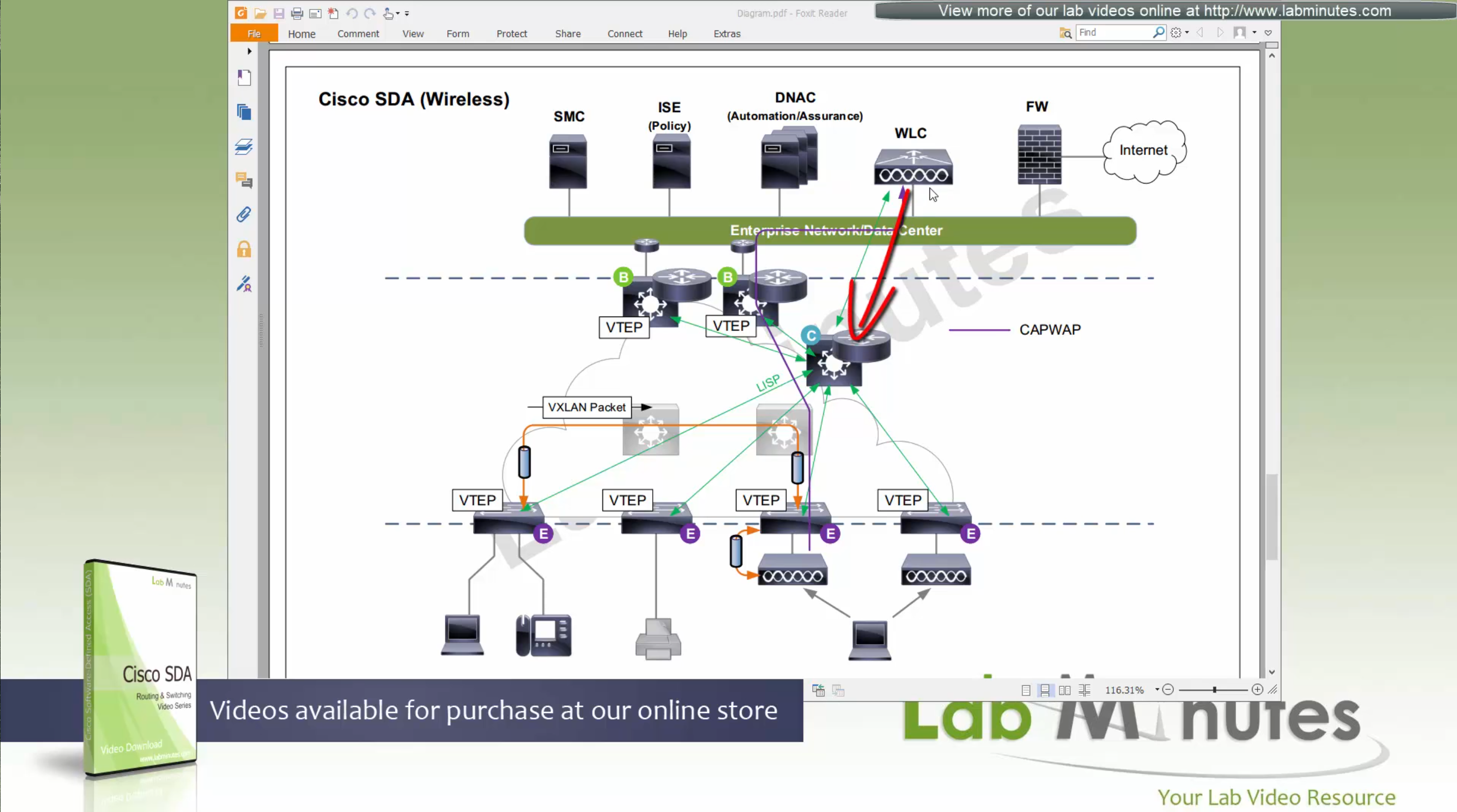
When wired client needs to communicate with the wireless client

edge node of the wired client will obtains the RLOC from control plane and make tunnel to the edge switch where wireless client’s AP is connected
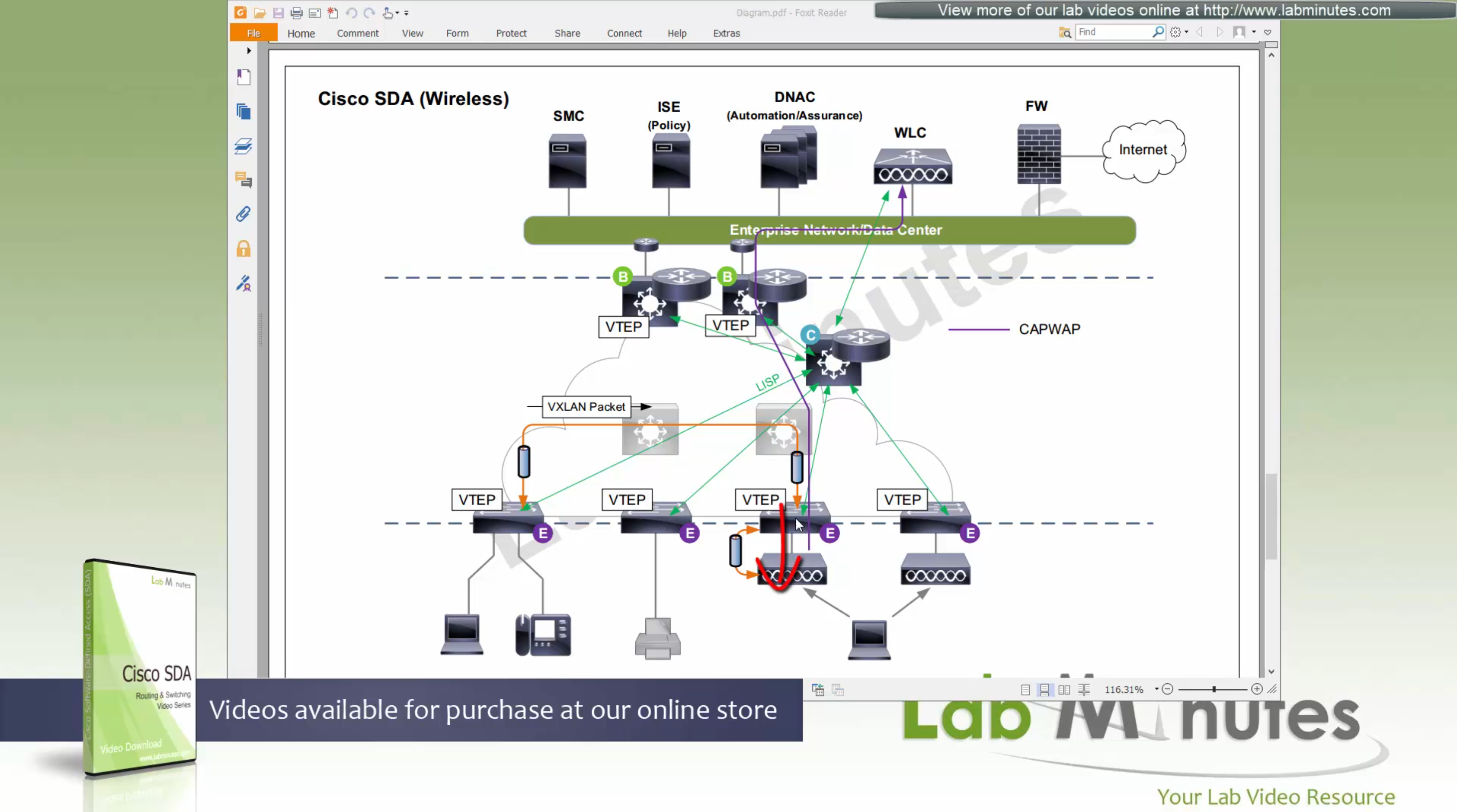
once edge node de-encapsulates the VXLAN tunnel, it checks and sees that mac address of the wireless client is behind that mini VXLAN tunnel, so it will re-encapsulate the traffic and send that to AP and vice versa in reverse
The reason for AP to VXLAN is so that AP can inform the switch of the correct VNI the client belongs to, this is the point or mechanism that keeps consistency from the wired world for VNI, making wireless clients seem like just like wired clients policy and monitoring wise, SGT are tagged in overlay and SGT tags are inside the tunnel and not outside on the VXLAN packets themselves
and when user roams from one AP on one edge switch to another AP on another edge switch, WLC will be informed about the roam by the roamed to and from APs, WLC will inform the control plane also and control plane will update the entry’s RLOC to be the new edge switch whose new AP client has roamed to
While in Fabric, WLC and APs can still be connected to the Fabric but operate in “Legacy mode” which is also called “over the top” setup, in which data from AP is sent in CAPWAP (Data tunnel) to WLC and WLC switches the traffic out
There is also a low latency requirement of 20ms between the WLC and AP so keep in mind that APs have to stay somewhat close to the controller in the campus setup
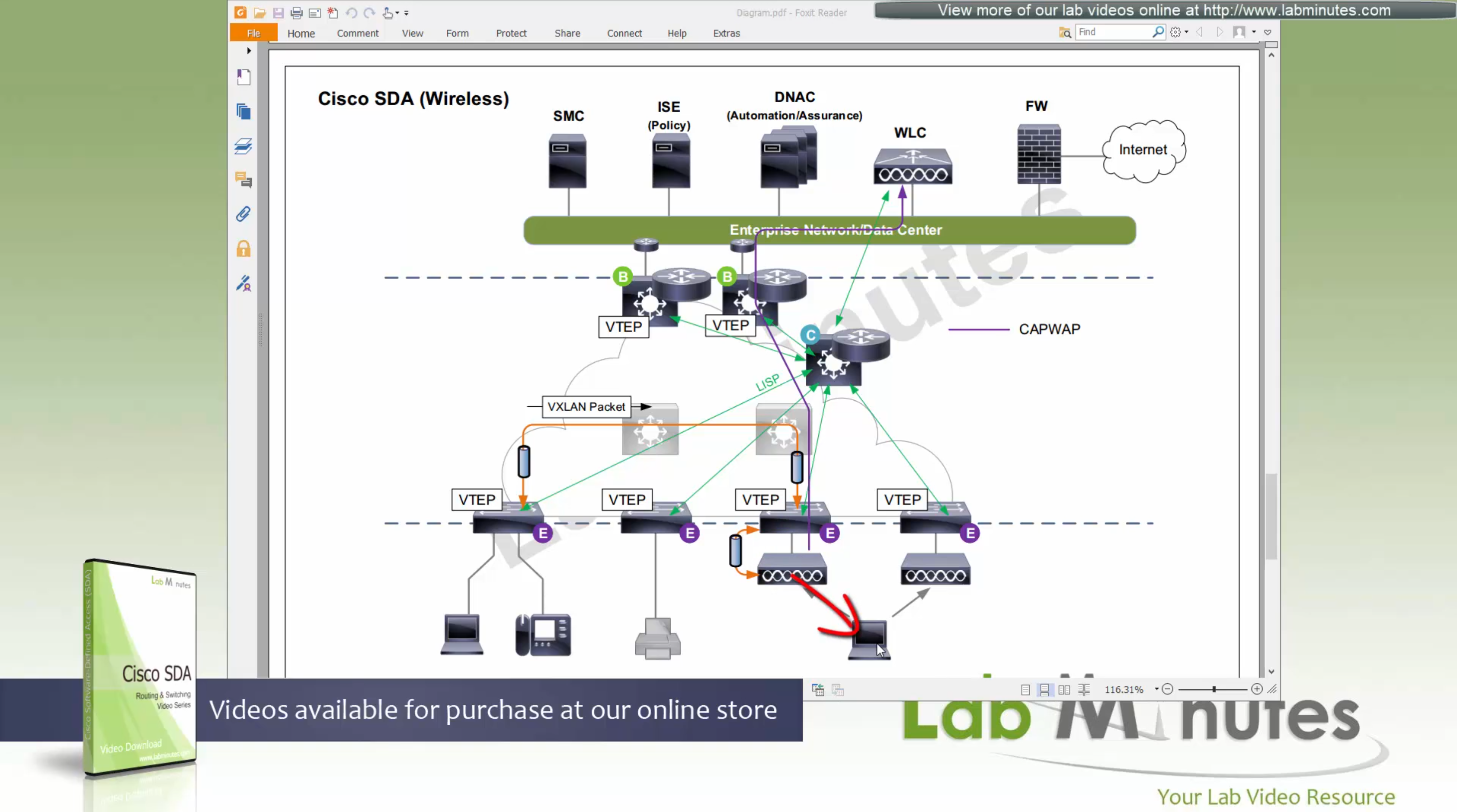
With Cat 9k we have following options for licensing
DNA Essential gives most of the feature set of the APIC-EM
while DNA Advantage gives most of the features in Assurance and NDP + SDA
SDA is only available with DNA Advantage license
Network Essentials and Network Advantage are for IOS-XE and Network Advantage is like IP services license (like it used to be in older IOS)
Cisco offers a license called One Advantage that offers DNA + ISE + Stealthwatch all in one license

Right after installation of DNAC and first GUI login we need to quickly download the packages or software apps which are GBAC Group Based Acccess Control ( SGT / SXP / ISE ) and also SDA package to enable SDA in DNAC. Cisco does not readily ship the DNAC with ova or iso, SDA and a lot of other modules need to be downloaded using below very specific settings


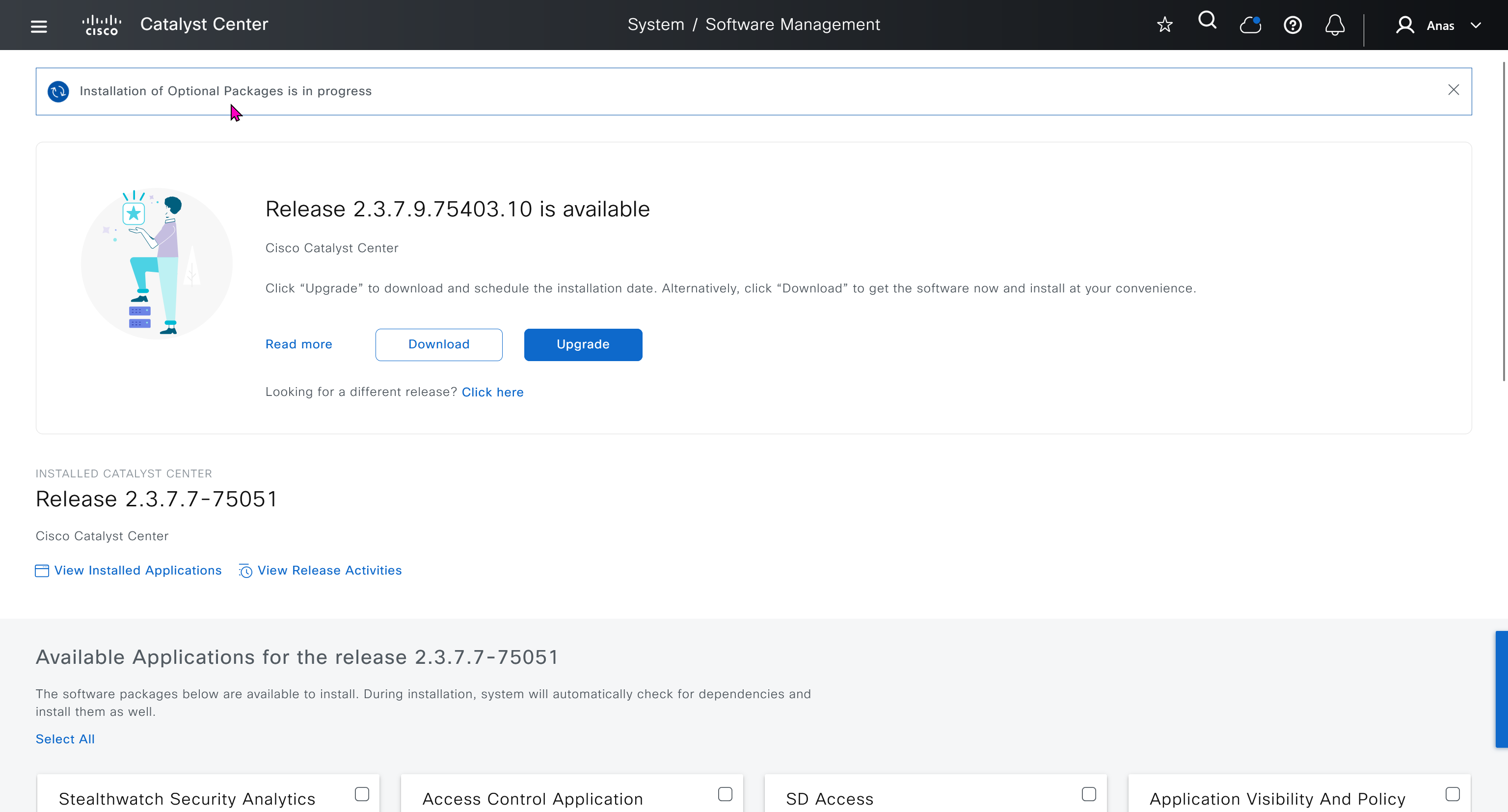
Group Based Access Control is not there and needs to be downloaded

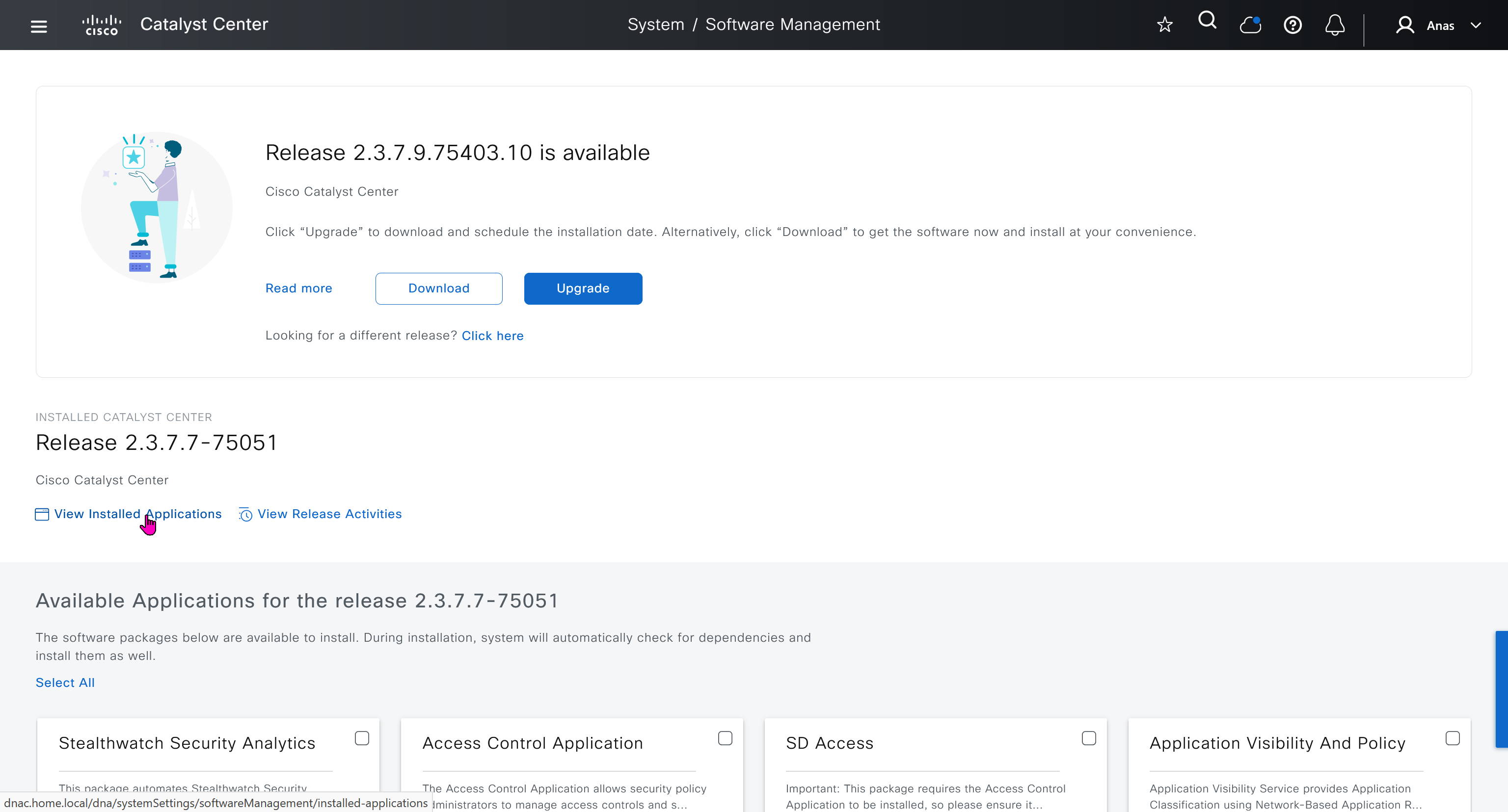

Installation kept failing at download stage

I had to remove the VM as there was something wrong and when new dnac was installed, one thing I did is I added the company’s cco information here but not in the smart licensing, dont add to the smart licensing section instead add at the beginning on first GUI login

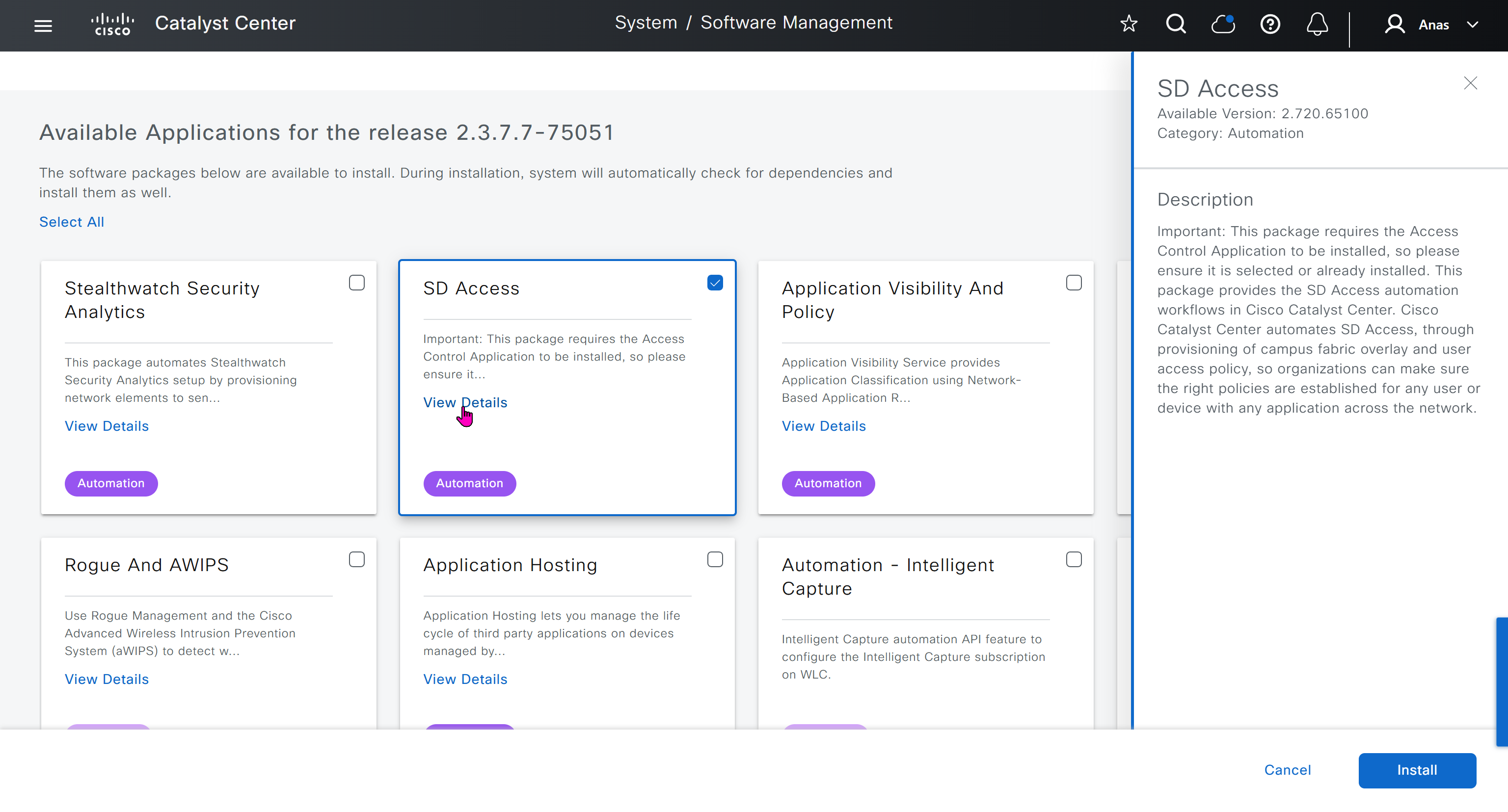
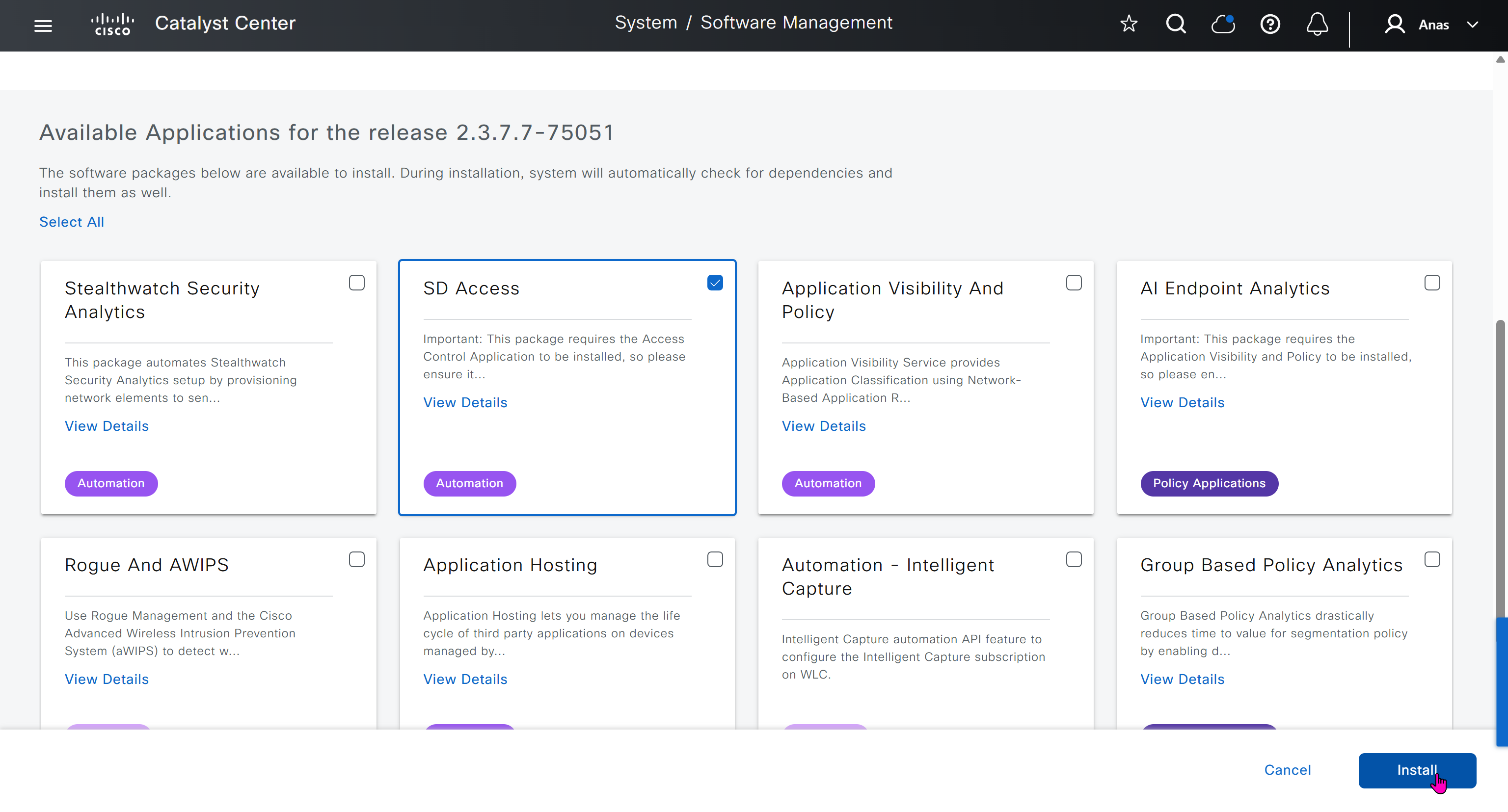

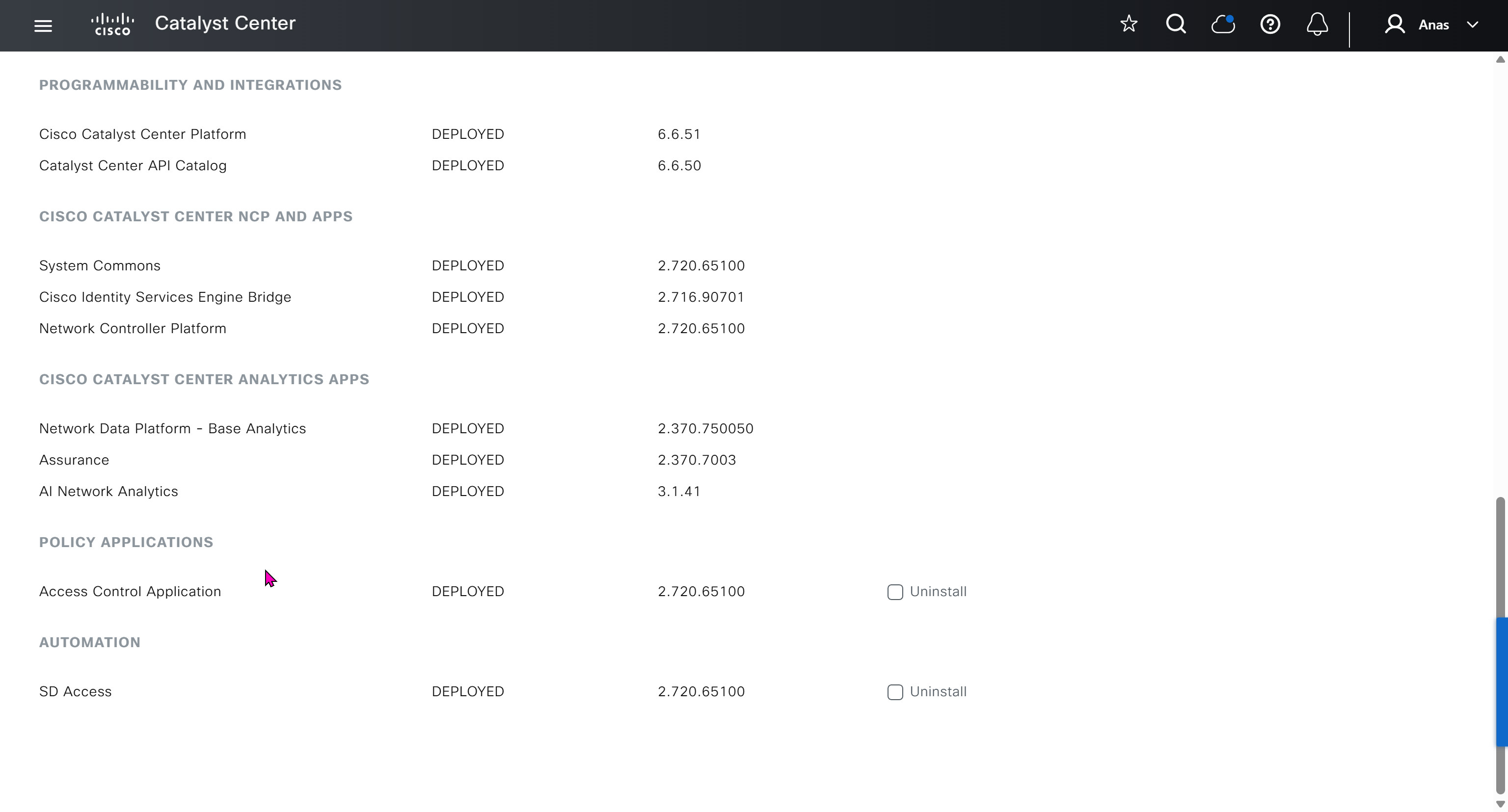
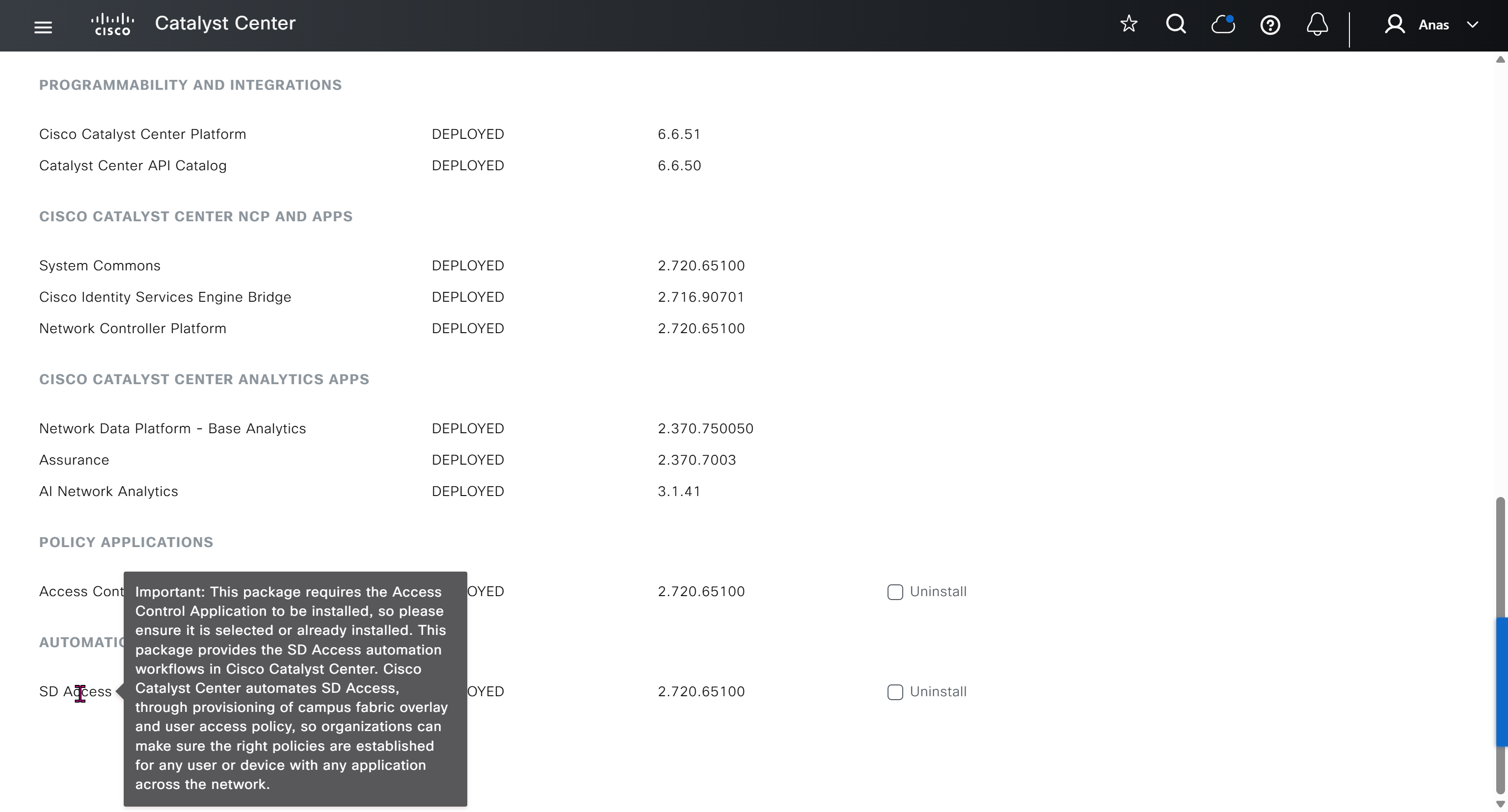
Finally it installed well
now Group Based Access Control GBAC is showing in menu now

We will take a look at installing certificate as ISE needs to be integrated, and for that we need to take information from default certificate’s information, common name is the name that we provided during the initial installation of DNAC

If we look at subject alternative names we can see a lot of SAN entries, these SAN entries contain IP addresses as well and one of those IP addresses will be of the VIP in case we have multiple DNAC appliances

Enhanced Key Usage: Server Authentication, Client Authentication as this is used for ISE PX Grid integration

