SEC0406 – Firepower 7.0 AnyConnect VPN Certificate Authentication Windows (Part 1)
SEC0406 – Firepower 7.0 AnyConnect VPN Certificate Authentication Windows (Part 1)
Certificate Authentication
Having non certificate based authentication means that if user knows their credentials then they can install anyconnect and use it from any device, connecting your network to another network making their machine a transit machine and deliver malware in network
This can be locked down using certificate based authentication
This way device can be locked down and credentials are locked down as well
These certificates are pushed using GPO and this machine certificate is used automatically for anyconnect certificate authentication
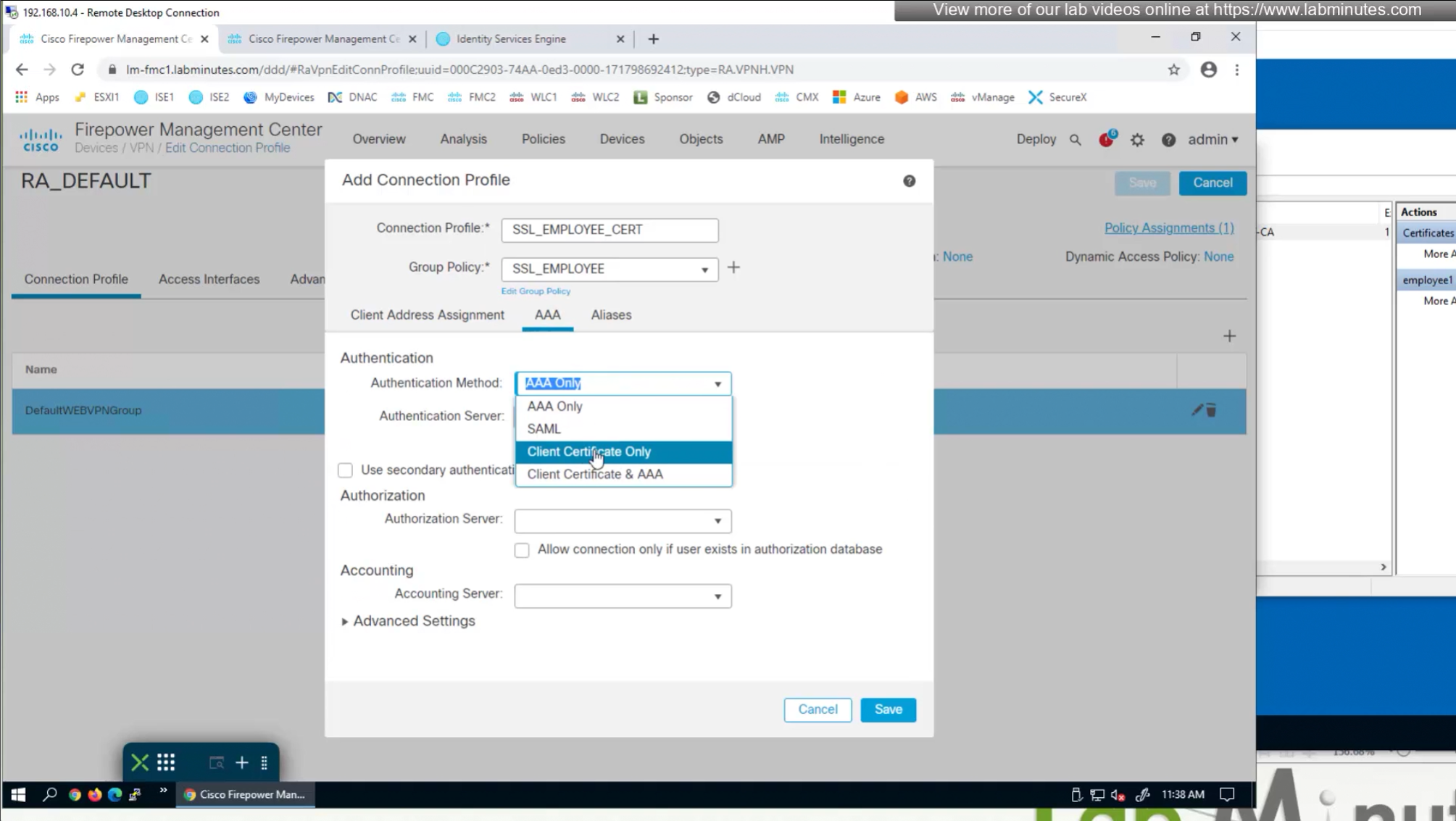
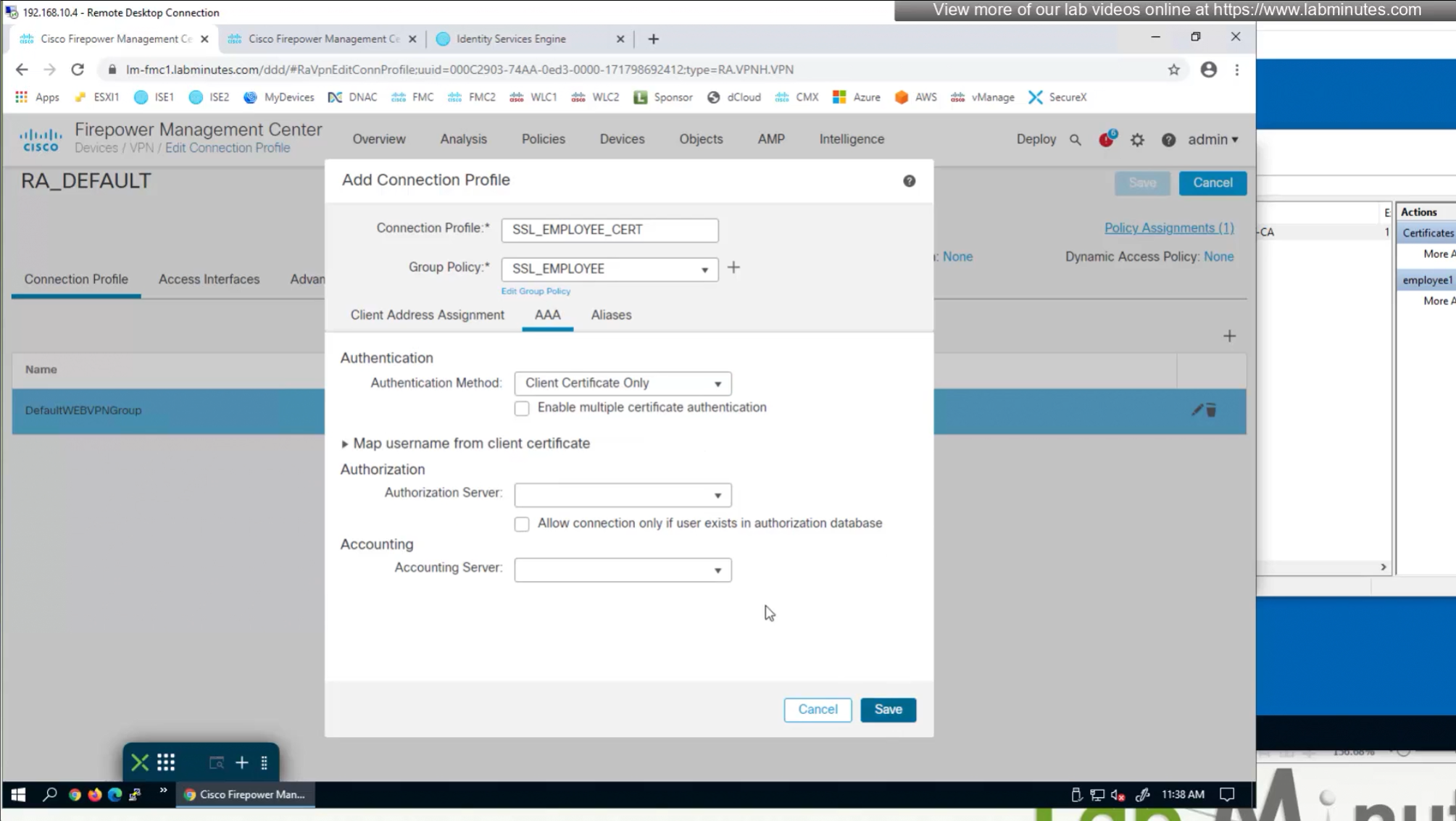