We will have to install the OpenSSL for Windows
cd C:\Program Files\OpenSSL-Win64\binopenssl req -new -nodes -newkey rsa:2048 -keyout dnac.key -out dnac.csr -subj "/C=UK/ST=GB/L=London/O=home.local/OU=IT/CN=dnac.home.local" -addext "subjectAltName=DNS:dnac.home.local,DNS:dnac01.home.local,DNS:dnac02.home.local,DNS:dnac03.home.local,DNS:dragonfly-kong-frontend,DNS:dragonfly-kong-frontend.maglev-ingress,DNS:localhost,DNS:pnpserver.dnac.home.local,DNS:pnpntpserver.dnac.home.local,DNS:dragonfly-kong-frontend.maglev-ingress.svc,DNS:dragonfly-kong-frontend.maglev-ingress.svc.cluster,DNS:dragonfly-kong-frontend.maglev-ingress.svc.cluster.local,IP:10.21.1.2,IP:169.254.6.66,IP:172.16.25.2,IP:127.0.0.1,IP:::1"openssl req -noout -text -in dnac.cerWe have added those lines
Make sure that Data and OOB IP addresses are added including all Data and OOB IP addresses from clusters too
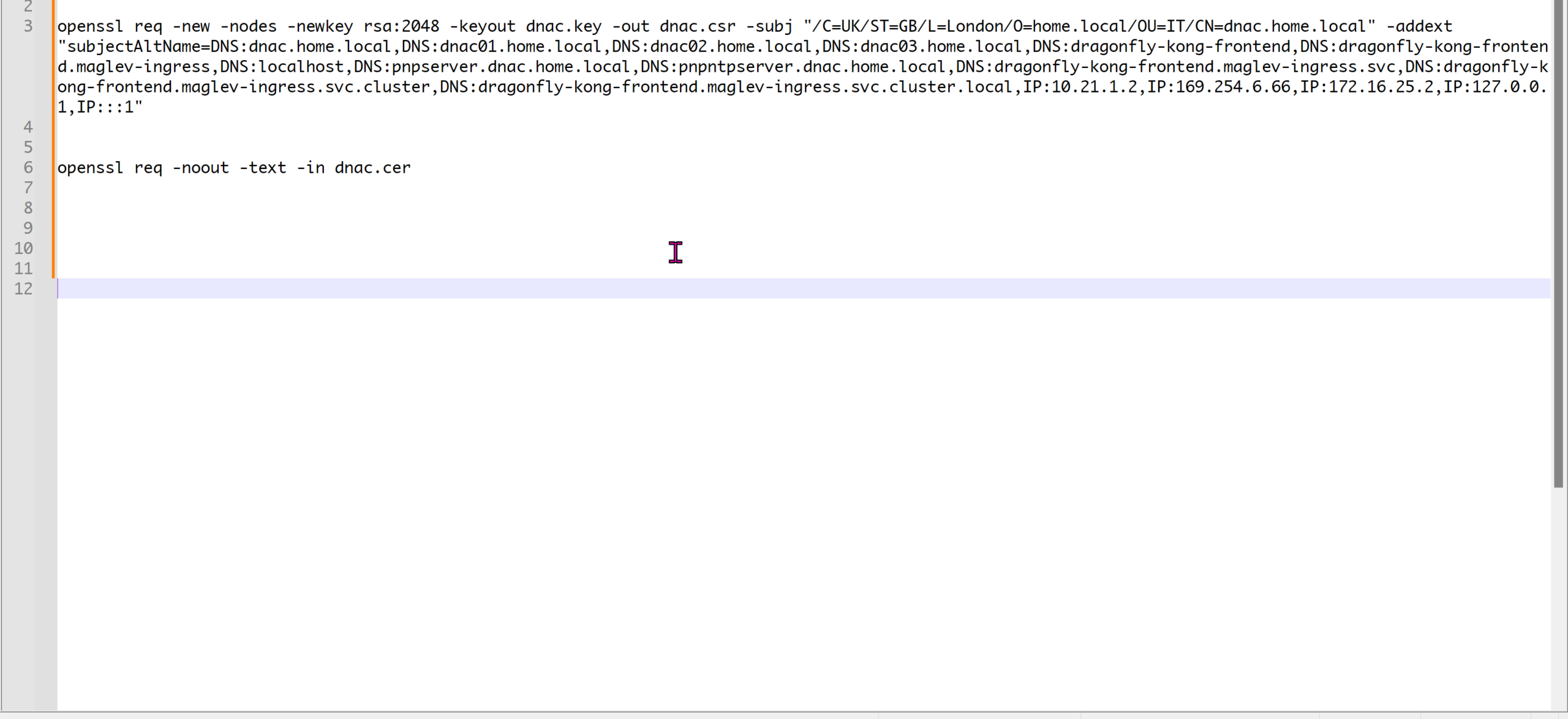


This Web Server EKU as Extended Key Usage has Client Authentication

We will append the root ca certificate (because identity cert comes first) in this notepad file and combine it for DNAC, in case you have any intermediate CA certificates then add them as well in the middle of identity and root ca certificate

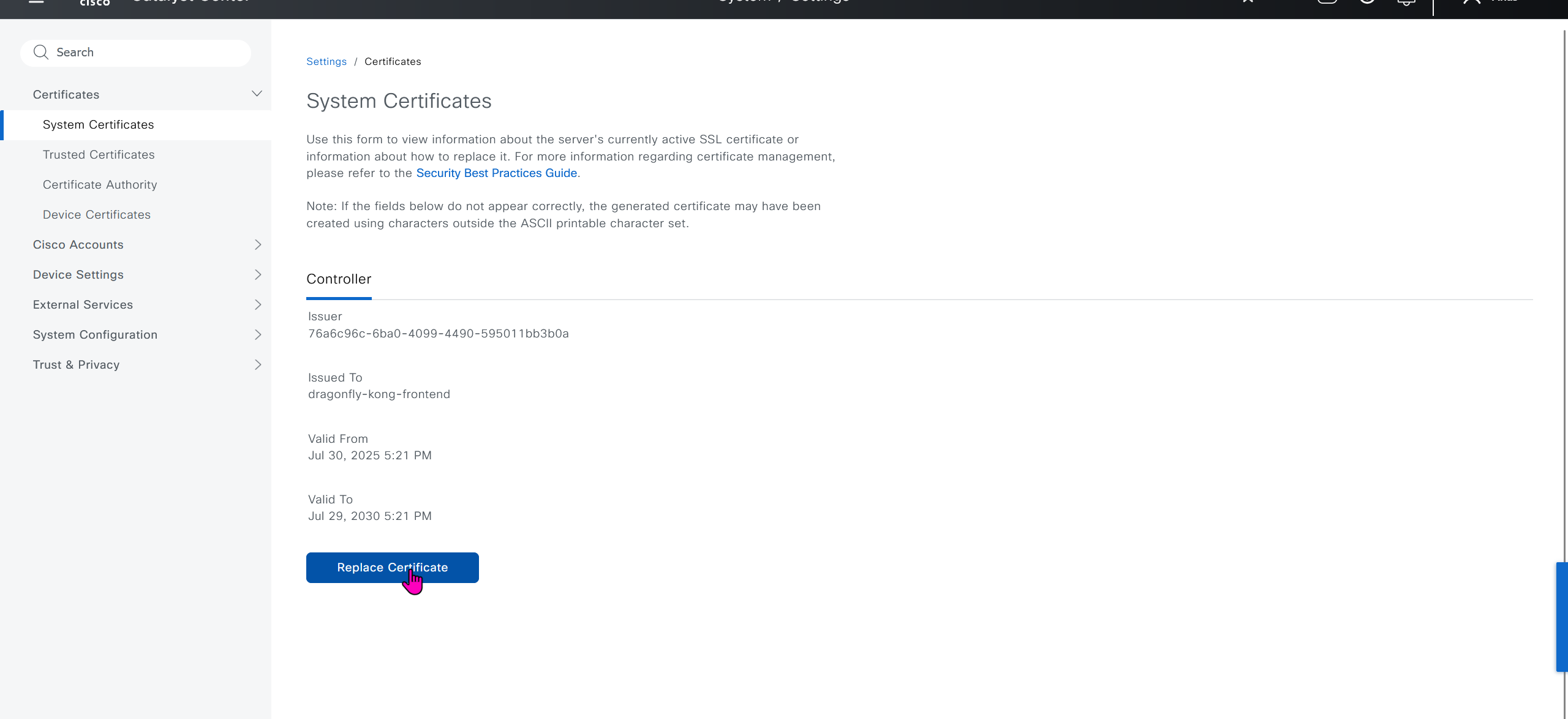
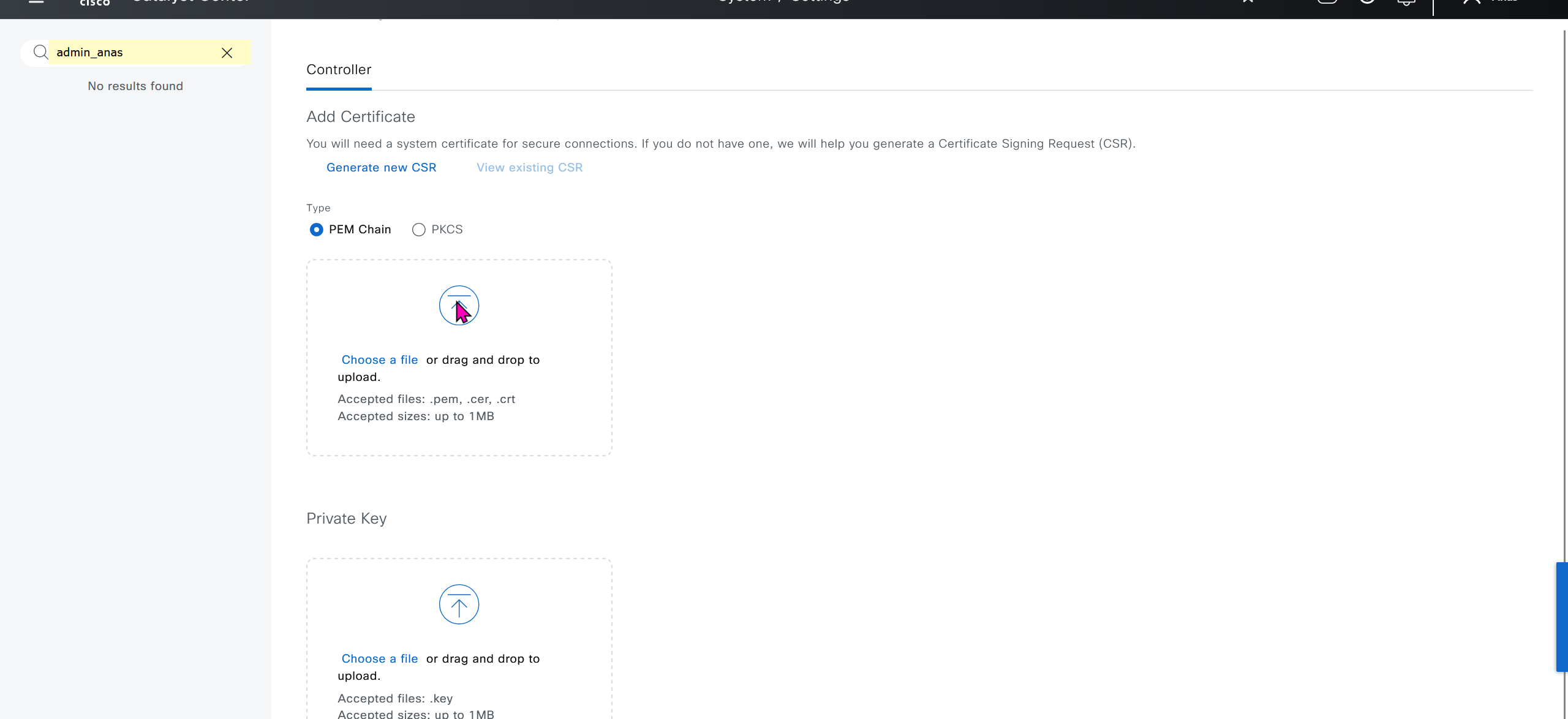






DNAC also issues certificates to devices which get added to it, and by default DNAC acts as the internal root ca but we can add our enterprise root ca or windows root ca too and this decision should be made right at the beginning before adding devices in DNAC or SDA fabric but once enterprise root ca is added we cannot convert this setting back to internal CA, usually we leave DNAC as the root ca for those devices

We can control the period for certificate’s validity
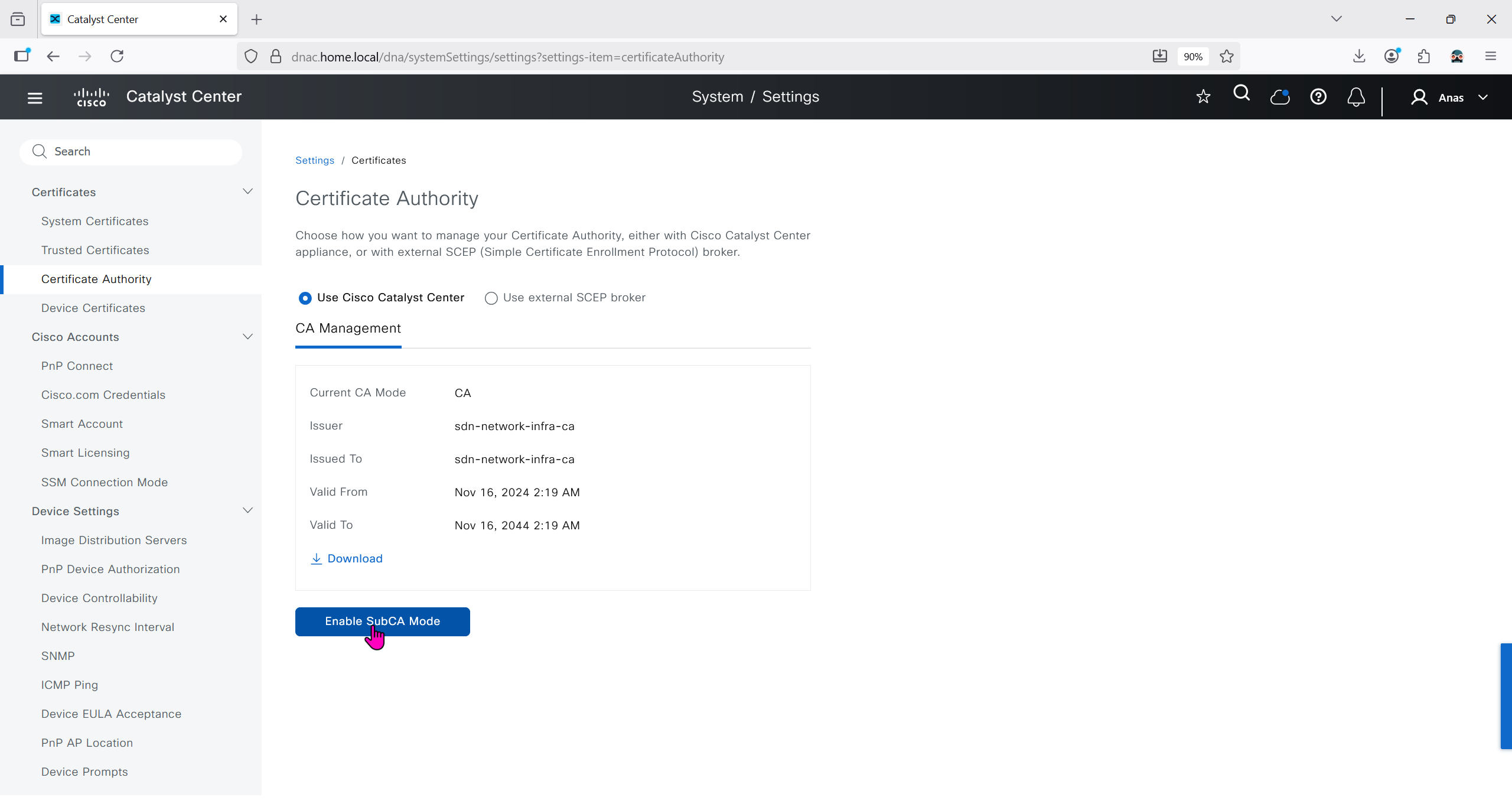
We will just click on option to enable SubCA mode but will not enable it just to see the message from DNAC
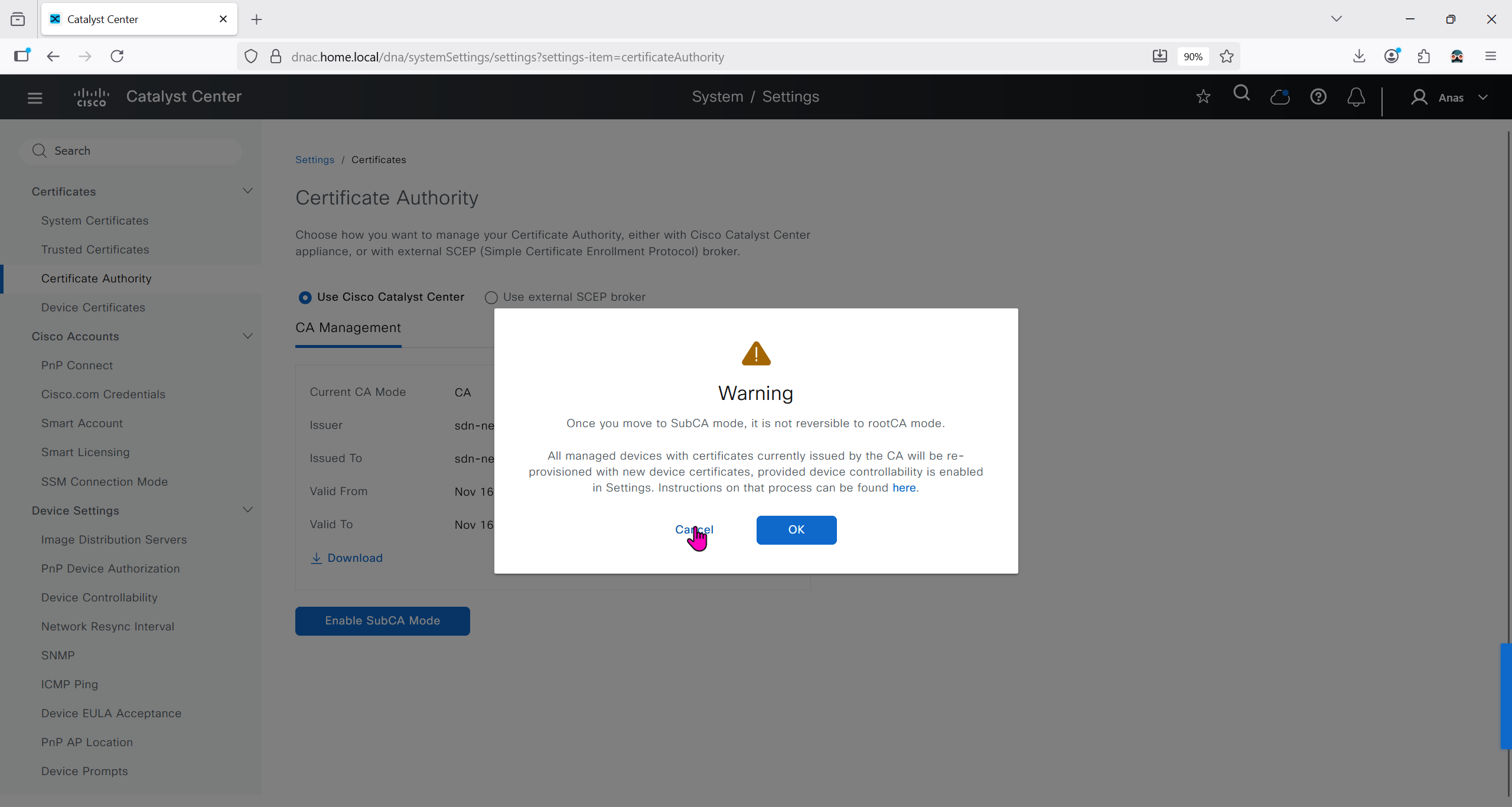
But if we were to enable it then following will be the steps
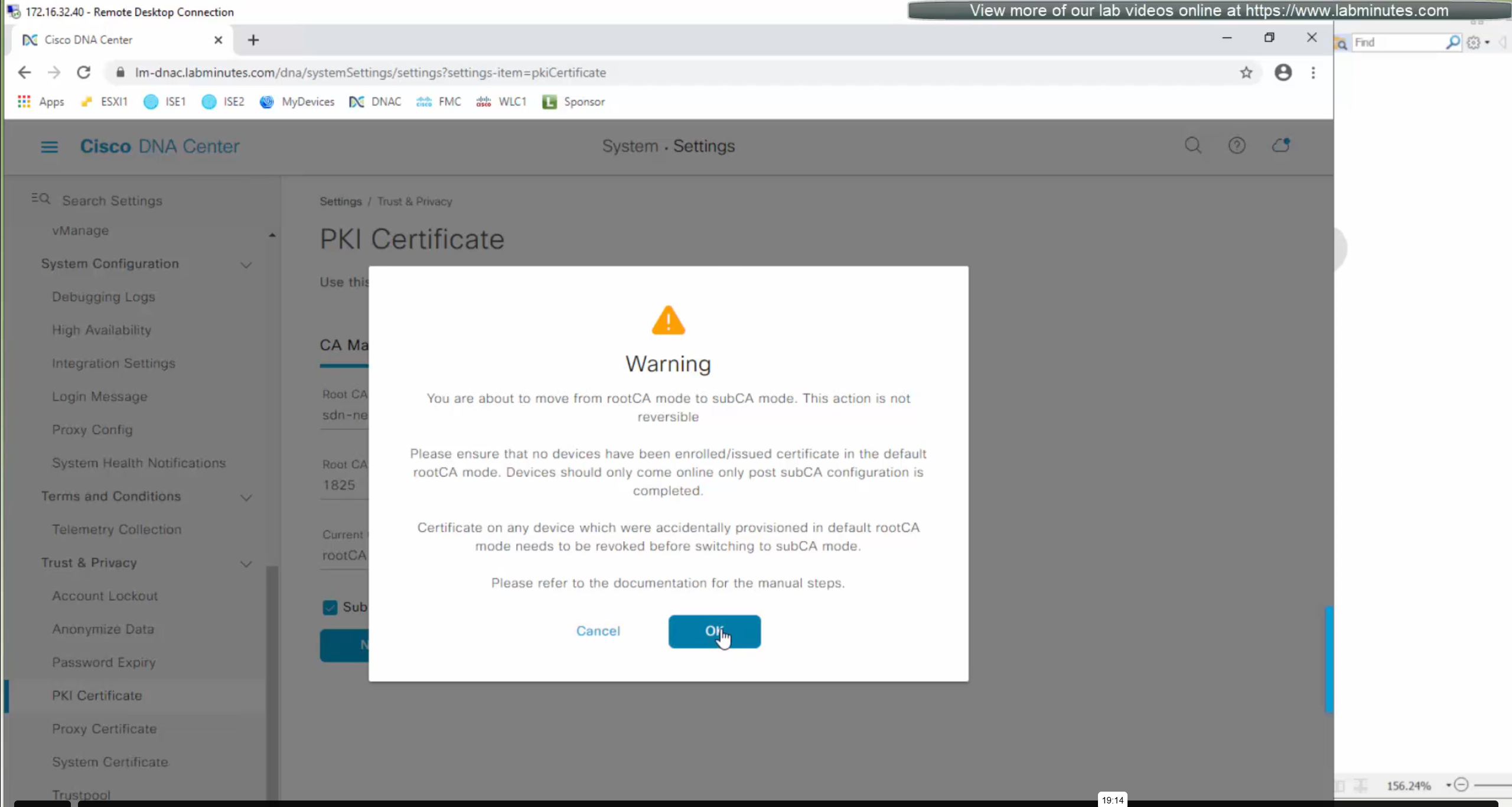
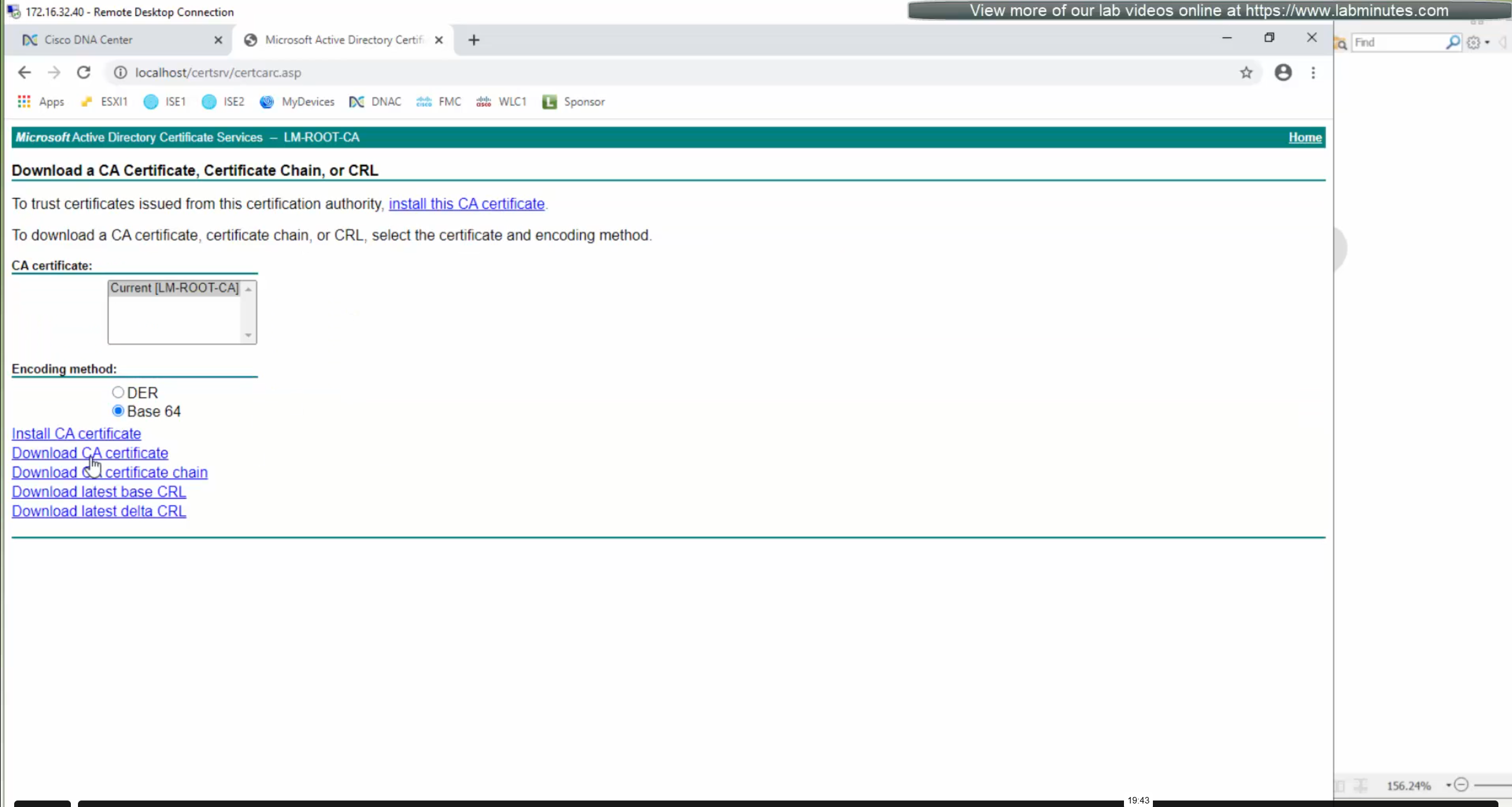
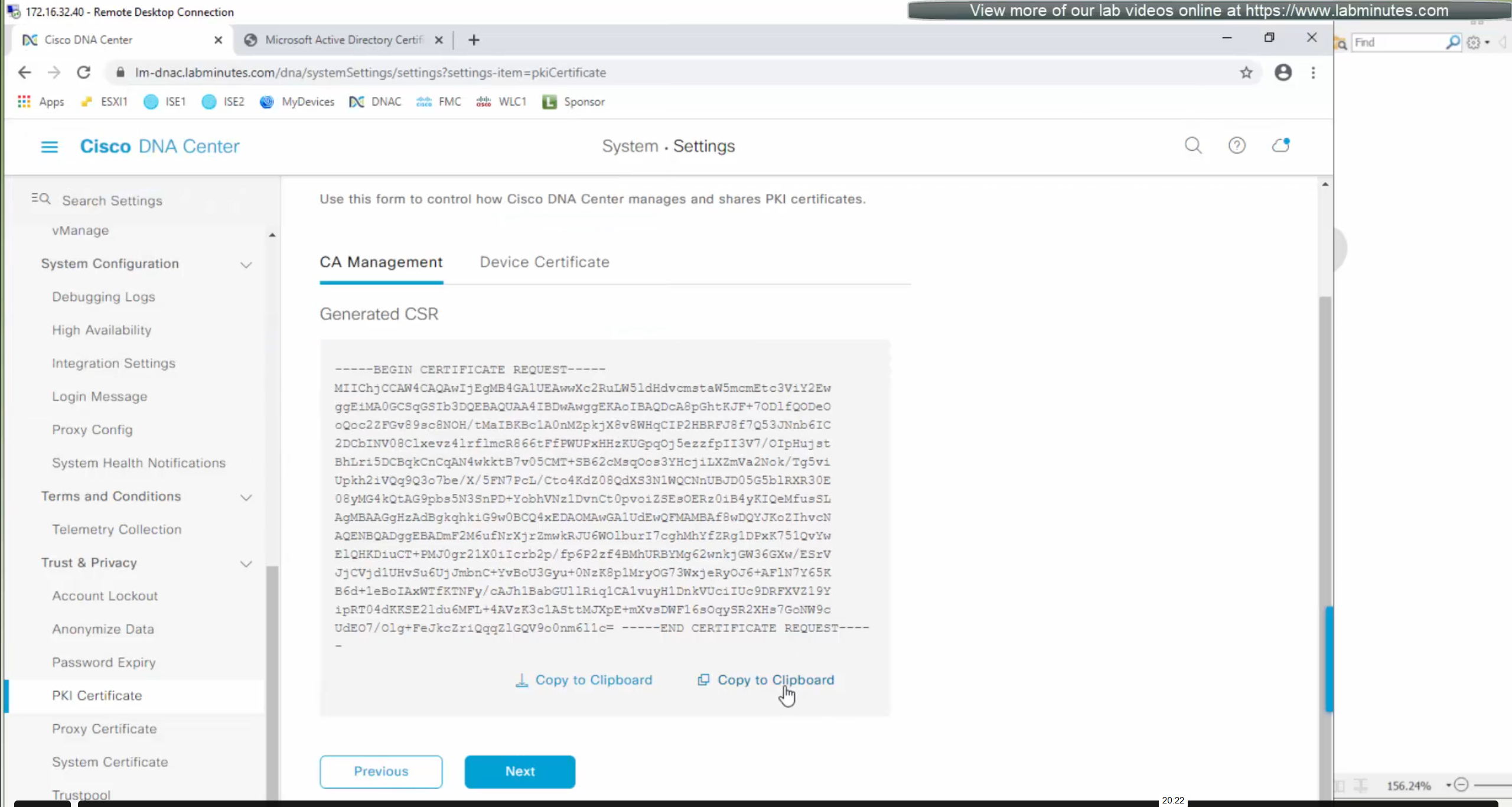





ISE is part of the SDA architecture by using RADIUS (Policy Server with mab and dot1x), TACACS and PXGrid
We need to have dot1x and mab authentication and
authorization configured in ISE
It used to be that ISE should not have TrustSec configuration configured, as config from DNAC will overwrite the existing config
But now if there is configuration conflict between ISE and DNAC then ISE configuration will take higher precedence
After integration, DNAC continues to poll ISE in order to keep trustsec configuration in sync
Integration between DNAC and ISE is very version specific so make sure you check documentation to see which version of ISE will integrate with which version of DNAC
Make sure that DNAC can reach ISE on ssh, and it is very important that GUI and CLI credentials are same
Also make sure that our ISE certificate has SAN entries for ISE IP and FQDN in ISE certificate


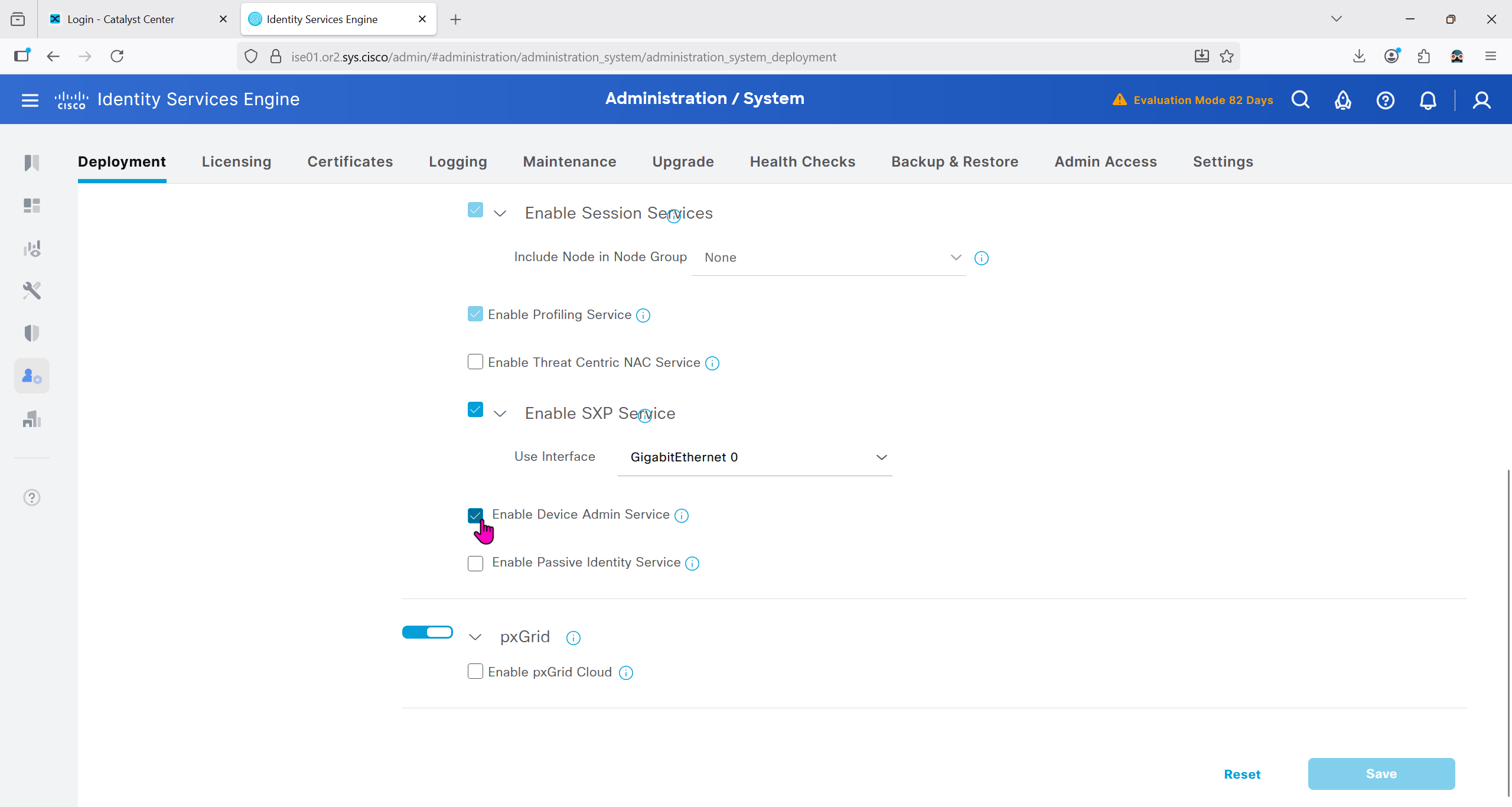


Make sure that when DNAC’s cert is presented it is trusted by ISE

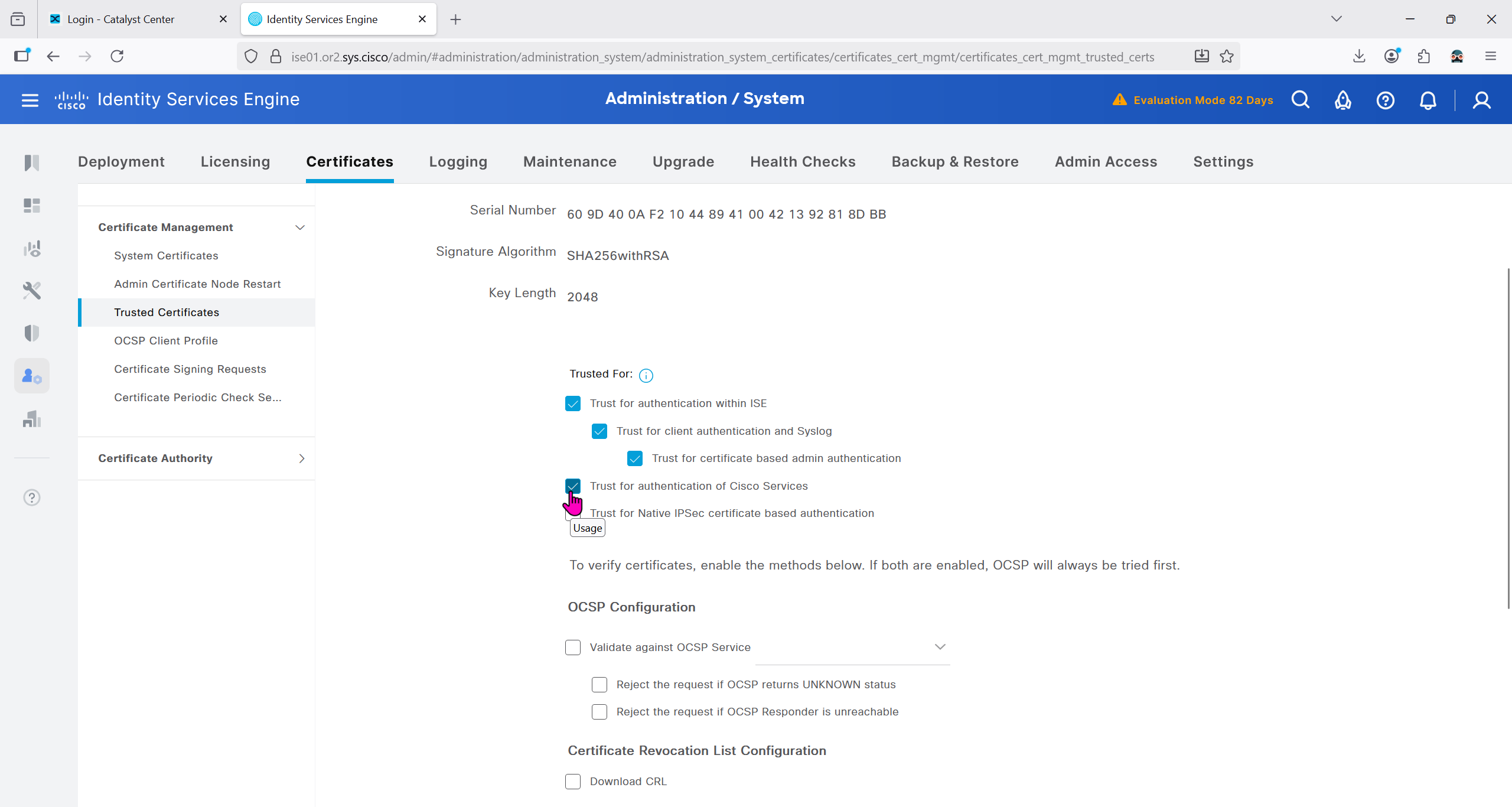
Because DNAC uses API to communicate with ISE, ERS needs to be enabled


Make sure PXgrid service is running
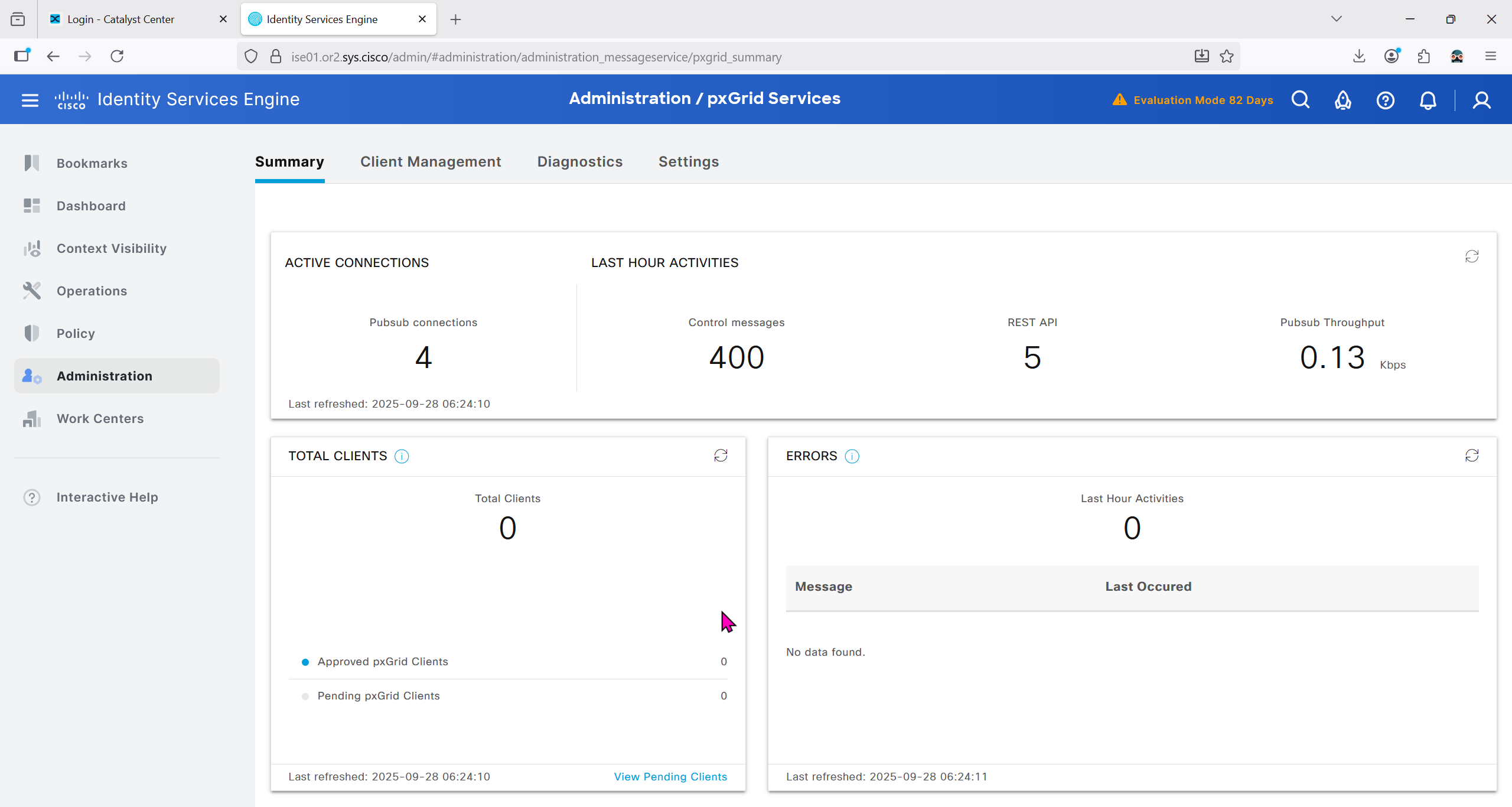
Currently in Client management we do not have any PXgrid clients yet
We will import the root ca cert in dnac so it can trust the certificate presented by ISE
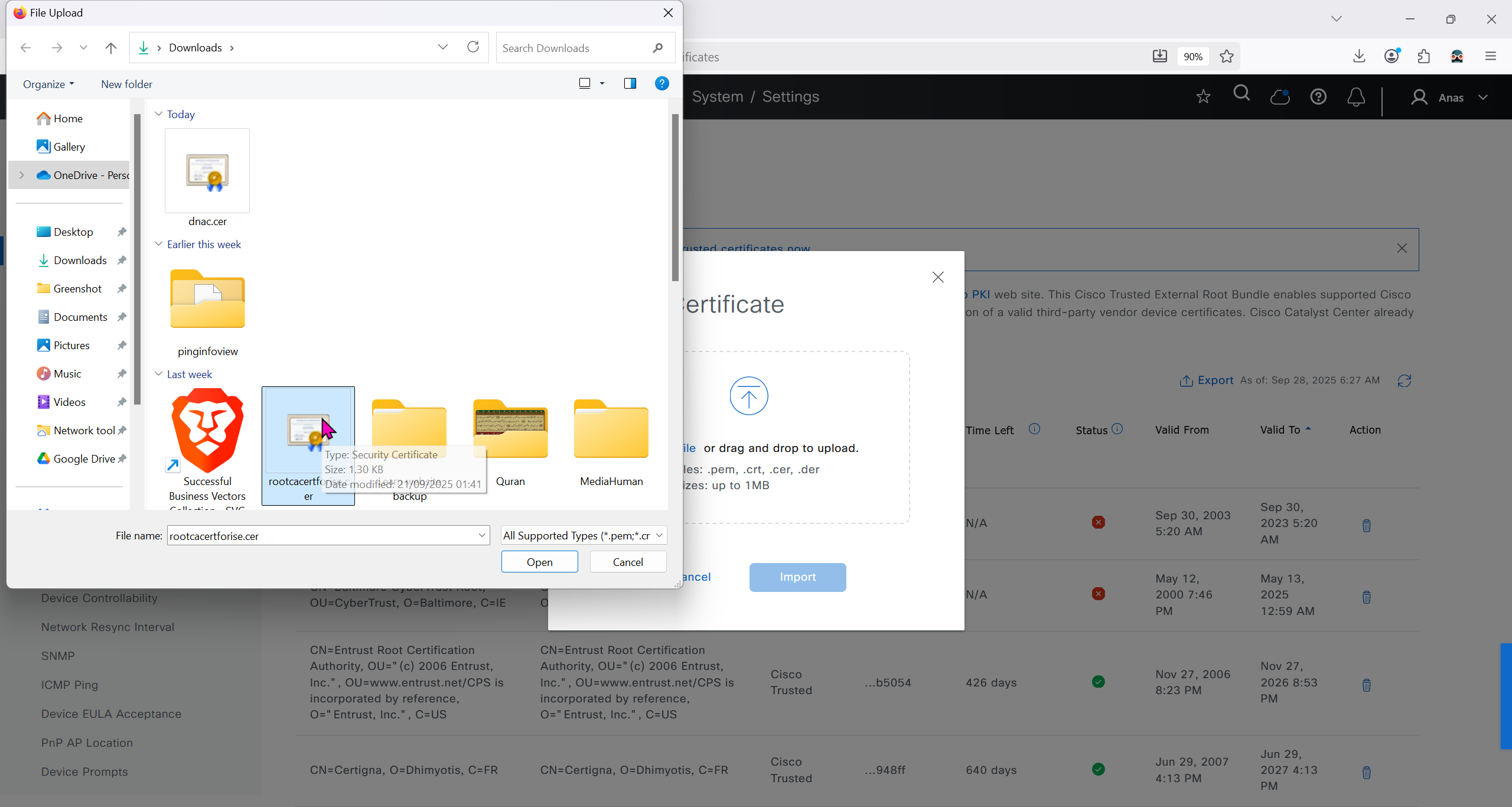
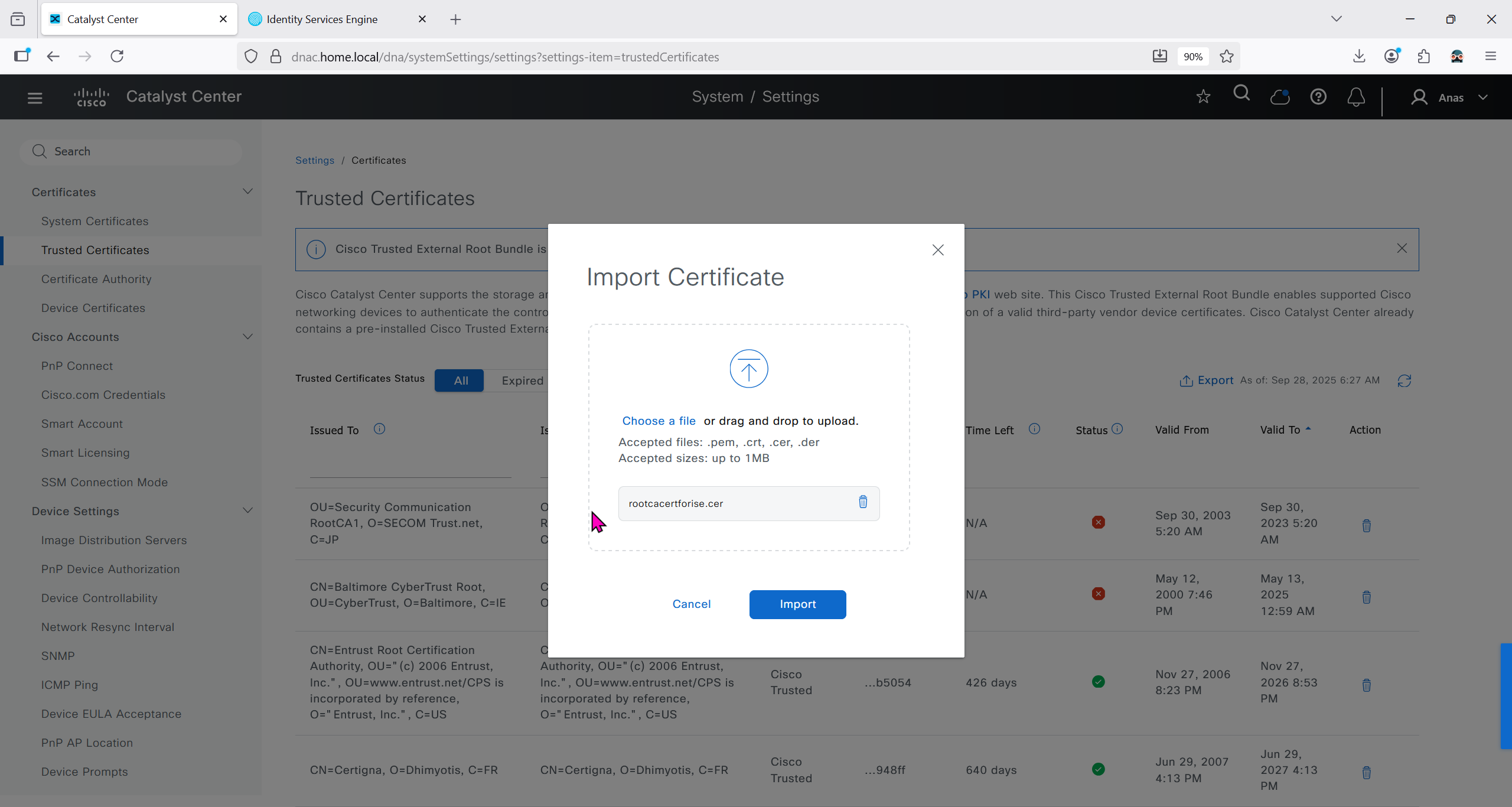

Make sure dnac can reach ise 172.16.32.12

Add ISE server 172.16.32.12 and this shared secret is the secret that will be used on catalyst devices which are added to dnac
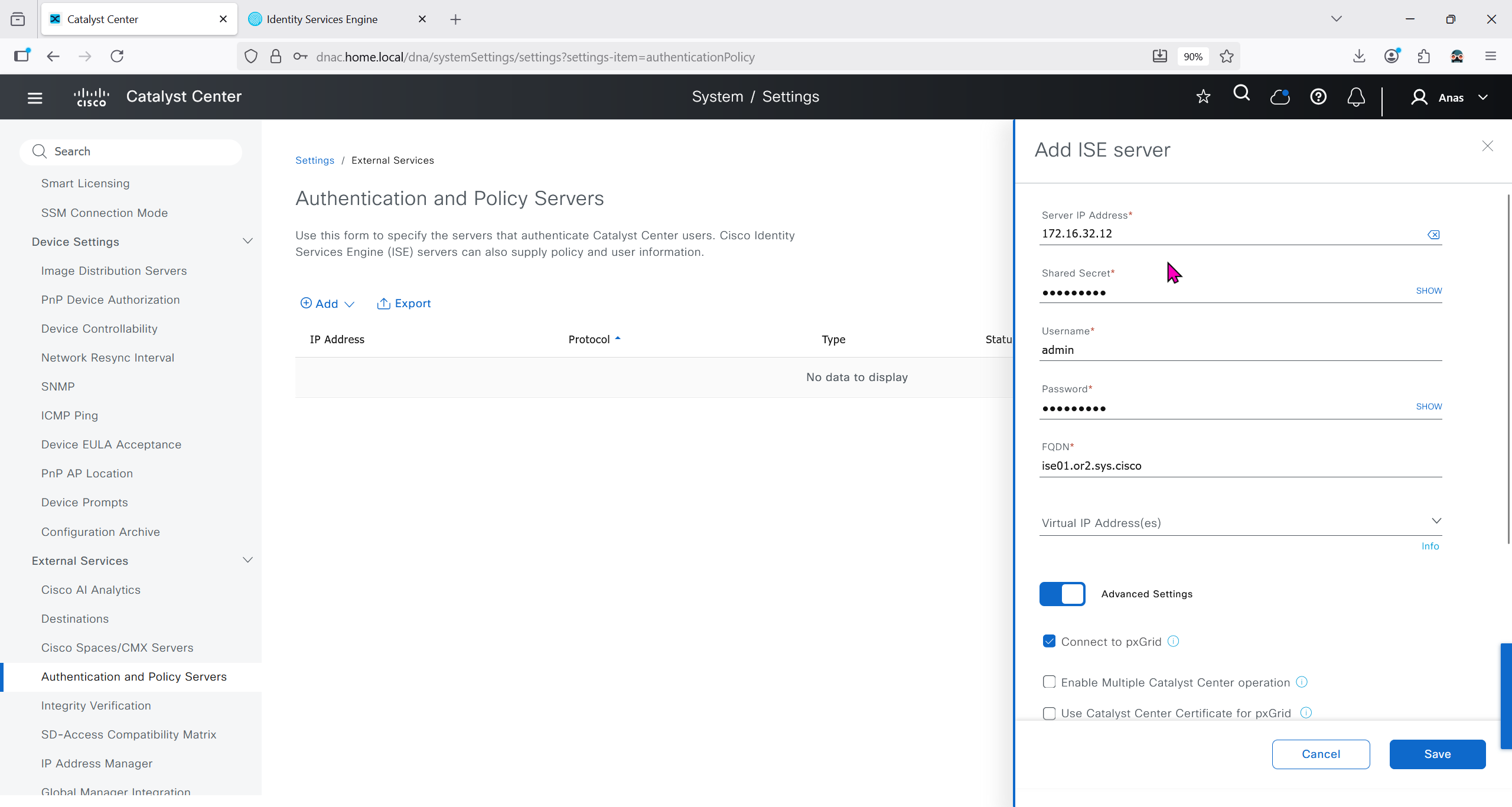
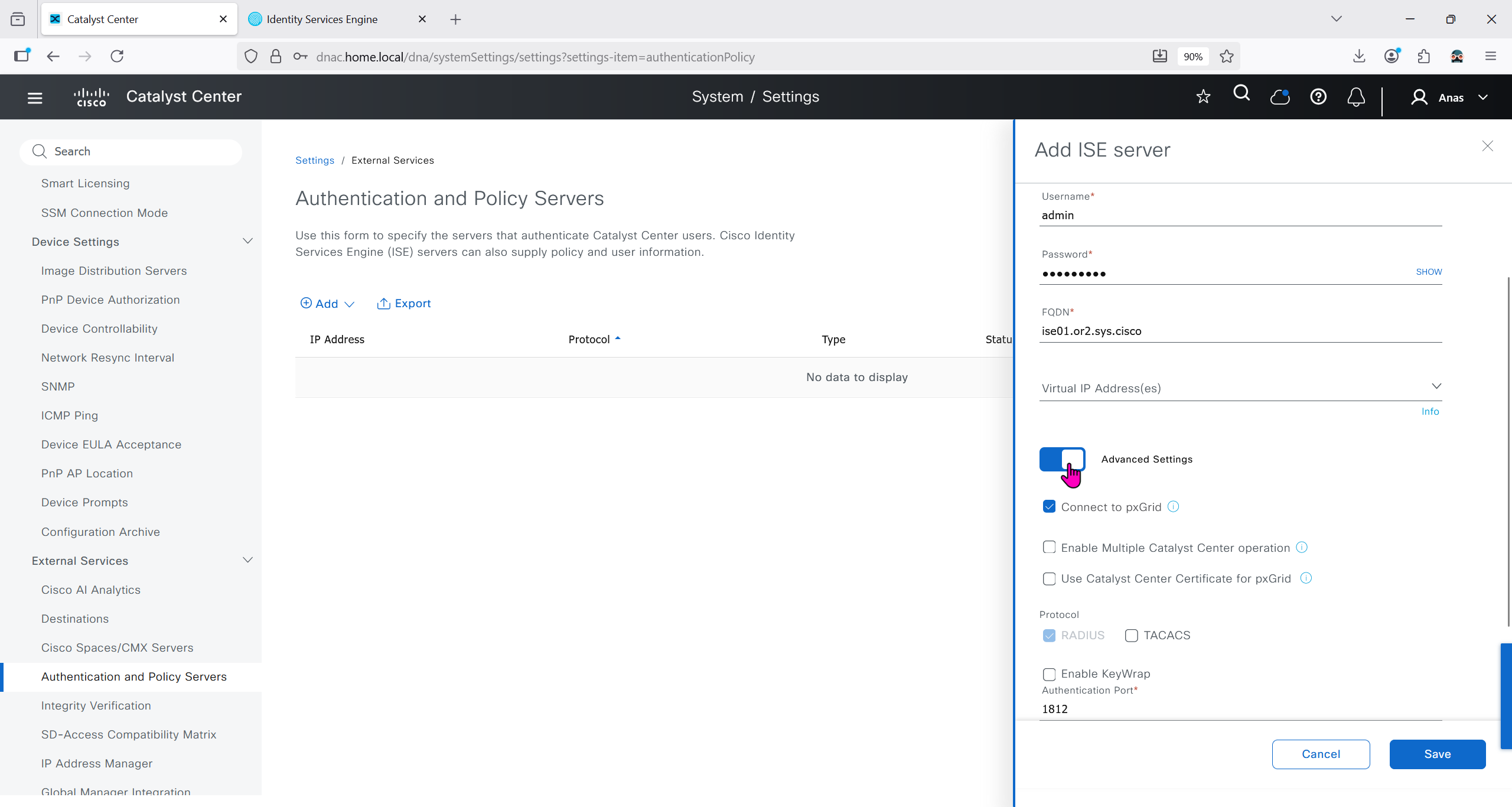
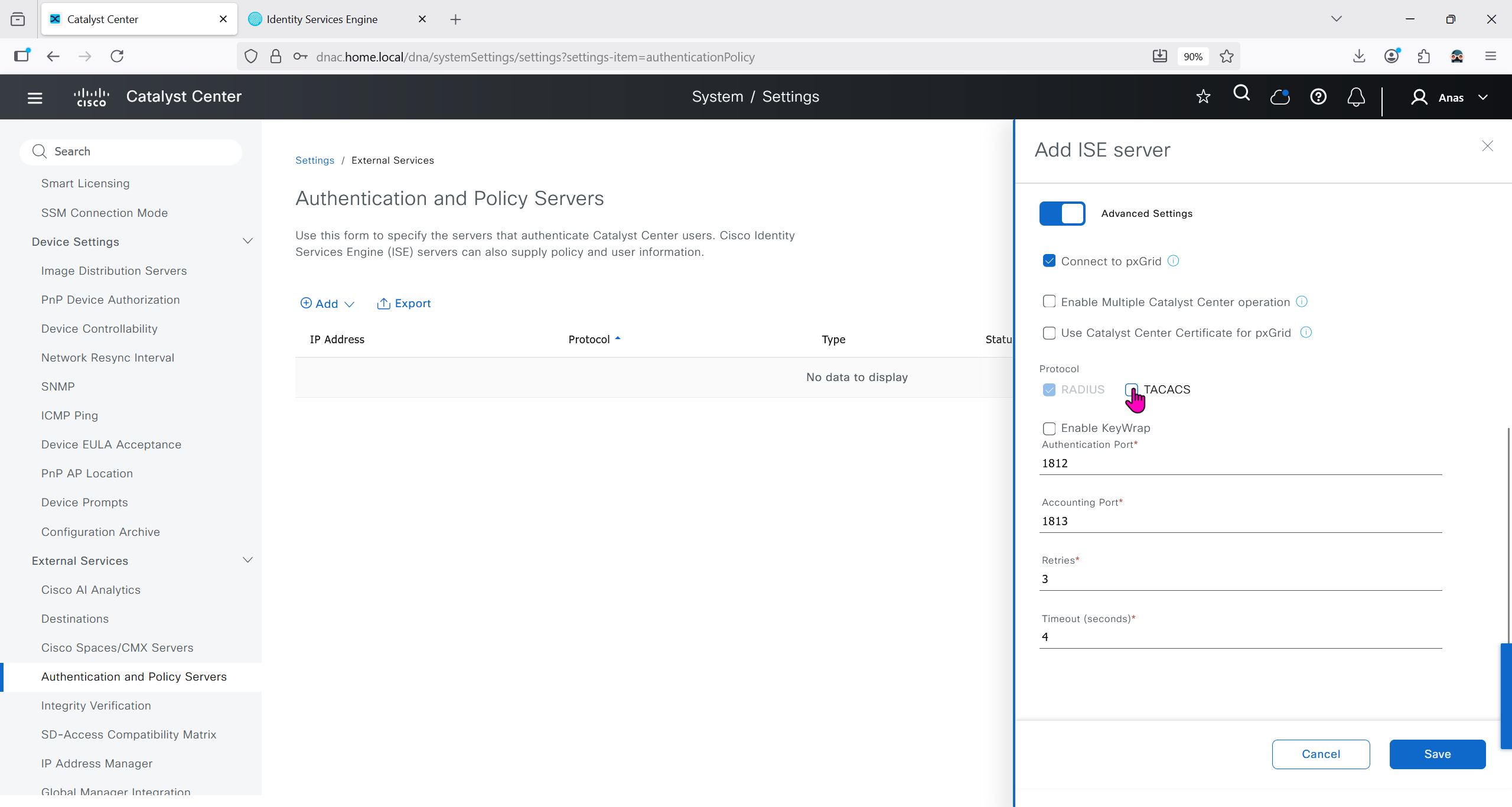
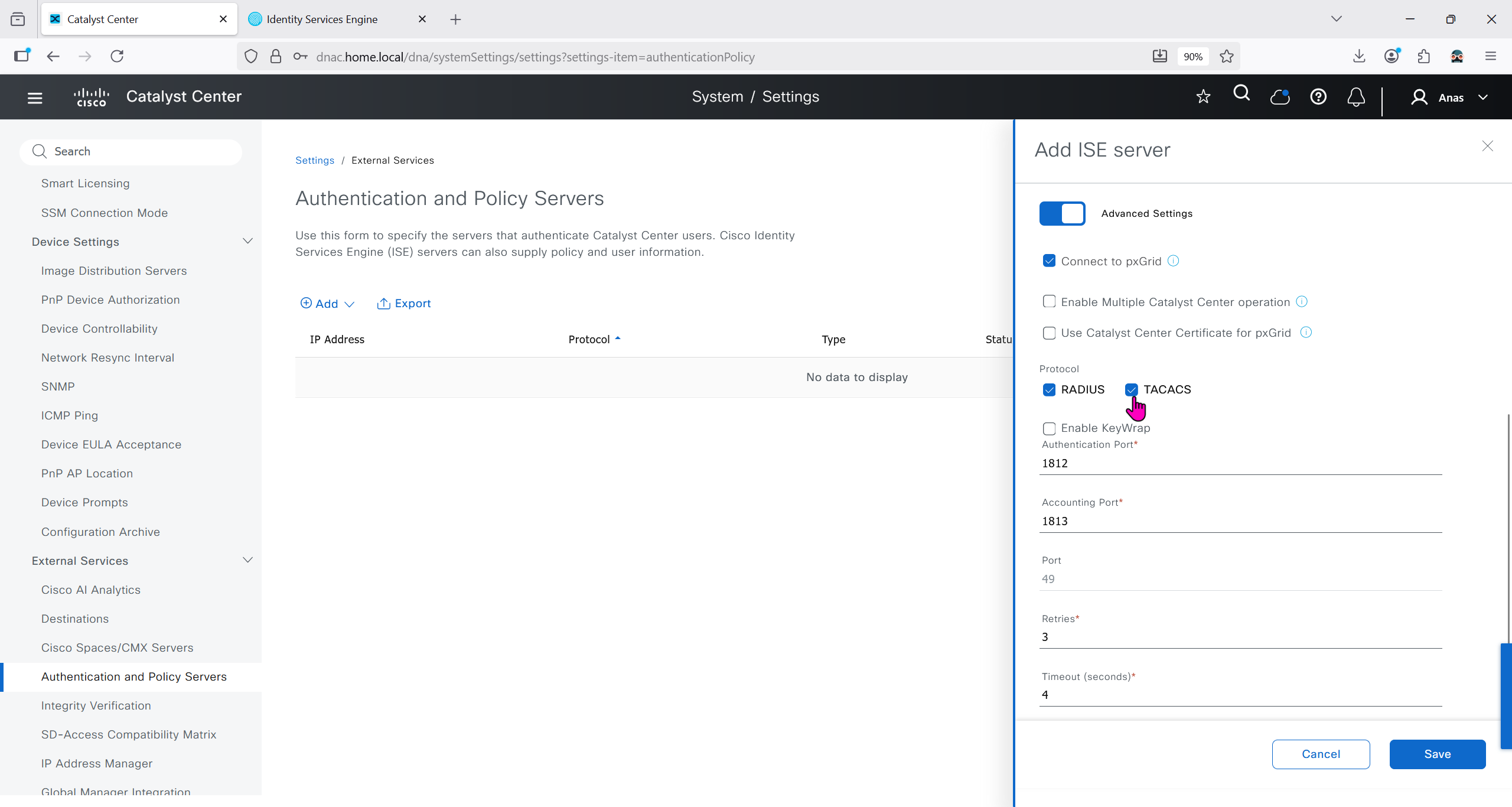

It should say IN PROGRESS and then it should move on to ACTIVE
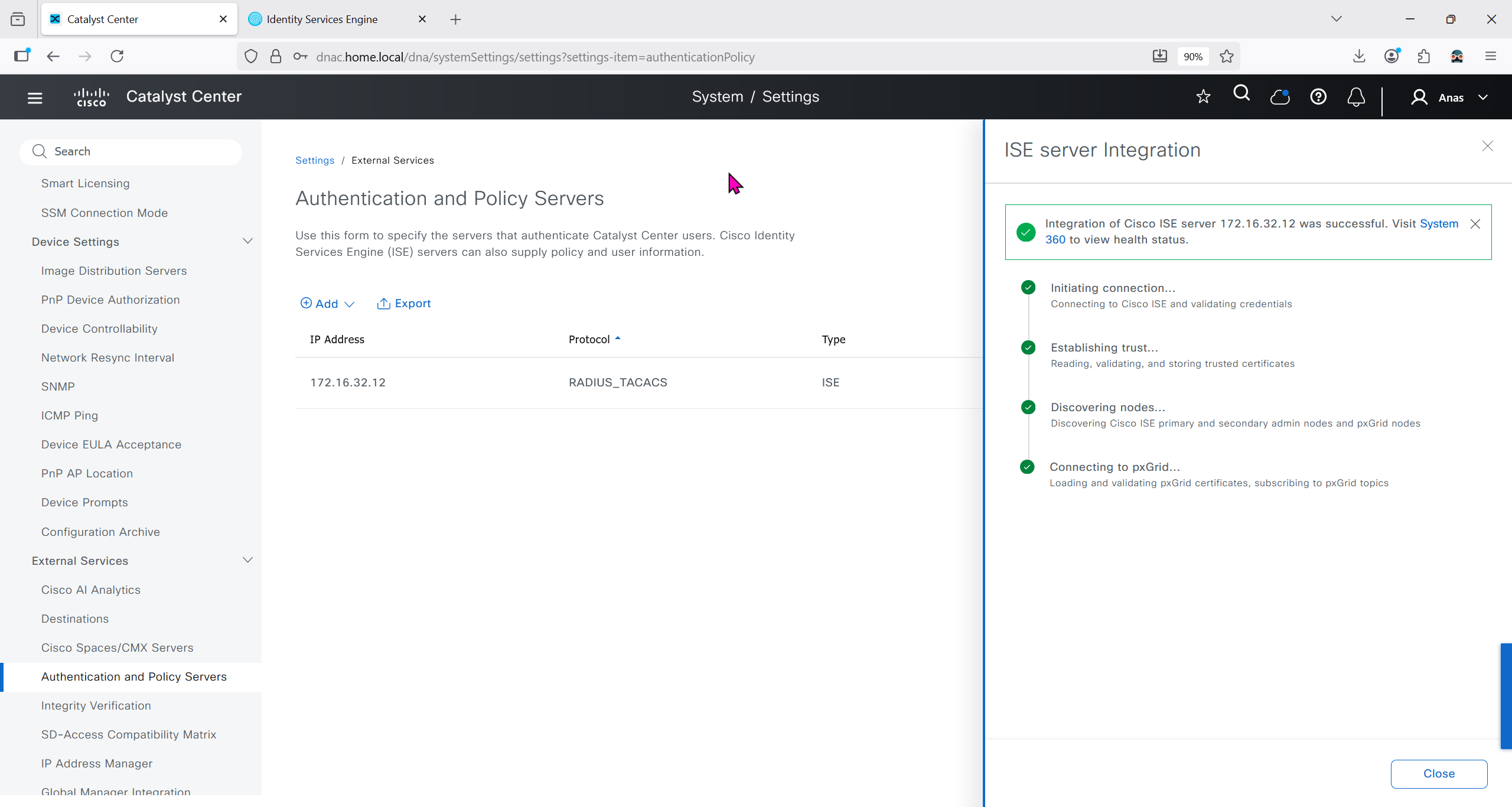
In ISE we will check Administration > pxgrid > summary for 1 client that is dnac

in pxgrid > client management, if dnac is showing pending then approve it




We should have installed Group based policy analytics, which we will do now
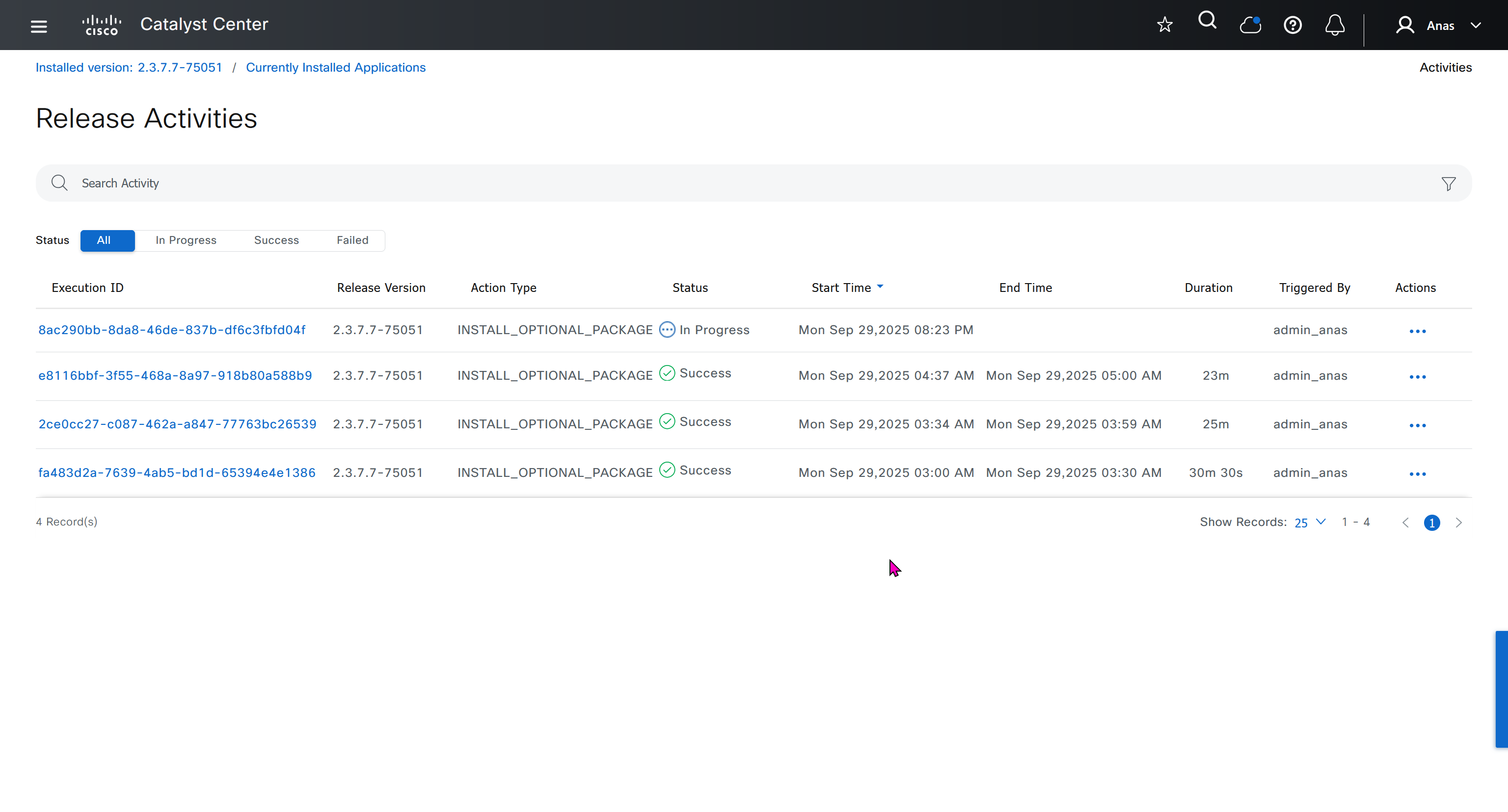