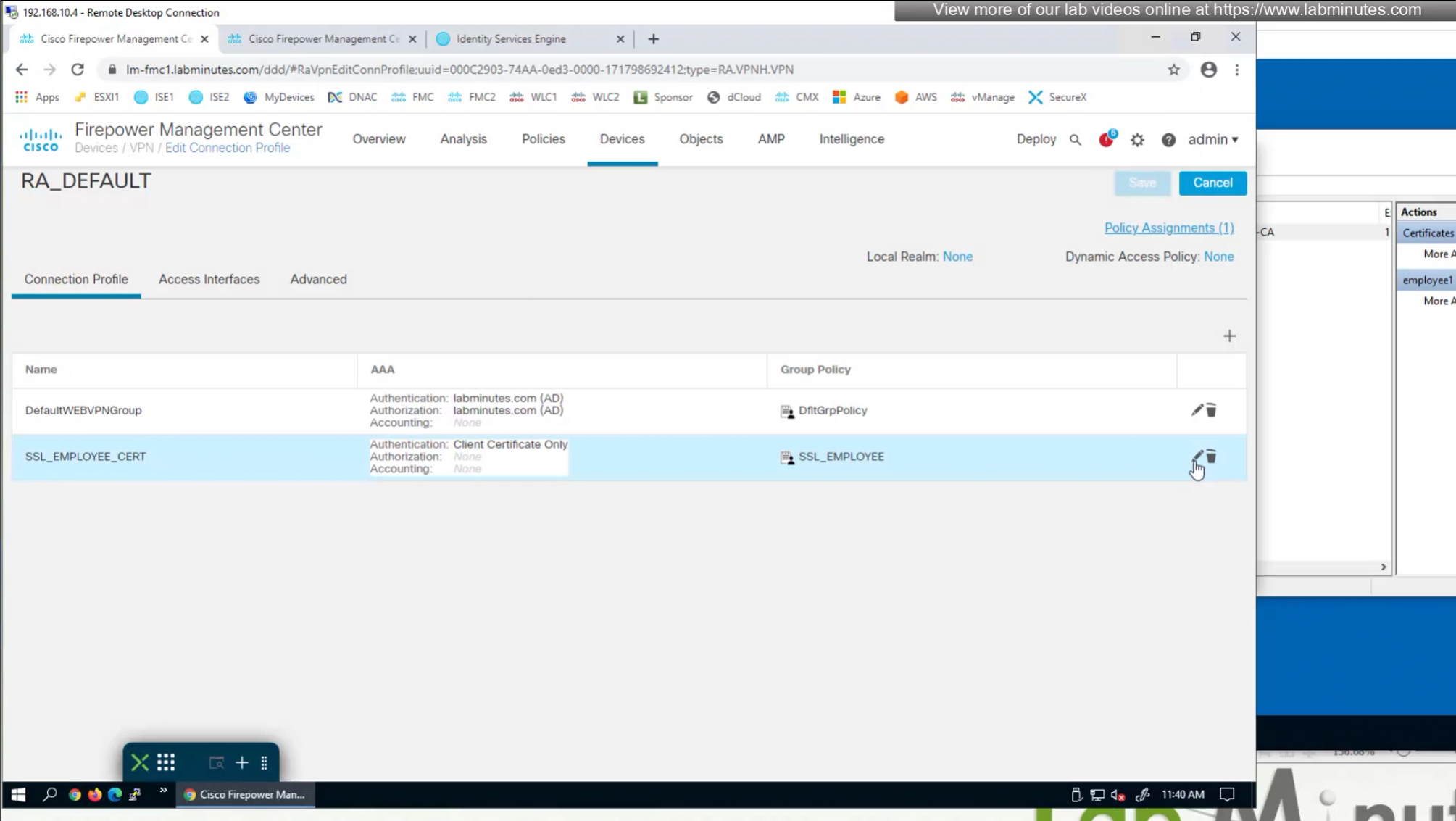
We need to create new connection profile because current connection profile is configured with AAA authentication and only one type of authentication can be configured on connection profile, either Certificate based authentication or AAA based authentication