This message basically says to config sync between DNAC and ISE and use DNAC as the administration point for GBAC policy
In order to begin using Catalyst Center as the administration point for Group-Based Access Control, Catalyst Center must migrate policy data from the Cisco Identity Services Engine (ISE):
Any policy features in Cisco ISE that are currently not supported in Catalyst Center will not be migrated, you will have a chance to review the migration rule after click on "Start migration"
Any policy information in Catalyst Center not already exist in Cisco ISE will be copied to Cisco ISE to ensure the 2 sources are in syncOnce the data migration is initiated, you cannot use Group-Based Access Control in Catalyst Center until the operation is complete.
Start migration
After policy data migration has completed, if you prefer to manage Group-Based Access Control in Cisco Identity Services Engine, you can select that option under “Group-Based Access Control Configuration”.
We need to click on Start migration, Backup is recommended because this is a 2 way sync and configuration in ISE will also change if there is pre existing config in DNAC
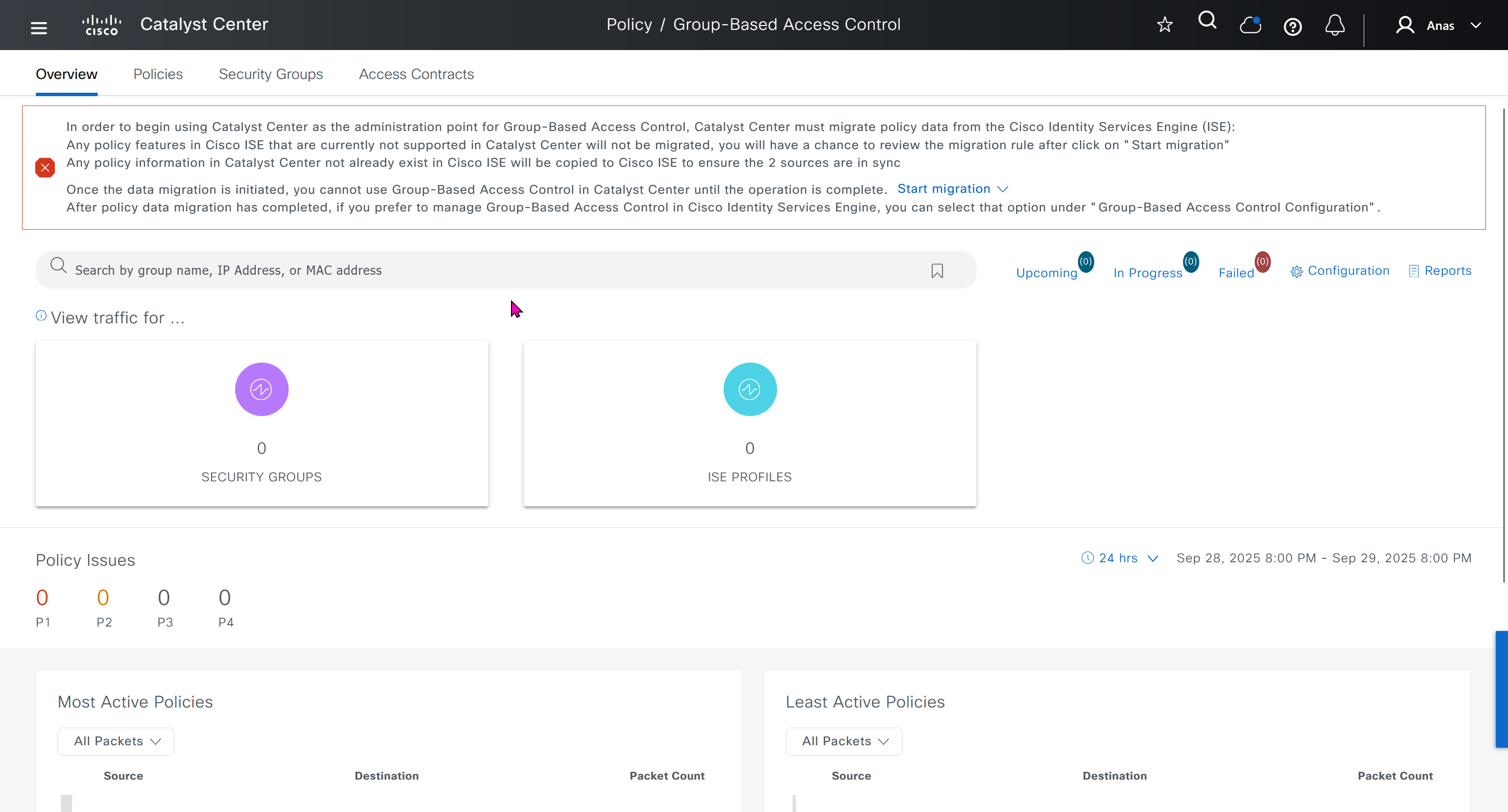
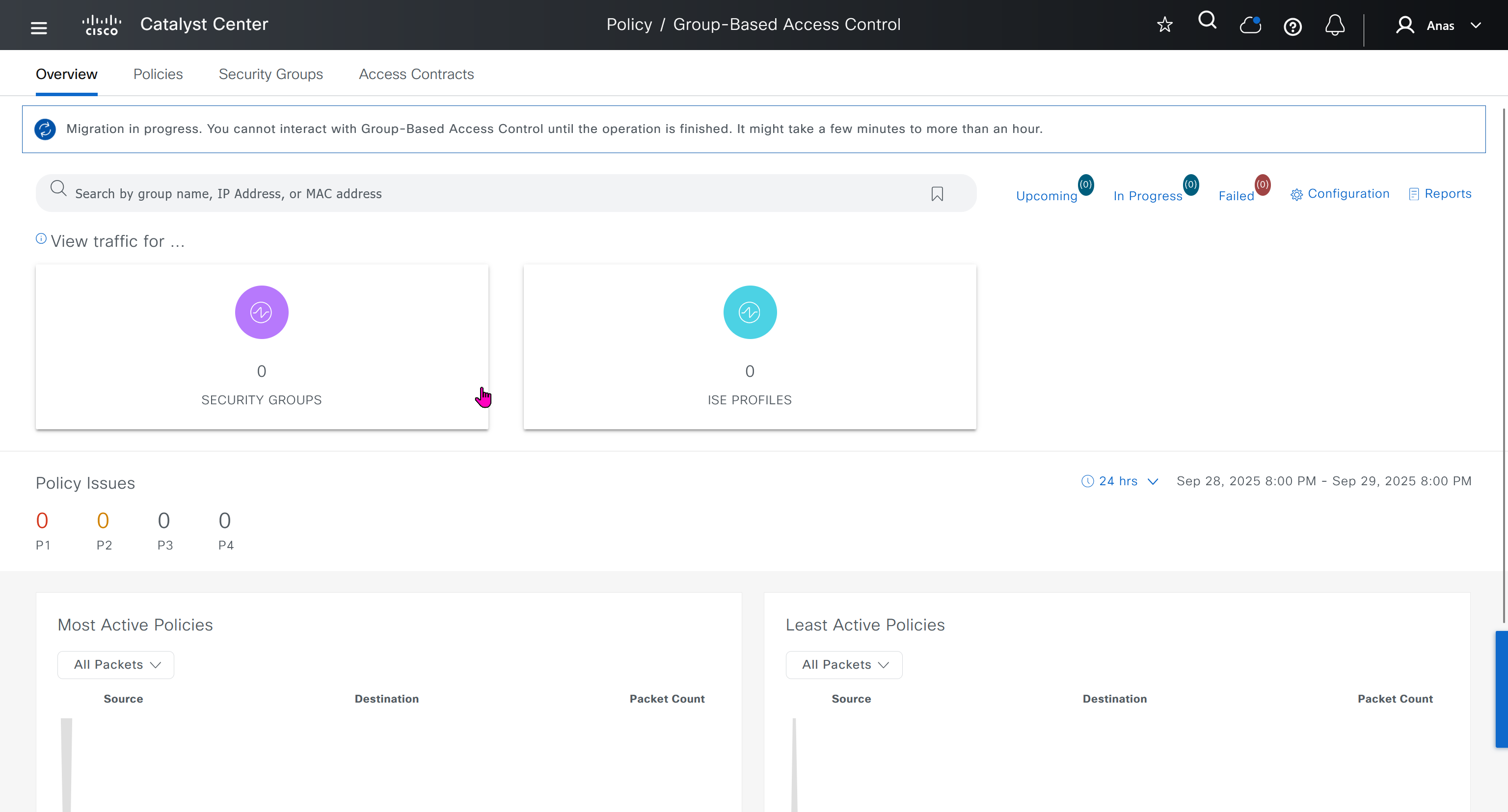
After migration DNAC has become the policy administration point and all changes should be made in ISE
“Migration is complete. Catalyst Center will be the policy administration point, and screens of Security Groups, Access Contracts and Policies in Cisco Identity Services Engine will be read-only. You can review the policy migration log, and/or change the administration mode in Group-Based Access Control Configurations”
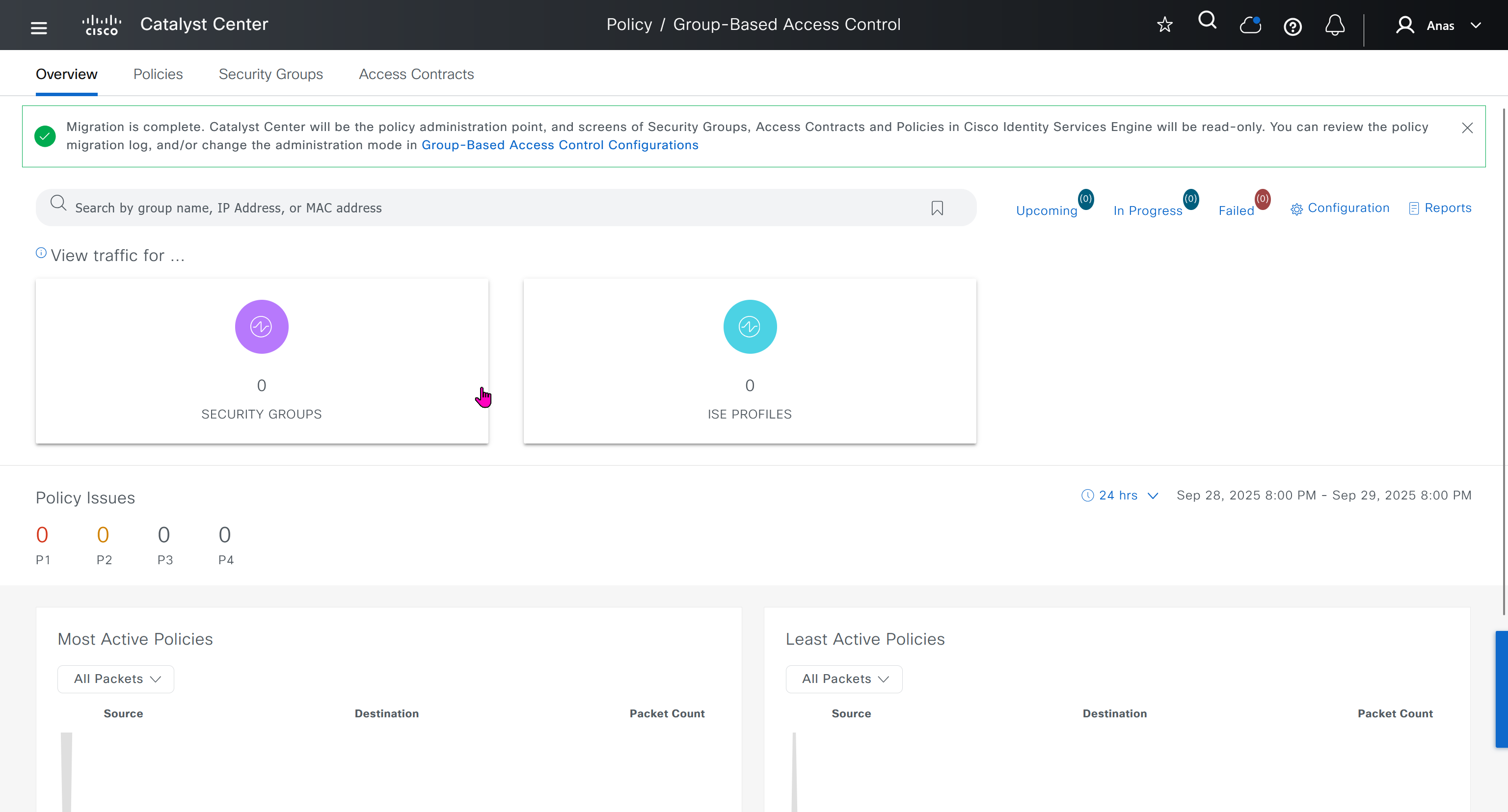
All these security groups have been downloaded into DNAC and any future configuration changes you make in DNAC will be reflected in ISE


next post
SDWAN commands
SDWAN commands
vsmart -
show omp routes
show omp route 192.168.33.0/24 | nomore
show license all > to check HSEC
show platform hardware throughput level > throughput levels licensed
show sdwan system > cli managed or vmanage managed
show sdwan control local-properties > certificate installed and token should be invalid
show sdwan control connection-history > what error code generated
show sdwan control connections > DTLS tunnels with SDWAN manager, controller and orches
show sdwan running—config > useful to check config and creating CLI template
show sdwan bfd sessions > check IPSEC tunnels to other TLOCs
show omp routes > omp routes
show sdwan omp routes > omp routes
show ip route vrf * > all sdwan and global routing table
show interface gig1 > check the service vpn interface
show interface gig2 > check the transport interface
show interface Tunn1 > check tunnel interface
show policy service-path vpn 1 interface Gi0/2 source-ip 192.168.33.1 dest-ip 192.168.44.1 protocol 1
show policy service-path vpn 1 interface Gi0/2 source-ip 192.168.33.1 dest-ip 192.168.44.1 protocol 1 all
show sdwan tunnel statistics
show processes cpu sorted
show platform hardware qfp active statistics drop
! drop statistics
! 'platform hardware' -> means ASIC
! 'qfp' -> means Quantum Flow Processor , This is Cisco’s hardware chip that processes packets at very high speed
! 'statistics' -> Counters and performance numbers
! 'drop' -> Packets that were discarded instead of being forwarded
show sdwan config-pull history
PROCESS
INDEX TIMESTAMP NAME TOTAL TIME RESULT FAIL REASON
----------------------------------------------------------------------------------
1 2025-04-30 12:13:18 pycfg-26502 0:00:02.547027 success -
2 2025-06-10 21:06:49 pycfg-17134 0:00:02.381984 success -
3 2025-06-10 21:13:47 pycfg-24614 0:00:02.234331 success -
4 2025-06-10 21:18:11 pycfg-29603 0:00:02.265134 success -
5 2025-06-10 21:31:13 pycfg-16327 0:00:02.295202 success -
6 2025-06-10 21:49:19 pycfg-1014 0:00:04.337417 failure commit-failure
7 2025-06-10 21:51:40 pycfg-3698 0:00:06.398463 success -
8 2025-06-10 21:57:49 pycfg-10648 0:00:06.921389 success -
9 2025-06-10 21:59:22 pycfg-13383 0:00:02.373731 success -
10 2025-06-10 22:02:32 pycfg-22890 0:00:07.149522 success -
11 2025-06-10 22:08:22 pycfg-29622 0:00:36.597725 success -
12 2025-06-11 22:38:01 pycfg-13695 0:00:07.507785 success -
13 2025-06-11 23:06:07 pycfg-14473 0:00:07.382631 success -
14 2025-06-11 23:26:44 pycfg-4645 0:00:02.468943 success -next post
SDA Deployment
SDA LISP Roles
ITR – Ingress Tunnel Router – devices which accepts traffic from the client and looks at transmitting to the destination.
ETR – Egress Tunnel Router – device which transmits traffic to the client, this is where destination client is attached.
These above roles of LISP would be on Fabric Edge node.
Example of Ping (I am omitting the full lookup against Map Resolver and RLOC etc):
Client A —> Switch A (ITR) —> Switch B (ETR) —> Client B
Reply:
Client A <— Switch A (ETR) <— Switch B (ITR) <— Client B
If a node has both roles ITR and ETR, that Fabric Edge switch is referenced as xTR
(P – Proxy) PITR and PETR would be the Border node which communicates with destinations outside the fabric, Similarly to the last example, one border node can have both roles and can be referenced as PxTR.
Traffic example: Client A —> Switch A (ITR) — Border A (PITR) —> Server A
Reply: Client A <— Switch A (ETR) <— Border A (PETR) <— Server A
ESXI and VCenter Deployment
-: Z840 :-
Upgrade BIOS
Factory Reset BIOS
set controller mode to AHCI from RAID
enable Intel VTd under System Security section
-: ESXI DEPLOYMENT :-
VMware-VMvisor-Installer-7.0.0-15843807.x86_64
ESXi 7.0 keys
JJ2WR-25L9P-H71A8-6J20P-C0K3F
ESXI01.home.local
192.168.0.10
root
C0mplex30-
-: VCENTER DEPLOYMENT :-
Create following entries in host file
192.168.0.10 esxi01.home.local <<<<
192.168.0.11 vcenter.home.local <<<< This is checked from local machine when running VCSA setup to install vcenter, this check is different from vcenter A and PTR record lookup by installer, that is why DNS server on Windows server 2016 is needed
Bring up a winserver 2016 instance in eveng metal and configure DNS server on it
VMware-VCSA-all-7.0.0-16386292.iso
vCenter 7 keys
406DK-FWHEH-075K8-XAC06-0JH08
VCENTER.home.local
192.168.0.11
root
C0mplex30-
administrator@vsphere.local
C0mplex30-
Import vcenter Certificates in Installation station
Because we are deploying appliance through VA launcher script, we need to import certificates of vcenter into local computer trusted root certificate’s store, go to https://vCenter_FQDN/certs/download.zip, download ZIP and extract all the certs and import them



Windows Server DNS deployment

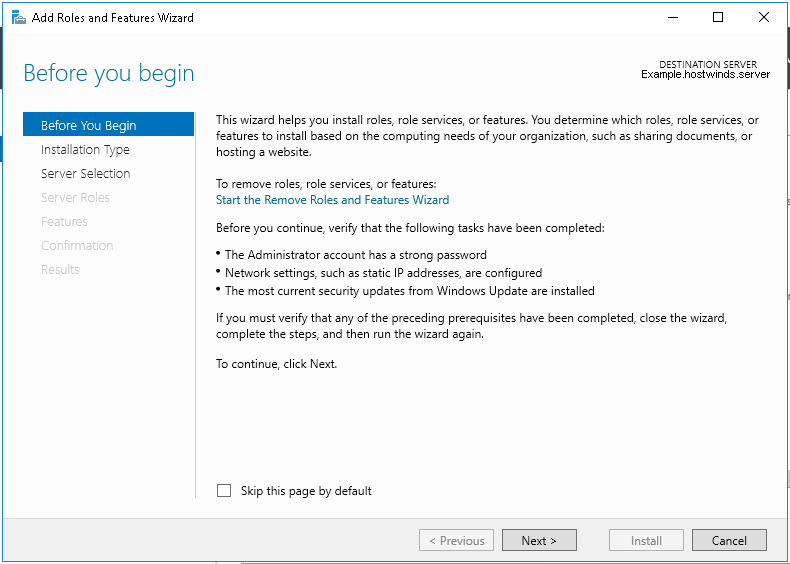

configure forward zone
configure reverse zone
create A record
vcenter.home.local 192.168.0.11
dnac.home.local 10.21.1.2
Windows 10 and VYOS deployment
Windows 10 VM
Create Windows 10 VM for VYOS deployment validation and internet access check
2 vCPUs
5GB RAM
25GB disk
admin/Test123
Pet name
dnac
City born in
dnac
City parents met
dnac
Assign only 192.168.0.200/24 and do not assign gateway 192.168.0.1
Disable IPv6 on the Windows VM interface
connect VM’s interface in vcenter
Go to Network folder and join the network
Share Downloads folder
copy wub and debloater to downloads folder
once all done then put network interface in DHCP again
VYOS deployment
2 CPUs
RAM 2 GB
4 GB Disk
! Install open-vm-tools on VY OS gateway
vyos@vy-gateway:~$ sudo vim /etc/apt/sources.list
! press esc to make sure we are in normal mode
! press i to go in insert mode
! enter first line
deb http://deb.debian.org/debian bullseye main contrib
! press escape
! enter ":wq"
vyos@vy-gateway:~$ sudo cat /etc/apt/sources.list
deb http://deb.debian.org/debian bullseye main contrib
! Update failed because of no DNS resolution
vyos@vy-gateway:~$ sudo apt update
Ign:1 http://deb.debian.org/debian bullseye InRelease
Ign:1 http://deb.debian.org/debian bullseye InRelease
Ign:1 http://deb.debian.org/debian bullseye InRelease
Err:1 http://deb.debian.org/debian bullseye InRelease
System error resolving 'deb.debian.org:http' - getaddrinfo (16: Device or resource busy)
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
All packages are up to date.
W: Failed to fetch http://deb.debian.org/debian/dists/bullseye/InRelease System error resolving 'deb.debian.org:http' - getaddrinfo (16: Device or resource busy)
W: Some index files failed to download. They have been ignored, or old ones used instead.
vyos@vy-gateway:~$ sudo bash
root@vy-gateway:/home/vyos# sudo bash -c 'cat > /etc/resolv.conf <<EOF
nameserver 8.8.8.8
nameserver 1.1.1.1
EOF'
root@vy-gateway:/home/vyos# cat /etc/resolv.conf
nameserver 8.8.8.8
nameserver 1.1.1.1
root@vy-gateway:/home/vyos# apt update
Get:1 http://deb.debian.org/debian bullseye InRelease [75.1 kB]
Get:2 http://deb.debian.org/debian bullseye/main amd64 Packages [8,066 kB]
Get:3 http://deb.debian.org/debian bullseye/main Translation-en [6,235 kB]
Get:4 http://deb.debian.org/debian bullseye/contrib amd64 Packages [50.4 kB]
Get:5 http://deb.debian.org/debian bullseye/contrib Translation-en [46.9 kB]
Fetched 14.5 MB in 4s (4,084 kB/s)
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
8 packages can be upgraded. Run 'apt list --upgradable' to see them.
! install should work now
root@vy-gateway:/home/vyos# apt install -y open-vm-tools
Reading package lists... Done
Building dependency tree... Done
Reading state information... Done
The following additional packages will be installed:
libdrm-common libdrm2 libmspack0 libssl1.1 libxmlsec1 libxmlsec1-openssl
libxslt1.1
Suggested packages:
open-vm-tools-desktop cloud-init
Recommended packages:
zerofree
The following NEW packages will be installed:
libdrm-common libdrm2 libmspack0 libssl1.1 libxmlsec1 libxmlsec1-openssl
libxslt1.1 open-vm-tools
0 upgraded, 8 newly installed, 0 to remove and 8 not upgraded.
Need to get 2,793 kB of archives.
After this operation, 8,598 kB of additional disk space will be used.
Get:1 http://deb.debian.org/debian bullseye/main amd64 libdrm-common all 2.4.104-1 [14.9 kB]
Get:2 http://deb.debian.org/debian bullseye/main amd64 libdrm2 amd64 2.4.104-1 [41.5 kB]
Get:3 http://deb.debian.org/debian bullseye/main amd64 libmspack0 amd64 0.10.1-2 [50.3 kB]
Get:4 http://deb.debian.org/debian bullseye/main amd64 libssl1.1 amd64 1.1.1w-0+deb11u1 [1,566 kB]
Get:5 http://deb.debian.org/debian bullseye/main amd64 libxslt1.1 amd64 1.1.34-4+deb11u1 [240 kB]
Get:6 http://deb.debian.org/debian bullseye/main amd64 libxmlsec1 amd64 1.2.31-1 [149 kB]
Get:7 http://deb.debian.org/debian bullseye/main amd64 libxmlsec1-openssl amd64 1.2.31-1 [100.0 kB]
Get:8 http://deb.debian.org/debian bullseye/main amd64 open-vm-tools amd64 2:11.2.5-2+deb11u3 [632 kB]
Fetched 2,793 kB in 0s (10.4 MB/s)
Preconfiguring packages ...
Selecting previously unselected package libdrm-common.
(Reading database ... 84389 files and directories currently installed.)
Preparing to unpack .../0-libdrm-common_2.4.104-1_all.deb ...
Unpacking libdrm-common (2.4.104-1) ...
Selecting previously unselected package libdrm2:amd64.
Preparing to unpack .../1-libdrm2_2.4.104-1_amd64.deb ...
Unpacking libdrm2:amd64 (2.4.104-1) ...
Selecting previously unselected package libmspack0:amd64.
Preparing to unpack .../2-libmspack0_0.10.1-2_amd64.deb ...
Unpacking libmspack0:amd64 (0.10.1-2) ...
Selecting previously unselected package libssl1.1:amd64.
Preparing to unpack .../3-libssl1.1_1.1.1w-0+deb11u1_amd64.deb ...
Unpacking libssl1.1:amd64 (1.1.1w-0+deb11u1) ...
Selecting previously unselected package libxslt1.1:amd64.
Preparing to unpack .../4-libxslt1.1_1.1.34-4+deb11u1_amd64.deb ...
Unpacking libxslt1.1:amd64 (1.1.34-4+deb11u1) ...
Selecting previously unselected package libxmlsec1:amd64.
Preparing to unpack .../5-libxmlsec1_1.2.31-1_amd64.deb ...
Unpacking libxmlsec1:amd64 (1.2.31-1) ...
Selecting previously unselected package libxmlsec1-openssl:amd64.
Preparing to unpack .../6-libxmlsec1-openssl_1.2.31-1_amd64.deb ...
Unpacking libxmlsec1-openssl:amd64 (1.2.31-1) ...
Selecting previously unselected package open-vm-tools.
Preparing to unpack .../7-open-vm-tools_2%3a11.2.5-2+deb11u3_amd64.deb ...
Unpacking open-vm-tools (2:11.2.5-2+deb11u3) ...
Setting up libssl1.1:amd64 (1.1.1w-0+deb11u1) ...
Setting up libmspack0:amd64 (0.10.1-2) ...
Setting up libxslt1.1:amd64 (1.1.34-4+deb11u1) ...
Setting up libxmlsec1:amd64 (1.2.31-1) ...
Setting up libdrm-common (2.4.104-1) ...
Setting up libxmlsec1-openssl:amd64 (1.2.31-1) ...
Setting up libdrm2:amd64 (2.4.104-1) ...
Setting up open-vm-tools (2:11.2.5-2+deb11u3) ...
Created symlink /etc/systemd/system/vmtoolsd.service → /lib/systemd/system/open-vm-tools.service.
Created symlink /etc/systemd/system/multi-user.target.wants/open-vm-tools.service → /lib/systemd/system/open-vm-tools.service.
Created symlink /etc/systemd/system/open-vm-tools.service.requires/vgauth.service → /lib/systemd/system/vgauth.service.
Processing triggers for libc-bin (2.36-9+deb12u10) ...
localepurge: Disk space freed: 0 KiB in /usr/share/locale
localepurge: Disk space freed: 0 KiB in /usr/share/man
localepurge: Disk space freed: 0 KiB in /usr/share/aptitude
localepurge: Disk space freed: 0 KiB in /usr/share/vim/vim90/lang
Total disk space freed by localepurge: 0 KiB
root@vy-gateway:/home/vyos#vyos/C0mplex30
Install from live image
install image
show configuration
show configuration commands
configure
set interfaces ethernet eth0 address '192.168.0.12/24'
set interfaces ethernet eth0 description 'home'
set interfaces ethernet eth1 address '172.16.25.1/24'
set interfaces ethernet eth1 description 'mgmt'
set interfaces ethernet eth2 address '10.21.1.1/24'
set interfaces ethernet eth2 description 'data'
show interface ethernet
show interface ethernet eth0
show interface ethernet eth0 physical
set protocols static route 0.0.0.0/0 next-hop 192.168.0.1 distance '1'
set service ssh port '22'
set system host-name 'vy-gateway'
commit
save vcenter
edit host and create a new standard switch and call it mgmt
edit host and create a new standard switch and call it data
add 2nd interface for vy-gateway into mgmt
add 3rd interface for vy-gateway into data

home router
Add routes for networks 10.21.1.0/24 and 172.16.25.0/24

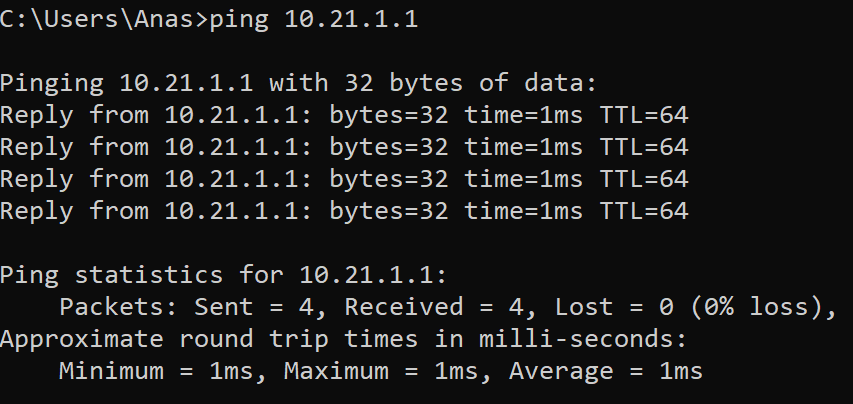
vyos routing is reachable
Cisco Catalyst Center 2.3.7.x on ESXi Deployment – Part 1
Virtual Machine Minimum Requirements
| Feature | Description |
|---|---|
| Virtualization platform and hypervisor | VMware vSphere (which includes ESXi and vCenter Server) 7.0.x or later, including all patches. |
| Processors | Intel Xeon Scalable server processor (Cascade Lake or newer) or AMD EPYC Gen2 with 2.1 GHz or better clock speed.32 vCPUs with 64-GHz reservation must be dedicated to the VM. |
| Memory | 256-GB DRAM with 256-GB reservation must be dedicated to the VM. |
| Storage | 3-TB solid-state drive (SSD).If you plan to create backups of your virtual appliance, also reserve additional datastore space. For information, see “Backup Server Requirements” in the Cisco Catalyst Center on ESXi Administrator Guide. |
| I/O Bandwidth | 180 MB/sec. |
| Input/output operations per second (IOPS) rate | 2000-2500, with less than 5 ms of I/O completion latency. |
| Latency | Catalyst Center on ESXi to network device connectivity: 200 ms. |
Scale numbers are different
for example maximum number of devices supported in non-fabric deployment is 1000 and maximum number of devices in fabric deployment is 2000, for more info
https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/network-automation-and-management/catalyst-center/catalyst-center-va/esxi/2-3-7/deployment-guide/b_cisco_catalyst_center_237x_on_esxi_deployment_guide.html
Cisco Catalyst Assurance uses near real-time streaming analytics, which requires heavy resource usage. When operating Catalyst Center on ESXi close to maximum scale, this functionality may be impacted by uncontrolled external events, such as host resource oversubscriptions and edge use cases that result in a resource usage spike. A number of things can indicate that these events are taking place, such as slow performance, data processing gaps, high I/O latency, and a CPU readiness percentage that’s higher than normal.
Catalyst Center VM can be deployed using Catalyst Center VA Launcher
Import the IdenTrust Certificate Chain
The Catalyst Center on ESXi OVA file is signed with an IdenTrust CA certificate, which is not included in VMware’s default truststore. As a result, the Deploy OVF Template wizard’s Review details page will indicate that you are using an invalid certificate while completing the wizard. You can prevent this by importing the IdenTrust certificate chain to the host or cluster on which you want to deploy the OVA file.

Cat center requires access to following URLs during install
| In order to… | …Catalyst Center on ESXi must access these URLs and FQDNs |
|---|---|
| Download updates to the system and application package software; submit user feedback to the product team. | Recommended: *.ciscoconnectdna.com:4431Customers who want to avoid wildcards can specify these URLs instead:https://www.ciscoconnectdna.comhttps://cdn.ciscoconnectdna.comhttps://registry.ciscoconnectdna.comhttps://registry-cdn.ciscoconnectdna.com |
| Catalyst Center on ESXi update package. | https://*.ciscoconnectdna.com/**.cloudfront.net*.tesseractcloud.com |
| Smart Account and SWIM software downloads. | https://apx.cisco.comhttps://cloudsso.cisco.com/as/token.oauth2https://*.cisco.com/*https://download-ssc.cisco.com/ |
| Authenticate with the cloud domain. | https://dnaservices.cisco.com |
| Integrate with ThousandEyes. | *.awsglobalaccelerator.comapi.thousandeyes.com |
| Manage Cisco Enterprise Network Function Virtualization Infrastructure Software (NFVIS) devices. | *.amazonaws.com |
| Collect product telemetry. | https://data.pendo.io |
| Allow API calls to enable access to Cisco CX Cloud Success Tracks. Otherwise, the enhancements made to extended configuration-based scanning for the Security Advisories, Bug Identifier, and EOX features that Machine Reasoning Engine (MRE) supports will not operate as expected. | https://api-cx.cisco.com |
| Integrate with Webex. | http://analytics.webexapis.comhttps://webexapis.com |
| User feedback. | https://dnacenter.uservoice.com |
| Integrate with Cisco Meraki. | Recommended: *.meraki.com:443Customers who want to avoid wildcards can specify these URLs instead:dashboard.meraki.com:443api.meraki.com:443n63.meraki.com:443 |
| Check SSL/TLS certificate revocation status using OCSP/CRL. | http://validation.identrust.com/crl/hydrantidcao1.crlhttp://commercial.ocsp.identrust.comNote These URLs should be reachable both directly and through the proxy server that’s configured for Catalyst Center. |
| Allow Cisco authorized specialists to collect troubleshooting data when Catalyst Center on ESXi Remote Support functionality is enabled. | wss://prod.radkit-cloud.cisco.com:443 |
| Integrate with cisco.com and Cisco Smart Licensing. | *.cisco.com:443Customers who want to avoid wildcards can specify these URLs instead:software.cisco.comcloudsso.cisco.comcloudsso1.cisco.comcloudsso2.cisco.comapiconsole.cisco.comapi.cisco.comapx.cisco.comsso.cisco.comapmx-prod1-vip.cisco.comapmx-prod2-vip.cisco.comtools.cisco.comtools1.cisco.comtools2.cisco.comsmartreceiver.cisco.com |
| Connect to the Network-Based Application Recognition (NBAR) cloud. | prod.sdavc-cloud-api.com:443 |
| Render accurate information in site and location maps. | www.mapbox.com*.tiles.mapbox.com/* :443. For a proxy, the destination is *.tiles.mapbox.com/* |
| For Cisco AI Network Analytics data collection, configure your network or HTTP proxy to allow outbound HTTPS (TCP 443) access to the cloud hosts. | https://api.use1.prd.kairos.ciscolabs.com (US East Region)https://api.euc1.prd.kairos.ciscolabs.com (EU Central Region) |
| Access a menu of interactive help flows that let you complete specific tasks from the GUI. | https://ec.walkme.com |
| Access the licensing service. | https://swapi.cisco.com |
| Integrate with Cisco Spaces. | https://dnaspaces.iohttps://dnaspaces.euhttps://ciscospaces.sg |
ciscoconnectdna.com is a cisco domain
Windows server NTP server
https://www.domat-int.com/en/how-to-configure-a-local-ntp-server
https://docs.litmus.io/litmusedge/product-features/system/network/configure-dns-ntp-servers/configure-local-ntp-server
Configure the Windows Time Service
In the File Explorer, navigate to: Control Panel\System and Security\Administrative Tools
Double-click Services. This same task can be completed by entering services.msc in the Windows Run dialog (Windows Key + R).

In the Services list, right-click on Windows Time and click Stop.
Note: The Windows Time service may already be stopped. In this case, skip this step and go to the next step to Update the Windows Registry

Update the Windows Registry to Create a Local NTP Service
Launch Windows Run (Windows Key + R).
Enter regedit and click OK.

Navigate to the registry key: Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\Parameters

If you do not see LocalNTP REG_DWORD in the list, create it using the following steps.
Right-click in the Registry Editor, select New, select DWORD and enter LocalNTP (note that this name is case sensitive).

Double-click LocalNTP, change the Value data to 1, select a Base of Hexadecimal , and click OK.
Do not close the Registry Editor because it is used in the following steps.
Update the Windows Registry to Configure the Time Provider
Navigate to the registry key: Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders
Select NtpServer, double-click Enabled, change the Value Data to 1, select a Base of Hexadecimal and click OK.

Do not close the Registry Editor because it is used in the following steps.
Update the Windows Registry to Configure the Announce Flags
Navigate to the registry key: Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\Config
Double-click AnnounceFlags, change the Value data to 5, select a Base of Hexadecimal, and click OK.
Close the Registry Editor.

Start the Local Windows NTP Time Service
In the File Explorer, navigate to: Control Panel\System and Security\Administrative Tools
Double-click Services.
In the Services list, right-click on Windows Time and configure the following settings:
Startup type: Automatic
Service Status: Start
OK

Finally, enable UDP port 123 on the Windows firewall for incoming connections.
In Search find Firewall in Windows Defender…
Go to Incoming rules
In the right column, select New rule…
Select the rule Port
Enter UDP port 123 and click Next
Select Allow connection and click Next
Select all domains
Enter the rule name, e.g. Local NTP server, and click Finish.
The local NTP Time Server configuration is now complete. You now can synchronize the time of other computers and devices on your local network.
To test the server functionality from another PC (e.g. a service notebook) use for example the NTP Server Test Tool:
https://www.ntp-time-server.com/ntp-software/ntp-server-tool.html

DNAC deployment

C:\\Users\\Anas\\Downloads\\CatC-SW-2.3.7.7-VA.ova
Add 2 backslashes for OVA path to escape it
vcenter.home.local
administrator@vsphere.local
C0mplex30-
C:\\Users\\Anas\\Desktop\\CatC-SW-2.3.7.7-VA.ova
dnac
thick
2
data
mgmt
10.21.1.2
255.255.255.0
10.21.1.1
Mgmt interface:
172.16.25.2
255.255.255.0
DNS
172.16.32.11
NTP
172.16.32.11
dnac.home.local
maglev
C0mplex30



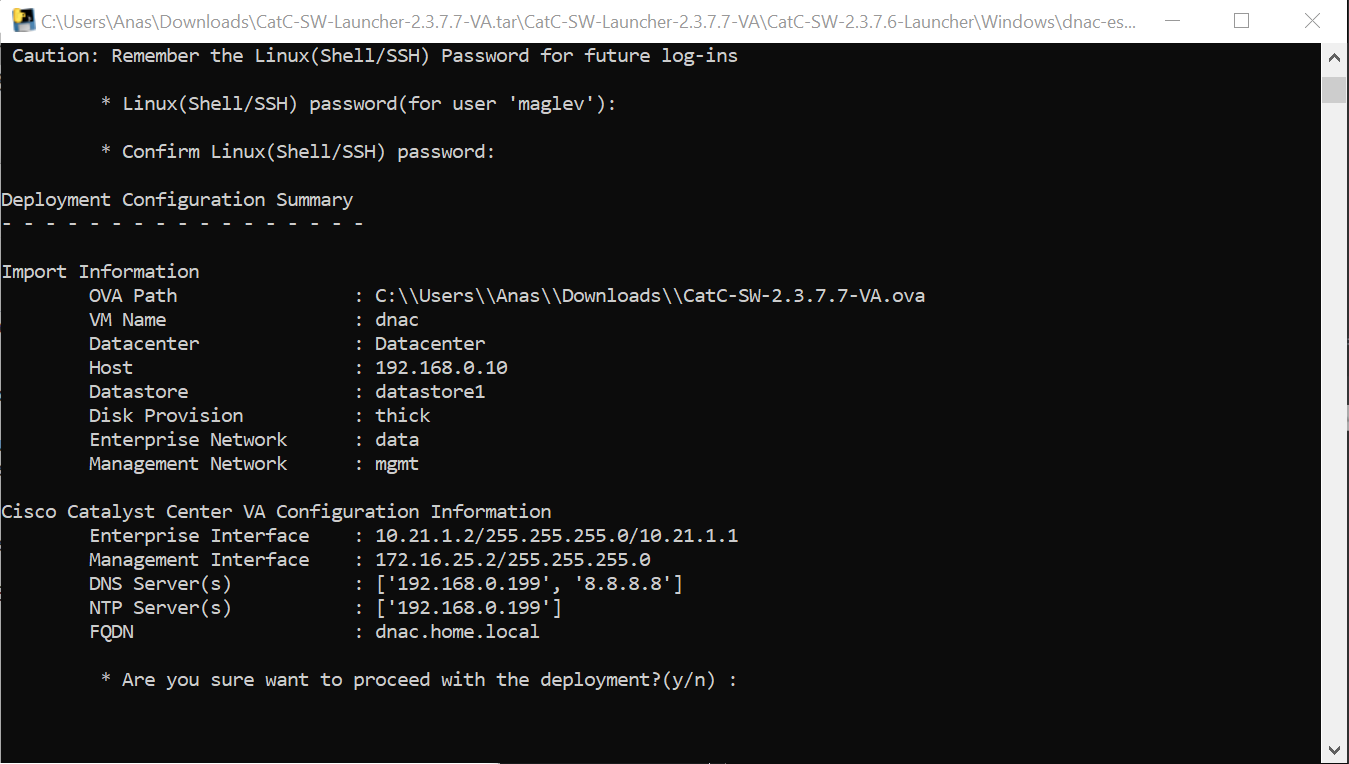




maglev will load containers

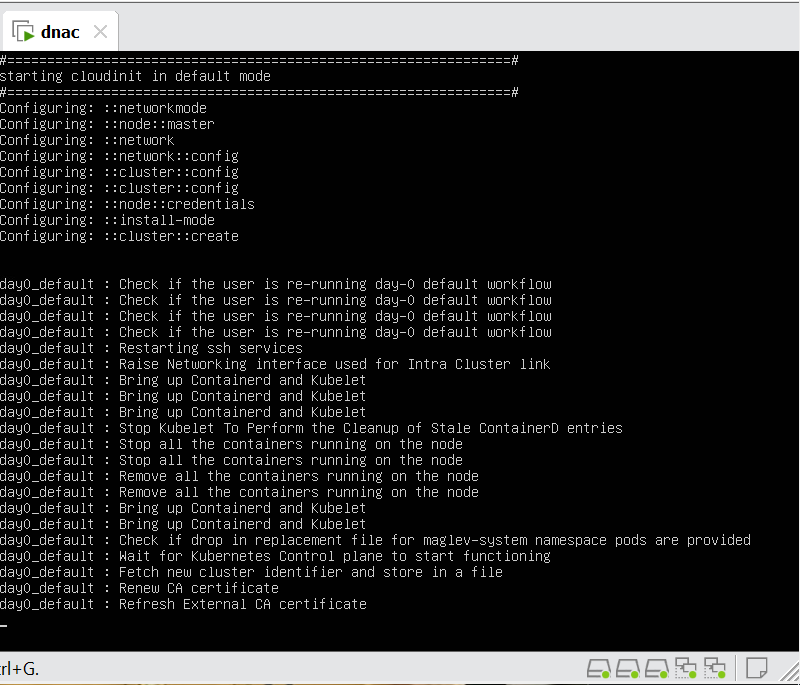
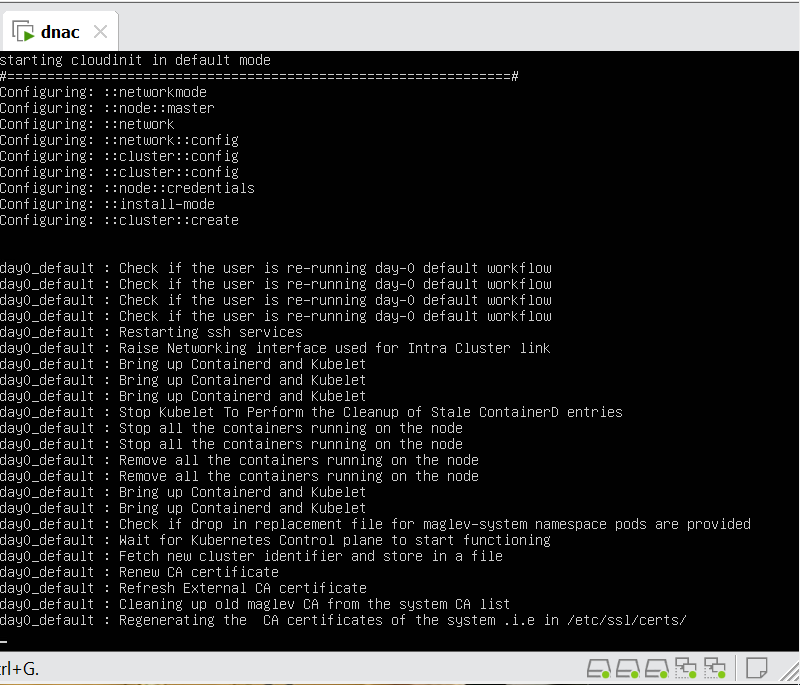
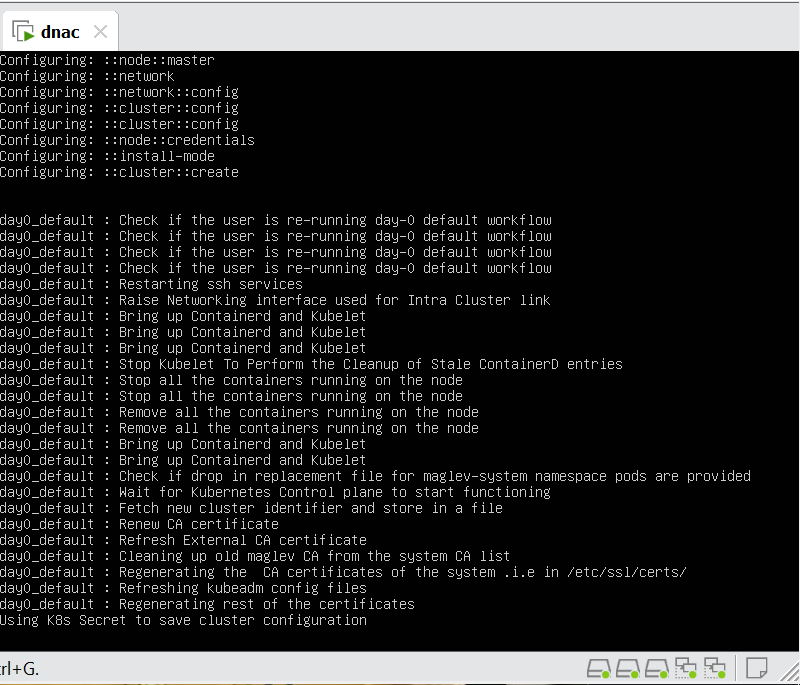
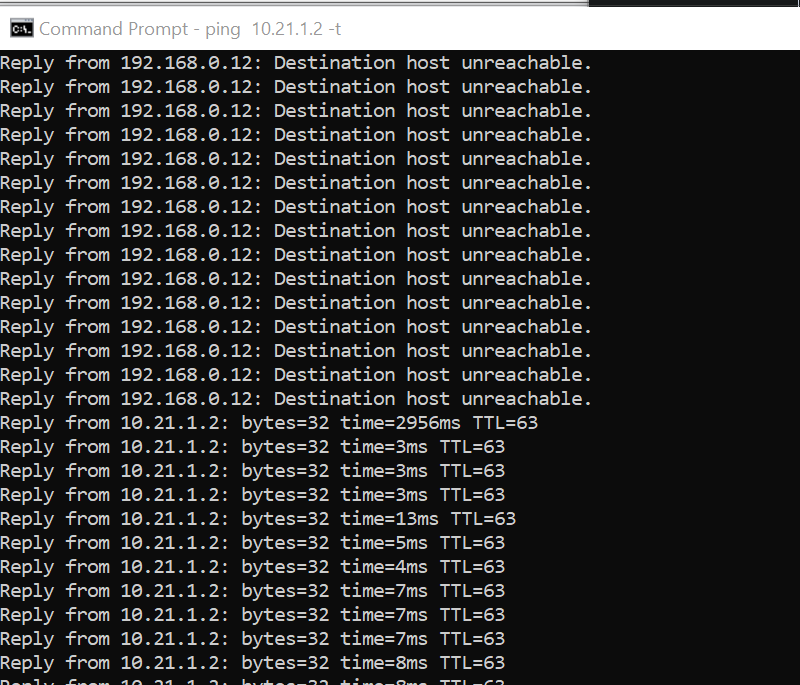

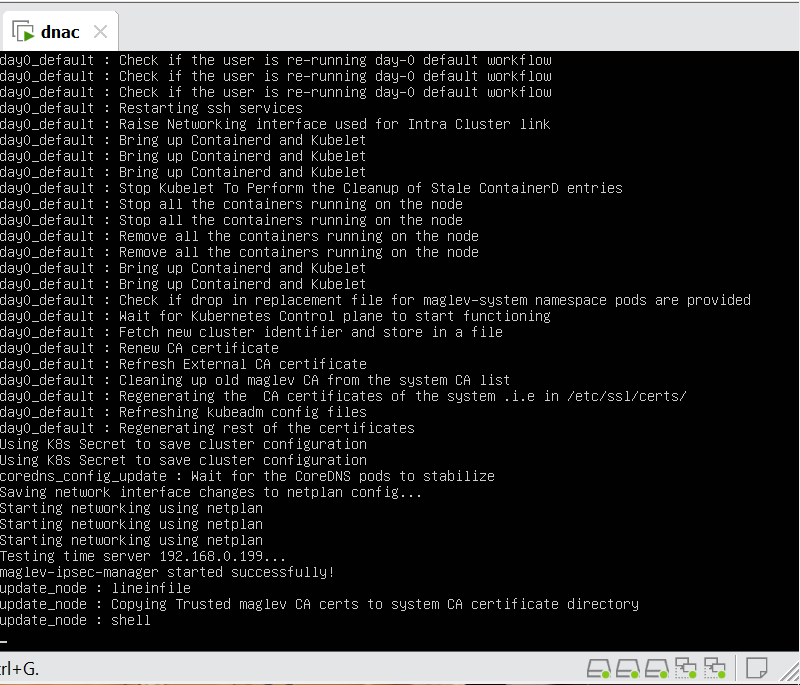
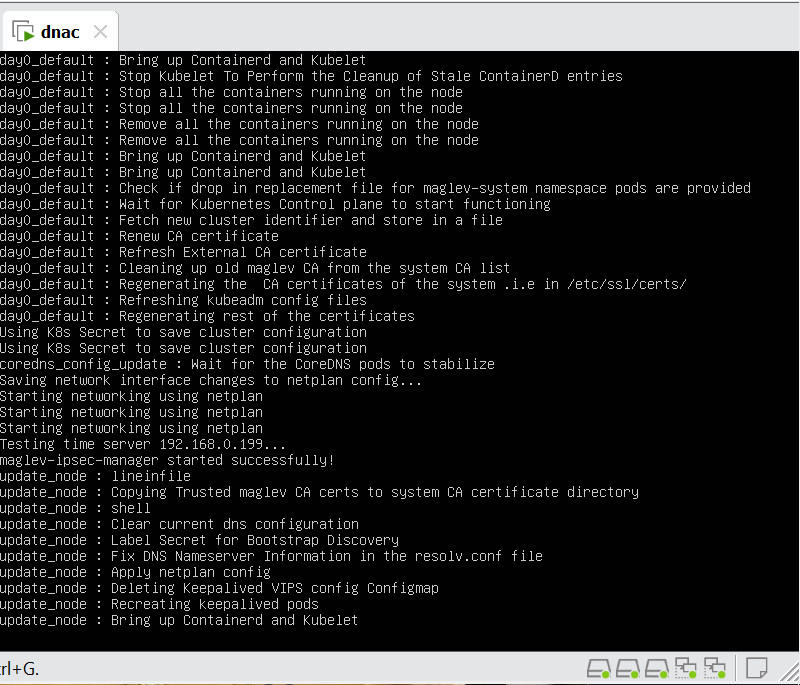
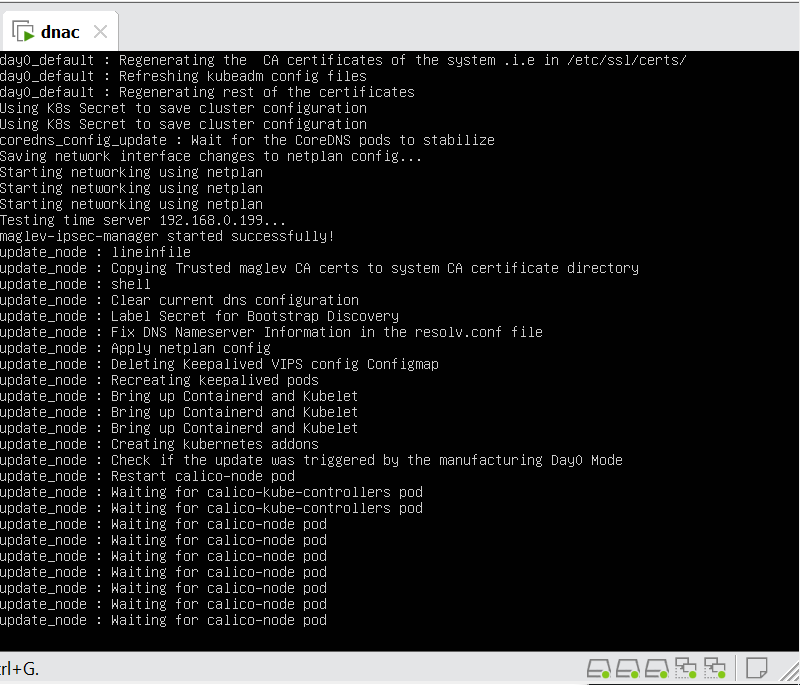
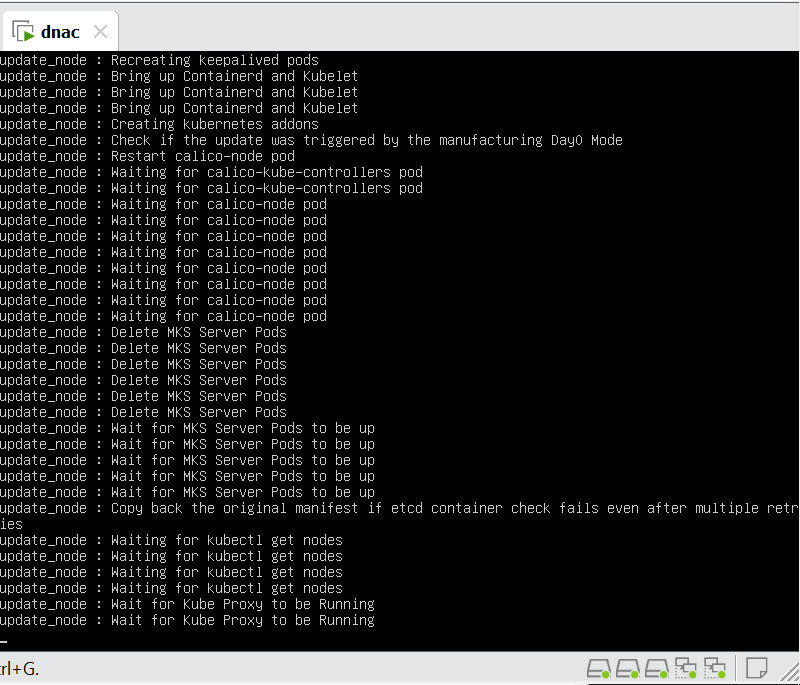
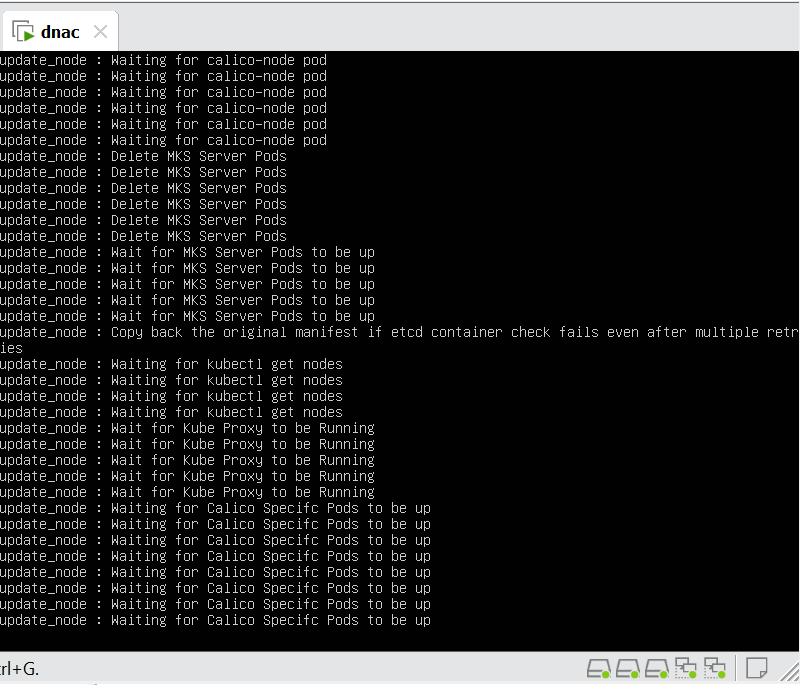
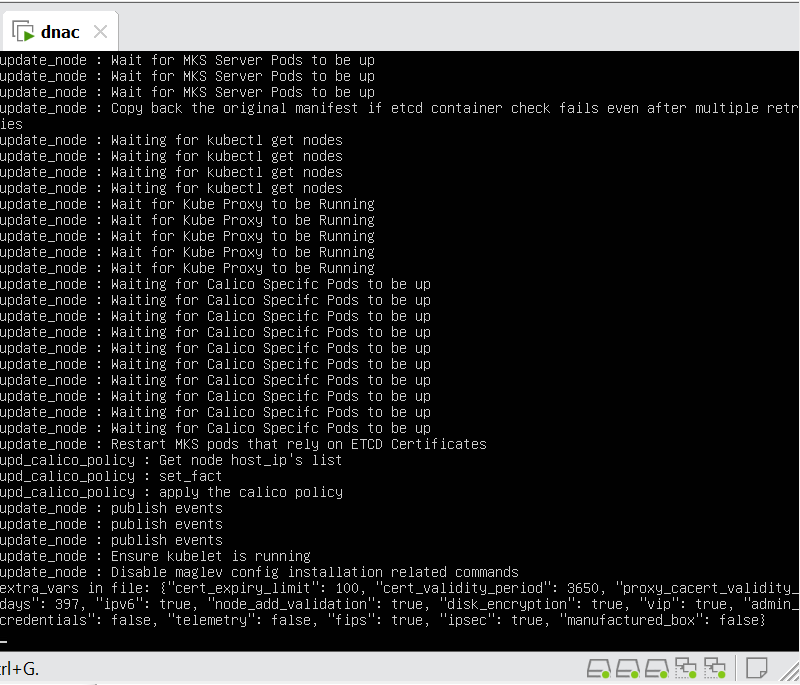

wait 30 mins before GUI shows up
In case unable to login
Login to CLI as maglev on VM’s console and reset password for admin
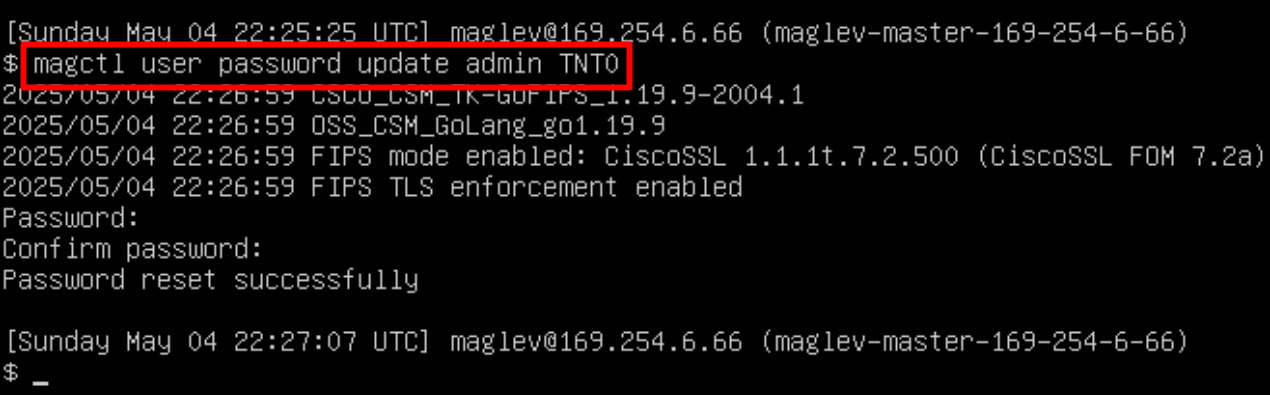
Logins
Default GUI login admin/maglev1@3
Login to create account admin_anas/C0mplex30
SSH login on port 2222 maglev/C0mplex30
DNAC VM Console login maglev/C0mplex30
Initial Login

provide user here that will be super admin such as admin_anas
provide your cco in email and not personal email
admin_anas/C0mplex30
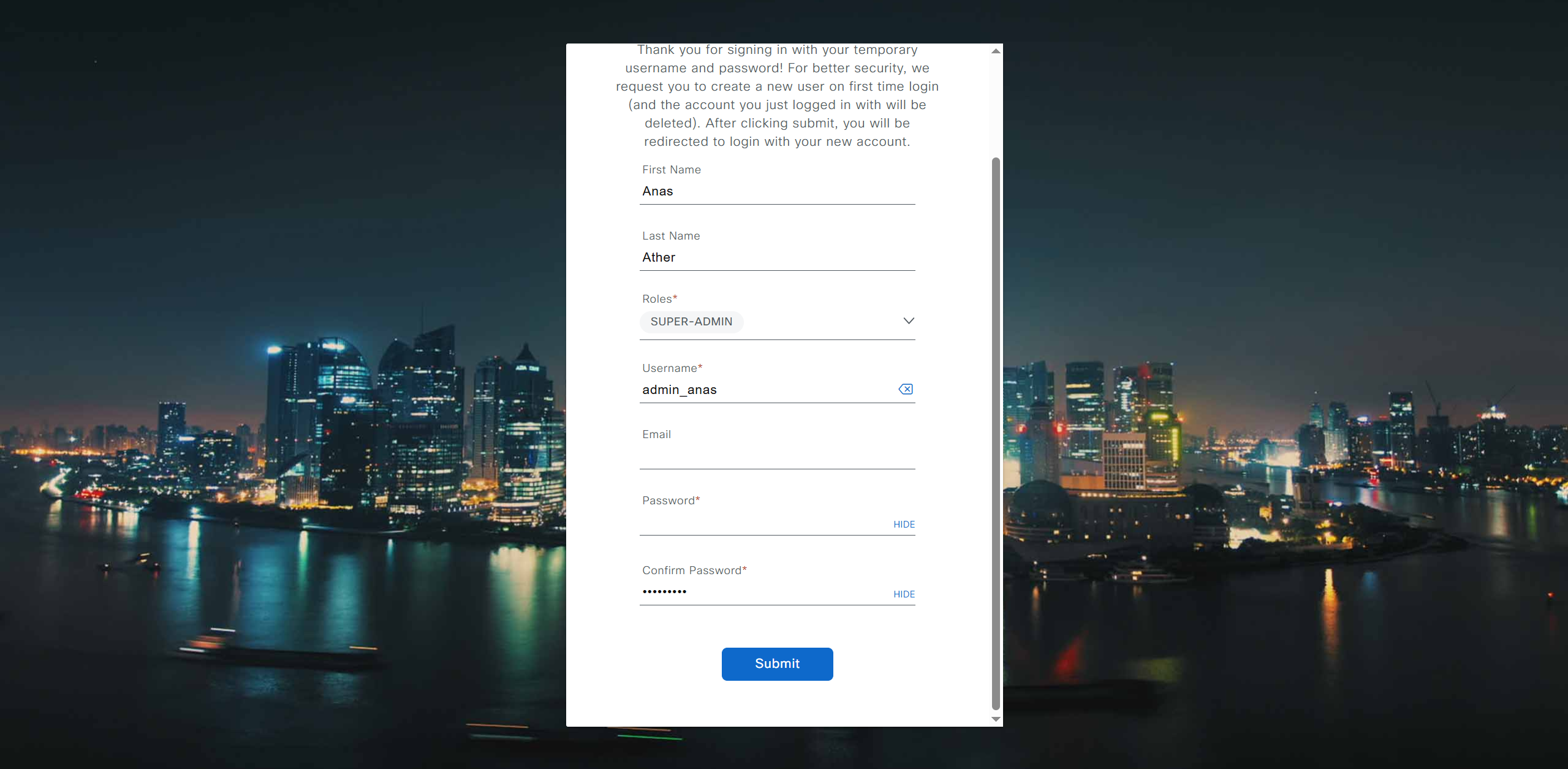
provide company’s CCO details here that has contract and active cco – this is very important otherwise packages will not work



With new build make sure DNAC has internet access, go ahead and download the applications packages which are needed for SGT and SDA, Cisco has divided these features into applications or packages and with fresh install / build download these packages
- Download these packages
- Turn off the VM
- Take Snapshot with exact date and time
- Turn off time syncing of VM with ESXI
- ESXI add NTP server same as Windows Server
- Windows Server move back time on server when it is time to restore the VM
- When restore cut off internet access to DNAC

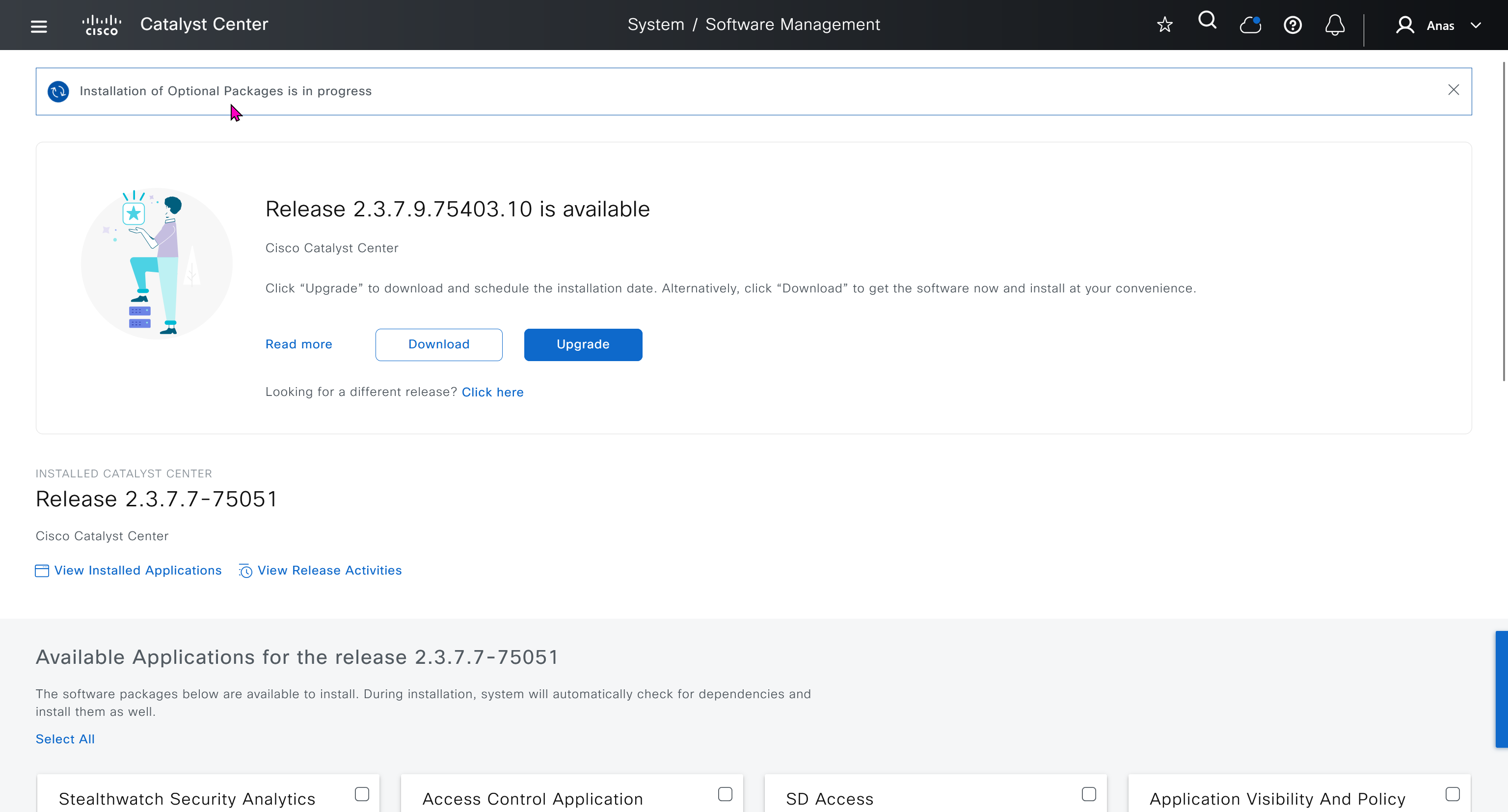
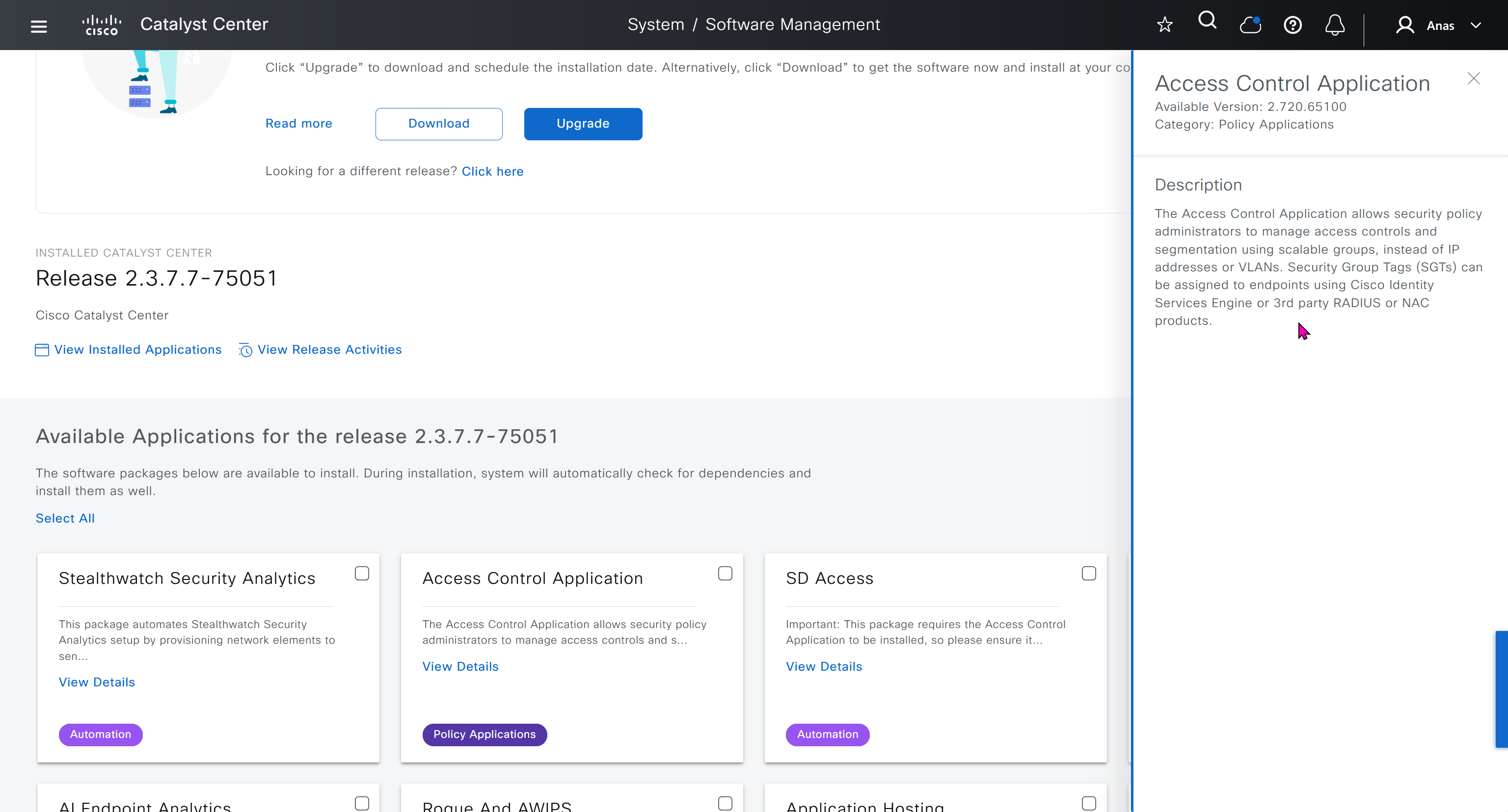

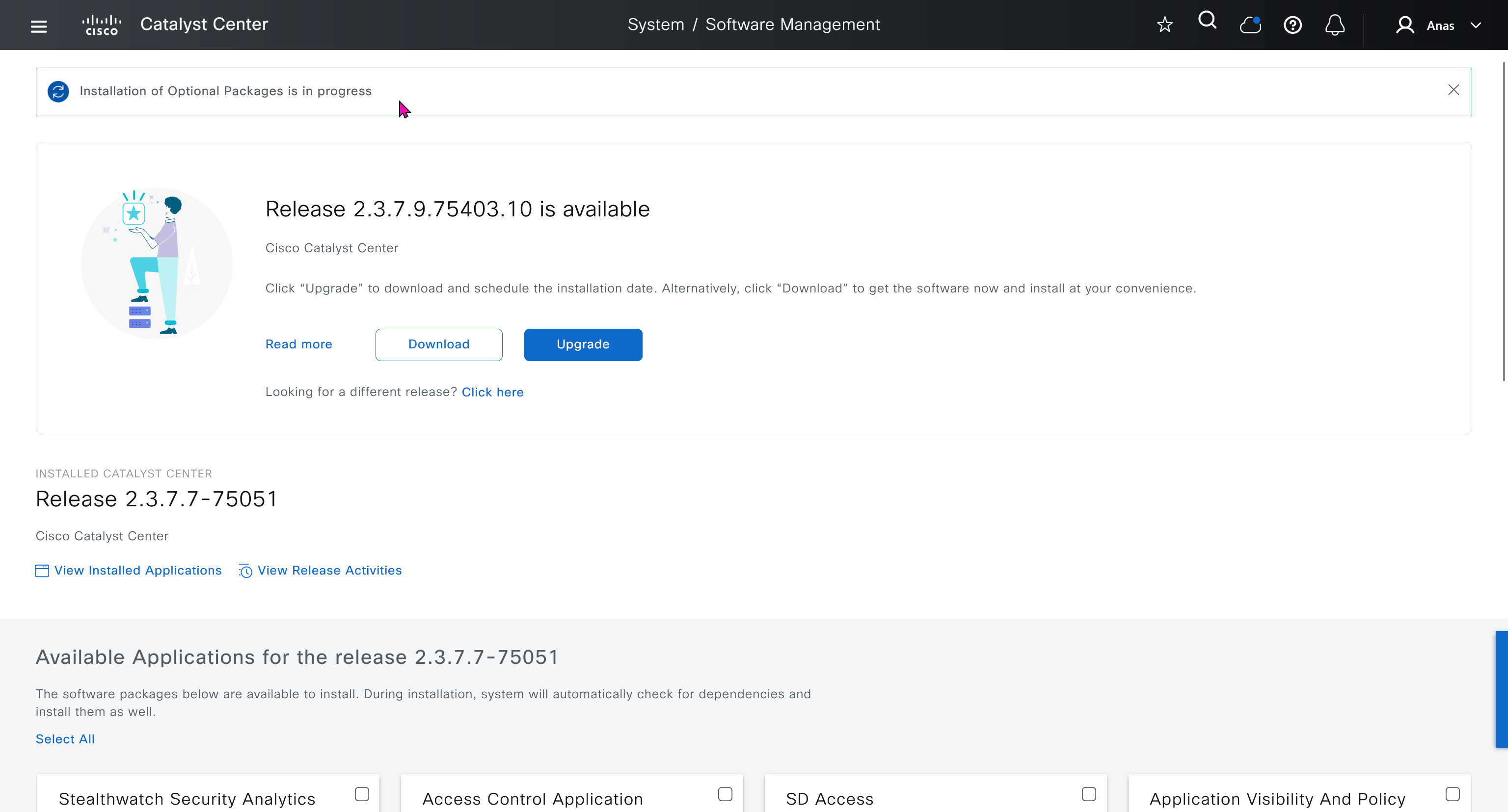
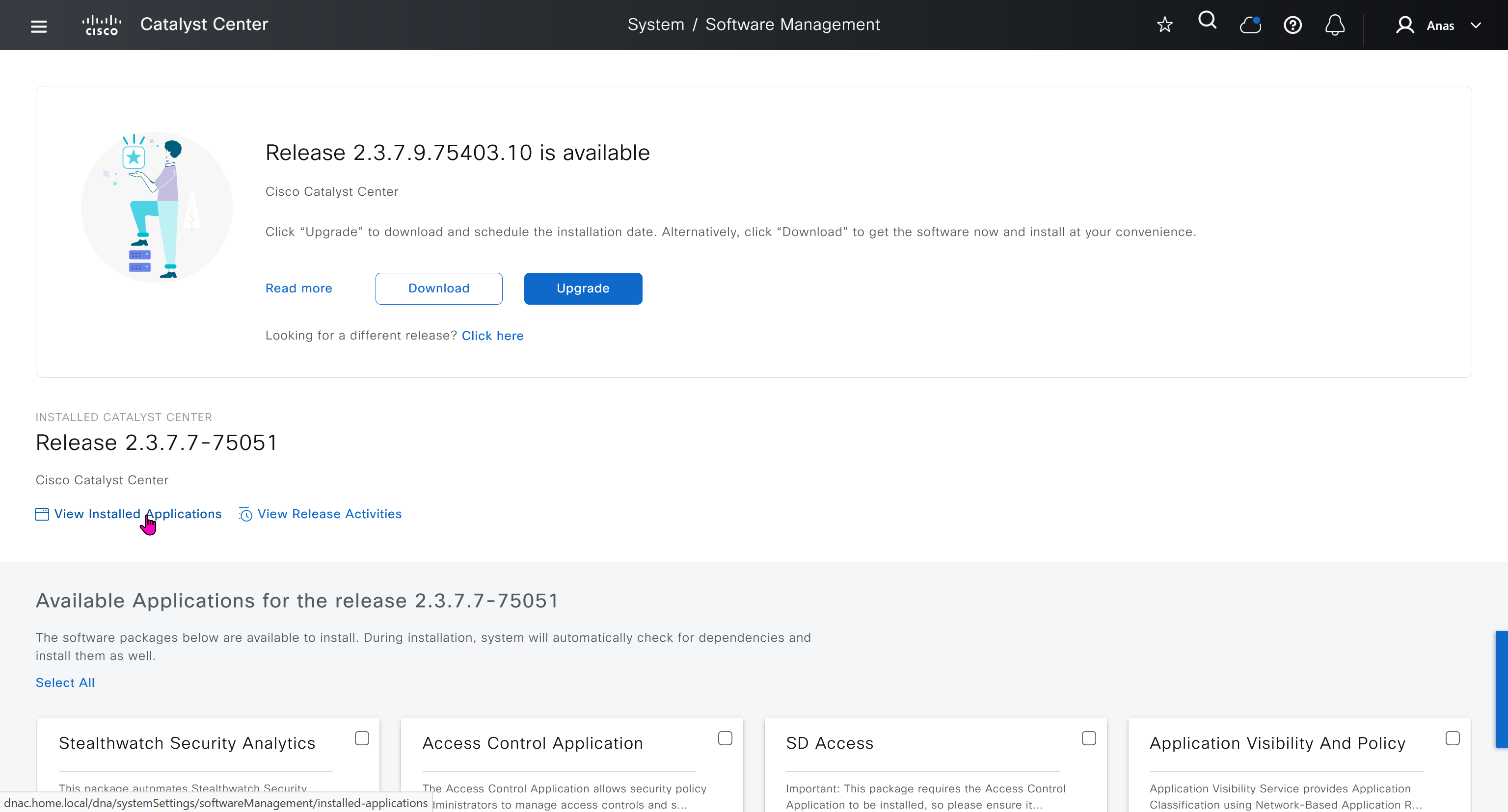