That is why we will configure new connection profile
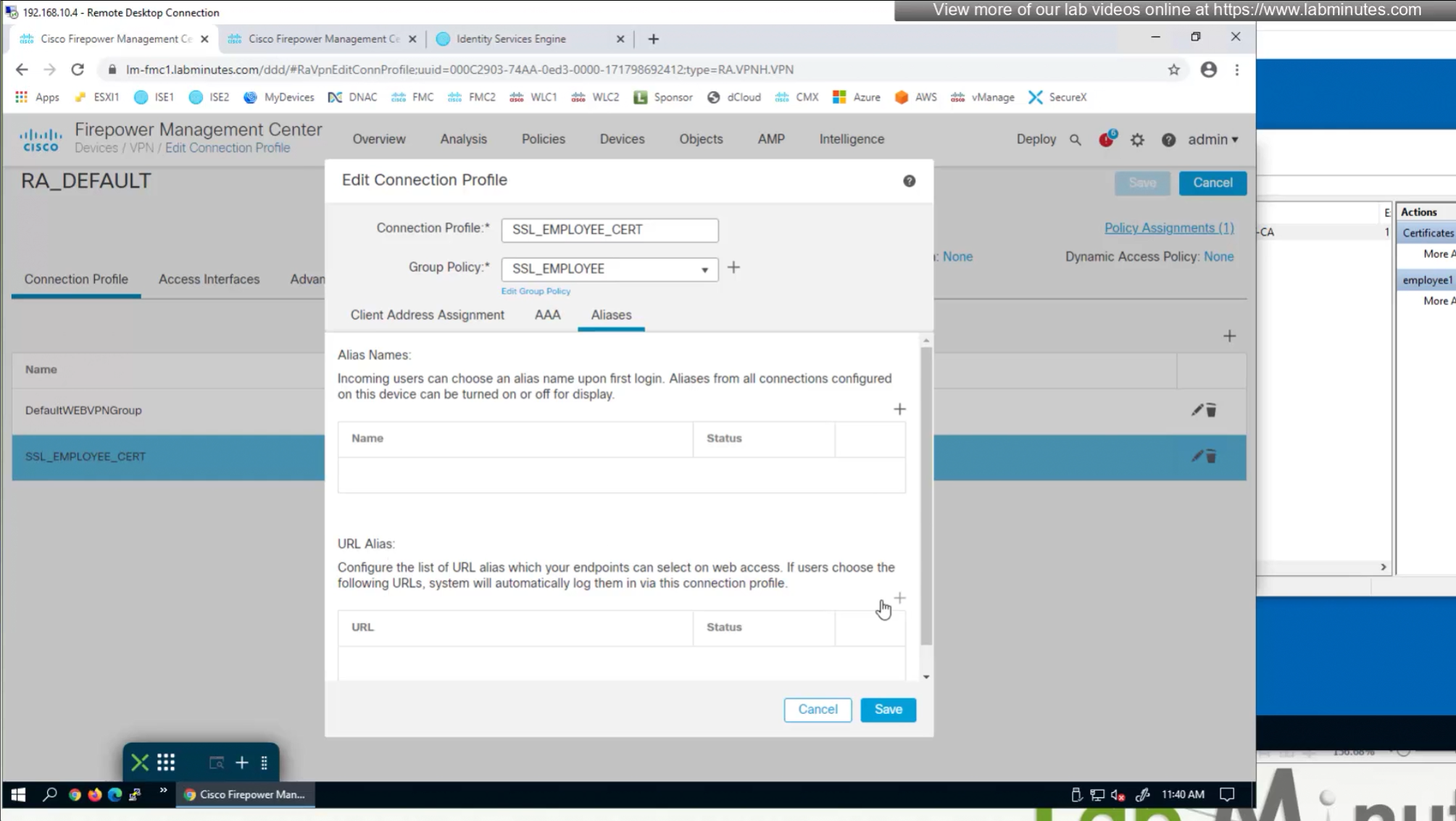
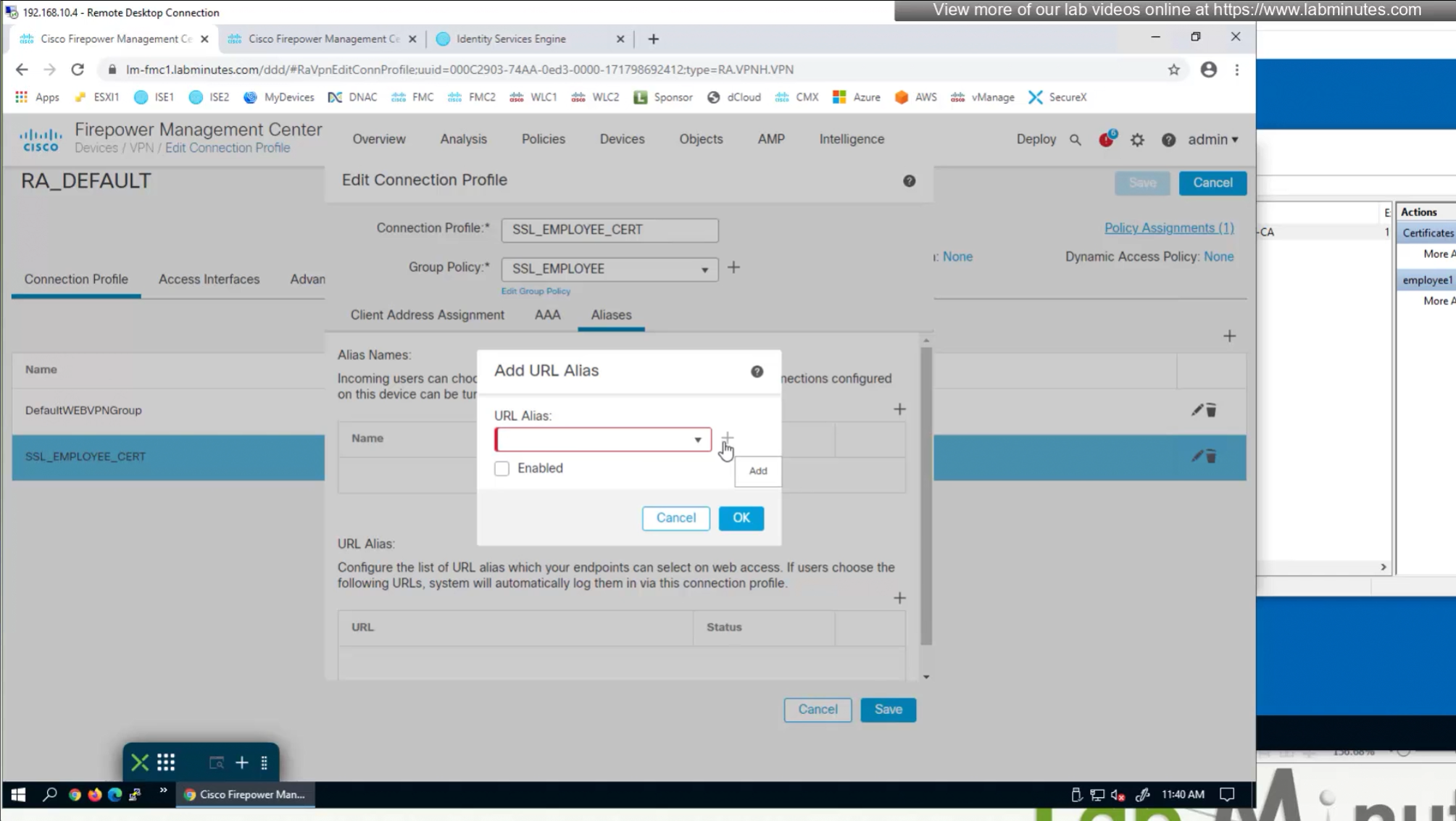
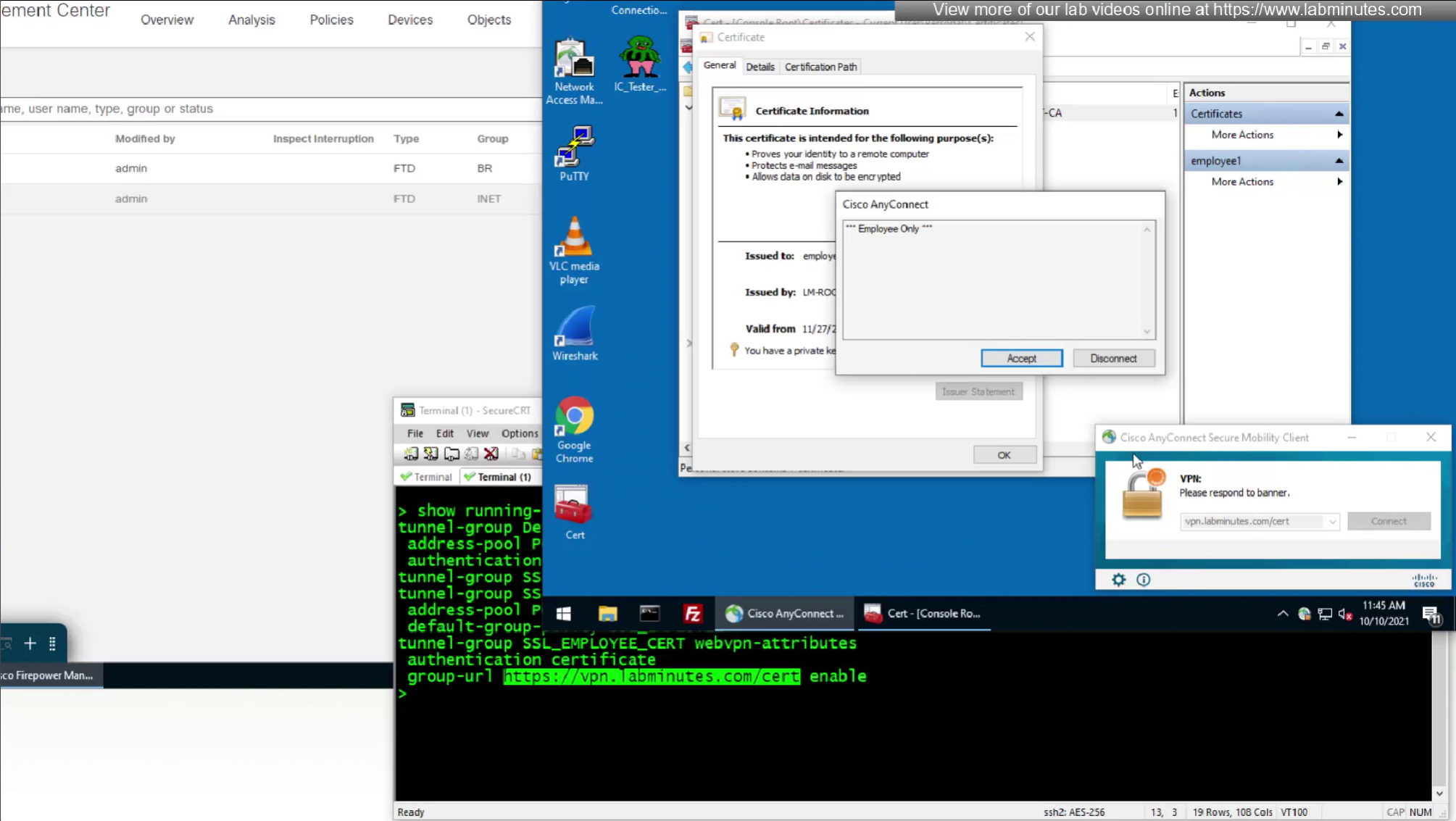
Question is how we get VPN users to use this certificate authentication connection profile