Here do not use personal email instead use email from company’s cco

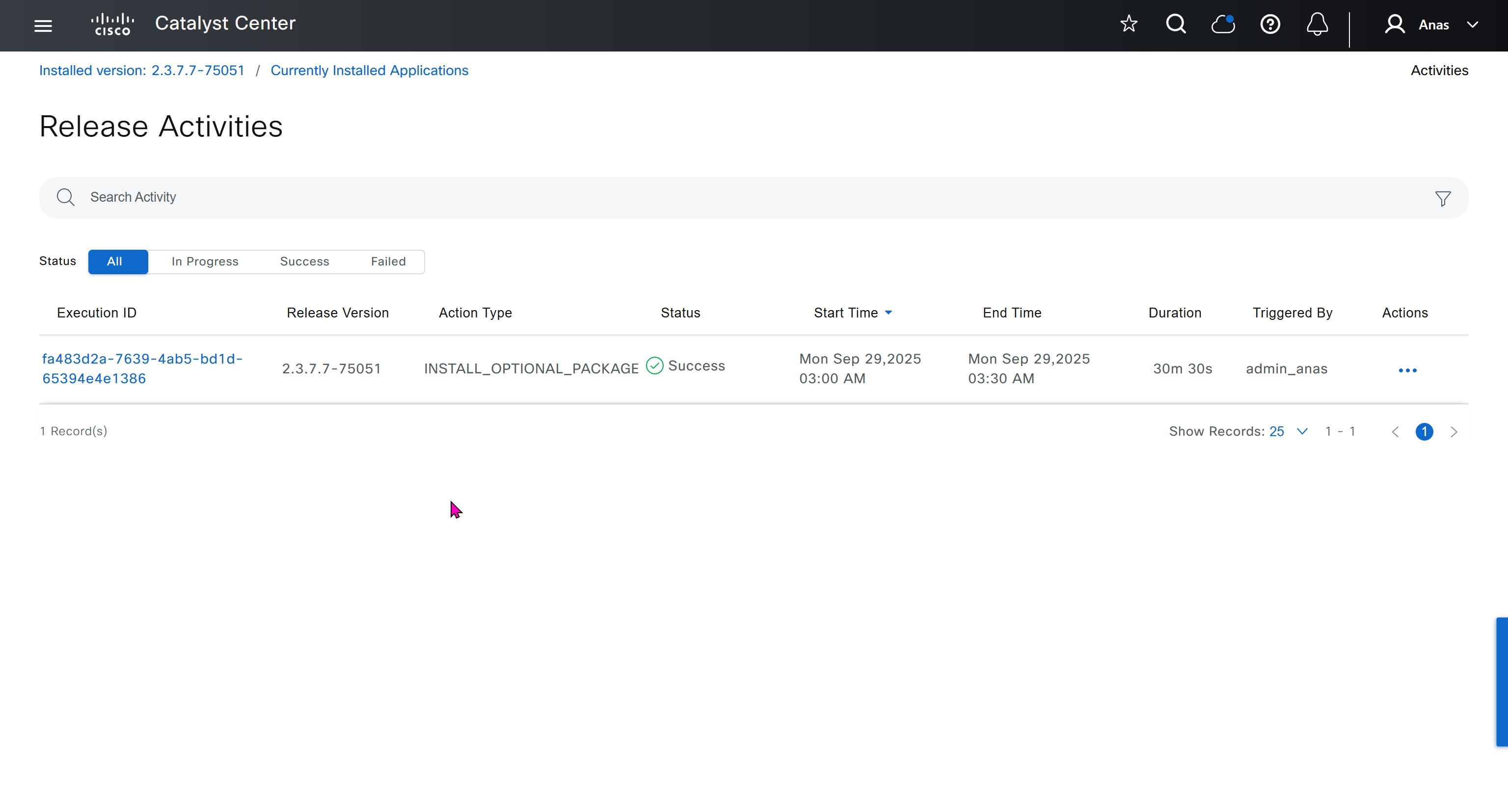
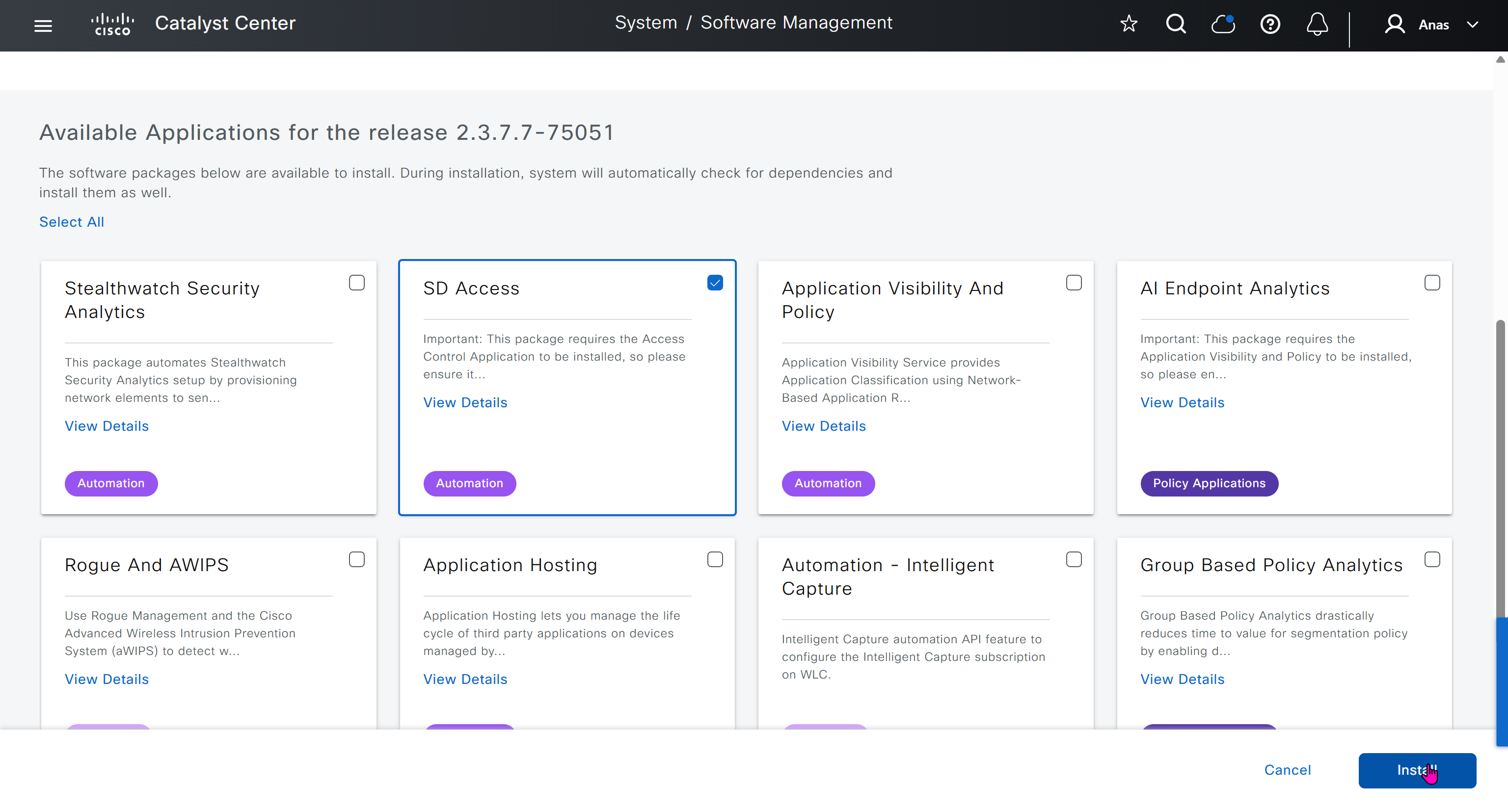
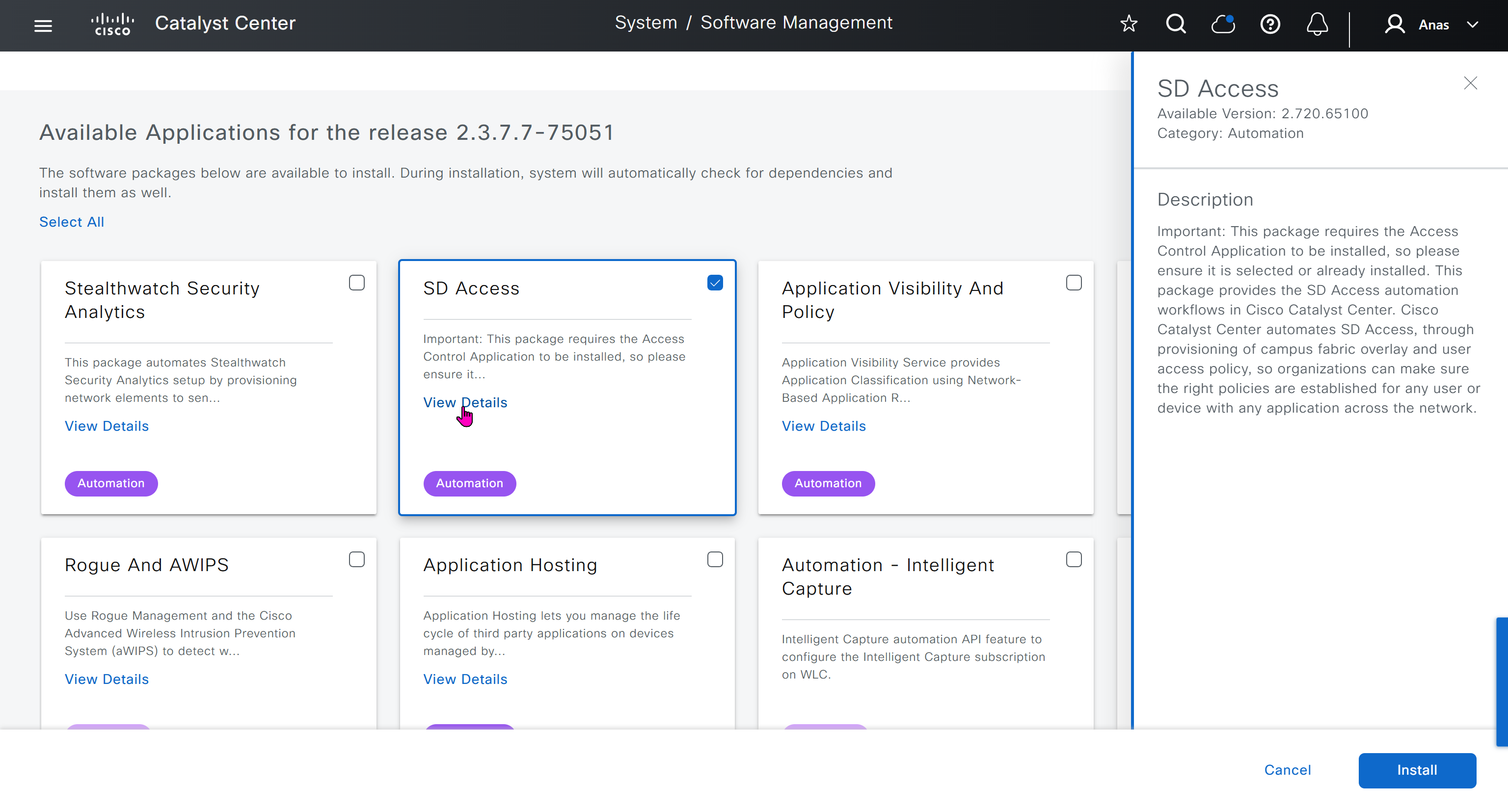

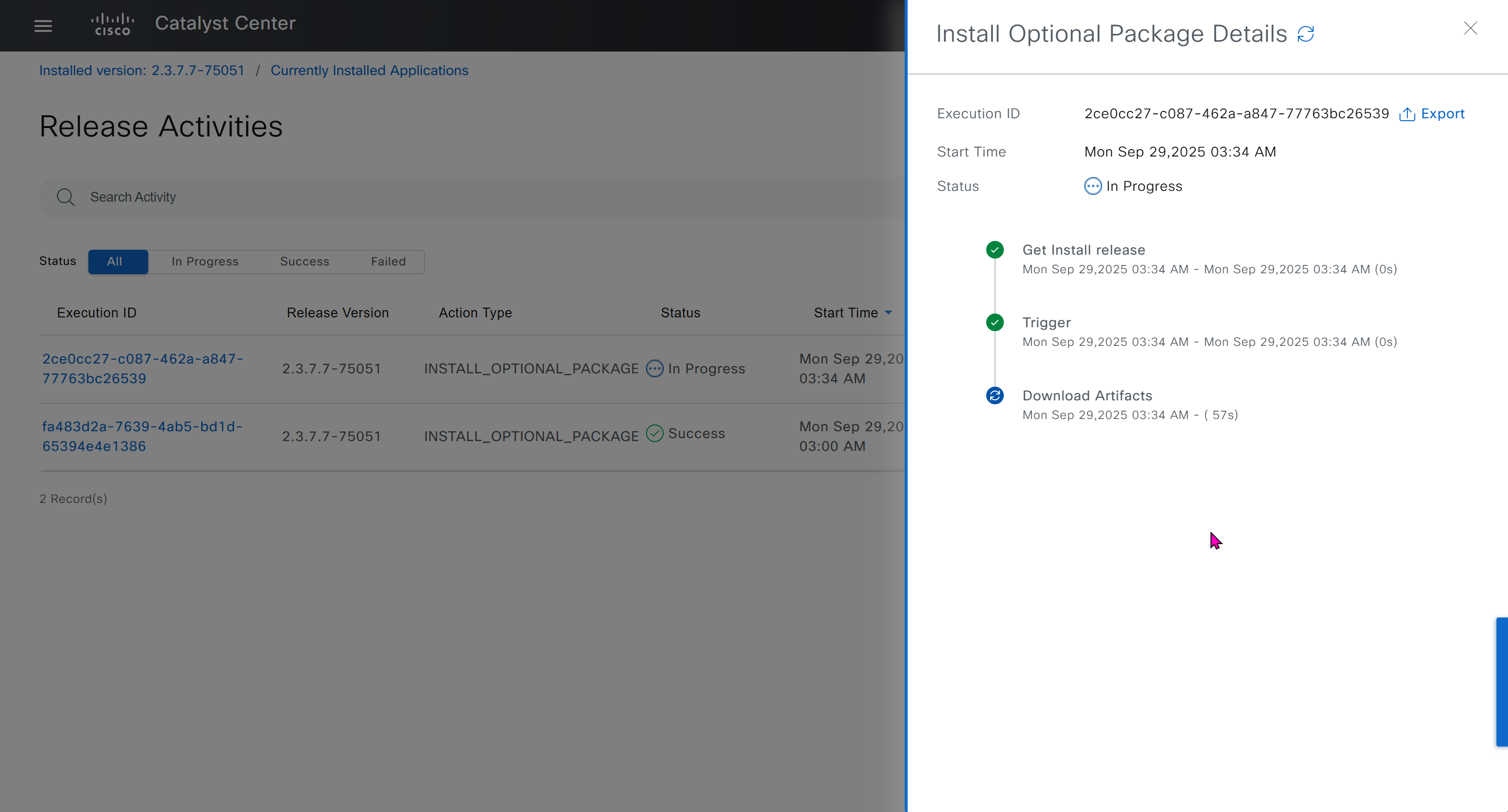

on next deployment also download below modules also
Sensor Assurance
AI Endpoint Analytics
Application Visibility and Policy (EasyQoS)
Only after these steps, add certificate to DNAC
Further configuration and ISE integration
Graceful shutdown DNAC
! Cat center shutdown
$ shutdown
! VYOS shutdown
sudo bash
shutdown -h now
! vcenter shutdown
Gracefully shutdown from esxiSDA Links
https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/network-automation-and-management/catalyst-center/catalyst-center-va/esxi/2-3-7/deployment-guide/b_cisco_catalyst_center_237x_on_esxi_deployment_guide.html#configure-a-virtual-appliance-using-the-interactive-cc-va-launcher
https://www.cisco.com/c/en/us/td/docs/solutions/CVD/Campus/SD-Access-Distributed-Campus-Deployment-Guide-2019JUL.html
https://www.cisco.com/c/dam/en/us/td/docs/solutions/CVD/Campus/sda-fabric-deploy-2019oct.pdf
https://www.cisco.com/c/en/us/td/docs/solutions/CVD/Campus/cisco-sda-design-guide.html
https://www.cisco.com/c/dam/en/us/td/docs/solutions/CVD/Campus/CVD-Software-Defined-Access-Segmentation-Design-Guide-2018MAY.pdf
next post
Python
Python Installation Guide
Download and Install Visual Studio Code from Microsoft
Choose dark theme because it is cool
Click on python on the right side
Click on python > install
Wait for it to install, this is just the support for the language in VSCode but not the language or Python interpreter itself, we will download it from Microsoft’s store later
Click on Open Project folder
right click, create new folder and name it VSCode
Click “Select Folder”
Tick that Trust option and Click on Trust button
Click on Create a python file
Click on create environment
Click on Venv ( this will be explained later )
See message that Python is missing, but still click on it
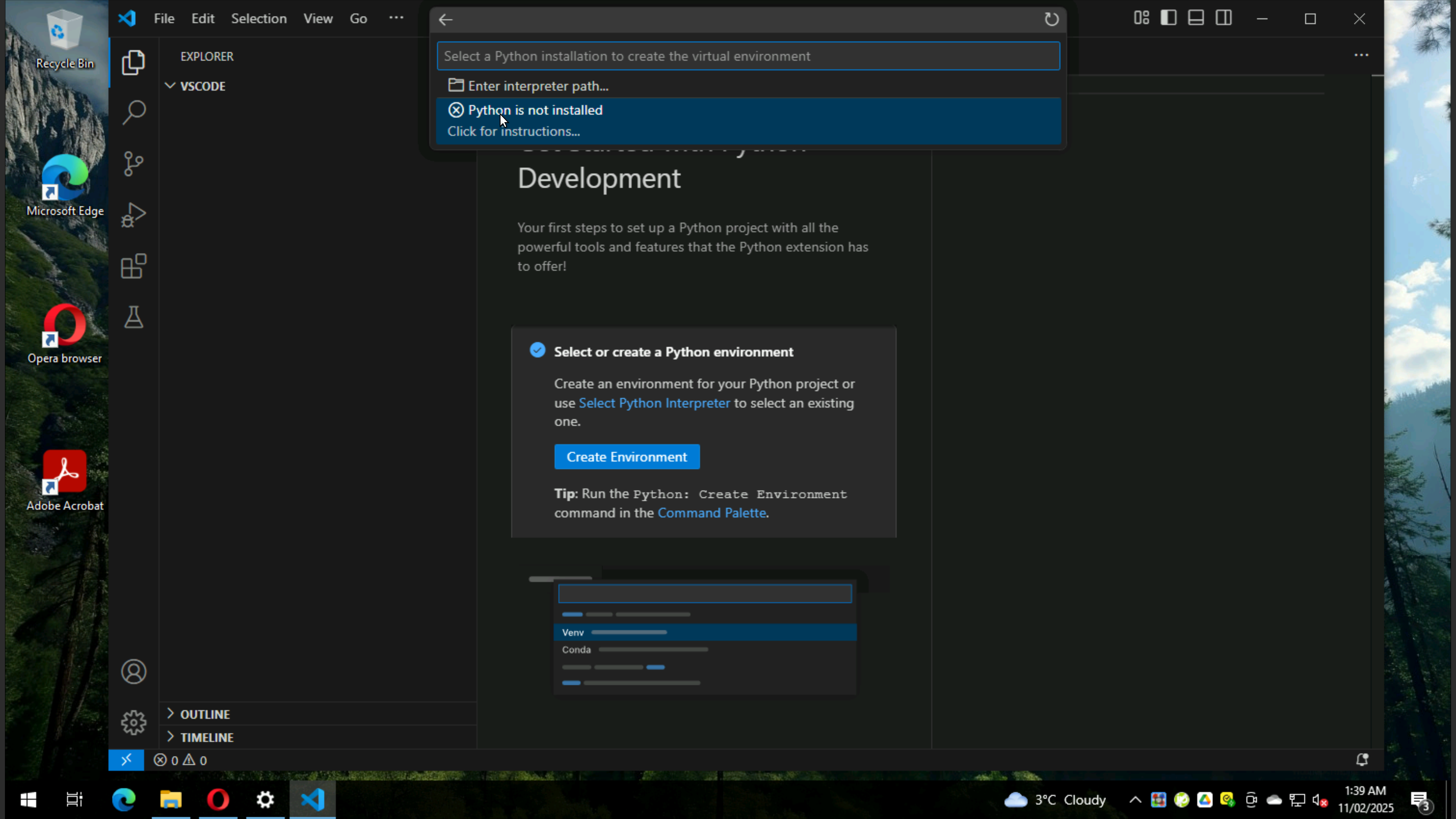
it will take us to Microsoft Store and click on install
Once it is installed Python interpreter will show, click on it
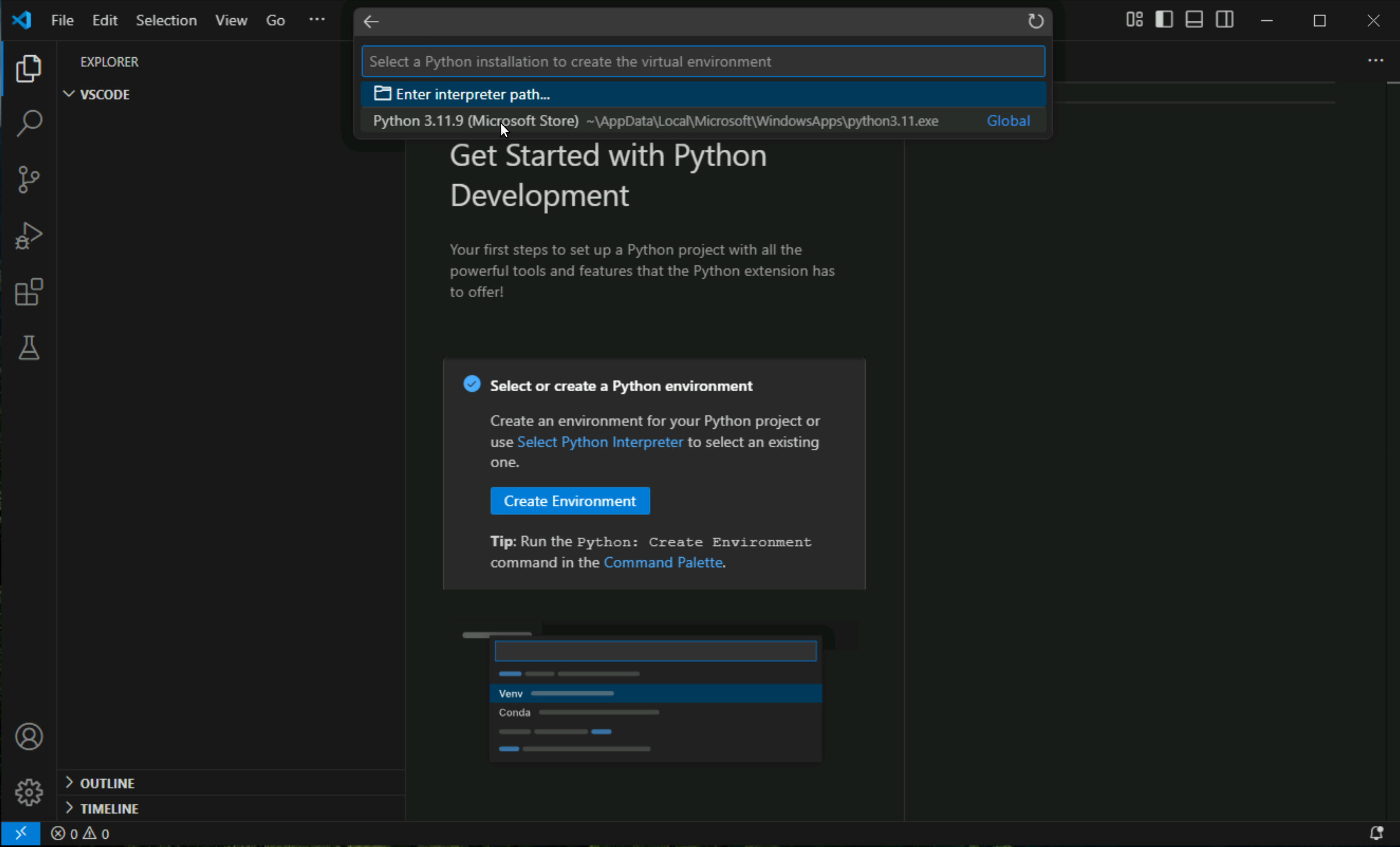
expand .venv and click on activate.bat > Reveal in File Explorer
Manually creating envrionement incase initial wizard does not allow or skips it
Create a virtual environment
A best practice among Python developers is to use a project-specific virtual environment. Once you activate that environment, any packages you then install are isolated from other environments, including the global interpreter environment, reducing many complications that can arise from conflicting package versions. You can create non-global environments in VS Code using Venv or Anaconda with Python: Create Environment.
Open the Command Palette (Ctrl+Shift+P), start typing the Python: Create Environment command to search, and then select the command.
The command presents a list of environment types, Venv or Conda. For this example, select Venv.
Click on activate.bat
Click on empty space in explorer and click on new file, create a test python file as Test.py
Type some test code into it and press Shift + Enter to run this code
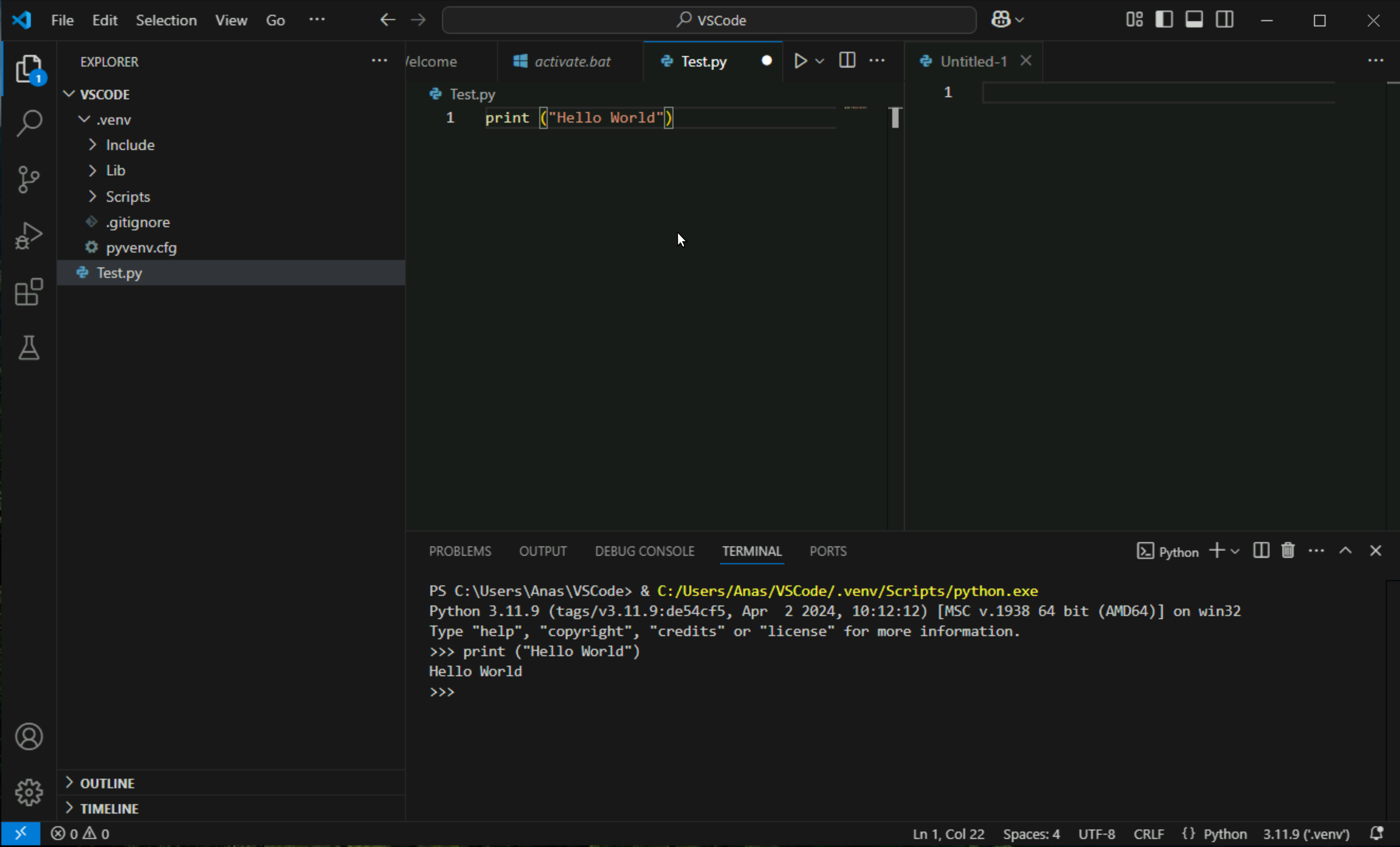
(Skip this) VSCode Extensions installation
Pylint
Black Formatter
File > Preferences > Settings
open settings.json file by clicking on top

Add this line in settings.json
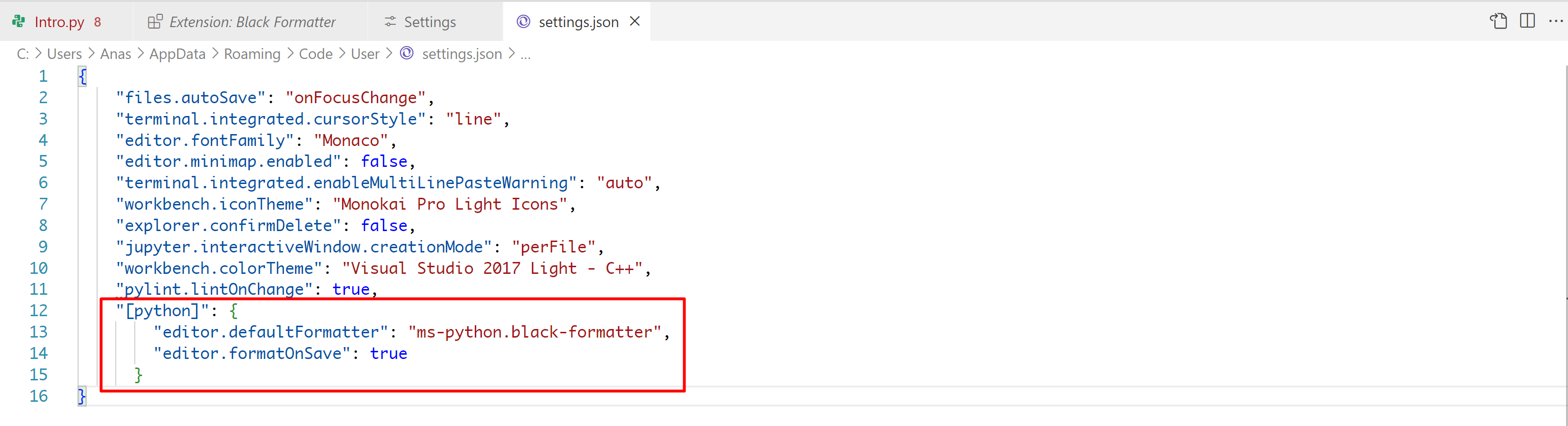
Environments
A Python environment is a container in which a Python runs. It consists of the Python interpreter (python.exe) and installed packages. There are different types of environments, but the most common ones are virtual environments.
Why Use Python Environments?
- Isolation: Each environment is isolated from others, meaning you can have different versions of Python and packages for different projects without conflicts. You dont really want to mix libraries between projects as it can increase code size of a particular project.
- Dependency Management: Helps manage dependencies for different projects, ensuring that each project has the correct versions of libraries it needs.
- Reproducibility: Makes it easier to reproduce the development environment on different machines, which is crucial for collaboration and deployment.
Types of Python Environments
- virtualenv:
- Creates isolated Python environments.
- Each environment has its own Python interpreter and libraries.
- Useful for managing dependencies for different projects.
- venv:
- A module that comes with Python 3.3 and later.
- Similar to
virtualenvbut included in the standard library.
- conda:
- A package and environment manager from Anaconda.
- Can manage environments and packages for Python as well as other languages.
- Useful for data science and machine learning projects.
Creating a Virtual Environment
python -m venv myenv
- is m is for manifest?
- This command creates a new directory called
myenvwhereever your cd is in CMD, containing a new Python environment.