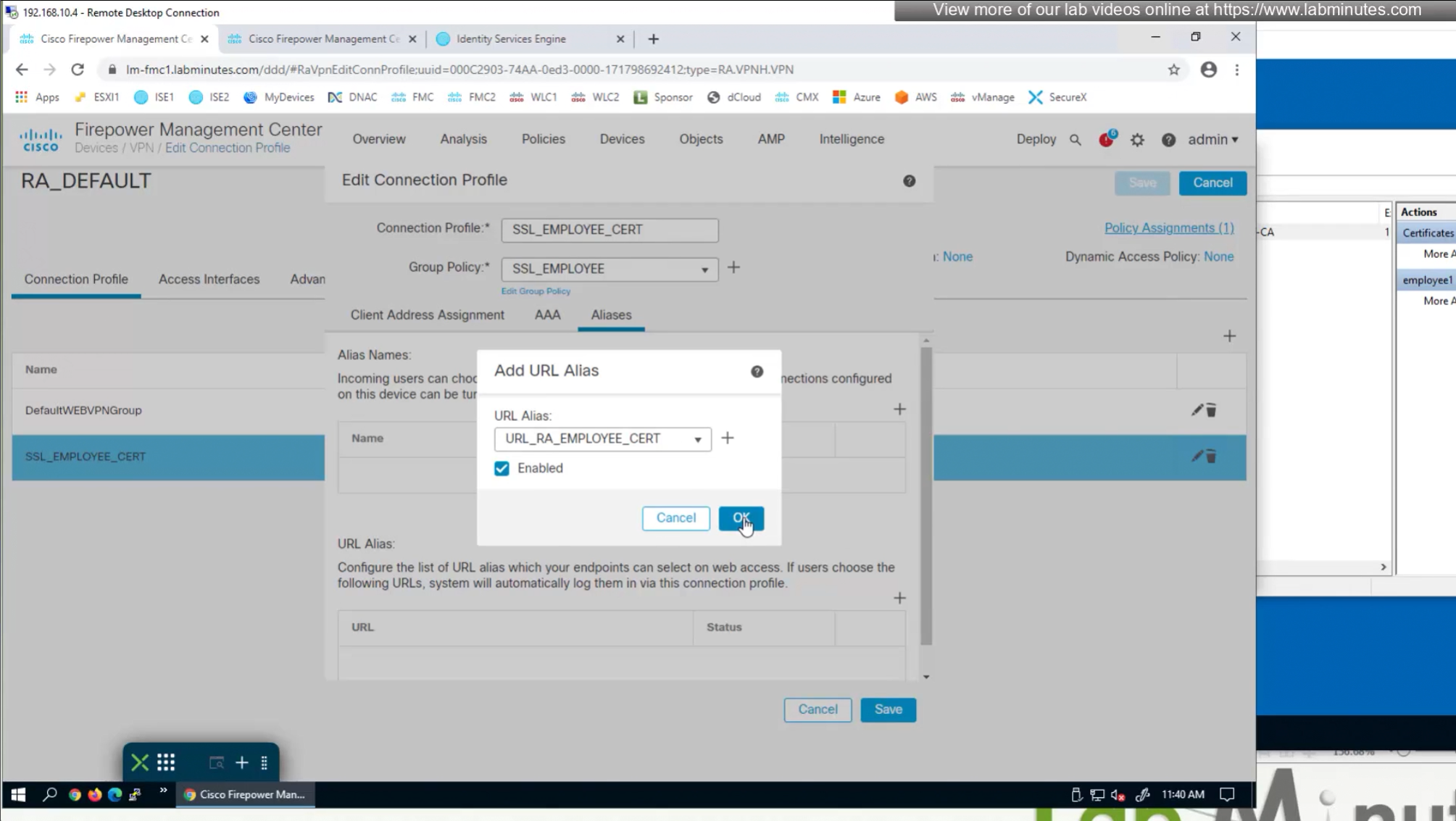
- Either enable group alias like before
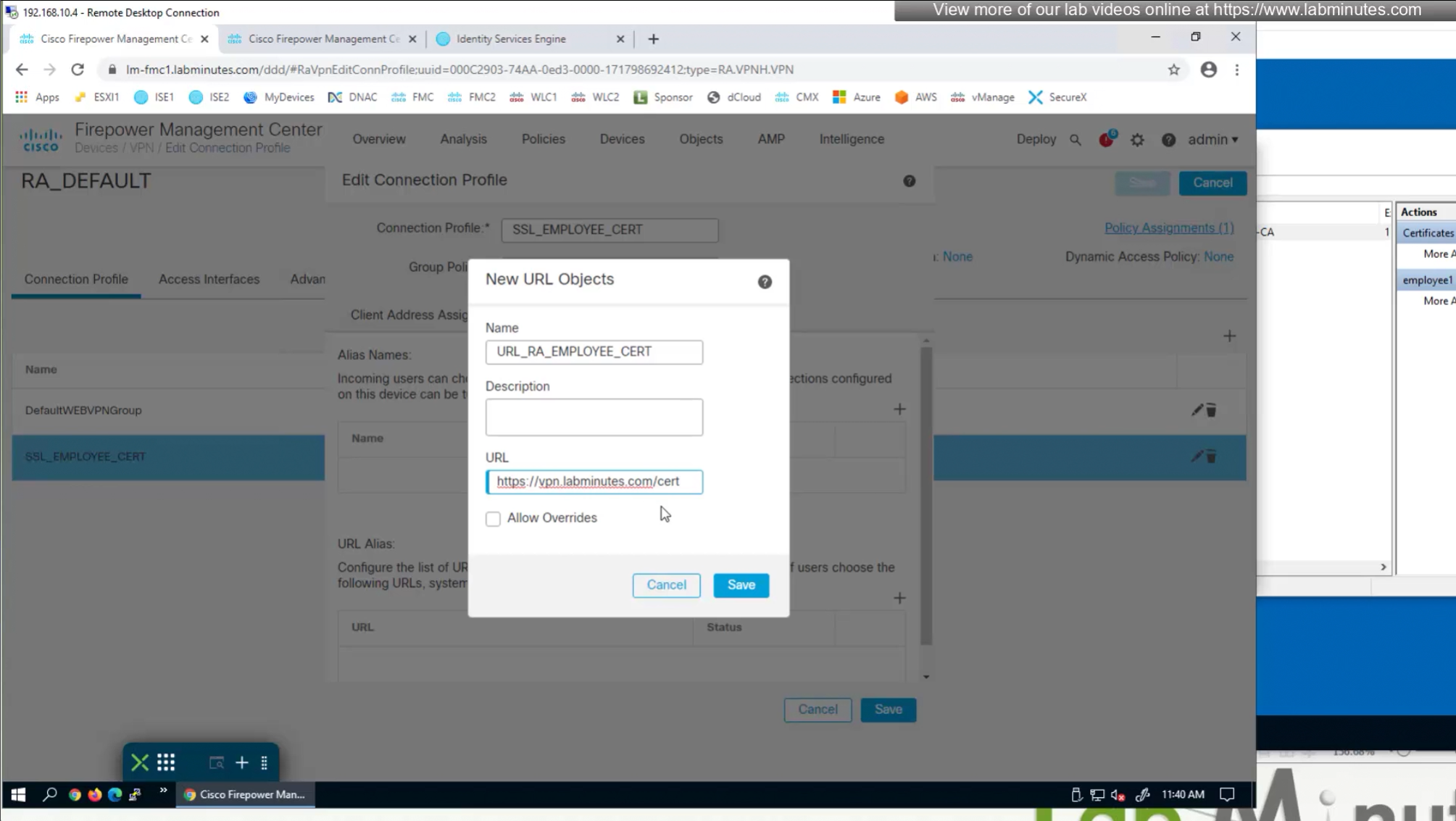
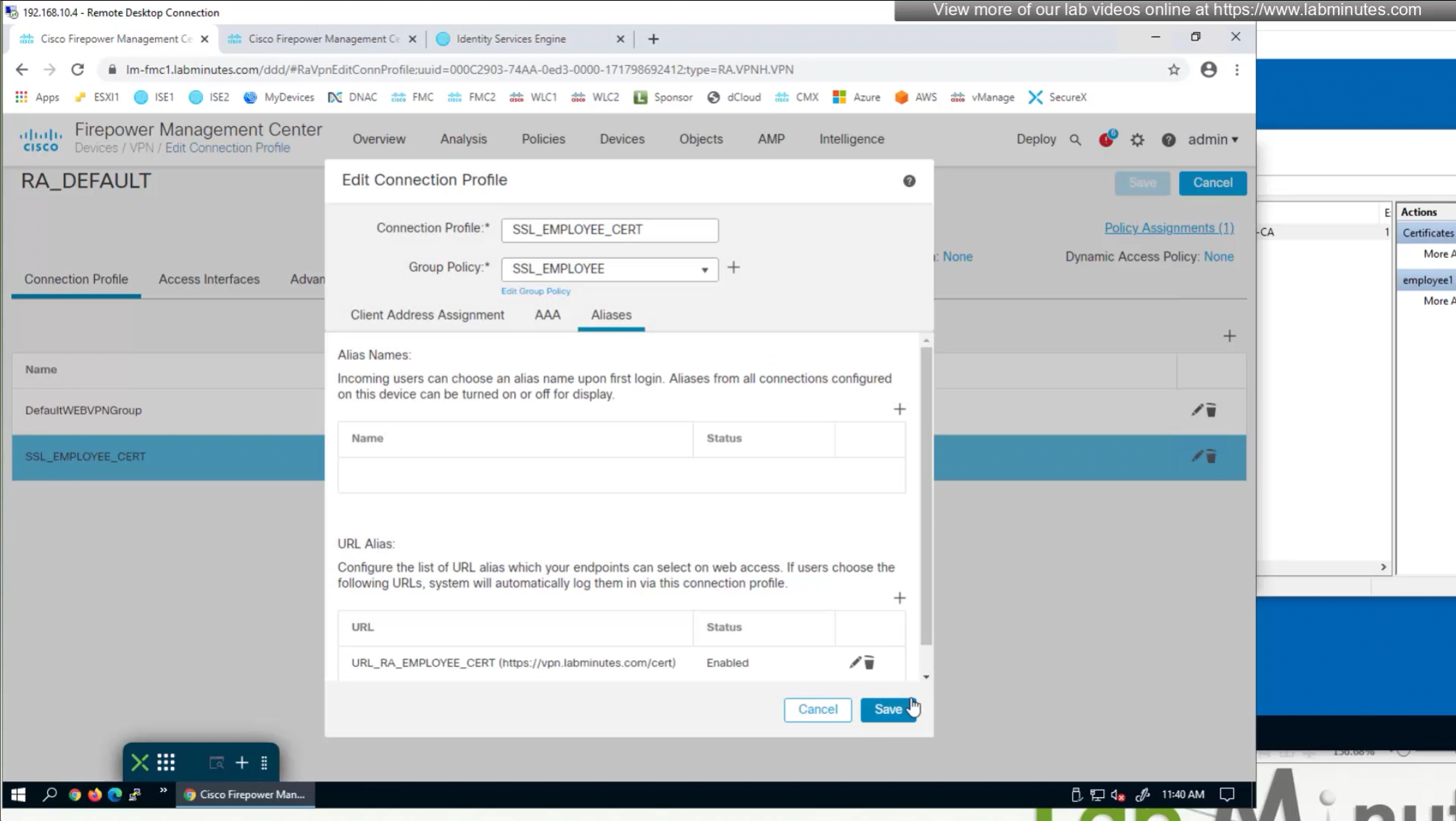
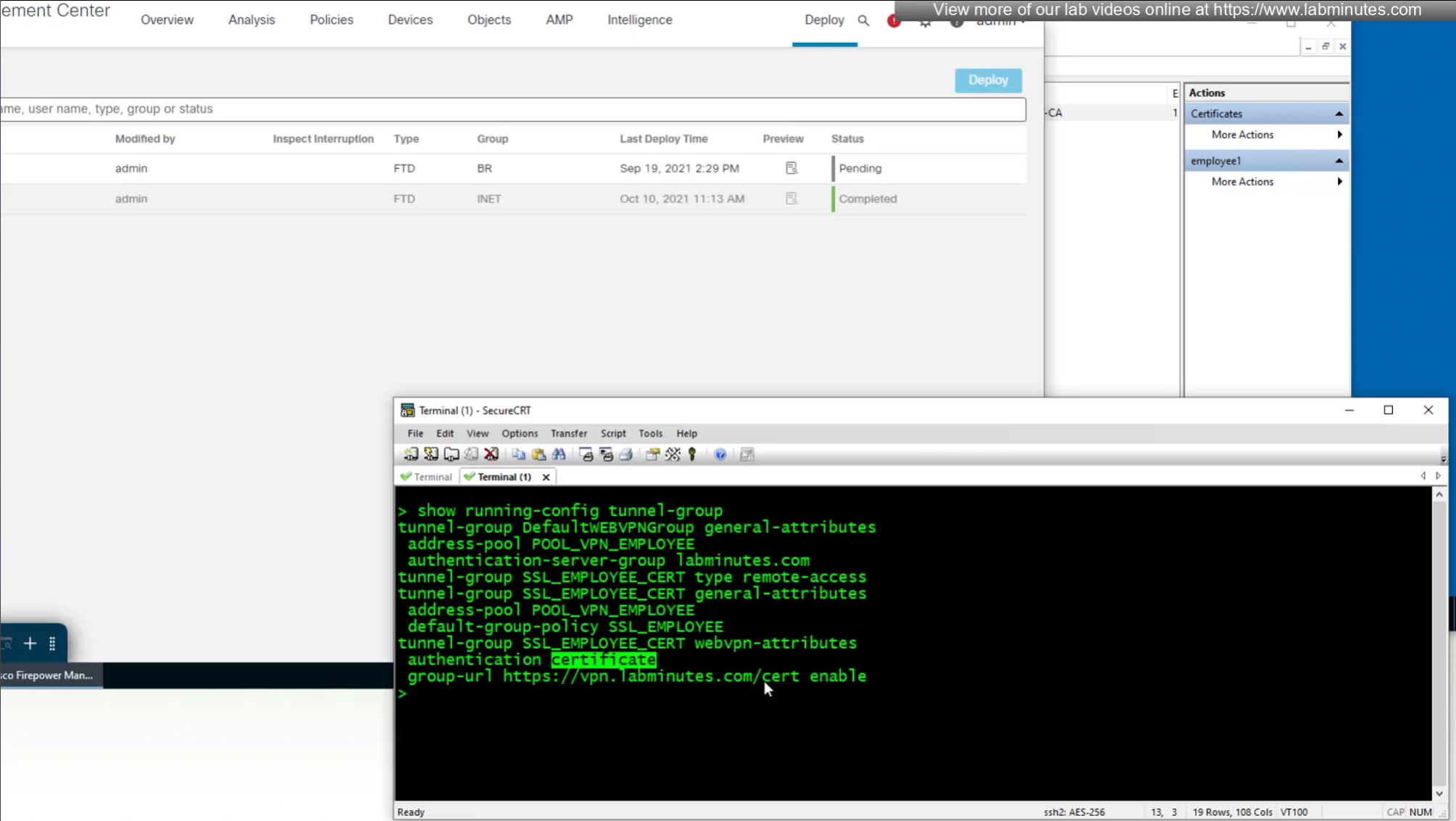
- (Preferred) We can provide a different URL for different connection profiles
URL is preferred and in some deployments URL part is treated as complex string to use it as a password and lock it down further with initial connection at build time and have anyconnect locked down

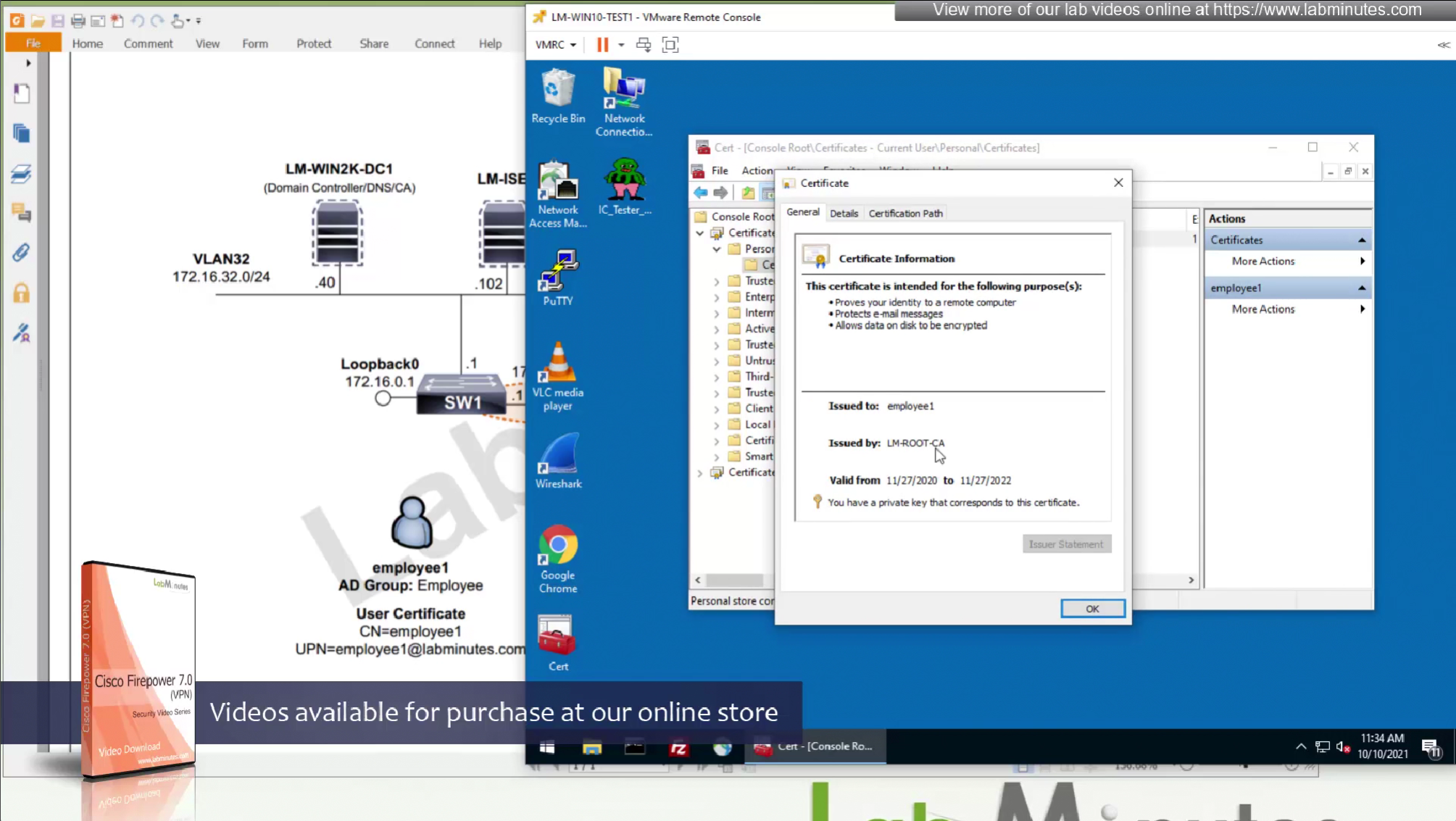
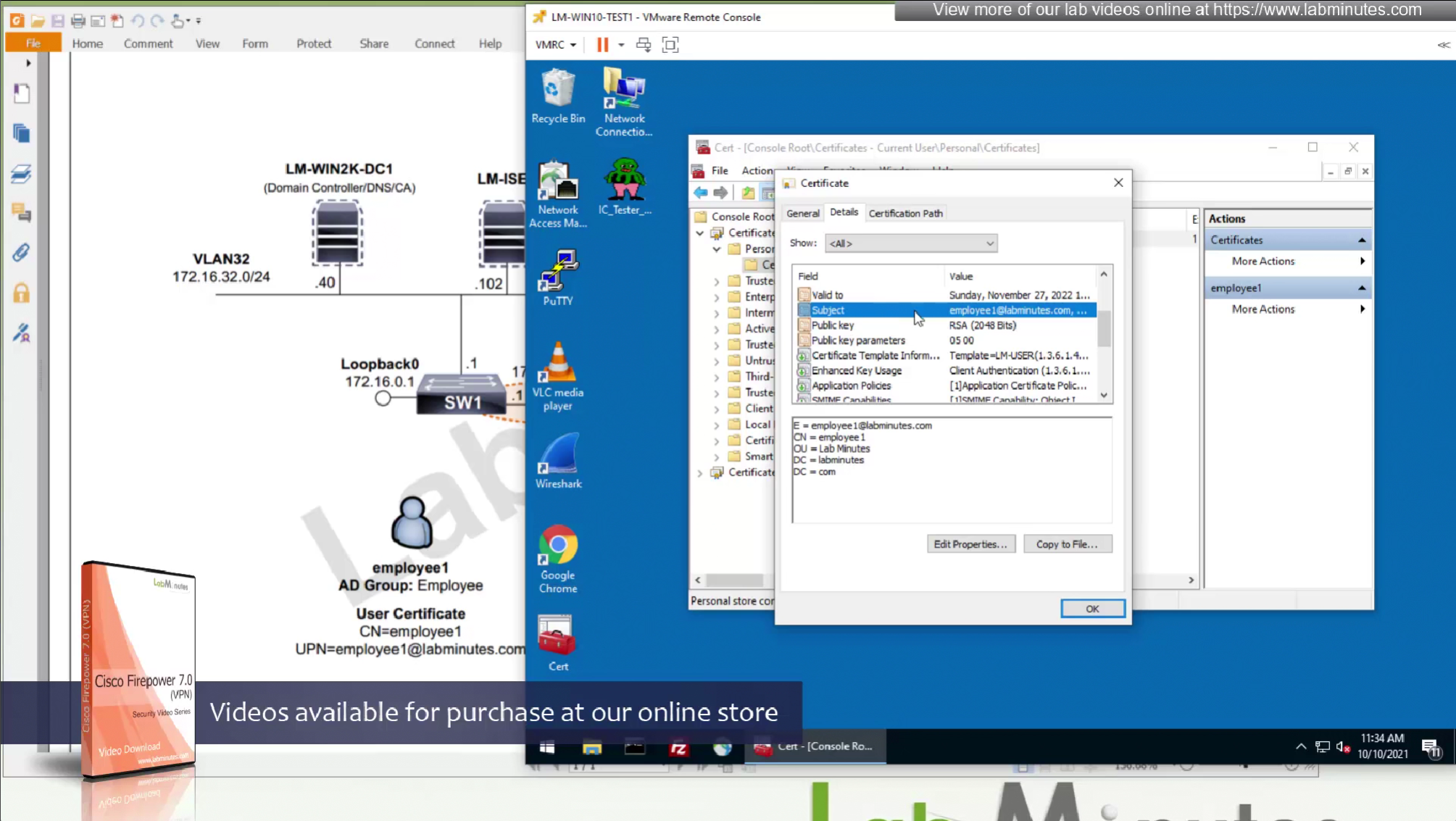
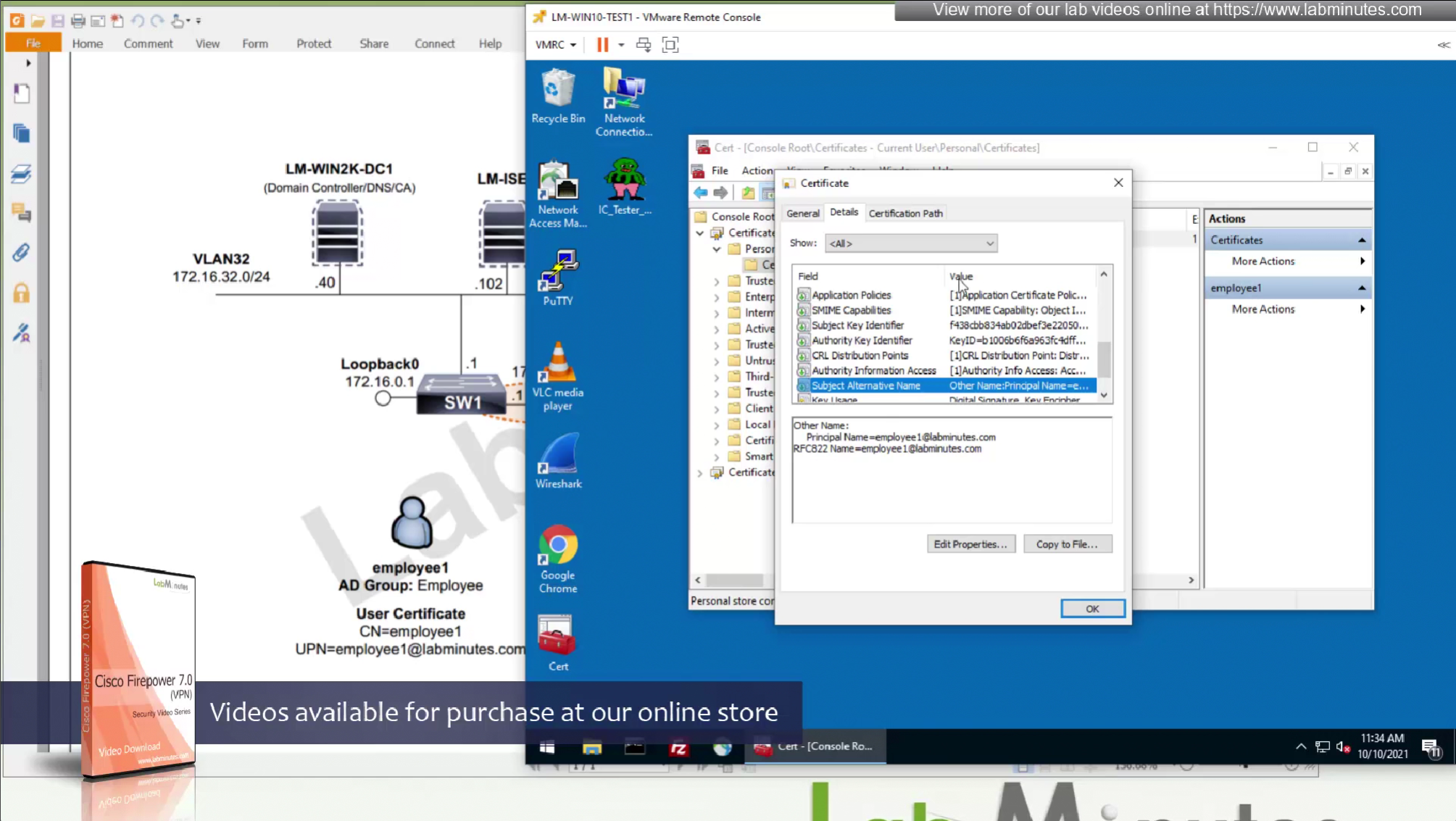
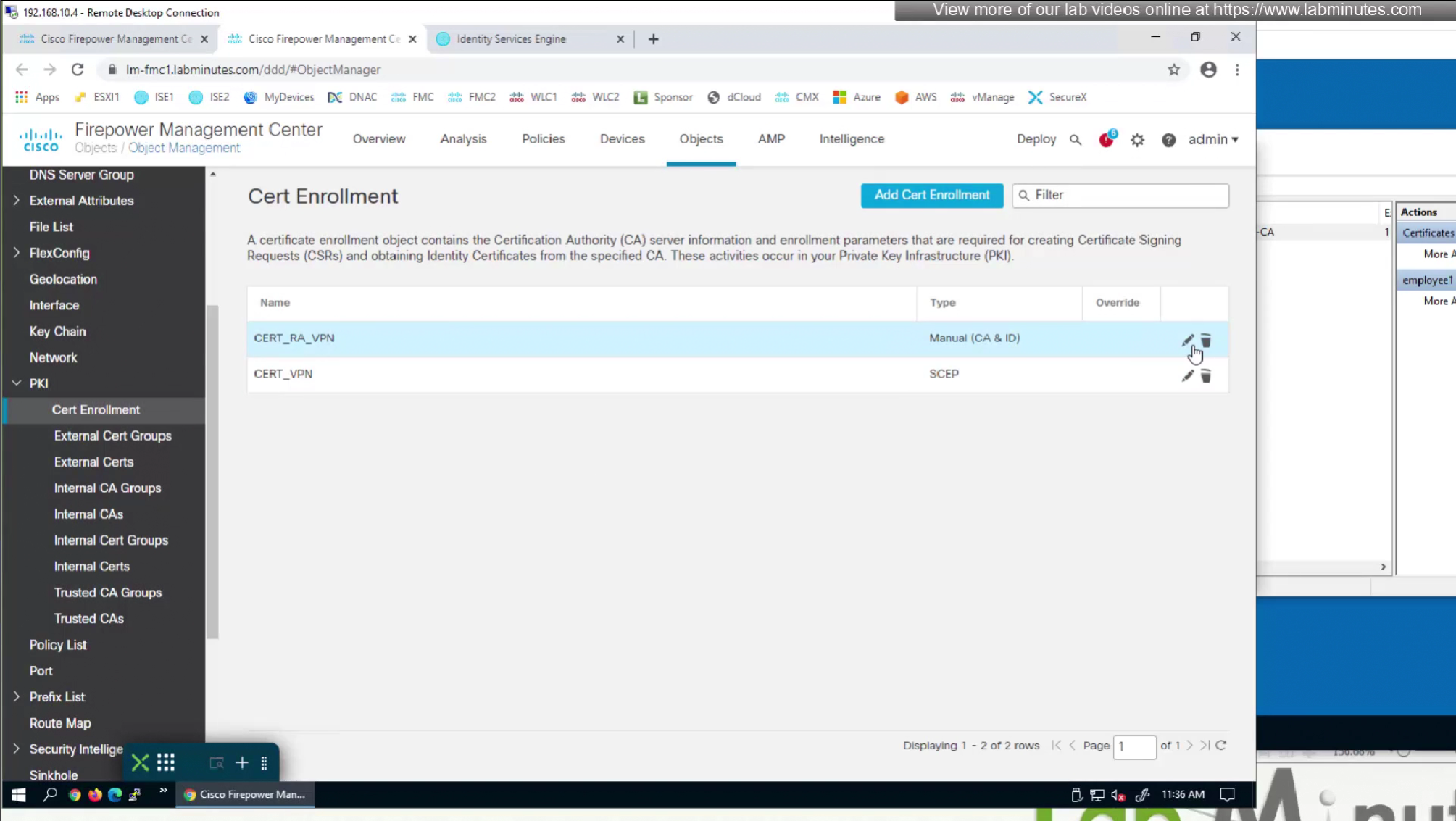
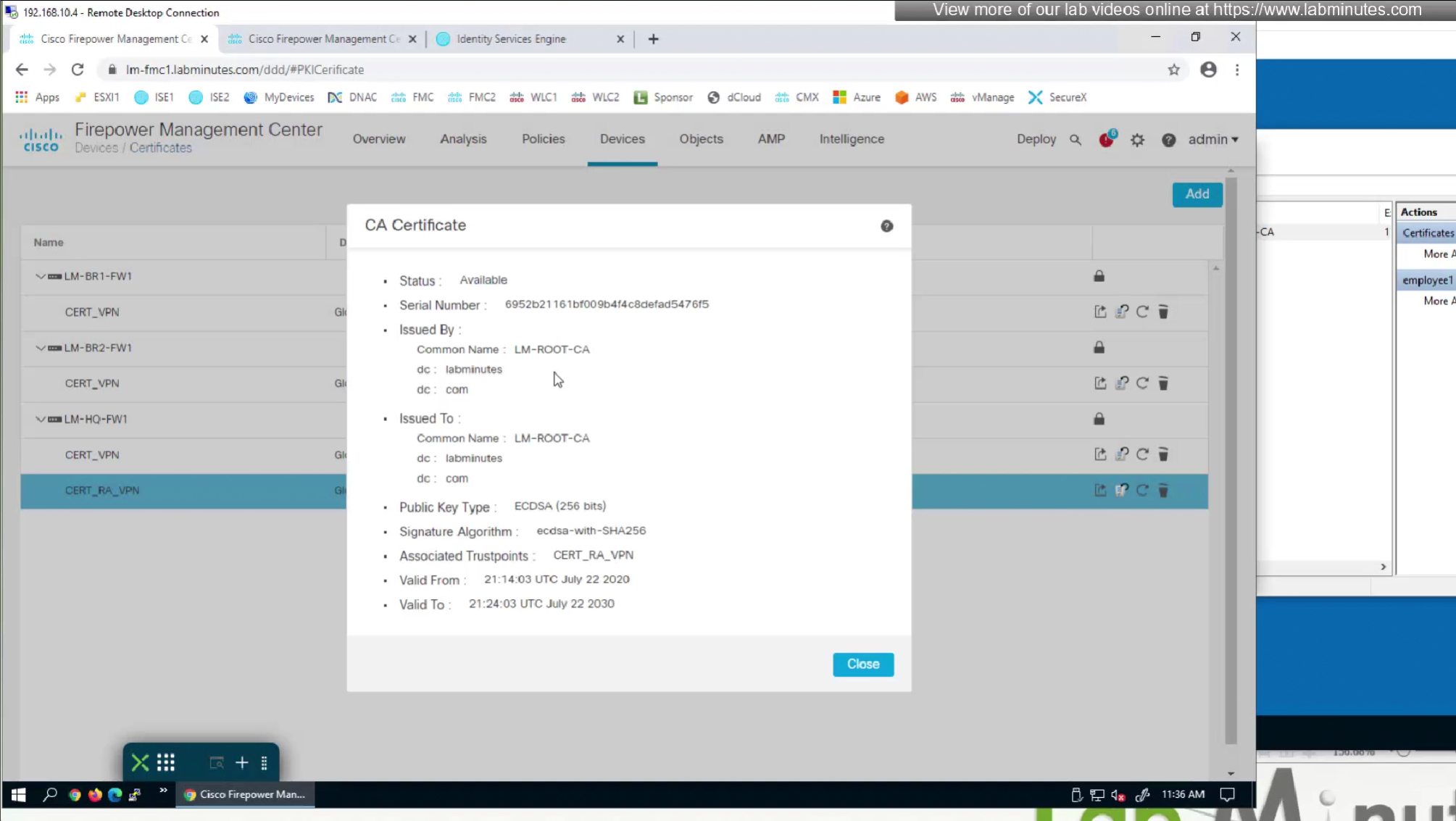
CA certificate is already on firewall as it was done as part of the Cert enrollment