This created myenv folder in User/Anas since CMD is cd there by default
Activating a Virtual Environment
- On Windows:
myenv\Scripts\activate.bat - On macOS and Linux:
source myenv/bin/activate --> that simple activate without extension is for linux and MacOS
Deactivating a Virtual Environment
To deactivate the environment, simply run:
deactivate.batvenv Environment created by Visual Studio Code for python
Sometimes running python in Visual studio runs it in and power shell says following
run following
Set-ExecutionPolicy -ExecutionPolicy Unrestricted -Scope LocalMachineVSCode reset keyboard shortcut to its defaults
- Click File > Preferences > Keyboard Shortcuts
- There is a triple-dot (…) at the top-right hand corner. Click on that and select “Show User Keybindings”
- Right click on the key-binding that you want to reset and choose “Reset Keybinding”
Run python script by pressing shift + enter
Open Command Palette (Ctrl+Shift+P or Cmd+Shift+P on Mac).
Search for: “Preferences: Open Keyboard Shortcuts (JSON)”.
Add this entry:
{
"key": "shift+enter",
"command": "python.execInTerminal",
"when": "editorTextFocus && editorLangId == 'python'"
},What are fields (attributes) in vscode?
In Python within VS Code, the term “fields” often refers to class attributes or instance attributes of a class.
- Class Attributes: These are variables defined directly within the class body, outside of any methods. They are shared among all instances of the class and their value stays same through out all instances
- Instance Attributes: Created at the time of instance being created, These are variables defined within the
__init__method (the constructor) or can be other methods of a class instance. They can be different or same for instances.
class MyClass:
class_attribute = "This is a class attribute" # Class attribute
def __init__(self, instance_value):
self.instance_attribute = instance_value # Instance attribute
working with self and init function just copy this line
def __init__("self, instance_value"):
and remove ", " and replace it with
".variablename ="
For example
self, instance_value
self.instance_attribute = instance_value
obj1 = MyClass("Value for obj1")
obj2 = MyClass("Value for obj2")
# Class attributes do not need to be defined at the time of object
# creation because they were already defined at the time of writing
# class
print(obj1.class_attribute) # Output: "This is a class attribute"
print(obj2.class_attribute) # Output: "This is a class attribute"
print(obj1.instance_attribute) # Output: "Value for obj1"
print(obj2.instance_attribute) # Output: "Value for obj2"In this example:
class_attributeare fixed and shared by bothobj1andobj2.instance_attributeis an instance attribute, and its value is different for each object.
f” {var} text ” – Easy formatting of text in print( )
a = "Hello"
b = "World"
print(f"{a} {b}")Easily print the variables along with string as single concatenated output by using short form of format function
Python code works inside { }
a = 5
b = 10
f"{a} plus {b} is {a + b}"
# 5 plus 10 is 15
# another example
def func1():
return f"""
{globals()}
"""
print(func1())
Self-Documenting f string f”{ variable= }”
number = 10
if number > 5:
raise Exception(f"The number should not exceed 5. ({number=})")
print(number)
Exception: The number should not exceed 5. (number=10)number=10 has come from code “number=” because this tells python to print the variable name and also its value after equals sign and even the object’s name and object content but only with f string, not with just the print function
user = 'eric_idle'
member_since = date(1975, 7, 31)
f'{user=} {member_since=}'
user='eric_idle' member_since=datetime.date(1975, 7, 31)immutable types
In Python, an immutable type is a type of object whose state or value cannot be changed after it is created or “not mutated”. Once an immutable object is created, any attempt to modify it will either result in an error or create a new object.
Common Immutable Types in Python:
- Integers (
int) - Floating-Point Numbers (
float) - Strings (
str) - Tuples (
tuple) - Frozen Sets (
frozenset) - Booleans (
bool)
x = 10
# remember that in python when we do x = 10, then x is not just x = 10 but x also becomes 10
print(id(x)) # Prints the memory address of x
x = x + 1
# that is why when we do x = x + 1, to python that looks like 10 = 10 + 1, but python still performs this operation by removing old x and by creating a new x and assign it 10 + 1, as python knows what programmer meant
print(id(x)) # A new memory address, showing that x now points to a new object
s = "hello"
print(id(s)) # Prints the memory address of the string "hello"
s = s + " world"
print(id(s)) # A new memory address, showing that s now points to a new objectt = (1, 2, 3)
print(id(t)) # Prints the memory address of the tuple, () is tuple
t = t + (4,)
# this is like adding two tuples together, here t is one tuple
# and (4,) is another tuple, just like x = x + 3 or s = s + " world!"
# this t + (4,) is another way of appending to a tuple
# because no changes are allowed in tuple since the creation
# of a tuple python creates a new tuple as tuple is immutable.
print(id(t))
# A new memory address, showing that t now points to a new objectvariables
x = "Name"
x = 10
# single line multiple declarations
x, y, z = 1, 2, 3
def func1():
a, b, c = 11, 22, 33string and range [x:x]
s = "Hello"
s = s + " world!"
print ("added two" + " lines together")
# string because is a list of characters
# individual letters can be accessed like below
somestring = "01234567890123456"
print(somestring[2])
print(somestring[0:15])
012345678901234
! 5 is not part of output but we expected it to be but it is not, end selector has last position but imagine that position to be occupied by our selector, and selection ends on one number before
somestring = "This is some string"
x = len(somestring) + 1
print(somestring[0:x])
# if we leave first number in range then it is
# considered 0 or beginning
somestring = "This is somestring"
print(somestring[:19])
# output
This is somestring
# if we leave the last or end of the range then it is
# considered end of the range
somestring = "This is somestring"
print(somestring[5:])
# output
is somestring
# if we leave both out then it is default as always
# will be considered to be 0 or start and end or last in range
somestring = "This is somestring"
print(somestring[:])
# output
This is somestring
# example of using negative range to access last item
print(list1[-1]) # will show the last item
# This is also a good way to access the last item
# in lists and tuples (not dictionarys)
list1 = [1, 2, 3, 4, 5, 6]
list2 = list1[0:]
list3 = list1[:3]
list4 = list1[0:4]
list5 = list1[:]
print(id(list1))
print(id(list2))
print(id(list3))
# 2581915590720
# 2581915738496
# 2581915593600
# when a list is returned using range
# then it is a new list
# similarly tuples, when using range
# it will be a new tuple
tuple1 = (1, 2, 3)
tuple2 = tuple1[0:3]
tuple3 = tuple1[0:2]
print(id(tuple1))
print(id(tuple2))
print(id(tuple3))
# but see if full tuple is returned as tuple1
# then both refer to same object or memory location
# is same, this is same as x = 1, then y = x
# this is not true for the list, this is because
# lists are mutable and tuples are immutable
# output
# 2319082021888
# 2319082021888
# 2319082312000list, tuple, dictionary, set
list1 = [1, 2, 3]
! list resembles actual paper list []
tuple1 = (1, 2, 3)
! tuple resembles and sounds like a plant ()
dictionary1 = {"key1": "val1"}
! dictionary is represented by {} and "" which is very dictionary like
set1 = {"val1", "val2"}
! set contains only values and not they keys
print(dictionary1["key1"])
print(set1[1]) # this will give error
# set contains only values and not the keys
# since sets are unordered, they cannot
# be accessed with an index "[1]", but we
# can still loop through a set, once a set
# is created you cannot change its items but
# you can add new items
set1 = {1, 2, 3}
for val in set1:
print(val)
# 1
# 2
# 3print( )
print("this is line 1", "and this is same line")
print("this is line 1" + " and this is same line")
print("this is line 1" " and this is same line")
print("this is one line", end="\n")
print("this is line two", end="\n")
#output
this is one line
this is line two
print("This is one line", end=" ")
print("This is same line", end=" ")
#output
This is one line This is same line (.venv) admin@EVE2:~/vscode$
#output
this is one linethis is line two
this is one line this is line two
this is one line
this is line two
this is one line
this is line twofunctions
Some functions are built in which can be run as print( )
but some functions are coded into class / objects can be called after referencing object such as object.func( ) with a dot
def func2():
passimport
from ….. import …..
Using import python code in one module (a module is simply a python .py file) gains access to the code in another module (file), allowing you to reuse code while keeping your projects maintainable
Module is a single python code file (file with .py extension) while a package is a collection of modules (with a _init_.py file). Usually a module is imported using import command (import from either internal python library of code or from external packages installed) and packages are installed using pip
import requestsThis imports the entire requests “package”
“from” comes first then comes “import” because we are only importing small code from the package or module
from requests.auth import HTTPBasicAuth
| | |
| | |
folder | |
.py file in requests folder
|
class onlyfrom “Folder”.”file” import “class or any other piece of code”
or
from “file” import “class or any other piece of code”
This only imports single class (HTTPBasicAuth) from the requests.auth file, that is how requests package is designed, specific parts can be imported and used
once import urllib3 is used we can use files under the folders as
# Silence the insecure warning due to SSL Certificate
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
| | |
| | |
Top Level Package Folder |
| |
.py file |
Class inside exceptions fileexceptions is a file inside the urllib3 package folder
InsecureRequestWarning is a class within this exceptions file
which is an empty class
from .api import delete, get, head, options, patch, post, put, request
# .api starts with dot because the file that is using api.py is in the same folder as api.py, The dot (.) signifies the current directory and package folder can be skipped in this case
# We can see that multiple functions from .api (.py) file have been imported
“From lets you import specific classes or functions or even variables or in general code section from a file in a package“
import: This keyword is used to bring in specific functions, classes, or variables from the specified file in the package into the current code and use it.
delete, get, head, options, patch, post, put, request: These are the specific functions being imported from the api.py file.
import json
# import JSON module so python can understand and work with JSON responses that are sent and received
import requests
# import requests module so python can handle HTTP headers
import urllib3
# import urllib3 which is a HTTP client
from requests.auth import HTTPBasicAuth
# imports HTTPBasicAuth method from the requests folder and auth file
# this class gives the ability to perform HTTP authentication to an HTTP server / website
from prettytable import PrettyTable
# Imports prettytable components from PrettyTable module to present returned data in table formatBeauty of imports is that you dont have to code HTTP headers mechanism from scratch but simply use requests
class
A class is makeup of an object, that you code before hand and use it by creating an instance.
Objects have member variables (attributes) and have functions (methods) associated with them
class Person:
person1 = Person("Alice", 30)
person1.introduce()type( ) – Finds type of an object using
Finds the type of the object
print(type(globals()))
#output
<class 'dict'>dictionary = { } – Remember { } and “” as this is frequently used in dictionary definition
Dictionaries are indexed by keys and not the index number like list and tuples are and you cannot skip defining keys, if you dont want to define keys then use something else and defined keys have to be unique
dictionary1 = {"1": "test", "two": "second-test"}
print(dictionary1[1])
# Traceback (most recent call last):
# File "g:\My Drive\0_Python\Projects\Learning_Sandbox\Intro.py", line 2, in <module>
# print(dictionary1[1])
# ~~~~~~~~~~~^^^
# KeyError: 1
# but if we define 1 as key in dictionary only then it will work
dictionary1 = {1: "test", "two": "second-test"}
print(dictionary1[1])
# testIt is best to think of a dictionary as a set of key: value pairs, with the requirement that the keys are unique (within one dictionary). A pair of braces { } creates an empty dictionary.
# define using curly braces
data_dct = {"name": "Alice", "age": 25, "city": "London"}
print(data_dct["name"]) # Output: Alice
# define using dict( ) function
data_dct = dict(name="Alice", age="30")
! using this method you dont have to use : and also dont have to "" the key names
# empty dictionary
data_dct = {}
# Changing values
data_dct["age"] = 28
# adding a new key value pair
data_dct["location"] = "Europe"
# clear all values using .clear( )
data_dct.clear()
print(data_dct)
# output
{}
# values, keys and items functions apply to the dictionary only
# because it is the only one with ability to store keys
# return all values using .values( )
values = data_dct.values()
# return all keys using .keys( )
keys = data_dct.keys()
# return all key value using .items( )
items = data_dct.items()
# checking a value using .get( ), returns none if values does not exist
age = data_dct.get("age")
# Removing Items using del and pop
del data_dct["city"]
age = data_dct.pop("age")
! assign and deleteNormal Iteration in dictionaries
data_dct = {
'name':'Anas',
'age':'31',
'profession':'Network Engineer',
'postcode':'IG3 8BD',
'car':'none',
'job status':'employed'
}
# Iterating in dictionary
# for loop gets keys only, not values
# for values we need to use a function
# .values()
for keys in data_dct:
print(f"{keys}: {data_dct[keys]}")
Getting values only using .values( )
data_dct = {
'name':'Anas',
'age':'31',
'profession':'Network Engineer',
'postcode':'IG3 8BD',
'car':'none',
'job status':'employed'
}
for key in dict_data:
print(key, dict_data[key])
for value in data_dct.values():
print(value)
print (data_dct.values())
# output
dict_values(['Anas', '31', 'Network Engineer', 'IG3 8BD', 'none', 'employed']Getting keys only using .keys( )
data_dct = {
'name':'Anas',
'age':'31',
'profession':'Network Engineer',
'postcode':'IG3 8BD',
'car':'none',
'job status':'employed'
}
for keys in data_dct.keys():
print(keys)
print(data_dct.keys())
# output
dict_keys(['name', 'age', 'profession', 'postcode', 'car', 'job status'])Iterate through keys and values using .items( )
data_dct = {"car": "Uber", "plane": "EasyJet"}
for key, value in data_dct.items(): # items() function allows keys with values in for
print(key, value)Nested Dictionaries
Persons = {
"Person1": {"Name": "person 1 ", "age": "33"},
"Person2": {"Name": "person 2 ", "age": "44"},
}
# 2 for loops will be needed
for key, val in Persons.items():
for key1, val1 in val.items():
print(f"{key1} \t {val1} \r\n")range( )
for i in range(5):
if i == 3:
continue #skip
print(i).items( )
items is a function that converts dictionary into a loopable list with key value tuple pairs
dict = {"car":"Uber", "plane":"737"}
print (dict) # This will print the entire dictionary as it is
print (dict.items()) # This will print a view object that displays a list of the dictionary’s key-value tuple pairs. This is mainly used in for loop
{'car': 'Uber', 'plane': '737'}
dict_items([('car', 'Uber'), ('plane', '737')])
^^ ^
|| |
[-----------------List----------------]
| |
(----Tuple---) |
(----Tuple---)
so this is a single List containing multiple Tuples of key and values
for loop looks at this as
[('car', 'Uber'), ('plane', '737')]
|
v
key value
| |
v v
('car', 'Uber')
('plane', '737')
for loop is passed a list
remember that anything that is passed to for loop is unpacked, so it unpacks list
and per pass for loop takes unpacked as below
key value
| |
v v
('car', 'Uber')
('plane', '737')
a good test is this code
# a list with tuples of 3 values
list1 = [
("key1", "value1", "metadata1"),
("key2", "value2", "metadata2"),
("key3", "value3", "metadata3"),
]
for first, second, third in list1:
print (first, second, third, end="\t")
print ("\r")
# output
key1 value1 metadata1
key2 value2 metadata2
key3 value3 metadata3
container = {
"key1":"value1",
"key2":"value2",
"key3":"value3",
"key4":"value4"
}
for keys, values in container.items():
print (keys, "\t", values, end="\r\n")
# same code can be written as
container_is_list = [
("key1", "value1"),
("key2", "value2"),
("key3", "value3"),
("key4", "value4"),
]
for keys, values in container_is_list:
print (keys, "\t", values)tuples = (1, 2)
Remember tuple from flower ( ), ( ) also looks like flower, may be remember tuple from tulips also
A tuple can store multiple items in a single variable, as it is not meant to be complicated, Tuples are immutable. Tuples are useful when you want data to never change. Tuples have advantage in being faster than lists for certain operations because of their immutability.
Ordered: The items in a tuple have a defined order, which will not change.
Unchangeable: Once a tuple is created, you cannot modify its items, you can’t add, remove, or change items to the tuple itself.
Allow Duplicates: Tuples can contain duplicate values.
Indexed: Each item in a tuple has an index, starting from 0.
Tuples are created by placing the items inside round parentheses ()
my_tuple = ("apple", "banana", "cherry")
print(my_tuple[1])
# Output: banana
# tuple short form like variable but with multiple quick values
my_tuple = 1, 2, 3
# empty tuple
empty_tuple = ()
# single value tuple
my_tuple = (5,)
mixed_tuple = ("abc", 34, True, 40.5)
If you want to create a tuple with only one item, you need to add a comma after the item:
single_item_tuple = ("apple",)
# comma is what actually defines the tuple, not the parentheses. Without the comma, Python would interpret the expression as a regular string enclosed in parentheses, rather than a tupleAppend to tuple
t = (1, 2, 3)
t = t + (4,)
# comma is what actually defines the tuple, not the parentheses. Without the comma, Python would interpret the expression as a regular number enclosed in parentheses, rather than a tupleConcatenation
tuple1 = (1, 2)
tuple2 = (3, 4)
result = tuple1 + tuple2 # Output: (1, 2, 3, 4)Repetition
repeated_tuple = (1, 2) * 3 # Output: (1, 2, 1, 2, 1, 2)Slicing
tuple1 = (0, 1, 2, 3, 4, 5)
| | | x
include these
|
but end here and do not include it
print(tuple1[1:4])
# output
(1, 2, 3)
tuple1 = (1, 2, 3, 4, 5, 6, 7, 8, 9)
# if i want 4, 5, 6
# count from where to start
# 4 is at the position 3
# and 7 is at position 6
print(tuple1[3:6])
# output
(4, 5, 6)
Common Use Cases:
Returning multiple values from a function:
def get_coordinates():
return (10, 20) # pass it as tuple
# assignment to variables from tuple
x, y = get_coordinates()As keys in a dictionary
dct = {('key1', 'key2'): 'value'}
# or
print({(1, 2): "key1 and 2"})
# output
{(1, 2): 'key1 and 2'}**kwargs
In Python, **kwargs is a special syntax used in functions to pass an undecided number of arguments. The term “kwargs” stands for “keyword arguments.”
When defining a function, you use **kwargs to allow the function to accept any number of keyword arguments. These arguments are passed as a dictionary where the keys are the argument names and the values are the argument values, useful when you want to create flexible functions that can handle a varying number of named arguments but name of the variables that are being passed in the function must have unique names among the variables.
def people (**kwargs):
for key, value in kwargs.items():
print (key, " ", value)
people (person1="Anas", person2="Mira")
# it will be wrong to repeat variable name person like below
# people (person="Anas", person="Mira")In this example, the function can accept any number of keyword arguments
def func_test(**kwargs):
pass
func_test(a=1)
# you cannot do func_test(1)Common Use Cases
- API Functions: Creating functions that can accept a wide range of parameters.
while loop
n = 0
while n < 5:
n += 1 ! remember to increment the condition as this is manual unlike for loop
if n == 3:
continue # skip
print(n)pass
The pass statement in Python is used as a placeholder for future code.
Here are some examples:
In a loop:
for i in range(5):
pass # Placeholder for future codeIn a function:
def my_function():
pass # Placeholder for future code In a class:
class MyClass:
pass # Placeholder for future codeIn an if statement:
if True:
pass # Placeholder for future codeUsing pass helps avoid syntax errors when you haven’t yet written the actual code
break
The break statement in Python is used to exit a loop early and exits the for or while loop
# break out of for loop
for i in range(5):
if i == 3:
break # exit if 3
print(i)
# break out of while loop
n = 0
while n < 5:
if n == 3:
break # exit if 3
print(n)
n += 1
continue
The continue statement in Python is used inside loops (like for and while) to skip the rest of the code for the current iteration and proceed directly to the next iteration of the loop
# continue in for loop
for i in range(5):
if i == 3:
continue #skip
print(i)
# continue in while loop
n = 0
while n < 5:
n += 1
if n == 3:
continue # skip
print(n).dir( )
The dir( ) function in Python is a built-in function used to list the variables (attributes) and methods of an object. Here’s a quick overview:
if no object is passed to dir( ) function then it lists the names in the current local scope
>>> print(dir())
['PS1', 'REPLHooks', '__annotations__', '__builtins__', '__doc__', '__loader__', '__name__', '__package__', '__spec__', 'get_last_command', 'original_ps1', 'sys']
# This will output the names of all the variables, functions, and imported modules in the current scope.
>>> globals () # this will show the content as well and not just the names
{'__name__': '__main__', '__doc__': None, '__package__': None, '__loader__': <_frozen_importlib_external.SourceFileLoader object at 0x000002A9582EBC50>, '__spec__': None, '__annotations__': {}, '__builtins__': <module 'builtins' (built-in)>, 'sys': <module 'sys' (built-in)>, 'original_ps1': '>>> ', 'REPLHooks': <class '__main__.REPLHooks'>, 'get_last_command': <function get_last_command at 0x000002A95889D260>, 'PS1': <class '__main__.PS1'>}Using dir( ) on a class:
>>> import math
>>> dir (math)
['__doc__', '__loader__', '__name__', '__package__', '__spec__', 'acos', 'acosh', 'asin', 'asinh', 'atan', 'atan2', 'atanh', 'cbrt', 'ceil', 'comb', 'copysign', 'cos', 'cosh', 'degrees', 'dist', 'e', 'erf', 'erfc', 'exp', 'exp2', 'expm1', 'fabs', 'factorial', 'floor', 'fma', 'fmod', 'frexp', 'fsum', 'gamma',
'gcd', 'hypot', 'inf', 'isclose', 'isfinite', 'isinf', 'isnan', 'isqrt', 'lcm', 'ldexp', 'lgamma', 'log', 'log10', 'log1p', 'log2', 'modf', 'nan', 'nextafter', 'perm', 'pi', 'pow', 'prod', 'radians', 'remainder', 'sin', 'sinh', 'sqrt', 'sumprod', 'tan', 'tanh', 'tau', 'trunc', 'ulp']
# This will output the attributes and methods of math classListing attributes of a list:
list1 = [1, 2, 3]
print(dir(list1))
['__add__', '__class__', '__class_getitem__', '__contains__', '__delattr__', '__delitem__', '__dir__', '__doc__', '__eq__', '__format__', '__ge__', '__getattribute__', '__getitem__', '__getstate__', '__gt__', '__hash__', '__iadd__', '__imul__', '__init__', '__init_subclass__', '__iter__', '__le__', '__len__', '__lt__', '__mul__', '__ne__', '__new__', '__reduce__', '__reduce_ex__', '__repr__', '__reversed__', '__rmul__', '__setattr__', '__setitem__', '__sizeof__', '__str__', '__subclasshook__', 'append', 'clear', 'copy', 'count', 'extend', 'index', 'insert', 'pop', 'remove', 'reverse', 'sort']
# This will show all the methods and attributes associated with a list object, such as append, remove, etc.Listing attributes of an object:
class MyClass:
def __init__(self):
self.name = "Python"
def greet(self):
return "Hello, " + self.name
obj = MyClass()
print(dir(obj))
['__class__', '__delattr__', '__dict__', '__dir__', '__doc__', '__eq__', '__format__', '__ge__', '__getattribute__', '__getstate__', '__gt__', '__hash__', '__init__', '__init_subclass__', '__le__', '__lt__', '__module__', '__ne__', '__new__', '__reduce__', '__reduce_ex__', '__repr__', '__setattr__', '__sizeof__', '__str__', '__subclasshook__', '__weakref__', 'greet', 'name']This will list the attributes and methods of the MyClass instance, including __init__, greet, and name.
# you can also perform dir( ) on class as well as objects
print(dir(MyClass))The dir() function is particularly useful for introspection, allowing you to explore the capabilities of objects and modules in Python, but it does not differentiate between methods / functions and attributes / variables
dir() function lists all the attributes and methods of an object, but it doesn’t differentiate between them. To distinguish between attributes (variables) and methods (functions), you can use the getattr() function along with the callable() function
class MyClass:
class_attribute = "I am a class attribute"
def __init__(self, name) -> None:
self.name = name
def greet(self):
print(f"Hello {self.name}")
Anas = MyClass ("Anas")
Anas.greet()
all_attributes = dir(Anas)
attributes = []
for attr in all_attributes:
if not callable(getattr(Anas, attr)):
attributes.append(attr)
methods = []
for method in all_attributes:
if callable(getattr(Anas, method)):
methods.append(method)
print("Attributes:")
for attri in attributes:
print(attri)
print("----------------------------")
print("Methods:")
for meth in methods:
print(meth + "()")
# output
Attributes:
__dict__
__doc__
__module__
__weakref__
class_attribute
name
----------------------------
Methods:
__class__()
__delattr__()
__dir__()
__eq__()
__format__()
__ge__()
__getattribute__()
__getstate__()
__gt__()
__hash__()
__init__()
__init_subclass__()
__le__()
__lt__()
__ne__()
__new__()
__reduce__()
__reduce_ex__()
__repr__()
__setattr__()
__sizeof__()
__str__()
__subclasshook__()
greet()attributes
Attributes in a class are essentially variables that belong to the class and its instances. There are two main types of attributes in a class:
Instance Attributes
These are attributes that are specific or unique to instance only and are not shared among all instances. They are usually defined within the __init__ method and are accessed using the self keyword.
class MyClass:
def __init__(self, name):
self.name = name # Instance attribute
obj1 = MyClass("Alice")
obj2 = MyClass("Bob")
print(obj1.name) # Output: Alice
print(obj2.name) # Output: BobClass Attributes
These are attributes that are shared among all instances of the class. They are defined directly within the class, outside of any methods.
class MyClass:
class_attribute = "I am a class attribute" # Class attribute
# class attributes are backed into every object
# that is created from this class
# class attribute is like DNA
def __init__(self, name):
self.name = name # Instance attribute
obj1 = MyClass("Alice")
obj2 = MyClass("Bob")
print(MyClass.class_attribute) # Output: I am a class attribute
print(obj1.class_attribute) # Output: I am a class attribute
print(obj2.class_attribute) # Output: I am a class attribute
Accessing Attributes
- Instance attributes are accessed using the instance name followed by a dot and the attribute name (e.g.,
obj1.name). - Class attributes can be accessed using the class name (e.g.,
MyClass.class_attribute) or through an instance (e.g.,obj1.class_attribute).
__init__ (self, value1, value2 … ):
class Person:
def __init__(self, name, age):
self.name = name
self.age = age
# like class attributes these variables are now defined
# use of self.name will create a variable inside the object
# self.name's self will also differentiate the argument's name
# with the object's name
# __init__ needs first argument as object and self is passed to it and "instance attributes"
def introduce(self):
print(f"Hello, my name is {self.name} and I am {self.age} years old.")
# Creating an instance of the Person class
person1 = Person("Alice", 30)
person1.introduce()
# another example
class person:
entity_type = "Human"
dimension = "3rd"
def __init__(self, name):
self.name = name
def introduce(self) -> None:
print(
f"Hello my name is {self.name} and I welcome you to {self.dimension} dimension"
)
person1 = person("Anas")
person1.introduce()
# output
Hello my name is Anas and I welcome you to 3rd dimensionDouble underscore methods such as __init__ etc
>>> dir(Person)
['__class__', '__delattr__', '__dict__', '__dir__', '__doc__', '__eq__', '__format__', '__ge__', '__getattribute__', '__gt__', '__hash__', '__init__', '__init_subclass__', '__le__', '__lt__', '__module__', '__ne__', '__new__', '__reduce__', '__reduce_ex__', '__repr__', '__setattr__', '__sizeof__', '__str__', '__subclasshook__', '__weakref__', 'age', 'country', 'name']The names you listed with double underscores (__) are known as “dunder” (double underscore) methods or “magic” methods in Python. These methods are special methods that have specific meanings and are used to define the behavior of objects in Python. Here’s a brief overview of some of them:
__init__: Initializes a new instance of a class.__str__: Returns a string representation of an object.__repr__: Returns an official string representation of an object.__eq__: Defines the behavior for the equality operator==.__lt__: Defines the behavior for the less-than operator<.__dict__: A dictionary or other mapping object used to store an object’s (writable) attributes.__class__: References the class to which an instance belongs.
Namespaces, Scope & Variables
https://realpython.com/python-namespaces-scope
Symbolic names: when you create a variable x
x = ‘something’, you have technically created a symbolic name x that refers to string object ‘something’
In a program of any complexity, you’ll create hundreds or thousands of such names, each pointing to a specific object. How does Python keep track of all these names so that they don’t interfere with one another? Enter Namespaces, Namespaces can be thought of as a nested collections containing loads of <object names: object’s content>
Namespaces in Python
You can think of a namespace as a dictionary in which the keys are the object names and the values are the objects themselves, Each key-value pair maps a name to its corresponding object.
In a Python program, there are four types of namespaces:
- Built-In
- Global
- Enclosing
- Local
These have differing lifetimes. As Python executes a program, it creates namespaces as necessary and deletes them when they’re no longer needed. Typically, many namespaces will exist at any given time.
The Built-In Namespace
The built-in namespace contains the names of all of Python’s built-in objects. These are available at all times when Python is running.
You can list the objects in built-in namespace using following command
dir(__builtins__)
['ArithmeticError', 'AssertionError', 'AttributeError',
'BaseException','BlockingIOError', 'BrokenPipeError', 'BufferError',
'BytesWarning', 'ChildProcessError', 'ConnectionAbortedError',
'ConnectionError', 'ConnectionRefusedError', 'ConnectionResetError',
'DeprecationWarning', 'EOFError', 'Ellipsis', 'EnvironmentError',
'Exception', 'False', 'FileExistsError', 'FileNotFoundError',
'FloatingPointError', 'FutureWarning', 'GeneratorExit', 'IOError',
'ImportError', 'ImportWarning', 'IndentationError', 'IndexError',
'InterruptedError', 'IsADirectoryError', 'KeyError', 'KeyboardInterrupt',
'LookupError', 'MemoryError', 'ModuleNotFoundError', 'NameError', 'None',
'NotADirectoryError', 'NotImplemented', 'NotImplementedError', 'OSError',
'OverflowError', 'PendingDeprecationWarning', 'PermissionError',
'ProcessLookupError', 'RecursionError', 'ReferenceError', 'ResourceWarning',
'RuntimeError', 'RuntimeWarning', 'StopAsyncIteration', 'StopIteration',
'SyntaxError', 'SyntaxWarning', 'SystemError', 'SystemExit', 'TabError',
'TimeoutError', 'True', 'TypeError', 'UnboundLocalError',
'UnicodeDecodeError', 'UnicodeEncodeError', 'UnicodeError',
'UnicodeTranslateError', 'UnicodeWarning', 'UserWarning', 'ValueError',
'Warning', 'ZeroDivisionError', '_', '__build_class__', '__debug__',
'__doc__', '__import__', '__loader__', '__name__', '__package__',
'__spec__', 'abs', 'all', 'any', 'ascii', 'bin', 'bool', 'bytearray',
'bytes', 'callable', 'chr', 'classmethod', 'compile', 'complex',
'copyright', 'credits', 'delattr', 'dict', 'dir', 'divmod', 'enumerate',
'eval', 'exec', 'exit', 'filter', 'float', 'format', 'frozenset',
'getattr', 'globals', 'hasattr', 'hash', 'help', 'hex', 'id', 'input',
'int', 'isinstance', 'issubclass', 'iter', 'len', 'license', 'list',
'locals', 'map', 'max', 'memoryview', 'min', 'next', 'object', 'oct',
'open', 'ord', 'pow', 'print', 'property', 'quit', 'range', 'repr',
'reversed', 'round', 'set', 'setattr', 'slice', 'sorted', 'staticmethod',
'str', 'sum', 'super', 'tuple', 'type', 'vars', 'zip']If you look you will recognise some of the commonly used functions as well such as print etc.
The Python interpreter creates the built-in namespace when it starts up. This namespace remains in existence until the interpreter terminates.
The Global Namespace
The global namespace contains any names defined at the level of the main program. Python creates the global namespace when the main program body starts, and it remains in existence until the interpreter terminates. term global namespace.
globals()
# globals( ) function gets us objects inside global namespace as a dictionary
{'__name__': '__main__', '__doc__': None, '__package__': None, '__loader__': <_frozen_importlib_external.SourceFileLoader object at 0x000001B4289CBCB0>, '__spec__': None, '__annotations__': {}, '__builtins__': <module 'builtins' (built-in)>, '__file__': 'g:\\My Drive\\0_Python\\Projects\\Learning_Sandbox\\Intro.py', '__cached__': None}
for key, val in dict(globals()).items(): # 1
print(f"{key}: {val}")
# 1: dict() function was used to force copy of the globals
# because running code with 'for key, val in globals().items()'
# gives error message 'RuntimeError: dictionary changed size during iteration'Strictly speaking, this may not be the only global namespace that exists. The interpreter also creates a global namespace for any module that your program loads with the import statement.
The Local and Enclosing Namespaces
Every function creates its own local namespace which is destroyed when function returns or exits. The interpreter creates a new namespace whenever a function executes. That namespace is local to the function and remains in existence until the function terminates. If we call the function multiple times each call creates new local scope
You can also define one function inside another:
def f():
print("Start f")
def g():
print("Start g")
print("End g")
return
g()
print("End f")
return
f()
# output
Start f
Start g
End g
End fWhen the main program calls f( ), Python creates a new namespace for f( ). Similarly, when f( ) calls g( ), g( ) gets its own separate namespace. The namespace created for g( ) is the local namespace, and from the perspective of g( ) the namespace created for f( ) is the enclosing namespace.
Each of these namespaces remains in existence until its respective function terminates.
In fact inner_function can access variables from all parent function’s namespaces above it including:
Global Namespace: Variables defined at the top level of the script or module.
Built-in Namespace: Names preassigned in Python (like len, print, etc.)
inner functions codes can access outer scope objects or names but outer scope codes cannot access inner scope objects or names.
What if there are 3 nested functions?
Yes, in Python, the innermost function can access the variables and names defined in all enclosing functions, including the outermost function. This is due to the concept of closures and the scope chain.
Here’s an example with three nested functions:
def outer_function():
outer_variable = 'I am outer'
def middle_function():
middle_variable = 'I am middle'
def inner_function():
inner_variable = 'I am inner'
print(inner_variable) # Accessing local variable
print(middle_variable) # Accessing middle function variable
print(outer_variable) # Accessing outer function variable
inner_function()
middle_function()
outer_function()
# output
I am inner
I am middle
I am outer
# another example
x = "x defined in global"
print(f"calling from global: {x}")
print("----------------------")
def level1():
y = "y defined in level1()"
print(f"calling from level1(): {x}")
print(f"calling from level1(): {y}")
print("----------------------")
def level2():
z = "z defined in level2()"
print(f"calling from level2(): {x}")
print(f"calling from level2(): {y}")
print(f"calling from level2(): {z}")
print("----------------------")
level2()
level1()
# output
calling from global: x defined in global
----------------------
calling from level1(): x defined in global
calling from level1(): y defined in level1()
----------------------
calling from level2(): x defined in global
calling from level2(): y defined in level1()
calling from level2(): z defined in level2()
----------------------
# first level1() is called and then level2()
# as level2() is called inside level1()
# even because of order of code and indents it
# looks like level2() was called but that is not
# the case
# another example
x = "x in global"
print(x)
def level1():
x = "x in level1()"
print(x)
def level2():
print(x) # 1
del x
print (x)
# error will happen because we deleted x in local scope
level2()
level1()
#1 If x is deleted then local scope will have no reference to x and above error will happen
# another example
x = "x in global"
print(x)
def level1():
x = "x in level1()"
print(x)
def level2():
print(x) # 1
level2()
level1()
x in global
x in level1()
x in level1()Variable Scope
The existence of multiple, distinct namespaces means several different instances of a particular name can exist simultaneously while a Python program runs. As long as each instance is in a different namespace, they’re all maintained separately and won’t interfere with one another.
But that raises a question: Suppose you refer to the name x in your code, and x exists in several namespaces. How does Python know which one you mean?
The answer lies in the concept of scope. The interpreter determines this at runtime
if your code refers to the name x, then Python searches for x in the following namespaces in the order shown (LEGB order):
- Local: If you refer to x inside a function, then the interpreter first searches for it in the innermost scope that’s local to that function.
- Enclosing: If x isn’t in the local scope but appears in a function that resides inside another function, then the interpreter searches in the enclosing function’s scope.
- Global: If neither of the above searches is fruitful, then the interpreter looks in the global scope next.
- Built-in: If it can’t find x anywhere else, then the interpreter tries the built-in scope.
This is the LEGB rule as it’s commonly called in Python literature
The interpreter searches for a name from the inside out, looking in the local, enclosing, global, and finally the built-in scope:

If the interpreter doesn’t find the name in any of these locations, then Python raises a NameError exception.
Single Definition
In the first example, x is defined in only one location, it resides in the global scope:
x = "global x"
def f():
def g():
print(x)
g()
f()
# output
global xDouble Definition
In the next example, the definition of x appears in two places
x = "global x"
def f():
x = "enclosing x"
def g():
print(x)
g()
f()
# output
enclosing xAccording to the LEGB rule, the interpreter finds the value from the enclosing scope before looking in the global scope. So the print() statement on line 7 displays ‘enclosing’ instead of ‘global’.
Triple Definition
n the next example, the definition of x appears in three places
x = "global x"
def f():
x = "enclosing x"
def g():
x = "local x"
print(x)
g()
f()
# output
local xHere, the LEGB rule dictates that g( ) sees its own local value of x first
No Definition
def level1():
def level2():
print(x)
level2()
level1()
Python Namespace Dictionaries
Earlier in this tutorial, when namespaces were first introduced, you were encouraged to think of a namespace as a dictionary in which the keys are the object names and the values are the objects themselves
In fact, for global and local namespaces, that’s precisely what they are! Python really implements these namespaces as dictionaries, the ones that are declared using { }, the only exception to this is __builtin__ namespace, __builtin__ doesn’t behave like a dictionary. Python implements it as a module, we will see that, it is eveident from the name __builtin__ that it is special
Python provides built-in functions called globals() and locals() that allow you to access global and local namespace dictionaries.
The globals( ) function
The built-in function globals() returns global namespace dictionary. You can use it to access the objects in the global namespace.
type(globals())
<class 'dict'>
globals()
{'__name__': '__main__', '__doc__': None, '__package__': None,
'__loader__': <class '_frozen_importlib.BuiltinImporter'>, '__spec__': None,
'__annotations__': {}, '__builtins__': <module 'builtins' (built-in)>}This is what is added by interpreter in globals namespace even before you have coded anything
now lets see what happens when we define a variable in the global scope:
x = 'foo'
globals()
{'__name__': '__main__', '__doc__': None, '__package__': None,
'__loader__': <class '_frozen_importlib.BuiltinImporter'>, '__spec__': None,
'__annotations__': {}, '__builtins__': <module 'builtins' (built-in)>,
'x': 'foo'}After the assignment statement x = ‘foo’, a new item appears in the global namespace dictionary.
If you are wondering why the contents of the module and class are not shown and just their description is shown, that is because it is easier to display small excerpt instead of long classes and modules, it can be seen that ‘x’ is the key in dictionary
Direct and Indirect access of the namespaces
You would typically access this object in the usual way, by referring to its symbolic name, x. But you can also access it indirectly through the global namespace dictionary:
x
# 'foo'
globals()['x']
# 'foo'
x is globals()['x']
# TrueThe is comparison confirms that these are in fact the same object. <namespace>( )[‘x’] can be used anywhere in code and objects inside that namespace can be accessed from anywhere indirectly even when there is no access to the namespace
You can create and modify entries in the global namespace using the globals() function as well as it is available for us to use and change just like any other dictionary:
globals()['y'] = 100
globals()
{'__name__': '__main__', '__doc__': None, '__package__': None,
'__loader__': <class '_frozen_importlib.BuiltinImporter'>, '__spec__': None,
'__annotations__': {}, '__builtins__': <module 'builtins' (built-in)>,
'x': 'foo', 'y': 100}
y
# 100
globals()['y'] = 3.14159
# notice that how we have to use ['y'] and not [y] because using [y] will result in this in globals dictionary: { 100: 3.14159 } which is valid as 100 can be key
y
3.14159The locals( ) function
Python also provides a corresponding built-in function called locals(). It’s similar to globals() but accesses objects in the local namespace instead:
def f(x, y):
a = "foo"
print(locals())
f(1, 2)
{'x': 1, 'y': 2, 'a': 'foo'}Notice that, in addition to the locally defined variable s, the local namespace includes the function parameters x and y since these are local to f() as well.
If you call locals() outside a function in the main program, then it behaves the same as globals(), because outside of the functions, locals ( ) will have same content as globals ( )

Deep Dive: A Subtle Difference Between globals() and locals() in same namespace level
globals() returns an actual reference to the dictionary that contains the global namespace, new variables will show up in the dictionary:
print(globals())
{'__name__': '__main__', '__doc__': None, '__package__': None, '__loader__': <_frozen_importlib_external.SourceFileLoader object at 0x0000018A7FCEBCB0>, '__spec__': None, '__annotations__': {}, '__builtins__': <module 'builtins' (built-in)>, '__file__': 'g:\\My Drive\\0_Python\\Projects\\Learning_Sandbox\\Intro.py', '__cached__': None}
x = "foo"
y = 29
print(globals())
{'__name__': '__main__', '__doc__': None, '__package__': None, '__loader__': <_frozen_importlib_external.SourceFileLoader object at 0x00000276F7AEBCB0>, '__spec__': None, '__annotations__': {}, '__builtins__': <module 'builtins' (built-in)>, '__file__': 'g:\\My Drive\\0_Python\\Projects\\Learning_Sandbox\\Intro.py', '__cached__': None, 'x': 'foo', 'y': 29}locals(), on the other hand, returns a dictionary that is a current “copy” of the local namespace, and not actual locals namespace like globals( ) function does
Changes in local namespace won’t update or effect previously stored copy until you call it again, because it was a true copy that was returned by locals( ) function
def f():
a = 1
local1 = locals()
print(local1)
a = 2
print(local1)
# still shows a = 1
print(locals()["a"])
# now it will show a = 2 as we got fresh copy
# by calling locals() again
f()
{'a': 1}
{'a': 1}
2Modify Variables Out of Scope
Situation exists when a function tries to modify a variable outside its local scope. A function can’t modify an immutable object outside its local scope at all:
x = 20
def f():
x = 40
print(x)
f() # 40
print(x) # 20When f() executes the assignment x = 40 on line 3, it creates a new local reference. At that point, f() loses the reference to the object named x in the global namespace. So the assignment statement doesn’t affect the global object. But after f() terminates, x in the global scope is still 20.
A function can “modify” an object of mutable type that’s outside its local scope
list1 = ["something", "is", "wrong"]
def change_list():
list1[1] = "is not"
change_list()
print(list1)
# output
['something', 'is not', 'wrong']But if f() tries to reassign my_list entirely, then it will create a new local object and won’t modify the global my_list:
list1 = ["something", "is", "wrong"]
def change_list():
list1 = ["something", "is", "off"]
print(list1)
change_list()
print(list1)
# output
['something', 'is', 'off']
['something', 'is', 'wrong']globals declaration
What if you really do need to modify a value in the global scope from within f()?
x = 20
def f():
global x #1
x = 40
print(x)
f()
print(x) #2
#1 global x declares that this x is same global x
#1 but this declaration must come on top inside the
#1 otherwise this error can be seen
def func1():
print(x)
del x
global x
x = 100
SyntaxError: name 'x' is used prior to global declaration
#2 global x was modified as expected Assignment x = 40 doesn’t create a new reference. It assigns a new value to x in the global scope

you could accomplish the same thing using globals() dictionary.
x = 20
def f():
globals()["x"] = 40
print(x)
f()
print(x)
# single line multiple declarations
# and declaring the global variables
# inside the function's namespace
x, y, z = 10, 20, 30
def f():
global x, y, zWhat if a function wants to modify values in enclosing or parent fucntion above it and not use global scope for setting and retrieving values
To modify variable in the enclosing scope from inside g(), you need the analogous keyword nonlocal. Names specified after the nonlocal keyword refer to variables in the nearest enclosing scope
def f():
x = 20
def g():
nonlocal x
x = 40
g()
print(x)
f()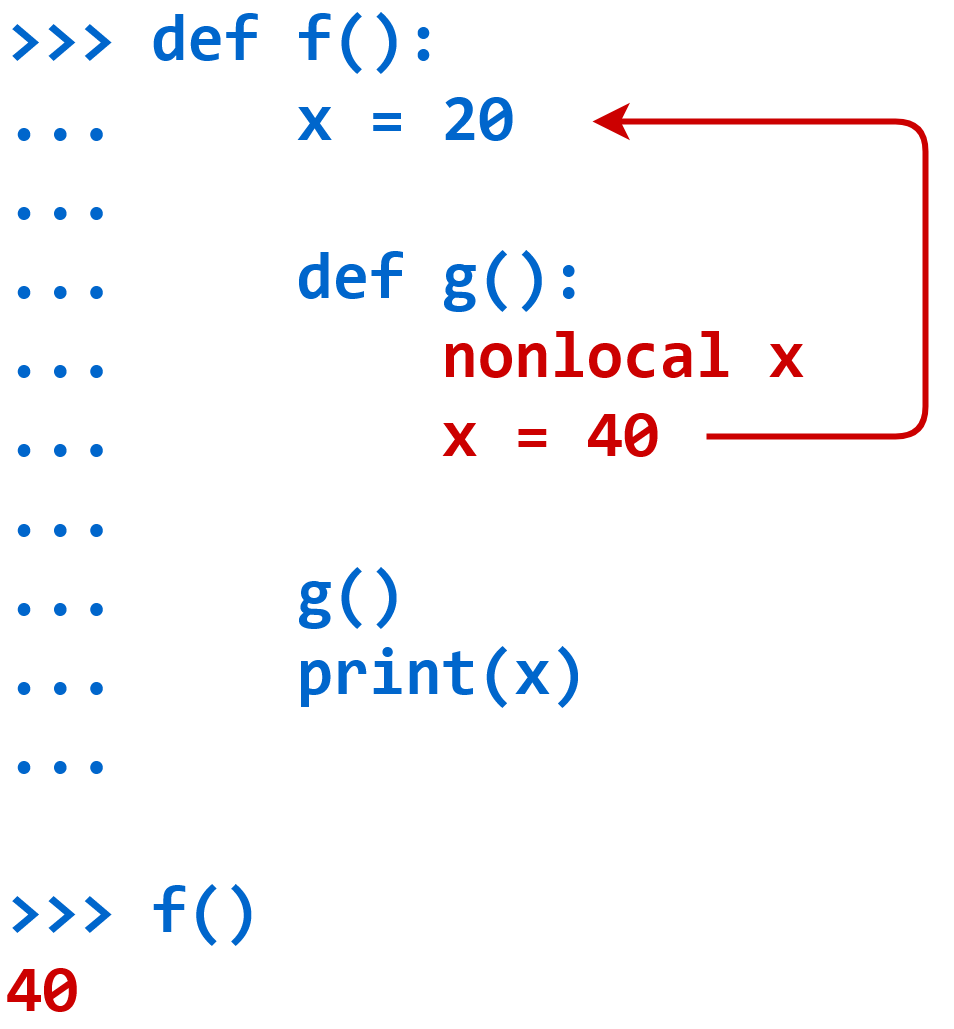
# another example
def func1():
func1 = 111
def func2():
nonlocal func1
func1 = 222
func2()
print(func1)
func1()prettytable
# install prettytable
pip install prettytable
from prettytable import PrettyTable
# Specify the Column Names while initializing the Table
# note that columns and rows are passed as one list as argument
# not as individual strings or variables
table1 = PrettyTable(["Name", "Class", "Section", "Percentage"])
or
table1 = PrettyTable()
table1.field_names = ["City name", "Area", "Population", "Annual Rainfall"]
table1.add_row(["Adelaide", 1295, 1158259, 600.5])
# Add rows
# if you do not pass values in the list that
# are equal to columns in the table, prettytable
# will error "Row has incorrect number of values, (actual) 1!=2 (expected)"
table.add_row(["Brisbane", 5905, 1857594, 1146.4])
table.add_row(["Darwin", 112, 120900, 1714.7])
table.add_row(["Hobart", 1357, 205556, 619.5])
print(table1)Pretty table requires lists while setting up column names and also when entering data such as add_row function, that also requires lists
you can simply print the table in the end
Adding data by column
You can add data one column at a time as well. To do this you use the add_column method, which takes two arguments – a string which is the name of the column and a list of data that should go in
table.add_column("City name",
["Adelaide","Brisbane","Darwin","Hobart","Sydney","Melbourne","Perth"])
# another example
table1 = PrettyTable()
table1.add_column("Attributes", attributes)
table1.add_column("Methods", methods)
print(table1)
# but doing this might cause this error since both columns are not
# of same size "ValueError: Column length 23 does not match number of rows 6"
Fix is to pad the smaller list with empty string to make it same size
from prettytable import PrettyTable
def show_attr_methods(object):
all_attributes = dir(object)
attributes = []
for attr in all_attributes:
if not callable(getattr(object, attr)):
attributes.append(attr)
methods = []
for method in all_attributes:
if callable(getattr(object, method)):
methods.append(method + "()")
if len(attributes) != len(methods):
print("both lists are not equals")
if len(attributes) > len(methods):
print(len(attributes) - len(methods))
for x in range(len(attributes) - len(methods)):
methods.append("")
elif len(attributes) < len(methods):
print(len(methods) - len(attributes))
for x in range(len(methods) - len(attributes)):
attributes.append("")
print(type(object))
table1 = PrettyTable()
table1.add_column("Attributes", attributes)
table1.add_column("Methods", methods)
table1.sortby = "Methods"
print(table1)
class person:
type = "Human"
def __init__(self, name):
self.name = name

Sorting
table.sortby = "Age"Alignment
table.align["Name"] = "l" # Left-align the 'Name' column
table.align["City"] = "r" # Right-align the 'City' columnAlignment of individual columns
table.align["City name"] = "l"
table.align["Area"] = "c"
table.align["Population"] = "r"
table.align["Annual Rainfall"] = "c"
print(table)
Border & Padding
table.border = False
table.padding_width = 2Adding sections to a table
table.add_row(["Hobart", 1357, 205556, 619.5], divider=True)
Deleting Rows
myTable.del_row(0)Clearing the Table
myTable.clear_rows()This will clear the entire table (Only the Column Names would remain).
Export to Other Formats
PrettyTable allows you to export tables to different formats such as HTML, CSV, or JSON:
# Export to HTML
print(table.get_html_string())
# Setting HTML escaping
# By default, PrettyTable will escape the data contained in the header
# and data fields when sending output to HTML. This can be disabled by
# setting the escape_header and escape_data to false. For example:
print(table.get_html_string(escape_header=False, escape_data=False))
# Export to CSV
print(table.get_csv_string())
# Export to JSON
print(table.get_json_string())Importing from CSV
from prettytable import from_csv
with open("myfile.csv") as fp:
mytable = from_csv(fp)Importing data from a database
import sqlite3
from prettytable import from_db_cursor
connection = sqlite3.connect("mydb.db")
cursor = connection.cursor()
cursor.execute("SELECT field1, field2, field3 FROM my_table")
mytable = from_db_cursor(cursor)Copying a table
new_table = old_table[0:5]list = [ ] – remember [] looks like a list
A Python list is a versatile and powerful data type used to store collections of items, it is like a tuple but values in positions can be changed. You can change, add, and remove items after the list has been created, while we cannot make changes on tuple, Lists can contain duplicate values.
Lists are created using square brackets [] which to be fair looks like a list itself, with items separated by commas, just like an array in PHP
my_list = ["apple", "banana", "cherry"]
# changing value on location 1
my_list[1] = "blueberry"
print(my_list) # Output: ["apple", "blueberry", "cherry"]Lists maintain the order of items. The first item has an index of 0, the second item has an index of 1, and so on.
print(my_list[0]) # Output: appleDuplicate values allowed
my_list = ["apple", "banana", "apple"]
print(my_list) # Output: ["apple", "banana", "apple"]A list can contain items of different data types, including strings, integers, and even other lists.
mixed_list = ["text", 123, True, [1, 2, 3]]
print(mixed_list) # Output: ["text", 123, True, [1, 2, 3]]Appending to list using append( ):
my_list.append("date")
print(my_list) # Output: ["apple", "banana", "cherry", "date"]Removing Items using remove( ):
my_list.remove("banana")
# directly reference the value to delete and not the key
print(my_list) # Output: ["apple", "cherry", "date"]
Length of List using len( ):
print(len(my_list)) # Output: 3
Slicing:
sub_list = my_list[1:3]
print(sub_list) # Output: ["cherry", "date"]Iterating through list
for item in my_list:
print (item)Keys are not part of the list but we can bring it using enumerate( ):
my_list = ["apple", "banana", "cherry"]
for index, value in enumerate(my_list):
print(f"Index: {index}, Value: {value}")Nested list loop
matrix = [
[1, 2, 3],
[4, 5, 6],
[7, 8, 9]
]
for row in matrix:
for value in row:
print(value, end=" ")
print() # Newline after each rowdel – delete objects
del is used to delete objects and any type of objects such as variables, lists, dictionary or its entries, and even entire objects, Frees up memory. Just like def, del is written as a construct, not as a function as it does not have ( ) parentheses.
Deleting a Variable
x = 10
print(x) # Output: 10
del x
print(x) # Raises NameError: name 'x' is not definedDeleting an Item from a List
my_list = [1, 2, 3, 4, 5]
del my_list[2]
print(my_list) # Output: [1, 2, 4, 5]Deleting a Slice from a List
my_list = [1, 2, 3, 4, 5]
del my_list[1:3]
# slice does not remove the last in range such as only my_list[1] and my_list[2] will be removed but not my_list[3], since position values start from 0
print(my_list)
#output: [1, 4, 5]
# another example
list1 = [1, 2, 3, 4, 44, 55, 5, 6, 7, 8, 9]
print(list1[4:6])
del list1[4:6]
print(list1)
Deleting a Dictionary Entry
my_dict = {'a': 1, 'b': 2, 'c': 3}
del my_dict['b']
print(my_dict) # Output: {'a': 1, 'c': 3}
Deleting an Object
class MyClass:
pass
obj = MyClass()
print(obj) # Output: <__main__.MyClass object at 0x...>
del obj
print(obj) # Raises NameError: name 'obj' is not definedid( )
The id() function in Python returns a unique identifier (memory address) for an object, You can use id() to check if two variables are pointing to the same object in memory, once an object is deleted using ‘del’ or any other way then that memory address or id can be reused by other objects
Basic Usage of id()
x = 10
y = 10
print(id(x)) # Prints the ID of the object 10
print(id(y)) # also prints the same id as x
# the reason they have same IDs is because of optimisation by python
# remember when we assign x = 10, x becomes 10
# and then when we assign y = 10, y also becomes 10
print (x == y) # True
print (id(x) == id(y)) # True
z = 20
print(id(z)) # Prints the ID of the object 20
Demonstrating Object Identity
x = [1, 2, 3] # this is a list
y = x # y points to the same list as x
# Same ID for both x and y
print(id(x))
print(id(y))
print(id(x) == id(y))
#output
True
y.append(4)
# Modifying y also modifies x because they refer to the same object as seen above that their memory address is same
print(x) # Output: [1, 2, 3, 4]
print(id(x) == id(y)) # True, they are still the same objectComparing Mutable and Immutable Types
x = [1, 2, 3]
y = [1, 2, 3]
# Different IDs because x and y are different objects
print(id(x))
print(id(y))
# different example
a = 42
b = 42
# Same ID because python optimizes by reusing objects
print(id(a))
print(id(b))len( )
my_list = [1, 2, 3, 4, 5]
# Count the size of the list
print (len(my_list))
# String
my_string = "Hello"
print(len(my_string)) # Output: 5
# Tuple
my_tuple = (1, 2, 3)
print(len(my_tuple)) # Output: 3
# Dictionary
my_dict = {"a": 1, "b": 2, "c": 3}
print(len(my_dict)) # Output: 3 (number of keys)
# Set
my_set = {1, 2, 3, 4}
print(len(my_set)) # Output: 4multiline comments
https://stackoverflow.com/questions/7696924/how-do-i-create-multiline-comments-in-python
“”” or ”’ is sometimes used for commenting and for multiline comments but in reality these are multiline strings and not the comments
'''
This is a multiline
comment.
'''
"""
This is a multiline
comment.
"""
I would advise against using """ for multi line comments!
Here is a simple example to highlight what might be considered an unexpected behavior:
print(
"This is one line",
"""
This is second line
but it is multiline
"""
"this is 3rd line",
)
Now have a look at the output:
This is one line
This is second line
but it is multiline
this is 3rd line
The multi line string was not treated as comment, but it was concatenated with next string
if you want to comment multiple lines, use # and in vscode use shortcut Ctrl + K Ctrl + C combination together and lines will be commented using #
if elif else
if True:
pass
x = 10
if x > 5:
print("x is greater than 5")
If with else
x = 3
if x > 5:
print("x is greater than 5")
else:
print("x is not greater than 5")
If with elif and else
x = 7
if x > 10:
print("x is greater than 10")
elif x > 5:
# elif comes first and then else comes in the end
# elif can not come after else
print("x is greater than 5 but less than or equal to 10")
else:
print("x is 5 or less")comparison operators
x == yinterpreter, simply enter object in interactive mode ‘>>>’
by simply entering the object’s name, the interpreter prints the object but first you have to create the object as interpreter instance when launched in interactive mode does not have your code so you have to create the object first
>>> x = 10
>>> x
10
.callable( )
xxxxxxx
.getattr( )
xxxxxxx
Helper code & tools
Print attributes and methods of the object in a prettytable
from prettytable import PrettyTable
def show_attr_methods(object):
all_attributes = dir(object)
attributes = []
for attr in all_attributes:
if not callable(getattr(object, attr)):
attributes.append(attr)
methods = []
for method in all_attributes:
if callable(getattr(object, method)):
methods.append(method + "()")
if len(attributes) != len(methods):
print("both lists are not equals")
if len(attributes) > len(methods):
print(len(attributes) - len(methods))
for x in range(len(attributes) - len(methods)):
methods.append("")
elif len(attributes) < len(methods):
print(len(methods) - len(attributes))
for x in range(len(methods) - len(attributes)):
attributes.append("")
print(type(object))
table1 = PrettyTable()
table1.add_column("Attributes", attributes)
table1.add_column("Methods", methods)
table1.sortby = "Methods"
print(table1)
class person:
type = "Human"
def __init__(self, name):
self.name = nameExample complex code stackoverflow
from prettytable import PrettyTable
def column_pad(*columns):
max_len = max([len(c) for c in columns])
for c in columns:
c.extend(['']*(max_len-len(c)))
# columns names
columns = ["Characters", "FFF", "Job"]
# lists
lista1 = ["Leonard", "Penny", "Howard", "Bernadette", "Sheldon", "Raj","Amy"]
lista2 = ["X", "X", "X", "X"]
lista3 = ["B", "C", "A", "D", "A", "B"]
column_pad(lista1,lista2,lista3)
# init table
myTable = PrettyTable()
# Add data
myTable.add_column(columns[0], lista1)
myTable.add_column(columns[1], lista2)
myTable.add_column(columns[2], lista3)
print(myTable)*args
In Python, the *columns syntax in a function definition indicates that the function can accept a variable number of positional arguments, which are collected into a tuple
the columns parameter will hold all the arguments passed to the function as a tuple
You can pass zero or more arguments to the function.
def column_pad(*columns):
max_len = max([len(c) for c in columns])
for c in columns:
c.extend(['']*(max_len-len(c)))
column_pad(lista1,lista2,lista3)
# another example
def args1(*values):
print(values) # 'values' is a tuple containing all the passed arguments.
args1("val1", "val2", "val3")
('val1', 'val2', 'val3')list comprehensions
List comprehensions are a powerful, they can generate list and also at the same time apply an expression to each element in iterable fashion for optional filtering. This simplifies and reduces code that would have required multiple lines of loop and conditions.
[expression for item in iterable (optional if_condition)]expression: This is the value that will go as a value in the new list.item: The current element being iterated over from theiterable.iterable: The source collection (e.g., a list, tuple, range, set, or generator) to iterate over.if_condition(optional): A filter that specifies which elements from theiterablewill be included.
How It Works
- The
iterableis iterated through one element at a time. - Each
itemis evaluated against theif condition(if provided). - The
expressionis applied to each validitem, and the result is added to the output list.
so we can read this in reverse by reading it from “for x in list1” then “if condition” if it exists and then expression which will be the value that new list will be populated with
# traditional code
square = []
for num in range(5):
square.append(num)
print(square)
# list comprehension
del square
square = [num for num in range(5)]
# | |
# | |
# num is what will be individual values in
# list so we will just use 'num'
# |
# |
# for loop start
print(square)
# list comprehension with if condition
evens = [num for num in range(0, 10) if num % 2 == 0]
print(evens)
# nested compression
pairs = [(x, y) for x in range(1, 2) for y in (33, 44)]
print(pairs)casting
# casting
# integers
x = int(1) # 1
y = int(2.8) # 2
z = int("3") # 3
# floats
x = float(1) # 1.0
y = float(2.8) # 2.8
z = float("3") # 3.0
w = float("4.2") # 4.2
# strings
x = str("s1") # s1
y = str(2) # 2
z = str(3.0) # 3.0Exception Handling
https://realpython.com/python-exceptions/
Python exceptions provide a mechanism for handling errors that occur during the execution of a program, Unlike syntax errors, which are detected by the parser (like when indentation is wrong or you missed a brace or parenthesis)
Knowing how to raise, catch, and handle exceptions is key to programming an error safe program
Arrow indicates that there was error syntax message, but if we run a code that is correct on syntax but has an issue with logic
>>> print(0 / 0)
Traceback (most recent call last):
File "<stdin>", line 1, in <module>
ZeroDivisionError: division by zeroPython details what type of exception error it encountered. It was a exception of type ZeroDivisionError.
Python comes with various built-in exceptions as well as user-defined exceptions which users can create as well
You can also “raise” exception manually because exceptions are handled at the end of the program and not just for logical errors in python that was raised by Puthon Interpreter but you can also raise exceptions for your own program’s logic
Assume that you’re writing a tiny toy program that expects only numbers up to 5. You can raise an error when an unwanted condition occurs:
number = 10
if number > 5:
raise Exception(f"The number should not exceed 5. ({number=})")
print(number)Traceback (most recent call last):
File "./low.py", line 3, in <module>
raise Exception(f"The number should not exceed 5. ({number=})")
Exception: The number should not exceed 5. (number=10Note that the final call to print() never executed, because Python raised the exception before it got to that line of code. which means that code execution stops upon encountering an exception.
With the raise keyword, you can raise any exception object in Python and stop your program when an unwanted condition occurs
Assert – exception that’s a bit different than the others
Python offers a specific exception type that you should only use when debugging your program during development, This exception is the AssertionError. The AssertionError is special because you shouldn’t ever raise it yourself using raise.
Instead, you use the “assert” keyword to check whether a condition is met and let Python raise the AssertionError if the condition isn’t met.
The idea of an assertion is that your program should only attempt to run if certain conditions are in place. If Python checks your assertion and finds that the condition is True, then that is excellent! The program can continue. If the condition turns out to be False, then your program raises an AssertionError exception and stops right away
So you can replace the if condition with an assertion
number = 1
if number > 5:
raise Exception(f"The number should not exceed 5. ({number=})")
print(number)to this
number = 1
assert (number < 5), f"The number should not exceed 5. ({number=})"
print(number)If the number in your program is below 5, then the assertion passes and your script continues, However, if you set number to a value higher than 5—for example, 10—then the outcome of the assertion will be False and assertion will be thrown and program also stops
number = 10
assert (number < 5), f"The number should not exceed 5. ({number=})"
print(number)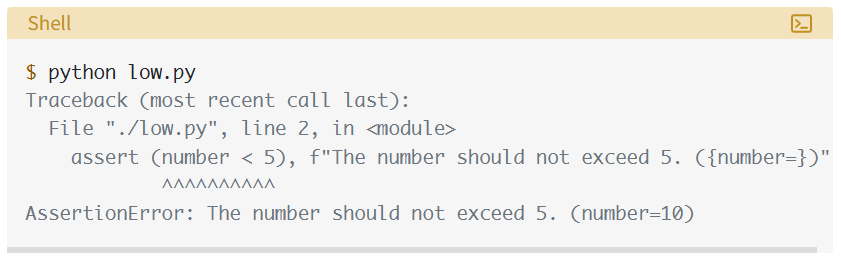
Using assertions in this way can be helpful when you’re debugging your program during development because it can be quite a fast and straightforward to add assertions into your code otherwise it is not mandatory to use it in code.
In production when python code is run, it is run in optimized mode where all the assertion statements are removed, which means that assertions aren’t a reliable way to handle runtime errors in production code so it is best to raise an exception, above exercise is to only teach about assertion so when you encounter it in code in real life, you know what it is
Handling Exceptions With the try and except Block
try:
some_code()
except:
passRemember except stands for exception
Example code for raising RuntimeError (builtin) exception.
def linux_interaction():
import sys
if "linux" not in sys.platform:
raise RuntimeError("Function can only run on Linux systems.")
print("Doing Linux things.")Python will raise a RuntimeError exception (a built in exception) if you call it on an operating system other then Linux.
Picking the right exception type can sometimes be tricky. Python comes with many built-in exceptions that are hierarchically related. so if you browse the documentation, you’re likely to find a fitting one, If you still didn’t find a fitting exception, then you can create a custom exception
Creating custom exception
class PlatformException(Exception):
"""Incompatible platform."""Custom exceptions are created by inheriting from Exception base class as shown above. You can inherit from different exception which has already inherited from the base Exception class.
class PlatformException(Exception):
"""Incompatible platform."""This is just example code.
def linux_interaction():
import sys
if "linux" not in sys.platform:
raise PlatformException("Function can only run on Linux systems.")
print("Doing Linux things.")If you now call linux_interaction() on macOS or Windows, then you’ll see that Python raises your custom exception:
$ python linux_interaction.py
Traceback (most recent call last):
...
PlatformException: Function can only run on Linux systems.If handle our exception using pass then, exception is not thrown
try:
linux_interaction()
except:
pass
! no outputBut letting an exception that occurred pass silently is bad practice. You should always at least know about and log if some type of exception occurred when you ran your code.
try:
linux_interaction()
except:
print("Linux function wasn't executed.")
.....
rest of the code
.....When you now execute this code on a macOS or Windows machine, you’ll see the message from your except block printed to the console:
$ python linux_interaction.py
Linux function wasn't executed.But we have suppressed the original exception message with our own message, but because we used the try and except sections, if exception was raised in try code, only that function will not be run, python will move on to rest of the code and execute rest of the program
try:
linux_interaction()
except RuntimeError as error:
print(error)
print("The linux_interaction() function wasn't executed.")In the except clause, you assign the RuntimeError to the temporary variable error—often also called err—so that you can access the exception object in the indented block. In this case, you’re printing the object’s string representation, which corresponds to the error message attached to the object.
Running this function on a macOS or Windows machine outputs the following:
$ python linux_interaction.py
Function can only run on Linux systems.
The linux_interaction() function wasn't executed.Notice that “Function can only run on Linux systems.” line is the line from original raise statement
and “The linux_interaction() function wasn’t executed.” is the string that we added after printing the exception “as error”
Sample code for exception handling
try:
with open("file.log") as file:
read_data = file.read()
except FileNotFoundError as fnf_error:
print(fnf_error)In this case, if file.log doesn’t exist, then the output will be the following:
$ python open_file.py
[Errno 2] No such file or directory: 'file.log'You can have more than one function call in your try clause and anticipate catching various exceptions. Something to note here is that the code in the try clause will stop as soon as it encounters any one exception.
Warning: When you use a bare except clause, then Python catches any exception that inherits from Exception—which are most built-in exceptions! Catching the parent class, Exception, hides all errors—even those which you didn’t expect at all.
Proceeding After a Successful Try With else
You can use Python’s else statement to instruct a program to execute a certain block of code only in the absence of exceptions:
try:
linux_interaction()
except RuntimeError as error:
print(error)
else:
print("Doing even more Linux things.")Running this code on Linux system will result in below
$ python linux_interaction.py
Doing Linux things.
Doing even more Linux things.Because the program didn’t run into any exceptions, Python executed the code in the else clause.
You can also create a nested try … except block inside the else clause and catch possible exceptions there as well:
try:
linux_interaction()
except RuntimeError as error:
print(error)
else:
try:
with open("file.log") as file:
read_data = file.read()
except FileNotFoundError as fnf_error:
print(fnf_error)If you were to execute this code on a Linux machine, then you’d get the following result:
$ python linux_interaction.py
Doing Linux things.
[Errno 2] No such file or directory: 'file.log'Cleaning Up After Execution With finally
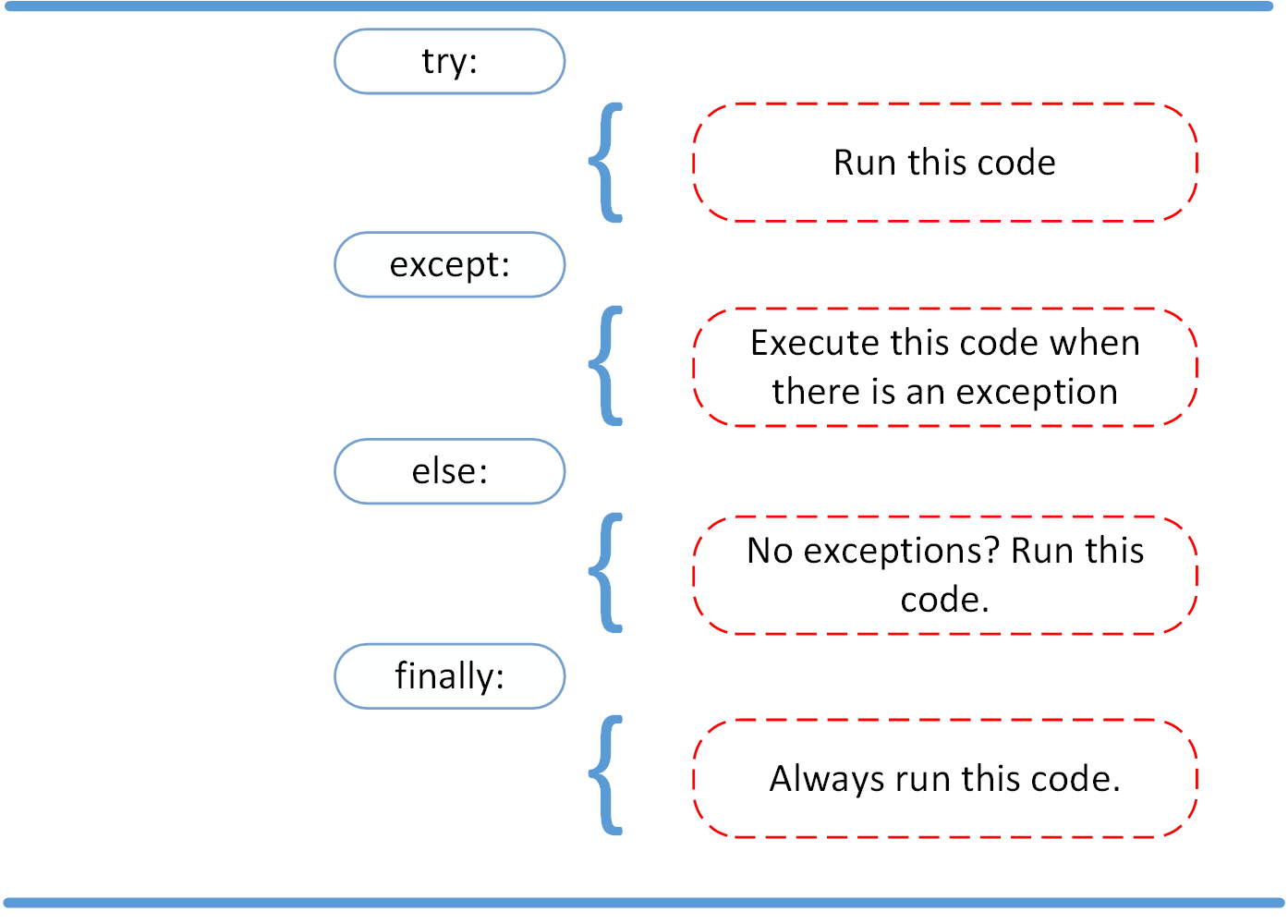
Imagine that you always had to implement some sort of action to clean up after executing your code. Python enables you to do so using the finally clause:
try:
linux_interaction()
except RuntimeError as error:
print(error)
else:
try:
with open("file.log") as file:
read_data = file.read()
except FileNotFoundError as fnf_error:
print(fnf_error)
finally:
print("Cleaning up, irrespective of any exceptions.")In this code, even if the exception is thrown at any point, code inside finally clause will always run, Running the code on a macOS or Windows machine will output the following:
$ python linux_interaction.py
Function can only run on Linux systems.
Cleaning up, irrespective of any exceptions.one more example where exception is raised but not handled using except block but only finally block is present
try:
linux_interaction()
finally:
print("Cleaning up, irrespective of any exceptions.")running this code we get
$ python linux_interaction.py
Cleaning up, irrespective of any exceptions.
Traceback (most recent call last):
...
RuntimeError: Function can only run on Linux systems.Despite the fact that Python raised the RuntimeError, the code in the finally clause still executed and printed the message to your console. This can be helpful because even code outside of a try… except block won’t necessarily execute if your script encounters an unhandled exception. In that case, your program will terminate and the code after the try … except block will never run. However, Python will still execute the code inside of the finally clause. This helps you make sure that resources like file handles and database connections are cleaned up properly.
Dictionary unpacking
Dictionary unpacking (or argument unpacking) in python allows a dictionary passed to function as argument, python then unpacks the dictionary so that each key–value pair is passed as a named argument, because dictionary conforms to arguments, each element in dictionary has unique and named keys with values which is why dictionary can be unpacked
switches_dic = {
"device_type": "cisco_ios",
"ip": "10.0.101.12",
"username": "admin",
"password": "cisco",
}
net_connect = ConnectionHandler(**switches_dic)This is equivalent to
net_connect = ConnectionHandler(
device_type="cisco_ios",
ip="10.0.101.12",
username="admin",
password="cisco"
)SSH connection handling with Netmiko and Cisco devices with use_textfsm
from netmiko import ConnectHandler
import json
from prettytable import PrettyTable
# ConnectHandler is responsible for handling SSH connection
# json will help us with parsing the retrned data from SSH
# create a dictionary containing IP address of the switches to login to
switches_dic = {
"device_type": "cisco_ios",
"ip": "192.168.0.201",
"username": "admin",
"password": "cisco",
}
net_connect = ConnectHandler(**switches_dic)
# unpack the dictionary with its key and values as arguments
# output = net_connect.send_command("show ip route | exc subnetted")
output = net_connect.send_command("show ip int brief", use_textfsm=True)
net_connect.disconnect()
interfaces_table = PrettyTable(["Interface", "IP address", "Status", "Protocol"])
for dict in output:
interfaces_table.add_row(
[dict["interface"], dict["ip_address"], dict["status"], dict["proto"]]
)
print(interfaces_table)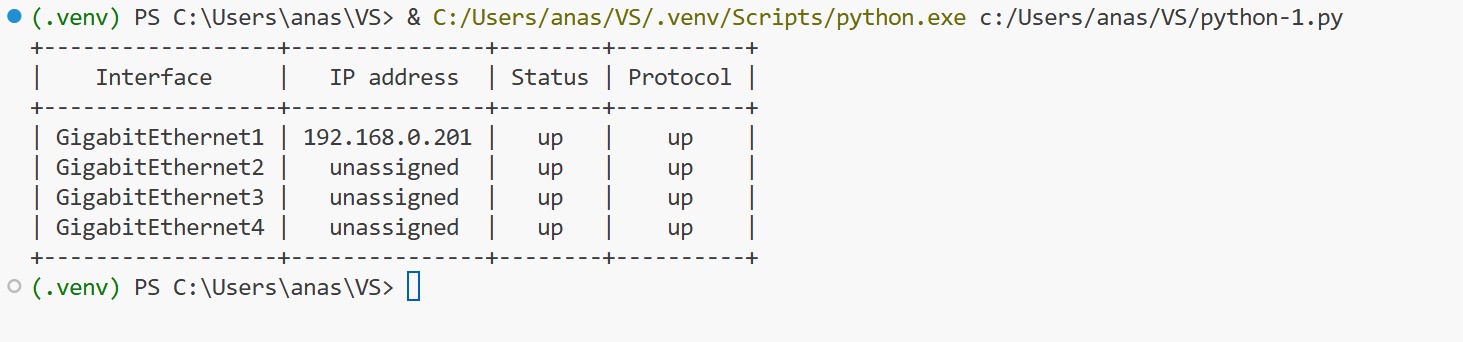
SSH connection handling with Netmiko and Cisco devices without use_textfsm
from netmiko import ConnectHandler
import json
from prettytable import PrettyTable
# ConnectHandler is responsible for handling SSH connection
# json will help us with parsing the retrned data from SSH
# create a dictionary containing IP address of the switches to login to
switches_dic = {
"device_type": "cisco_ios",
"ip": "192.168.0.201",
"username": "admin",
"password": "cisco",
}
net_connect = ConnectHandler(**switches_dic)
# unpack the dictionary with its key and values as arguments
output = net_connect.send_command("show ip route | exc subnetted")
net_connect.disconnect()
print(output)
"""
interfaces_table = PrettyTable(["Interface", "IP address", "Status", "Protocol"])
for list in output:
interfaces_table.add_row(
[list["interface"], list["ip_address"], list["status"], list["proto"]]
)
print(interfaces_table)
"""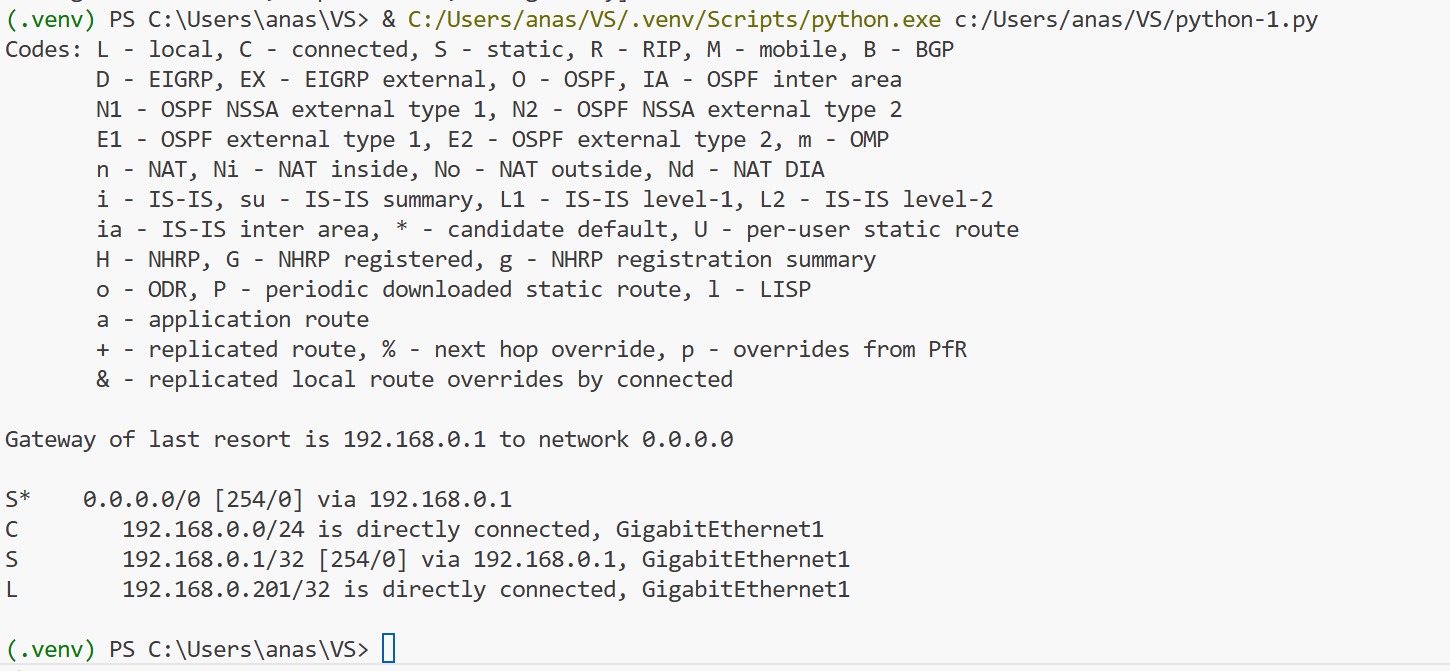
next post
Difference between BPDU guard & Root guard
Difference between BPDU guard & Root guard
What Is the Difference Between STP BPDU Guard and STP Root Guard
BPDU guard and root guard are similar, but their impact is different. BPDU guard disables the port upon BPDU reception if PortFast is enabled on the port. The disablement effectively denies devices behind such ports from participation in STP. You must manually reenable the port that is put into errdisable state or configure errdisable-timeout .
Root guard allows the device to participate in STP as long as the device does not try to become the root. If root guard blocks the port, subsequent recovery is automatic. Recovery occurs as soon as the deviant device ceases to send superior BPDUs.